Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases

Balada Injector is a long-running malware campaign that targets WordPress websites by exploiting vulnerabilities in plugins and themes. The attackers inject malicious code into compromised sites, leading to unauthorized redirects, data theft, and the creation of [backdoors](https://any.run/malware-trends/backdoor) for persistent access. The campaign operates in waves, with spikes in activity observed every few weeks, continually adapting to exploit newly discovered vulnerabilities.
|
Backdoor
Type
:
|
Unknown
Origin
:
|
|
2 July, 2017
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
2 July, 2017
First seen
:
|
27 February, 2026
Last seen
:
|

 787
787
 0
0

 478
478
 0
0

 2728
2728
 0
0
Balada Injector is a large-scale and persistent malware campaign that has been targeting WordPress websites since 2017, potentially compromising nearly one million sites. While it was active for years, the campaign was officially named "Balada Injector" in December 2022.
This malware exploits vulnerabilities in WordPress plugins and themes, injecting malicious code and backdoors that redirect end users to fake and harmful sites. In addition to redirections, Balada Injector exfiltrates sensitive information, such as database credentials, archive files, access logs, and other data that may not be securely stored.
A notable wave of attacks occurred in September 2023 when the campaign exploited a cross-site scripting (XSS) vulnerability in CVE-2023-3169, associated with the tagDiv composer plugin. During these attacks, the malware employed injection methods such as HTML, database, and arbitrary file injections. The attackers also planted backdoors capable of executing PHP code and installed malicious WordPress plugins, including one named "wp-zexit," to maintain persistent control over compromised systems.
Balada Injector operates in recurring waves, with activity spikes observed every few weeks. Its ability to adapt and exploit newly discovered vulnerabilities, combined with techniques for maintaining long-term access, makes it a significant threat to WordPress websites globally.
