Several sophisticated phishing campaigns are currently spreading fast that pose challenges for detection.
Crooks are increasingly using captchas and QR codes to mask malicious content. The goal is adding another step, which requires human interaction — instead of directly embedding or linking to a payload or using elements that bypass email spam filters, as is the case with “quishing”.
As of this writing, you can easily find examples of these campaigns on ANY. RUN’s public submissions database. We’re observing more than 2,000 phishing attempts each week, with activity spiking as we approach Friday. Here’s the data for the week of September 30 to October 6:
Number of public submissions with phishing tag:
| Number of tasks | Day of the week |
|---|---|
| 572 | Friday, 10.06 |
| 438 | Thursday, 10.05 |
| 400 | Wednesday, 10.04 |
| 310 | Tuesday, 10.03 |
| 189 | Monday, 10.02 |
| 22 | Sunday, 10.01 |
| 88 | Saturday, 09.30 |
In this article, we’ll examine three new phishing techniques: captchas, QR codes, and emails that link to password-protected payloads hosted on file-sharing services, with the password provided in the email body itself.
A phishing campaign uses captchas to stall analysis
Hackers are increasingly using legitimate tools to make their campaigns appear more credible. But now, they’ve taken it a step further by using actual security solutions in their attacks.
The attack — which begins like a standard credential harvesting attempt and targets O365 credentials — uses a spam email as an initial vector. Hackers lure the user into logging into what appears to be legitimate software.
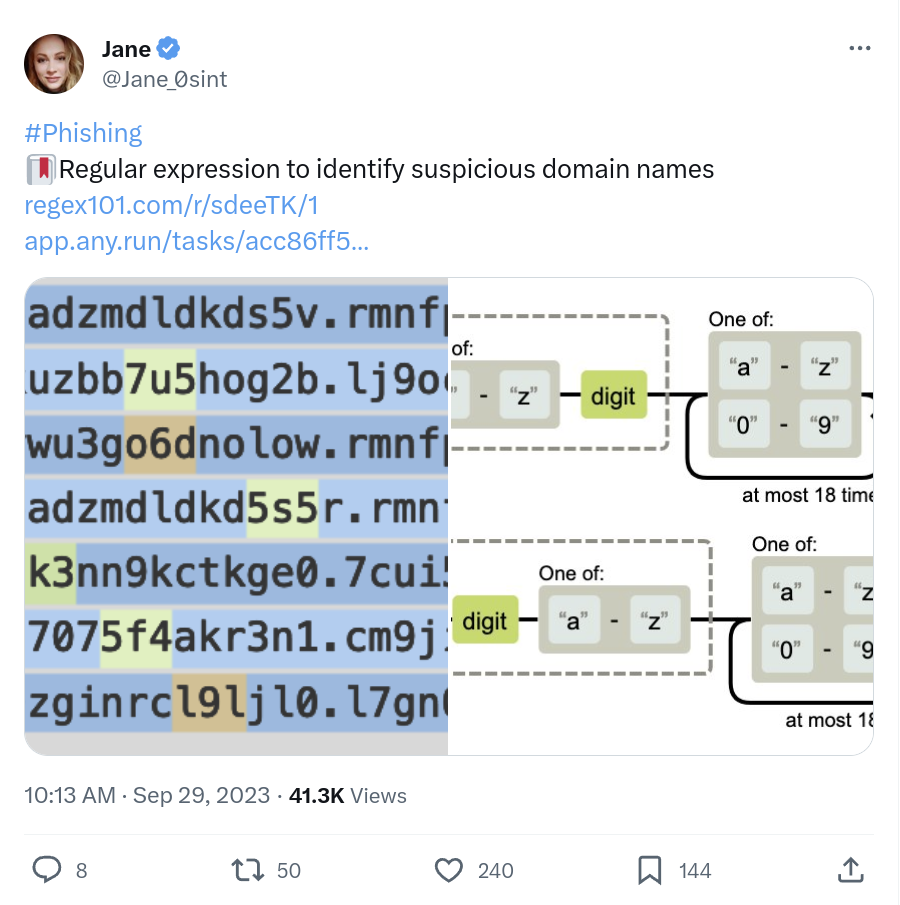
The attackers use the Cyber Panel—an open-source web development panel—to create hundreds of cryptic domain names daily using a Randomized Domain Generated Algorithm (RDGA). These domains host credential-harvesting pages. Because the domains are highly randomized, hosting providers find it challenging to locate and shut them down.
