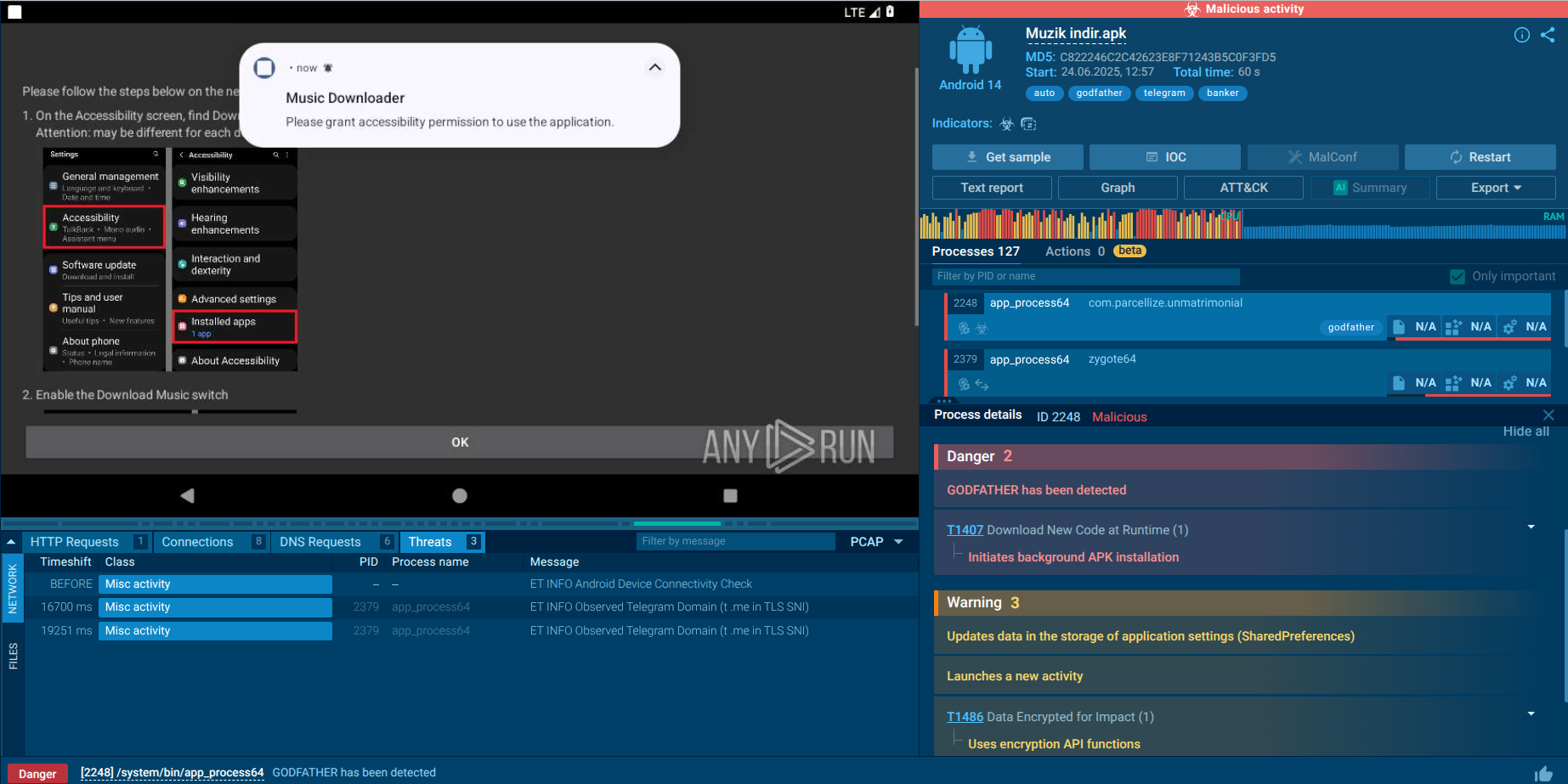
Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


CryptoWall is a notorious ransomware family that emerged in early 2014 and rapidly became one of the most destructive cyber threats of its time. This malware encrypts victims' files using strong AES encryption, demands ransom payments in Bitcoin, and has generated hundreds of millions of dollars for cybercriminals.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
1 January, 2014
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 January, 2014
First seen
:
|
27 February, 2026
Last seen
:
|

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
filePath:"Project_Workshop_7th_Minutes.txt".
