Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases

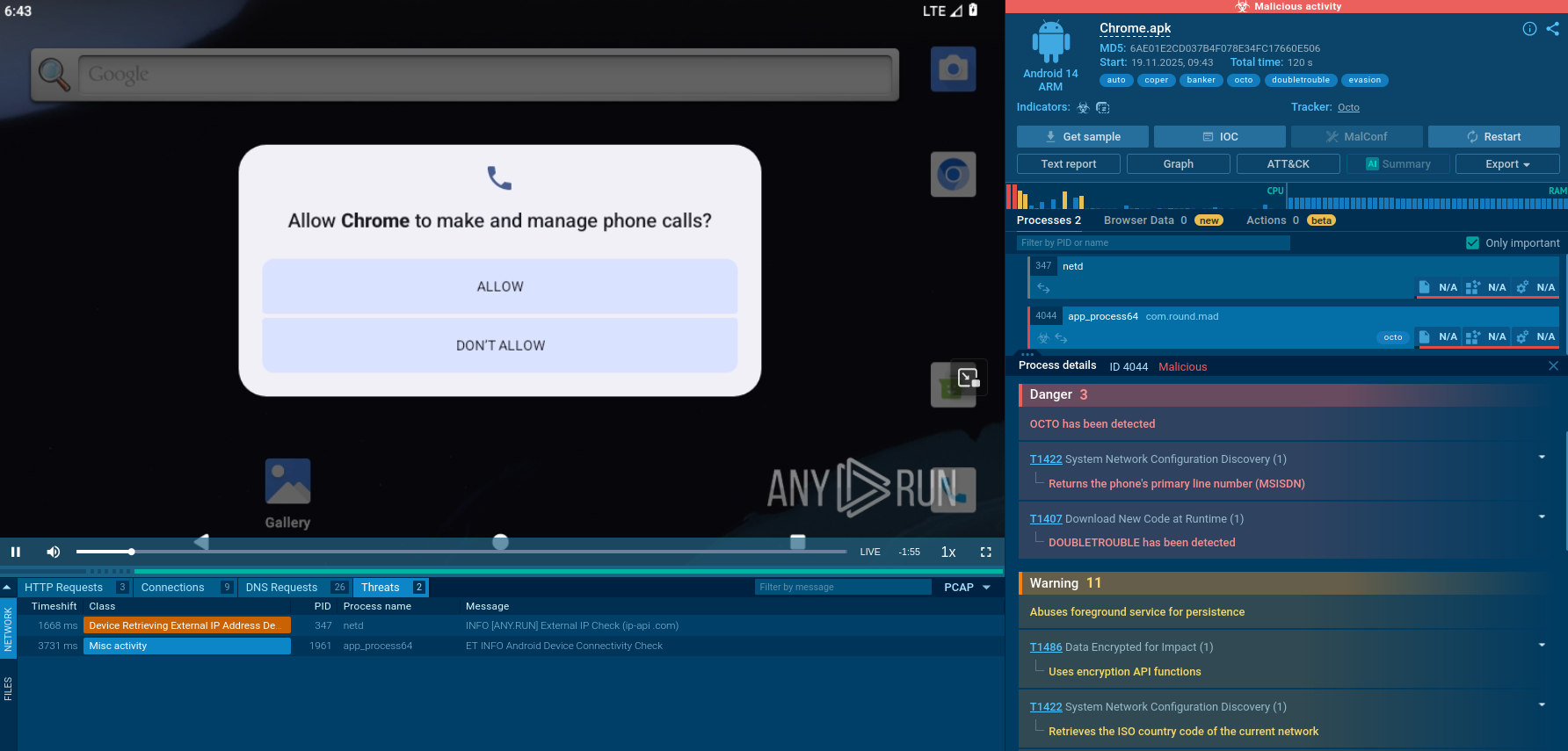
njRAT is a remote access trojan. It is one of the most widely accessible RATs on the market that features an abundance of educational information. Interested attackers can even find tutorials on YouTube. This allows it to become one of the most popular RATs in the world.
|
Trojan
Type
:
|
Middle East
Origin
:
|
|
1 January, 2013
First seen
:
|
8 February, 2026
Last seen
:
|
|
Type
:
|
Middle East
Origin
:
|
|
1 January, 2013
First seen
:
|
8 February, 2026
Last seen
:
|

 454
454
 0
0

 2374
2374
 0
0

 4589
4589
 0
0
njRAT, also called Bladabindi and Njw0rm is a remote access trojan that is used to remotely control infected machines. Because of its availability, excess of online tutorials, plenty of information, and a robust core feature set along with several implemented evading techniques made njRAT one of the most widely used RATs in the world.