ANY.RUN’s security researcher @Jane_0sint has written a RegEx rule to identify these domains:
The credential harvesting forms are concealed behind CloudFlare’s Turnstile service:
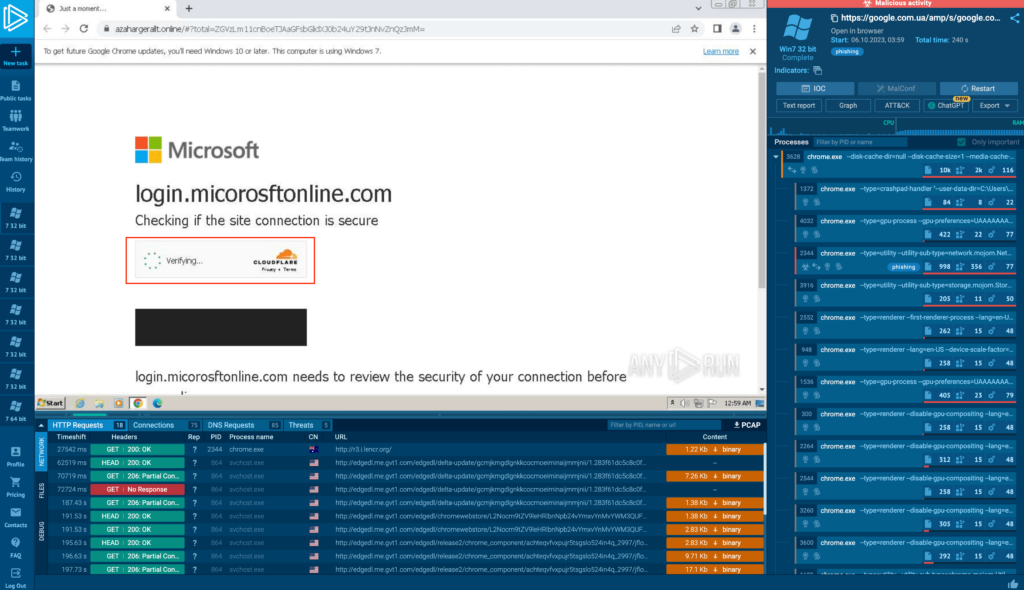
By putting CloudFlare’s legitimate captcha in front of malicious content, the attackers are essentially pitting one security system against another — that’s because automated security solutions, like web crawlers designed for threat detection, get stopped by the captcha. As a result, the content evades being flagged as malicious, and emails with links to this page slip through spam filters. Attacks involving CAPTCHA target individual users, using the challenge as a way to ensure that actual victims rather than bots are interacting with the malicious content. It’s worth noting that attackers do not use CAPTCHA codes in this campaign.
But this attack is more than just one of CAPTCHA scams.
