Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases
Ransomware is a type of malicious software that locks users out of their system or data using different methods to force them to pay a ransom. Most often, such programs encrypt files on an infected machine and demand a fee to be paid in exchange for the decryption key. Additionally, such programs can be used to steal sensitive information from the compromised computer and even conduct DDoS attacks against affected organizations to pressure them into paying.

 890
890
 0
0

 530
530
 0
0

 2830
2830
 0
0
Ransomware is malware that restricts access to a computer system or its data until a ransom is paid. This can be done in a variety of ways.
For instance, screen locker ransomware blocks access to the system by overlaying the display with a ransom note window, prompting the user to make a payment to get control over the machine back.
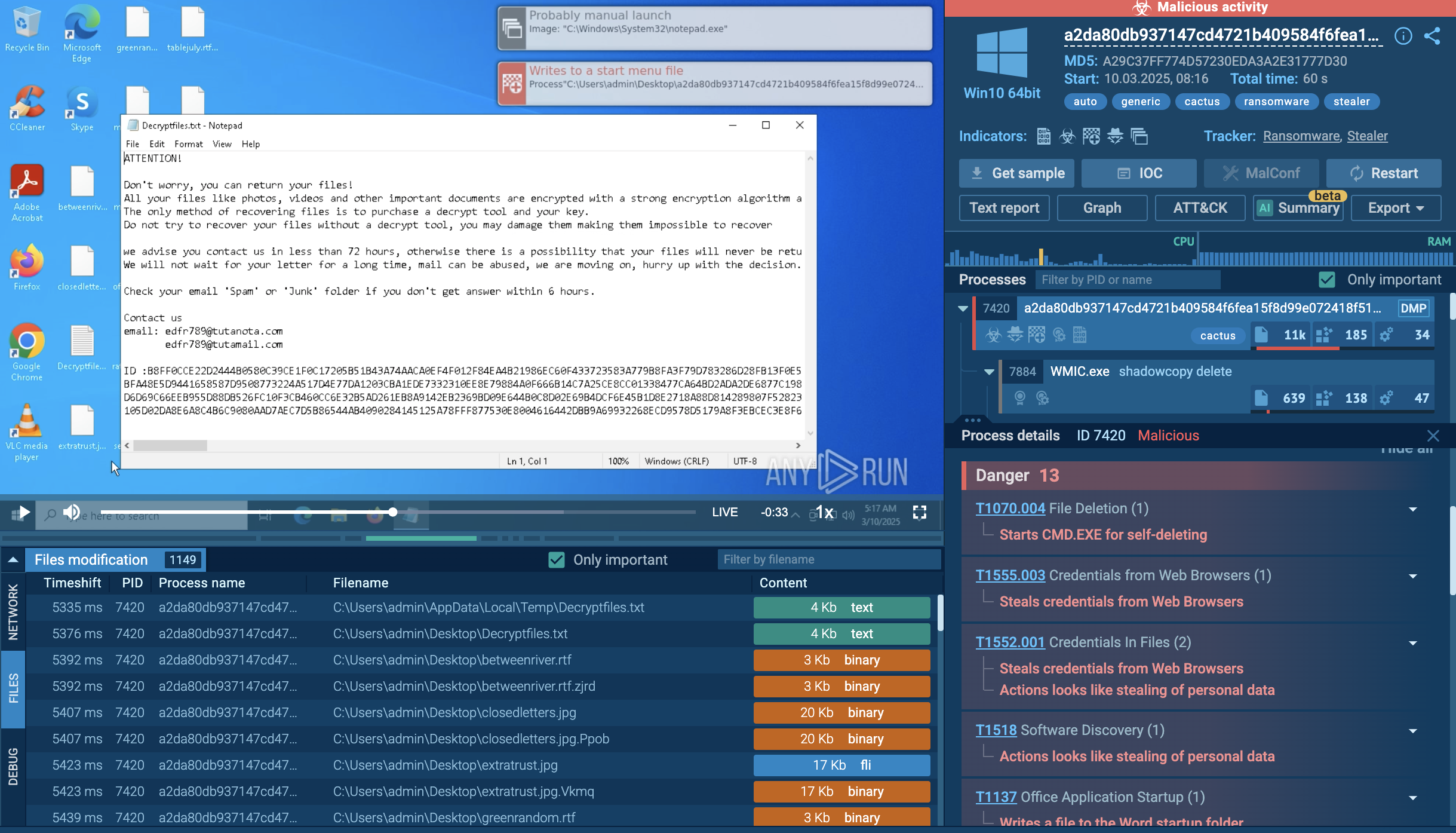
However, the primary type of ransomware used by attackers nowadays is crypto-ransomware, which specifically uses encryption to hold data hostage. This means that the attacker scrambles the victim's files using a strong encryption algorithm, making them unreadable without the decryption key that can be obtained only after paying a ransom.
