Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Interlock is a relatively recent entrant into the ransomware landscape. First identified in 2023, it's a multi-functional malware strain used in ransomware-as-a-service (RaaS) operations.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
1 October, 2023
First seen
:
|
15 December, 2025
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 October, 2023
First seen
:
|
15 December, 2025
Last seen
:
|

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
Interlock is a modular ransomware tool that enables hackers to lock and encrypt files, exfiltrate data, and demand ransoms in double extortion schemes. It targets both Windows and Linux systems, with 64-bit executables (Windows PE and Linux ELF formats).
Interlock gained attention for its stealth and customizability, starting from targeting small and midsize enterprises with limited cybersecurity maturity and proceeding to industry leaders for really big ransoms. Healthcare organizations are another common victim of Interlock.
Discover detailed investigation into Interlock attacks on U.S. hospitals and healthcare providers.
Like many modern malware strains, Interlock leverages common but effective attack vectors. Adversaries send malicious attachments or links in well-crafted spear phishing messages, sometimes including QR codes or cloud-sharing links to bypass email filters. They exploit vulnerabilities, purchase credentials from initial access brokers and employ malvertising — drive-by downloads from fake ads or compromised legitimate websites.
Upon a successful infiltration, Interlock exploits active directory misconfigurations and uses PowerShell, WMI, and RDP for lateral movement within the network. Having established itself in the system, it dumps credentials from memory, exfiltrates data before encryption (double extortion), encrypts data with strong algorithms (often AES or ChaCha20) and greets the victim with a customized ransom note. Optionally, Interlock can recruit keyloggers, browser data collectors, and screenshot capturing.
The malware affects both Windows and Linux environments, with binaries tailored for each, indicating broad compatibility and intent to hit diverse infrastructures. It may use scheduled tasks or registry modifications to maintain access, ensuring it can resume operations after a reboot.
Interlock poses significant risks due to its:
Interlock is notable for deploying a rare FreeBSD encryptor, aiming at critical infrastructure servers (e.g., web hosting, mail servers). While specific FreeBSD attacks are not yet detailed, this capability suggests potential for broader disruption in future incidents.
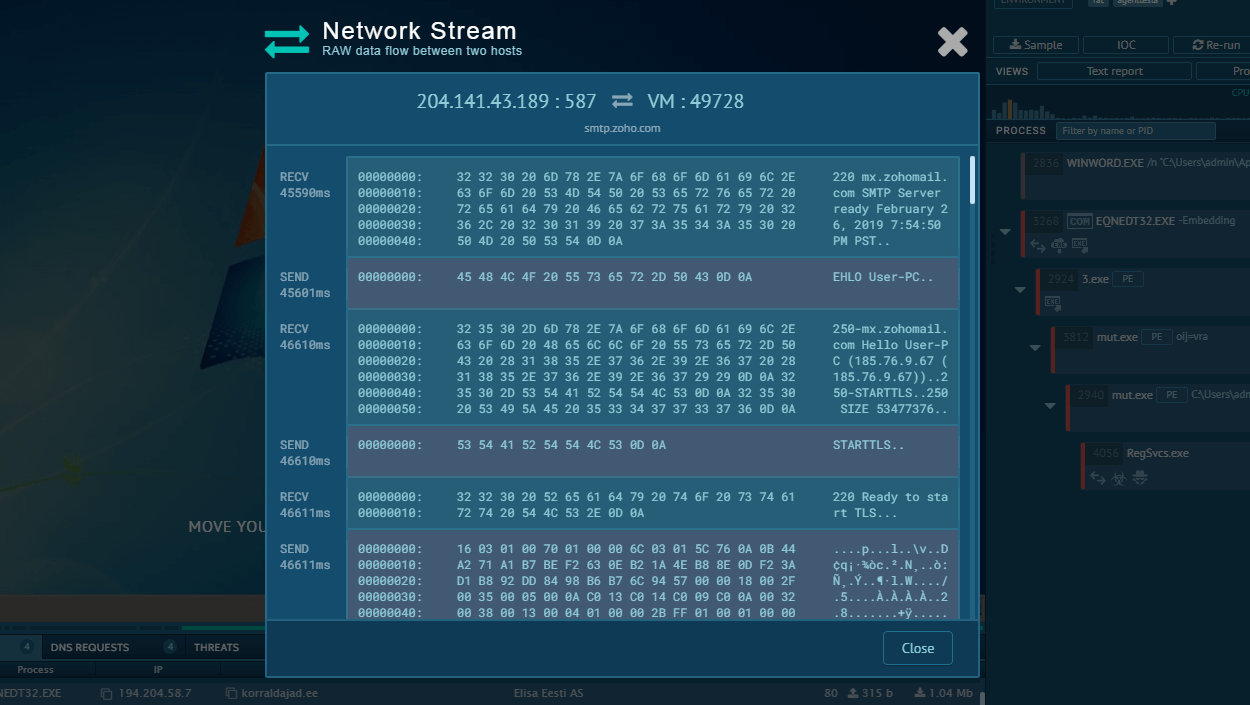
To watch Interlock enforce its varying attack scenarios, search for this malware via ANY.RUN’s Threat Intelligence Lookup and explore the analyses of its samples publicly submitted in the Interactive Sandbox.