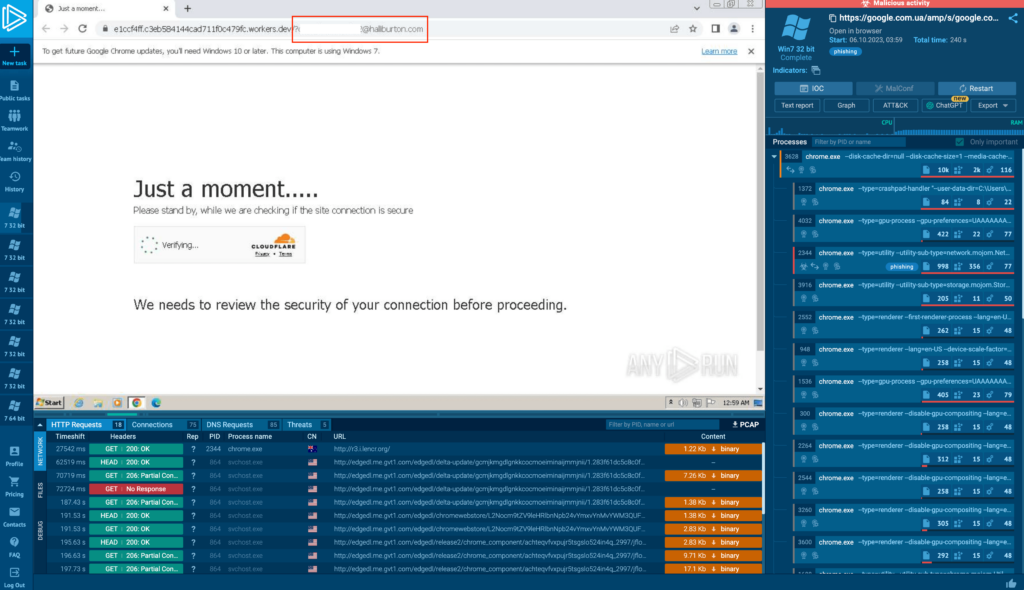
Attackers append the victim’s email address as a GET parameter after the target completes the captcha. They then execute a script to extract the domain name of the target’s organization, using this data to display a custom login page that mimics the victim’s actual login portal.
In this example, the targeted organization is Halliburton Corporation.
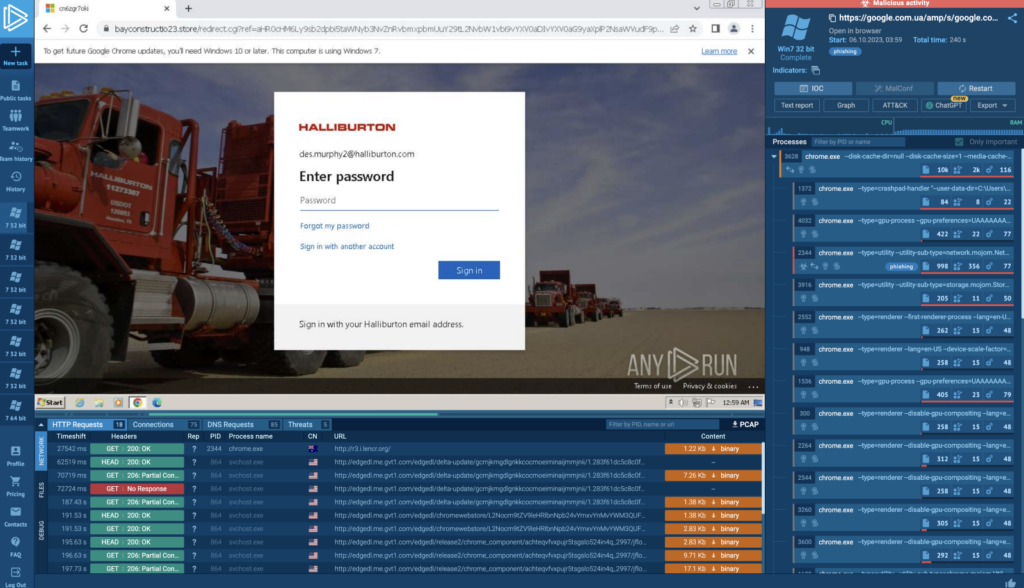
The target, who likely sees this interface almost daily, has few cues to raise suspicion, making it very difficult to realize that they are being scammed.
The realistic Office 365 private login page is provided by Dadsec. This is part of their Phishing as a Service (PhaaS) platform, and it has been distributed through Telegram since January 2023.
After the victim lands on the login page, the remainder of the attack follows a standard credential harvesting pattern. Once the victim enters their login credentials, a “wrong credentials” error message is displayed. The attackers then quickly redirect the victim to a legitimate website, while exfiltrating the credentials to their Command-and-Control server.
This poses challenges for investigation as well, given that not all automated sandboxes can bypass a captcha. This is where the interactivity in ANY.RUN becomes valuable — you can manually complete the captcha within the Virtual Machine view and see the most interesting aspects of the attack.
Quishing, a variation of phishing, uses QR codes to evade detection
Quishing — derived from combining words QR and phishing — is a phishing strategy that has been gaining popularity since late summer of 2023.
