Trusted by 15,000 industry leaders
Strengthening businesses from finance to healthcare
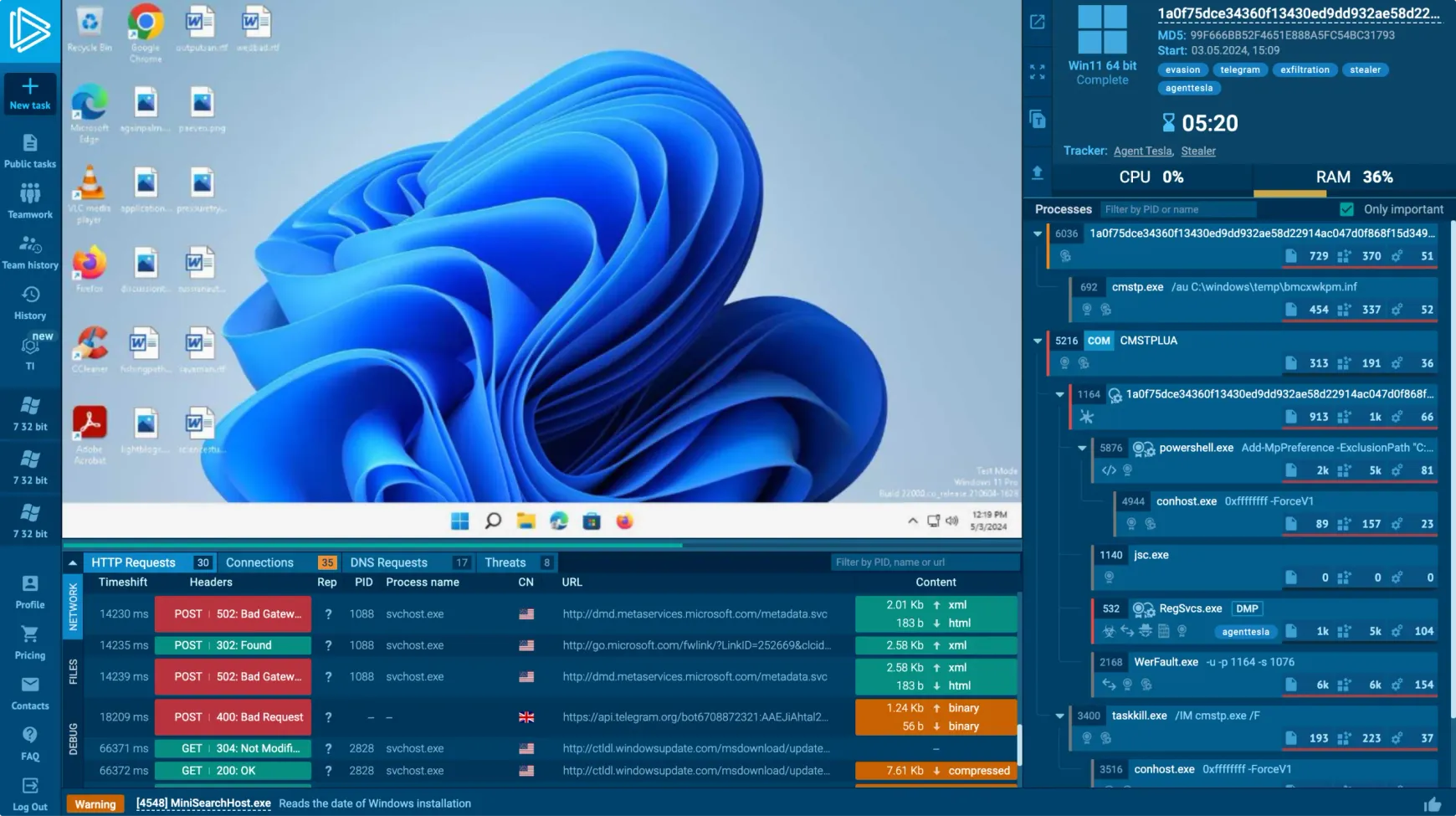
Interactivity in safe environment
Interact with the VM in your browser. Click on files, open archives or browse websites.
Fast access to knowledge
Our VMs start in under 10s. And it takes just 40s until the report.
