Improve your incident response and forensic capabilities
Automate initial triage and access contextual data to quickly identify alerts for investigation or escalation to incident response teams.
Benefits of ANY.RUN
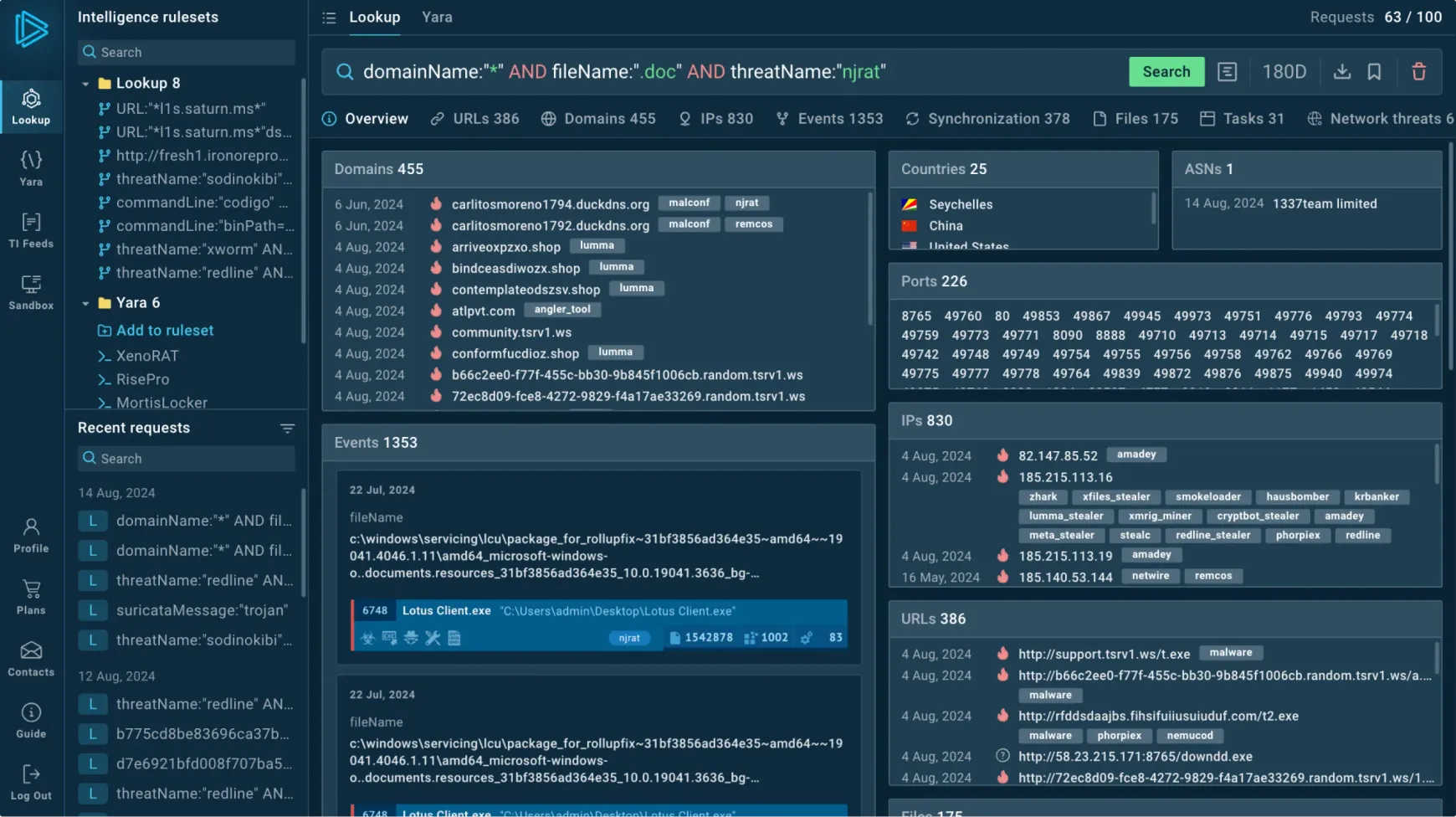