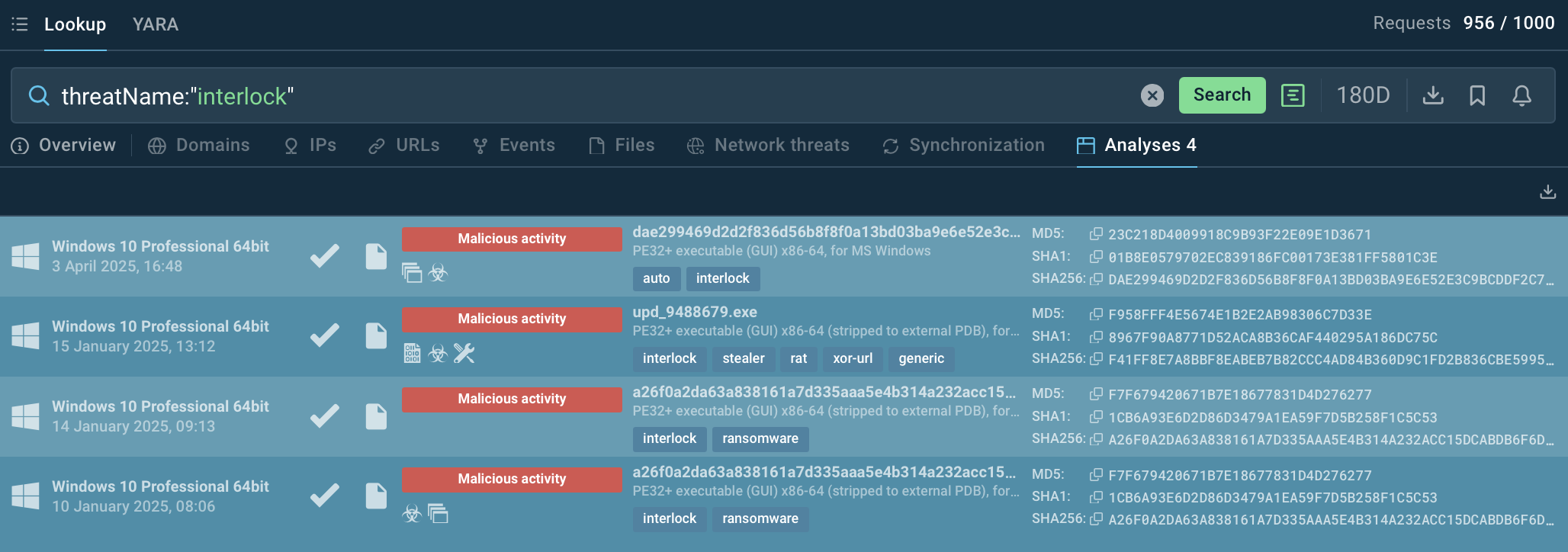 Interlock ransomware analyses in ANY.RUN's Interactive Sandbox
Interlock ransomware analyses in ANY.RUN's Interactive Sandbox
Let’s watch one of the analysis sessions closer
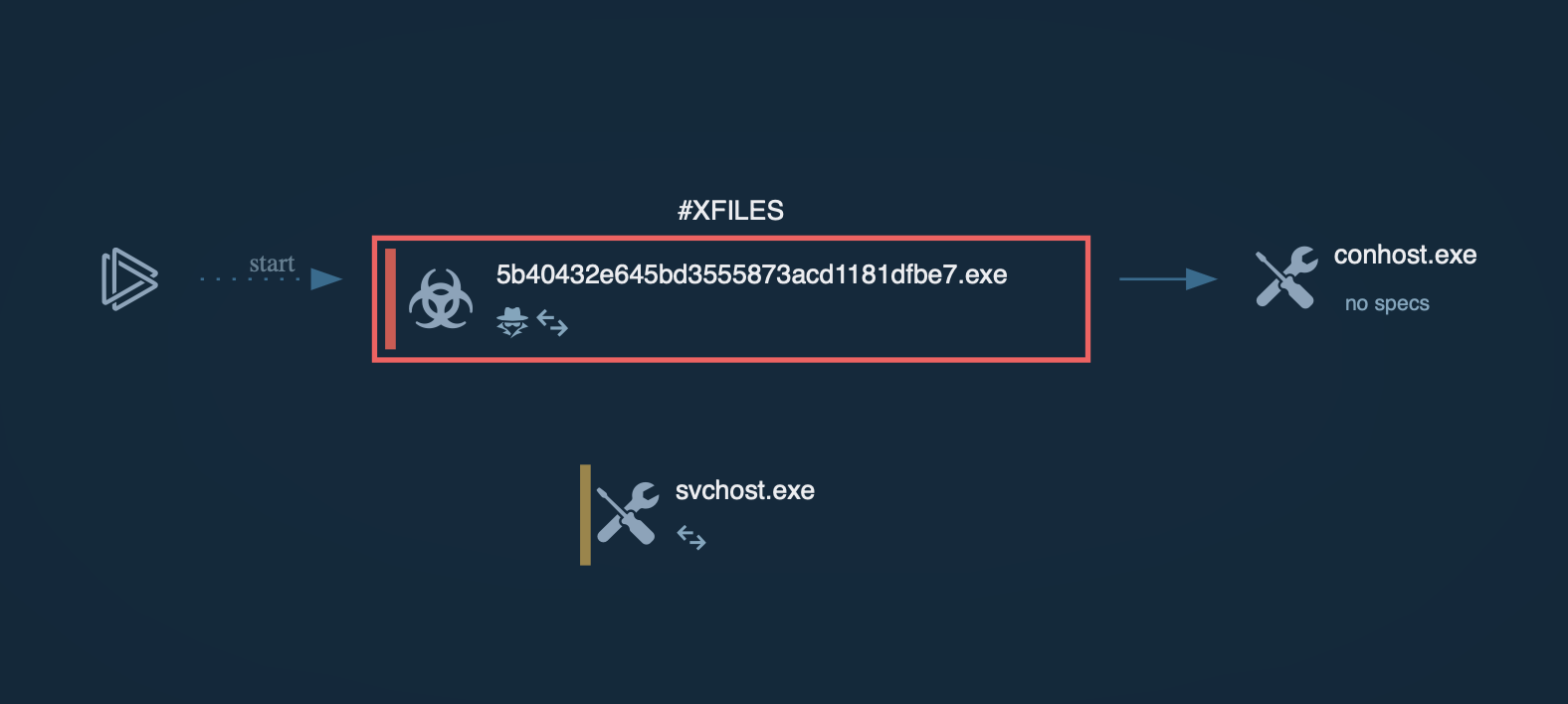
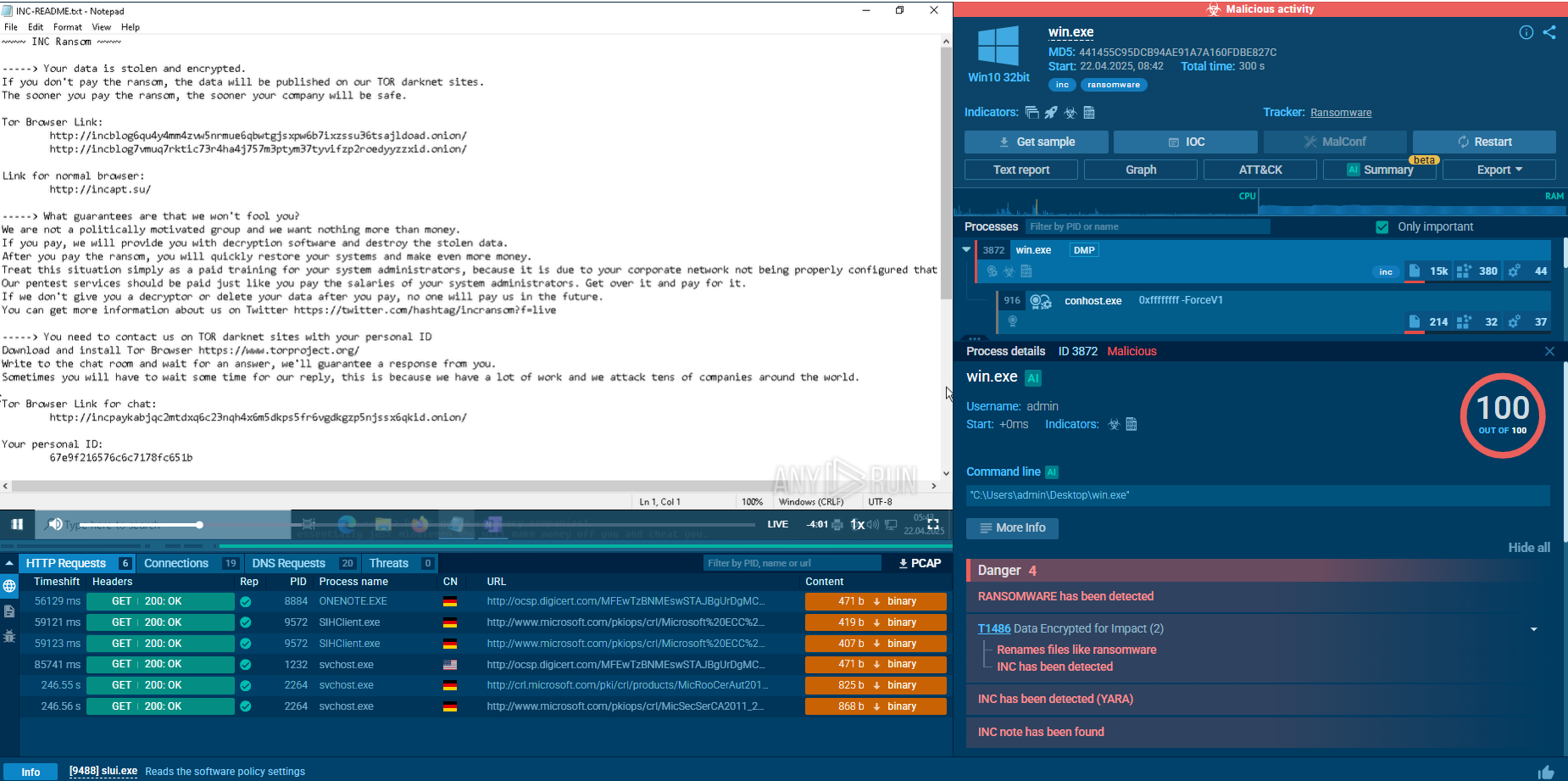
The execution chain of Interlock ransomware unfolds in several stages, employing both deception and sophisticated tools to compromise and extort victims. It typically