Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases
A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices.

 857
857
 0
0

 508
508
 0
0

 2788
2788
 0
0
A backdoor is a way of bypassing the standard authentication and security systems of a device or application in a stealthy manner. Backdoors can be intentionally created or unintentionally introduced.
Unintentional backdoors are usually the result of misconfigurations, coding errors, or design flaws. Intentional ones, on the other hand, can be implemented by developers of certain software or hardware for both legitimate and malicious purposes, including as a way to carry out maintenance and recovery.
In one instance of an intentional software backdoor, an attacker attempted to insert a backdoor into the code of XZ Utils, a set of tools for lossless data compression. The attacker had been actively contributing to the software's repository and eventually gained maintainer responsibilities, making it easier to introduce the malicious code. Learn more about it on ANY.RUN’s blog
Still, both types of backdoors can be exploited by threat actors for unauthorized access to an endpoint to conduct illicit activities such as data theft, system damage, or deployment of malicious payloads in the form of malware families.
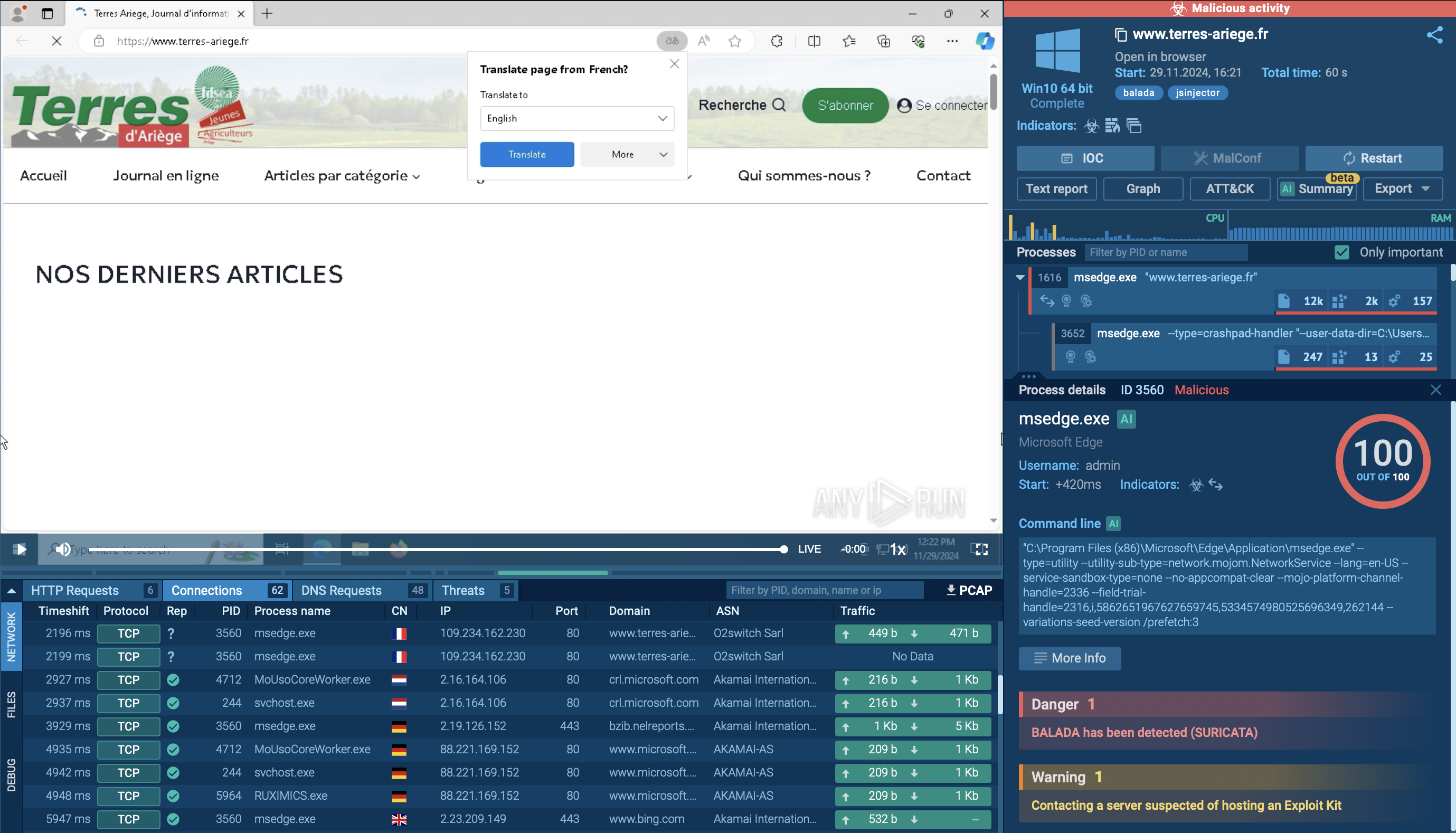
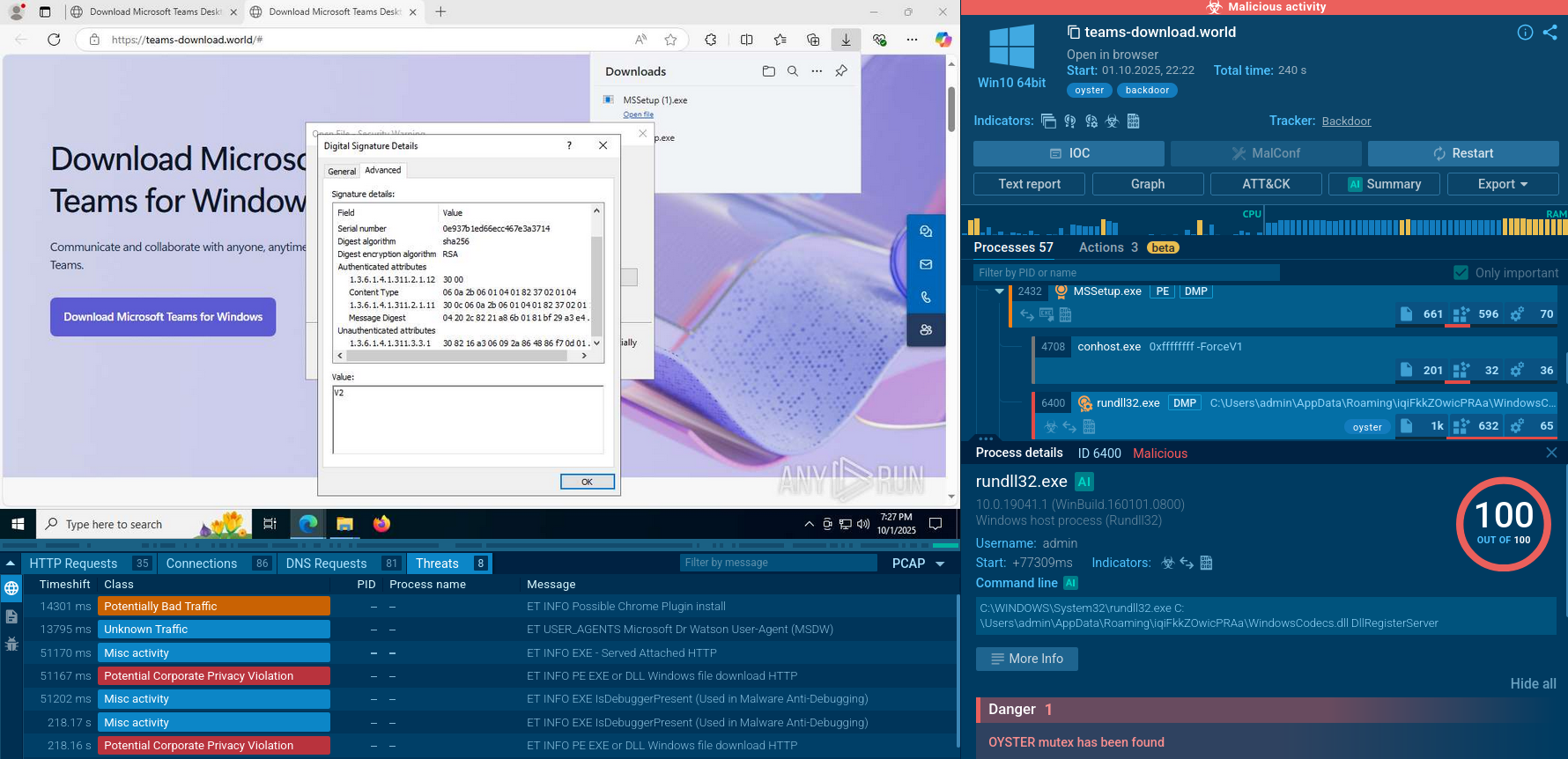
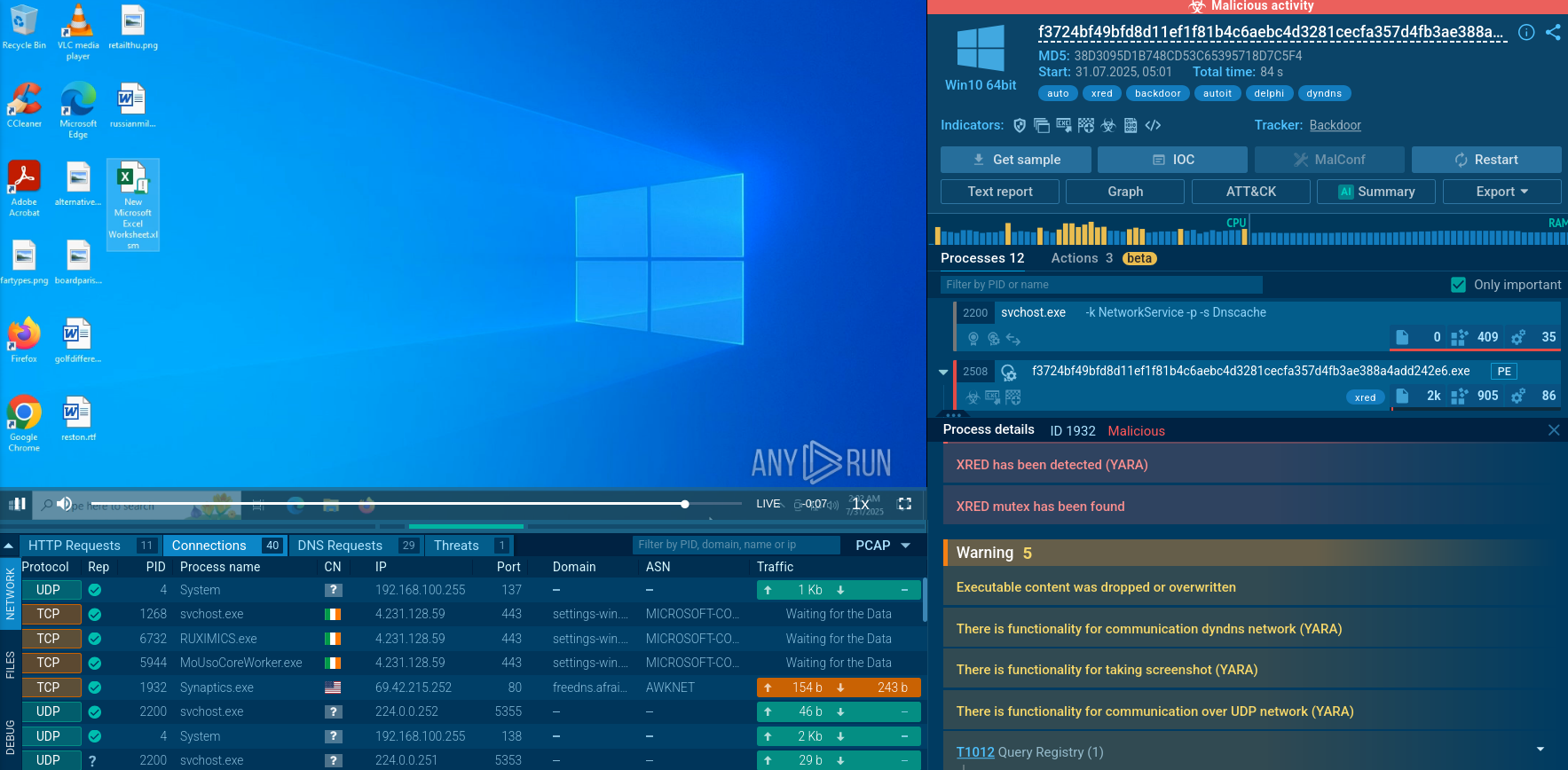
There is also backdoor malware, which is malicious software utilized by criminals with the intention to extract sensitive data while hiding its presence on the system. Trojans are the primary category of malware selected by criminals for such operations. One of the most complex backdoor forms is rootkit malware that gains access to the kernel level of the system, which makes it difficult to detect. As a result, the use of a backdoor may not trigger any security alerts, as the attacker is using a legitimate, albeit unauthorized, entry point.
