Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases

WSHRAT is a Remote Access Trojan — a malware that allows the attackers to take over the infected machines. The RAT has been in circulation since 2013 and it is arguably most notable for the numerous versions released into the wild.
|
RAT
Type
:
|
likely Algerian
Origin
:
|
|
24 September, 2013
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
likely Algerian
Origin
:
|
|
24 September, 2013
First seen
:
|
27 February, 2026
Last seen
:
|

 857
857
 0
0

 508
508
 0
0

 2788
2788
 0
0
WSHRAT is a Remote Access Trojan — a type of malware that attackers use to gain remote control of machines and steal information. This particular RAT has seen several revisions, and depending on the version it’s also known as Dunihi, Houdini, H-worm, Jenxcus, and Kognito.
This RAT was first used in attacks against energy sector companies all around the world. With time, the malware became widely available and attackers used it in less coordinated attacks. The most recent version of WSHRAT changed target victims and now focuses on the banking sector.
The functionality of this RAT can vary by version, but they commonly include:
The malware surfaced for the first time in 2013 when it was known under the name H-worm. At the time, it was a RAT written in VBS (Visual Basic Script) programming language. Already, some samples featured code obfuscation and the malware packed with some advanced info-stealing functions.
The malware was developed by a user known in the underground community as Houdini. Houdini used to host a website, where people could learn about the capabilities of the RAT from an explanation video. Analysis of the content allowed researchers to conclude with a high degree of certainty, that Houdini is likely to be Algerian. This is mainly based on his fluent knowledge of French and Arabic languages.
It should be noted while analyzing the first samples of WSHRAT, researchers found out that it has similarities in command and control infrastructure with NjW0rm, njRat/LV, XtremeRAT, and PoisonIvy. These are all RATs operated by the njq8 cybergang. It is likely, that Houdini is collaborating with the gang, or he could even be a part of the njq8 syndicate.
The malware became relatively popular and VBS versions circulated in the wild for a while. In 2015, the author came out with an announcement of his plans to rewrite the malware in the Delphi programming language.
However, another version that researchers started investigating in 2016 still used VBS. This time, the RAT came in SFX files and exhibited new behavior. For example, it would launch a YouTube or open a browser URL as a decoy to hide its execution and infection happening in the background. Among others, the 2016 version of WSHRAT can be distinguished by its use of mixed binary and ASCII protocols over TCP.
The newest version of WSHRAT has popped up in 2019. This iteration of the malware targets the commercial banking sector. The RAT was completely rewritten in JavaScript from the original code of Visual basic. However, most aspects of the updated version remained identical to the older iterations. For example, it uses the same URL structure for C2 servers and exhibits similar behavior patterns.
This version is available to purchase for 50 USD and it is heavily marketed on the underground forums. In particular, the marketing campaign highlights such features of the RAT like WinXP-Win10 compatibility and a large number of information stealing and remote control functions.