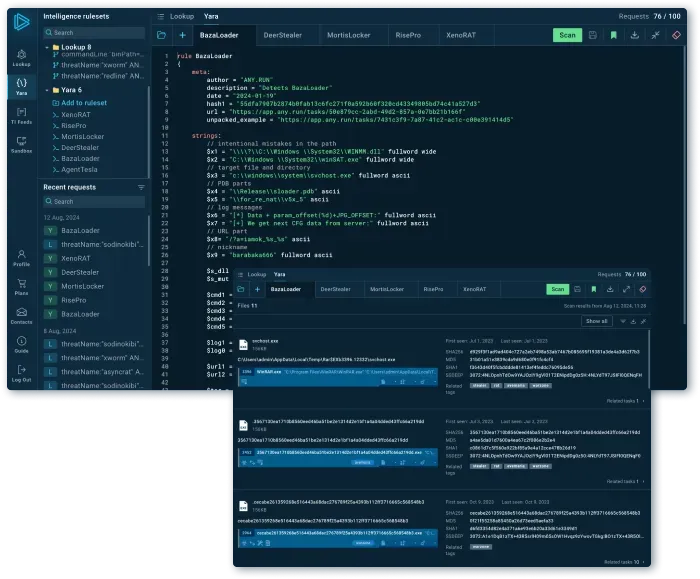
Threat Intelligence Lookup
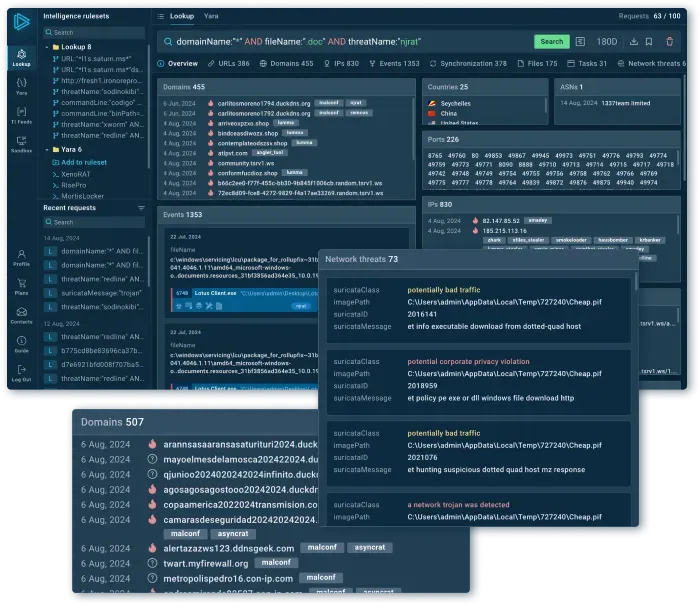
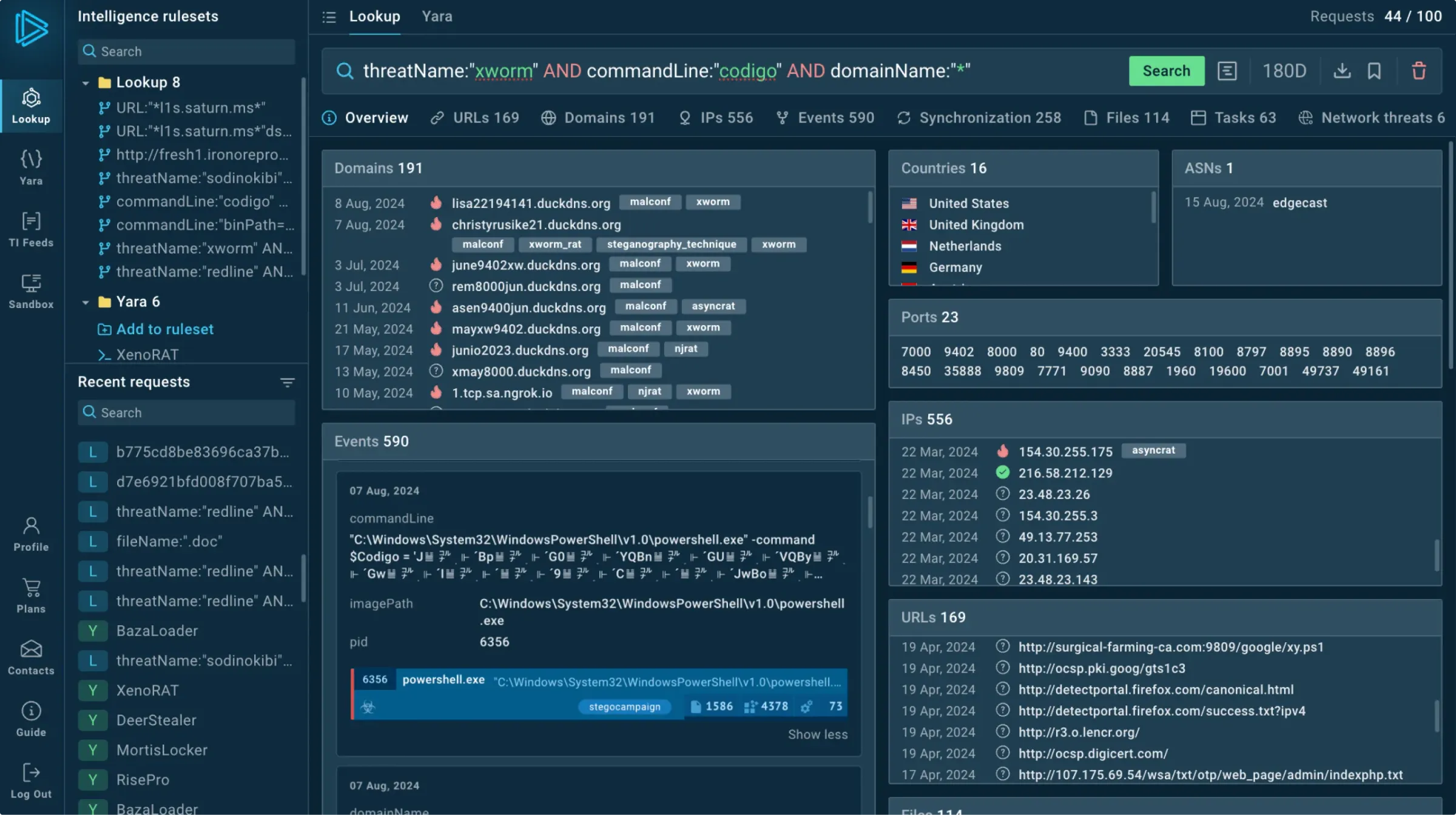
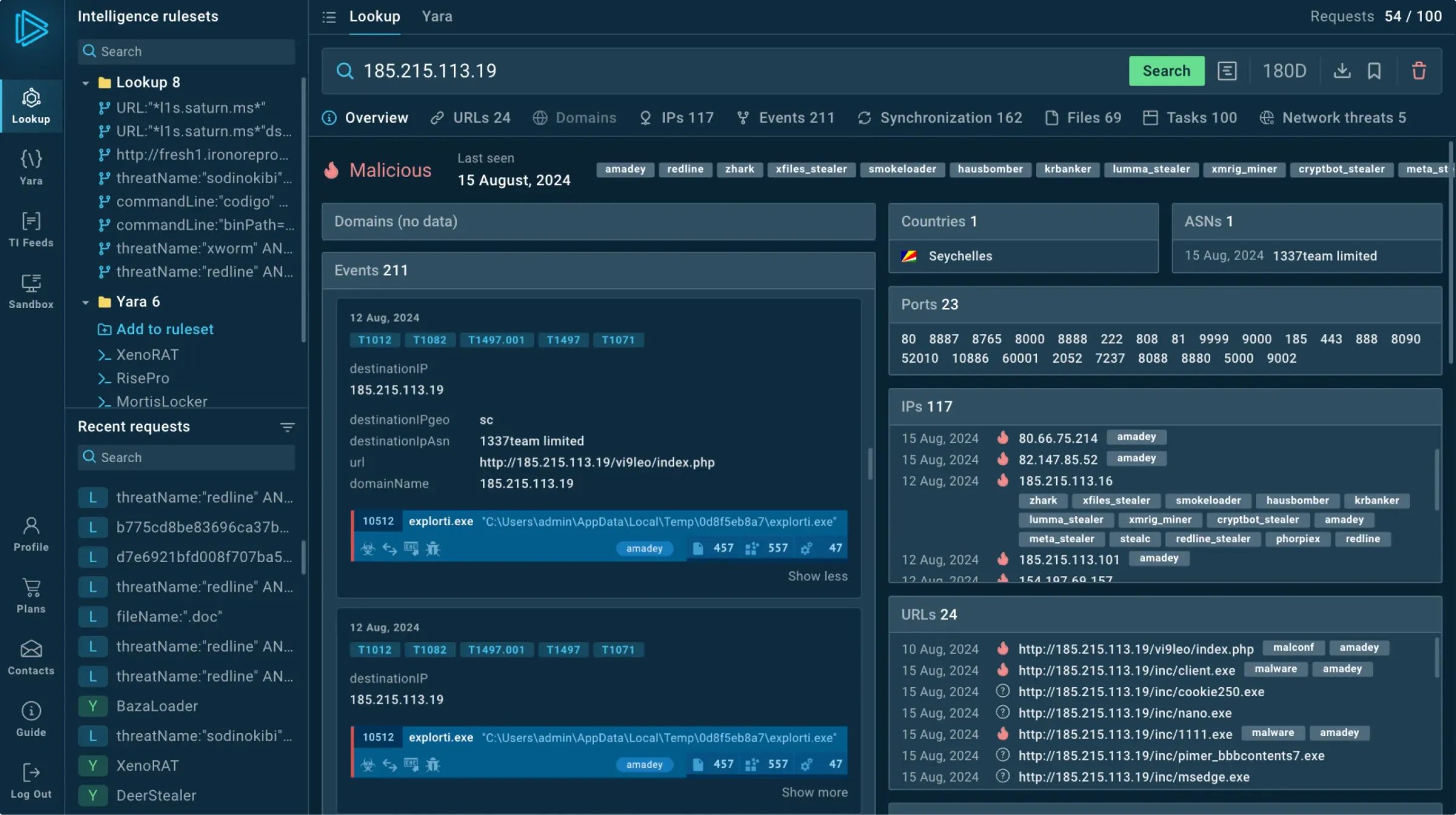
Browse contextual data
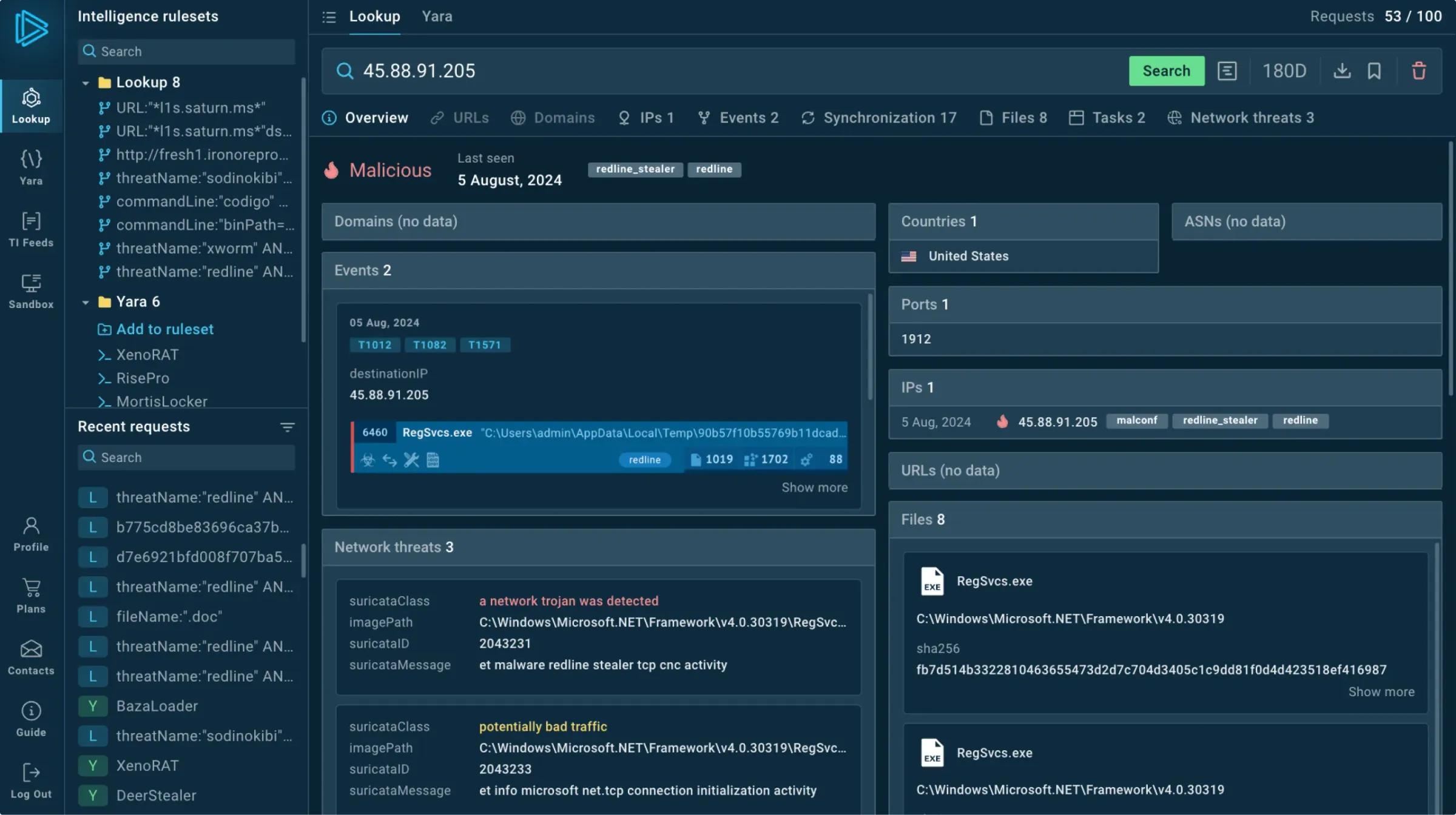
Every record contains related information such as threat names, IP addresses, and hashes.
Reinforce security systems
Receive continuously updated feeds of IOCs in your SIEMs and IPS/IDS systems using API and supplement it with SDK.