A backdoor attack is a type of cybersecurity breach that involves the exploitation of a backdoor to access a system without authorization. Backdoor attacks based on malware can be carried out in various ways, including:
The impact of a backdoor on an endpoint device can be considerable and lead to significant consequences for the organization affected by it, both in terms of its reputational and financial damage.
Depending on their functionality, backdoors allow attackers to perform a variety of malicious activities, including:
One of the malware families belonging to the backdoor type is PlugX. It is a malicious software that has been in existence since 2008. For over a decade, it has been a go-to choice for many Chinese state-affiliated advanced persistent threats (APTs), such as Mustang Panda. These threat actors typically use PlugX as part of their espionage operations. As a result, some of the core features of the malware include keylogging, data exfiltration, and capabilities like side-loading that let it evade detection by security solutions.
MadMxShell is another example of a backdoor malware. It leverages DNS MX queries to establish communication with its command and control (C2) server. This malware is capable of executing a range of malicious activities, including gathering system data and running commands via Cmd.exe. Learn more about and a campaign using Google Ads to spread on ANY.RUN’s blog.
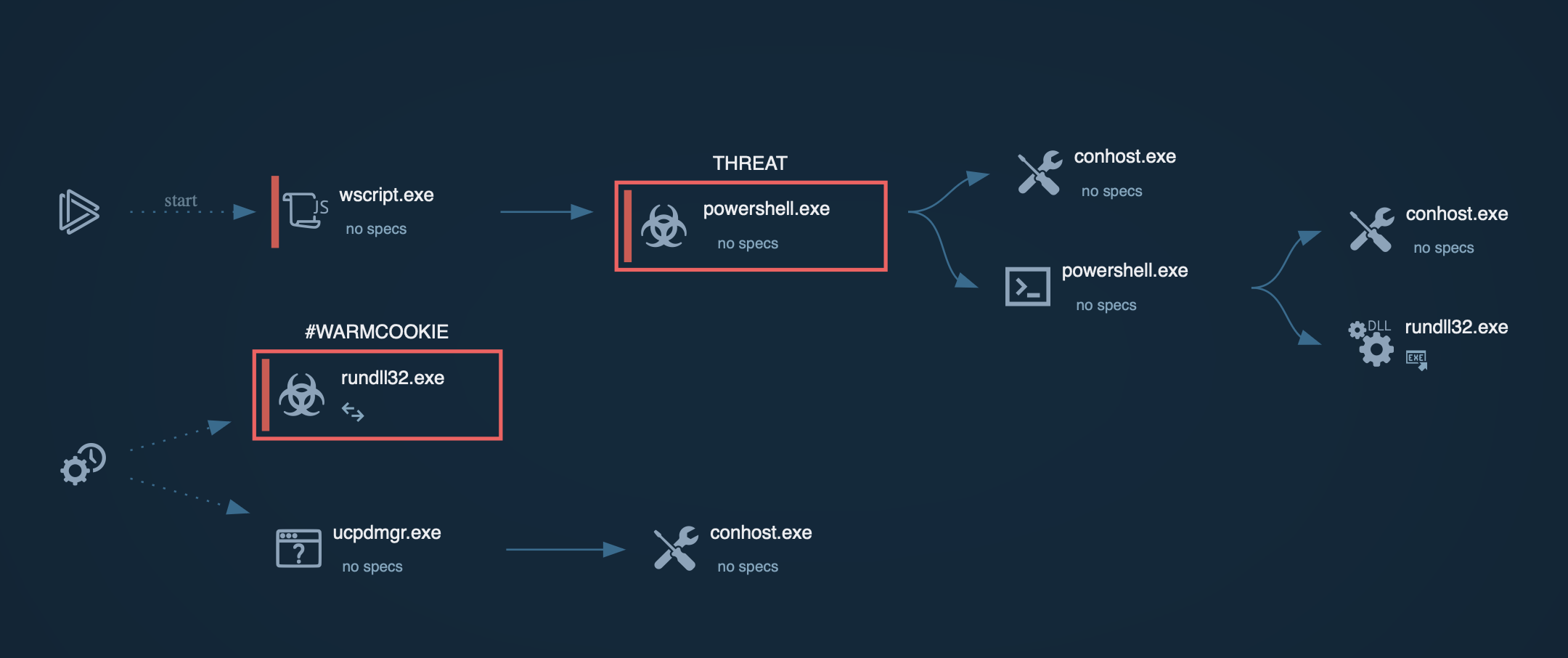
To observe a typical execution process of a backdoor malware, let’s upload a sample of PlugX into the ANY.RUN sandbox for in-depth analysis. View the analysis sessions by following this link