begins with a drive-by compromise, where users are tricked into visiting phishing websites that appear legitimate. These sites offer fake updates or tools, which, once downloaded, infect the user’s device with malware. For example, malicious software might be disguised as a legitimate update for a popular application such as Chrome or Microsoft Edge. In one observed instance, the executable file was named upd_9488679.exe, where upd is short for “update,” although it can also appear under names like Update or ChromeSetup.
Once inside the system, attackers may deploy malicious payloads or execute harmful commands to take full control of the victim’s network. Prior to encryption, they often exfiltrate sensitive data as part of a double extortion strategy, threatening not only to encrypt the data but also to release the stolen information publicly if the ransom is not paid.
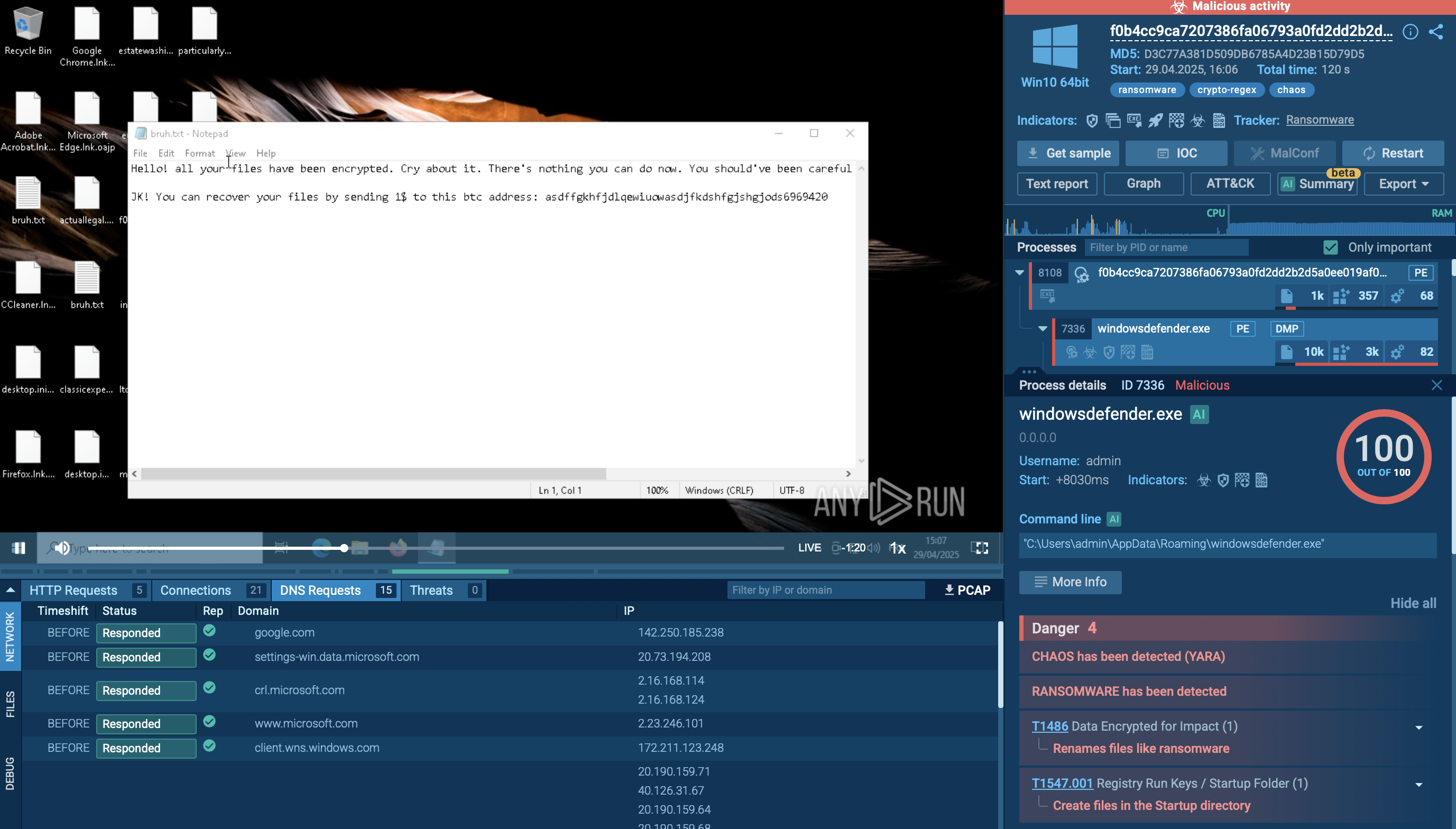