Perform deep searches
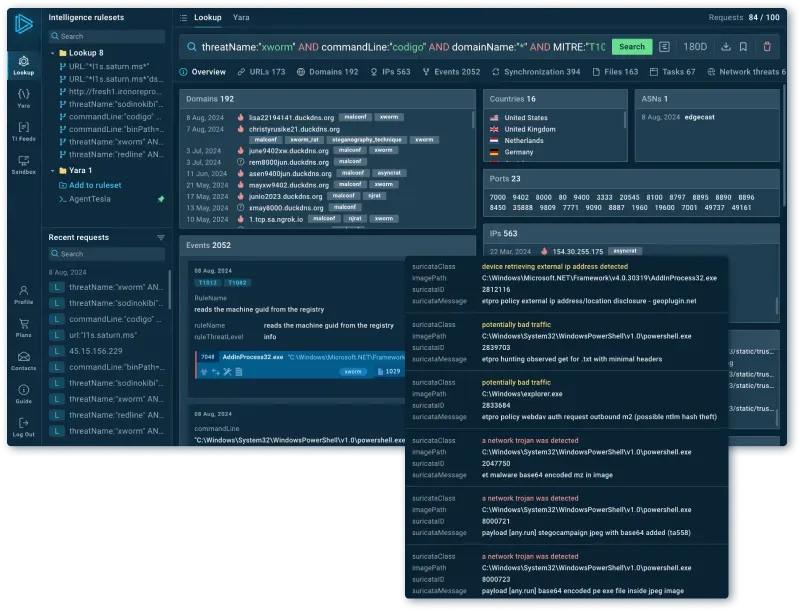
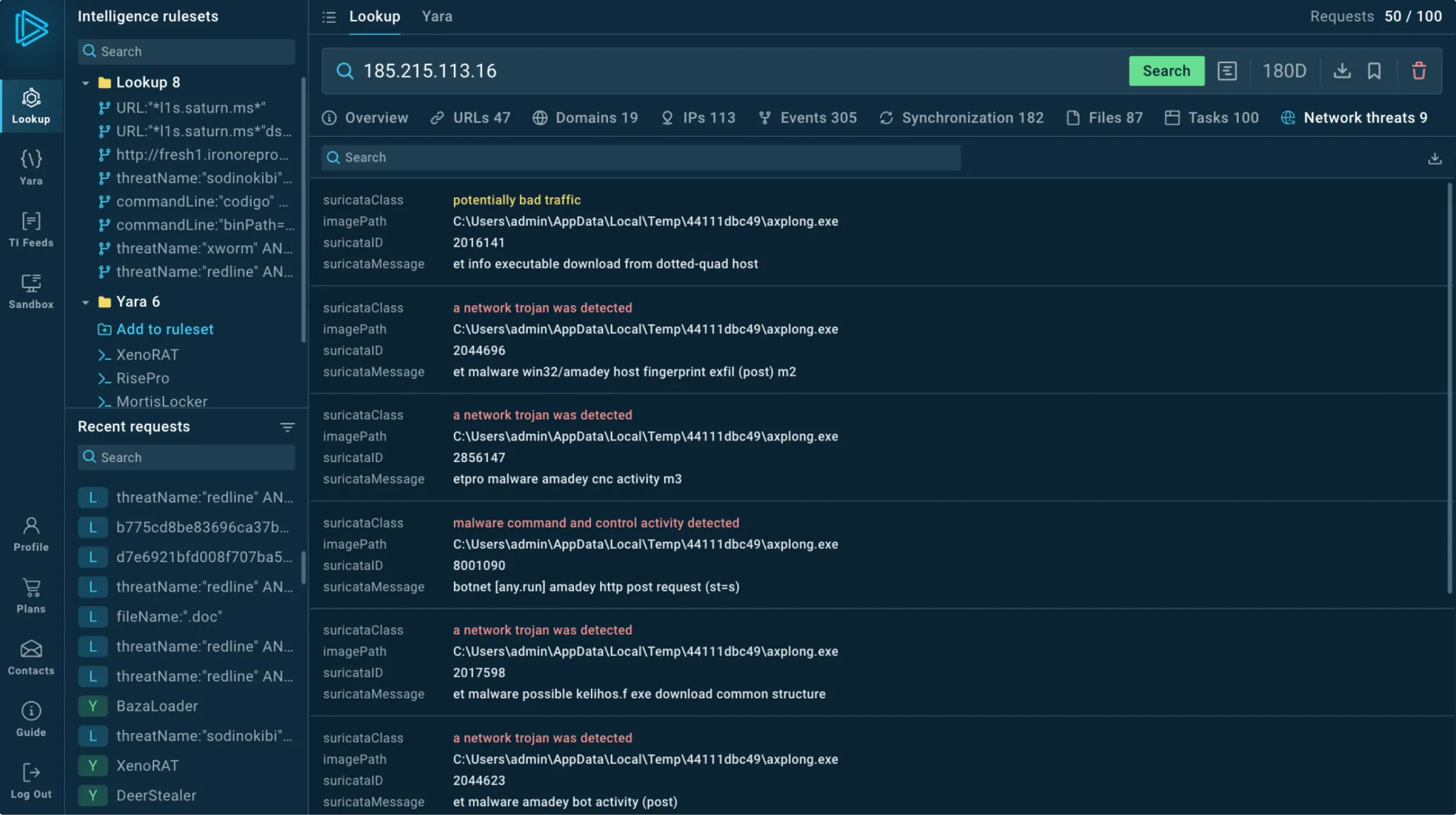
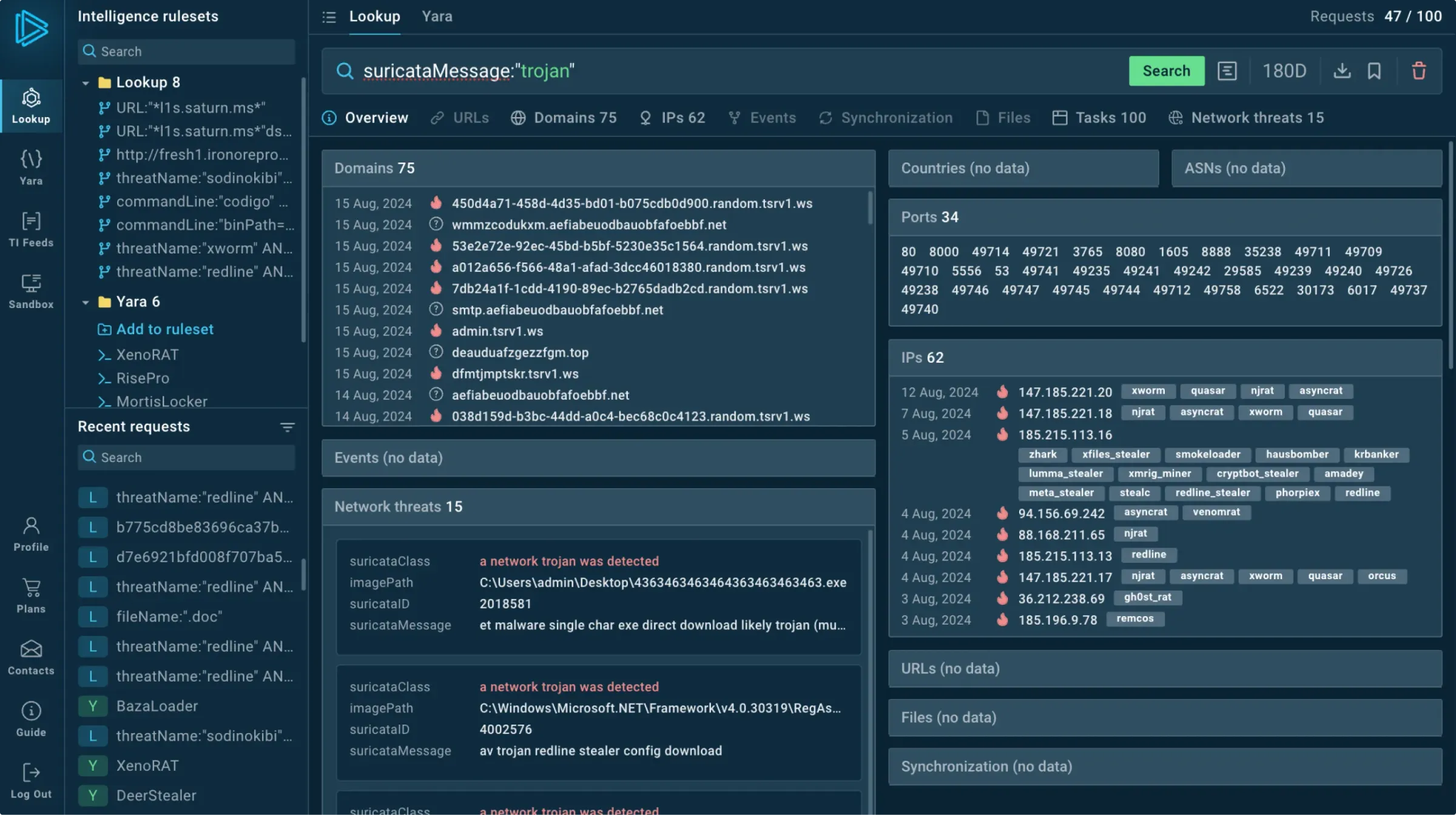
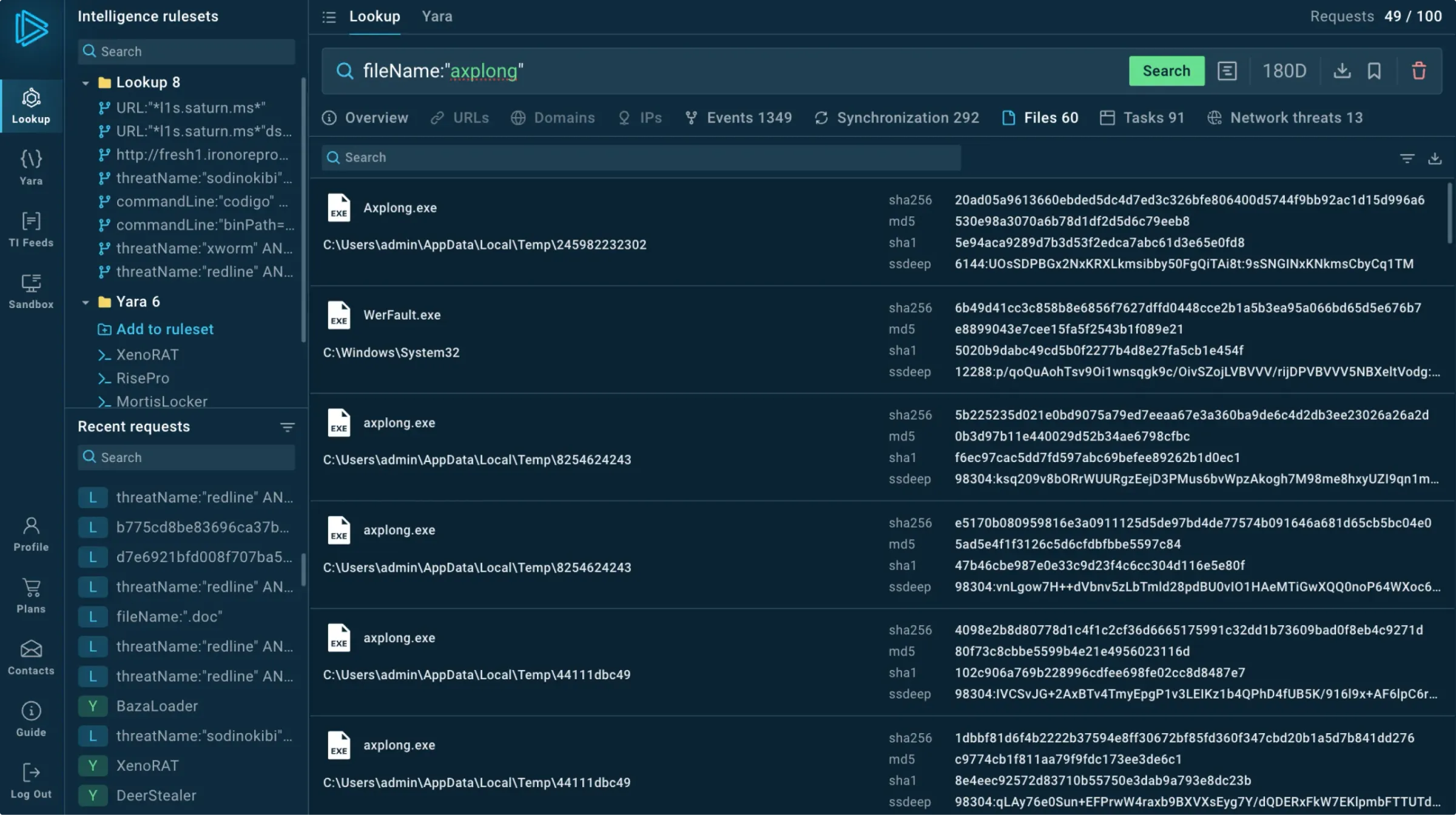
Look up any event fields or indicators (URLs, TTPs, file paths, etc.) and see connections between them.
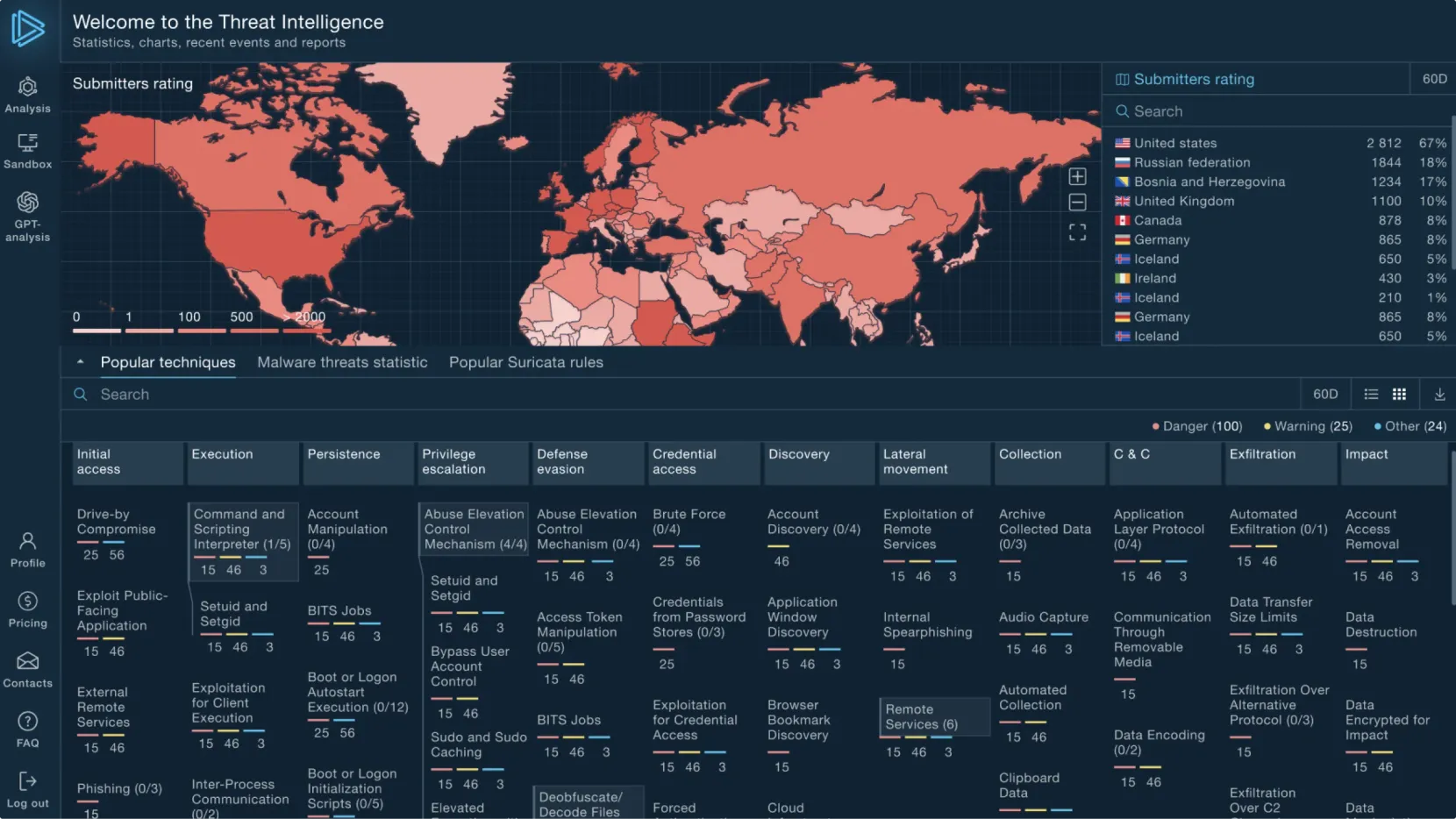
Explore threat landscape
Research threats by industries and regions to strengthen risk awareness and prioritization.