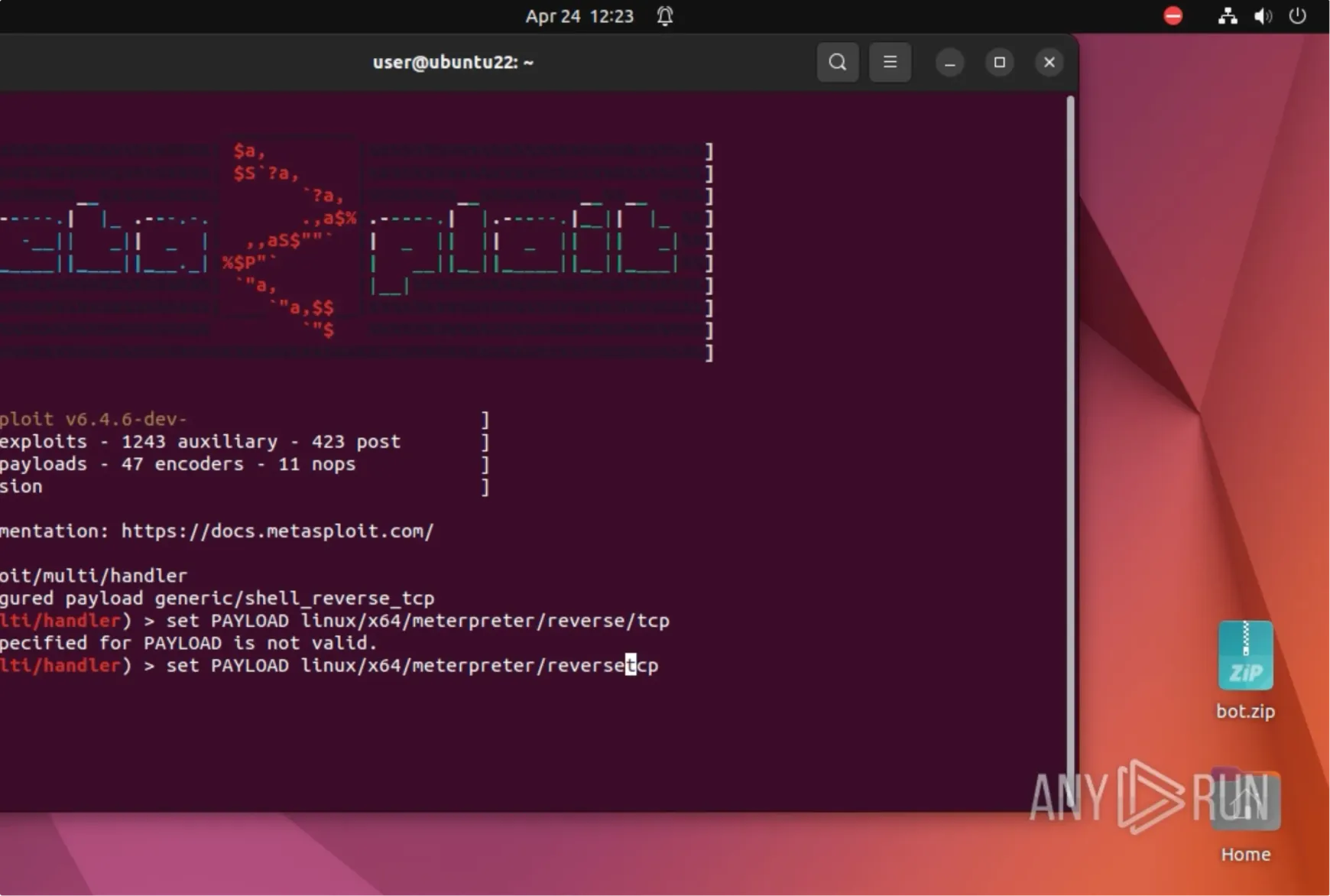
Windows, Linux, Android Support
Analyze in Windows (7, 10, 11), Linux (Ubuntu, Debian ARM), and Android 14 VMs.
Multiple report formats
View MITRE ATT&CK TTPs, IOCs, process graphs, and customizable text reports.
Observe and interact
with the VM in real time
Detonate and engage with cyber threats in a live system to see how they operate and respond to user actions.