This malware was detected for the first time in 2013, however, some related RATs have been observed by researchers in 2012. The highest surge of njRAT trojan attacks was recorded in 2014 in the middle east, which is the most targeted region for this malware.
In Q2 2024, it became the third most widespread malware according to ANY.RUN's report.
njRAT trojan is built on the .NET framework. This RAT gives hackers the ability to control the victim’s PC remotely. njRAT allows attackers to activate the webcam, log keystrokes, and steal passwords from web browsers as well as multiple desktop apps.
In addition, the malware gives hackers access to the command line on the infected machine. It allows to kill processes as well as remotely execute and manipulate files. On top of that, njRAT is capable of manipulating the system registry. When infected, Bladabindi trojan will collect several bits of information about the PC that it got into, including the name of the computer, operating system number, country of the computer, usernames, and OS version.
Also, this malware is able to target cryptocurrency wallet applications and steal cryptocurrency from PCs. For example, it is known to be able to grab bitcoins and even access credit card information which sometimes can be stored in crypto apps as a means to purchase cryptocurrency.
After infecting a computer the malware uses a variable name and copies into %TEMP%,
%APPDATA%, %USERPROFILE%,%ALLUSERSPROFILE% or %windir% – a behavior not uncommon for this time of malware. It can also copy itself into
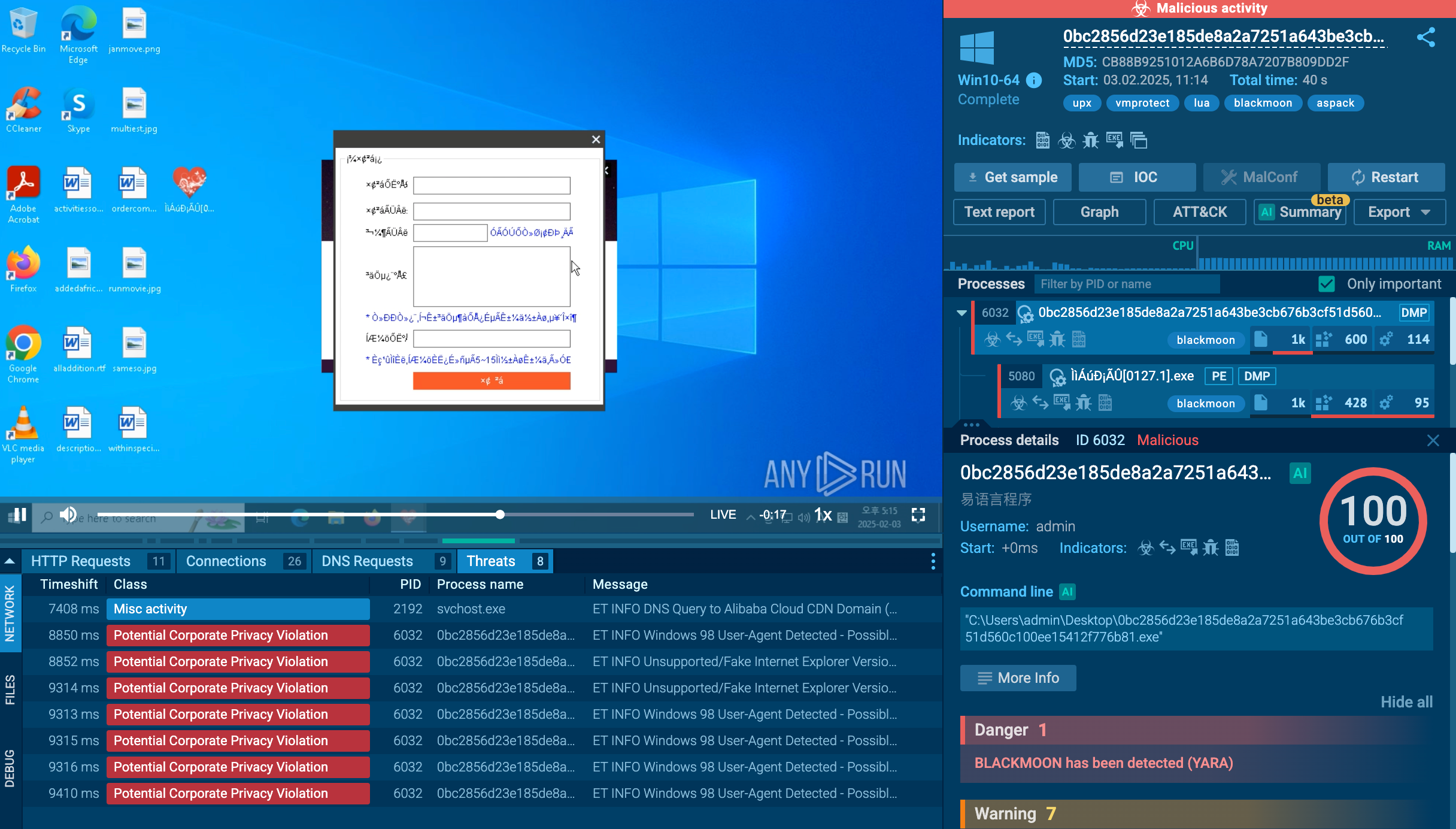
njRAT trojan has a few tricks up its sleeve to avoid detection by antivirus software. For example, it uses multiple .NET obfuscators to obstruct its code. Another technique that the malware uses is disguising itself into a critical process. This does not allow the user to shut it down. It also makes njRAT hard to remove from the infected PCs. Bladabindi RAT can also deactivate processes that belong to antivirus software, allowing it to stay hidden. njRAT also knows how to detect if it has been run on a virtual machine which helps the attackers to set up countermeasures against researchers.
