A new malicious advertising campaign on Google Ads is exploiting a group of up to 45 domains that impersonate an IP scanner to distribute a new backdoor called MadMxShell.
What is MadMxShell?
MadMxShell is a sophisticated Windows backdoor that uses DNS MX queries to communicate with its C2 server, located at litterbolo[.]com. The malware can:
- Collect system data.
- Run commands via Cmd.exe.
- Read, write, and delete files on the infected host.
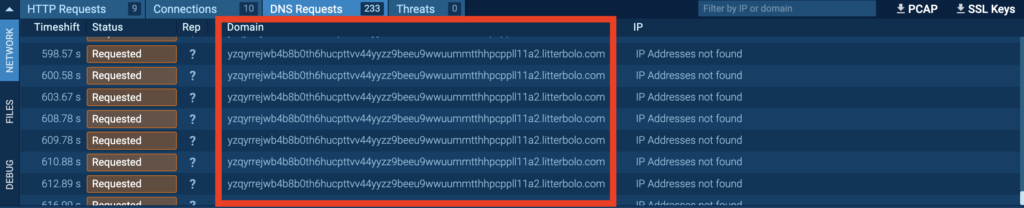
Notably, it communicates with the C2 server by encoding data in the subdomains of DNS MX query packets and receives commands encoded within the response packets, hence the name MadMxShell.
Why is this significant?
This is the first time a campaign has used Google Ads to spread a sophisticated Windows backdoor — a technique known as malvertising.
Malvertising involves using Google Ads to push malicious domains to the top of search engine results for specific keywords, tricking victims into visiting them.
In this case, between November 2023 and March 2024, attackers registered a group of over 45 domains that mimic legitimate software such as Advanced IP Scanner, Angry IP Scanner, PRTG IP Scanner, and ManageEngine Advanced IP Scanner.
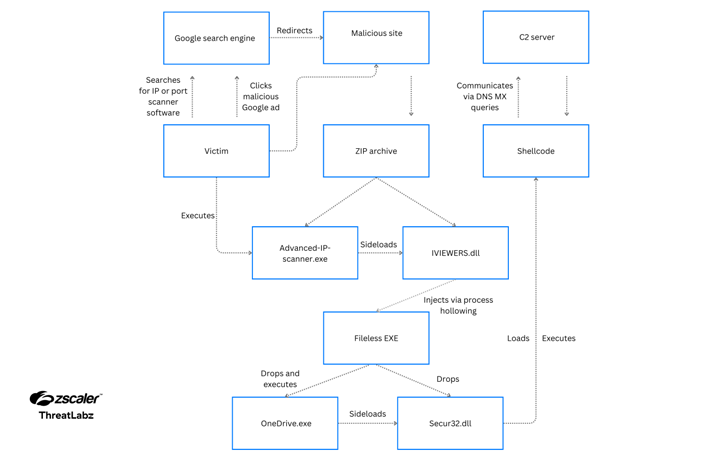
How does the infection chain work?
The infection process begins when a user searching for popular IP scanning tools clicks on a malicious Google Ad and is directed to one of the 45 typosquatted domains registered by the attackers.
Upon clicking the download button on these fake sites, a malicious ZIP archive named “Advanced-ip-scanner.zip” is downloaded. As we can see in this recording of an interactive analysis session in ANY.RUN sandbox, this archive contains two files: a DLL file named IVIEWERS.dll and an executable named Advanced-ip-scanner.exe:
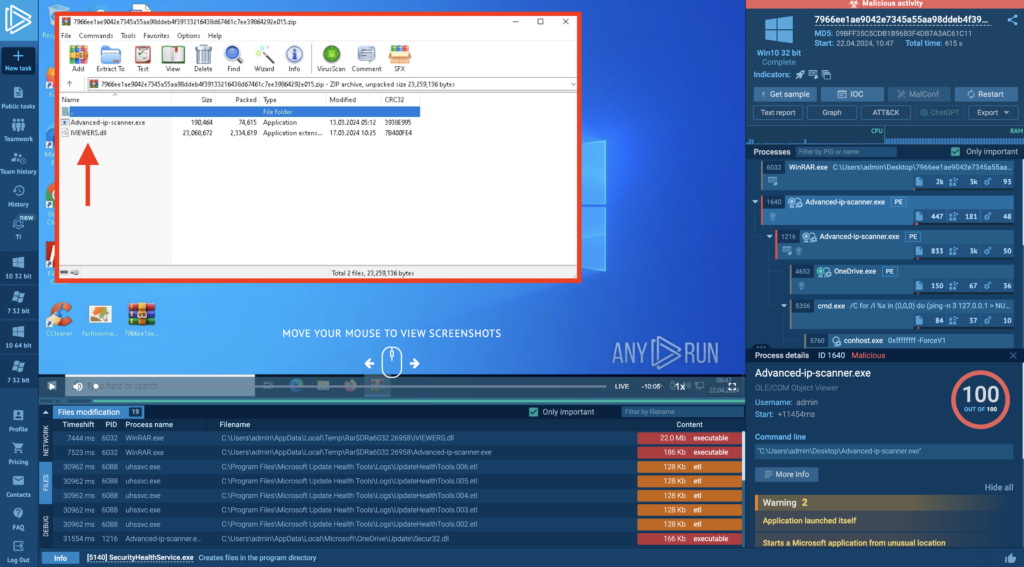
When the user runs the Advanced-ip-scanner.exe, it uses DLL side-loading to load the malicious IVIEWERS.dll file and initiate the infection sequence.