At the same time, some malware may employ fake encryption as a deceptive tactic to instill fear and pressure victims into paying ransoms. For example, STRRAT, a Java-based malware, is known for appending the .crimson extension to victims' files. However, this encryption is merely a superficial disguise, as users can easily restore access to their files by manually removing the added extension.
Certain strains of wiper malware disguise themselves as ransomware, exploiting victims' desperation for data recovery. These malicious programs permanently destroy files while falsely promising decryption upon ransom payment.
A ransomware attack is the process by which cybercriminals infiltrate a computer system or network and deploy malicious software that encrypts or locks critical data, rendering it inaccessible to the owner.
Ransomware attacks can target individuals, businesses, and organizations of all sizes, causing significant disruption, financial losses, and reputational damage. The attackers often exploit vulnerabilities in software, operating systems, or human behavior.
While attackers often promise to restore the victim’s access to their system once they pay a fee, there is never a guarantee they will do it. In many cases, attackers simply take the money and disappear. On top of that, paying criminals further encourages them to continue carrying out illicit activities.
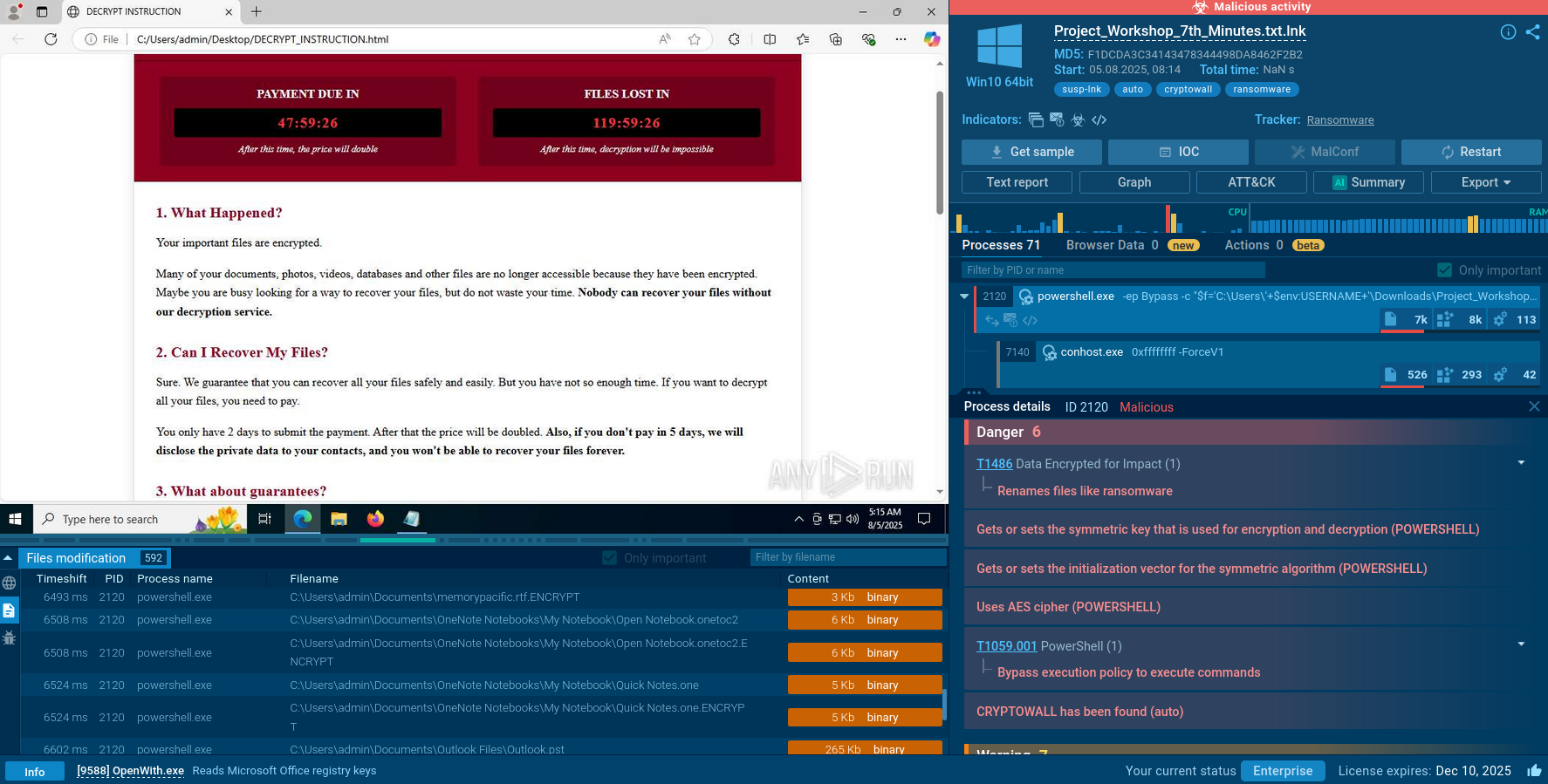
Although how ransomware works depends on particular malware families, it usually begins with system infiltration through various means, such as phishing emails, malicious links, or software vulnerabilities.
Most frequently, once the ransomware is installed on a victim's device, it will encrypt the victim's files, making them unreadable. The attacker will then display a message, often