Authors of Bladabindi are leveraging Pastebin to avoid investigation by cybersecurity researchers. njRAT downloads additional components and executes secondary-stage payloads from Pastebin. So, the malware has no need to establish a traditional command-and-control (C2) server. The Pastebin creates a pathway between njRAT infections and new payloads. With the trojan acting as a downloader, it will grab encoded data dumped on Pastebin, decode, and deploy.
For spreading, njRAT can detect external hard drives connected via USB. Once such a device is detected, the RAT will copy itself onto the connected drive and create a shortcut.
Creators of njRAT are members of an underground hacker community named Sparclyheason. Evidently, they have created a very popular and destructive malware. njRAT was classified as “severe” by Microsoft Malware Protection Center.
In fact, following a large malicious campaign in 2014, Microsoft shut down four million websites in an effort to filter traffic that was going through no-ip.com domains.
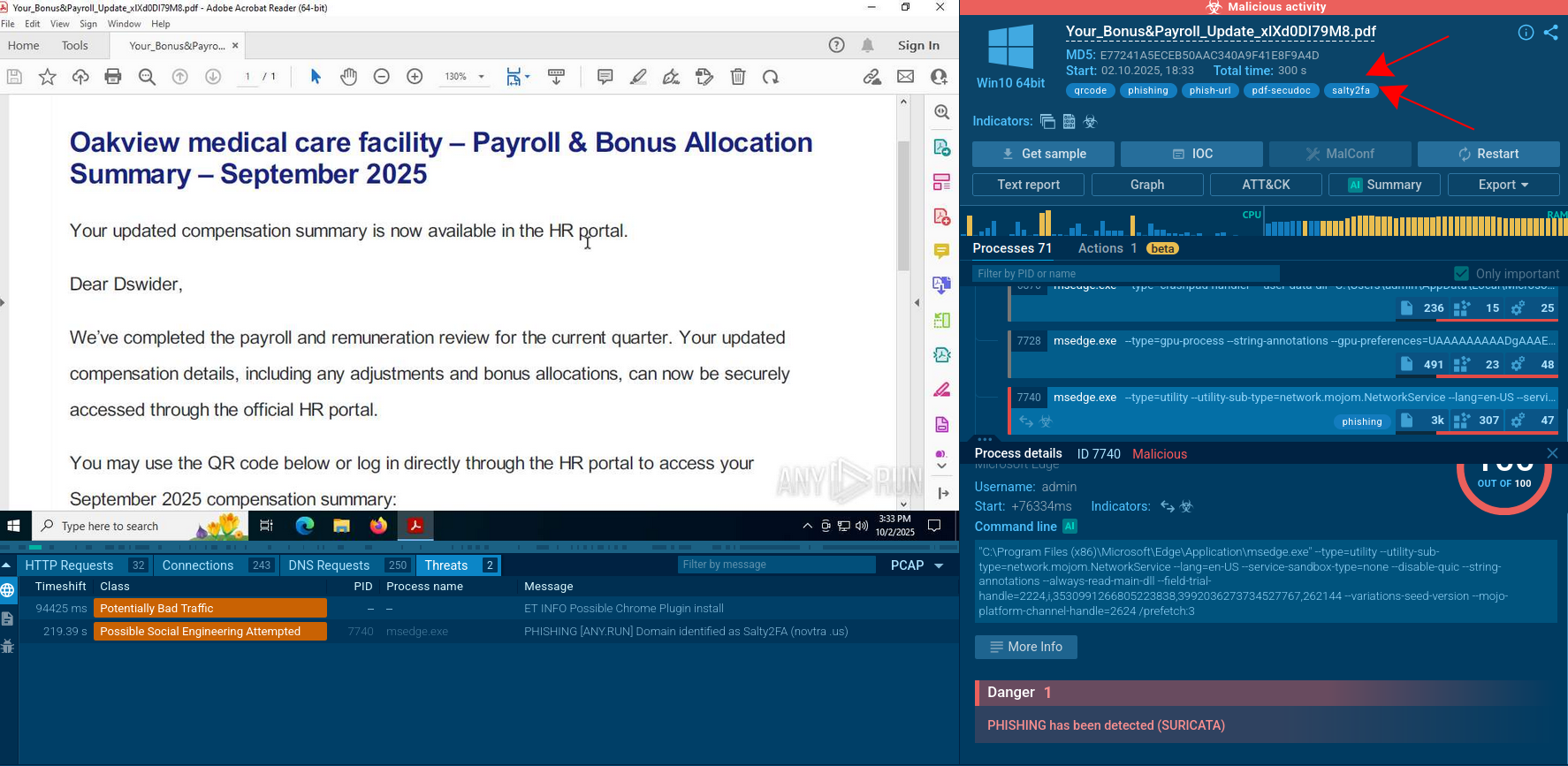
ANY.RUN allows researchers to watch the njRAT in action in an interactive sandbox simulation.
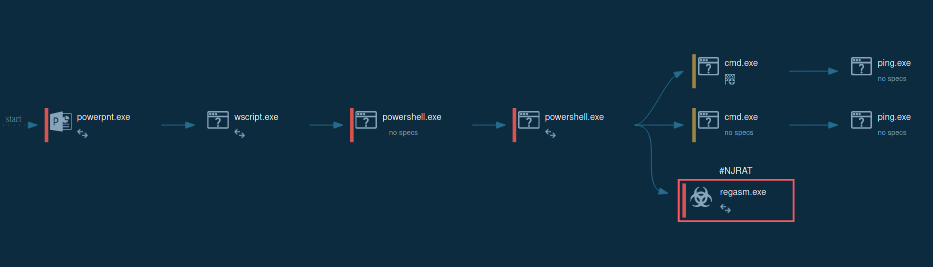
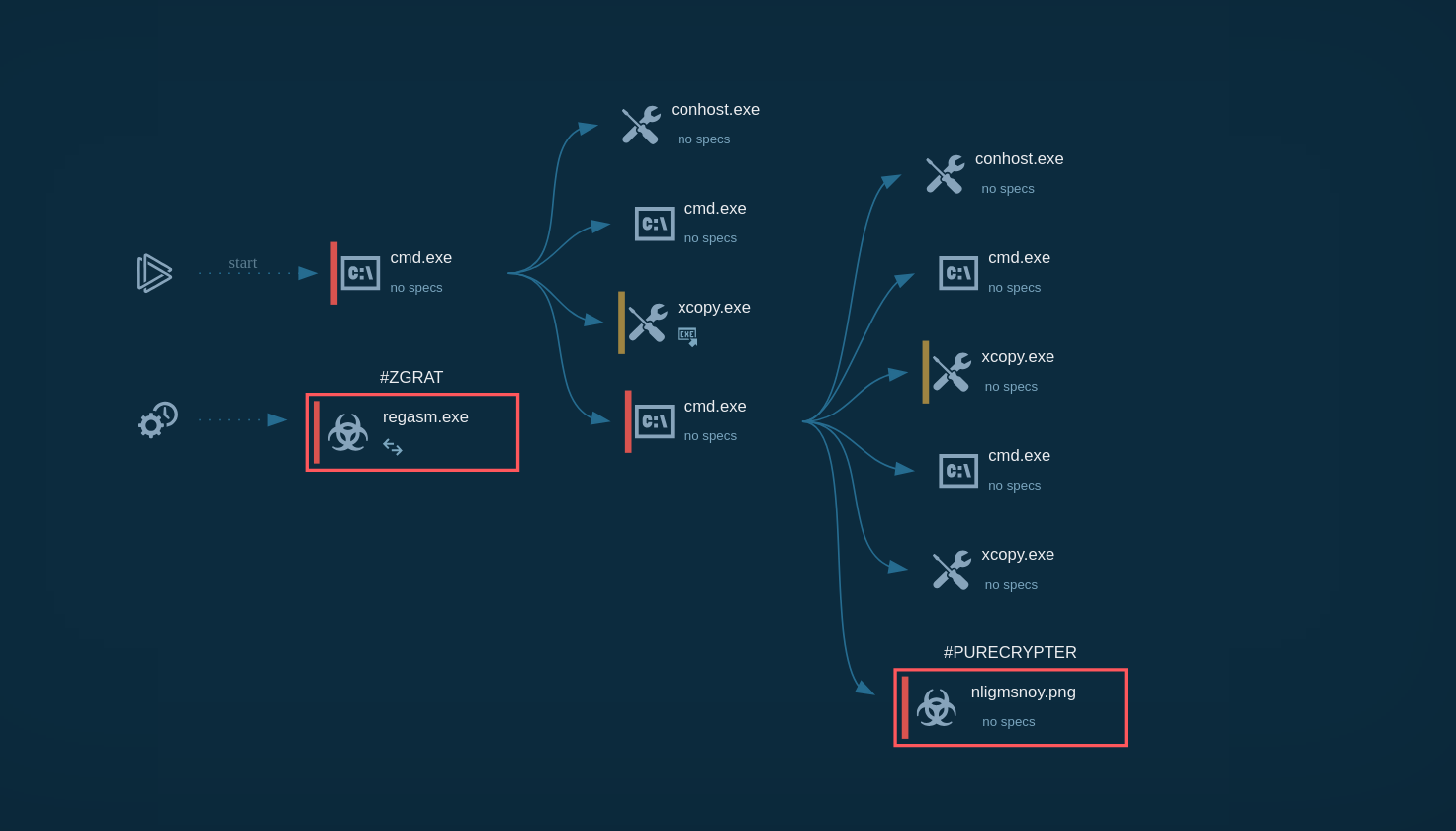
Figure 1: Displays the lifecycle of njRAT in a visual form as a process graph generated by ANY.RUN malware hunting service
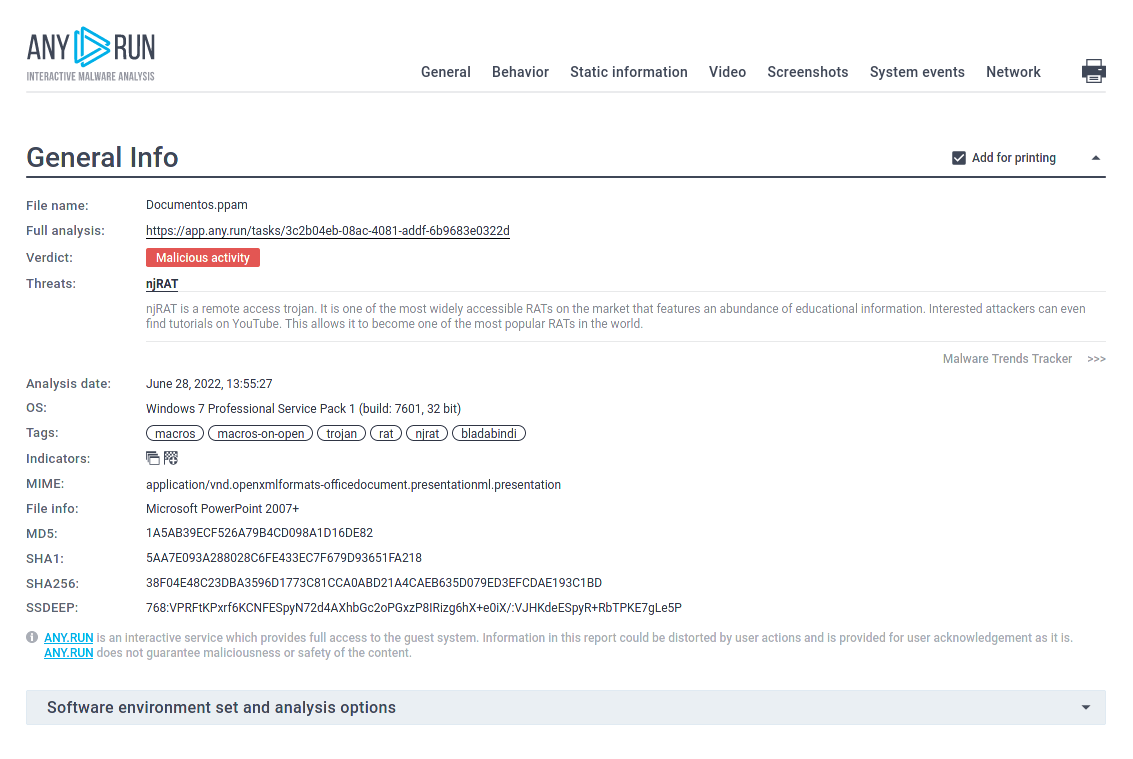
Figure 2: A customizable text report generated by ANY.RUN allows to take an even deeper look at the malware and helps to share the research results
In our simulation, after njRAT got into the target device and began execution it instantly started its malicious activity. Usually, the initial file renames itself and creates a child process. Sometimes njRAT trojan injects its code into legitimate processes such as RegSvcs.exe and RegAsm.exe.
