Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


ACR Stealer is a modern information-stealing malware designed to harvest sensitive data from infected devices. Like other infostealers, it targets credentials, financial details, browser data, and files, enabling cybercriminals to monetize stolen information through direct fraud or underground market sales.
|
Stealer
Type
:
|
Unknown
Origin
:
|
|
1 March, 2024
First seen
:
|
14 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 March, 2024
First seen
:
|
14 February, 2026
Last seen
:
|

 779
779
 0
0

 476
476
 0
0

 2720
2720
 0
0
ACR Stealer is a sophisticated information-stealing software sold as a Malware-as-a-Service (MaaS) on underground forums, primarily targeting credentials, browser data, and cryptocurrency wallets to facilitate identity theft and financial fraud.
It is lightweight, fast, and capable of exfiltrating a broad spectrum of data types, including login credentials, cryptocurrency wallet information, and system fingerprints. Its developers continuously update the malware to bypass traditional defenses, making it a persistent threat in the cybercrime ecosystem. According to Stamus Networks, ACR Stealer is an evolved version of GrMsk Stealer, which had been privately sold by the threat actor SheldIO since around July 2023. In 2025, Proofpoint researchers confirmed that ACR Stealer was significantly updated and rebranded as Amatera Stealer. Key enhancements included improved anti-analysis features and a shift away from previously used C2 mechanisms like Steam/Telegram dead drops.
ACR Stealer operates by injecting itself into system processes to avoid detection, then systematically scans the endpoint for valuable data. It uses encryption to obfuscate stolen information before exfiltrating it to C2 servers, sometimes leveraging unconventional platforms like Google Docs for command retrieval. The malware employs dead drop resolvers for dynamic C2 resolution, enhancing its resilience against takedowns. Variants like Amatera introduce advanced string obfuscation and virtual machine checks to evade sandboxes and antivirus software.
ACR Stealer commonly spreads through:
