Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Cactus ransomware-as-a-service (RaaS) was first caught in March 2023 targeting corporate networks. It became known for its self-encrypting payload and double extortion tactics. Cactus primarily targets large enterprises across industries in finance, manufacturing, IT, and healthcare. It is known for using custom encryption techniques, remote access tools, and penetration testing frameworks to maximize damage.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
5 March, 2003
First seen
:
|
9 January, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
5 March, 2003
First seen
:
|
9 January, 2026
Last seen
:
|

 833
833
 0
0

 497
497
 0
0

 2767
2767
 0
0
A relatively new player in the cybercrime landscape, it’s a RaaS sold or leased by its developers to affiliates who carry out attacks. It uses both technical exploits and evasive maneuvers to compromise networks, encrypt data, and extort victims.
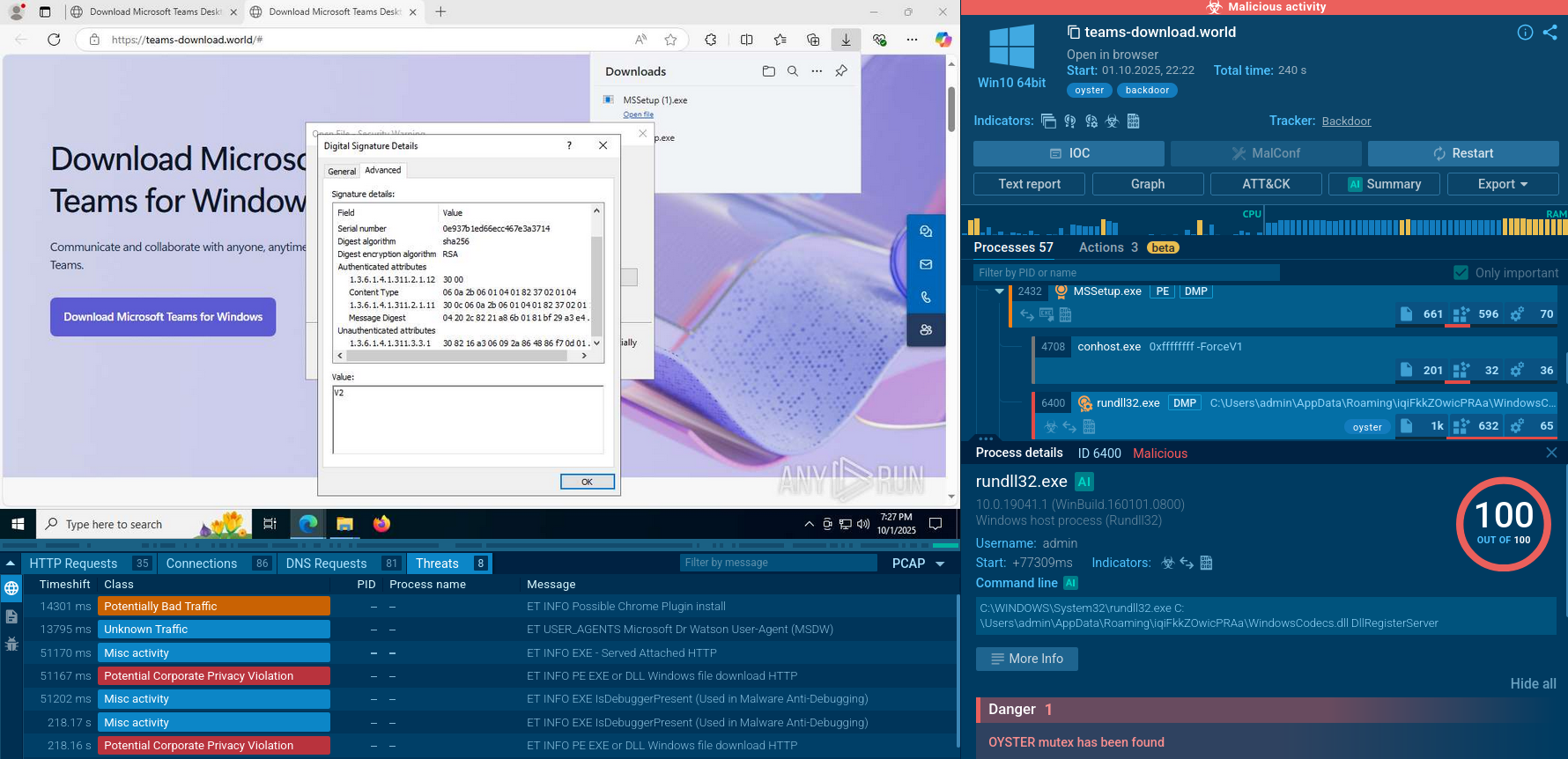
Cactus infiltrates networks by brute-forcing credentials and exploiting known vulnerabilities in VPN appliances and remote access solutions, such as Fortinet, Citrix, Qlik Sense. Threat actors also purchase stolen credentials or use brute-force attacks against Remote Desktop Protocol (RDP) services.