in the form of a text file or a separate window, demanding a payment to be made in cryptocurrency or other hard-to-trace method of payment.
Analyze malware for free in a fully interactive cloud sandbox – sign up now!
The exact amount of the ransom demand can vary widely. For instance, the WannaCry ransomware requested $300 to be paid within 3 days, when targeting individuals, while organizations that suffered an extensive network infection had to fork out millions of dollars. In their turn, the criminals behind LostTrust require their victims to pay at least $100,000.
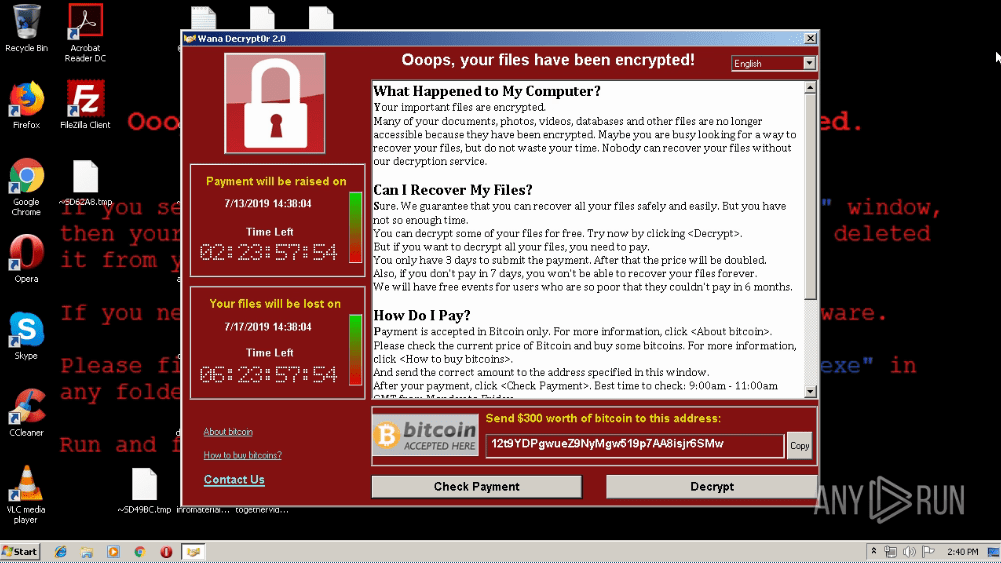 A desktop displaying the WannaCry ransom note
A desktop displaying the WannaCry ransom note
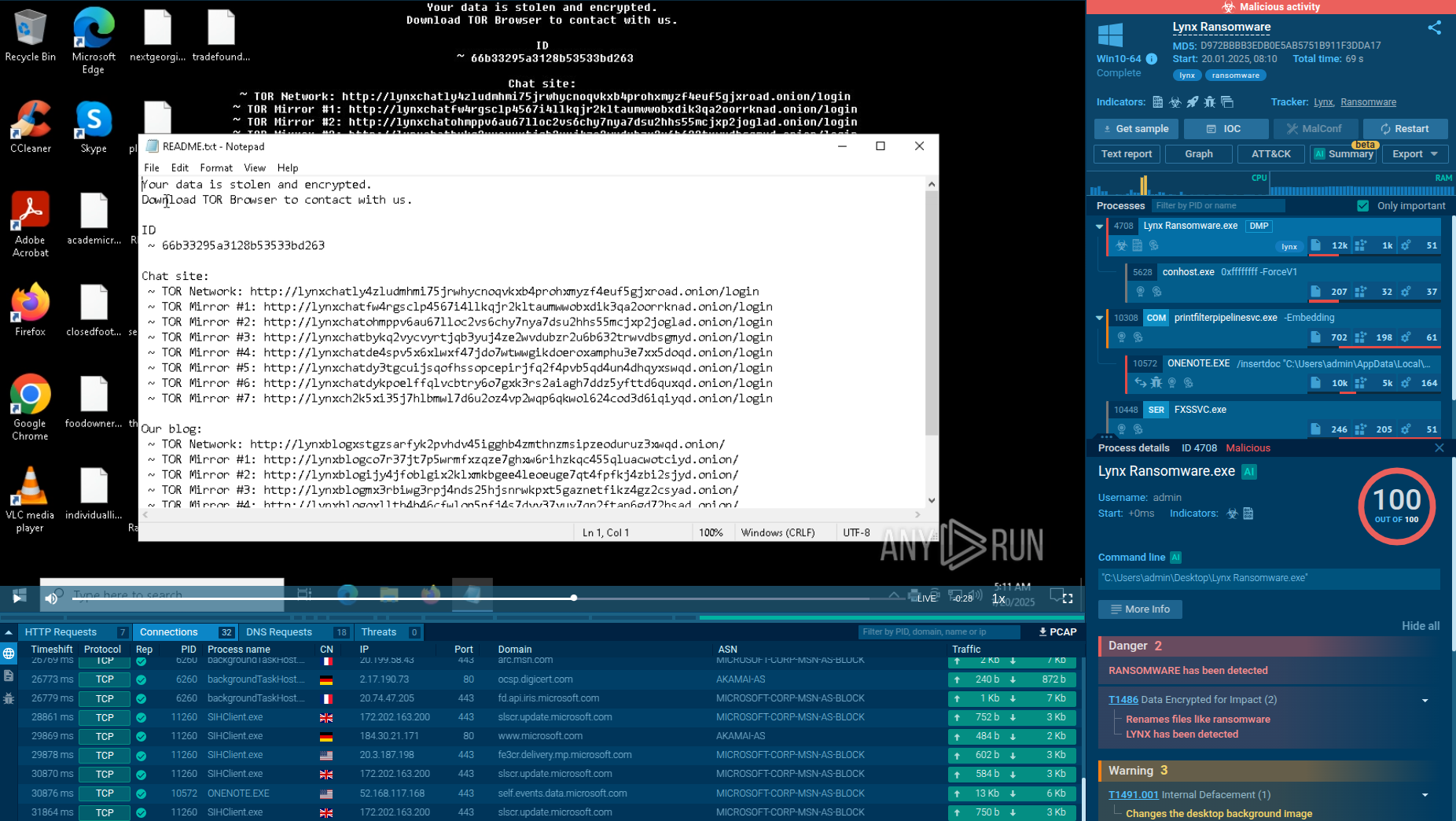
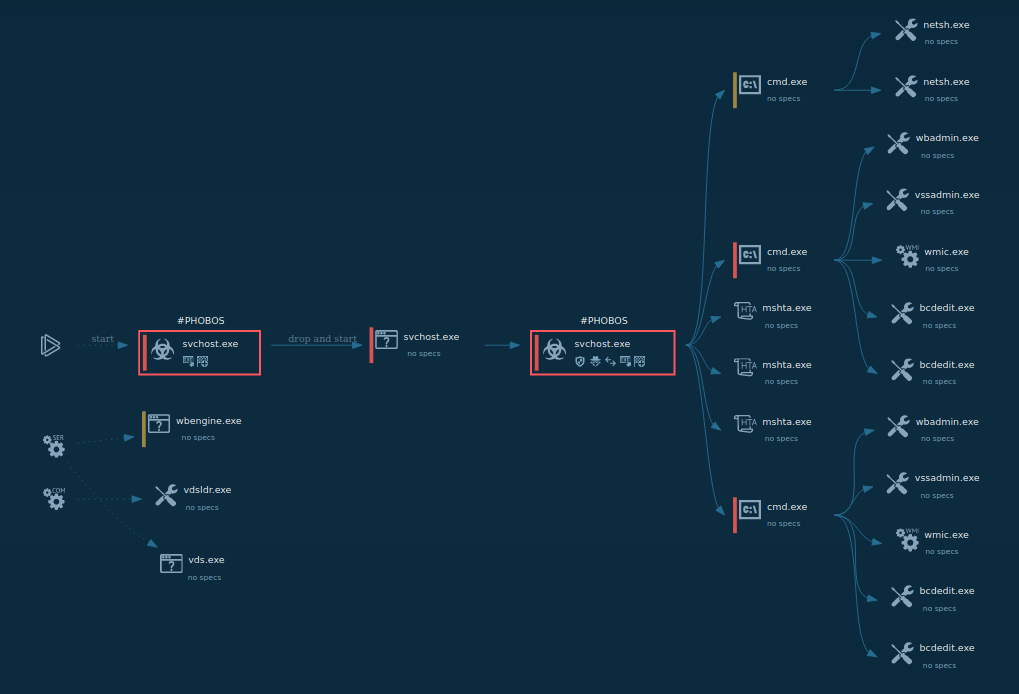
Let’s use the LockBit malware family to see how a typical ransomware works:
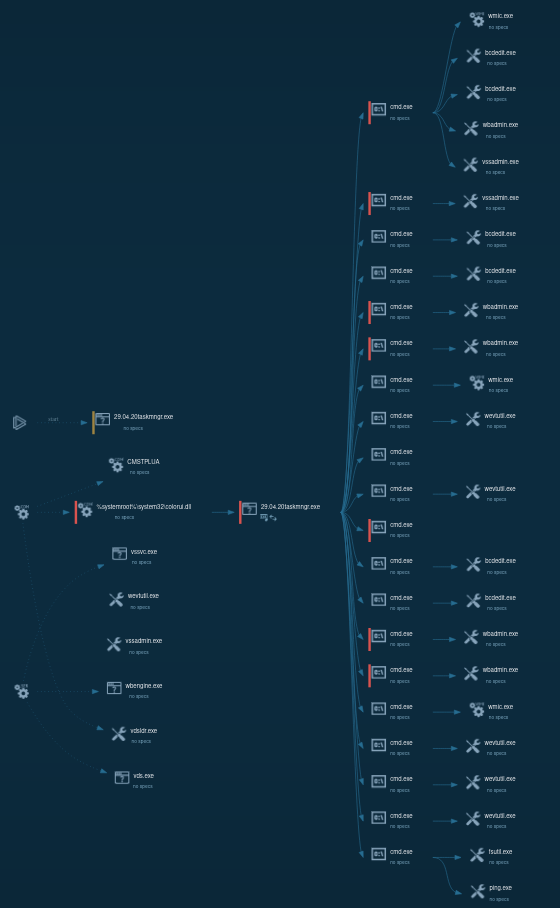 LockBit 1.0 process graph
LockBit 1.0 process graph
Ransomware deals a serious blow to endpoint devices, causing several major detrimental effects:
In order to track both active and no longer operational ransomware families, use ANY.RUN’s Malware Trends Tracker.
Here are some of the notable examples of ransomware, according to the service:
Phishing emails serve as the primary weapon of choice for ransomware attackers. These carefully crafted messages, often disguised as legitimate communications from trusted entities like banks or online services, aim to deceive recipients into clicking malicious links or opening infected attachments.
Ransomware can also move laterally, which is to spread across the entire network of computers, once it gains a foothold on one of them. Additionally, many malware families are distributed via file sharing services, where they can be masqueraded as legitimate software.