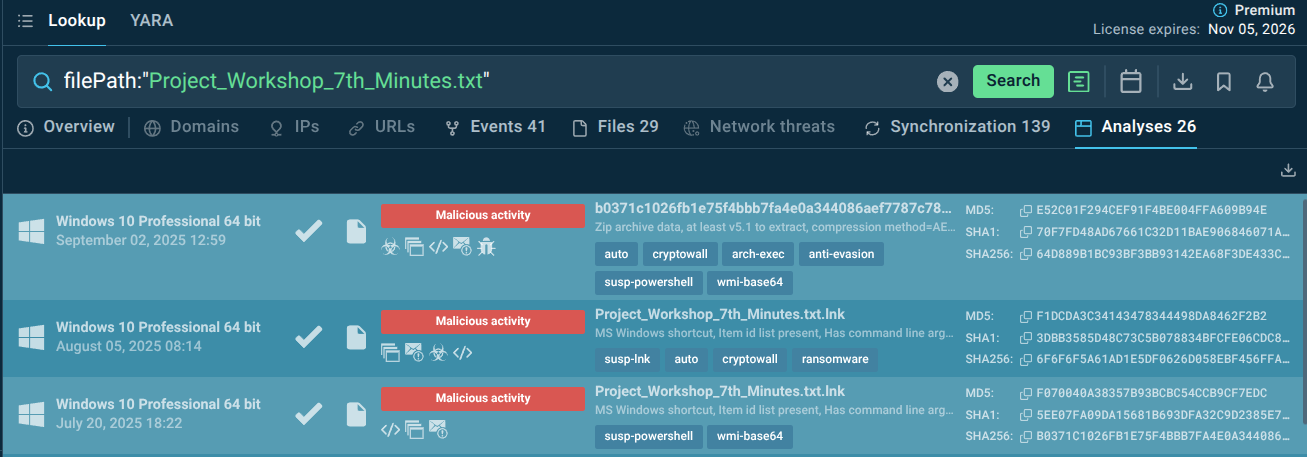 File detected in CryptoWall malware samples via TI Lookup
File detected in CryptoWall malware samples via TI Lookup
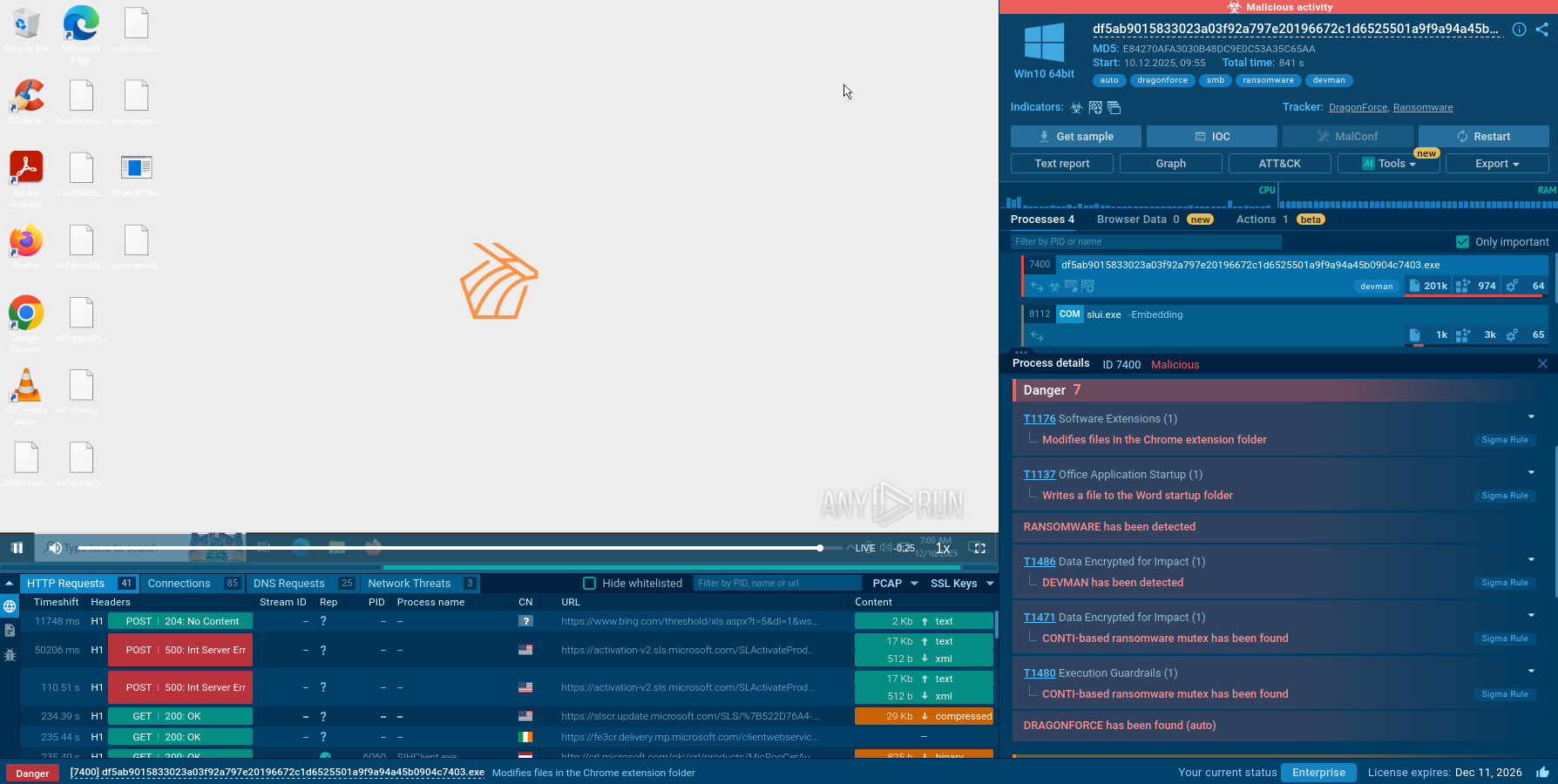
 CryptoWall sample detonated in the ANY.RUN Sandbox
CryptoWall sample detonated in the ANY.RUN Sandbox
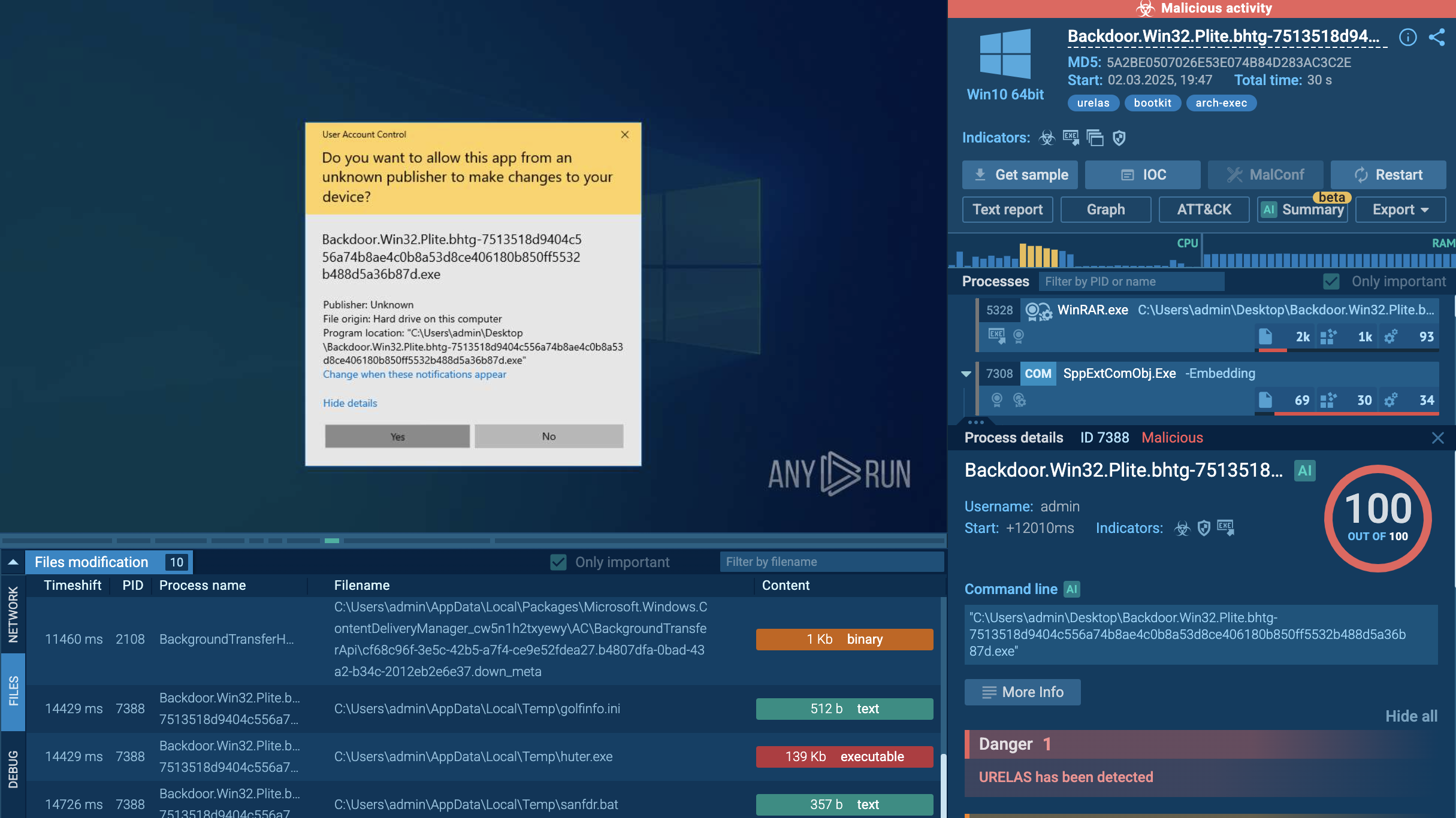
CryptoWall represents a pivotal evolution in ransomware, transforming from a crude CryptoLocker clone into a sophisticated, polymorphic threat. Initially distributed in November 2013, it gained prominence in early 2014, after law enforcement dismantled CryptoLocker's infrastructure. By mid-2015, it has generated an estimated $325 million in revenue for its operators through relentless campaigns.
Unlike earlier ransomware that merely locked screens, CryptoWall employs asymmetric RSA encryption to scramble files across local drives, network shares, and removable media, appending extensions like .cryptowall to affected documents, photos, and databases. Its variants, up to CryptoWall 4.0, incorporated anti-detection techniques, such as Tor and I2P anonymity networks for command-and-control (C2) communication, RC4-encrypted traffic, and polymorphic code to evade antivirus signatures.
The malware communicates with command-and-control servers over the Tor anonymous network, making it difficult to trace or disrupt. After encryption, victims receive detailed ransom notes with instructions for payment, typically ranging from $200 to $10,000, though some victims reportedly paid significantly more. CryptoWall's trademark is its psychological warfare: ransom notes taunt victims with countdown timers, previews of decryptable files to build false hope, and threats to destroy keys if unpaid, often within 72 hours.
What distinguishes CryptoWall from simpler ransomware is its technical sophistication. It operates on both 32-bit and 64-bit systems, deletes shadow copies to prevent file recovery, disables System Restore features, and even installs spyware to steal passwords and Bitcoin wallets. The encryption implementation is effectively unbreakable without the private key held by attackers, making prevention the only viable defense strategy.
The targeting strategy appears opportunistic rather than selective. CryptoWall campaigns have affected individuals who accidentally opened malicious email attachments, businesses whose employees fell victim to phishing schemes, and organizations with unpatched software vulnerabilities. Notable incidents included the Australian Broadcasting Corporation, which experienced disrupted television programming due to a CryptoWall infection, and numerous healthcare organizations that faced operational challenges when patient records became encrypted.
Geographic analysis shows that targets have primarily been concentrated in the United States and United Kingdom, though infections occurred globally. The ransomware infected over 625,000 systems within its first six months of widespread distribution, encrypting approximately 5.25 billion files.
The attack sequence begins when the malware gains initial access through various infection vectors. Email remains the primary distribution method, with attackers using the Cutwail spam botnet sending massive campaigns that contain malicious attachments or links.
