Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Netwalker is ransomware — it belongs to a malware family which encrypts files and demands users to pay a ransom to get their data back. Netwalker utilizes several sophisticated techniques, such as process hollowing and code obfuscation to target corporate victims.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
1 August, 2019
First seen
:
|
25 December, 2025
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 August, 2019
First seen
:
|
25 December, 2025
Last seen
:
|

 421
421
 0
0

 2239
2239
 0
0

 4358
4358
 0
0
Netwalker, also called Mailto is a Ransomware — malware that encrypts files on infected devices and uses lost information as leverage to make the victim pay a ransom in exchange for the lost access to their data.
Although Netwalker is relatively novel, having been discovered in August 2019, it has already been featured in successful attacks against multiple companies. And amidst the Coronavirus pandemic, it started using the virus-related emails to play on natural fears and potentially infiltrate more networks.
Netwalker usually targets businesses and corporate victims, infiltrating a corporate network and spreading to all connected Windows PCs. One of the first campaigns where this ransomware was seen included an attack on an Australian company Toll Group, which temporarily paralyzed over 1000 endpoints in February 2019.
Since then the malware has continued to stay active but changed the distribution method to take advantage of the chaos caused by the COVID 19 pandemic, heavily utilizing phishing techniques. In addition, Netwalker started targeting medical and healthcare institutions, since they are potentially the most vulnerable due to the pandemic.
Netwalker ransomware is considered highly dangerous since it incorporates advanced anti-detection and persistence mechanisms. What’s more, successful attacks in the past prompted the FBI and the U.S Department of Homeland Security to issue warnings about this malware.
