Embedding malicious payloads in QR codes is a phishing strategy increasingly exploited in recent campaigns. Automated defenses often struggle to decode and conduct QR code analysis, allowing adversaries to leverage these vectors effectively.
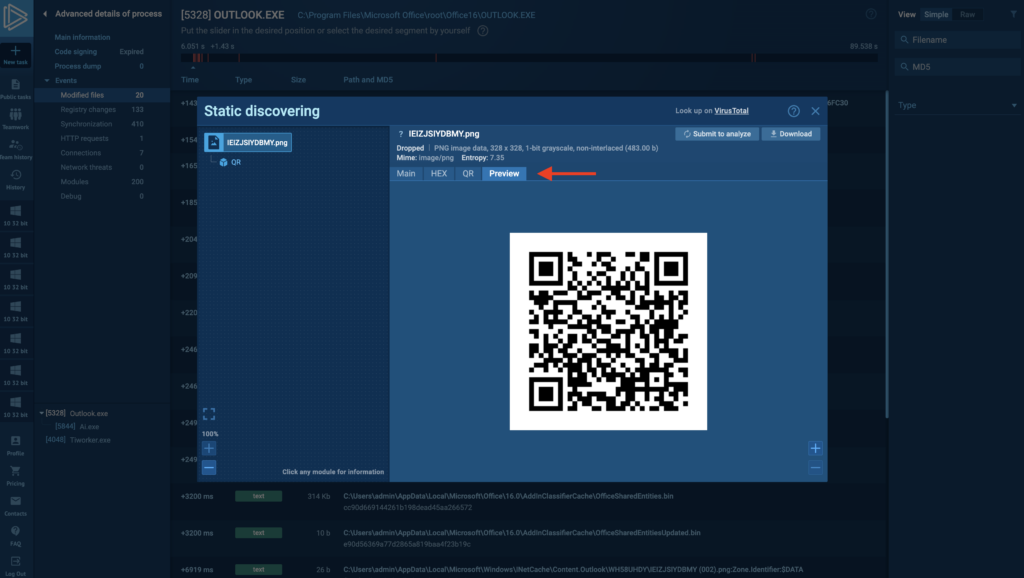
Our sandbox is now equipped with an automated QR code analyzer.
ANY.RUN has updated its sandbox to easily detect and analyze malicious content in QR codes within images.
Now, when the sandbox identifies a QR code containing a link.
- The image with the QR code is placed on the desktop of the virtual machine, where you can find it for further analysis later. The QR code is also accessible in Static discovering.
- When you submit a QR code for analysis, the sandbox launches a browser and navigates to the URL encoded in the QR code, opening it in a new tab.
Importantly, this feature will also function if the embedded link within the QR code is in plain text form.
The importance of QR code detection
Distributing QR code malware is a phishing method known as “quishing.” Since early September, we’ve seen a surge in phishing emails using this technique, with incidents climbing to over 500 emails on Fridays in the first weeks of October.
Read how this phishing campaign delivers malware in QR codes.
Not only can security software struggle to detect malicious QR codes, but users often don’t link them with potential threats. Most information about the dangerous of phishing emails that you can find only typically focuses on executables and macros.
QR codes, on the other hand, are usually seen as tools for marketing, which helps quishing tactics to slip under the radar. This underscores the need for an efficient analysis tool that covers quishing.
Previously, to analyze QR code in ANY.RUN required saving the image and using an external QR scanner like qrcoderaptor[.]com to extract the URL during the task.
This workaround, while not overly complex, still demanded extra time. Considering the increasing use of quishing to deliver malware, it was crucial for us to streamline the process for users. Now, you no longer need to extract link from QR code manually, as it is now done automatically.
Detection of malicious payloads in QR codes in action
Let’s see how QR code detection works in the sandbox using this task as an example.
To submit a URL from a malicious QR code, follow these steps: after completing your current task, go to Static discovering and select the object containing the QR code (in our example, an email with attached images).
Next, click Submit to analyze, and a new task will launch. The URL recognized in the new task will then automatically open in a web browser. Thus, you will be able to safely study the website, determine its risk level, and avoid introducing a QR code virus to your system.
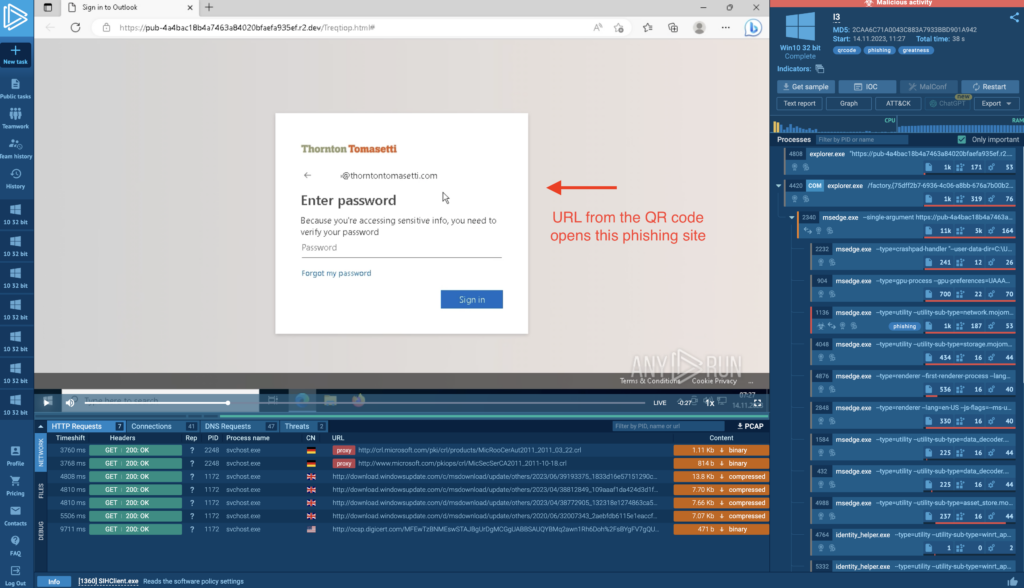
Here is another example with a PDF file, where QR code contains a URL to a phishing site.
Wrapping up
Given that attackers are definitely not running out of QR codes any time soon, it is important for organizations to be prepared for quishing attacks. Conducting a quick QRcode test in ANY.RUN will help you safely determine if a suspicious QR you encounter poses any risk.
What are your thoughts on this new feature? Have you had a chance to extract URL from QR code in ANY.RUN? Share your experience in the comments below.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.








0 comments