Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases
Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth.

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
Crypto miner malware is a type of malicious software that gains unauthorized access to a computer and utilizes its resources to mine cryptocurrencies. This type of malicious activity is also known as cryptojacking. There are variants of cryptojacking that do not require the installation of malware on the device. This is usually done via a malicious script added to a website.
Mining is a process that involves complex mathematical calculations to validate and add transactions to a blockchain. In return, miners typically receive a small amount of cryptocurrency.
Crypto miner malware is not only a threat to individual users but also to companies. In a business environment, a crypto miner can infect multiple systems, leading to a significant impact on productivity and increased energy costs.
Plus, crypto miners are often implemented simply as additional modules to different malicious software. Consequently, such malware can not only mine virtual currencies, but also steal sensitive information from the machine or spy on the user.
Crypto miners can significantly impact a computer's performance and lifespan due to their resource-intensive nature. Since mining involves complex mathematical calculations to validate and add transactions to a blockchain, crypto miners can consume a significant portion of the computer's central processing unit (CPU) or graphics processing unit (GPU) power, leading to slower performance, increased latency, and even system crashes in extreme cases.
Crypto miners may also consume a significant amount of network bandwidth, especially when communicating with the mining pool or the command-and-control (C2) server. This can lead to slower internet speeds and impact the performance of other network-dependent applications.