Shared hosting environments, where plugins and themes may not always be securely maintained, are especially vulnerable.
The campaign's evolving methods and extensive impact highlight the need for rigorous security measures, timely updates, and proactive monitoring to protect websites from compromise.
To do this, you can use tools like ANY.RUN interactive sandbox and analyze all the suspicious activities inside a secure environment: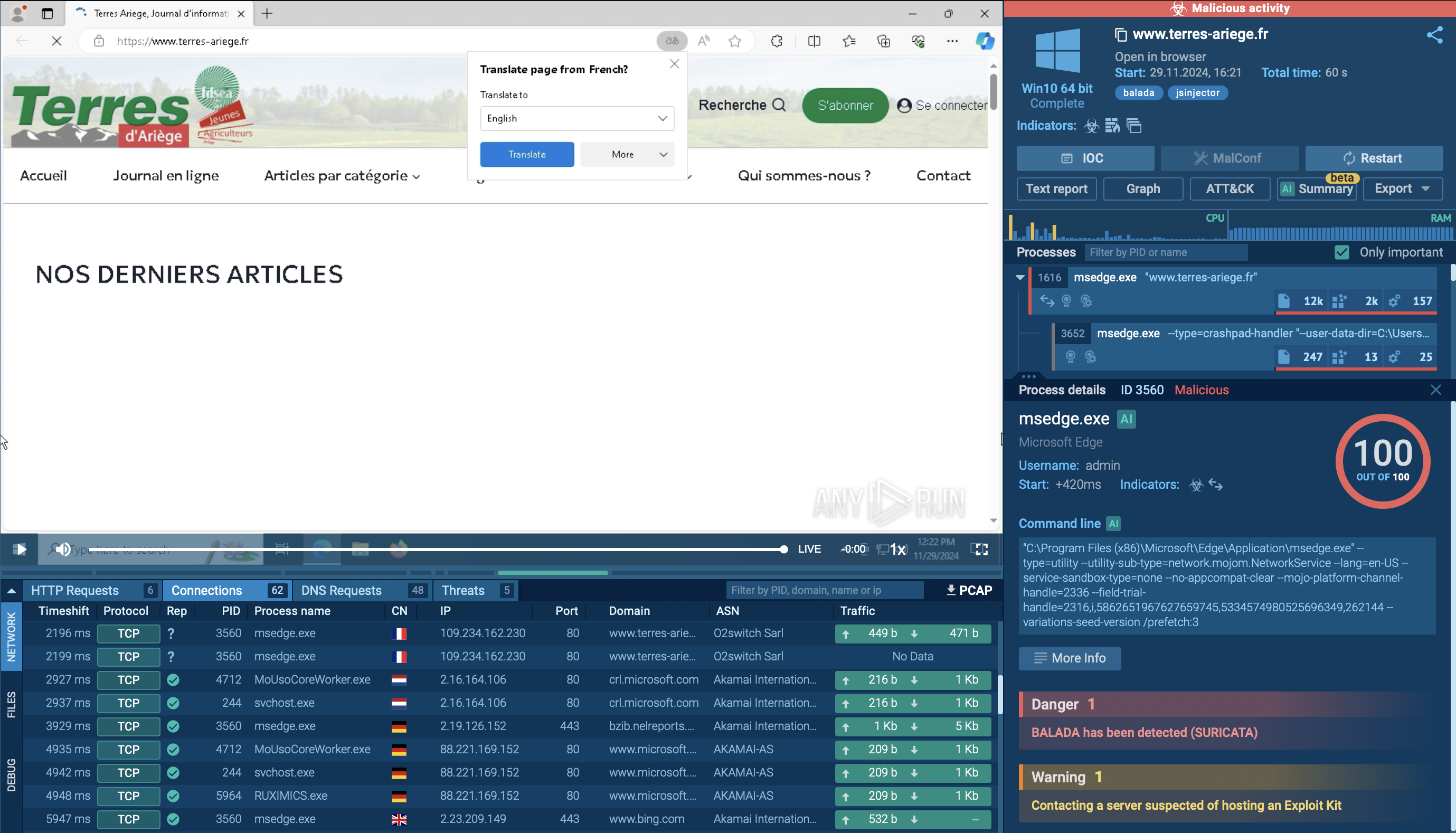 Analysis of Balada Injector inside ANY.RUN sandbox
Analysis of Balada Injector inside ANY.RUN sandbox
The main technical features and functionalities of Balada Injector include:
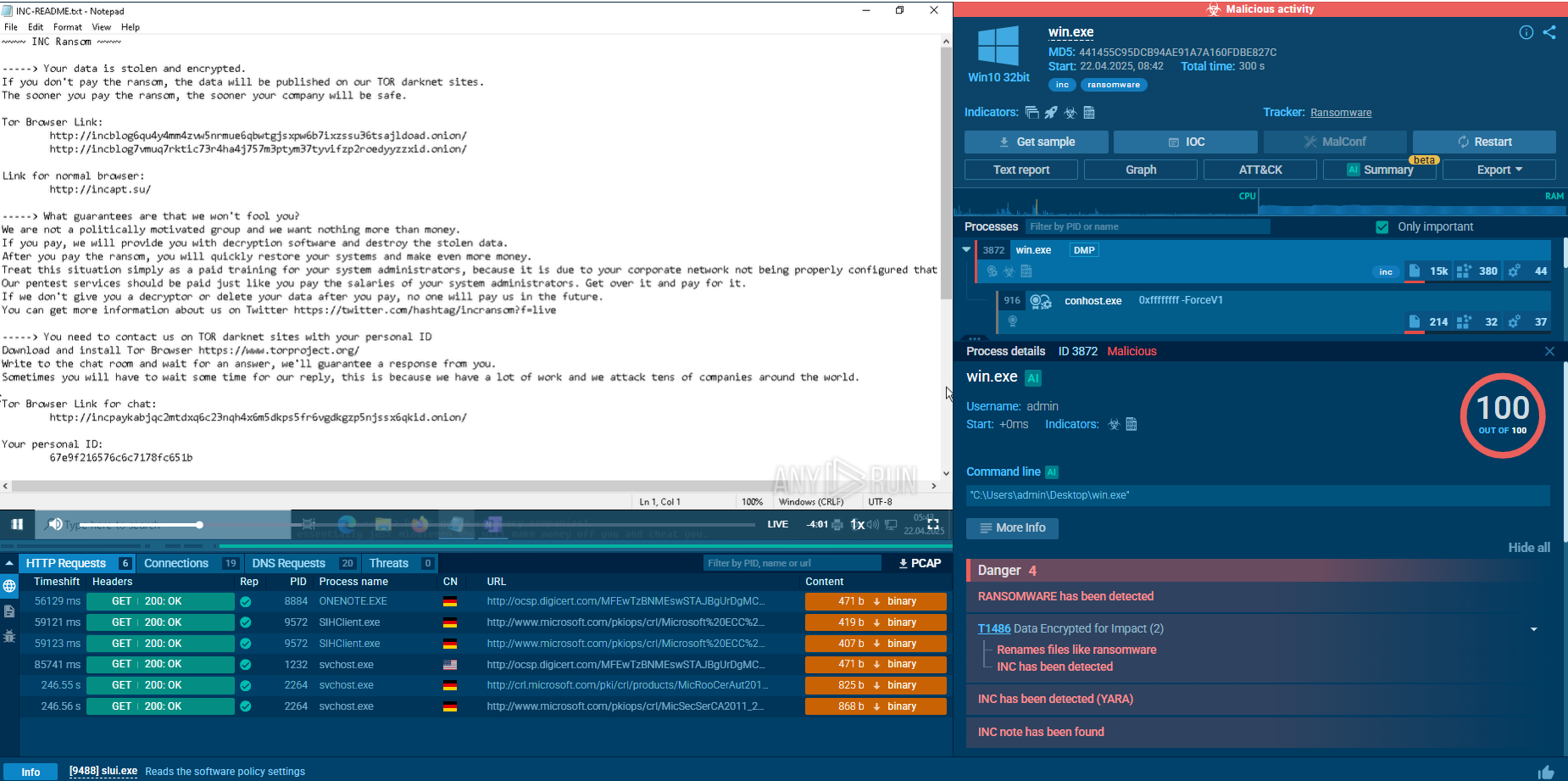
To see how Balada Injector operates, let’s upload its sample into ANY.RUN’s interactive sandbox.
The infection begins with attackers exploiting known vulnerabilities, particularly in popular WordPress themes and plugins.