The malware also has the ability to run itself through Task Scheduler. This child process executes the main malicious activity. Such activity includes stealing information, connecting to C2 servers, and changing the autorun value in the registry to run itself when the operating system starts.
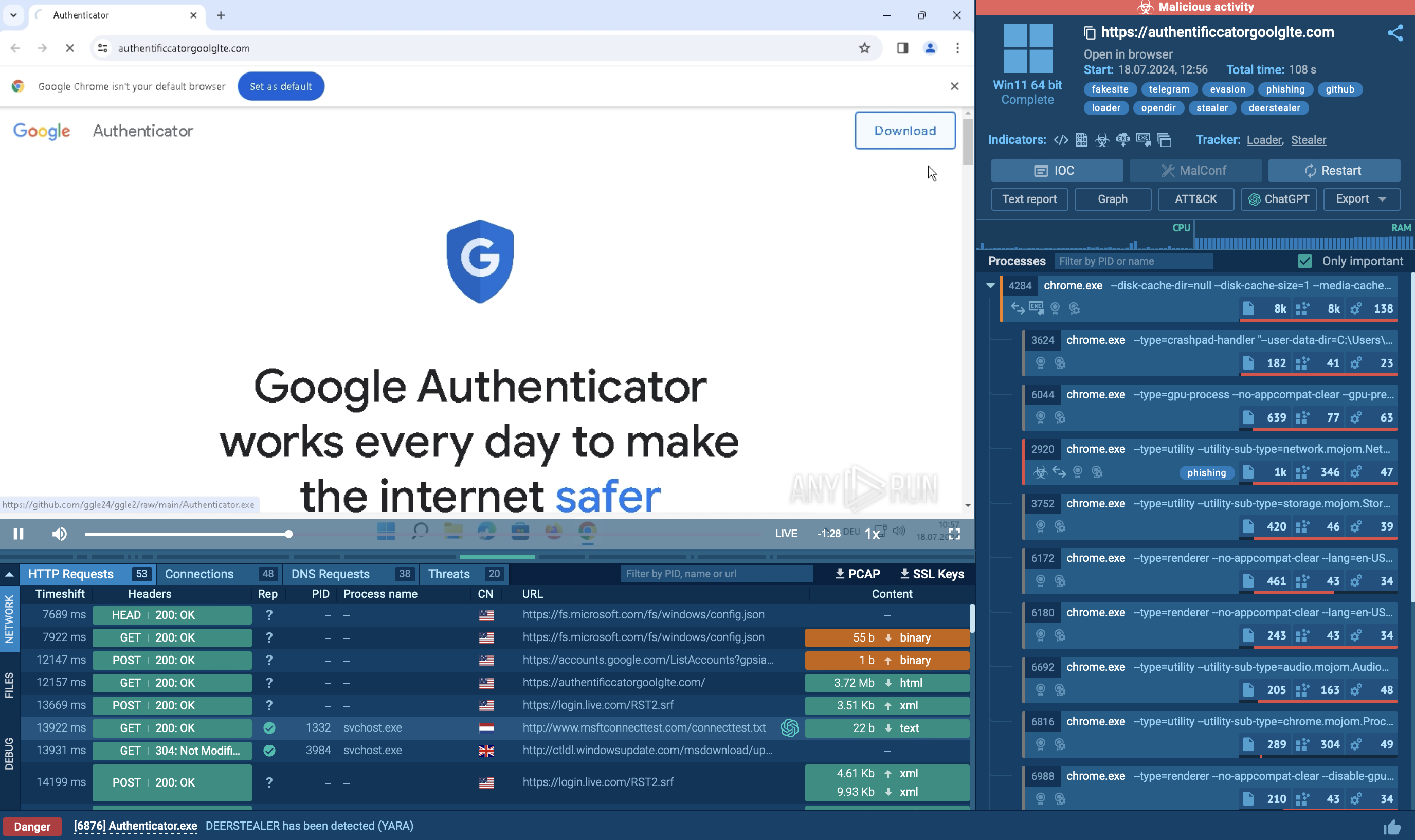
njRAT trojan uses quite a few attack vectors to infect its victims. For example, the malware is known to target Discord users as part of spam campaigns. In addition, leverage cracks and keygens in well-known software in order to trick users. It installs malicious packages to infect the machine.
Another known distribution method was through a compromised website that tricked users into downloading a fake Adobe product update which in turn installed njRAT malware to the PC. Bladabindi was also featured in phishing email campaigns. In this case, it was delivered to potential victims as a malicious attachment.
In October 2020 mailspam used the 'shipment tracking' theme, faking popular courier and postal services. Malicious packages contain attachments in Zip format with an encoded Visual Basic script (VBE) payload and components.