The higher use of system resources can also lead to increased power consumption, resulting in higher electricity bills. In a corporate environment, cryptojacking can cause significant business disruptions, impact productivity, and lead to financial losses.
Crypto miners can often operate in the background and employ techniques to evade detection. For example, they may reduce the mining process when the user is actively using the system or use legitimate system processes to disguise the mining activity.
Crypto miners can spread in different ways, similar to other types of malware.
Phishing emails constitute the primary attack vector. Through social engineering, threat actors can get users to download and run malicious software on their system. To prevent falling victim to a phishing attack, users can analyze suspicious links and files in the ANY.RUN sandbox to quickly see if they are malicious.
Another common method of infection involves file sharing platforms. In such cases, attackers usually disguise malware as legitimate or pirated software that users may download and execute.
Attackers may also embed malicious scripts into compromised websites. Once the user visits such a website, the script begins mining using the user's device's resources.
In order to observe the behavior of a cryptojacking malware, we can upload it to the ANY.RUN sandbox. This service will let us safely execute the malicious program in a virtual environment and study all aspects of its operation.
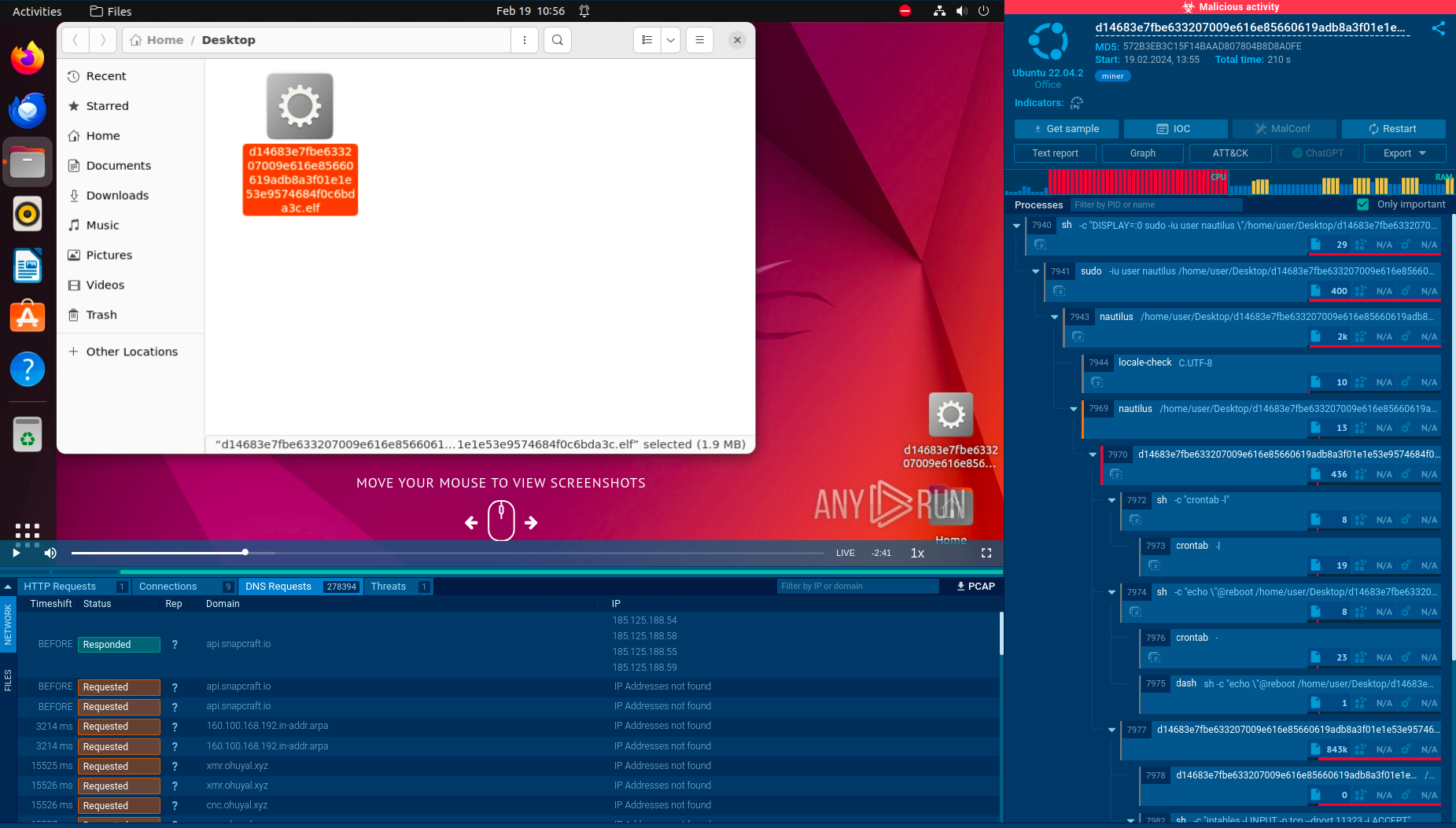 The malicious crypto miner executable analyzed in ANY.RUN
The malicious crypto miner executable analyzed in ANY.RUN
In this analysis session, we can see how a miner executable is distributed in the form of an .elf file, an executable format on Linux systems. After execution, the service instantly detects malicious activity and provides us with valuable insights into the malware’s behavior.
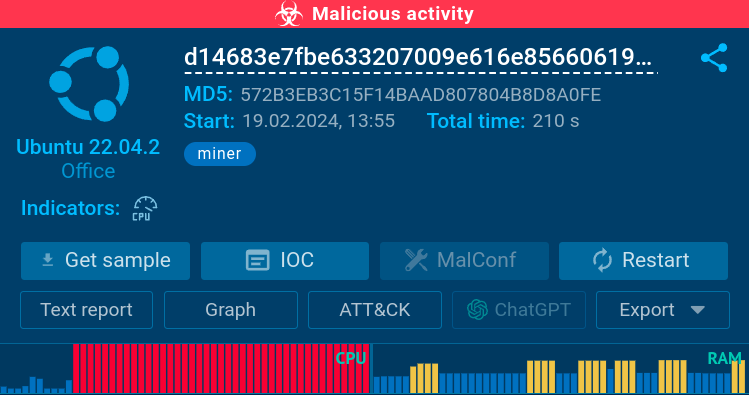 The CPU and RAM graphs indicate the miner’s presence
The CPU and RAM graphs indicate the miner’s presence
One telltale sign of the malware’s is a spike in the CPU and RAM usage, which is clearly shown by the sandbox.