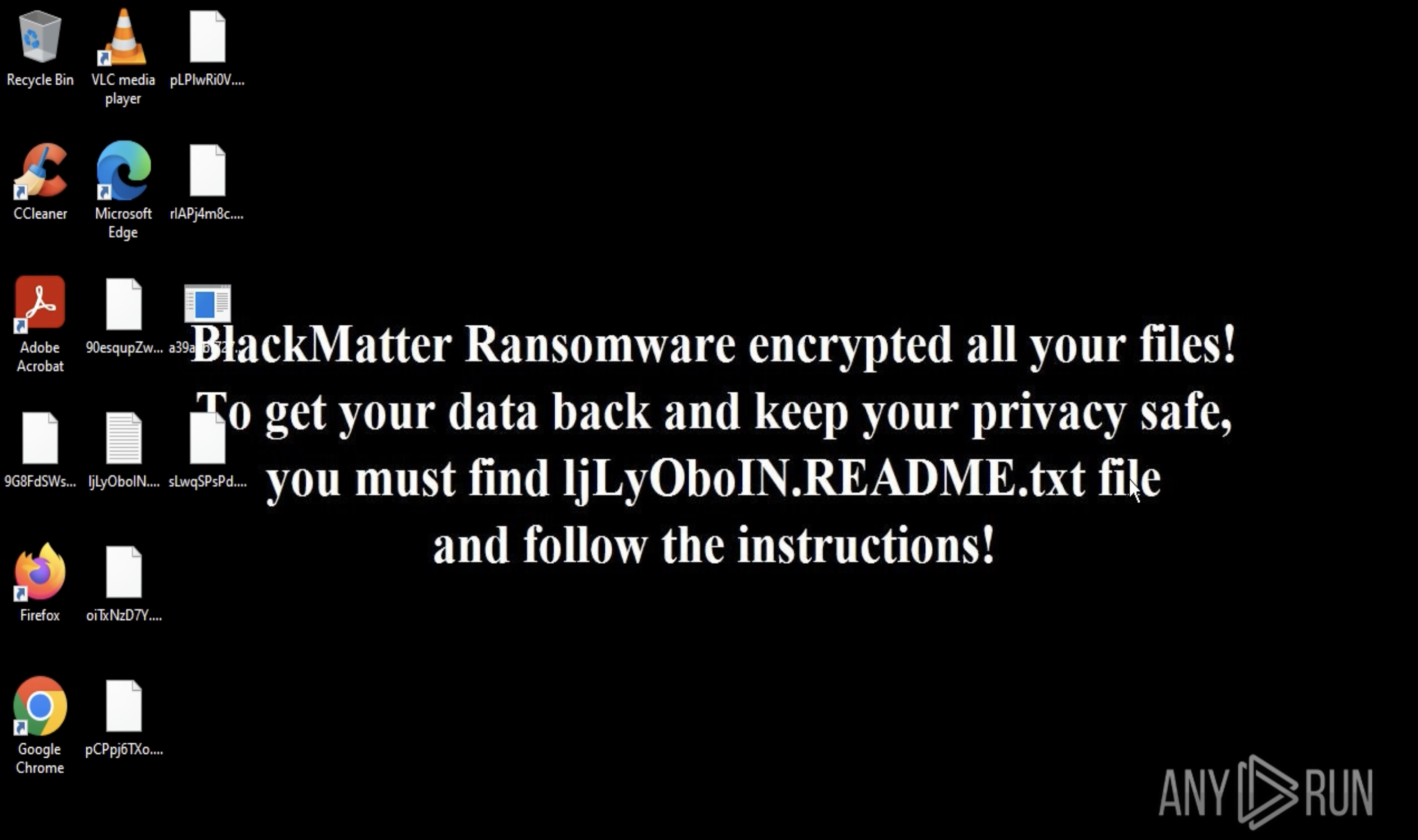
Next, the Interlock ransomware encryptor is deployed, appending the .interlock extension to files and dropping a ransom note titled !README!.txt in affected directories. This note typically provides instructions on how to contact the attackers and pay the ransom. The reliance on double extortion further pressures victims, who risk losing both access to their data and control over the disclosure of sensitive information.
