There’s a new Linux backdoor with a 10.0 CVSS score, and it shows that sometimes an attack can come from unexpected sources, especially if your environment heavily relies on open-source software. The recently discovered supply chain exploit affects XZ Utils, a popular open-source tool, and is currently tracked as CVE-2024-3094. It has received the highest CVSS score: 10.0.
What happened?
An attacker introduced malicious code into XZ Utils release versions 5.6.0 and 5.6.1. To achieve this, the actor became a contributor to the XZ project over the course of two years, slowly building credibility until they were given maintainer responsibilities. The actor, using the name Jia Tan, introduced the backdoor through a series of changes that made their way into XZ Utils release versions 5.6.0 and 5.6.1.
Jia Tan used social engineering and other accounts, now believed to be fake, under the names Jigar Kumar and Dennis Ens, to send feature requests and report various issues in the software. This forced the original maintainer, Lasse Collin of the Tukaani Project, to add a new co-maintainer to the repository. The attacker then introduced compressed test files that had been added to the code for setting up the backdoor via additions to the configure script in the tar files.
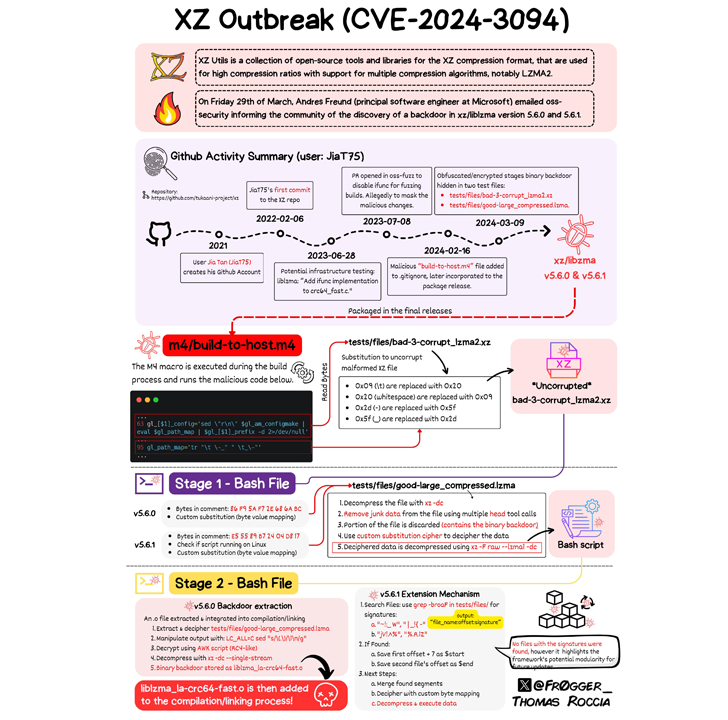
The backdoor allows remote attackers to send arbitrary payloads through an SSH certificate, which will be executed in a way that bypasses authentication protocols, effectively granting control of the victim machine. Any machine with the vulnerable package that exposes SSH to the internet is potentially at risk.
What is XZ Utils?
XZ Utils is an open-source data compression utility, similar to gzip and bzip2, that is present in major Linux distributions. Developed by The Tukaani Project, it is used to compress and decompress the xz and lzma file formats. The utility is used in popular Linux distributions, including Fedora, Slackware, Ubuntu, and Debian.
Are state-sponsored adversaries involved?
The cybersecurity community largely agrees that this supply chain attack is notable for the extreme lengths the attacker went to in order to sneak in the malicious code, spending over two years on this project.
The attacker first established themselves as a legitimate maintainer, offering to help with various OSS projects and committing code across multiple projects to avoid detection.
Some experts believe that the complexity of the attack suggests it may be a state-sponsored operation, as the level of effort involved doesn’t align with a one-shot operation.
How can you secure your infrastructure against these types of vulnerabilities?
The key is for businesses to use tools and implement processes to monitoring and detect malicious activity. It’s nearly impossible, and arguably undesirable, to rely less on open-source or community-run tooling, which inherently comes with this type of risk.
In this case, the exploit was discovered largely by accident by Andres Freund, a Microsoft engineer and PostgreSQL developer. Freund was performing micro-benchmarking when he noticed sshd processes exhibiting suspicious behavior.
Using ANY.RUN to analyze Linux vulnerabilities
ANY.RUN is an interactive cloud malware sandbox that can be used to analyze files, programs, and websites for vulnerabilities. With ANY.RUN, you can run virtual machines on Ubuntu, allowing you to analyze potential threats as if they were running on a real system. The platform’s behavioral signatures enable malicious activity detection even when dealing with undefined threats.
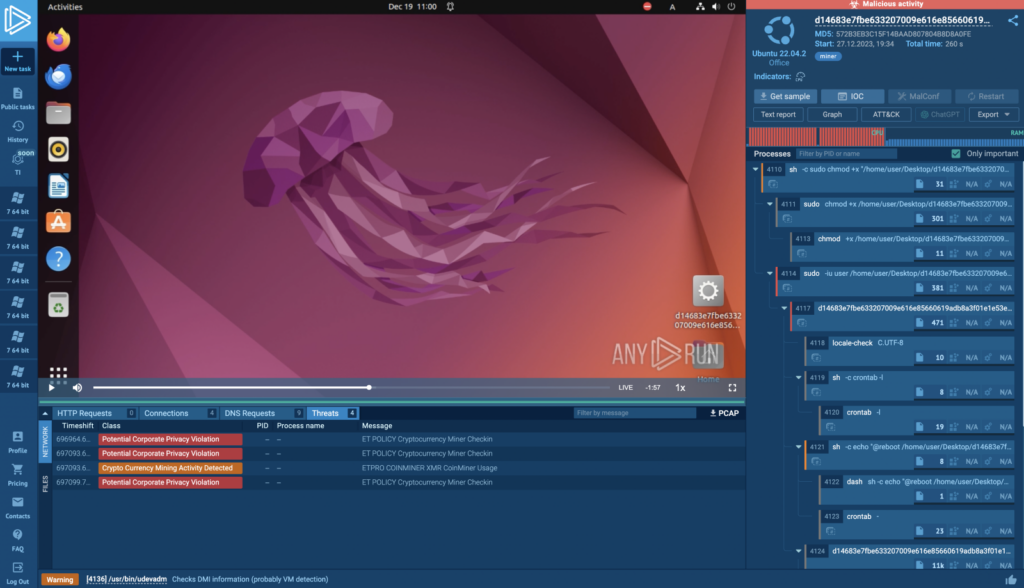
Read this article to see how we used ANY.RUN to analyze 3 Linux malware samples, or this one, where we showed how to detect and write detection rules for MonikerLink bug, also known as CVE-2024-21413.
About ANY.RUN
ANY.RUN’s flagship product is an interactive malware sandbox that helps security teams efficiently analyze malware.
Every day, a community of 400,000 analysts and 3000 corporate clients use our cloud-based platform to analyze Windows and Linux threats.
Key advantages of ANY.RUN for businesses:
- Interactive analysis: Analysts can “play with the sample” in a VM to learn more about its behavior.
- Fast and easy configuration. Launch VMs with different configurations in a matter of seconds.
- Fast detection: Detects malware within roughly 40 seconds of uploading a file.
- Cloud-based solution eliminates setup and maintenance costs.
- Intuitive interface: Enables even junior SOC analysts to conduct malware analysis.
Learn how ANY.RUN can benefit you or your security team. Schedule a free demo with one of our sales representatives, and we’ll walk you through real-world examples.












0 comments