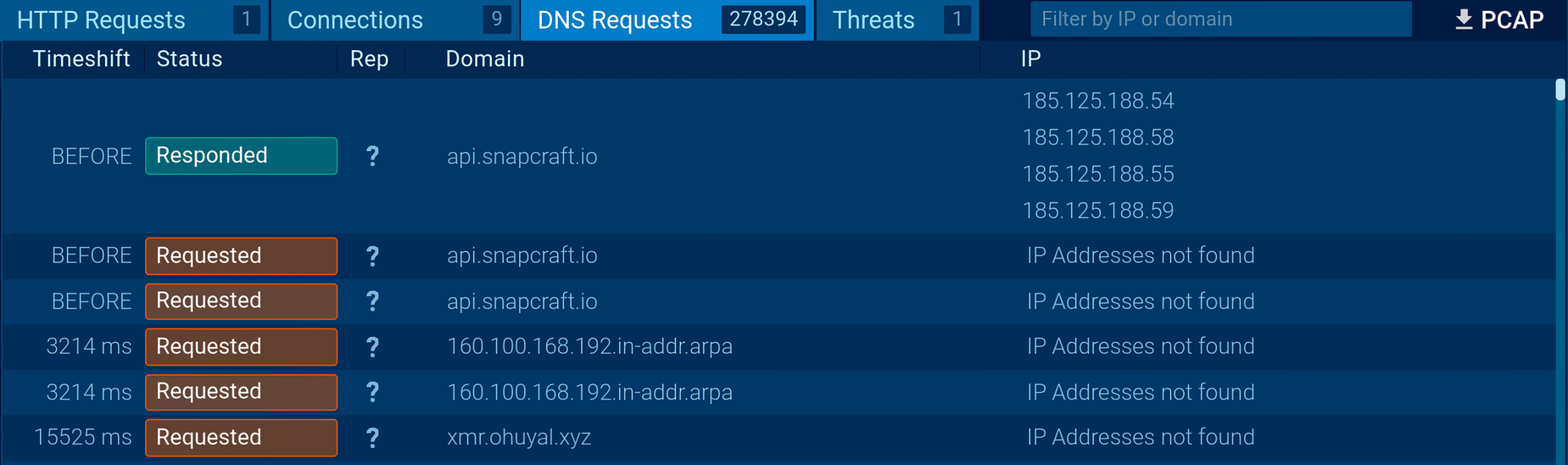 The DNS Requests segment lists more than 270,000 entries
The DNS Requests segment lists more than 270,000 entries
Additionally, the network analysis reveals how the malware makes hundreds of thousands of DNS requests.
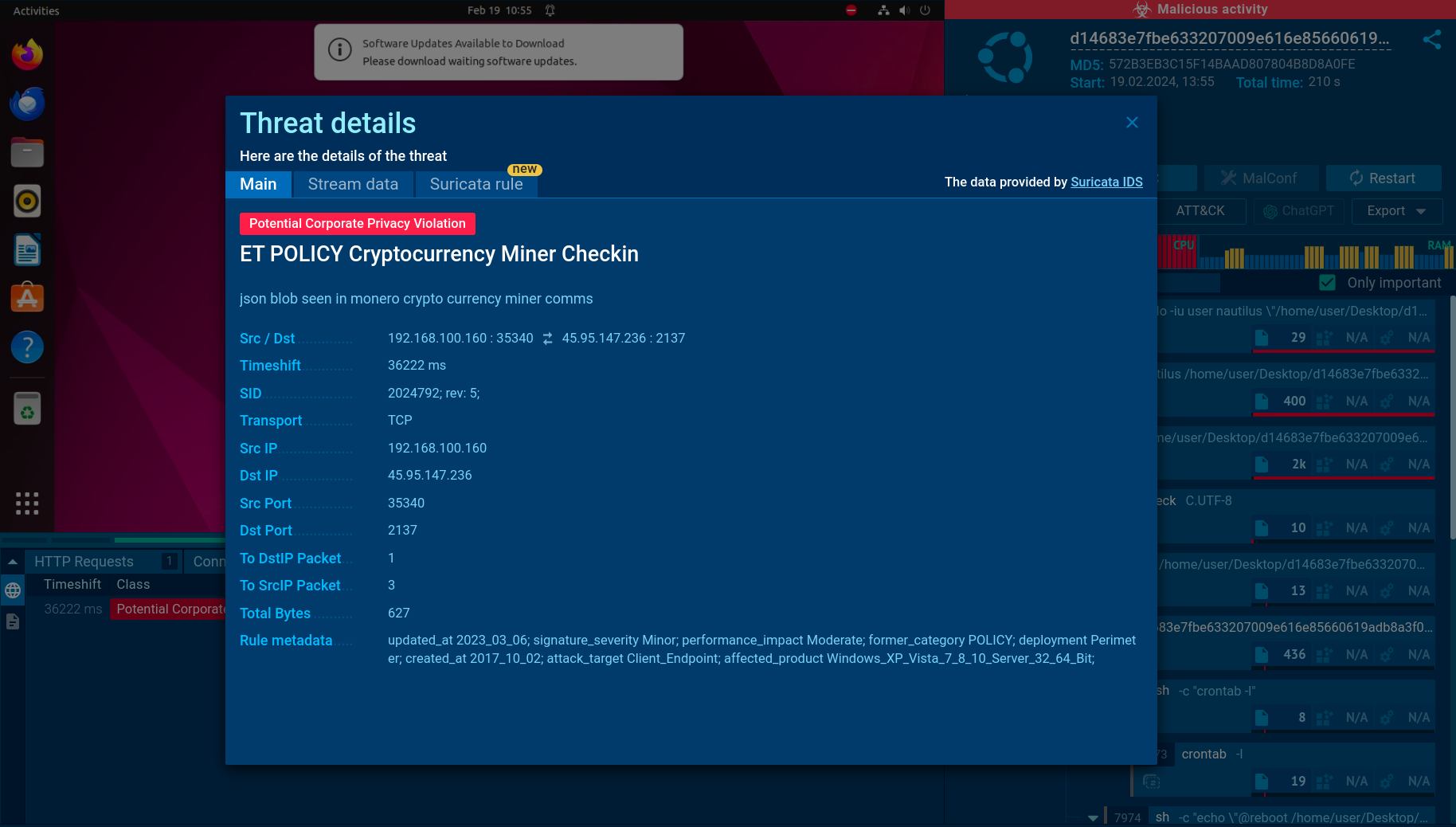 The Suricata rule utilized for detecting the miner
The Suricata rule utilized for detecting the miner
Finally, the service lets us learn more about the Suricata rule used to detect this malware. It points out that the miner in question is used for mining the Monero cryptocurrency.
In order to prevent crypto miner infection, it is vital to stay in the know about all the currently active malware engaging in such activities. DarkGate is one example of a malware that is used by different threat actors to deliver mining software on to victims' devices. One of the most common cryptojacking payloads distributed by DarkgGate is XMRig, which can mine Monero.
There are also JavaScript-based browser miners such as CoinIMP that can be employed by criminals to mine Monero or MintMe cryptocurrencies.
