Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Tykit is a sophisticated phishing-as-a-service (PhaaS) kit that emerged in May 2025, designed to steal Microsoft 365 corporate credentials through an innovative attack vector: malicious SVG files.
|
Phishingkit
Type
:
|
Unknown
Origin
:
|
|
1 April, 2025
First seen
:
|
5 January, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 April, 2025
First seen
:
|
5 January, 2026
Last seen
:
|

 787
787
 0
0

 478
478
 0
0

 2728
2728
 0
0
Use ANY.RUN’s Threat Intelligence Lookup to search by domain patterns, explore Tykit samples, gather additional IOCs for detection.
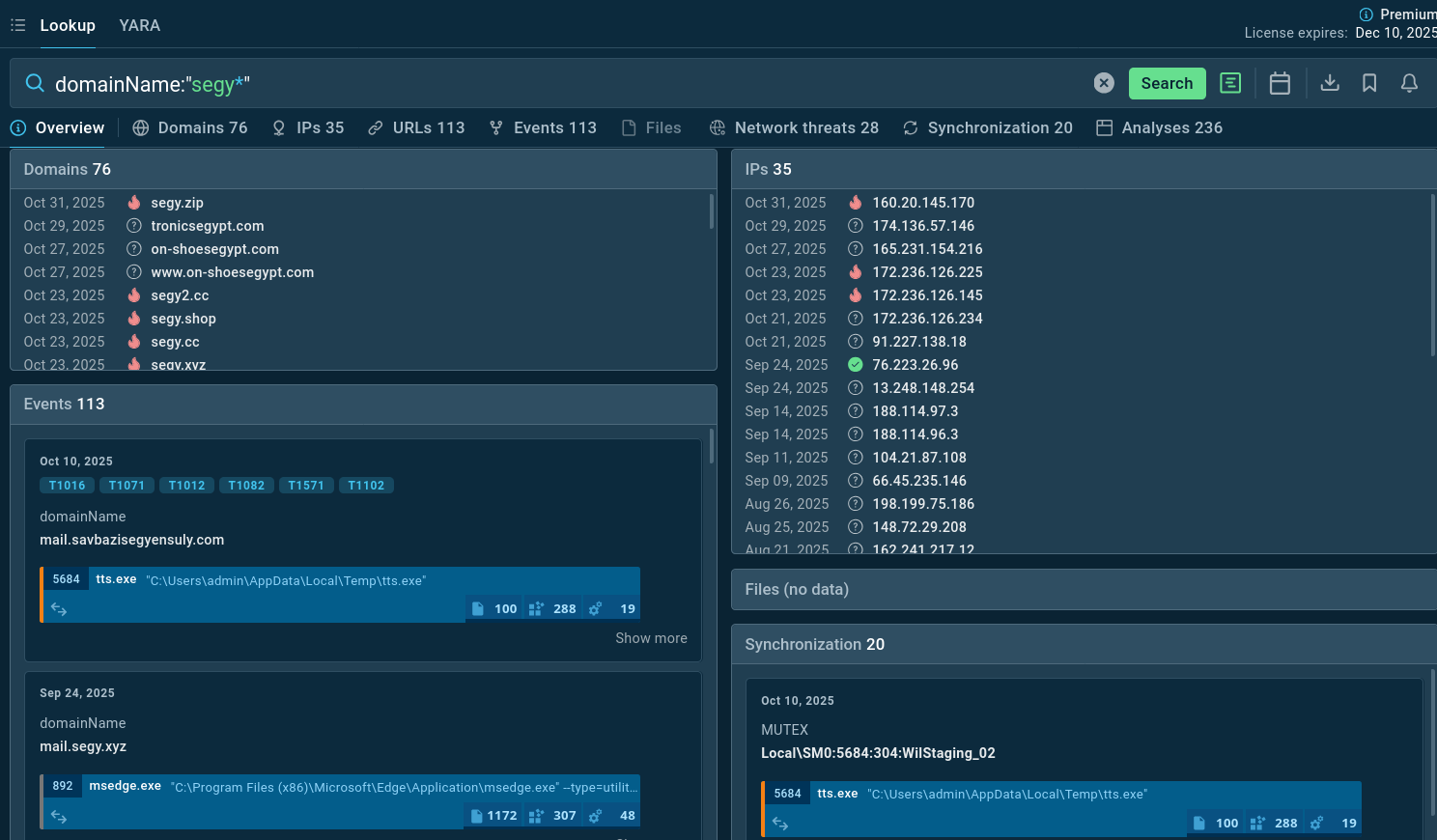 Domains linked to Tykit campaigns found via TI Lookup
Domains linked to Tykit campaigns found via TI Lookup
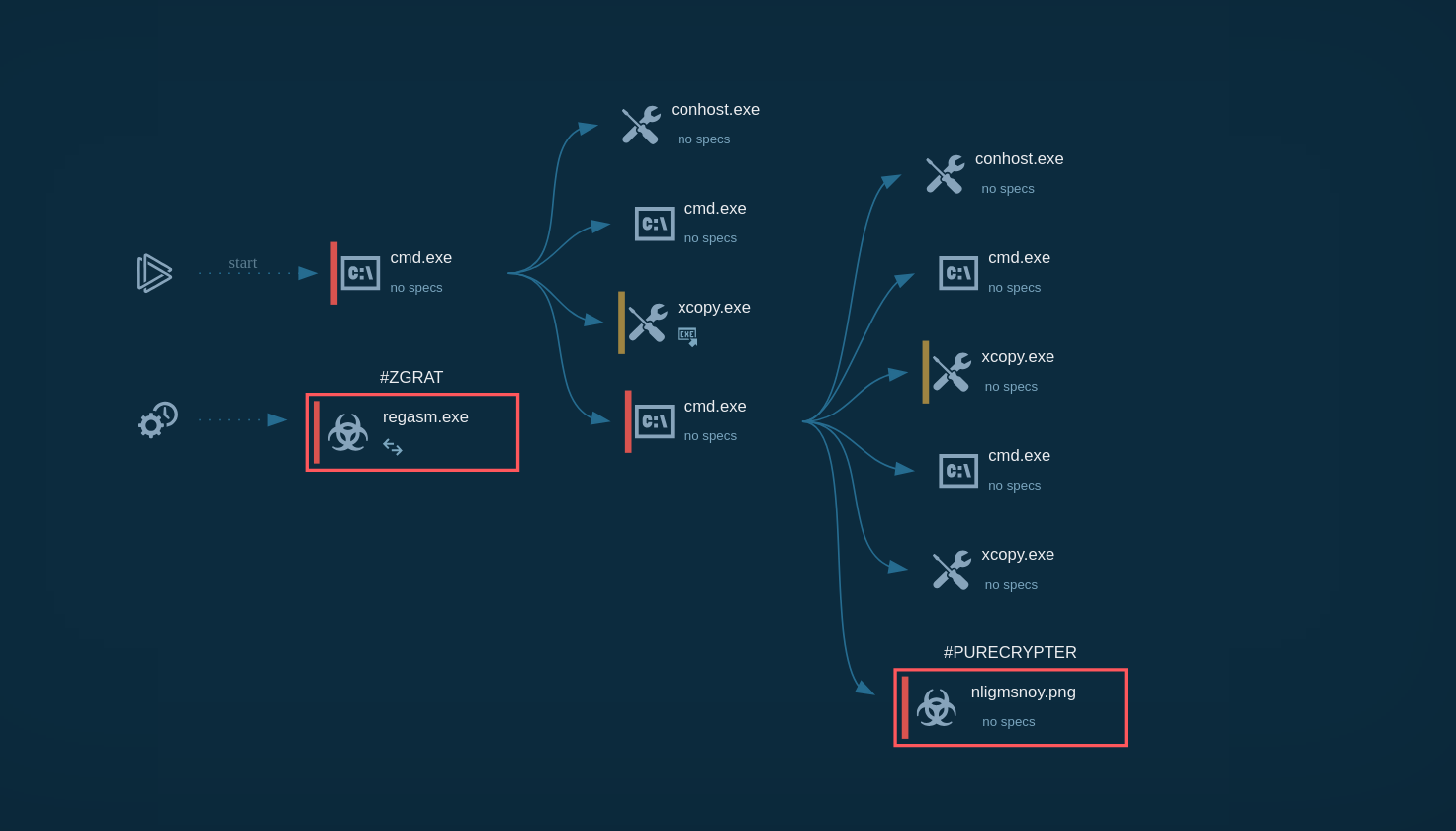
View a Tykit analysis session in the sandbox:
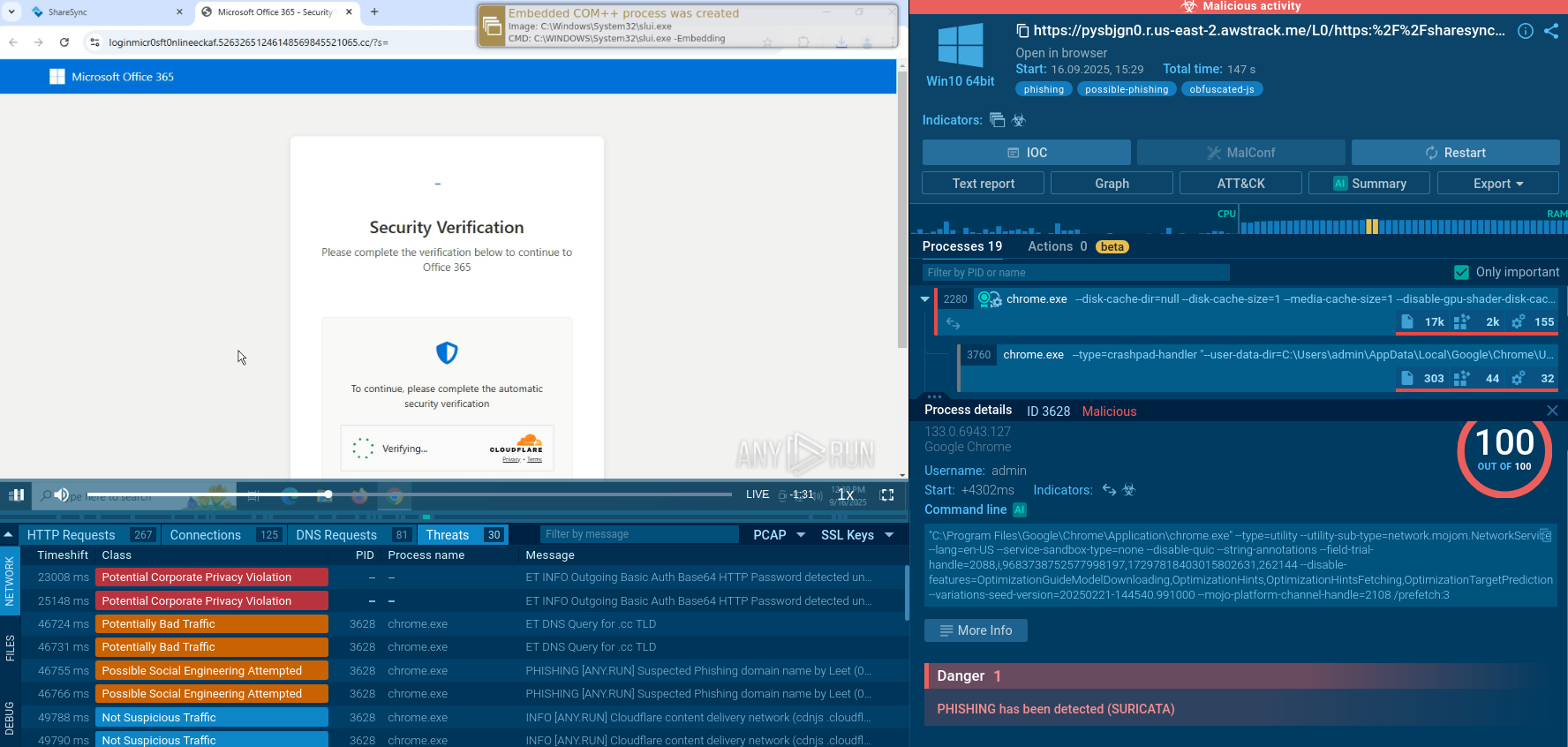 Tykit sample detonated in the ANY.RUN Sandbox
Tykit sample detonated in the ANY.RUN Sandbox