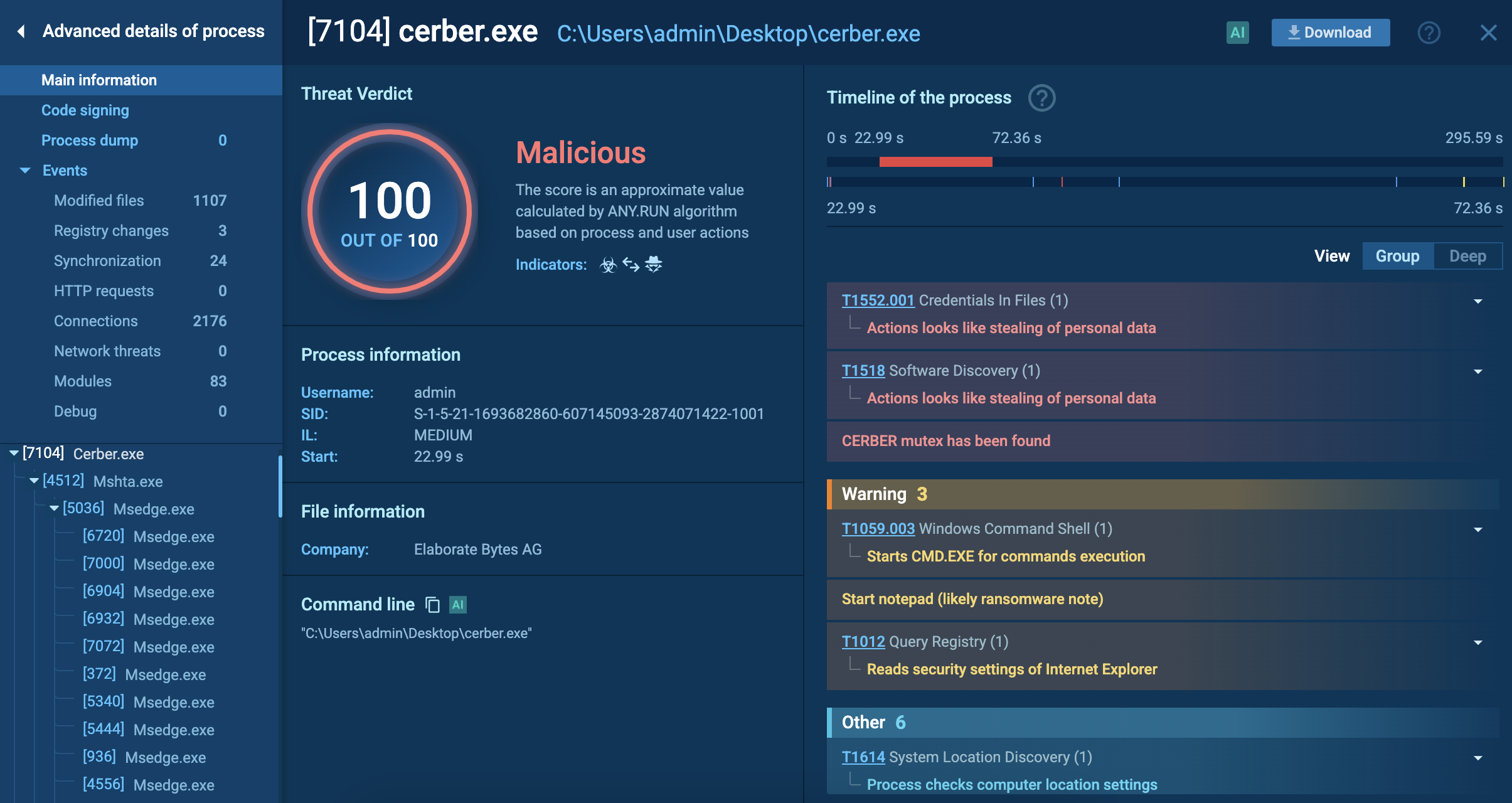
The ANY.RUN malware hunting service provides a video, where researchers can see the execution process of WSHRAT or other RATs like njRAT or NanoCore.
