Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


FatalRAT is a malware that gives hackers remote access and control of the system and lets them steal sensitive information like login credentials and financial data. FatalRAT has been associated with cyber espionage campaigns, particularly targeting organizations in the Asia-Pacific (APAC) region.
|
RAT
Type
:
|
Unknown
Origin
:
|
|
1 August, 2021
First seen
:
|
11 January, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 August, 2021
First seen
:
|
11 January, 2026
Last seen
:
|

 868
868
 0
0

 515
515
 0
0

 2802
2802
 0
0
A Remote Access Trojan detected in August 2021, FatalRAT became known for targeting an array of industries in the Asia-Pacific region. It has hit government agencies, manufacturing, construction, IT, telecom, healthcare, energy, logistics, and transportation companies, particularly in countries like Taiwan, Malaysia, Japan, South Korea.
It specializes in unauthorized information access: captures input by keyloggers and makes screenshots; finds, encrypts, corrupts, and deletes user data. It doesn’t always demand a ransom, is often used for espionage, sabotage, stable persistent access to a compromised network, and as a vehicle for further attacks.
It employs a number of attack vectors to infiltrate network, mostly phishing and social engineering tactics. FatalRAT is also known to abuse legitimate services like Chinese myqcloud CDN and Youdao Cloud Notes to host and deliver its payloads. The malware also leverages DLL side-loading techniques, where a legitimate executable is used to load a malicious DLL, initiating the infection chain without raising immediate suspicion.
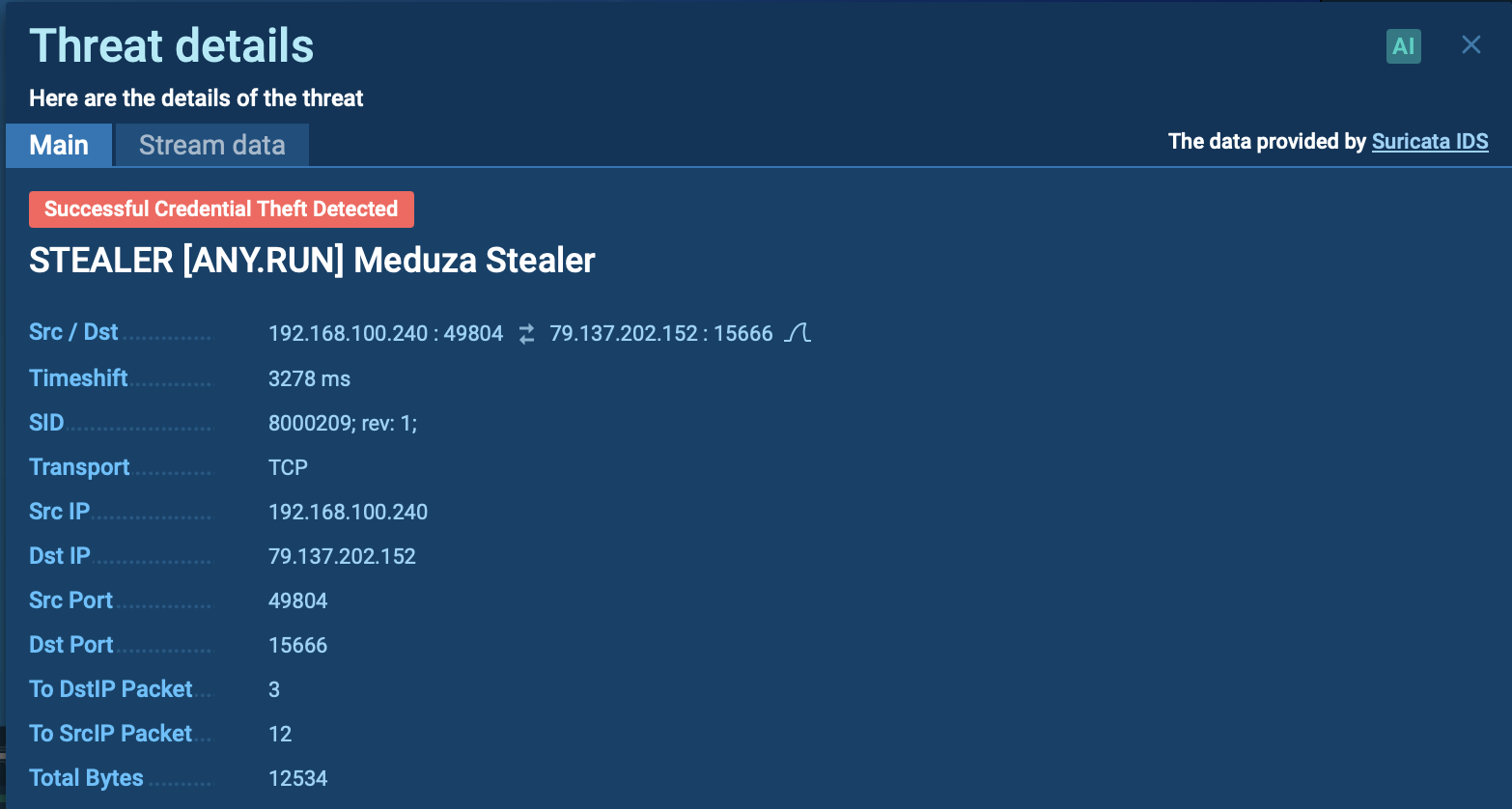
Once inside the network, FatalRAT gathers extensive system information, including external IP addresses, usernames, and details about installed security products, which it exfiltrates to a command-and-control (C2) server over an encrypted channel. It manipulates system settings, for example, disables the CTRL+ALT+DELETE lock function or changing screen resolution.
FatalRAT is sophisticated in evading detection and maintaining access. It performs up to 17 checks to detect virtual machines or sandbox environments and halts execution to avoid analysis if it detects some.
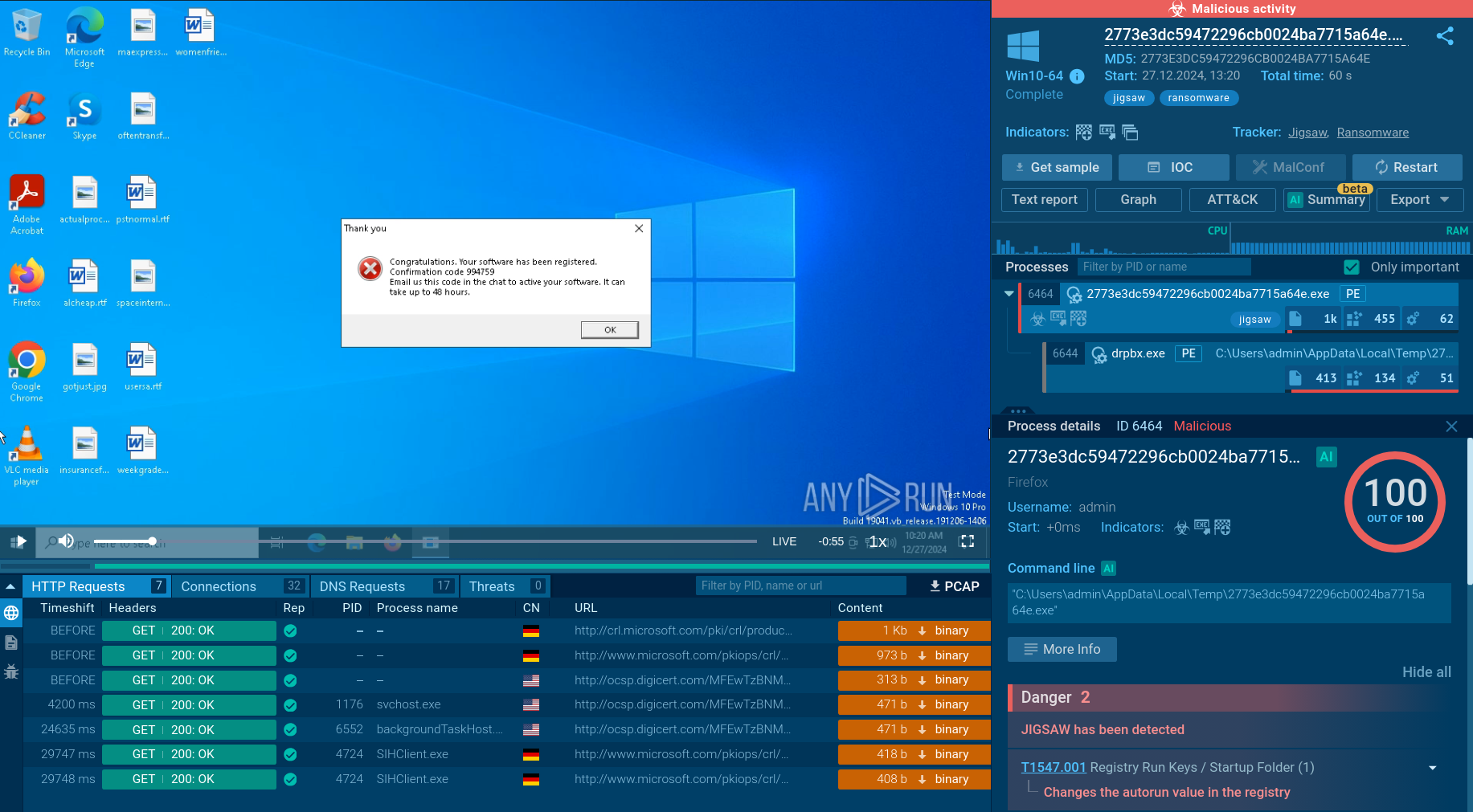
In spite of FatalRAT’s anti-detection and sandbox evasion proficiency, there is quite a selection of FatalRAT analysis sessions in ANY.RUN’s Interactive Sandbox — including fresh samples added by the community just recently.
The attack begins with phishing emails or messages distributed through platforms like WeChat and Telegram. These communications often masquerade as legitimate tax documents or invoices, containing ZIP archives packed with loaders protected by tools such as AsProtect or UPX. Once executed, these loaders retrieve dynamically updated command-and-control (C2) configurations from legitimate cloud services, initiating the infection.