The quishing definition is an attack that involves criminals sending a QR code that redirects the target to a malicious website. Embedding the malicious link within a QR code helps the attacker bypass spam filters, as QR codes are generally considered safe, and many security tools lack the capability to parse their content.
Emails are often the initial point of contact in quishing campaigns. In the example below, the attackers combine the common trope of a fake payment invoice email and quishing:
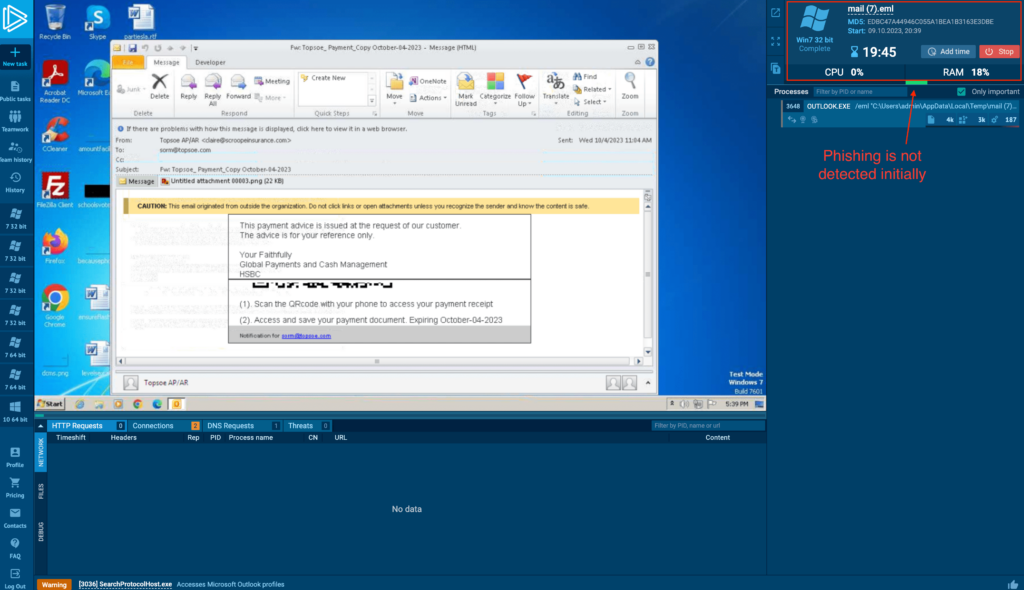
ANY.RUN currently can’t extract URLs from QR codes, so initially it misses detecting the phishing attempt, as