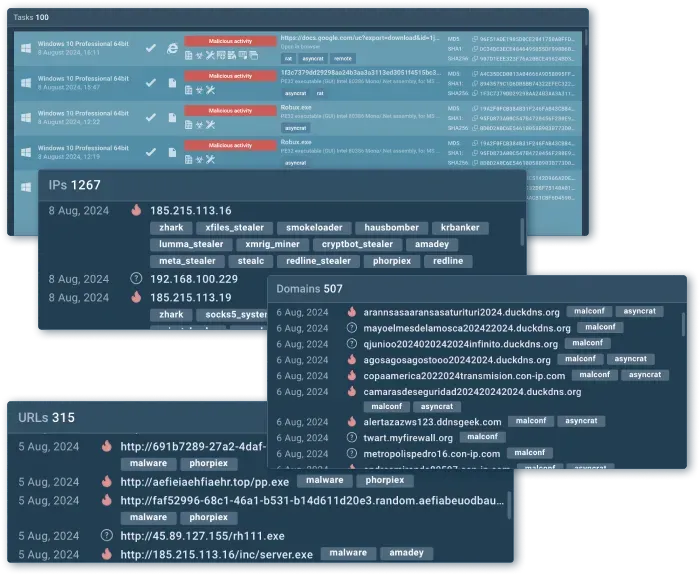
Look up threats across millions of sandbox research sessions
Find data, like malware actions and IOCs, across all ANY.RUN sandbox malware research sessions from 600,000 analysts.
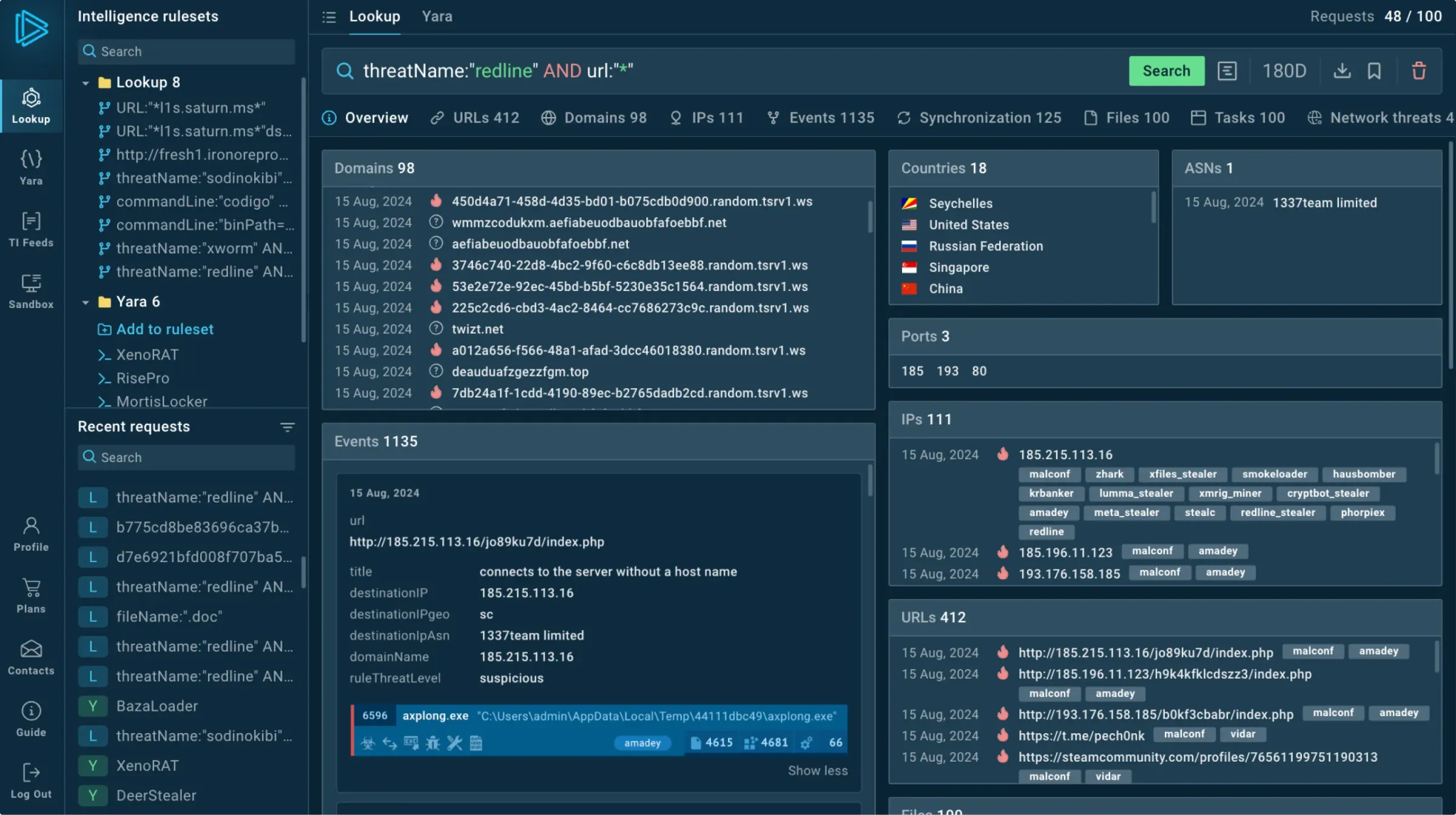
Use over 40 search parameters
Get results as wide or as precise as you need from 6 months of research data, which includes links to examples of TTPs implementation within interactive sandbox sessions.