Tykit emerges in 2025 as a phishing kit that departs from simpler credential-stealers by embedding JavaScript inside SVG image files. These SVGs act as stealthy “redirectors” or “trampolines” rather than being seen as overt phishing HTML pages.
Once the victim interacts (for example, being prompted to “enter the last 4 digits of your phone number” within the SVG), the flow proceeds through a trampoline script or intermediate redirect, then to a phishing page (often imitating Microsoft 365).
The phishing landing page typically contains a Cloudflare Turnstile anti-bot / CAPTCHA widget to block automated scanners or bots, then shows a fake Microsoft login portal. After credential submission, JSON-style API calls are made to attacker-controlled domains (often containing “segy” strings) to validate or exfiltrate data.
Researchers have observed that many samples share nearly identical code structure, obfuscation, domain naming patterns, redirect logic, and C2 endpoints. This suggests a templated (or service) model rather than one-off bespoke campaigns.
The first recorded sightings in ANY.RUN’s sandbox traces date to May 2025, with campaign activity peaking in September – October 2025. Tykit has been identified targeting organizations across various sectors globally (US, Canada, EMEA, Southeast Asia) and particularly in industries that rely heavily on Microsoft 365 and corporate email: finance, government, IT, construction, professional services, telecommunications, real estate, education, etc.
Because the core mechanism is phishing / credential capture (rather than remote code execution, file encryption, etc.), it is often classified in reports as a phishing kit rather than a “malware” in the classic sense. But its sophistication, multi-stage execution, use of obfuscation and anti-detection controls, and templated reuse give it traits worth analyzing like malware
Tykit primarily preys on corporate users in sectors handling sensitive data, with finance and construction leading the pack due to their reliance on Microsoft 365 for financial transactions and project management.