Once a site is compromised, the malware injects malicious scripts into various files, including critical components like 404.php. This initial payload often consists of obfuscated JavaScript that loads additional malicious scripts from attacker-controlled domains through AJAX requests.
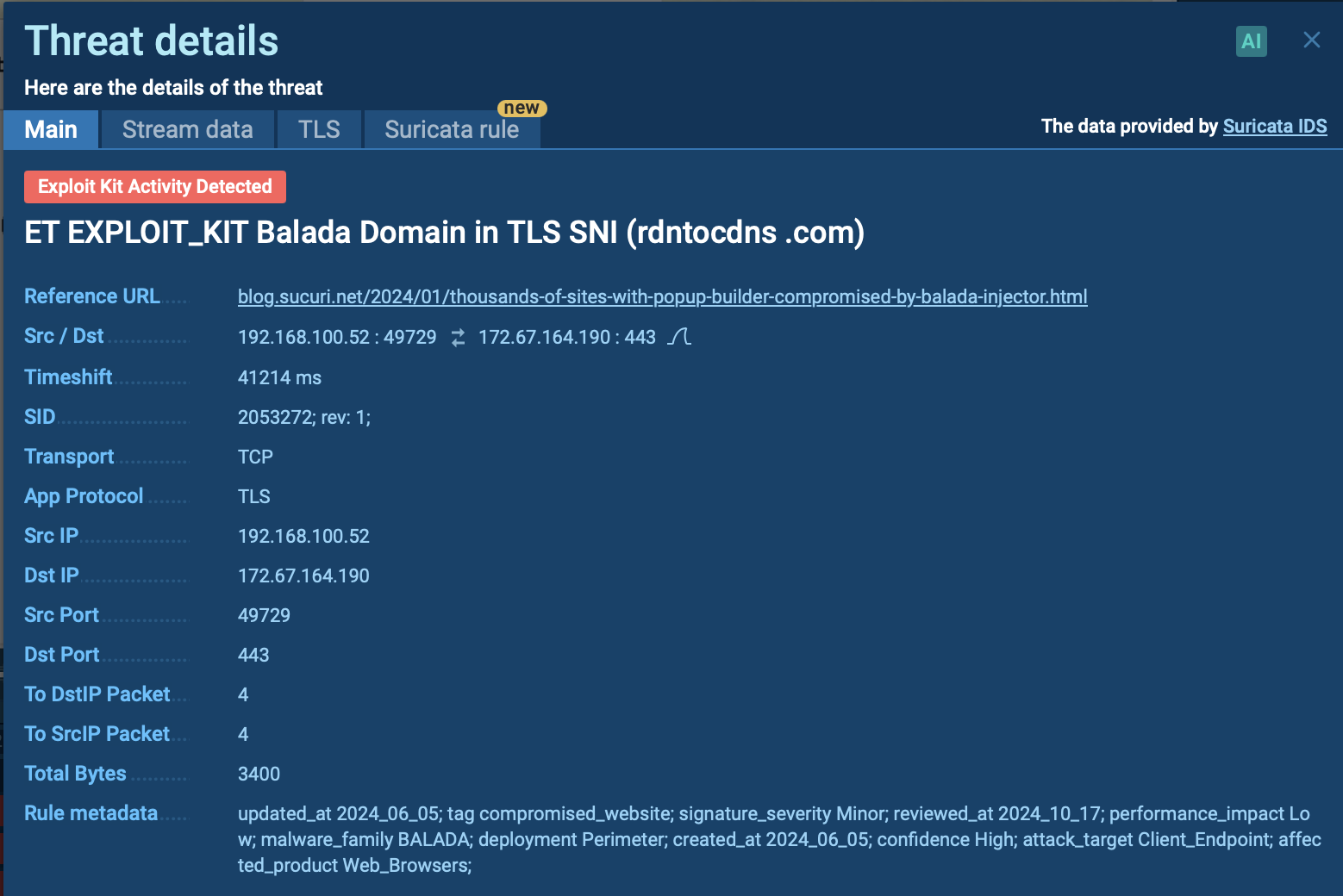 Suricata rule triggered inside ANY.RUN sandbox by Balada Injector
Suricata rule triggered inside ANY.RUN sandbox by Balada Injector
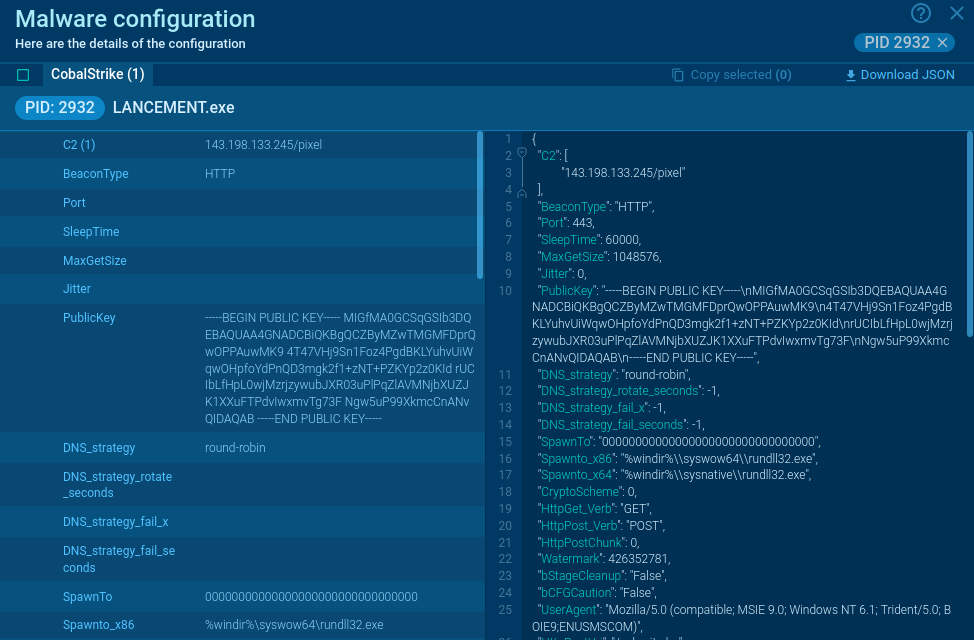
As part of this process, the malware may create new malicious admin users with randomly generated passwords, which are reported back to the attackers via POST requests. This allows the attackers to maintain control over the compromised site.
Data exfiltration is another key aspect of the Balada Injector's execution chain. The malware is designed to steal sensitive information, such as database credentials from wp-config.php files and other critical data stored on the server. Attackers often look for backup archives and logs that may contain valuable information for further exploitation.