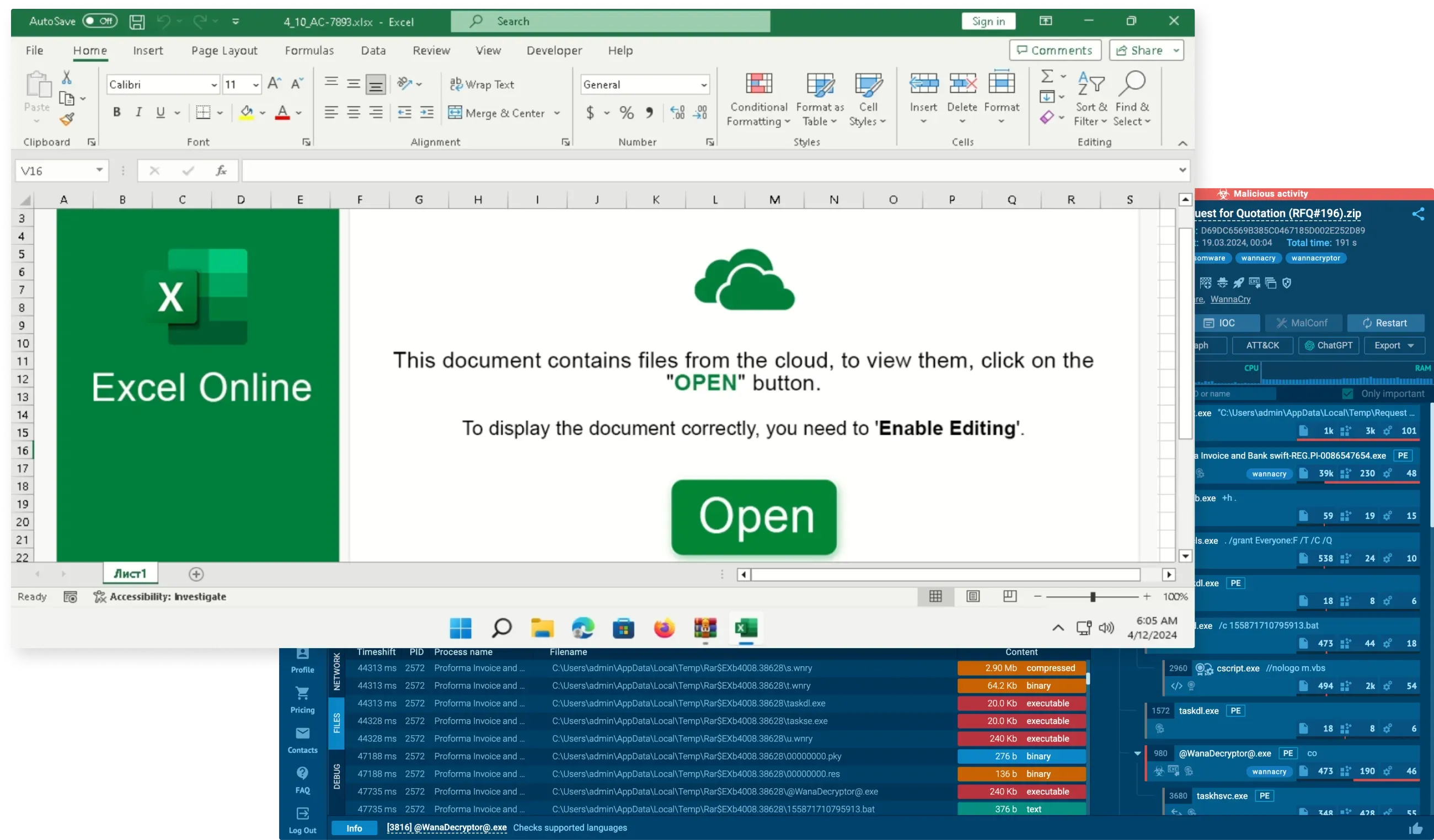
Benefits of cloud interactivity
Easy to use, even for beginners, lowering the learning curve and streamlining onboarding.
Quickly delivers IOCs during live analysis sessions, saving time when it's critical.
Cuts costs and boosts security across the organization by reducing dependency on hardware malware labs.
Understand everything the malware is doing
What our clients say
ANY.RUN scales with the largest cybersecurity teams
SOC collaboration and visibility
Work more effectively as a team by sharing results, coordinating incidents, monitoring work quality, and improving SOC information transfer for faster investigations.
