Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases
Spyware is a stealth form of malware whose primary objective is to gather sensitive information, such as personal data, login credentials, and financial details, by monitoring user activities and exploiting system vulnerabilities. Spyware operates secretly in the background, evading detection while transmitting collected data to cybercriminals, who can then use it for malicious purposes like identity theft, financial fraud, or espionage.

 799
799
 0
0

 484
484
 0
0

 2736
2736
 0
0
Spyware is a type of malicious software that is designed to infiltrate endpoints without the user’s notice. Once on the system, such malware can engage in different illegal activities, including collecting sensitive data, monitoring user actions, and transmitting the gathered information to an unauthorized party.
Spyware can be targeted against both individual users and organizations, including businesses, educational institutions, and those affiliated with governments. It is commonly employed as part of sophisticated cyberattacks carried out by advanced persistent threats (APTs), which are typically state-sponsored hacking groups or highly skilled cybercriminals. The primary purpose of using spyware in these attacks is to conduct espionage, gather intelligence, or steal valuable information for political, economic, or military gain.
There are many families of malware that belong to the spyware category. These are usually customizable and can be configured to affect specific systems, applications, or networks. Such programs are also equipped with the capabilities to evade detection and establish persistence on the device to ensure the malware’s presence over an extended period of time.
One example of a spyware is PlugX. This malicious software has been in active use by Chinese APTs since 2008. Over the years, different versions of the malware have been distributed in dozens of campaigns against organizations in Asia.
A spyware attack occurs when a cybercriminal or a group of threat actors attempt to deliver a malicious program to a target device. Such activities may involve the use of various tactics, including:
In case of a successful attack, the spyware may persist on the infected device for years without the victim’s knowledge.
When viewed from the perspective of the MITRE ATT&CK matrix, several key stages in spyware’s execution process can be observed:
As noted, the main focus of spyware lies in locating and exfiltrating sensitive information from the machine. This is usually accompanied by granting attackers remote access to the device, letting them have a certain degree of control over it. For instance, Xeno RAT enables attackers to utilize the Hidden Virtual Network Computing (HVNC) module that gives them real-time access to the system.
Apart from browser data, such as history and bookmarks, many families of spyware can identify and exfiltrate files. They also frequently have the ability to record keystrokes of the user that makes it possible to capture more confidential information.
Some spyware programs may be configured to take screenshots, record the machine’s screen, and even listen to the microphone. One example here is Loda RAT, which on top of these activities lets attackers communicate with the victim using a special chat window.
Here are some of the most widespread spyware families:
We can safely study the execution process of Formbook by uploading its sample to the ANY.RUN sandbox.
We can observe how after the launch, Formbook initiates a connection to the command-and-control server.
Subsequently, a malicious executable file, disguised as a .png in this particular analysis, is dropped or overwritten and executed. FormBook then proceeds to steal personal data and modify the autorun value in the registry.
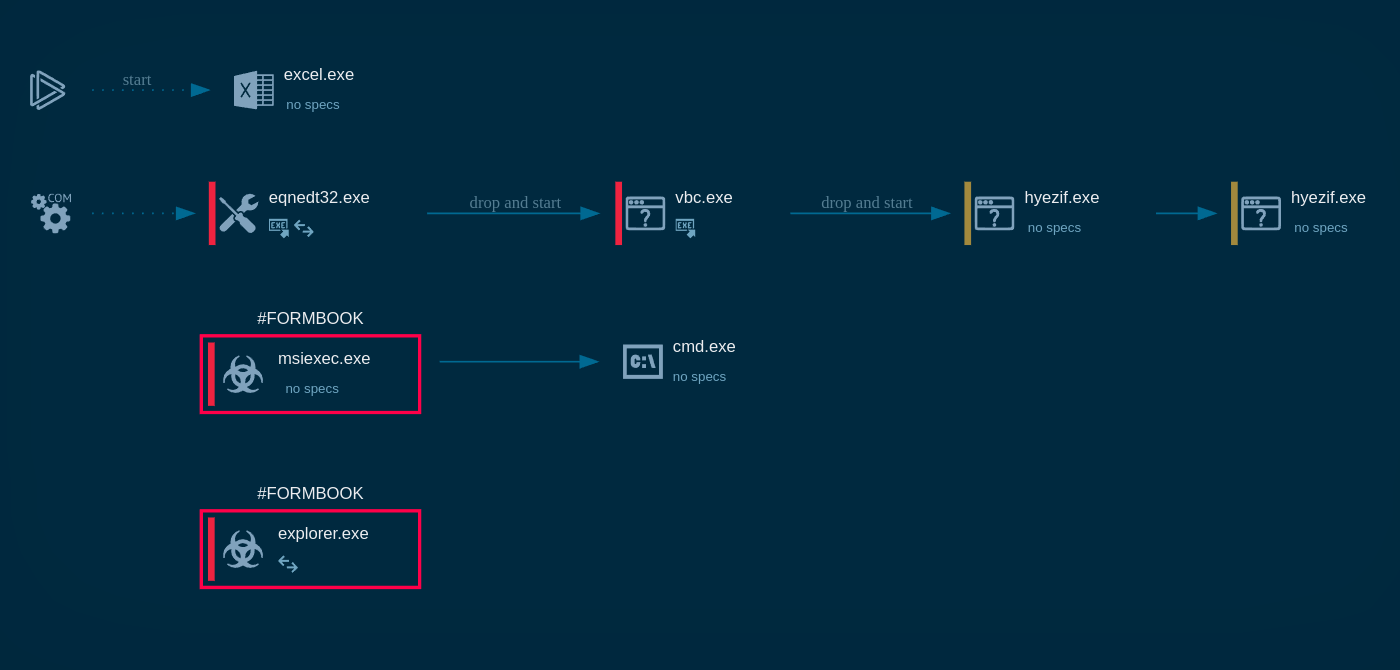 Formbook process graph shown in ANY.RUN
Formbook process graph shown in ANY.RUN
Additionally, the virus loads a DLL from Mozilla Firefox, creates files in the user directory, and launches CMD.EXE to establish persistence and prepare for process injection. Ultimately, the injected Firefox.exe is executed to log keystrokes, steal clipboard data, and extract authentication information from browser HTTP sessions.
Check out this video to see how a typical Formbook infection unfolds and learn how you can analyze spyware in the ANY.RUN sandbox.
Phishing emails remain a top method for delivering spyware to victims' devices. These typically involve the use of social engineering tactics designed to make the target believe in the legitimacy of the emails. For this purpose, attackers may mimic the visual style and language of entities like established companies and government agencies.
The infection chain begins with malicious attachments in the form of executables, PDFs, documents, and archives containing the payload. Alternatively, attackers may include malicious links that, when clicked, can eventually lead to the installation of spyware on the victim's device.
Another widespread spyware infection method is via special malware called loaders, DarkGate is a loader that is frequently observed to deliver Remocs.
Spyware infections are among the most serious, as they can be difficult to spot. As a result, the malicious program can continue operating on the compromised system for a long time, regularly exfiltrating private information and tracking victims' activities. Preventing spyware attacks requires a comprehensive security approach that includes sandbox analysis.
ANY.RUN is a cloud-based sandbox designed for effective investigations into suspicious files and links. It can detect spyware and other types of malware in under 40 seconds. The sandbox users also get to access: -Interactive Windows and Linux VMs