While primarily single-device malware, once credentials are stolen, attackers often use them to move laterally within corporate networks.
ACR Stealer targets a broad spectrum of victims, with no specific industry or demographic limitation. The malware's distribution methods suggest that it primarily affects:
The distribution trend of ACR Stealer from June 2024 to February 2025 indicates a dramatic rise in 2025, suggesting an expanding victim base and increased threat actor adoption of this malware family.
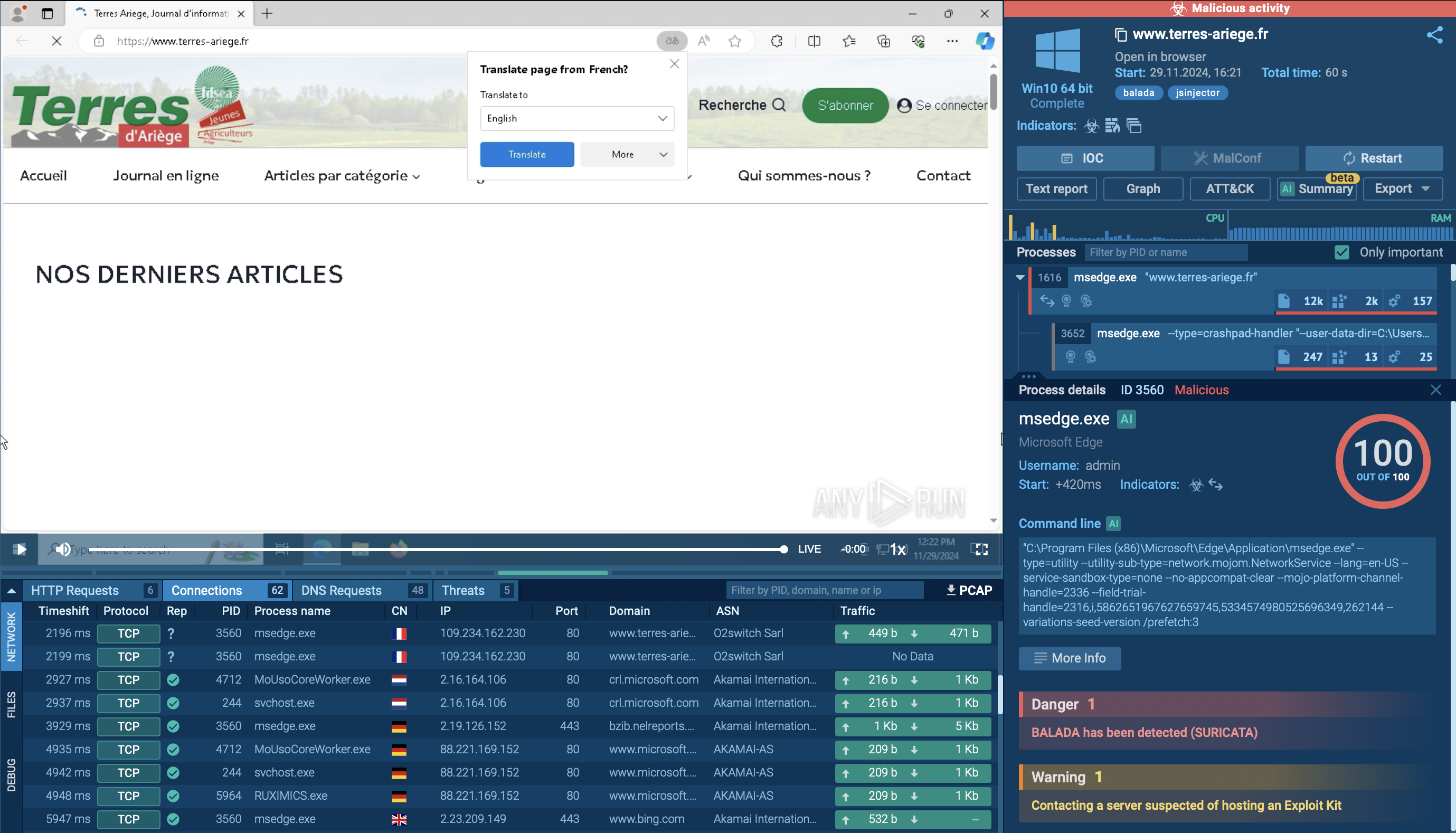
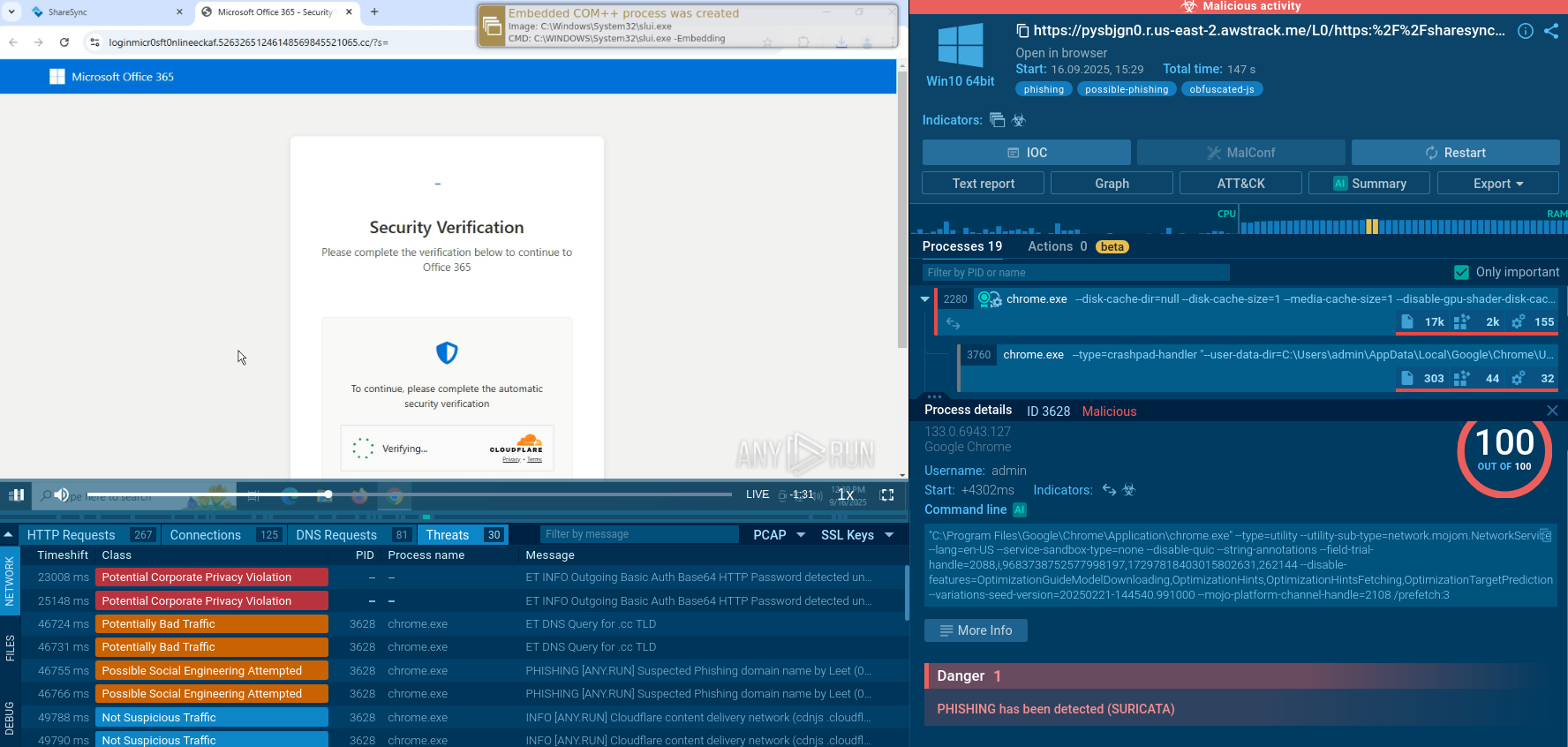
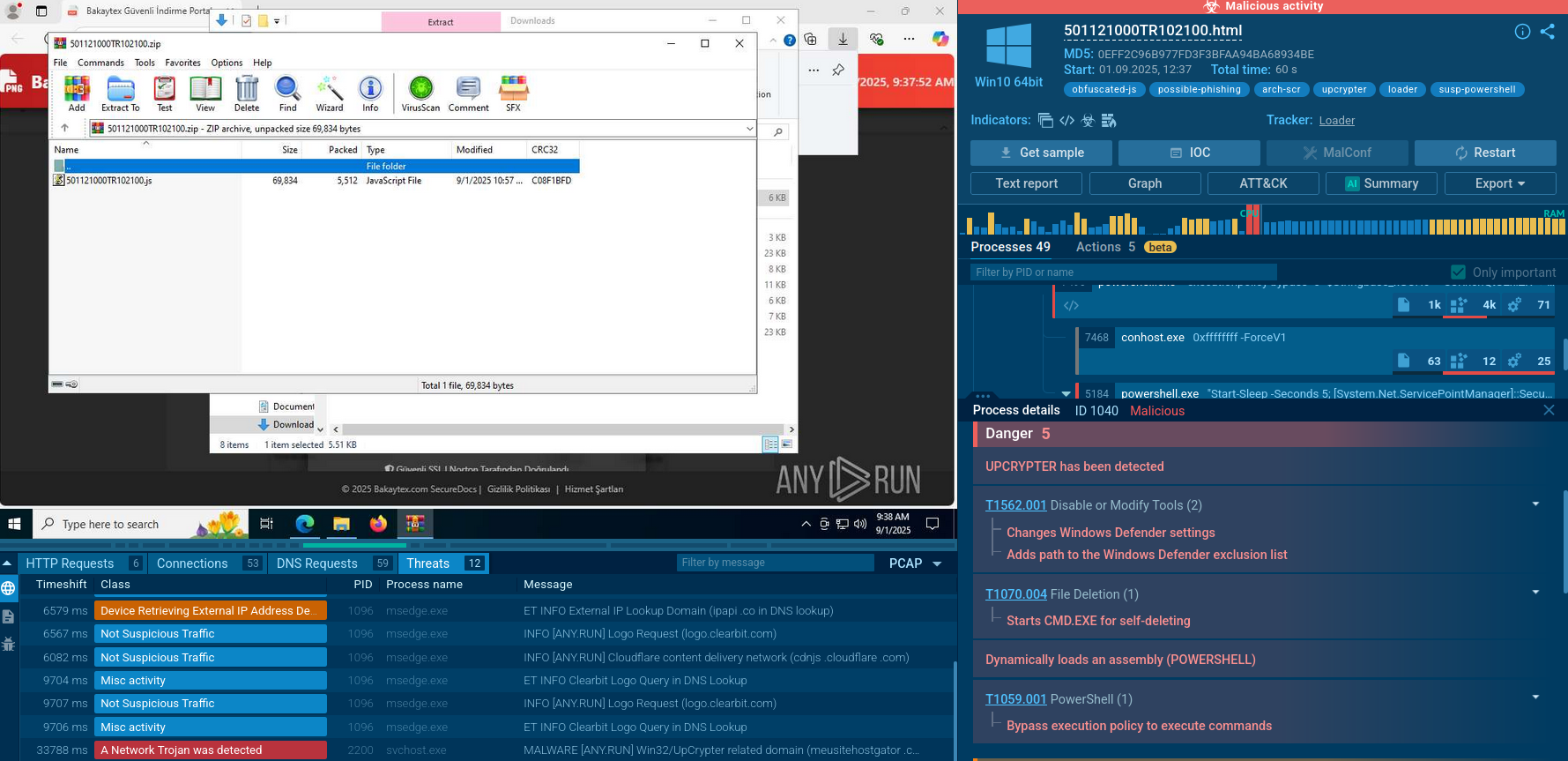
Let’s observe an ACR Stealer typical attack chain on a sample analyzed in ANY.RUN’s Interactive Sandbox.
 ACR Stealer sample analysis in the Interactive Sandbox
ACR Stealer sample analysis in the Interactive Sandbox
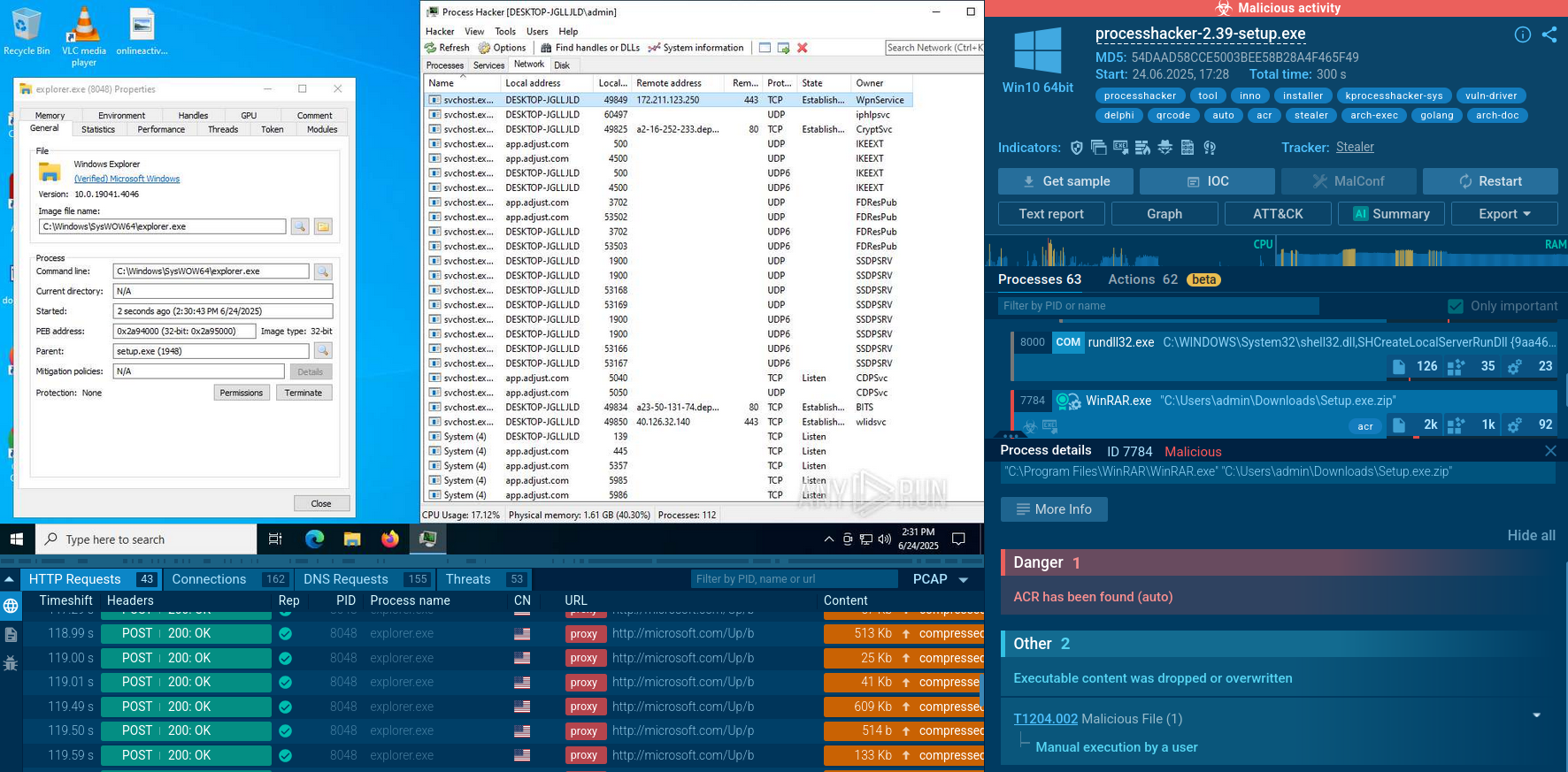
An interesting feature of ACR Stealer is that HTTP packet headers may use legitimate domains such as microsoft.com, although the packets are sent to IP addresses not associated with these domains.