Following its main functions, the ransomware may erase Windows event logs to conceal evidence of its activities. It can also delete its own binary after encryption, further complicating forensic analysis and recovery efforts.
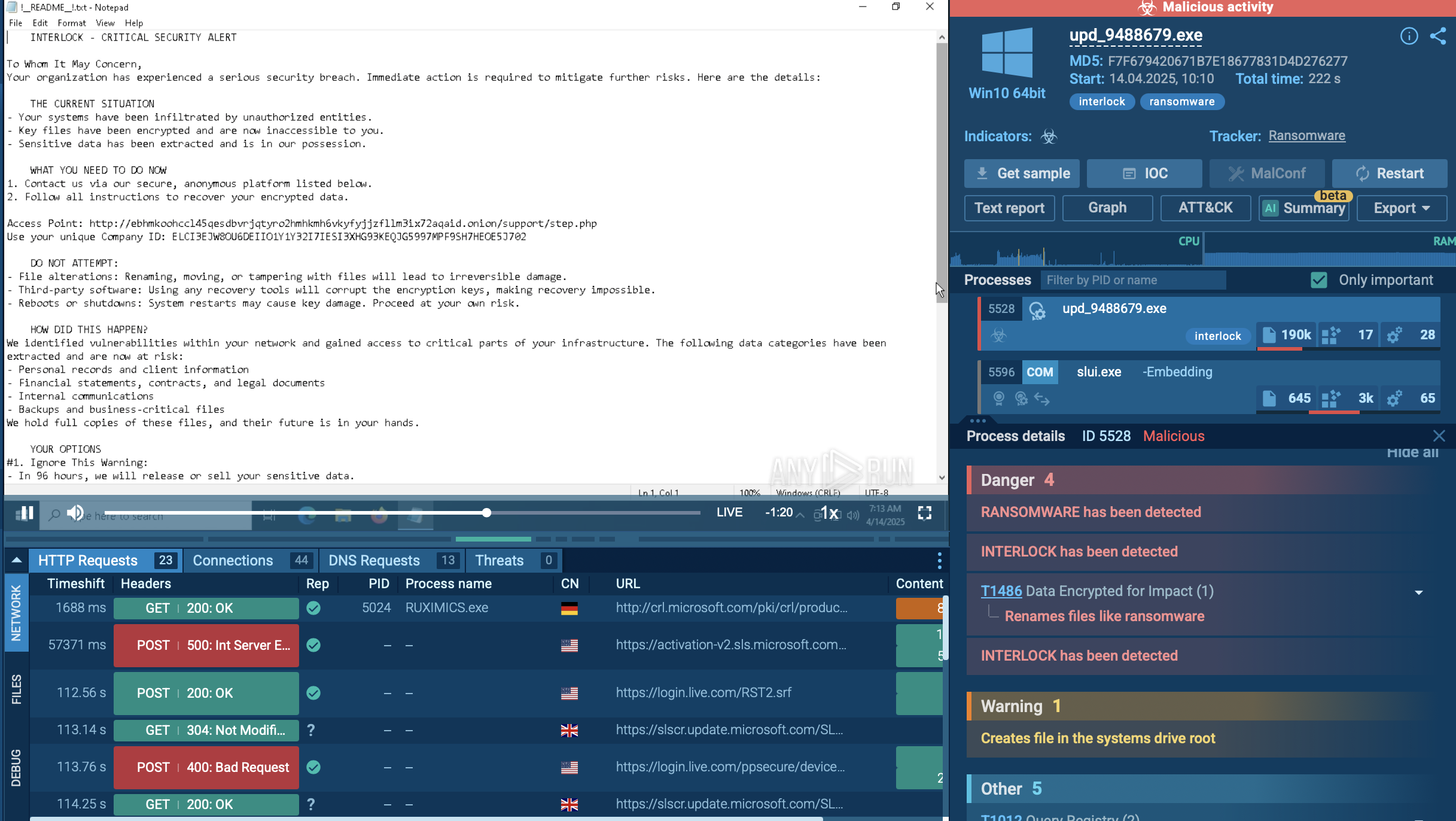 A sample of Interlock detonated inside ANY.RUN's Interactive Sandbox
A sample of Interlock detonated inside ANY.RUN's Interactive Sandbox
Integrating threat intelligence into security operations is much more efficient than paying huge ransoms to Interlock operators or dealing with devastating aftermath of data loss and leaks. Focus on TTPs (tactics, techniques, procedures) shared by TI reports, such as phishing, scheduled tasks to anticipate attack vectors.
