Welcome to ANY.RUN‘s Q2 2023 malware trends analysis — our latest quarterly update on prevalent malware families, types, and TTPs.
Summary
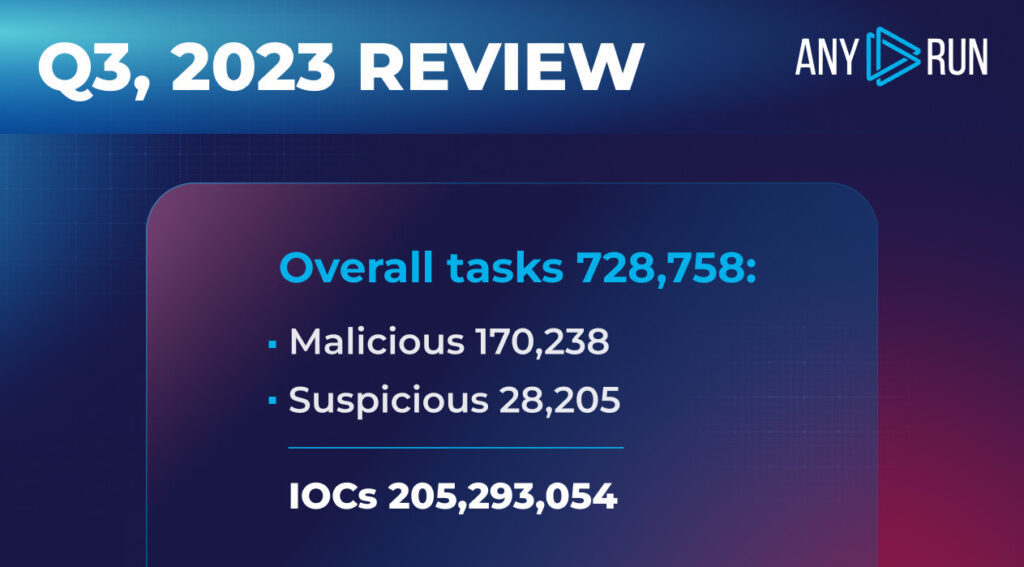
This quarterly review for Q3 2023 shows that ANY.RUN’s users processed a total of 728,758 submissions. Out of these, we identified 170,238 tasks, accounting for 23.4%, as malicious, and an additional 28,205 tasks (3.9%) as suspicious.
Compared to the previous quarter, the percentage of tasks classified as malicious has dropped slightly from 29.9% to 23.4%. Tasks marked as suspicious have decreased in percentage from 4.5% to 3.9%.
As for Indicators of Compromise (IOCs), our users collected a staggering 48,932,710 unique IOCs and a cumulative total of 205,293,054 IOCs this quarter. This shows an increase in unique IOCs from approximately 45 million last quarter.
In this report, we’ll:
- Explore which malware types and families were the most used in Q3 2023, according to ANY.RUN’s data
- Provide insights into the most used MITRE ATT&CK TTPs this quarter
Let’s get started.
Top Malware Types in Q3 2023
Let’s examine the most common malware types processed by the ANY.RUN sandbox. Given the large dataset we’re working with, this offers insight into the threats your organization is most likely to face.