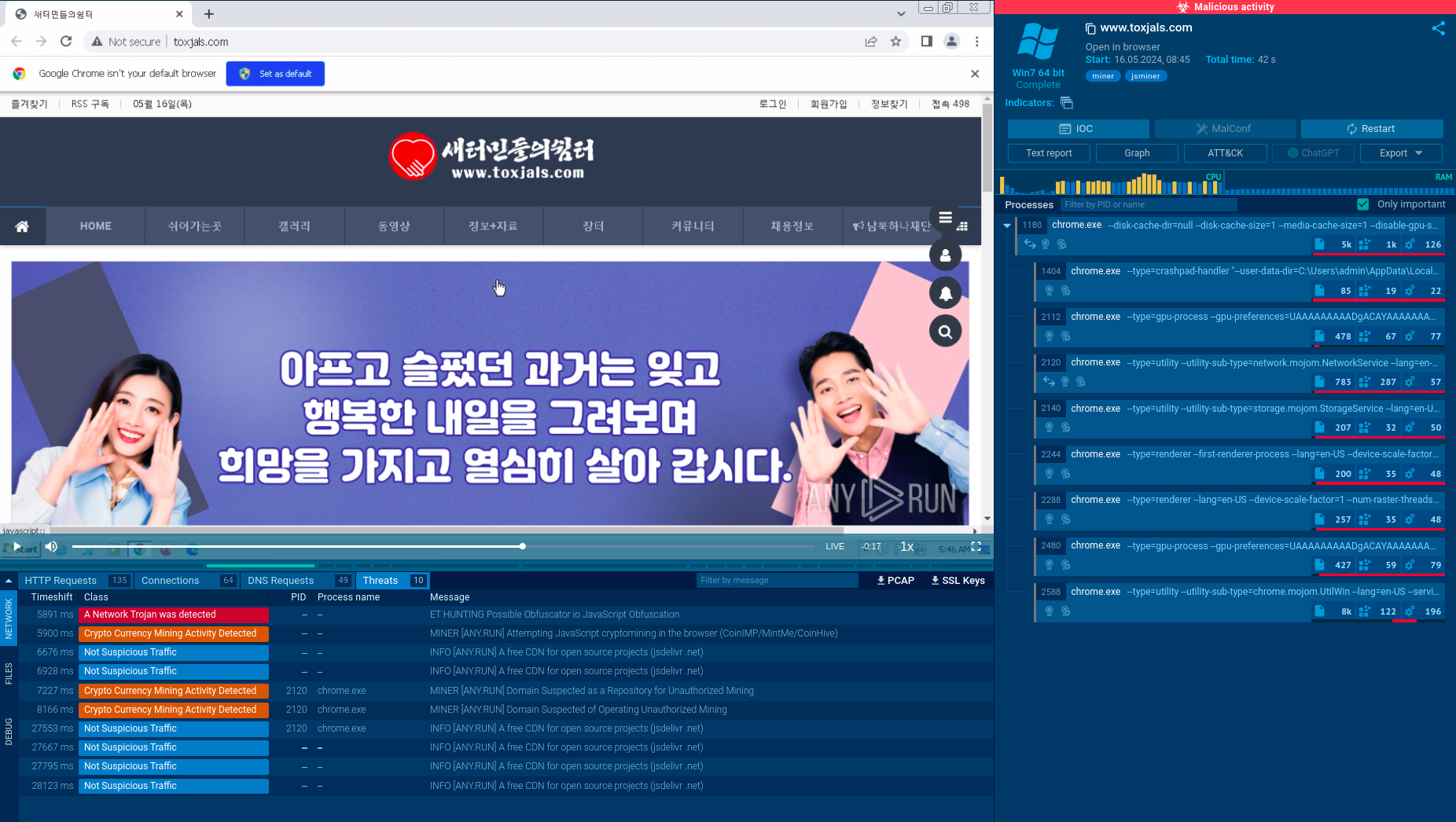 This website launches cryptojacking code that mines crypto using visitors’ resources
This website launches cryptojacking code that mines crypto using visitors’ resources
Check out this analysis session in the ANY.RUN sandbox that features an example of a website injected with the CoinIMP miner.