Other targeted industries include IT, professional services, government, and telecommunications, where quick access to cloud resources is critical.
Geographically, North American companies, particularly in the US and Canada, face the brunt, followed by European entities in the EMEA region and Southeast Asian firms.
Victims are often mid-to-large organizations with distributed workforces, making them vulnerable to phishing via email attachments disguised as invoices or diagrams—common lures in construction and finance.
The kit's global reach shows no favoritism toward small businesses; instead, it exploits the ubiquity of Microsoft 365, affecting over 15,000 organizations tracked in related threat reports.
Tykit employs a multi-stage attack architecture designed to evade detection while maximizing credential harvesting efficiency.
Stage 1: Initial Delivery via SVG
The attack begins with an SVG file, typically delivered through phishing emails as an attachment or embedded link. SVG files are XML-based vector image formats that can contain embedded scripts. Tykit exploits this by hiding JavaScript code within the SVG structure.
The malicious code uses XOR encoding and reconstruction techniques to rebuild the payload, which then executes via the dangerous eval() function. This approach bypasses many email security gateways that don't deeply inspect SVG contents, treating them as simple image files.
Stage 2: Trampoline Redirection
When the victim opens the SVG file in their browser, the embedded JavaScript executes automatically, redirecting them to a "trampoline" page (an intermediate server that performs additional checks and forwards the victim to the main phishing infrastructure).
The trampoline typically includes a fake verification step, such as prompting victims to "enter the last 4 digits of your phone number" (though any input is accepted). This creates a false sense of security and legitimacy while collecting additional targeting data.
The victim's email address is encoded in Base64 and passed as a URL parameter (e.g., ?s=[base64-encoded-email]), allowing the phishing page to personalize the attack.