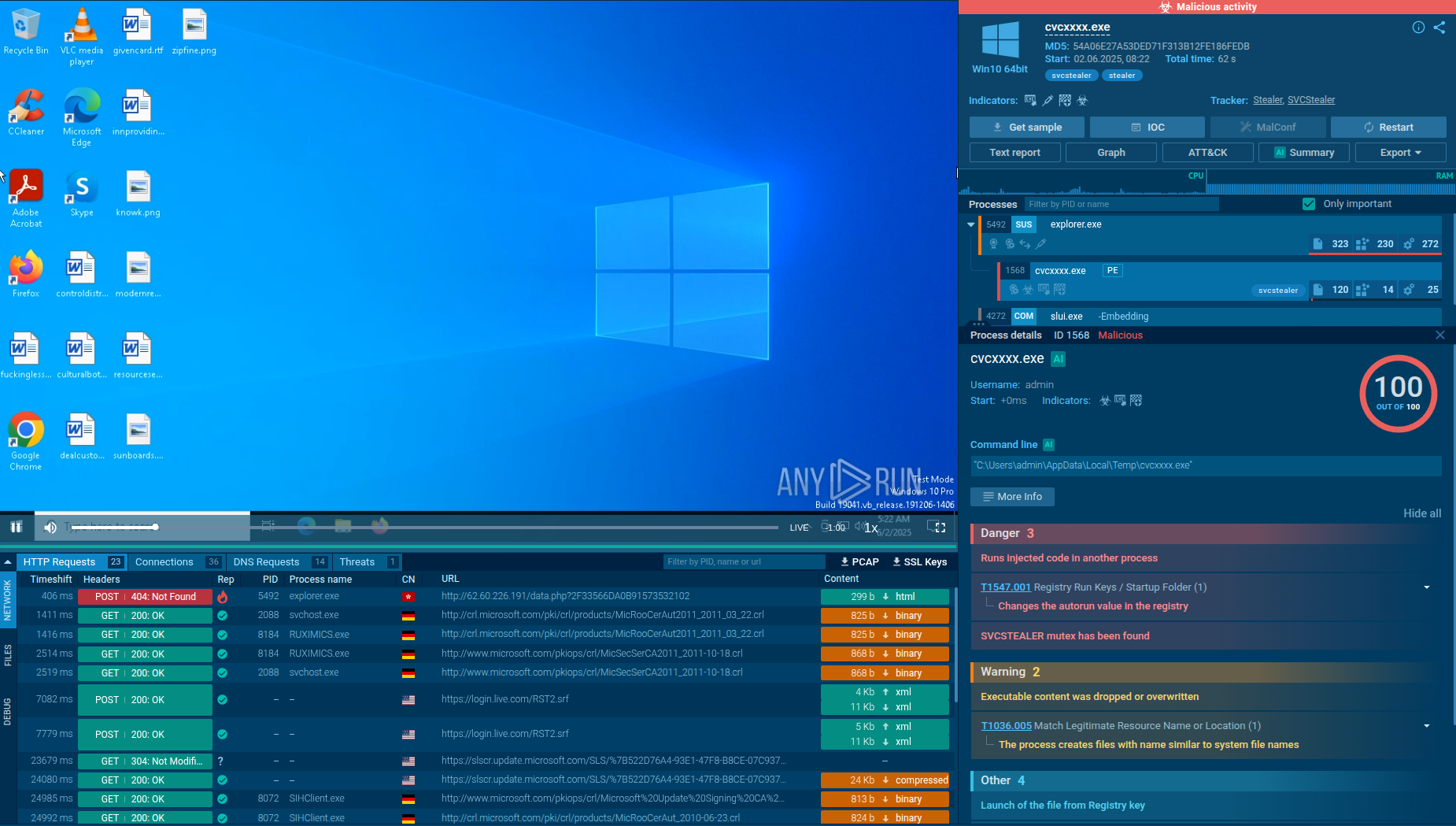
Netwalker indeed has several advanced features. For example, experts report that this malware utilizes process hollowing, a technique that allows the attackers to execute the malware while masing it with a legitimate process, “explorer.exe” in the case of Netwalker. Thus, the malware cannot be detected simply by looking at the list of processes, since it does not trigger the occurrence of any suspicious processes.
The malware also may copy itself into “AppData” subfolders and use a registry key to automatically launch itself and survive system reboots, achieving persistence in the infected system.
Additionally, Netwalker features code obfuscation to complicate the static analysis of the samples. The malware encodes all strings in its source code to prevent the analysts from easily reading its code.