Phishing and malwertising campaigns may also be used to harvest employee login details. Once inside, attackers perform reconnaissance, escalate privileges, and move laterally, often targeting critical systems like domain controllers.
Cactus operates as a double-extortion ransomware, meaning it doesn’t just encrypt files—it also steals data and threatens to leak it. Some reports suggest it employs triple-extortion by targeting victims’ partners or clients with threats to increase pressure. The double- or triple-extortion model makes it especially harmful to organizations handling sensitive customer data, intellectual property, or proprietary information, as leaks can lead to regulatory fines and reputational damage.
The entire process can unfold rapidly—sometimes within 24 hours of initial access, especially if a vulnerability is freshly disclosed.
Cactus encrypts itself before execution, making detection more difficult. It uses AES-RSA encryption to lock files and appends a .cts or .cactus extension.
The malware drops a ransom note demanding payment through Tor-based negotiation sites.
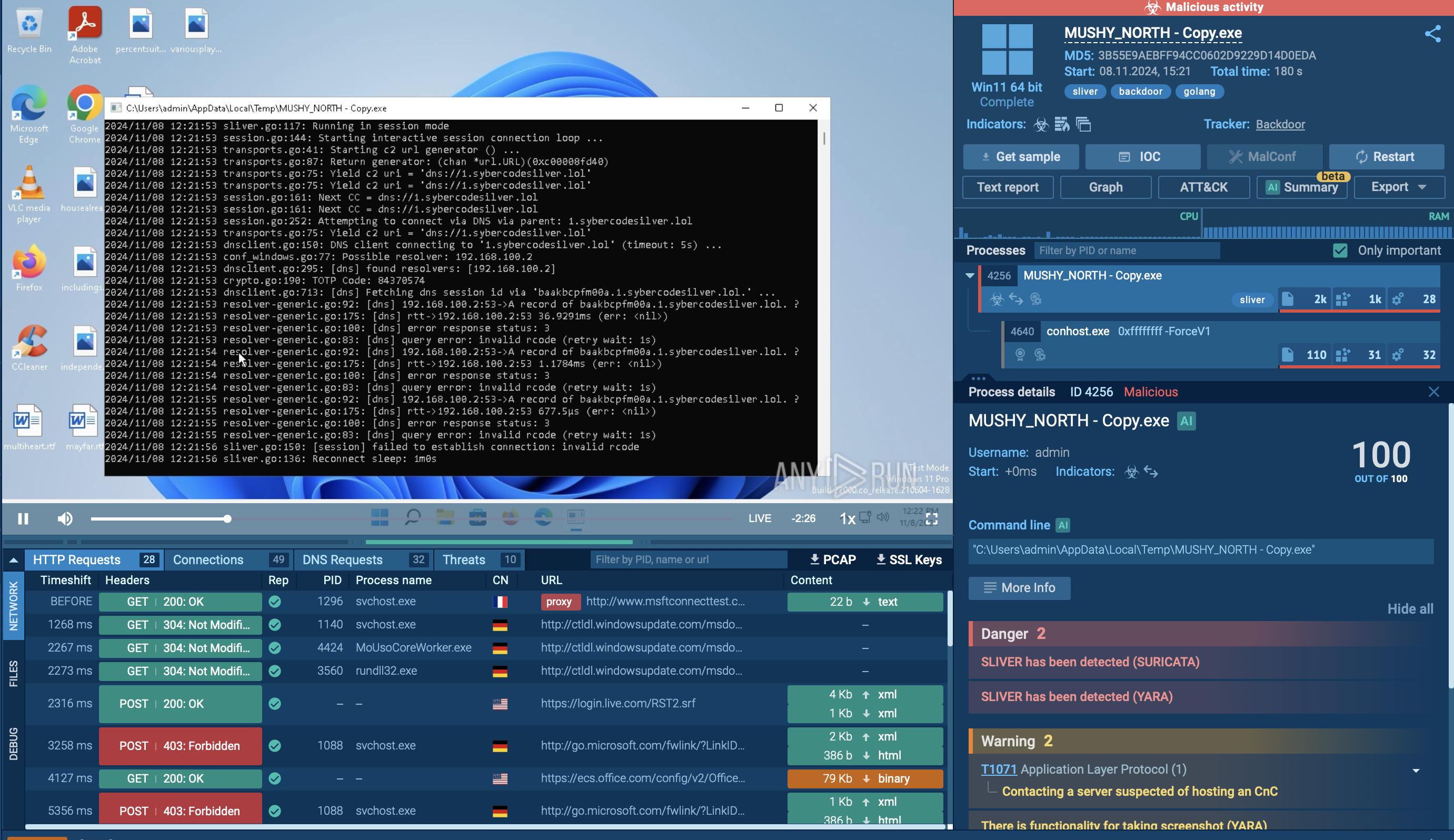
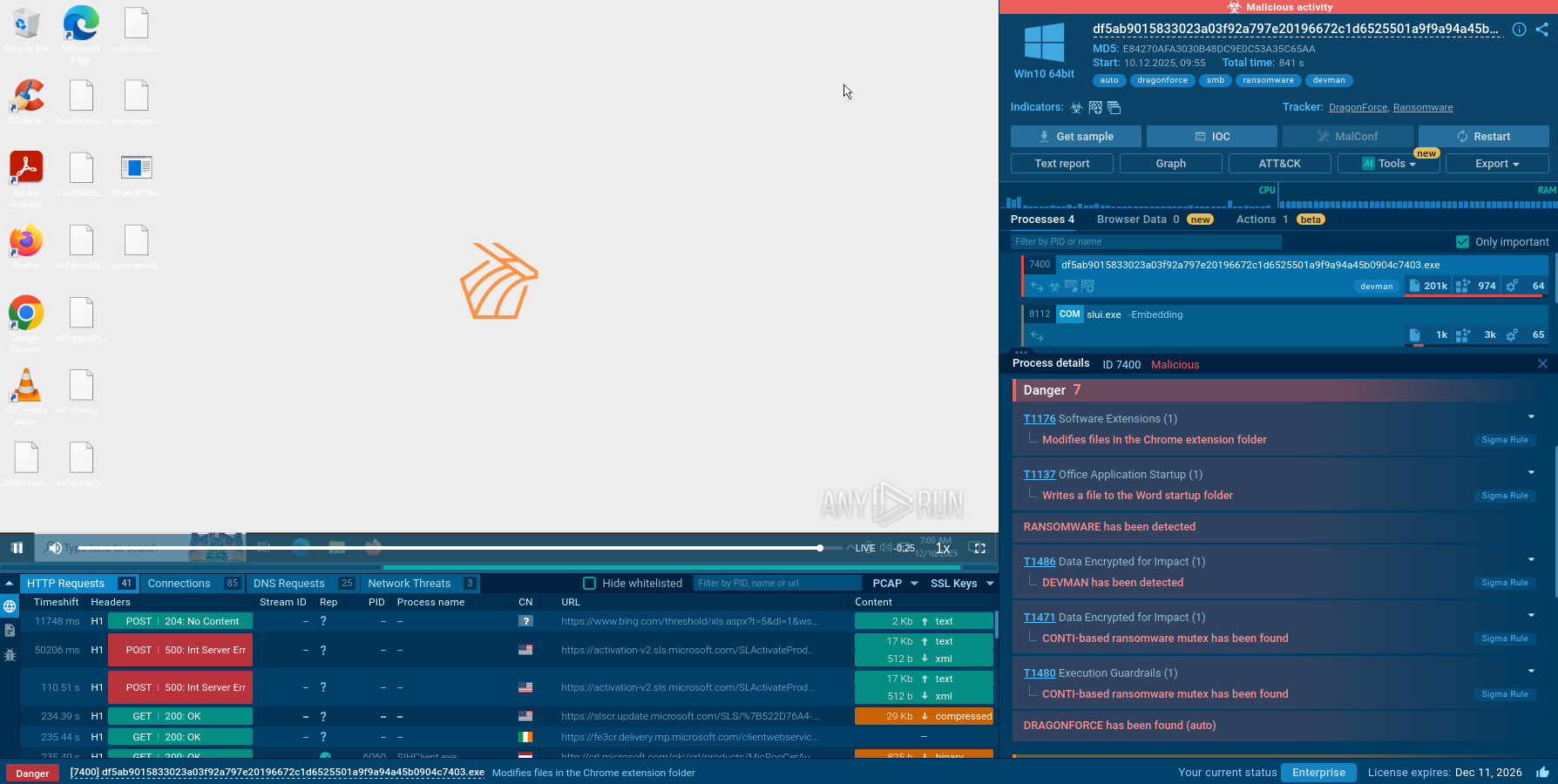