The DLL file then injects embedded shellcode into the Advanced-ip-scanner.exe process using process hollowing. The DLL effectively replaces the memory of a legitimate process with malicious code, allowing the malware to masquerade as a benign process.
After the injection, the compromised Advanced-ip-scanner.exe process unpacks two additional files:
- OneDrive.exe.
- Secur32.dll.
OneDrive.exe is a legitimate Microsoft binary that has been digitally signed. The malware abuses this trusted binary to sideload the malicious Secur32.dll file, which sets a scheduled task for persistence and executes the shellcode backdoor.
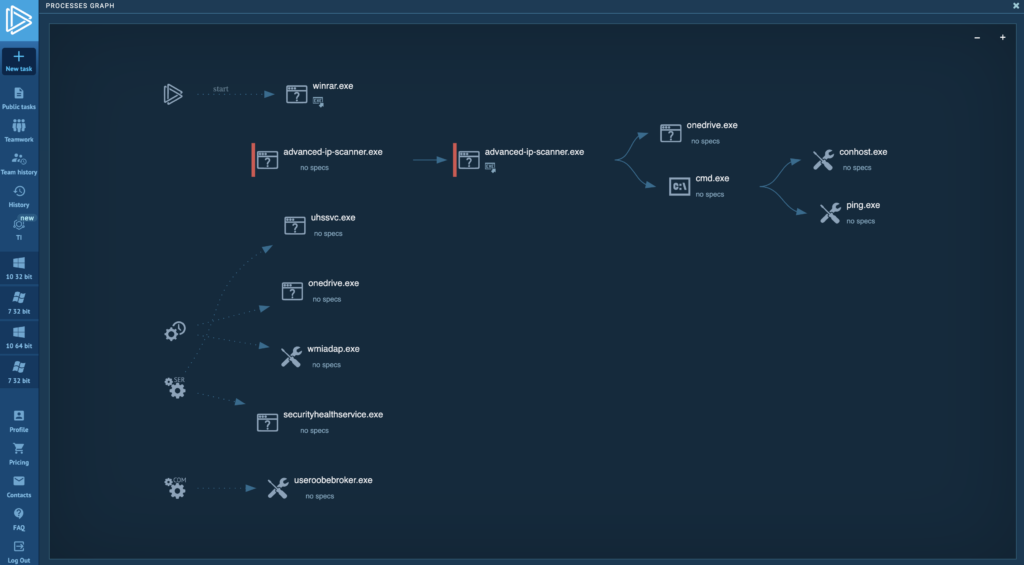
MadMxShell uses a variety of evasion techniques to complicate analysis. In addition to DNS tunneling for its C2 communication and multi-stage DLL loading, running a sample in ANY.RUN reveals more tricks. The Cmd.exe process with ID 5356 runs a ping command to delay simulation—likely an attempt to evade automatic sandboxes that have a limited time window for analyzing samples.
About ANY.RUN
ANY.RUN is a trusted partner for more than 400,000 cybersecurity professionals around the world. Our interactive sandbox simplifies malware analysis of threats targeting both Windows and Linux systems, providing analysts with an advanced tool for investigations. Our threat intelligence products, Lookup and Feeds, offer refined indicators of compromise and context that lets users detect threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s: ANY.RUN detects malware within about 40 seconds of a file upload. It identifies prevalent malware families using YARA and Suricata rules and uses behavioral signatures to detect malicious actions when you encounter a new threat.
- Interact with samples in real time: ANY.RUN is an interactive cloud sandbox powered by VNC, which means that you can do everything you could on a real system: browse webpages, click through installers, open password-protected archives.
- Save time and money on sandbox setup and maintenance: ANY.RUN’s cloud-based nature eliminates the need for setup or maintenance by your DevOps team, making it a cost-effective solution for businesses.
- Record and study all aspects of malware behavior: ANY.RUN provides a detailed analysis of malware behavior, including network traffic, system calls, and file system changes.
- Collaborate with your team: easily share analysis results, or, as a senior team member, check work of junior analysts by viewing recordings of their analysis sessions.
- Scale as you need: as a cloud service, you can easily scale your team, simply by adding more licenses.
Get in touch with us and we’ll provide you with a guided tour of ANY.RUN and show you how it can help your security team.








0 comments