It should also be noted that after encrypting the targeted files, depending on the version the malware can append the string “mailto” to filenames. This is how the first known name of this Ransomware was created. The name was later changed, after researchers analyzed a discovered decryptor, and found out that the original creator likely called the software “Netwalker”.
The ANY.RUN malware hunting service features a video that displays the complete execution process of Netwalker.
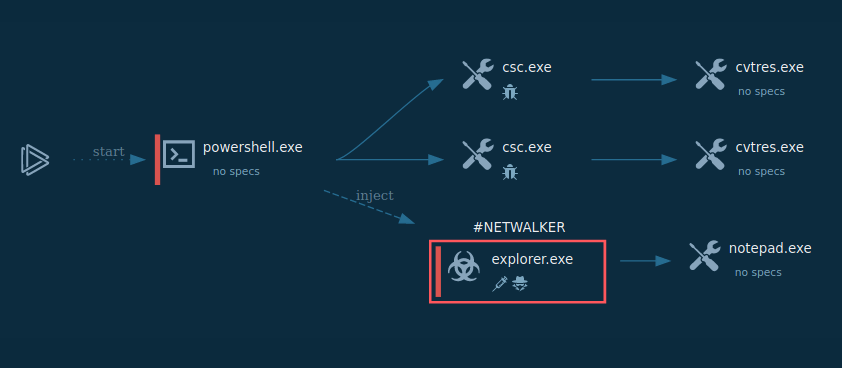
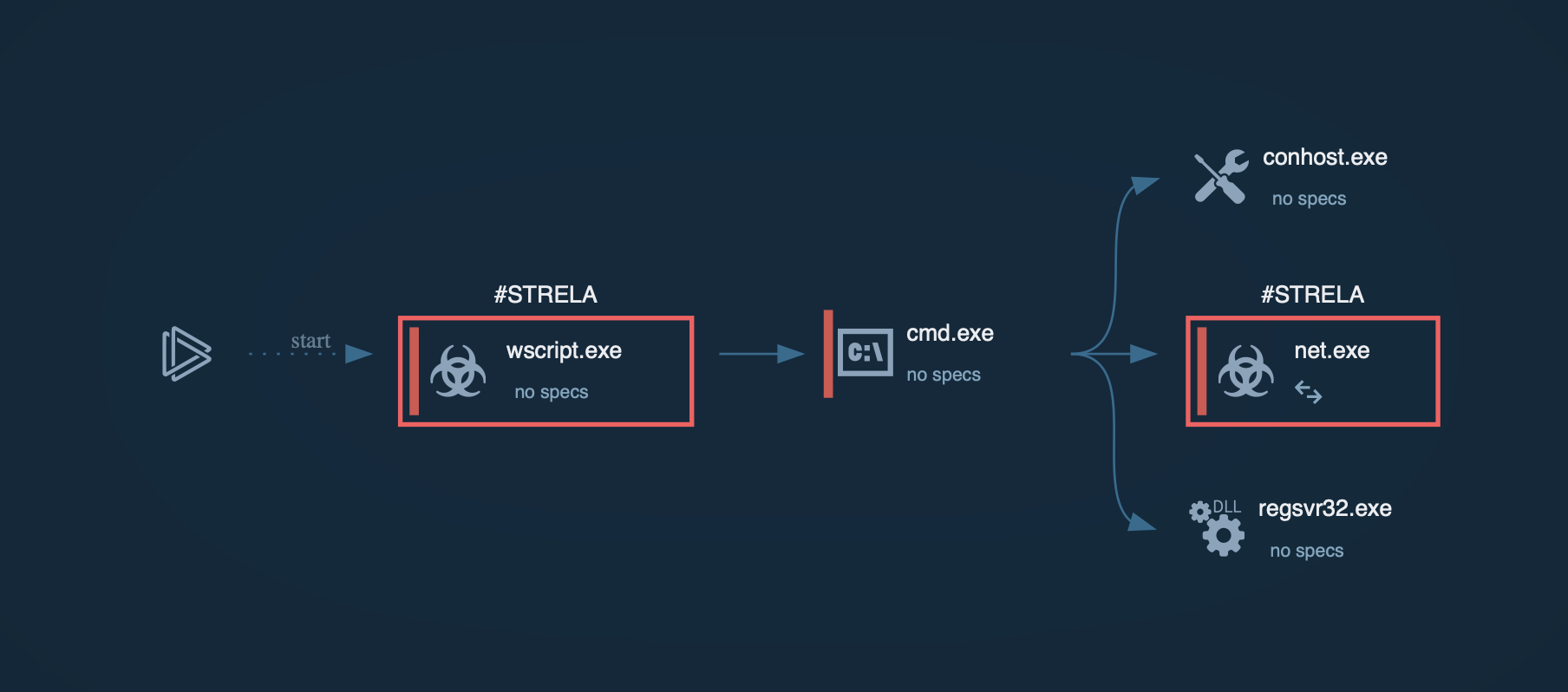
Figure 1: Shows the graph of processes created by the ANY.RUN interactive malware analysis service
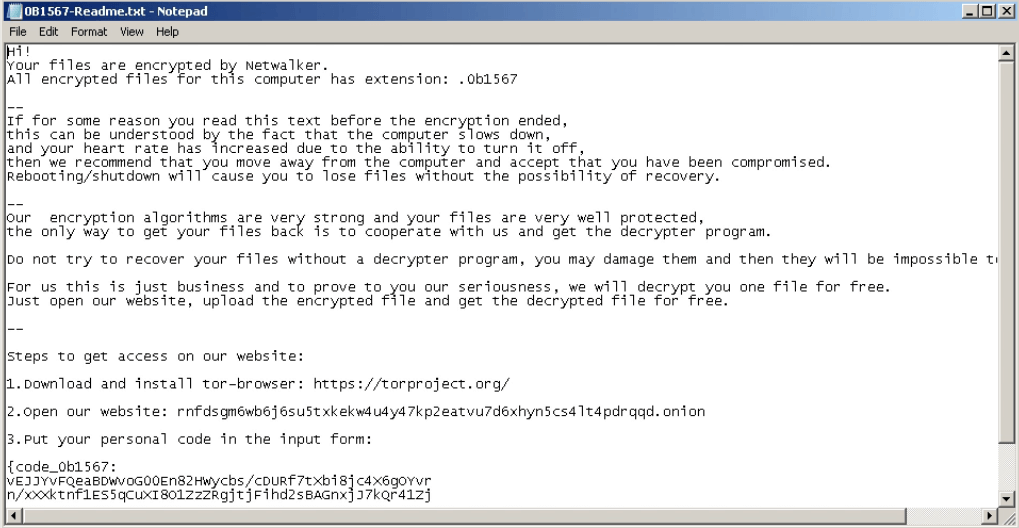
Figure 2: Netwalker ransom note
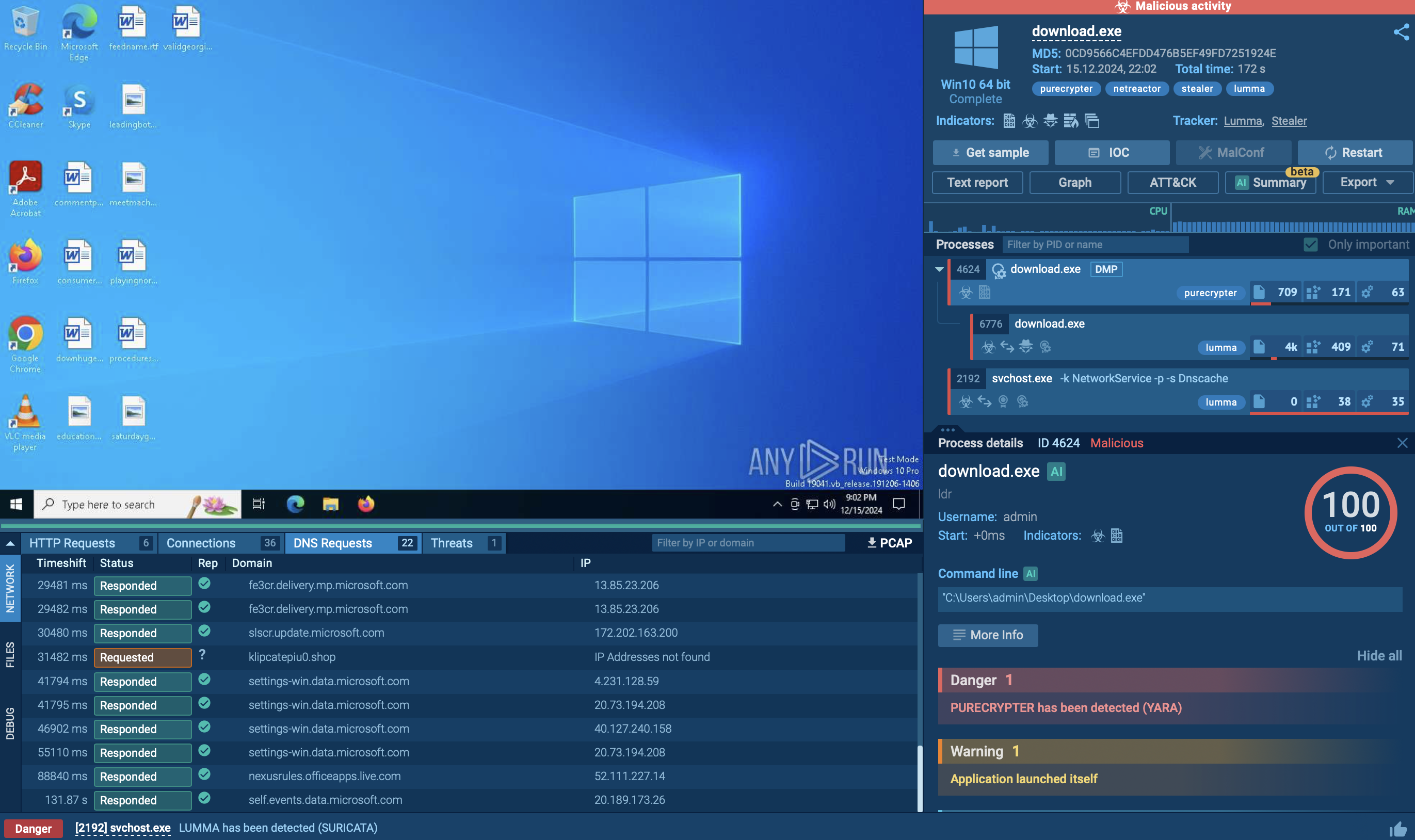
In general, the execution process of Netwalker is not much different from other ransomware like Ryuk. At first, Netwalker was distributed as an executable file, but then it soon started utilizing script files such as VBS and Powershell. After the ransomware