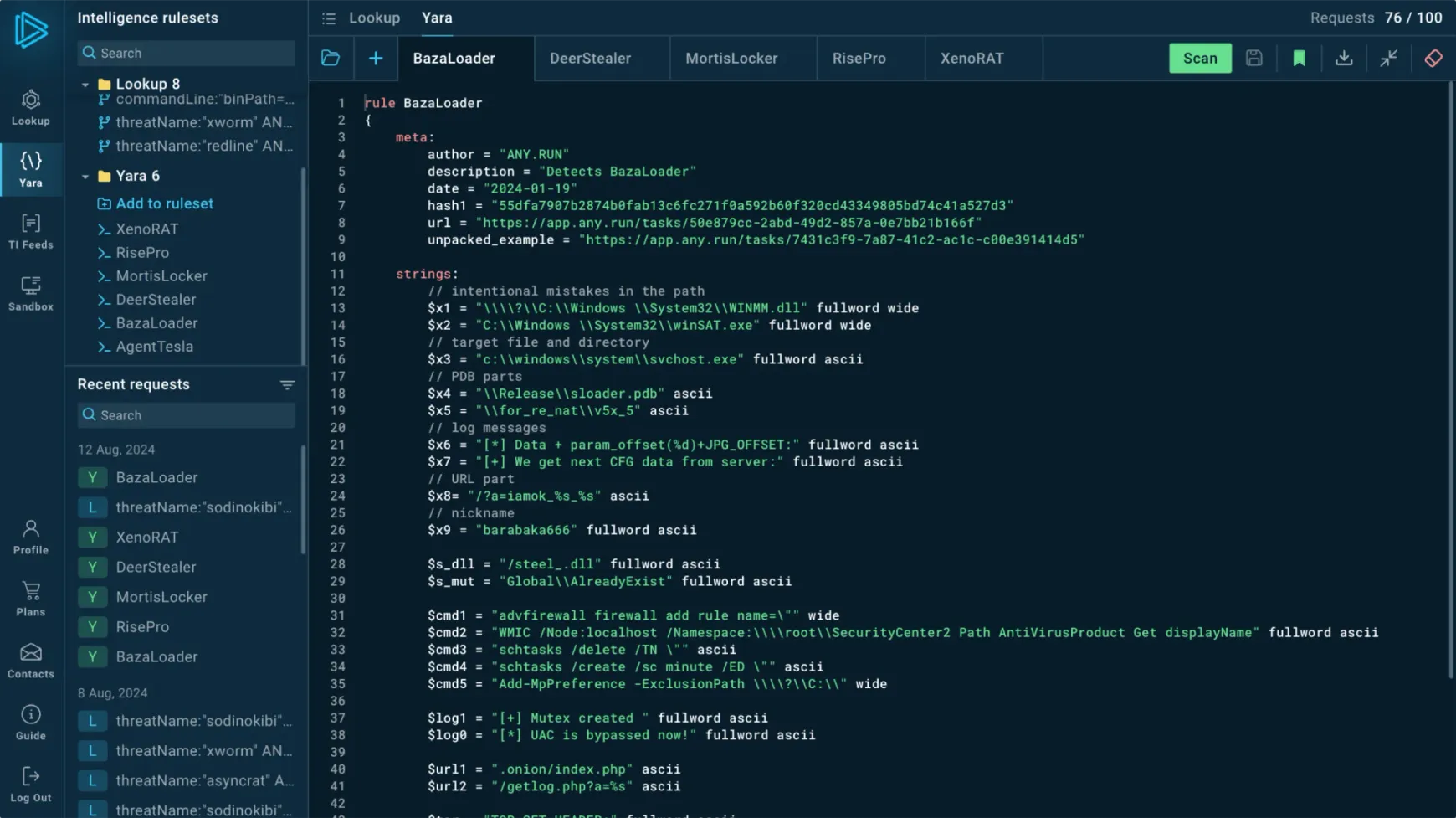
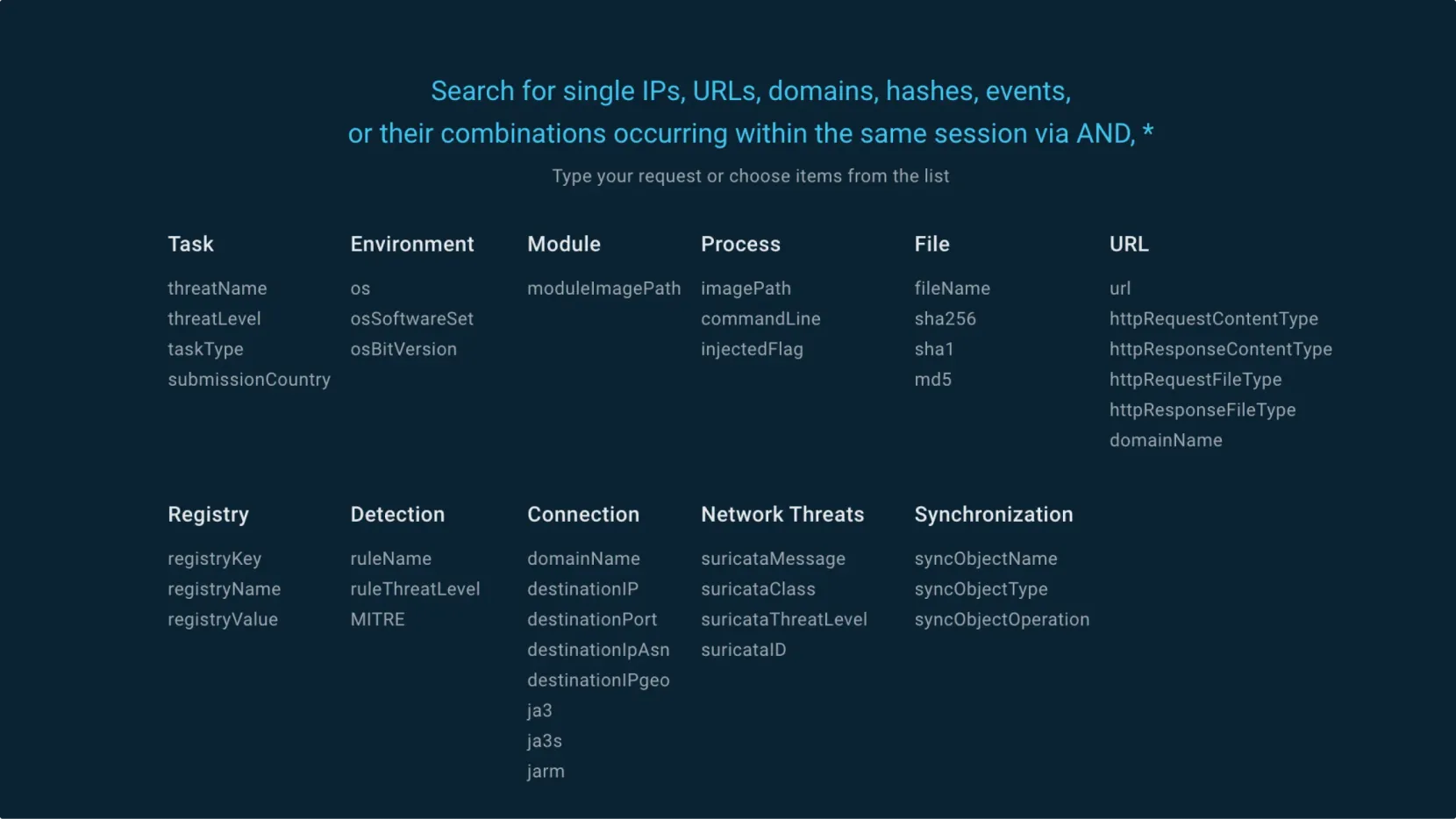
See examples of TTPs implementation
Each MITRE TTP entry contains an implementation example, from a real-world malware sample processed in our sandbox.