The loader sends HTTP requests to specific URLs, which respond with encrypted JSON containing links to additional modules. To evade detection, malware often abuses legitimate software — such as GoogleUpdate.exe — allowing it to operate surreptitiously within the infected system. It may also modify the registry’s autorun value to add itself, ensuring it starts automatically upon system reboot.
FatalRAT is only deployed after extensive anti-analysis checks, including registry scans for virtual environment artifacts and verification of locale settings to match predefined criteria. Once active, FatalRAT logs keystrokes, exfiltrates sensitive data through encrypted C2 channels, and enables remote control of the victim’s machine. Its capabilities include stealing credentials, capturing screenshots, recording audio and video, and manipulating files and processes on the infected system. This robust feature set makes FatalRAT a potent tool for espionage and data theft across targeted industries.
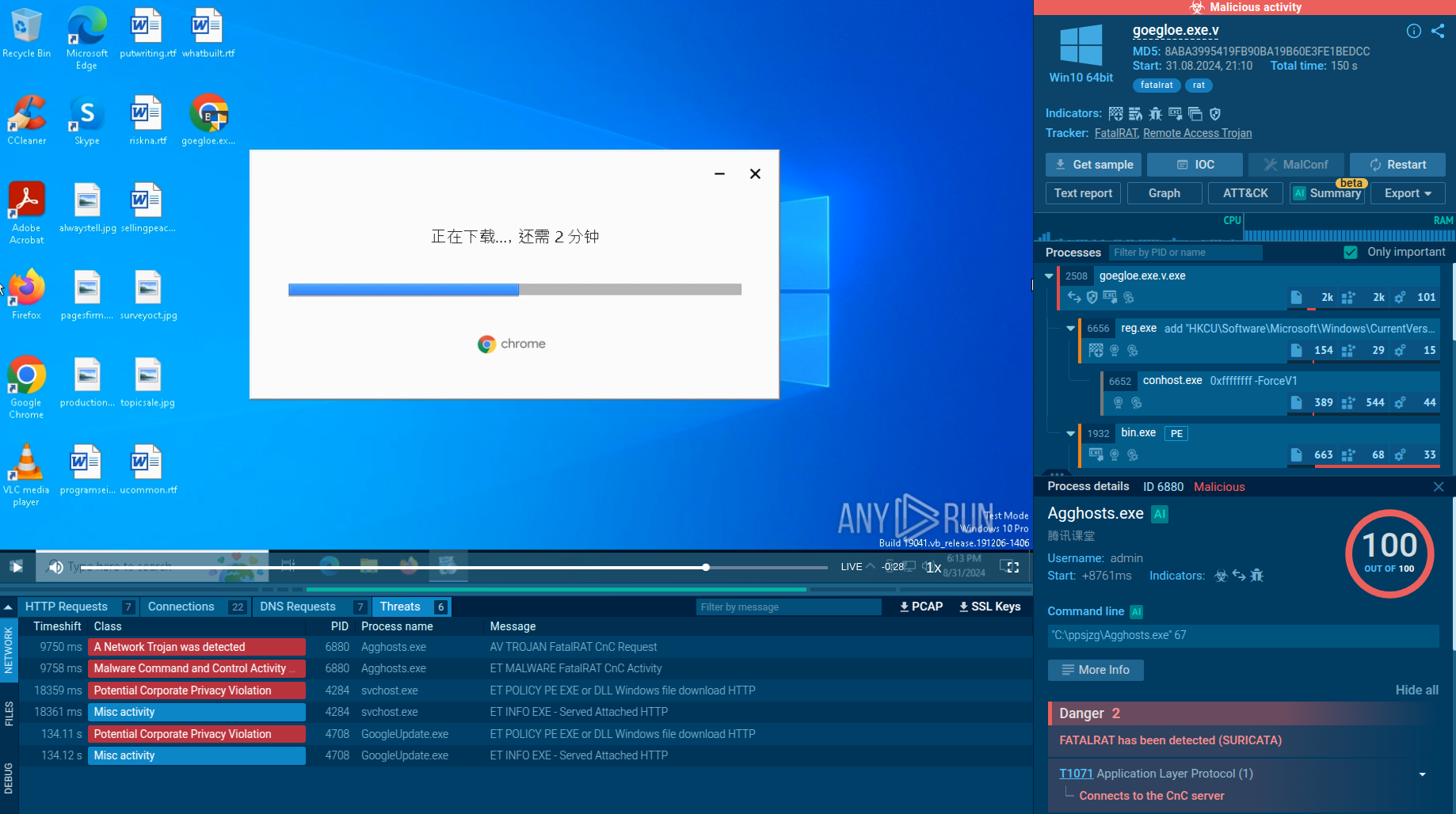 FatalRAT sample detonated inside ANY.RUN's Interactive Sandbox
FatalRAT sample detonated inside ANY.RUN's Interactive Sandbox
Once inside a network, FatalRAT exhibits a wide range of capabilities designed to maximize damage and maintain control:
FatalRAT is relatively new compared to legacy RATs like SubSeven or Poison Ivy, and its attacks are often part of broader, less publicized campaigns attributed to Chinese-speaking groups. FatalRAT’s operations prioritize stealth and long-term access over immediate, headline-grabbing disruption. As a result, specific "named" attacks are scarce.
Threat intelligence helps build proactive defense against threats even as intricate as FatalRAT. Leverage tools like ANY.RUN’s Threat Intelligence Lookup to gather indicators like C2 domains and file hashes and update firewalls and IDS/IPS. Track emerging patterns in APAC-focused campaigns to anticipate new variants.
Via TI Lookup, you can find fresh recently analyzed samples, be sure to get actual IOCs and to stay on top of new tactics and methods of FatalRAT’s beneficiaries.
 FatalRAT new samples
FatalRAT new samples
FatalRAT stands out as a stealthy, multi-faceted threat that blends espionage, disruption, and persistence. Its reliance on legitimate services, advanced evasion tactics, and broad targeting make it a formidable adversary.
By combining robust endpoint monitoring, network analysis, and real-time threat intelligence, organizations can detect and neutralize FatalRAT before it inflicts irreparable damage. Staying vigilant in high-risk regions like APAC and adapting defenses to its evolving tactics are key to staying ahead of this RAT.
Gather IOCs to defend your network against FatalRat with 50 trial requests to TI Lookup