To ensure persistent access to compromised sites, multiple backdoors are installed. This includes modifying existing files like 404.php, allowing easy access without triggering security alerts. The malware notifies attackers when a backdoor is successfully installed, enabling them to monitor their control over infected sites.
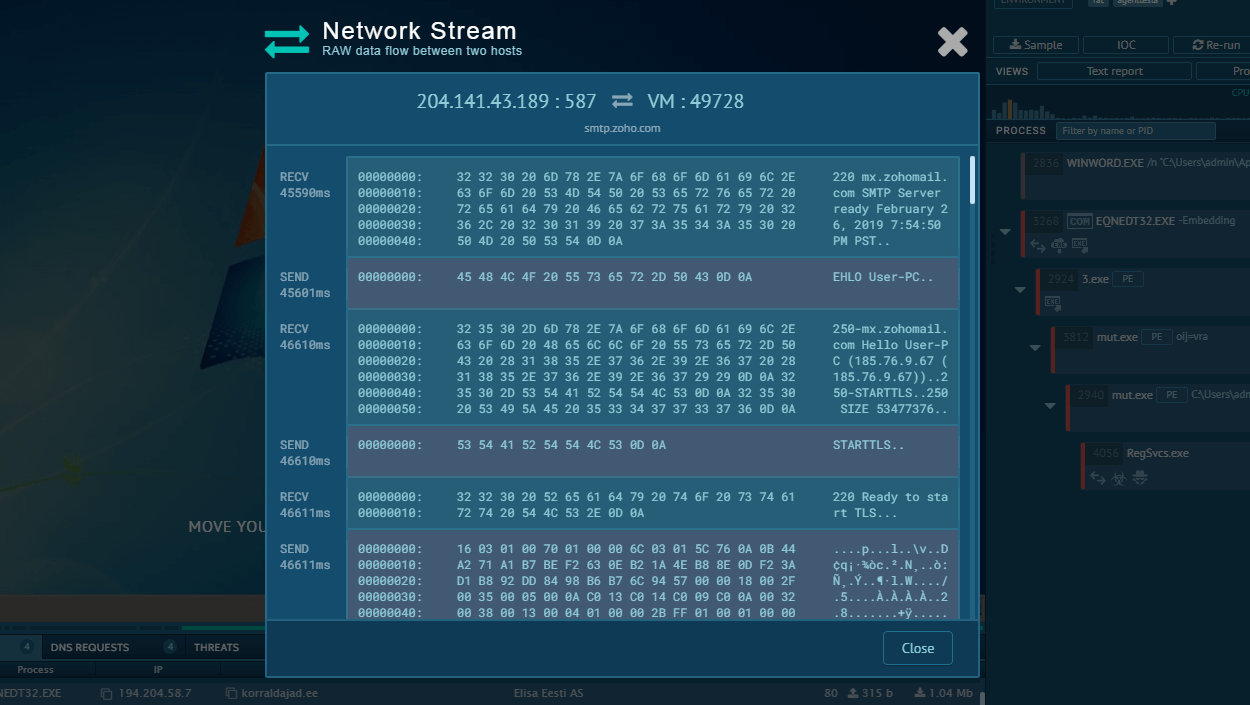
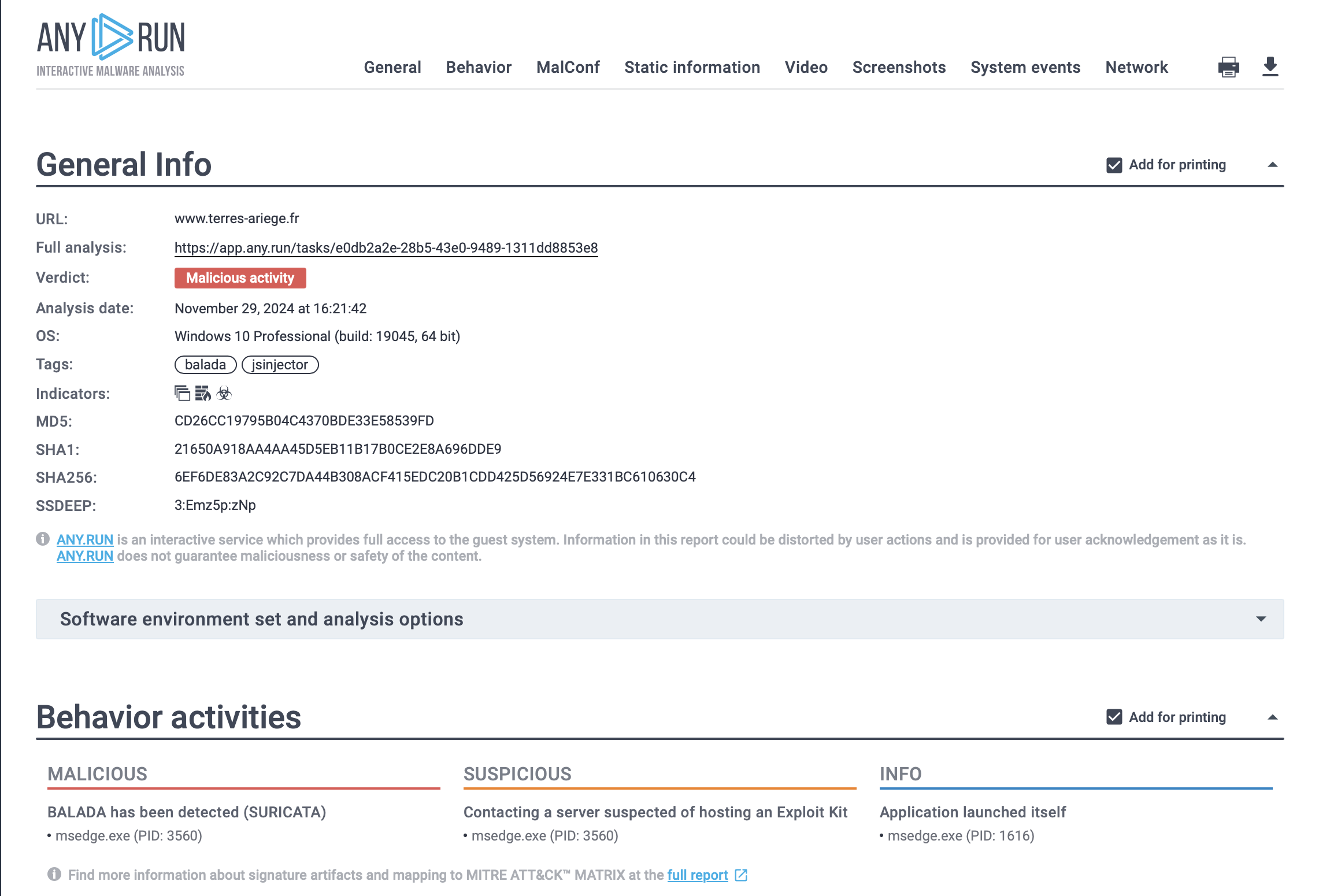 Text report of Balada Injector generated by ANY.RUN sandbox
Text report of Balada Injector generated by ANY.RUN sandbox
The Balada Injector also employs a strategy of reinfection by utilizing previously collected data on compromised domains to launch subsequent attacks on these sites or related ones sharing the same server environment. If direct access methods fail, attackers may initiate brute-force attacks against admin accounts, attempting numerous credential combinations in an effort to gain access.
Evasion techniques are integral to the Balada Injector's effectiveness. The campaign frequently changes its command and control (C2) domains and employs various obfuscation techniques in its scripts to avoid detection by security software. By using newly registered domains for each wave of attacks, the malware complicates efforts to block it effectively.
There are several ways that attackers use to distribute the Balada Injector malware. The most common ones include:
To gather up-to-date intelligence on Balada Injector, utilize Threat Intelligence Lookup.
This tool provides access to a comprehensive database of insights derived from millions of malware analysis sessions performed in the ANY.RUN sandbox. With over 40 customizable search options, you can uncover detailed information on threats, including IPs, domains, file hashes, filenames, and process artifacts.