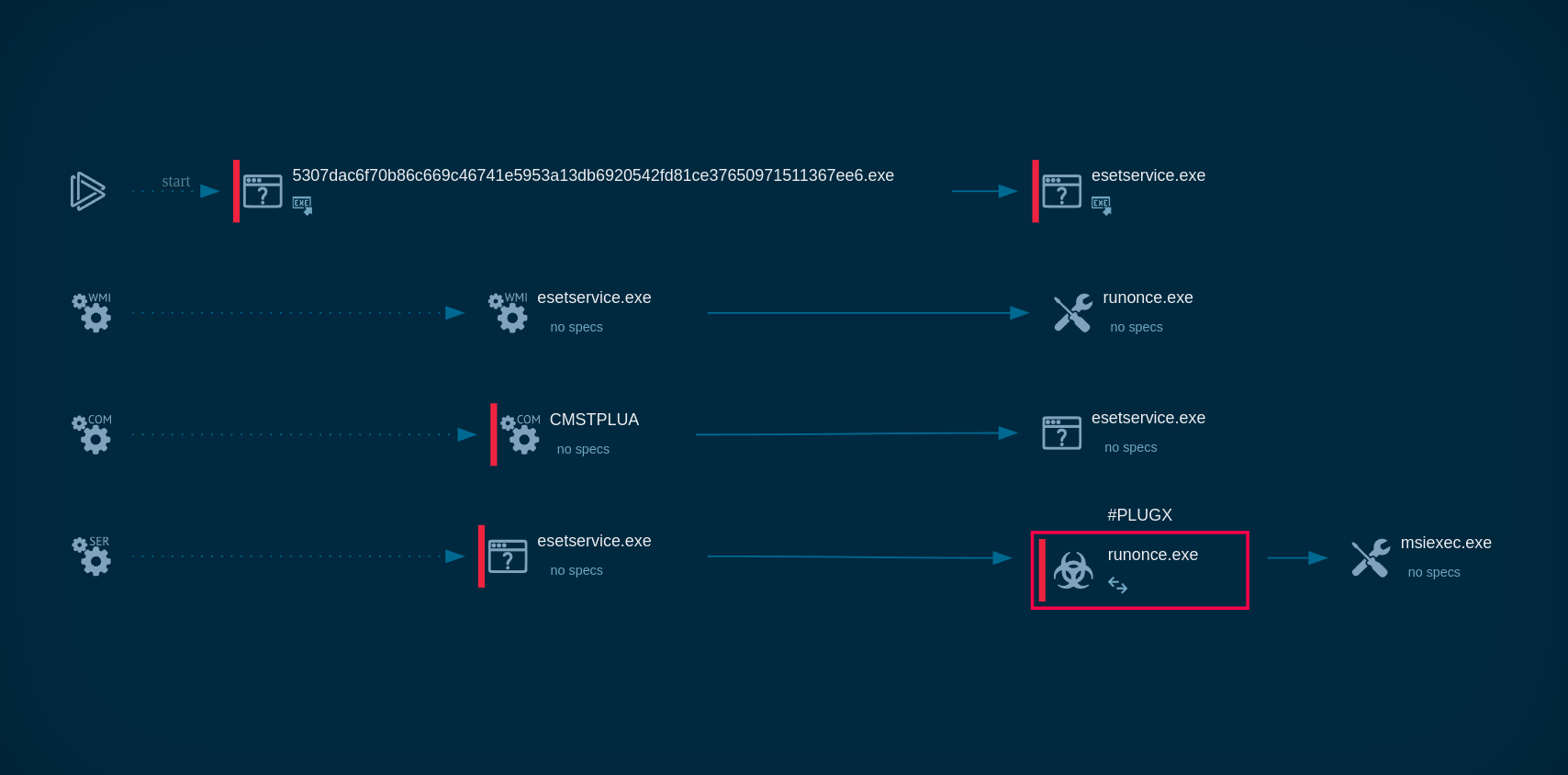 Process graph showing the execution chain of PlugX in ANY.RUN
Process graph showing the execution chain of PlugX in ANY.RUN
The sandbox lets us observe the steps taken by the malware to fully deploy itself on the systems:
The delivery method depends on each backdoor malware type. For instance, PlugX is equipped with worm capabilities, allowing it to spread through USBs that come into contact with the infected machine.
However, in many cases, to deliver backdoor malware, attackers use social engineering techniques, such as phishing emails or fake software updates, to trick users into installing or enabling a backdoor.
To minimize the risk of suffering from backdoor attacks, organizations should implement robust security practices and take a proactive approach to cybersecurity. This also includes analyzing malicious and suspicious files and links in a sandbox environment. Thus, you will be able to not only assess if a certain file or URL poses a threat to your infrastructure, but also expose the latest TTPs and collect fresh indicators of compromise (IOCs).
ANY.RUN is a cloud-based sandbox platform that enables users to quickly and thoroughly investigate malware and other types of threats. With the ability to detect backdoor and other types of malware in under 40 seconds, users can quickly determine the potential threat level of the sample they are dealing with.
The platform provides access to interactive Windows and Linux virtual machines, allowing users to analyze malicious behavior in a safe and isolated environment. The service supplies detailed threat reports that include IOCs and a comprehensive overview of malicious network and registry activities and processes. This information can be used to better understand and respond to potential threats, and to protect sensitive data and assets.