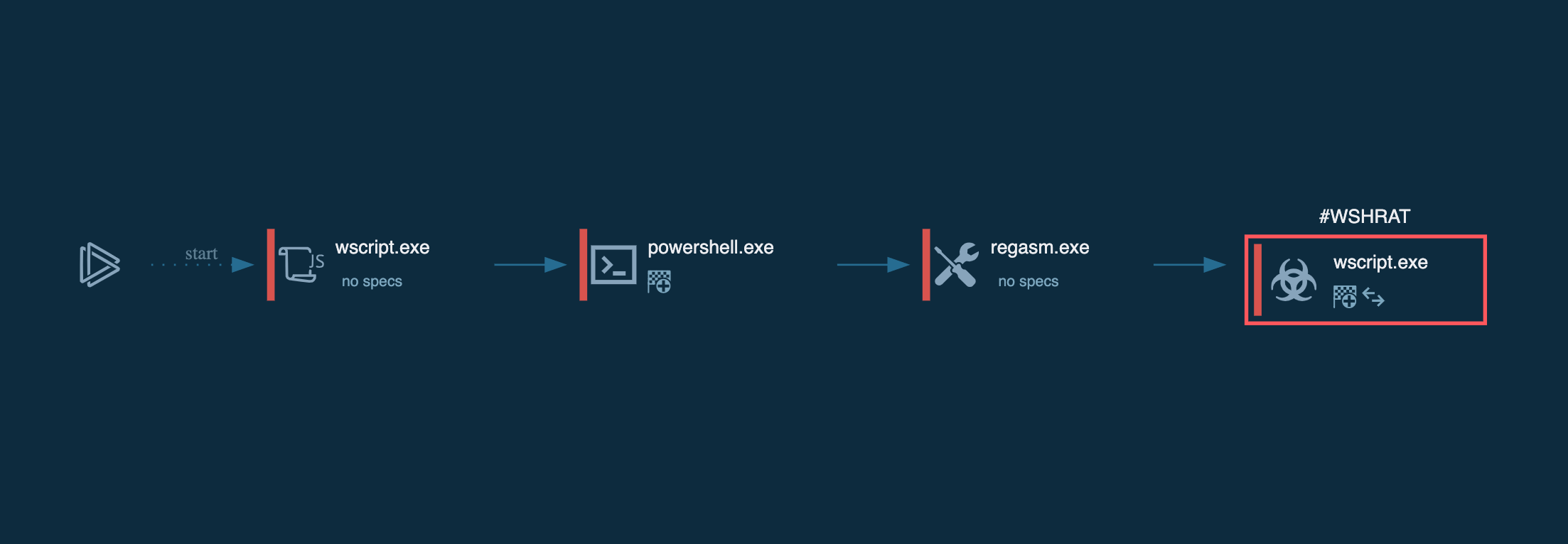
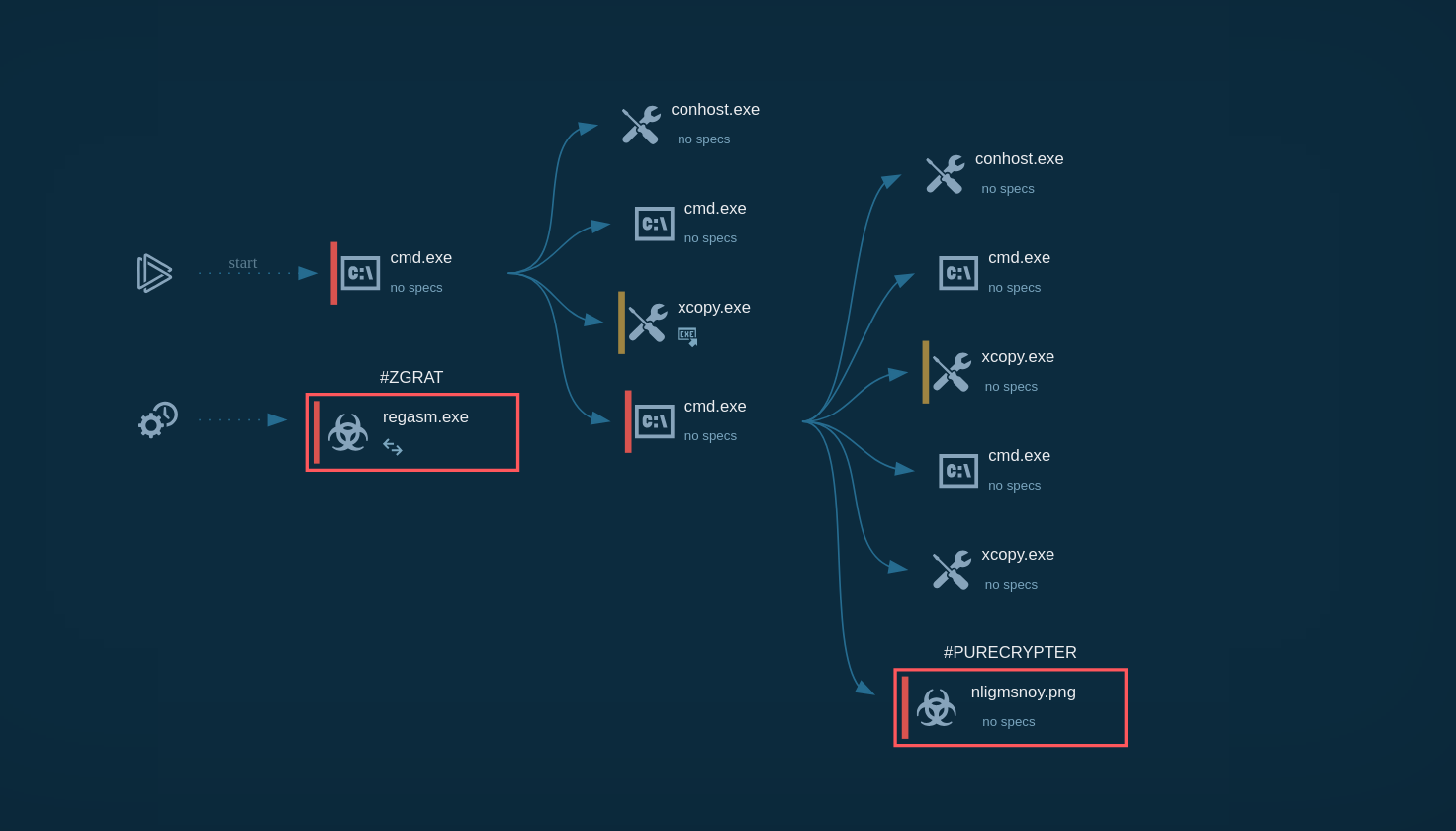
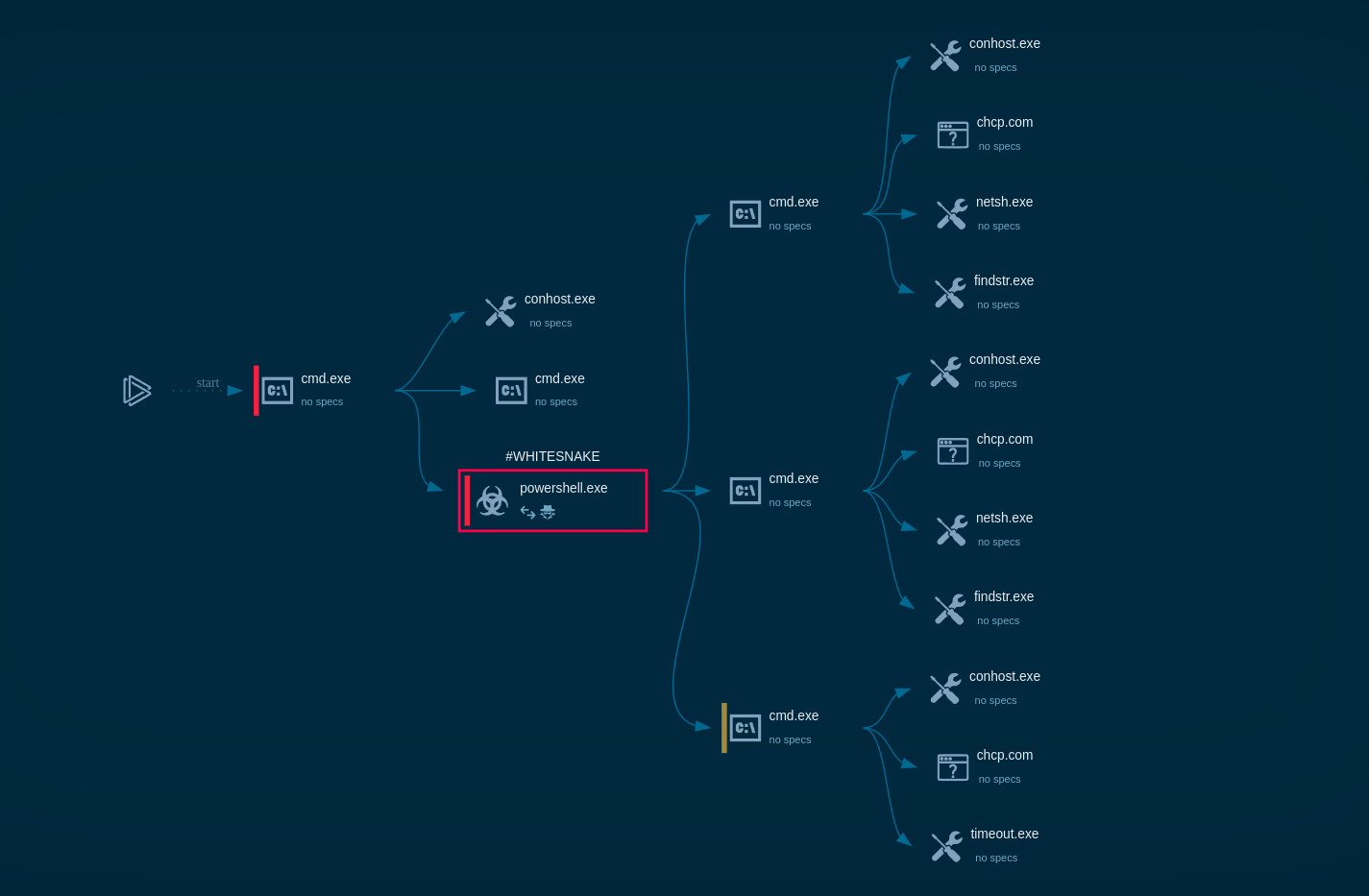
Figure 1: Shows the Wshrat graph of processes created by the ANY.RUN interactive malware analysis service.
Execution process of WSHRAT is straightforward — after the trojan makes its way into the system as a script file it either runs directly by wscript process or uses system processes such as powershell and regasm for persistence and defense evasion. After it gains persistence in the system, WSHRAT starts sending requests to the C2 server for further commands and fetches additional payloads such as its modules with different functionality.
Criminals commonly distribute WSHRAT with emails that contain infected attachments. There is evidence to believe that this RAT is used both in highly targeted attacks as well as in more broadly distributed email spam campaigns. Phishing is used to trick victims into installing the malware.