When victims open attachments disguised as PDF files, Word documents, or ZIP archives, they actually execute the dropper, which then contacts compromised websites to download the CryptoWall payload. This multi-stage delivery complicates detection, as the initial file may appear benign to security software while the actual ransomware is fetched dynamically.
Exploit kits represent another major infection vector. Major advertising networks serving sites including Disney, Facebook, and The Guardian were compromised in campaigns that exposed millions of users to potential infections.
Within organizational networks, CryptoWall spreads by encrypting files on network shares accessible to the infected user account. While the malware doesn't include worm-like capabilities for self-propagation between systems, its ability to encrypt files across mapped network drives means a single infected endpoint can potentially encrypt data throughout an entire organization.
Upon execution, the ransomware immediately attempts to establish persistence mechanisms, though later variants operate entirely in memory to avoid disk-based detection.
The malware's first critical action involves contacting command-and-control servers, typically hosted on the Tor network for anonymity. This communication serves multiple purposes: retrieving the public key used for encrypting the symmetric encryption keys, registering the victim with a unique identifier, and receiving configuration parameters that control the encryption process. If network connectivity fails, some variants will wait and retry rather than proceeding, as the C2 communication is essential for the attack's success.
Once connected, CryptoWall initiates its file discovery and encryption routine. The malware creates malicious instances of legitimate Windows processes like explorer.exe and svchost.exe to perform its operations, helping it blend with normal system activity. It systematically enumerates all accessible storage, identifying files with targeted extensions. The encryption process uses AES symmetric encryption for speed, with each file receiving a unique AES key. These symmetric keys are then encrypted with an RSA public key, making recovery impossible without the corresponding private key held by attackers.
Throughout the encryption process, CryptoWall takes defensive actions to prevent recovery. It deletes Volume Shadow Copies using the Windows vssadmin.exe utility with commands like "vssadmin delete shadows /all /quiet" to eliminate backup copies without user notification. The malware modifies registry entries to disable System Restore and may clear Windows Event Logs to remove evidence of its activities. Some variants also attempt to disable or evade antivirus software through various techniques including process injection and rootkit-like behaviors.