Among millions of malware analysis sessions conducted in the ANY.RUN sandbox, there is a number of Cactus fresh samples. Let’s see it in action in safe VM environment.
The core of Cactus ransomware's functionality lies in its payload execution. It employs a combination of AES-256 and RSA-4096 encryption algorithms to encrypt files on infected systems. The ransomware checks for specific command-line arguments upon execution; if certain flags are present, it alters its behavior accordingly. For example, if executed without specific flags, it begins encrypting files throughout the system while appending unique extensions to encrypted files.
During encryption, Cactus ransomware also deletes shadow copies and terminates essential services that could interfere with its operations. The ransomware scans all drives for files to encrypt, excluding certain file types like executables and system files to maintain operational integrity. Upon completion of the encryption process, a ransom note is dropped into each affected directory, demanding payment for file recovery.
Cactus Ransomware analysis inside ANY.RUN's Interactive Sandbox
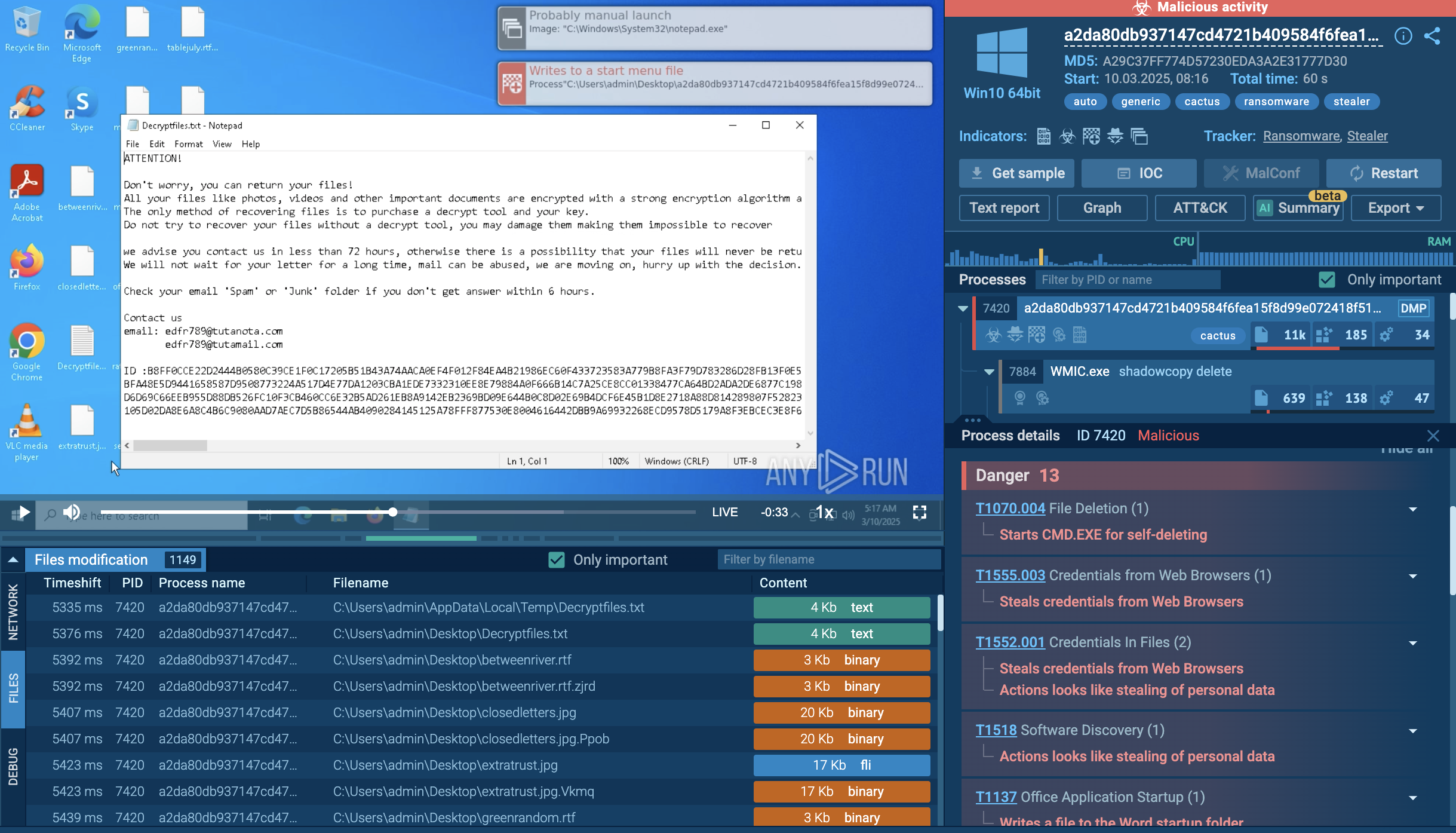
After encryption, Cactus deletes itself by execution CMD with command-line of deletion with delay.