Stage 3: Anti-Bot Protection
The victim is then presented with a Cloudflare Turnstile CAPTCHA, which serves dual purposes:
The phishing page also implements basic anti-debugging techniques:
Stage 4: Phishing Page Presentation
After passing the CAPTCHA, victims reach a convincing Microsoft 365 login page that closely mimics the legitimate interface, including:
Stage 5: Credential Exfiltration via API Calls
When victims enter their credentials, obfuscated JavaScript captures the data and transmits it through a series of API calls to the attacker's C2 servers:
POST to /api/validate: Validates the submitted email address and determines next steps
POST to /api/login: Exfiltrates credentials, including email addresses, passwords, expired JWT tokens (for authenticity), session data.
POST to /x.php: Secondary logging endpoint for debugging or additional data collection.
The server response dictates the victim's experience:
This multi-request architecture allows attackers to validate credentials in real-time, immediately identifying high-value accounts and potentially bypassing MFA through AitM techniques.
Evasion / anti-detection measures observed:
To sum up: Tykit’s functionality is not a binary dropper or red team tool, but a cleverly engineered front-end phishing kit with multiple stages, obfuscation, anti-bot measures, and template reuse.
SOC teams can quickly identify Tykit attacks using ANY.RUN’s Interactive Sandbox, which provides a fast, safe, virtual environment for hands-on analysis of malware and phishing.
Check out sandbox analysis of Tykit
Initial Delivery: Common Vectors
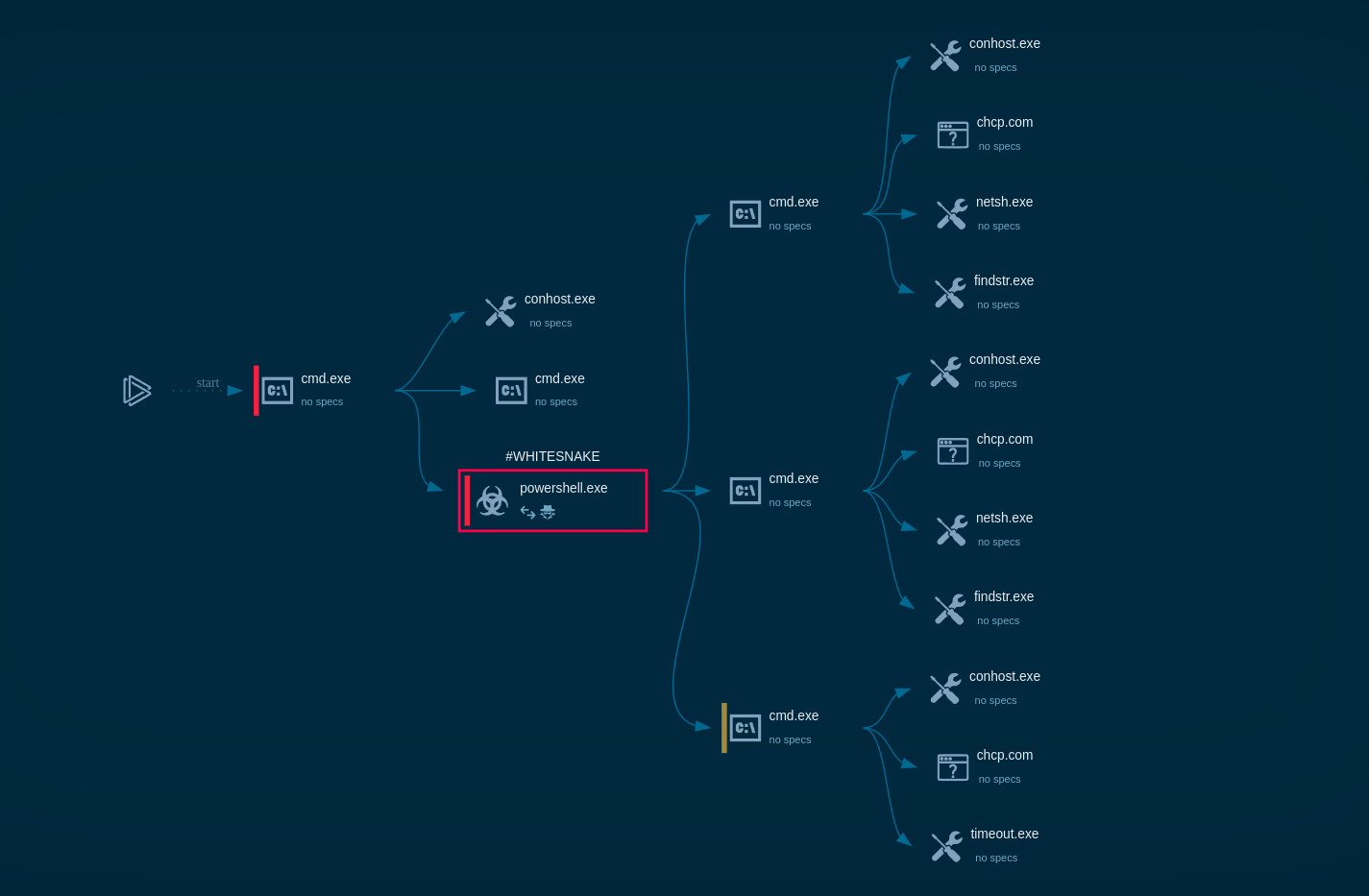
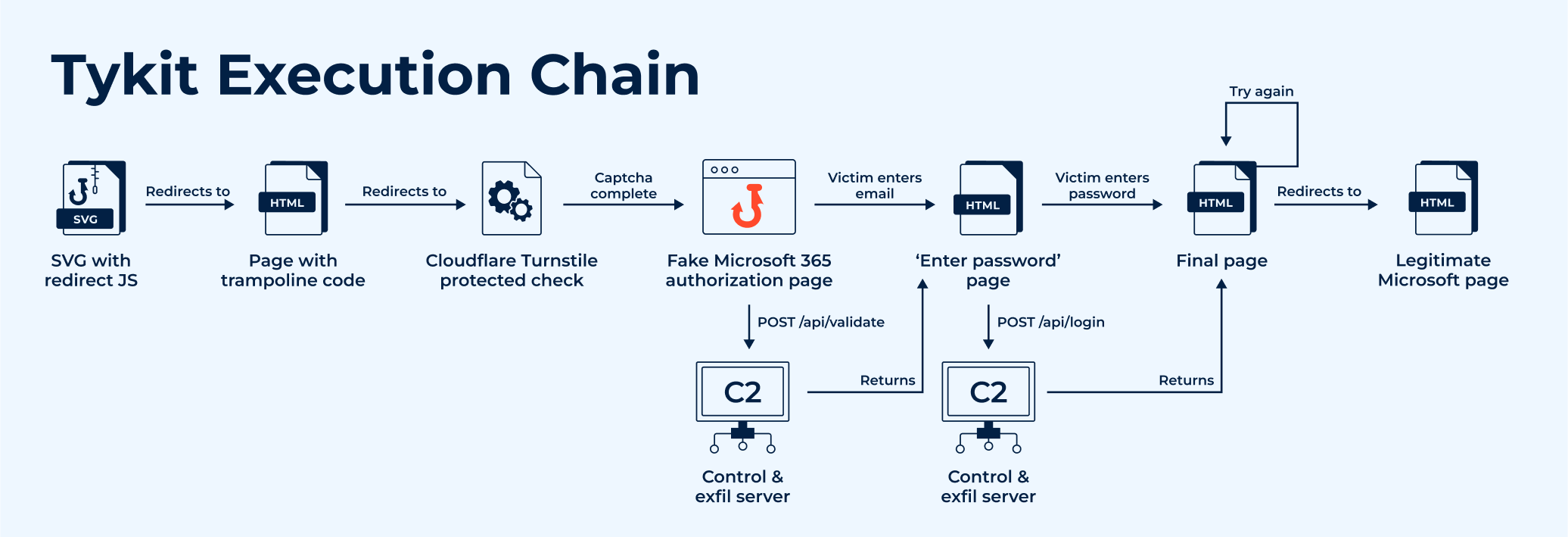 A common kill chain of a Tykit attack
A common kill chain of a Tykit attack
Tykit phishing attacks tend to start with SVG images that redirect the browser to a fraudulent page. These files typically feature deceptive prompts, such as a "check stub" asking users to input seemingly harmless information, like the last four digits of a phone number, though any input is usually accepted to proceed.