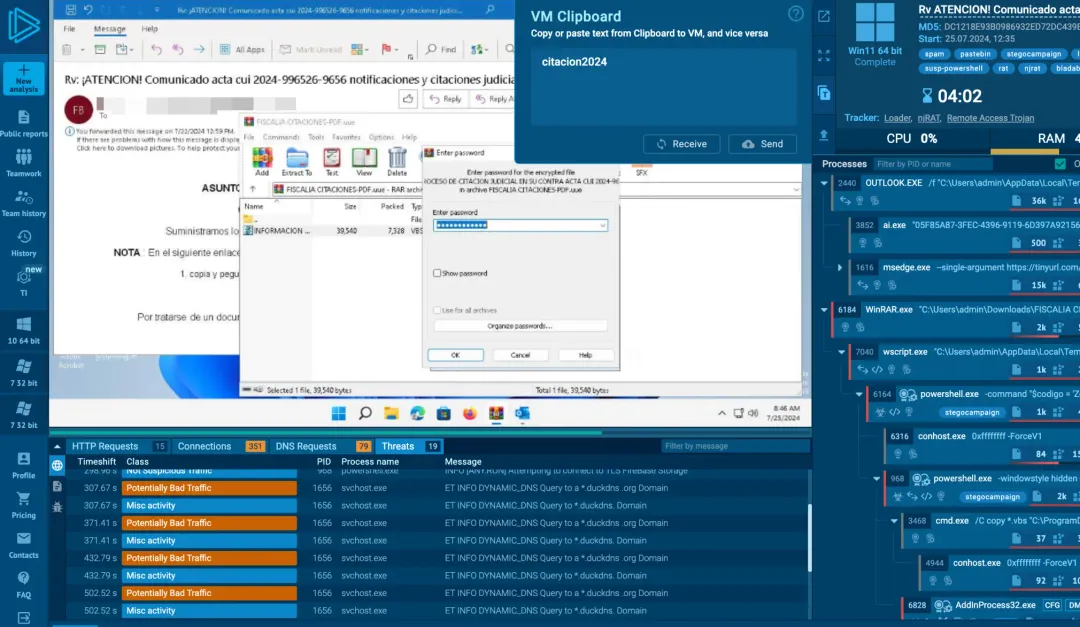
Seamless integration
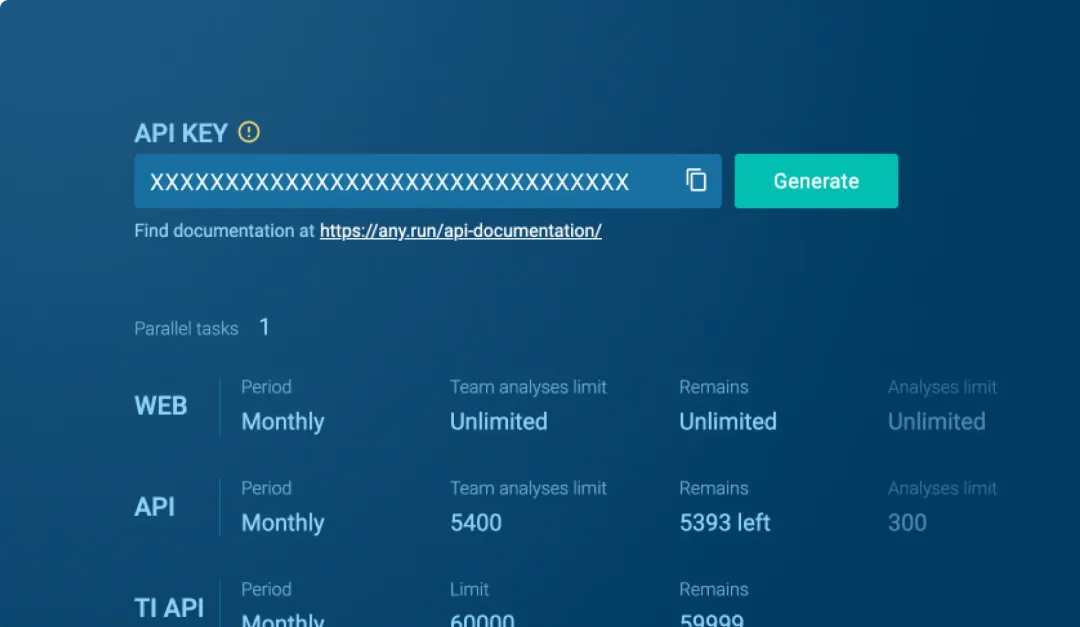
Access data via API, SDK, and STIX/MISP. Integrate with SIEM, TIP, and XDR to detect anomalies in real time and enhance response quality with fresh, relevant data.