makes its way into an infected system and runs, the main malicious activity begins. Like many other ransomware families, Netwalker deletes shadow copies. After the encryption process ends, this ransomware often stops its process and deletes itself. Like other malware of this type, it creates a text file with a ransom note and drops it in every directory that contains encrypted files. The ransom note file opens on the desktop after the encryption process is ended. Also, Netwalker uses the process hollowing technique to inject the payload into ‘explorer.exe’.
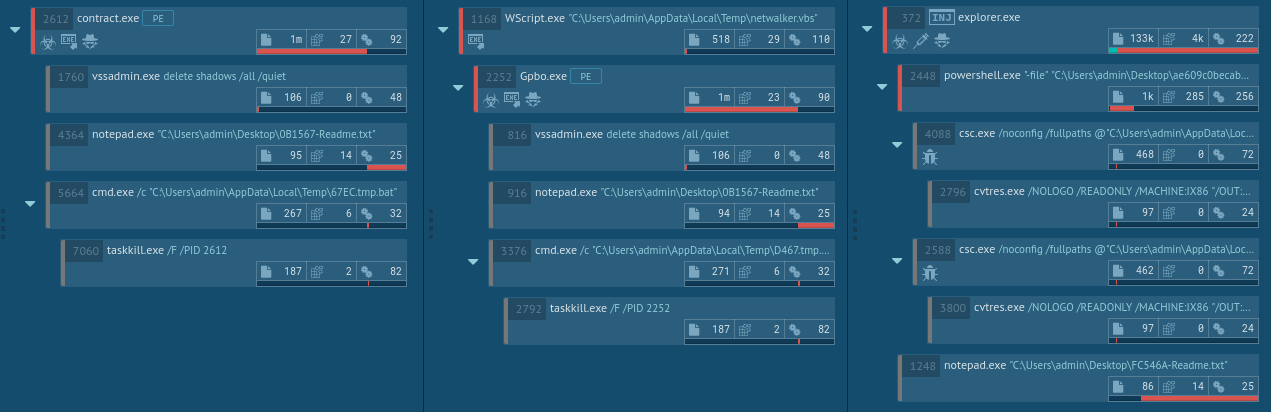
Figure 3: Netwalker versions process tree comparison: first is executable file, second is VBS script, and third is Powershell script
The malware uses multiple attack vectors to infiltrate the networks of its targets. It can utilize mail spam, web-injects, botnets, exploits, fake software updates, infected installers, and hacks that utilize insecure RDP configurations.