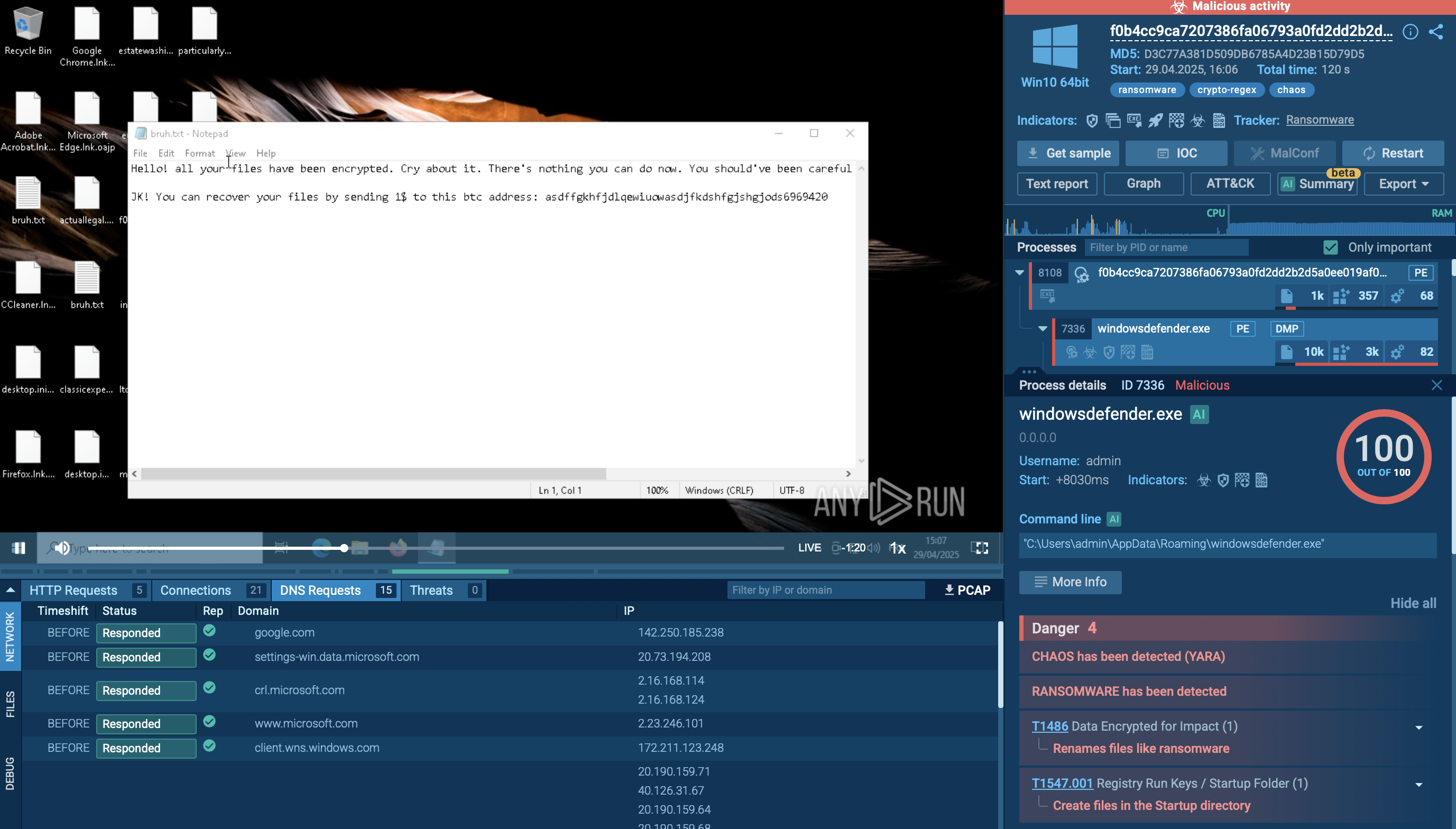
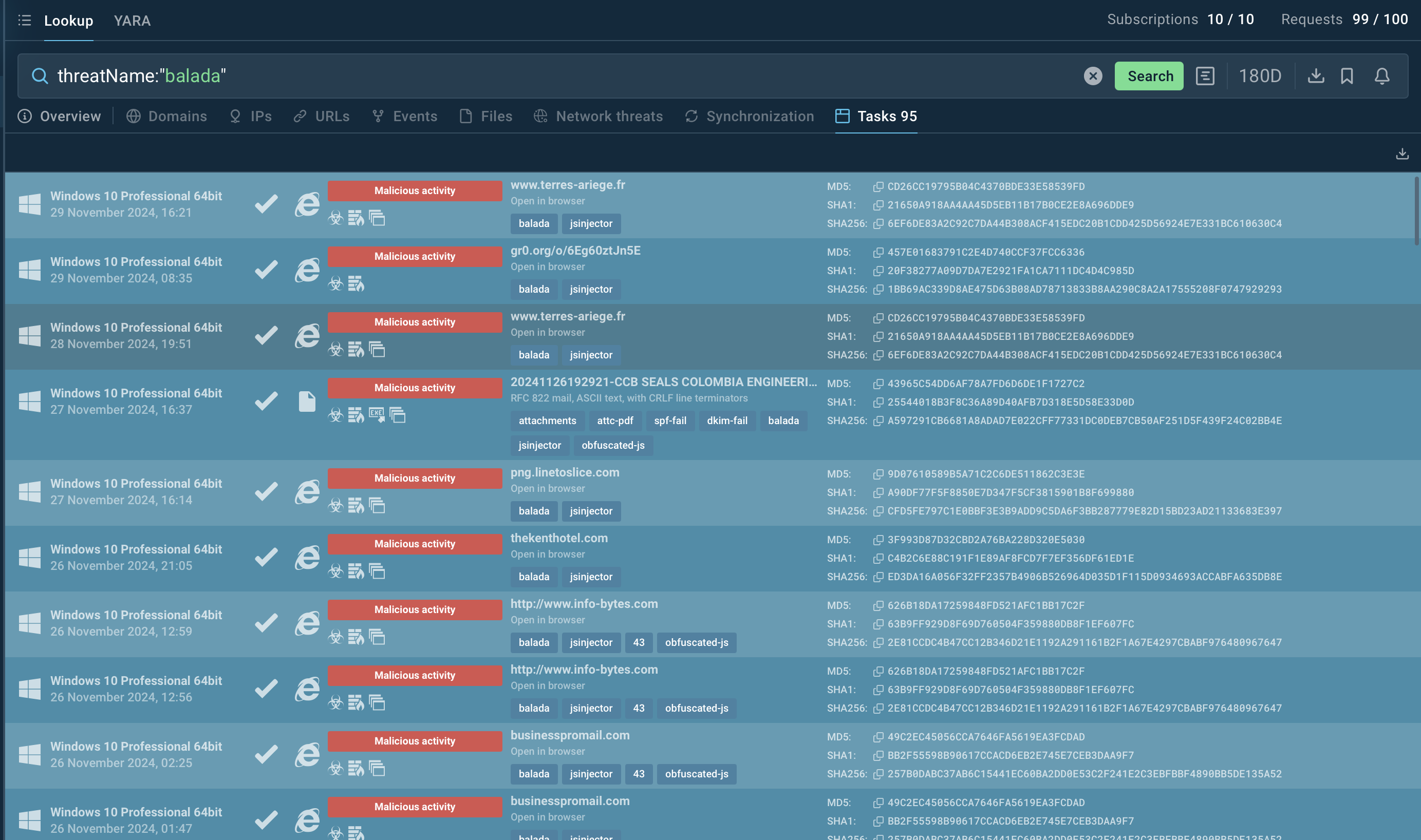 Balada Injector search in ANY.RUN’s TI Lookup
Balada Injector search in ANY.RUN’s TI Lookup
For example, you can look up Balada Injector directly by its name or search using related artifacts. Entering a query such as threatName:"Balada" in the Threat Intelligence Lookup will display all relevant samples and sandbox results linked to this malware, providing you with actionable intelligence.
Start exploring with a 14-day free trial of Threat Intelligence Lookup and the ANY.RUN sandbox today!
Balada Injector is a persistent threat, exploiting vulnerabilities in WordPress plugins and themes to inject malicious code, steal data, and create backdoors. Proactively analyzing suspicious activity is essential to prevent compromises and protect your site from such malware.
ANY.RUN provides real-time malware analysis, enabling users to investigate malicious activity, uncover attack methods, and gather actionable intelligence to strengthen security defenses.
Sign up for a free ANY.RUN account today and start analyzing cyber threats like Balada Injector!