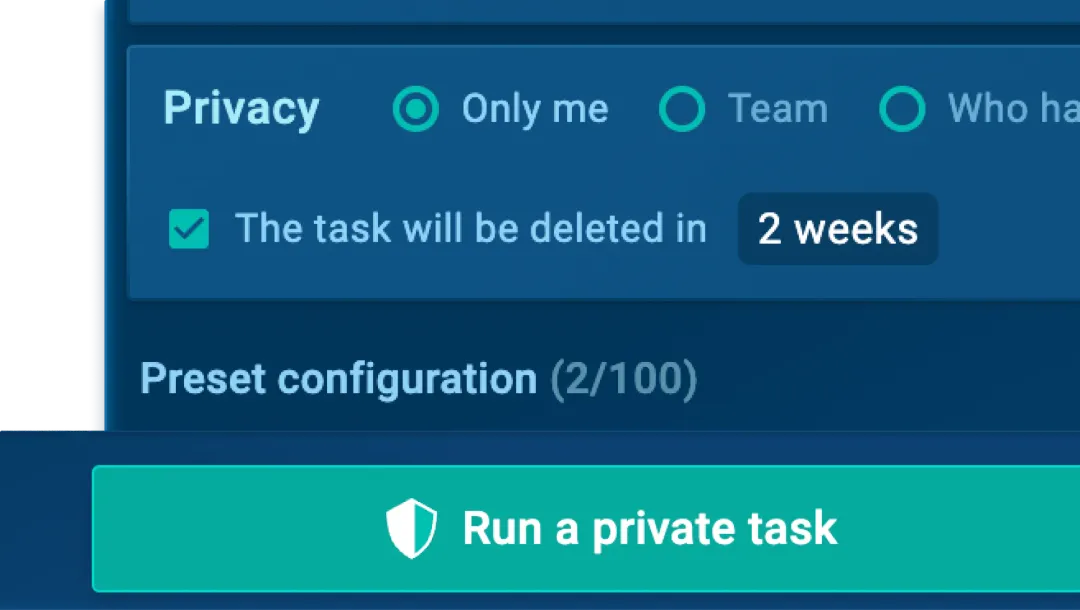
Privacy controls
Set session visibility per seat, control access with SSO, manage analysis history, and ensure data security with compliance to AICPA Trust Services Criteria.
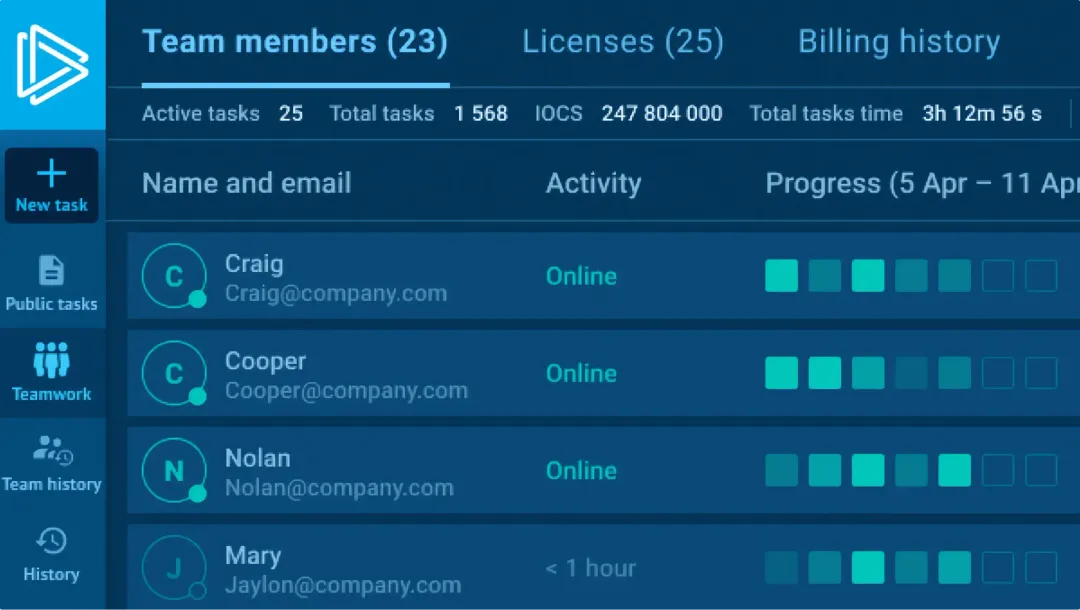
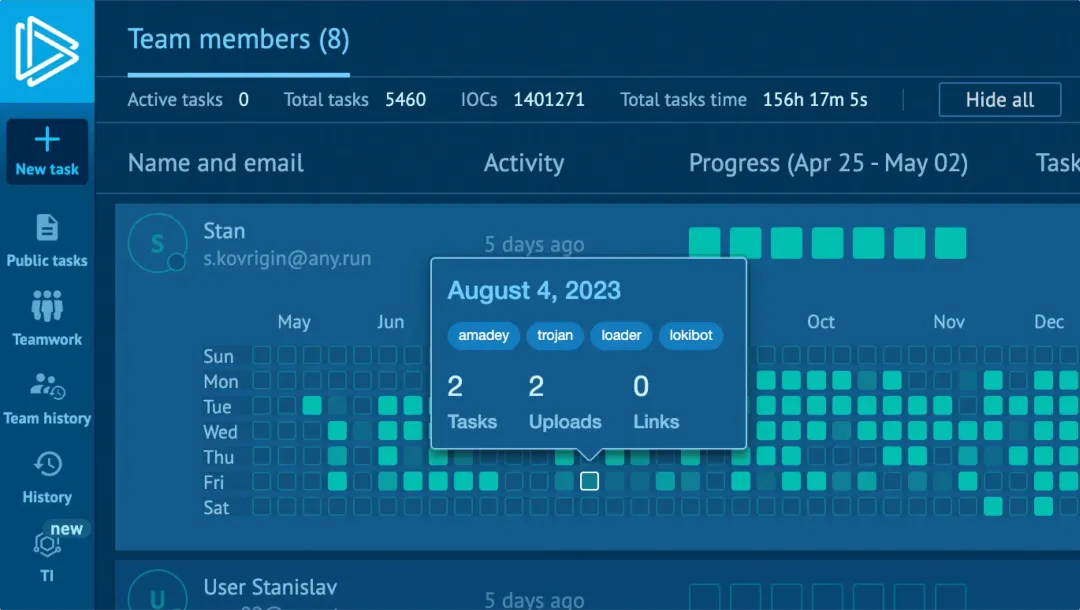
Workspace analytics
The bigger your team, the harder it is to stay aligned. See who works on what with filters by date, analysis session, and more.