indicated in the screenshot above. However, you can very easily save the QR code and upload it to a third-party QR scanning service to extract the URL:
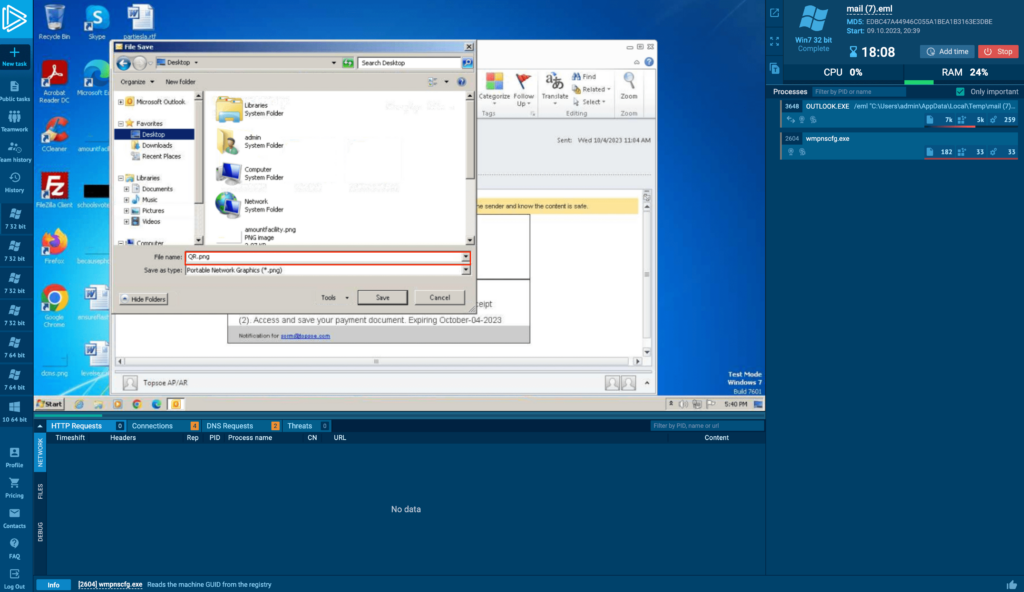
We used qrcoderaptor[.]com to pull the URL:
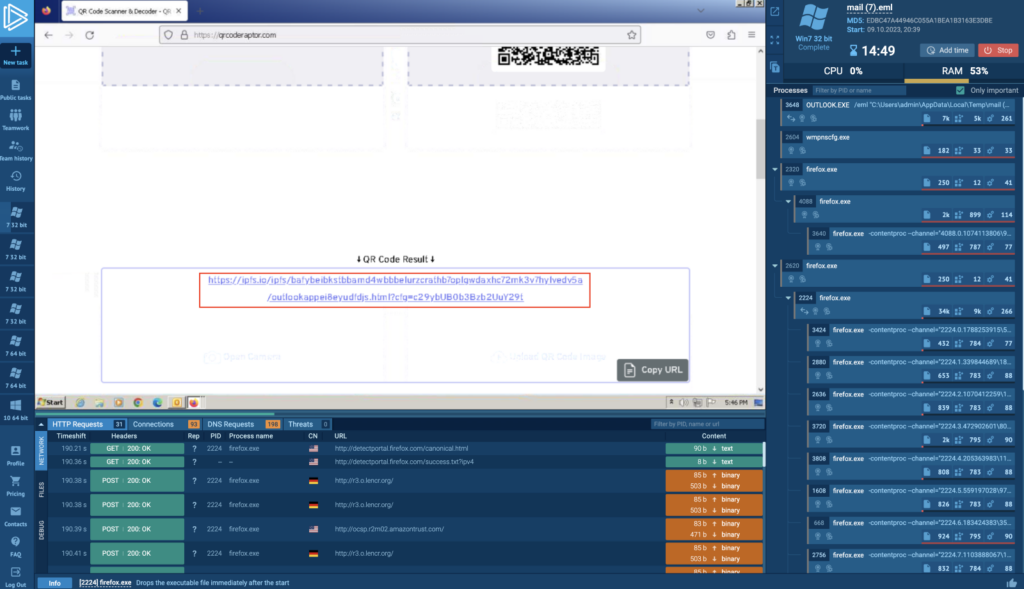
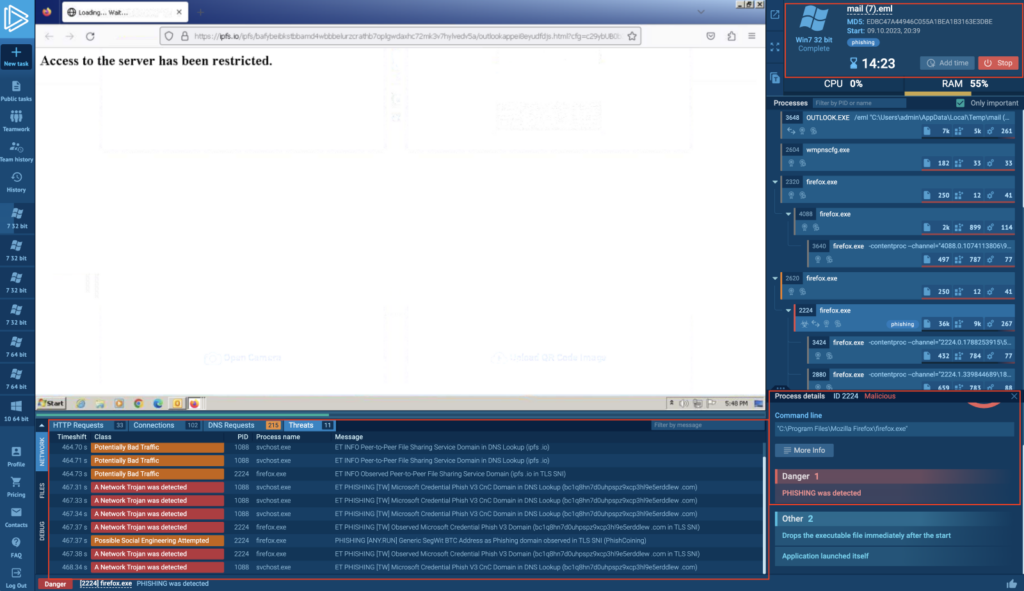
After following the link sandboxing confirms malicious intent and phishing is detected:
Another phishing campaign bypasses detection with a combo of evasion techniques
In another campaign we recently observed, threat actors combine well-known phishing methods in a clever way to sidestep detection from automated sandboxes.