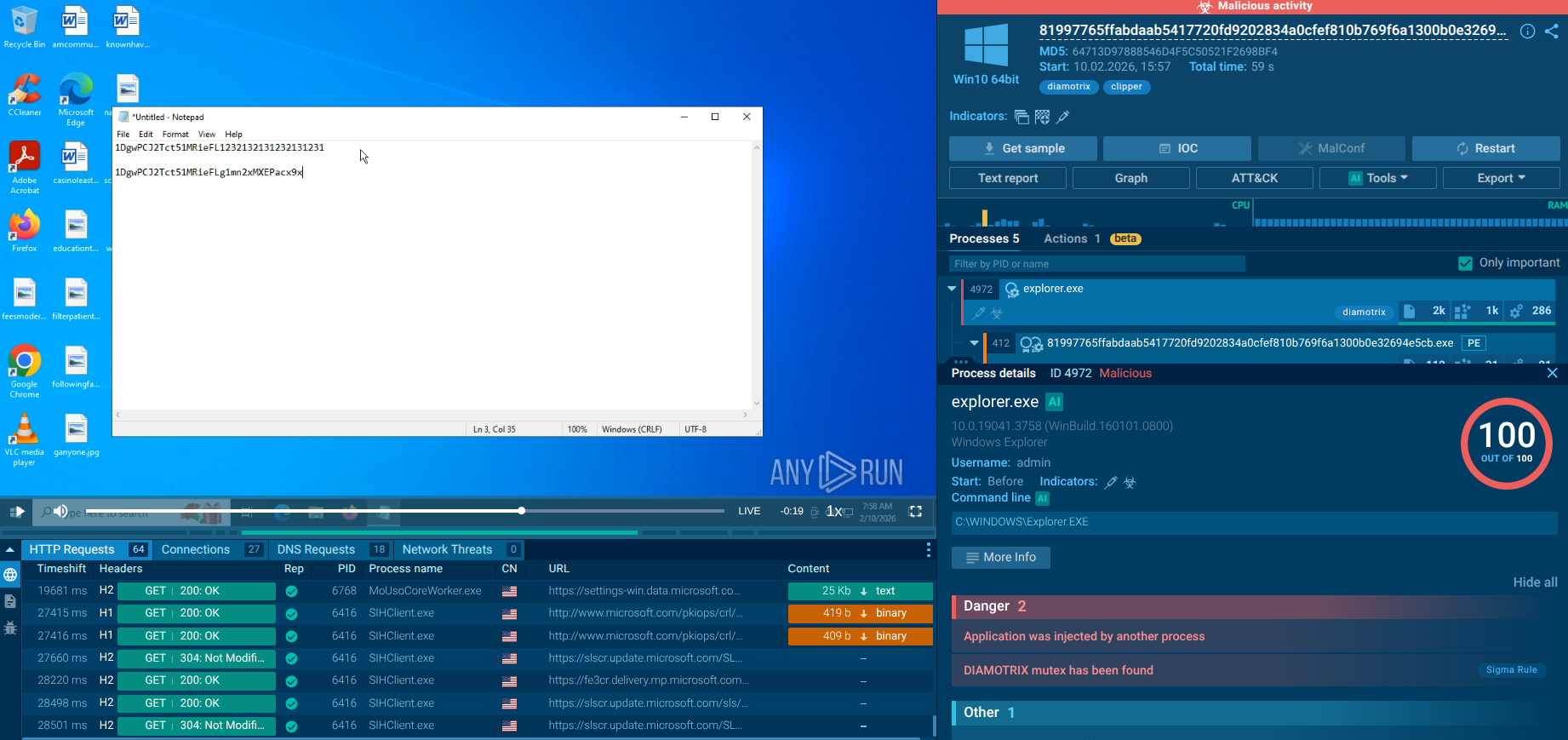
Sometimes valuable information about the malware family can be found in the network activity. Wshrat is not an exception. This malware sends HTTP requests to the Command & Control server using POST method and it names itself as a User-Agent. You can find details at "HTTP Requests" tab by clicking at "POST" method icon. In an opened window, take a look at the User-Agent and if it says WSHRAT, you know which malware family you are dealing with.