Create and manage team resources
Create shared presets for VM configurations, manage openVPN settings, and use a team API quota.
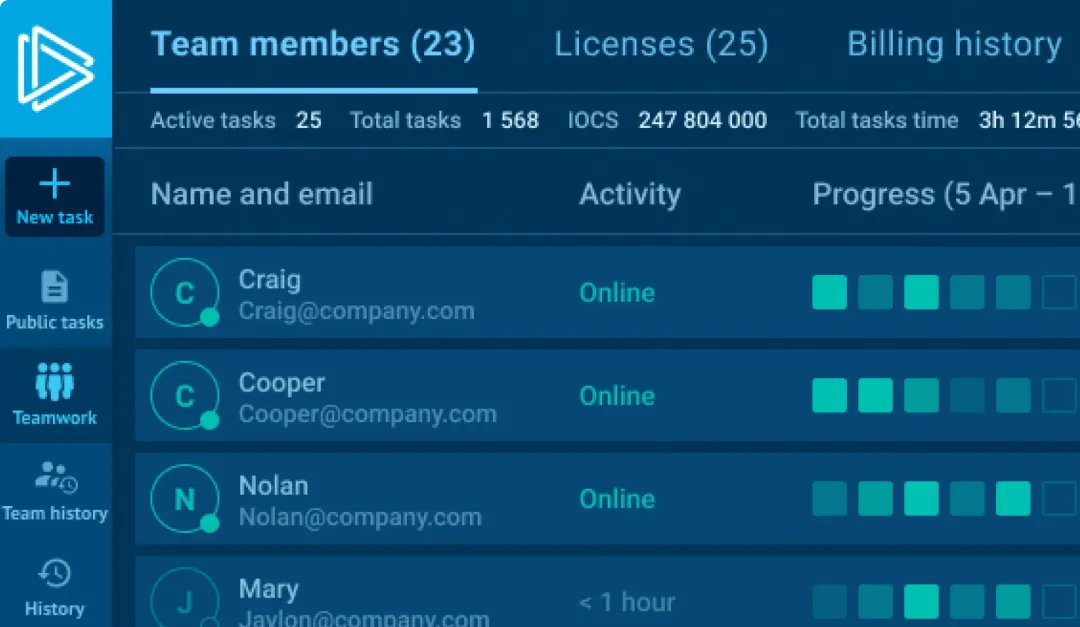
Track analysis completion
Designed for team leads: easily stay aligned and track workload with transparent workspace analytics.
Integrate ANY.RUN in your company
Equip your SOC with advanced threat analysis capabilities to:
- Boost detection rate
- Cut MTTD & MTTR
- Reduce alert fatigue
- Grow team expertise