Alternatively, ransomware can end up on systems through the means of loaders, special malware designs with the sole purpose of distributing other malicious programs.
Ransomware is an extremely widespread type of malware and knowing how to protect from ransomware is essential for every organization valuing its cybersecurity. A comprehensive defense stack against attacks consists of multiple solutions, including the malware sandbox that can be employed in different scenarios.
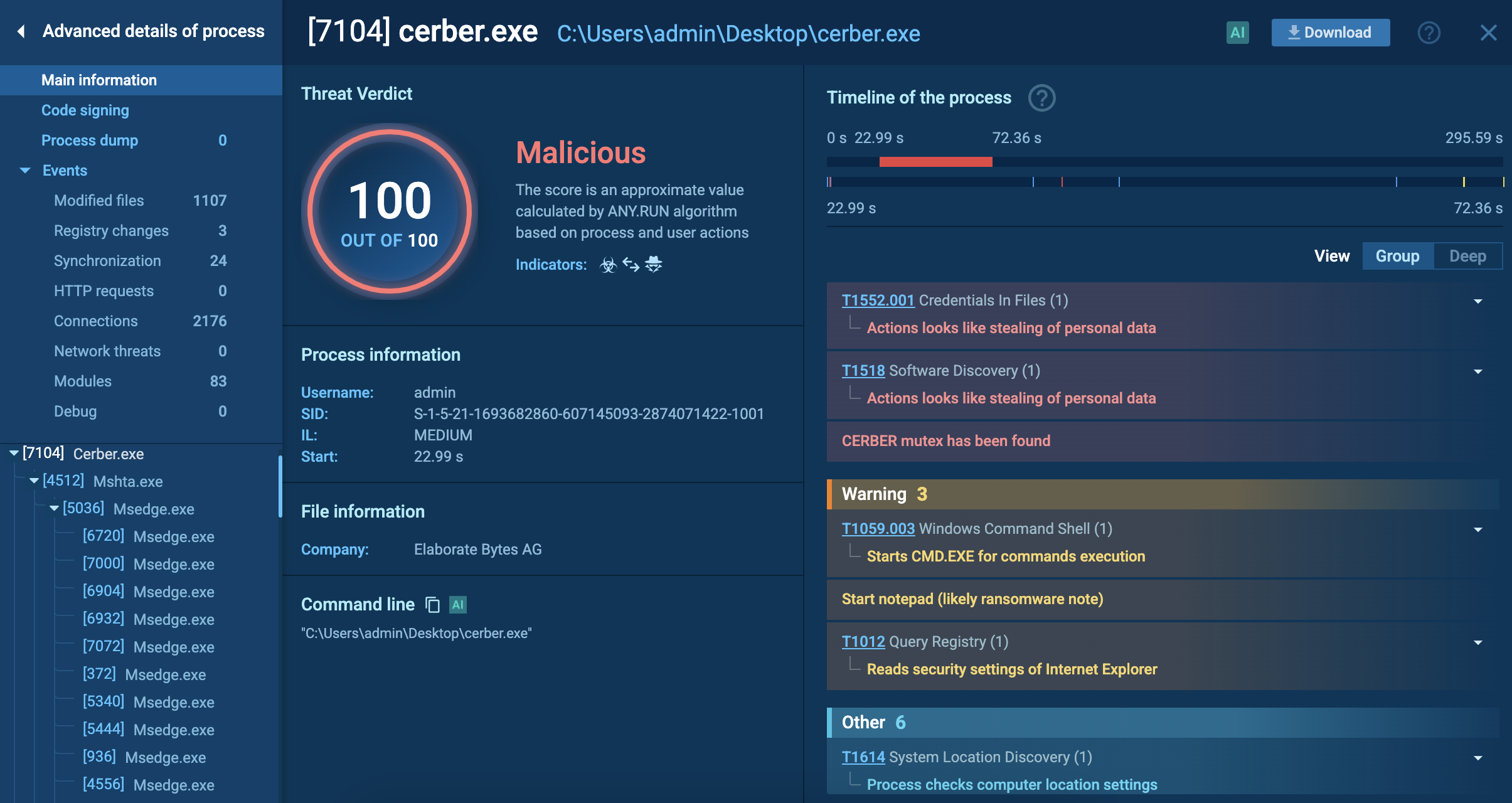
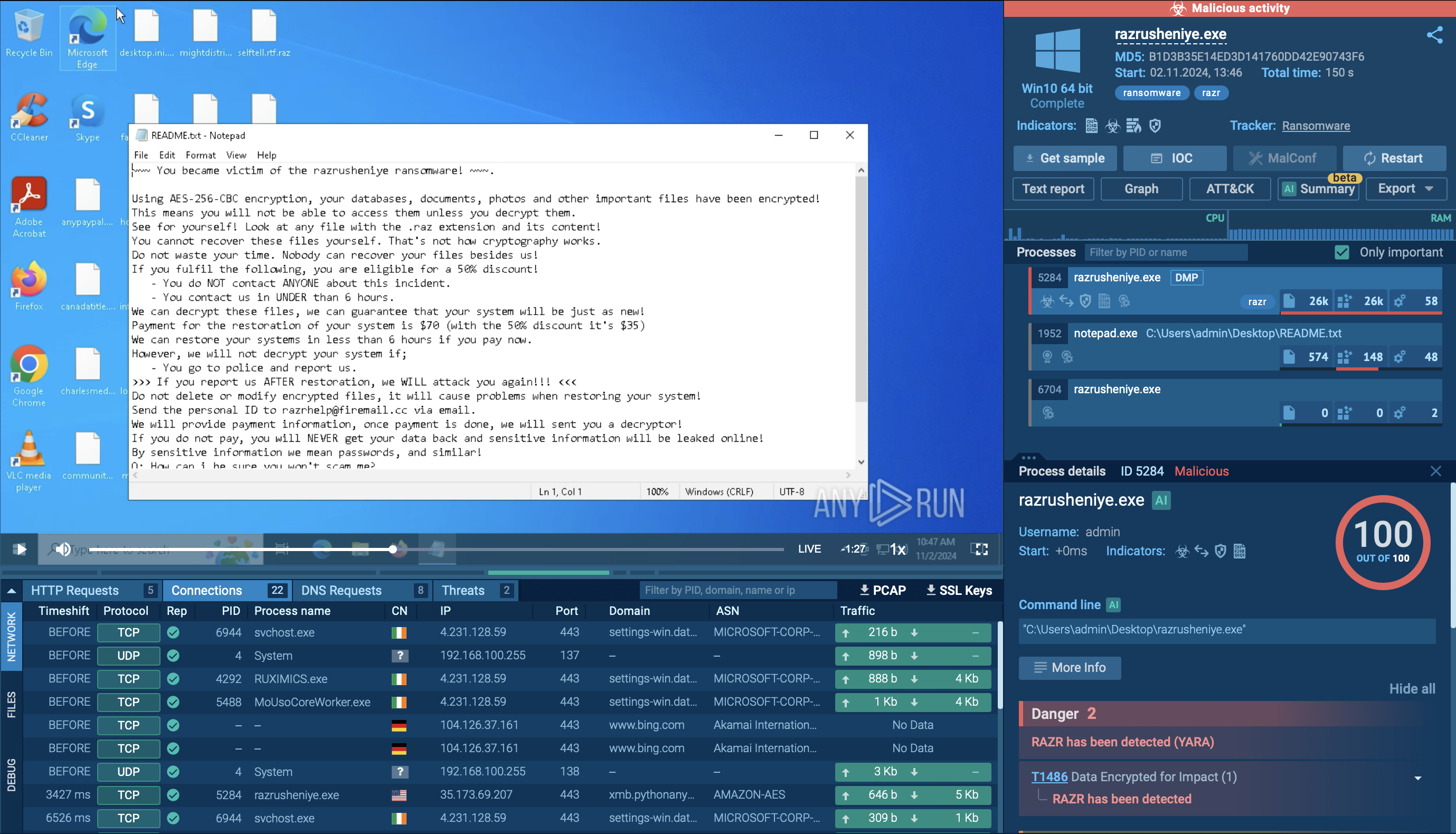
For instance, infections stemming from phishing emails and websites can be avoided, if a sandbox is first used to analyze them. The ANY.RUN malware sandbox lets you quickly determine whether a file or link poses a threat by uploading it to the service. ANY.RUN produces a detailed report featuring the verdict on the sample’s maliciousness and relevant indicators of compromise (IOCs) that can be used for detection.