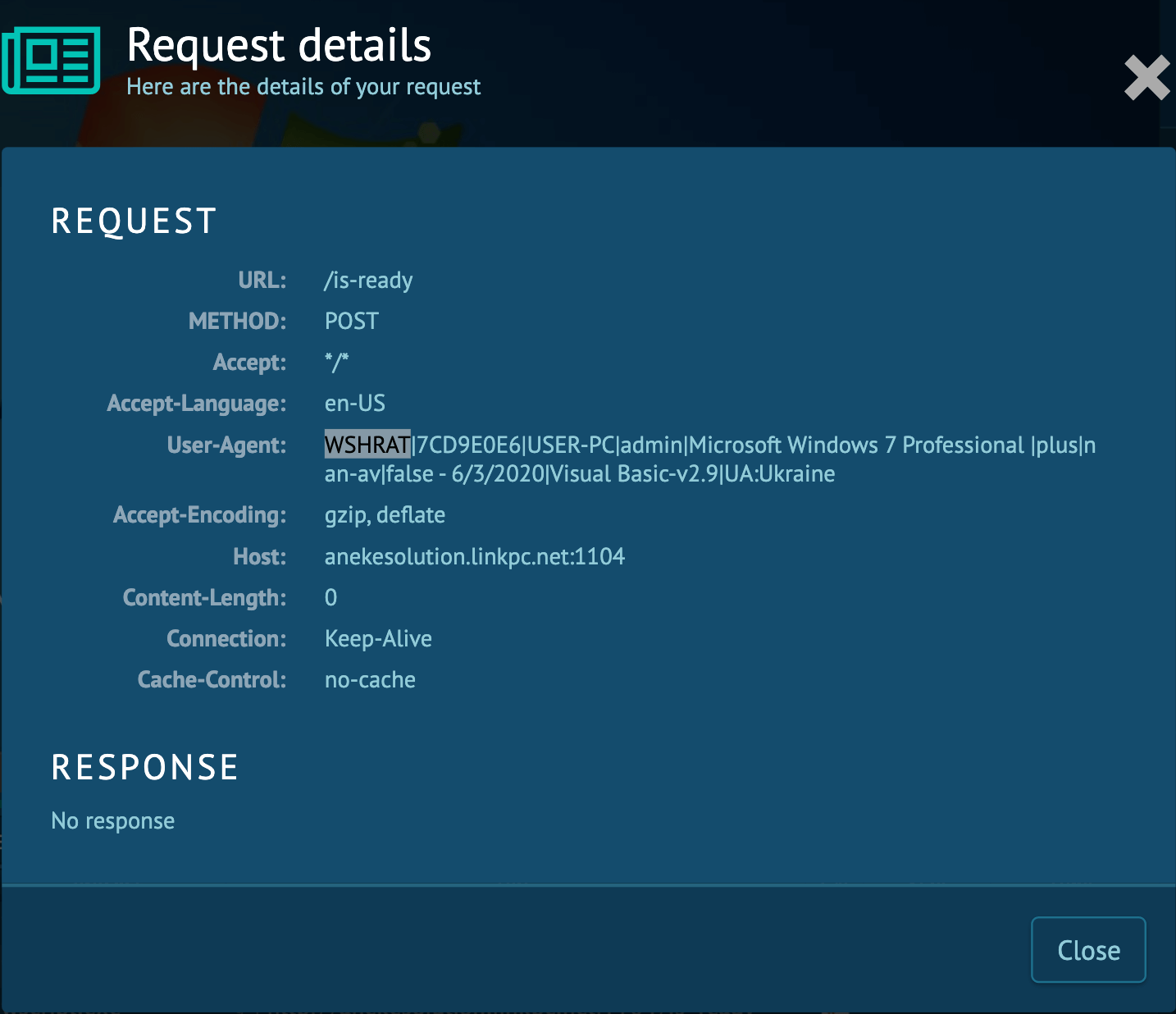
The danger of malware like WSH RAT lies not only in its robust feature set as a RAT but also in its morphing capability. Writing in VBS helped the attackers to push out an incredible number of versions. While security researchers were busy analyzing one sample, a new iteration could be released into the wild.
In cases like this, the ability to perform research fast is of crucial importance. This is especially true if we consider that certain samples of WSHRAT use code obfuscation and encryption that render static analysis ineffective. This means that a more complicated and time-consuming dynamic analysis is a must.
Thankfully, interactive analysis services like ANY.RUN help solve this problem. ANY.RUN allows launching samples in a secure, interactive online environment, where researchers can choose a variety of system parameters that influence the flow of execution. This vastly accelerates the research process and the results are presented in real-time.