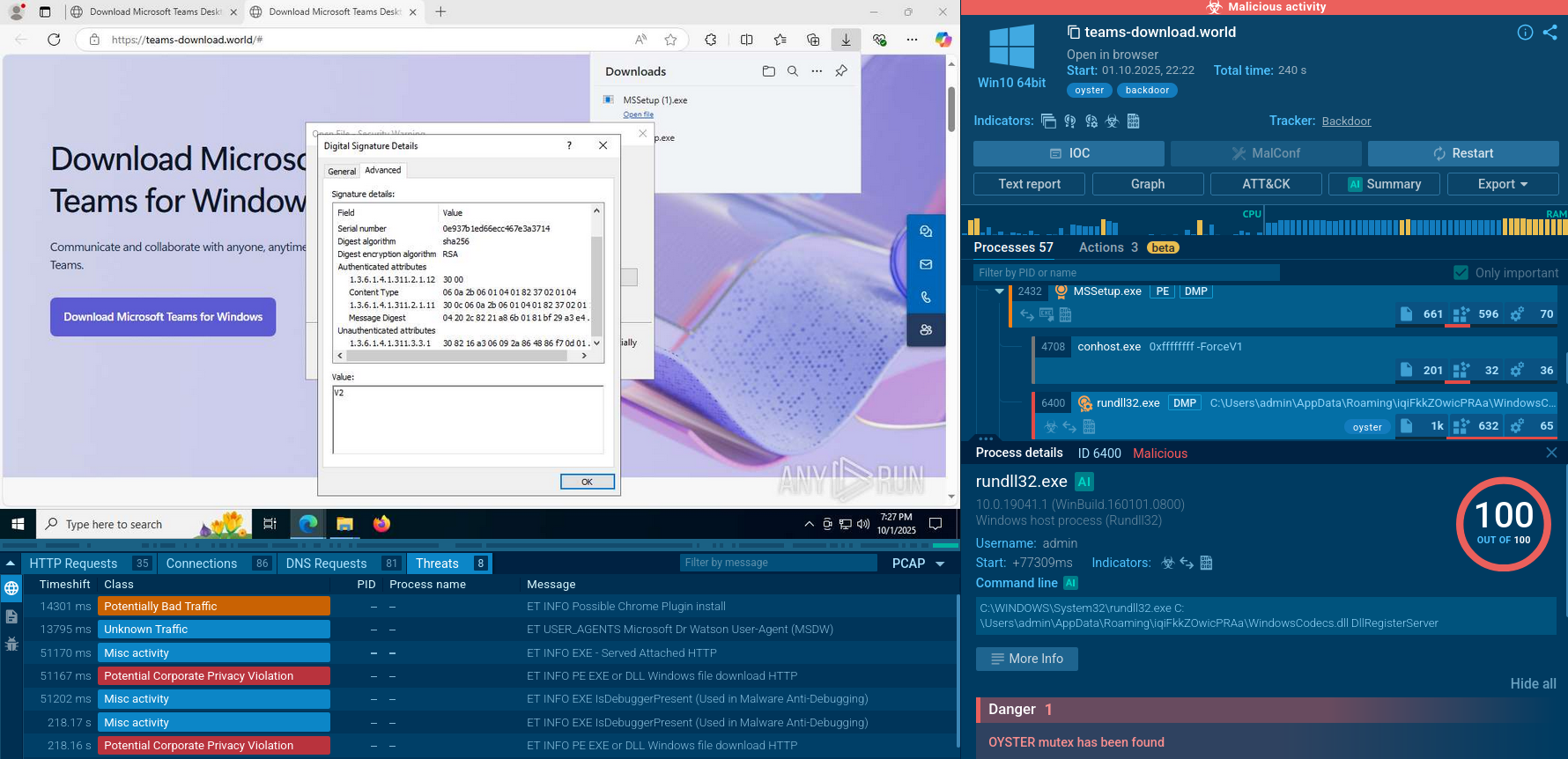
For example, it has been seen masquerading as a real software product “Sticky Password”. “Sticky Password” is a password management application developed by AVG Technologies — a very well-known player in the cybersecurity industry.
Another attack vector is using VBS scripts distributed via Coronavirus-themed spam email campaigns.