This attack kicks off with a phishing email disguised as a judicial court notification from the Republic of Colombia. Attached to the email is what appears to be a PDF, but is in fact an image designed to mimic a file:
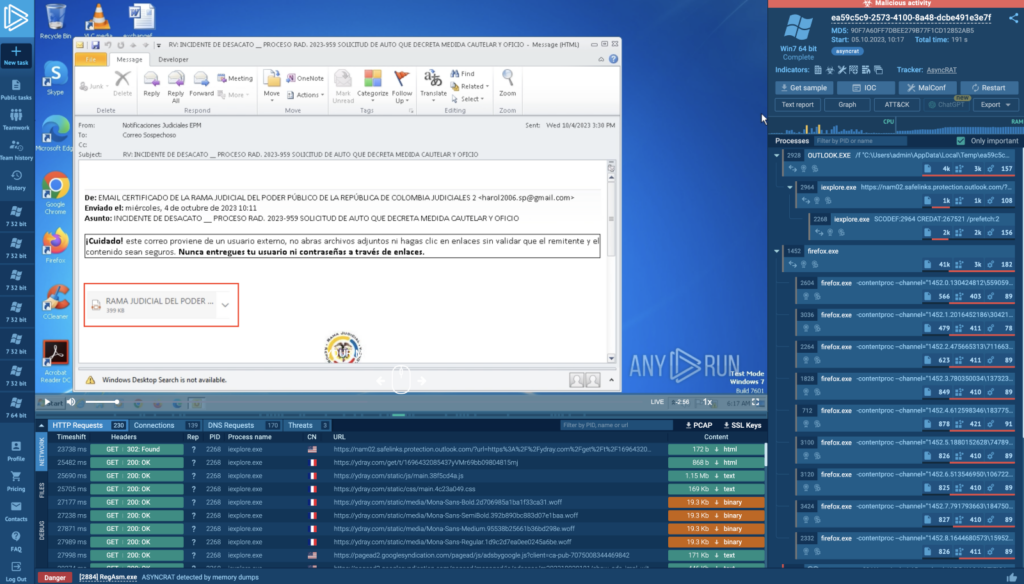
When clicked, the image redirects the user to a file hosted online:
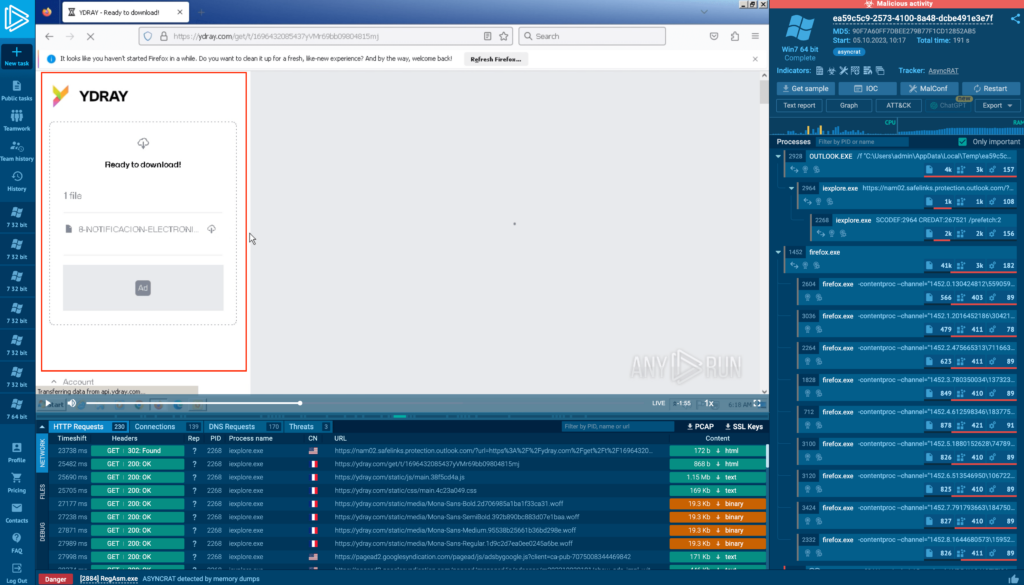
The file is encrypted, and password-protected. The password for this archive is provided in the body of the email.