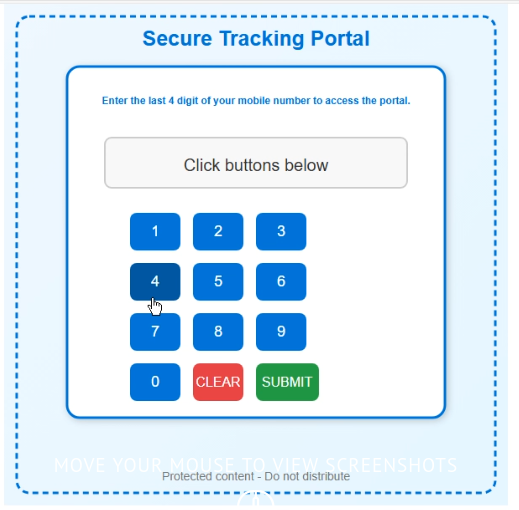 Fake prompt asking the user to enter phone digits
Fake prompt asking the user to enter phone digits
Trampoline and CAPTCHA Stage
After the initial interaction, the page redirects to a trampoline script, which then forwards the victim to the main phishing site. The URL often includes encoded parameters, such as the victim’s email in Base64 format.
The next step usually involves a CAPTCHA page, often using Cloudflare Turnstile or similar anti bot protections. These pages may also incorporate basic anti debugging techniques, like blocking DevTools access or disabling the context menu, to hinder analysis.
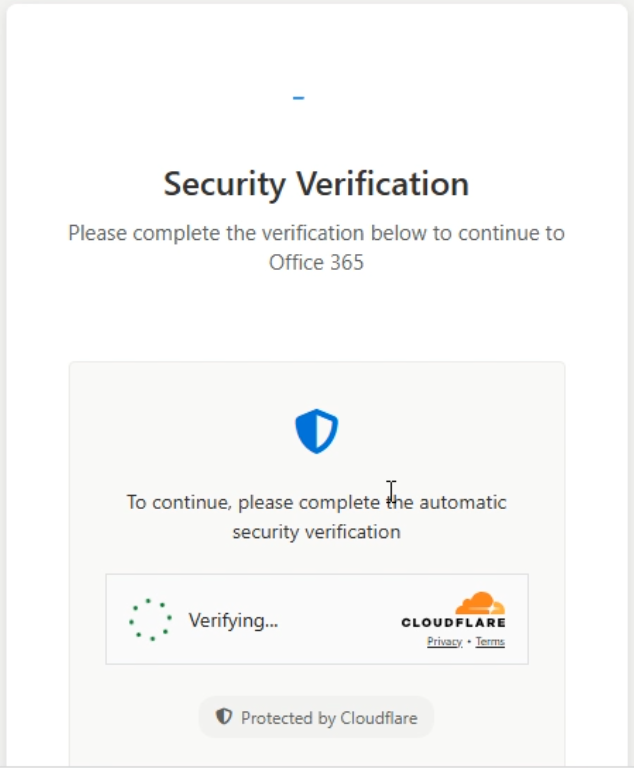 Tykit uses anti-bot protection on the phishing page using Cloudflare Turnstile
Tykit uses anti-bot protection on the phishing page using Cloudflare Turnstile
Credential Capture and C2 Communication
Once the CAPTCHA is bypassed, victims encounter a spoofed login page, commonly mimicking trusted services like Microsoft 365. Simultaneously, a background request is sent to the command and control (C2) server, typically at an endpoint like /api/validate. This request includes a session or license key, a redirect URL, and the victim’s decoded email. The C2 server responds with instructions for the next stage, often embedded in HTML, along with a status update.
Password Exfiltration and Final Actions
The final stage usually presents a password entry form. Obfuscated JavaScript embedded in the page handles the exfiltration of stolen credentials to the C2 server, often via a POST request to an endpoint like /api/login. This request typically includes the victim’s email, password, an authorization token (sometimes expired), and other metadata.