ANY.RUN's interactive malware sandbox allows analysts to safely execute and analyze CryptoWall samples, revealing evasion techniques, C2 communications, and encryption behaviors that inform detection rules and defensive strategies.
View a CryptoWall sample analysis
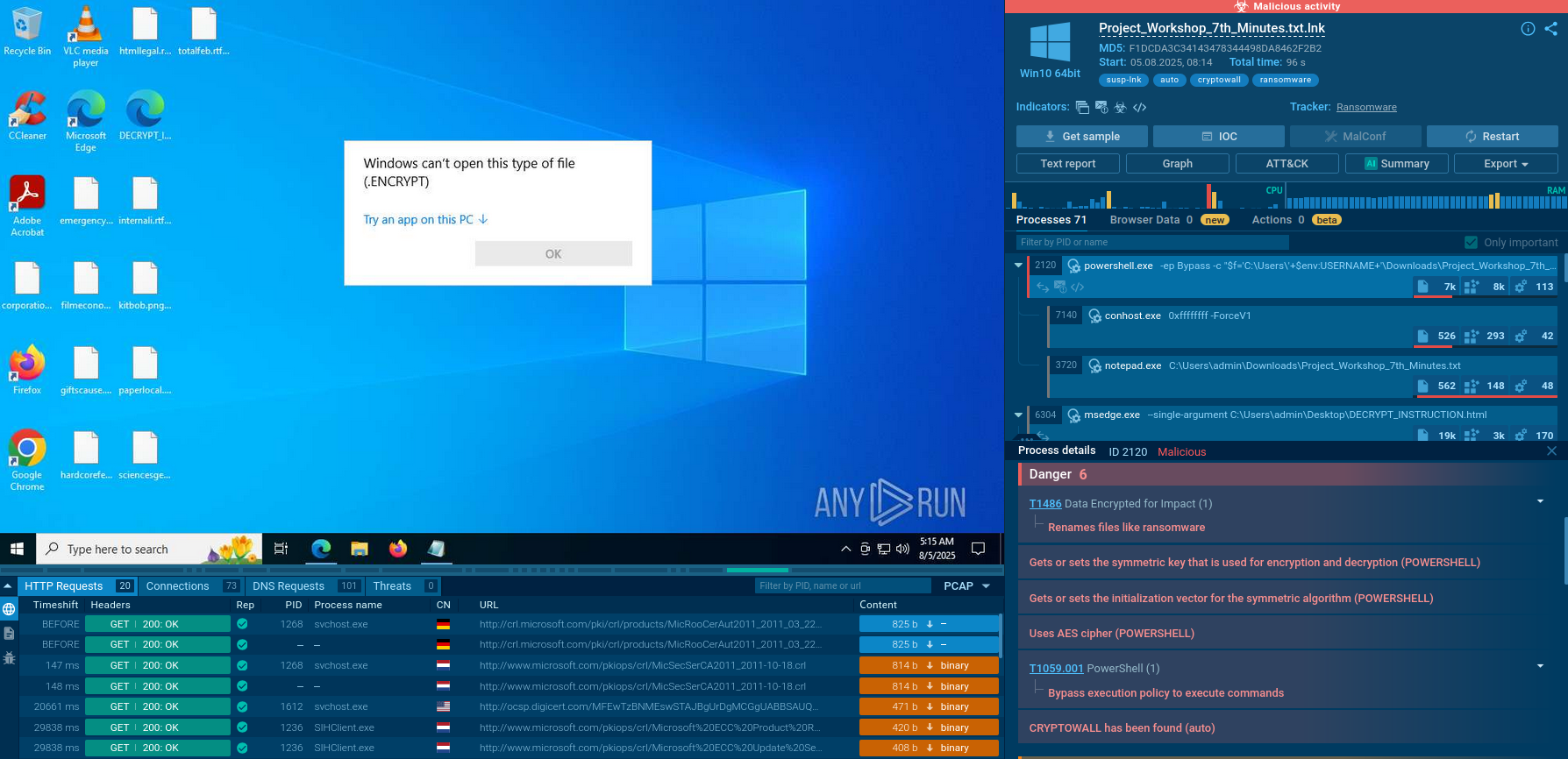 CryptoWall Sandbox analysis
CryptoWall Sandbox analysis
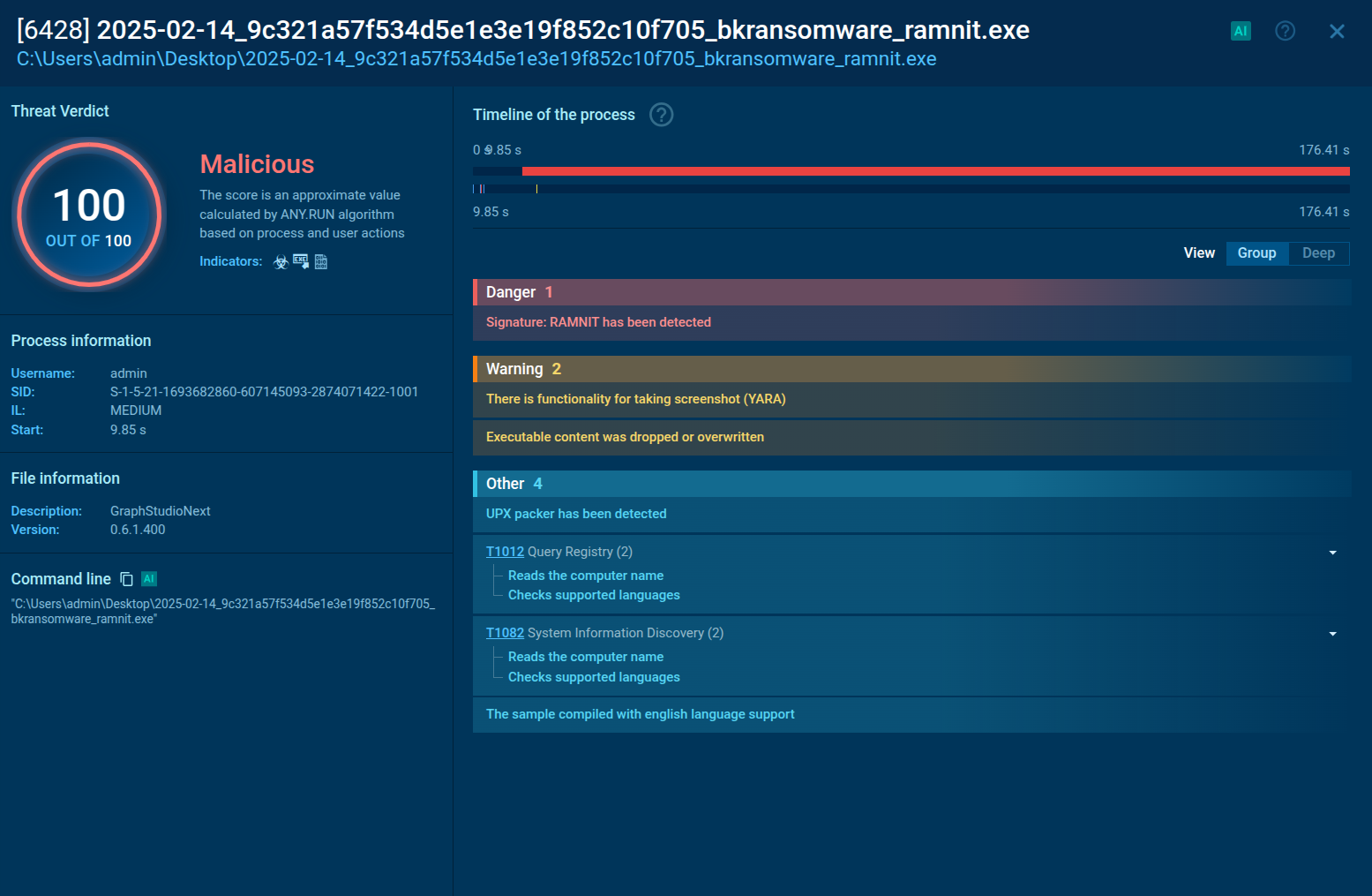
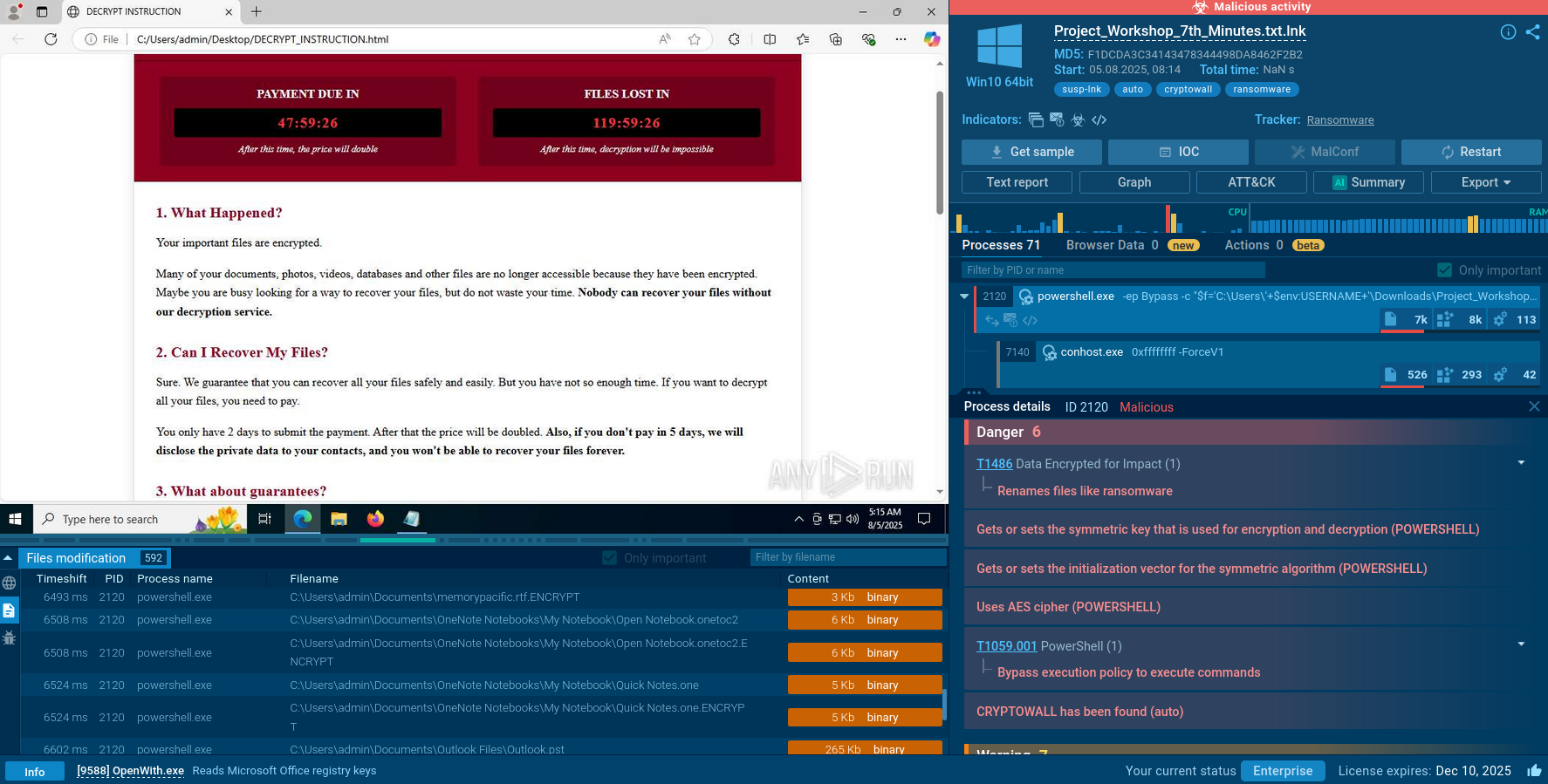
The malware is distributed as an LNK file disguised as a legitimate shortcut. When opened, the LNK launches a PowerShell script that executes the core functionality.
The script tracer of the Sandbox shows how at the start, the malware creates a scheduled task to ensure persistence. The parameters are added: daily mode, no additional day intervals or random delays, and an exact start time of 17:00. Additional options are configured so the task runs even on battery power, does not stop when switching to battery, starts as soon as possible, and ignores the computer's sleep mode.
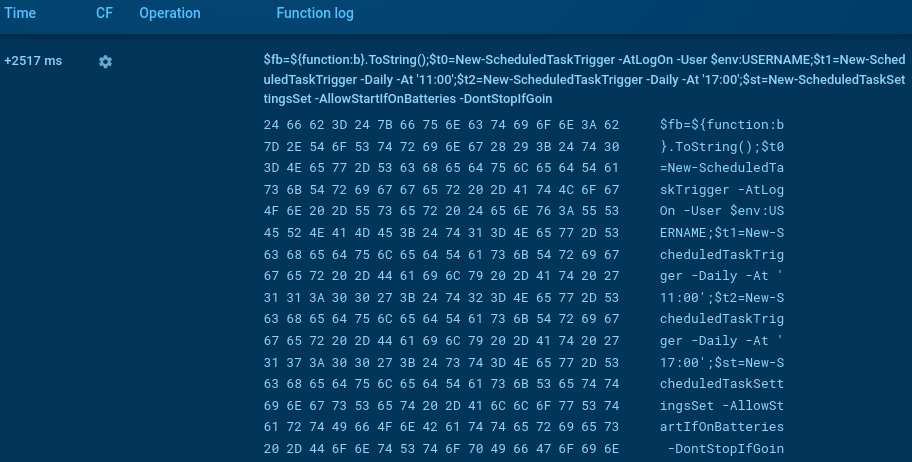 CryptoWall script establishing persistence
CryptoWall script establishing persistence
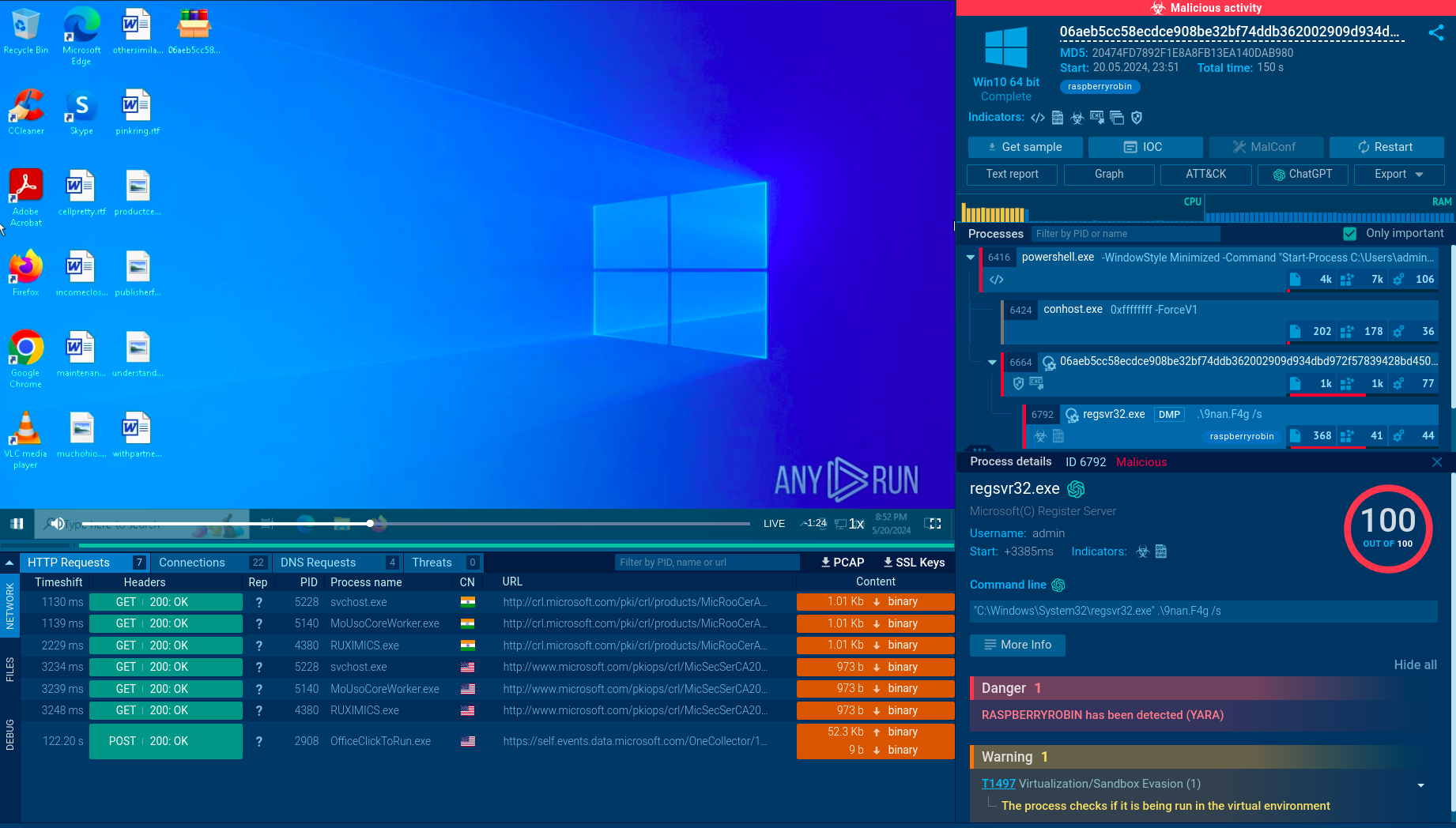
The malicious program also launches Windows Notepad to display the file Project_Workshop_7th_Minutes.txt, created to mask the program's main functionality.
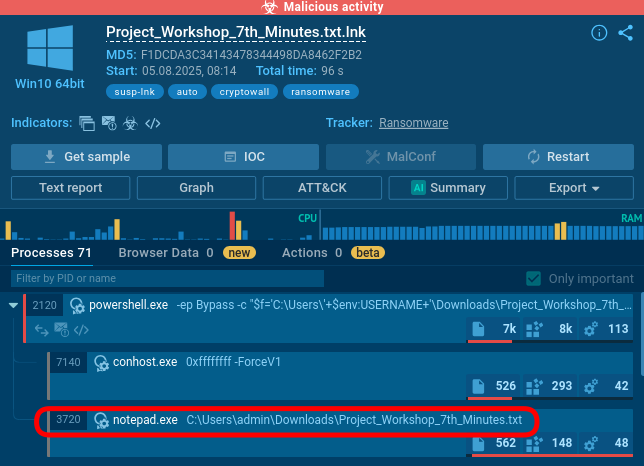 CryptoWall key processes