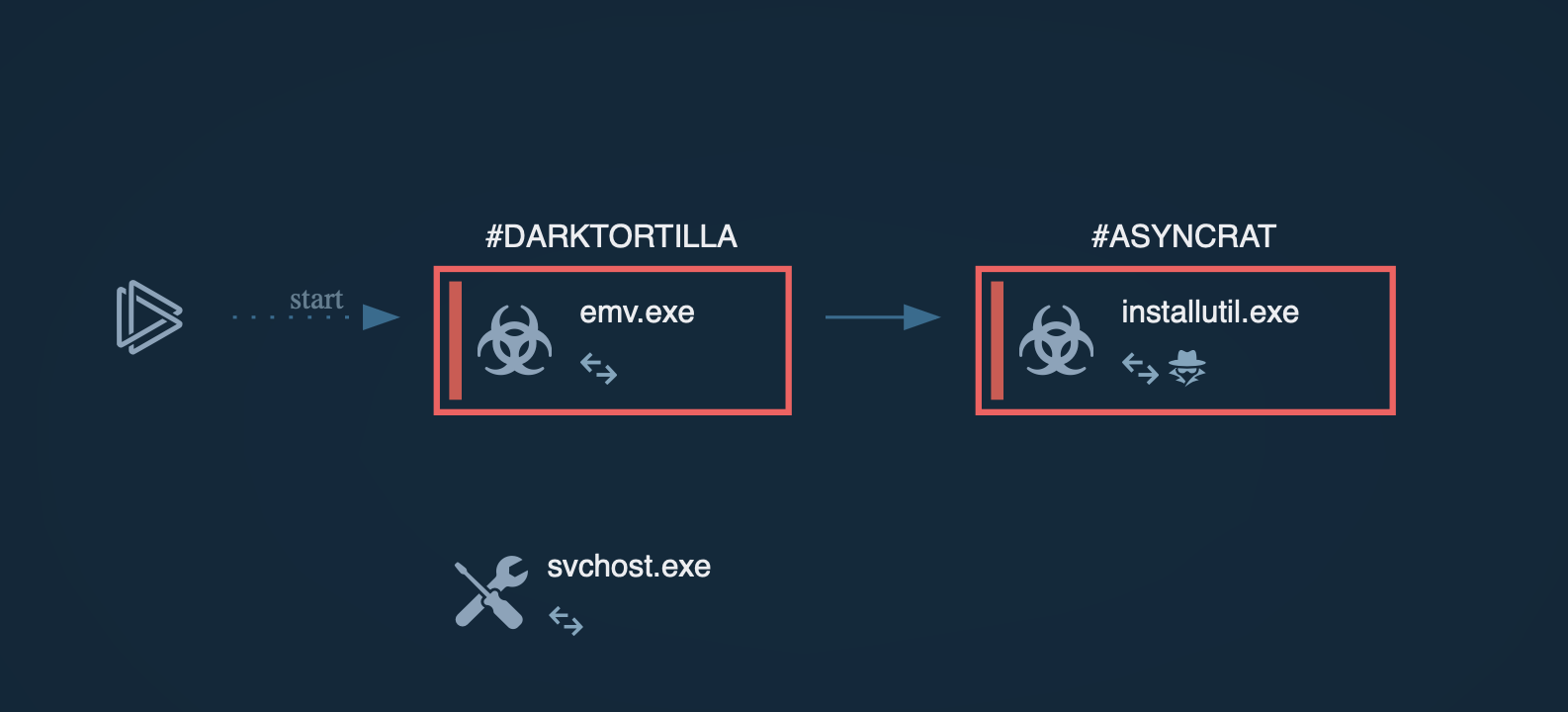
These incidents illustrate Cactus ransomware's strategic targeting of diverse industries, its sophisticated infiltration methods, and the substantial impact on affected organizations.
Threat intelligence is critical for staying ahead of Cactus, given its rapid evolution and use of fresh exploits. Leverage TI to hunt for IOCs specific to Cactus, like known C2 domains, IPs, or file hashes. Focus on TTPs (tactics, techniques, procedures) shared by TI reports, such as self-encryption or LotL behaviors, to build detection rules in SIEM systems.
Use ANY.RUN’s Threat Intelligence Lookup: start with searching by the ransomware name and dive into IOCs and TTPs research along with analysis sessions from the Sandbox.