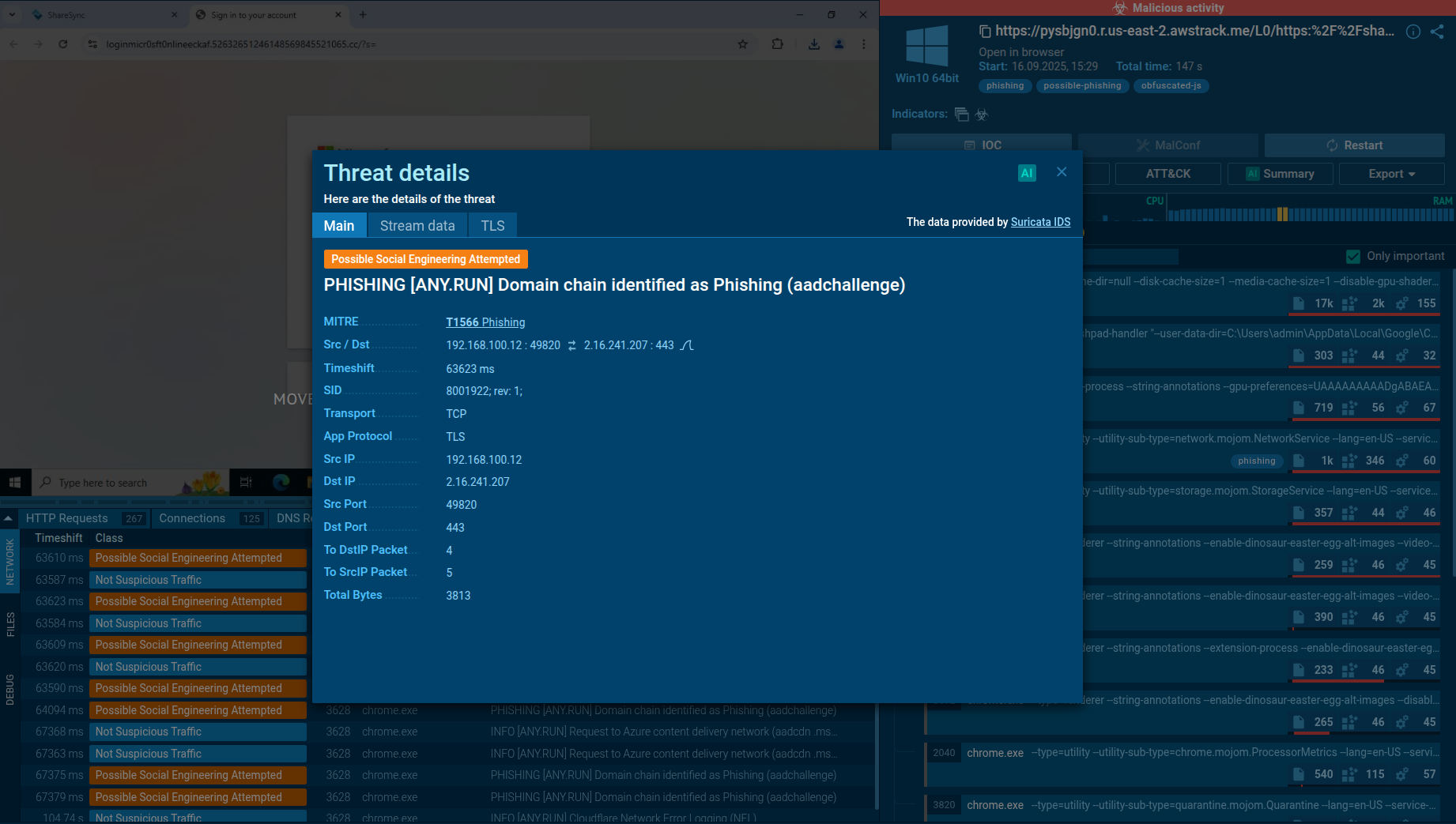 ANY.RUN's Interactive Sandbox automatically detects Tykit attacks
ANY.RUN's Interactive Sandbox automatically detects Tykit attacks
The server’s response dictates subsequent actions, such as rendering additional HTML, triggering debugging processes, or displaying fake error messages to maintain the illusion of legitimacy.
Although the toolkit itself is not destructive, its threat to organizations is serious because:
Credential compromise leads to further attacks
Evasion and persistence
Scale and reuse
Indirect risks
Thus, Tykit's danger is its role as a stepping stone: the initial breach vector that enables far more serious intrusions.
Detection of Tykit is challenging because it is a phishing kit (not a file-based payload). But TI solutions like ANY.RUN’s Threat Intelligence Lookup help with connecting indicators of compromise to the phishkit’s activities and mining additional IOCs.
TI helps map the evolution of Tykit (new domains, variant payloads, new redirect patterns), enabling defenders to anticipate new waves or clusters.