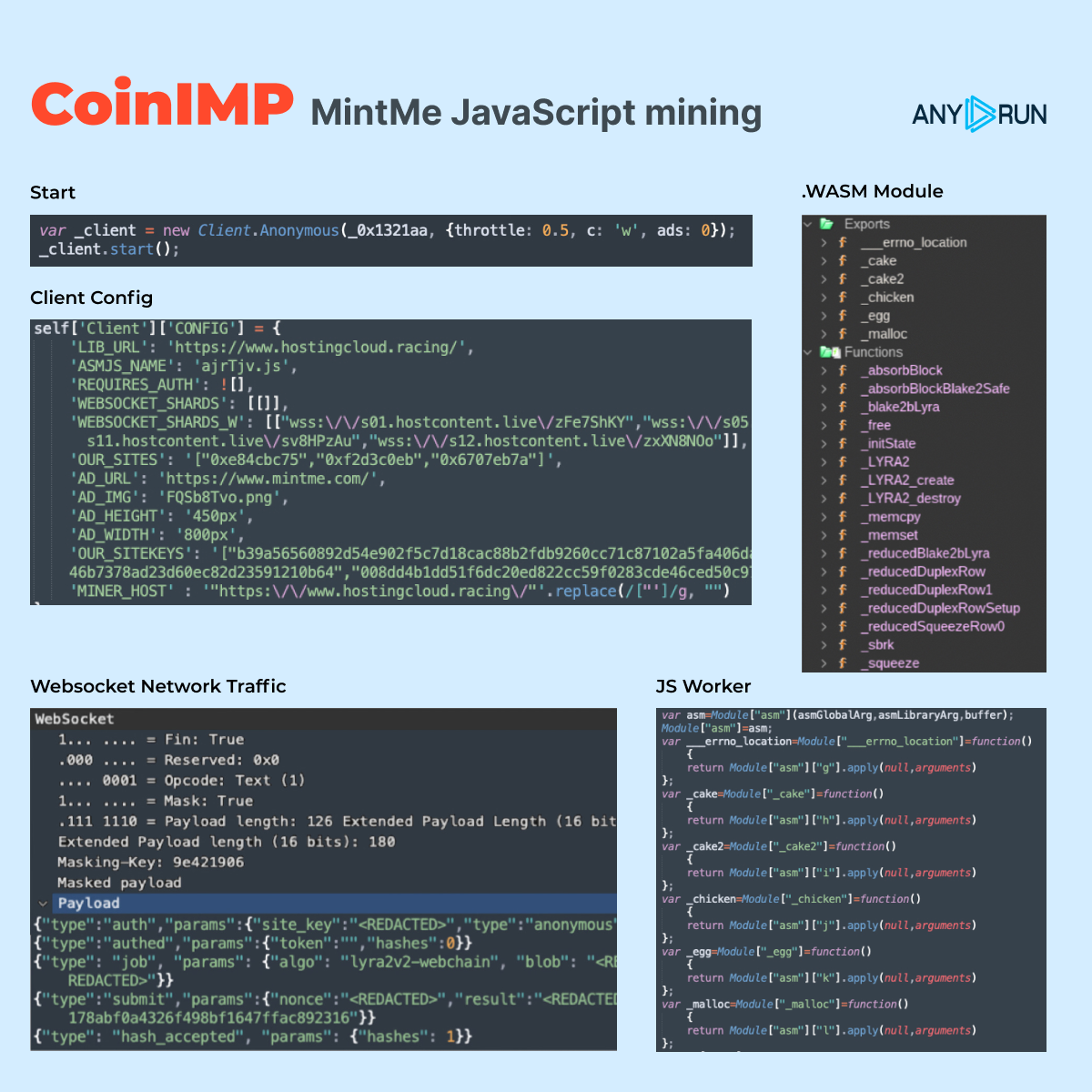 A detailed description of how the mining process takes places
A detailed description of how the mining process takes places
The operation involves obfuscated JS wrapper code, obfuscated JS miner launcher, and an XORed .wasm module. The miner configuration is hard-coded inside the JavaScript body. The JS wrapper communicates via an encrypted XOR masked WebSocket with the mining pool.
To ensure your company's safety from crypto miners and other harmful software, a layered security strategy is needed. A key part of this strategy is using malware analysis sandboxes.
ANY.RUN provides an easy-to-use cloud environment for checking files and URLs. It gives you access to various tools for threat investigation and can automatically spot malicious activity.
ANY.RUN also lets you work with malware in an isolated virtual machine, just like on your own computer, to do complex actions needed for analyzing certain malware types.