CryptoWall key processes
The encryption process can be divided into several stages. File discovery occurs recursively through user directories, skipping system folders.
Encryption uses the typical combination of symmetric AES for file encryption. The AES key is encrypted with the attackers' public RSA key. This encrypted AES key, along with the initialization vector and the encrypted file contents, is appended to the end of the file.
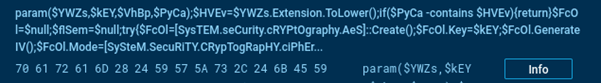 PowerShell commands showing AES key generation and RSA encryption
PowerShell commands showing AES key generation and RSA encryption
A ransom note is created as an HTML file with detailed payment instructions and a timer to pressure the victim into acting quickly.
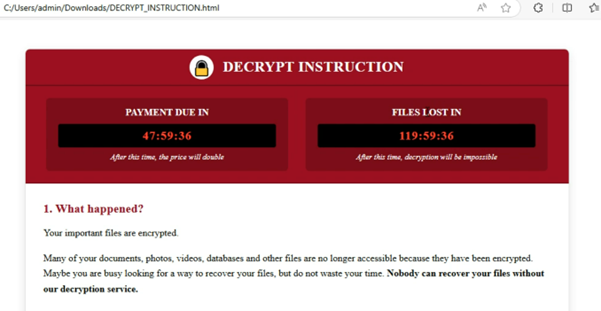 CryptoWall ransom message screenshot with countdown timers for payment and file deletion
CryptoWall ransom message screenshot with countdown timers for payment and file deletion
Overall, CryptoWall is a classic ransomware specimen: a combination of stealthy infection, rapid encryption, and mechanisms to pressure the victim. Regularly back up important files to external media, use up-to-date antivirus software, monitor the Windows Task Scheduler for suspicious entries, disable macros in Office and PDF files, and train users not to open suspicious shortcuts from emails or downloaded files.