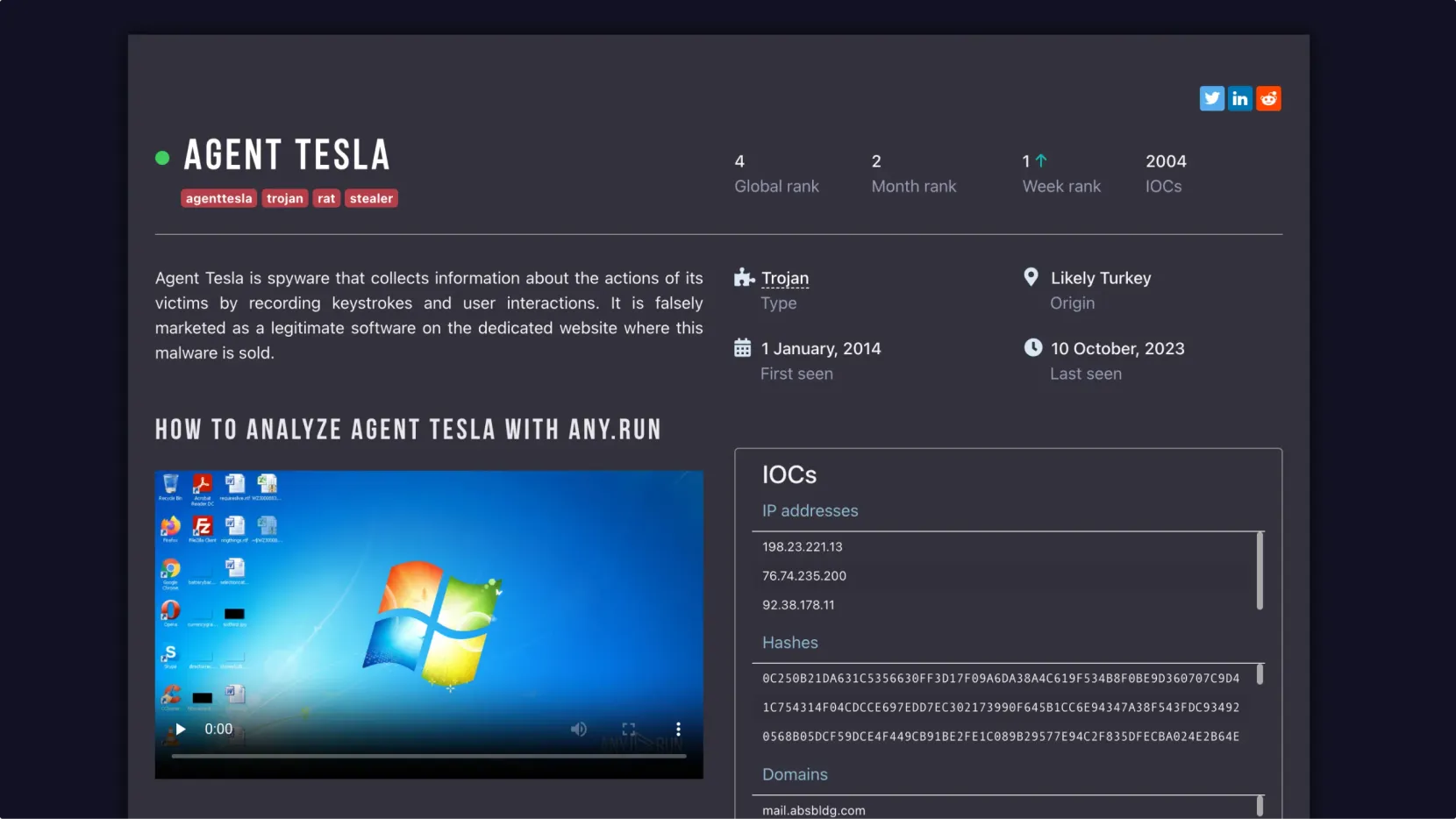
Track activity per family
Access comprehensive threat profile pages to get a holistic view of malware families, including popularity trends, detailed descriptions, and the latest IOCs.
Apply expert research on new cyber attacks and APTs
Discover reports, complete with search queries, on active threats from our analyst team to improve threat monitoring, incident response, and compliance.
Search by any indicator or event’s field
Use any suspicious indicator found in your system to find contextual threat information, including:
Threat names
Events
Domains
IPs
Process fields
YARA rules
URLs
TTPs
Hashes
Files
Suricata rules
Signatures
Our TI data sources
ANY.RUN Threat Intelligence Lookup provides a single web service, combining all information on cyberthreats and their relationships acquired by ANY.RUN.
Database with
50 million+ threats
It contains in-depth insights from threat investigations done in ANY.RUN's malware sandbox.
16 thousand new threats added daily
Threats are submitted by our community of over 600,000 researchers and 15,000 corporate clients.
Highly trusted, pre‑processed data
By running threats through our sandbox first we are able to extract rich contextual data such as events, TTPs and IOCs.
Integrate ANY.RUN in your company
Equip your SOC with rich context on the latest threats to:
- Streamline triage & response
- Gain better incident clarity
- Boost proactive security
- Track evolving attacks in real time