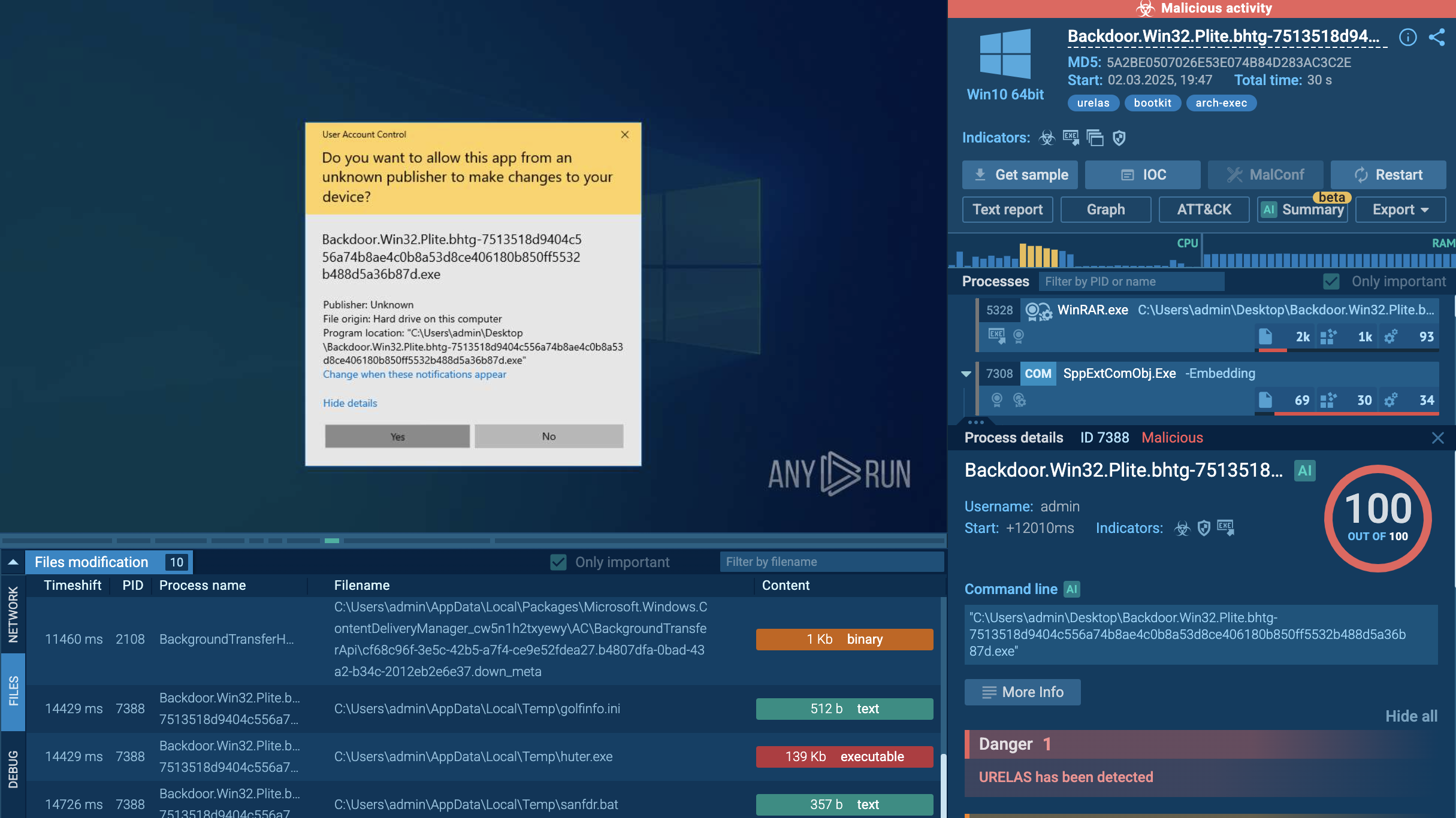
Netwalker ransomware can be detected by several different activities — such as by finding the keys that it adds into the registry or by certain files that it creates. However, the most reliable way is finding the Netwalker ransom note — not only does it have similarities with notes from other tasks, but after getting an update, this malware started adding self-defining strings: "Your files are encrypted by Netwalker."