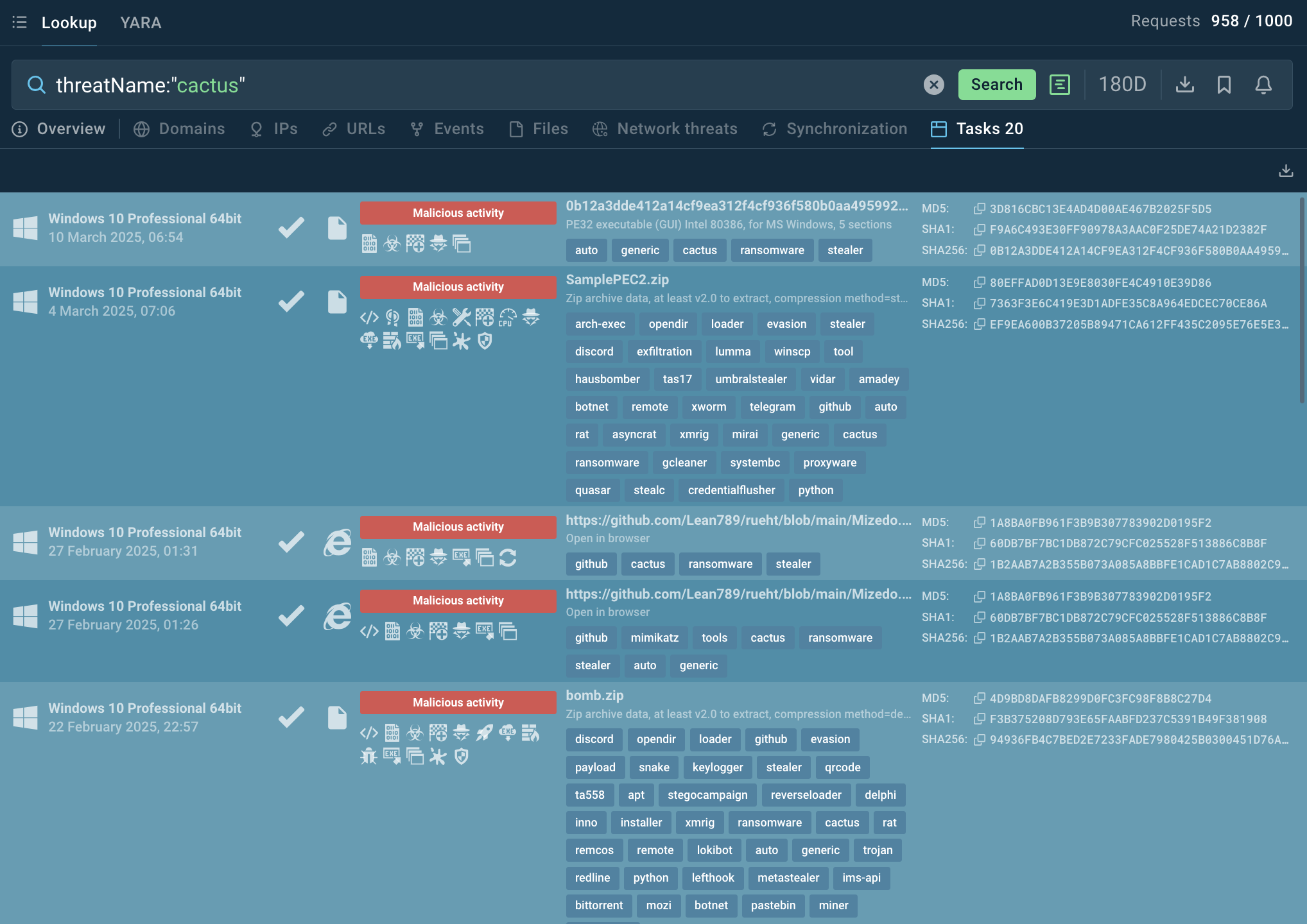
Cactus samples with basic IOCs
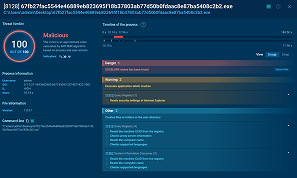
Study Cactus ransomware behavior: see how a malicious process unwraps
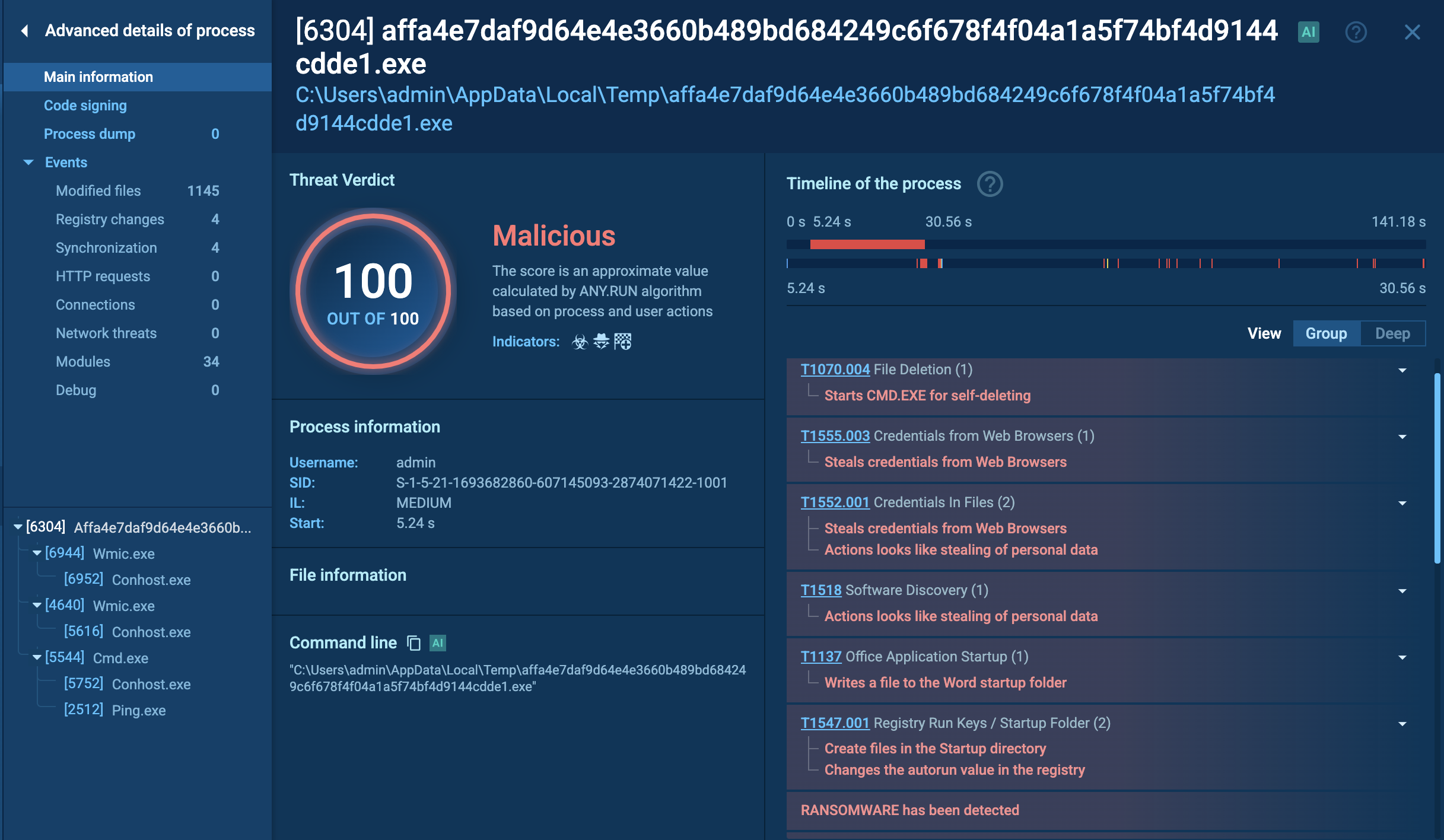
Details on Cactus actions in the system
Cactus ransomware is a highly sophisticated threat leveraging self-encrypting payloads, living-off-the-land techniques, and double extortion. Its targeted nature makes it a high-risk ransomware strain for enterprises.
By leveraging threat intelligence, proactive threat hunting, and strong security controls, organizations can detect and mitigate Cactus ransomware infections before they cause irreparable damage.
Start with 50 requests in TI Lookup to collect IOCs on Cactus and be ready to detect and respond