Leverage ANY.RUN’s Threat Intelligence Lookup to hunt for IOCs specific to Interlock, like domains, IPs, or file hashes.
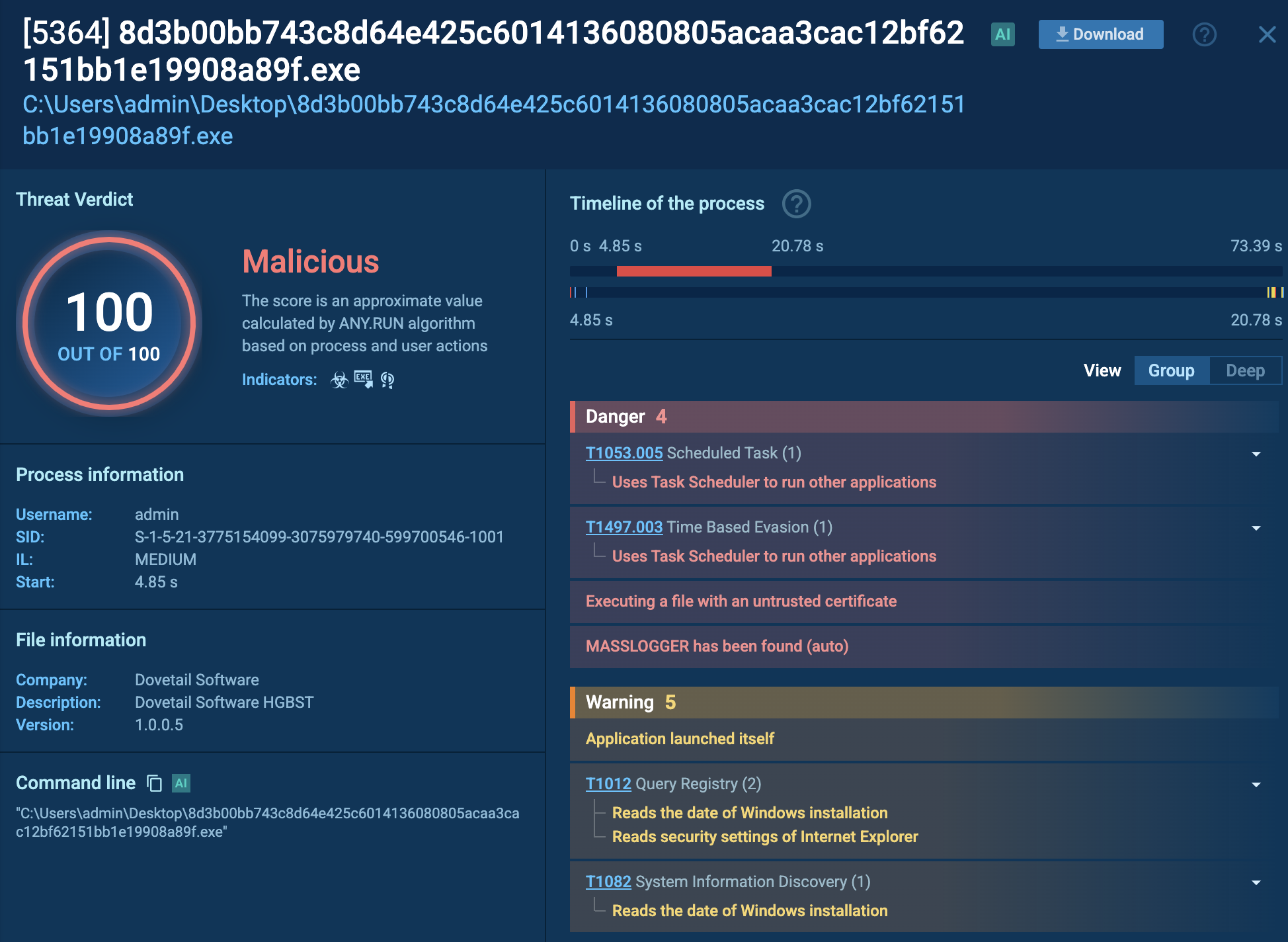
Each analysis session in the Sandbox contains a number of IOCs. Use them as search requests to TI Lookup for further exploring the threat and gathering data for monitoring and detection.