For healthcare organizations, CryptoWall infections can delay patient care, limit access to medical records, and force reliance on paper-based systems. Educational institutions face interrupted classes, lost research data, and administrative challenges. Financial services organizations risk regulatory penalties for data security failures, while manufacturing and logistics companies experience supply chain disruptions when production systems become unavailable.
Customers and partners lose confidence in organizations that suffer ransomware attacks, particularly if sensitive data is potentially compromised. Media coverage of infections can damage brand value and market position. Even organizations that successfully recover from attacks often face long-term trust deficits that affect business relationships and customer retention.
Threat Intelligence Lookup enables security teams to quickly search for information about suspicious files, URLs, domains, and IP addresses potentially associated with CryptoWall.
By querying file hashes or URLs encountered in environments, analysts can immediately determine if they match known CryptoWall samples, view detailed behavioral analysis, and understand the specific capabilities and infrastructure of particular variants.
This rapid intelligence access accelerates incident response and enables proactive blocking of threats before they impact systems.
Start exploring the threat by looking it up by the name:
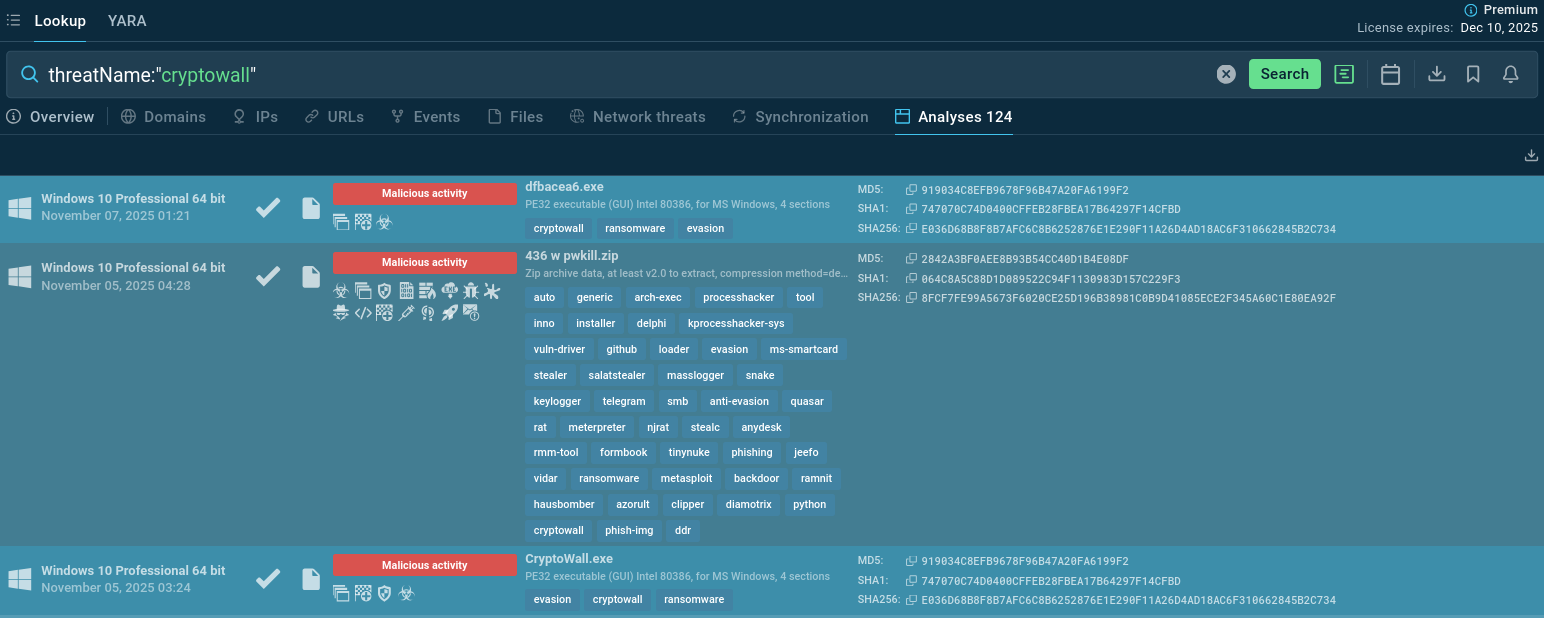 Malware samples with CryptoWall detected, found via TI Lookup]
Malware samples with CryptoWall detected, found via TI Lookup]
CryptoWall demonstrates how cybercriminals can weaponize strong encryption to generate hundreds of millions of dollars while causing widespread organizational disruption. Though newer ransomware families have emerged since CryptoWall's peak activity, the fundamental threat model it established (combining multiple infection vectors, strong encryption, anonymous infrastructure, and cryptocurrency payments) persists across modern ransomware operations.
Modern threat intelligence and analysis tools have evolved significantly in response to threats like CryptoWall. Malware sandboxes, threat intelligence platforms, and security automation enable faster detection, more effective response, and proactive defense strategies that were unavailable during CryptoWall's emergence. Organizations that leverage these capabilities while maintaining security fundamentals position themselves to resist not only CryptoWall variants that may still circulate but also the next generation of ransomware threats.
Start gathering actionable threat intelligence on CryptoWall by signing up to ANY.RUN’s TI Lookup: protect your business with timely detection and response.