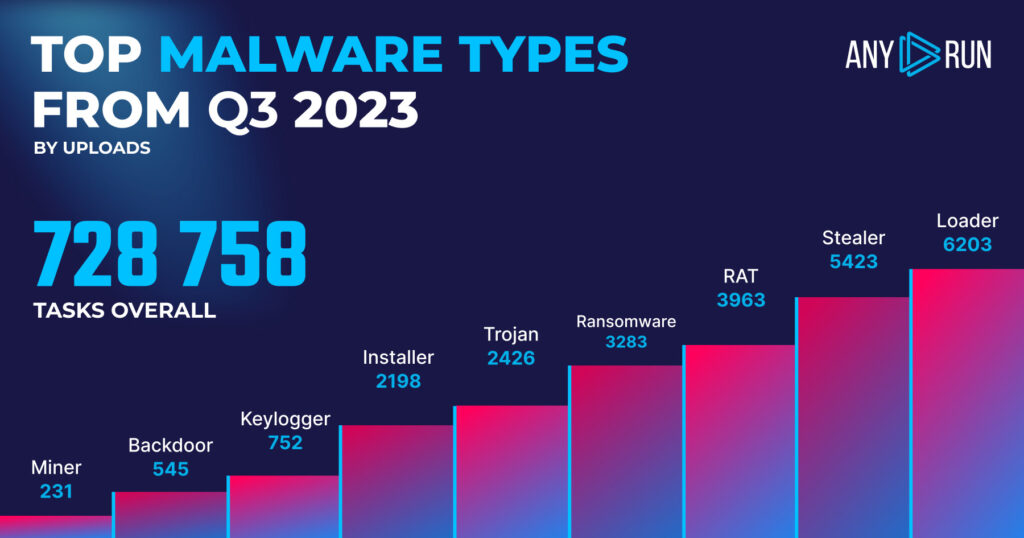
- Loader: 6203
- Stealer: 5423
- RAT: 3963
- Ransomware: 3283
- Trojan: 2426
- Installer: 2198
- Keylogger: 752
- Backdoor: 545
- Miner: 231
Highlights
In Q3 2023, the top three most uploaded types of malware were Loader, Stealer, and RAT, showing a shift in the landscape compared to Q2 2023, where RAT, Loader, and Trojan were the leaders.
Specifically, Loader instances remained high but showed a slight decrease, going from 5685 in Q2 to 6203 this quarter. That’s a 9.1% increase, which is notable but not as dramatic as some of the shifts we’ve seen. Stealer has emerged as a major player, with 5423 instances, but wasn’t a top-three contender in Q2. RAT instances decreased from 5974 in Q2 to 3963 in Q3, marking a 33.6% drop.
In a noteworthy trend, Ransomware moved to the fourth position with 3283 instances, but it’s Trojan that experienced the most dramatic decrease among the previous top three, dropping from 4246 in Q2 to 2426 this quarter, a decline of 42.9%.
Top Malware Families in Q3 2023
The leading malware families typically remain stable, but this quarter saw a shift in the top 3 rankings. Here’s the rundown:
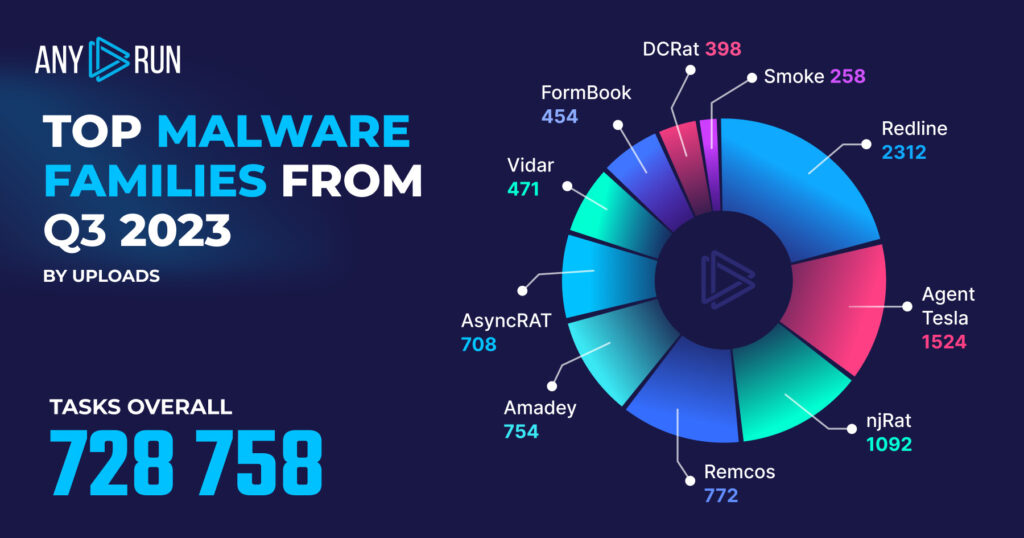
- RedLine: 2312
- AgentTesla: 1524
- NjRAT: 1092
- Remcos: 772
- Amadey: 754
- AsyncRAT: 708
- Vidar: 471
- Formbook: 454
- DCRat: 398
- Smoke Loader: 258
Highlights
In Q3 2023, the top malware families were RedLine, AgentTesla, and NjRAT. This shakes up the usual top three — Remcos held the spot for the second most common malware in the previous quarter.