Moreover, crooks use cloud-based storage platforms more often. Attackers host malicious files there to deliver malicious software, and even use them as part of a command and control (C&C) architecture. That is why it's crucial to know general malware removal instructions and analyze viruses in a safe environment.
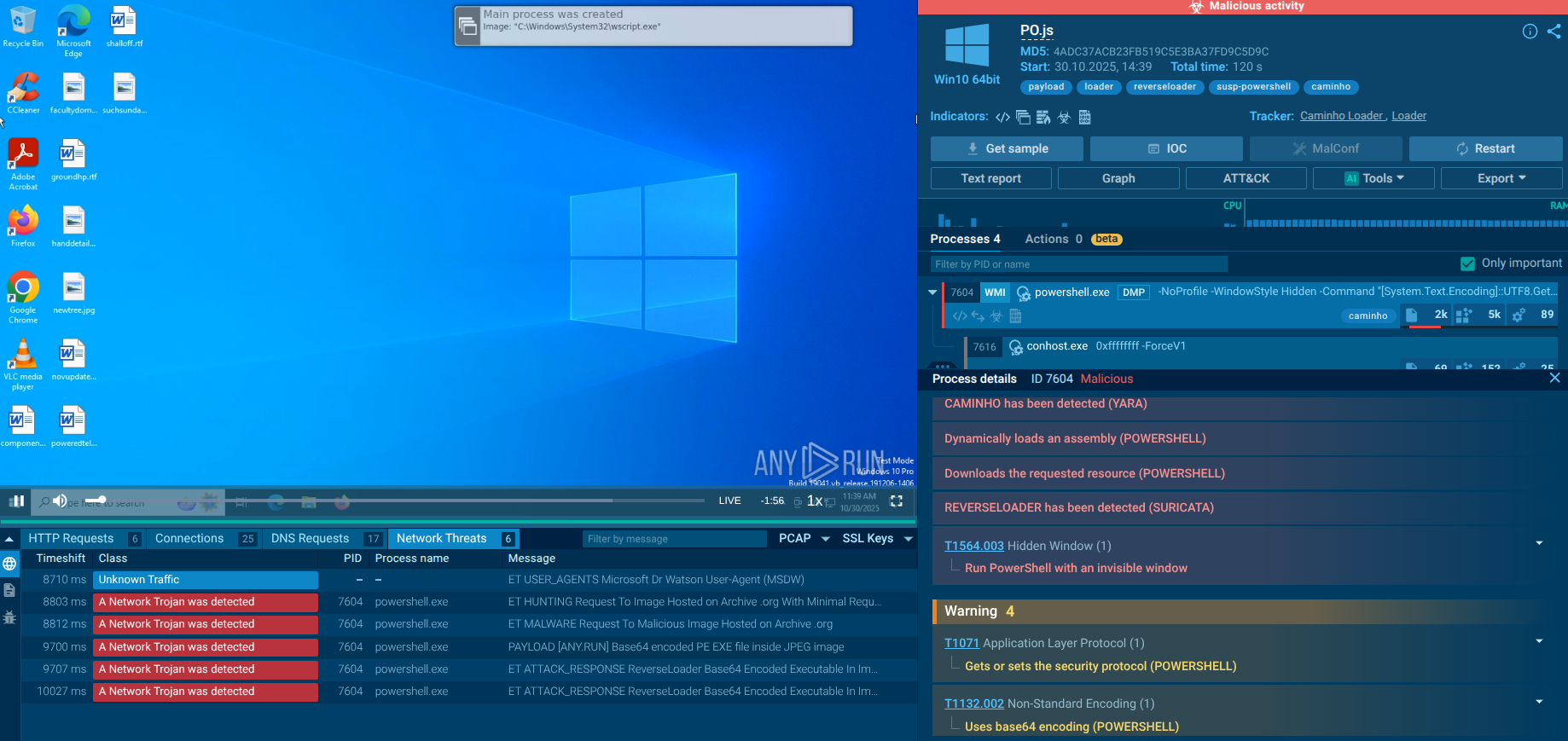
To determine whether the sample under review is njRAT or not, you can take a look at the changes that it made in the registry. To do so, open the Advanced details of process section of the malicious process and look at the "Registry changes" tab in the "Events" section. If a process has created a key with the name [kl] into the path HKEY_CURRENT_USER\Software\32_characters_and_digits, you can be sure that the given sample is njRAT.
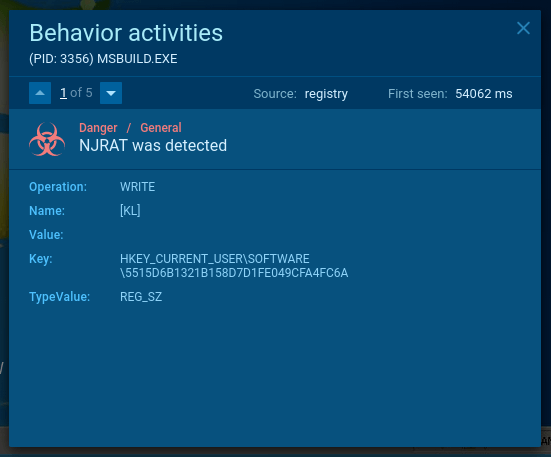 Figure 3: Сhanges made by njRAT in registry
Figure 3: Сhanges made by njRAT in registry
The relative ease of operation, multiple tutorials on how to set up this malware, and very extensive information stealing feature set have made this RAT one of the most popular remote access trojans in the world.
Even though the peak of its activity was recorded in 2014 and targeted mostly the middle east and India, the njRAT trojan remains to be extremely popular today. This malware is known to have targeted both private and corporate victims and poses a lot of danger to internet users, especially considering that it can be delivered by packages to potential victims in several ways, and preventing infection is much harder in some cases than in others.
Even though Bladabindi malware creators have taken several steps to hinder the analysis, malware hunting services like ANY.RUN allows professionals to easily study njRAT malware samples or other RATs like Orcus RAT or WSHRAT and share the research results with the world to improve global cybersecurity.
Create your free ANY.RUN account to analyze malware and phishing without limits!