Start exploring the threat by looking it up by the name:
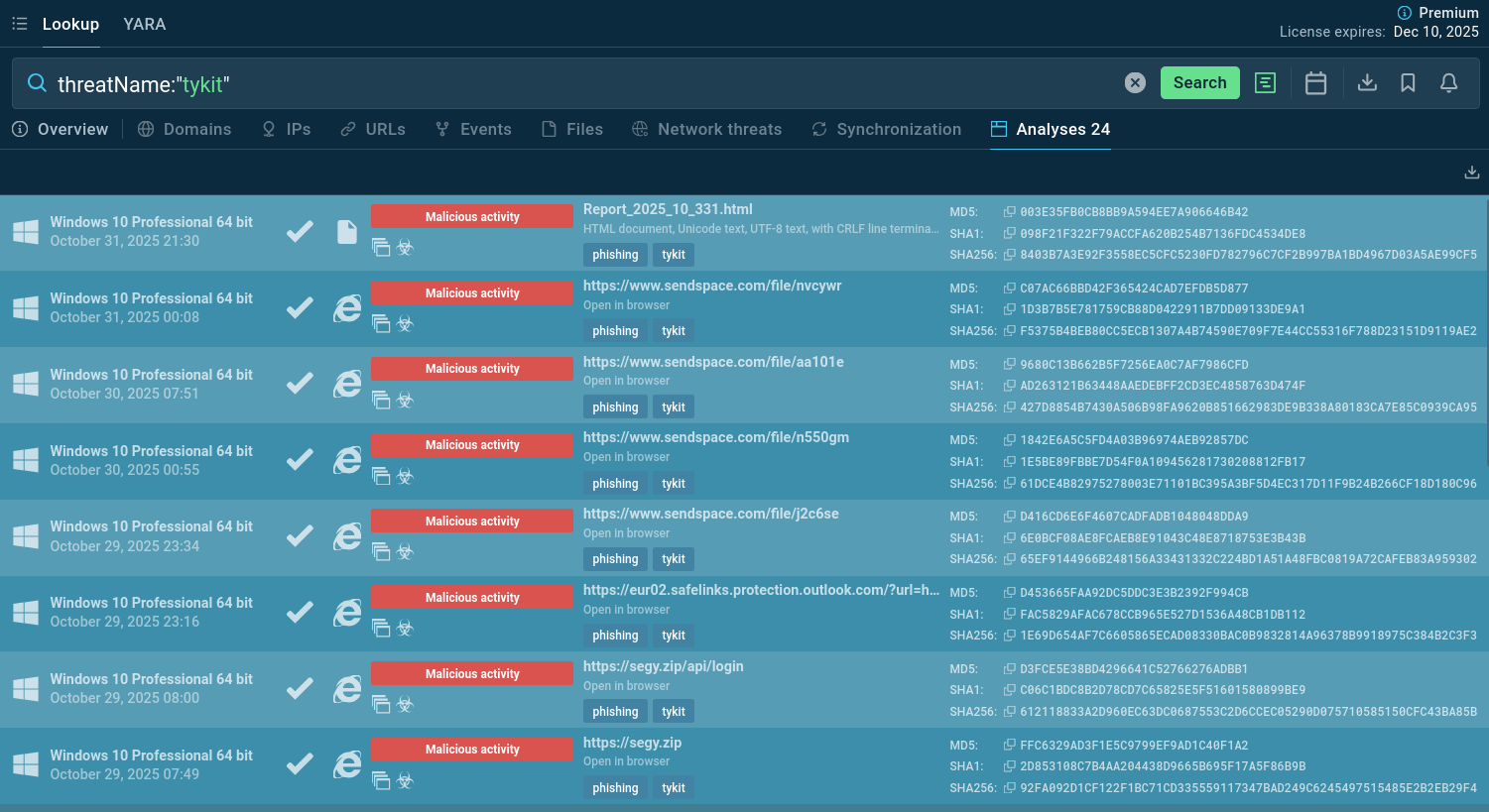 Tykit samples submitted to the Sandbox
Tykit samples submitted to the Sandbox
Tykit is a rising phishing kit threat that leverages SVG attachments, multi-stage redirects, and obfuscation logic to steal Microsoft 365 credentials. Though it doesn’t drop malware on endpoints itself, its consequences can be severe, enabling email compromise, lateral movement, and further attacks.
Because of its phishing-based nature, the most effective defenses lie in preventative controls (MFA, conditional access, email filtering), behavioral detection, and threat intelligence to rapidly identify new variants.
Sandboxes like ANY.RUN help uncover Tykit’s execution logic and support pivoting, while TI feeds help defenders block known infrastructure and hunt unknown variants. Together, these solutions and strategies form a layered defense against credential-harvesting kits like Tykit.
Start gathering actionable threat intelligence on Tykit by signing up to ANY.RUN’s TI Lookup: protect your business with timely detection and response.