Analysts can take a look at these notes by using ANY.RUN Static Discovering. Click on the "Files modification" tab, then find the file with the name such as "{encrypted files extension}-Readme.txt". To take a look inside this file just click on it.
If you find the line above, then be sure that the sample you are dealing with is Netwalker ransomware. With ANY.RUN you can also analyze other types of malware such as Crimson RAT.
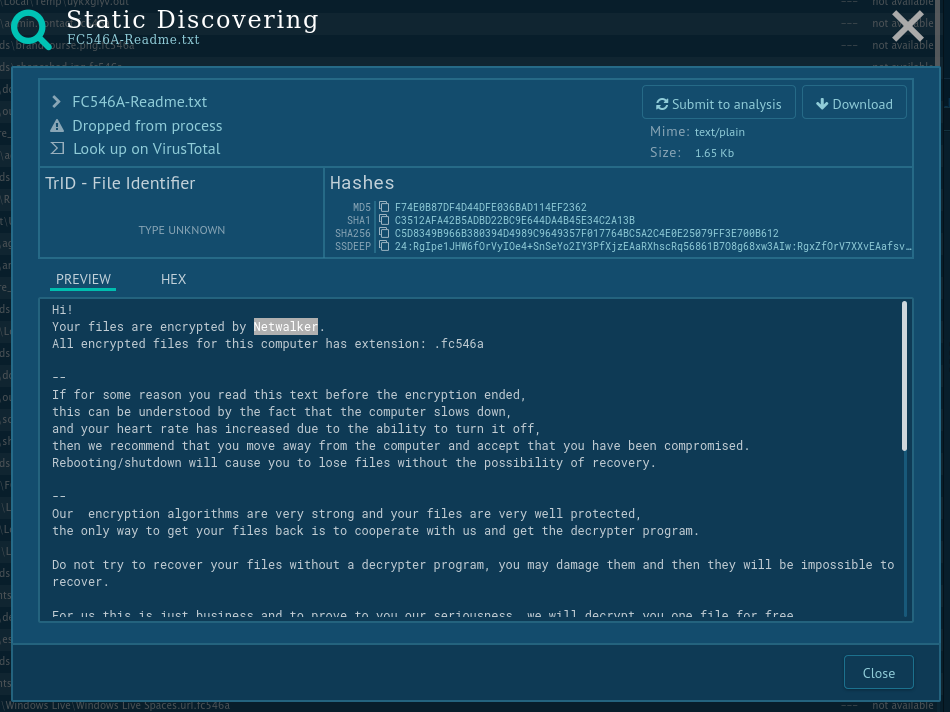
Figure 4: How to detect Netwalker ransomware using ANY.RUN
Thanks to the use of advanced persistence and anti-evasion mechanisms, Netwalker is a serious threat to the cybersecurity of organizations. This malware is one of those malicious programs that quickly started utilizing the Coronavirus pandemic for its benefit, which may point to the adaptability of the cyber-gang behind it. Thus, we can be quite certain that Netwalker attacks will continue to happen going forward.
What’s more, usually building a cyber defense against malware that uses code obfuscation is not the easiest task, since the only way to learn about the malicious program is through dynamic analysis, which demands significant time and resources.
01/28/20 Update: In January 2021 US and Bulgarian law enforcement agencies teamed up against NetWalker. Bulgarian authorities took over domains in a dark web used by malware actors. It was used to provide ransom instructions and connect with victims.
Sebastien Vachon-Desjardins, a Canadian citizen, was charged in a Florida court, that accused him of obtaining over $27.6 million from infecting companies with NetWalker. On January 10th, authorities managed to seize $454,530.19 in cryptocurrency, which is made up of payments made by malware victims.
ANY.RUN malware hunting service enables researchers to perform dynamic analysis in an interactive and safe online environment with our user-friendly tools and help learn as much as possible about this and other similar ransomware threats.