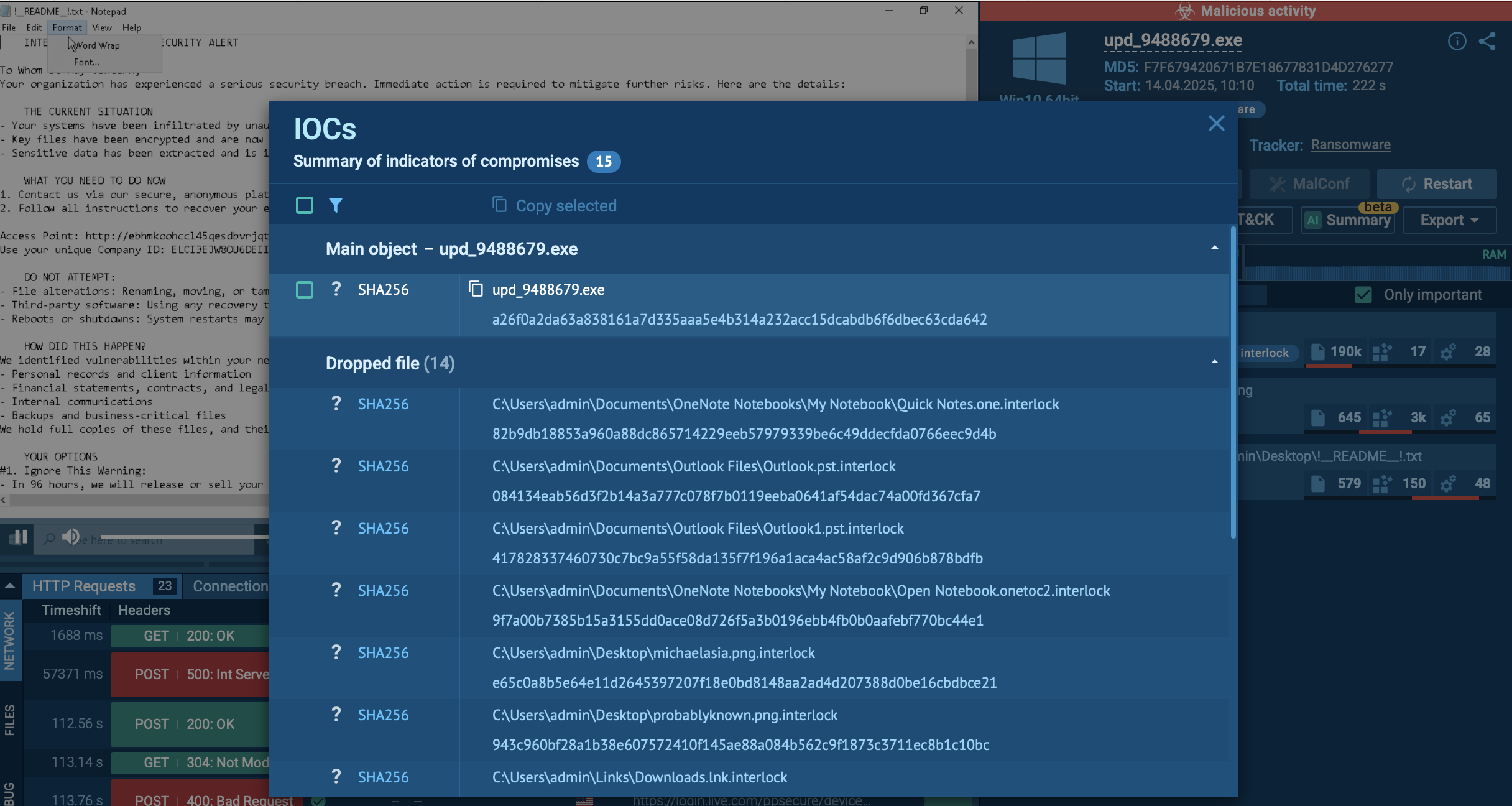 Files found in an Interlock sample during Sandbox analysis
Files found in an Interlock sample during Sandbox analysis
Interlock is a young ransomware market player yet already notorious for its big ransom appetites, opportunistic targeting across various sectors, and sophisticated tactics to infiltrate systems, exfiltrate data, and disrupt operations. The group's activities have had significant impacts on the affected organizations, leading to operational downtime, data breaches, and potential financial losses.
To avoid becoming the next victim, reinforce your proactive cybersecurity efforts with actionable data brough to you by threat intelligence.
Start with 50 requests in TI Lookup to collect IOCs on Interlock and be ready to detect and respond