- RedLine, although still the most prevalent, saw a notable drop in instances, decreasing 32.3% from 3415 in Q2 to 2312 this quarter. This reverses the previous surge we saw last quarter.
- AgentTesla catapulted into the second spot with 1542 instances, replacing Remcos, which moved down to the fourth position with 772 instances—a drop of 43.6% from 1368 in Q2.
- NjRAT remains in the top three but witnessed a minor decline in instances, decreasing from 1142 in Q2 to 1092 in Q3, a 4.4% reduction.
Top MITRE ATT&CK techniques in Q2 2023
MITRE ATT&CK is a globally recognized framework that categorizes various adversary behaviors into tactics and techniques. It serves as a vital resource for malware analysts to identify, assess, and counter threats more effectively.
In ANY.RUN, malware behaviors are automatically mapped to techniques, enabling us to compile this list:
| MITRE ATT&CK Technique | Count |
|---|---|
| T1036.005 Masquerading: Match Legitimate Name or Location | 151,442 |
| T1518.001 Software Discovery: Security Software Discovery | 108,077 |
| T1569.002 System Services: Service Execution | 30,215 |
| T1114.001 Email Collection: Local Email Collection | 27,329 |
| T1497.003 Virtualization/Sandbox Evasion: Time-Based Evasion | 22,407 |
| T1053.005 Scheduled Task/Job: Scheduled Task | 20,291 |
| T1059.003 Command and Scripting Interpreter: Windows Command Shell | 17,788 |
| T1218.011 Signed Binary Proxy Execution: Rundll32 | 17,764 |
| T1562.001 Impair Defenses: Disable or Modify Tools | 12,948 |
| T1204.002 User Execution: Malicious File | 9,186 |
| T1059.001 Command and Scripting Interpreter: PowerShell | 7,715 |
| T1547.001 Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | 5,612 |
| T1059.005 Command and Scripting Interpreter: Visual Basic | 4,871 |
| T1574.002 Hijack Execution Flow: DLL Side-Loading | 4,126 |
| T1222.001 File and Directory Permissions: Linux and Mac File and Directory Permissions Modification | 3,364 |
| T1059.007 Command and Scripting Interpreter: JavaScript/JScript | 2,410 |
| T1564.001 Hidden Files and Directories: Hidden Files and Directories | 2,352 |
| T1562.006 Impair Defenses: Disable or Modify Tools | 1,890 |
| T1546.015 Event Triggered Execution: Accessibility Features | 1,868 |
| T1564.003 Hidden Files and Directories: Hidden Users | 1,766 |
Highlights
- T1036.005, Masquerading: Match Legitimate Name or Location, made a significant return to the top spot with 151,442 instances. This is notable since it was absent from the top ten in Q2.
- T1518.001, Software Discovery: Security Software Discovery, entered the list as the second most prevalent technique with 108,077 instances, marking its first appearance in the top ranks.
- T1569.002, System Services: Service Execution, also a new entry, takes the third spot with 30,215 instances.
- T1059.003, Command and Scripting Interpreter: Windows Command Shell, although it increased to 17,788 instances, moved down from the most prevalent in Q2 to a lower rank in Q3.
- T1059.001, Command and Scripting Interpreter: PowerShell, the second most prevalent technique in Q2, is notably missing from the top ten this quarter.
Report methodology
We’ve analyzed data from 728,758 tasks submitted to our public threat database. This data comes from a wide range of researchers who have chosen to make their findings public.
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.








0 comments