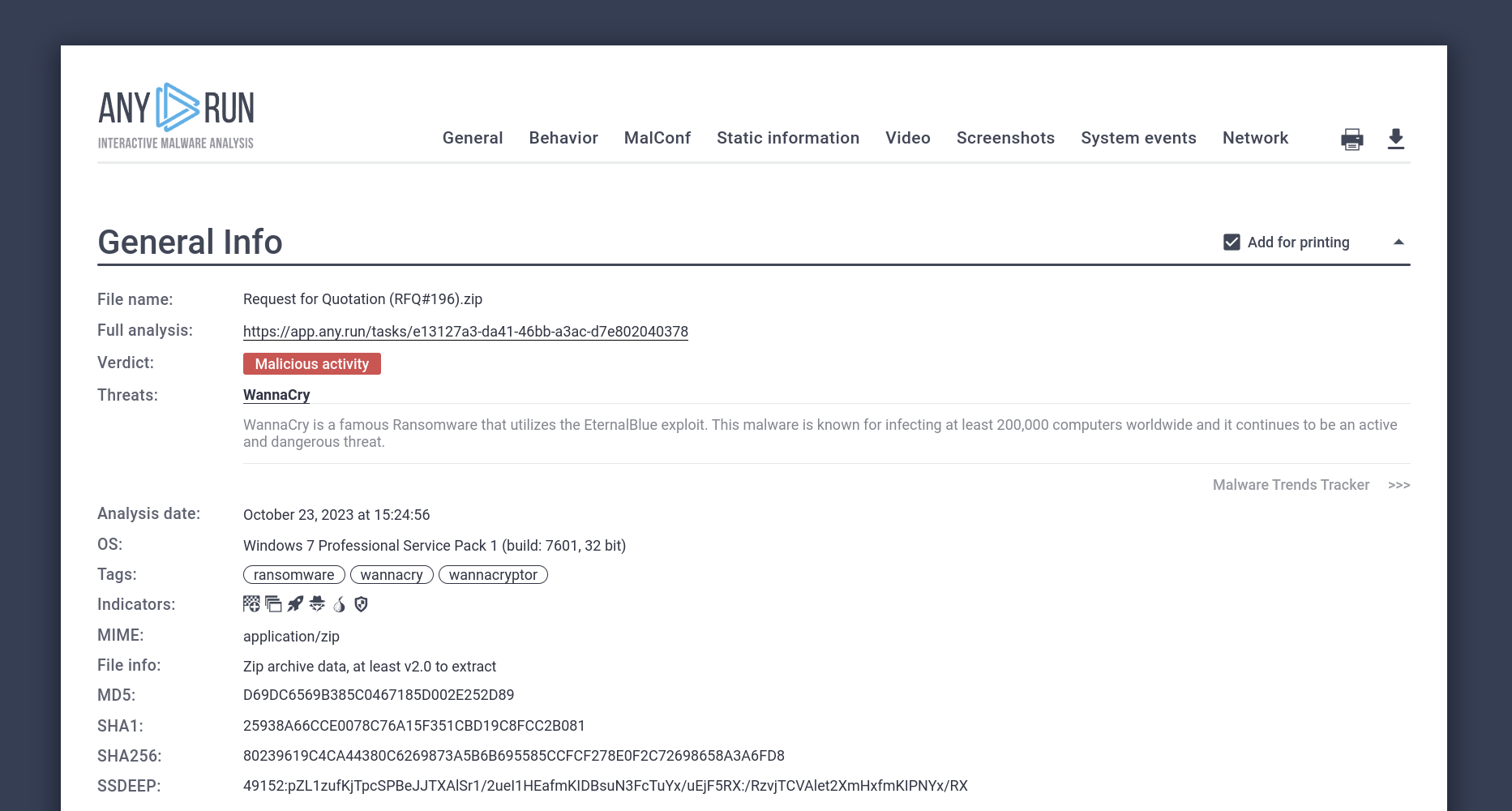 ANY.RUN report on a WannaCry sample
ANY.RUN report on a WannaCry sample
On top of that, the sandbox is fully interactive, meaning you can engage with malicious files and links in a safe cloud virtual machine like you would on a normal computer.
Try ANY.RUN for free – request a demo!