Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases
Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links.

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
A remote access trojan (RAT), also referred to as a remote administration tool, is a sophisticated form of malware that enables an unauthorized individual to gain clandestine remote control of a target's computer system.
Commonly propagated through phishing emails that rely on manipulation and social engineering techniques, RATs pose a significant threat to cybersecurity.
The distinctive feature of RATs is unauthorized access to the victim's computer that attackers gain, allowing them to execute commands, browse files, and even modify system settings without the user's knowledge or consent.
RATs also tend to operate in a clandestine manner, hiding their activity from security software. This is in contrast to other types of malware, such as ransomware that tend to make their presence known to the victim by presenting them with a ransom note.
Once a RAT infiltrates a system, it opens the door to a myriad of malicious activities. These can include, but are not limited to:
The particular set of capabilities depends on the malware’s configuration. For instance, the known malware OrcusRAT has a sophisticated modular architecture, enabling cyber threat actors to craft personalized plugins that seamlessly integrate with the malware.
Check out a technical analysis of OrcusRAT in our blog.
This modular design, popular across many RAT families, enhances the malware’s scalability and ease of management, making it simple to adjust its functionalities according to the specific requirements of different cyber campaigns.
Phishing emails are a prevalent vector utilized by Remote Access Trojan operators to spread their malicious activities. These deceptive emails employ various techniques to lure unsuspecting users into clicking on malicious attachments or links.
Attachments found in phishing emails can be in the form of seemingly harmless documents, such as PDFs or Word files or links. However, cybercriminals cleverly embed malicious code within these attachments and links, aiming to exploit vulnerabilities in computer systems and gain unauthorized remote access. Once clicked, these attachments or links initiate the download and installation of the RAT onto the victim's computer.
RATs can also end up on users’ devices through P2P file-sharing websites. These malicious software can masquerade as legitimate files, such as movies, music, or programs.
Alternatively, RATs can be downloaded by special loader malware, which is intended for the purpose of disseminating different payloads on compromised systems. GuLoader is a prime example of such malware, as it has been instrumental in infecting thousands of machines around the world with multiple RAT families, including Remcos.
In order to begin the infection process, RATs typically exploit vulnerabilities present in the operating system or applications. For instance, they may employ zero-day attacks to exploit undisclosed vulnerabilities or leverage well-known weaknesses in third-party software.
Once launched, RATs employ persistence mechanisms such as disabling antivirus software and utilizing rootkit methodologies, to ensure their continuous operation even after the user logs out or restarts the computer.
After establishing persistence, RATs tend to connect to a C2 server to grant the attacker full control over the compromised computer, allowing them to execute various malicious actions, including data exfiltration, installation of additional malware, and the execution of malicious commands.
RATs can also create and maintain hidden backdoors within the infected system. These covert entry points serve as secret access channels, letting attackers maintain control even if the RAT itself is removed or disabled.
We can examine the execution process of a typical RAT by analyzing a sample of njRAT in the ANY.RUN sandbox.
Analyze malware for free in a fully interactive cloud sandbox – request demo.
Upon successful infiltration of the target device, njRAT swiftly initiates its operation. One of its primary tactics involves the immediate self-renaming of the initial file, concealing its presence from unsuspecting users.
Additionally, njRAT possesses the capability to spawn a child process, often strategically injecting its malicious code into legitimate processes such as RegSvcs.exe and RegAsm.exe.
It also leverages the power of the Task Scheduler to ensure its persistence within the compromised system. Through this mechanism, the child process responsible for executing njRAT's main malicious activities is scheduled to run at predetermined intervals.
The malware then begins exfiltration of sensitive information, establishing connections with command and control (C2) servers.
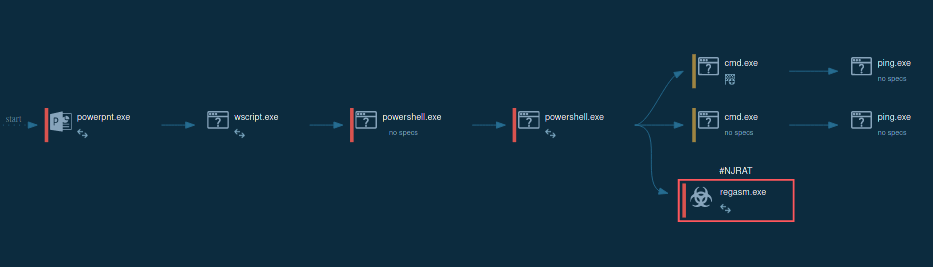 The lifecycle of njRAT demonstrated by ANY.RUN
The lifecycle of njRAT demonstrated by ANY.RUN
Staying informed on the latest developments in the cybersecurity landscape, we can use ANY.RUN’s Malware Trends Tracker. This service offers a comprehensive view of the most widespread malware families currently active on the global scale.
Here are top three RATs in terms of their popularity, according to the service:
Organizations with lax security controls are easy prey for RAT attacks. One employee's negligence in handling external files and links can set off a domino effect, compromising the entire network.
To add an extra layer of security, make sure to use ANY.RUN, a cloud-based sandbox for analyzing suspicious files or URLs to determine if they pose any threat. The service generates reports on each sample submitted by users, providing them with IOCs and other crucial information needed for mitigation.
This platform ensures a safe and controlled environment for users to interact with potentially harmful elements, without putting their devices and data at risk.
Try ANY.RUN for free – request a demo!