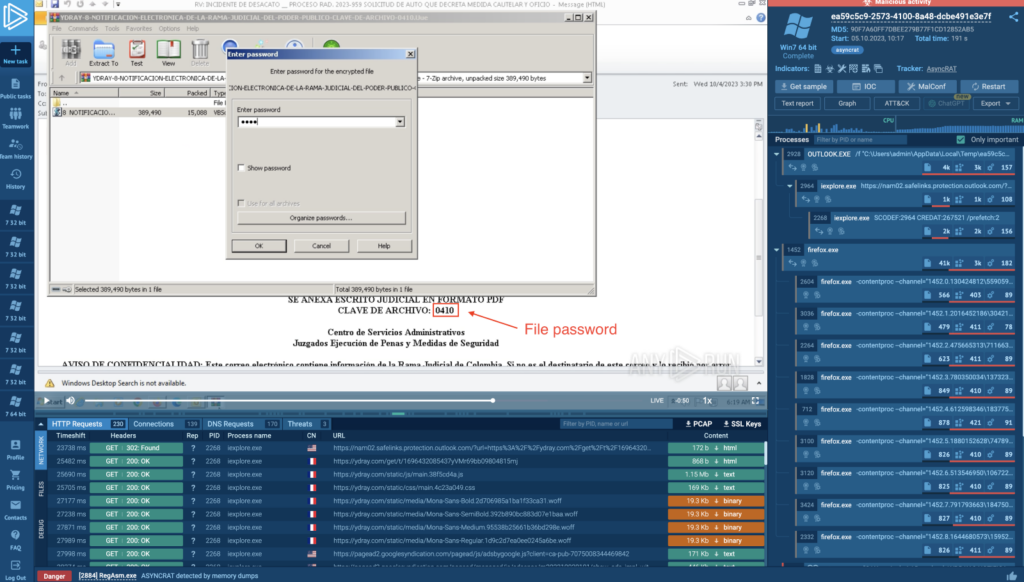
Using images as fake attachments is a tactic that’s been around, probably, since the mid-2010s, and delivering payloads in password protected archives is an even older trick. However, combining them together like this is a powerful way to evade automated analysis.
A security orchestration platform would need to recognize the clickable image, download the file from a hosting service, locate the password within the email, and then decrypt the archive using that password. This scenario is easy for a human, but tough to replicate reliably with automation.
How to detect these phishing campaigns: our recommendations
These three examples underscore that attackers don’t always need groundbreaking techniques to run impactful campaigns. By smartly combining existing tools, they achieve a high impact with minimal effort.
It seems the attackers are exploiting the limitations of automated security systems, particularly those lacking dynamic analysis capabilities. We recommend incorporating a malware sandbox into your security workflow for dynamic analysis, allowing you to safely engage with and scrutinize the malicious content.
For ANY.RUN users, analyzing these campaigns is simplified, since they get direct, real-time access to our cloud virtual machines during task execution.
About ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.
1 comments







The problem isn’t realistic looking fake web pages or sign-ins. The problem is people still haven’t learned not to sign in on web pages they opened from links in emails.