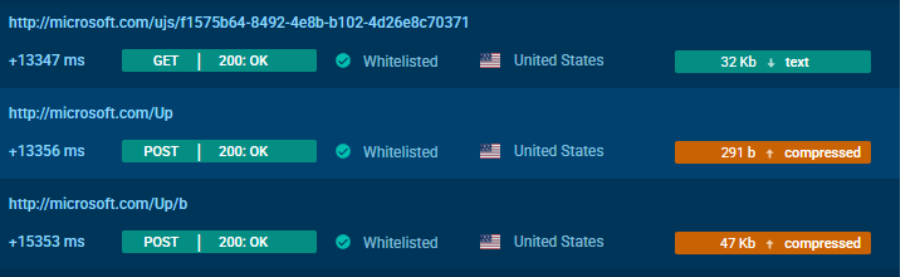 ACR HTTP requests seen in Interactive Sandbox
ACR HTTP requests seen in Interactive Sandbox
In the first response to an HTTP request, there is a large Base64-encoded string of 32 KB. When attempting to decode it, it turns out to be additionally encrypted using an XOR operation. After decryption, it produces a large configuration file, which is a key component of ACR Stealer’s operation.
The ACR Stealer configuration file is a structured JSON-like object that manages data theft in the Windows environment. It defines the targets and parameters for collecting sensitive information, ensuring flexibility and stealth of the malware.
The stealer targets data from numerous browsers, including Google Chrome, Microsoft Edge, Opera, Firefox, Brave, Vivaldi, and lesser-known ones such as CocCoc, 360Browser, and K-Meleon. It extracts cookies, passwords, browsing history, autofill data, credit card details, and extensions, many of which are cryptocurrency wallets (MetaMask, Coinbase Wallet), password managers, and censorship bypass tools.
Messengers such as Telegram, WhatsApp, Signal, Tox, and Psi+ are targeted for theft of session keys, chats, and contacts via files such as *.sqlite or accounts.xml located in %AppData% directories. Cryptocurrency wallets, including Bitcoin, Electrum, Exodus, Ledger Live, Binance, and others, are subject to theft of wallet.dat, *.json, *.config files containing private keys and seed phrases.
Additionally, the stealer attacks password managers (Bitwarden, NordPass, 1Password), FTP clients (FileZilla, WinSCP), email clients (The Bat!, eM Client, Outlook), VPNs (NordVPN, AzireVPN), and applications such as AnyDesk and Sticky Notes, extracting logins, passwords, and 2FA tokens. Global disk searches target files with keywords like bitcoin, wallet, seed, metamask in the Documents and Recent folders to locate seed phrases and keys.
The configuration supports downloading additional files from external URLs and uses a dictionary of strings for parsing browser data (Login Data, Cookies, key4.db), obfuscation, and adaptation to Windows versions, minimizing detection by antivirus software.
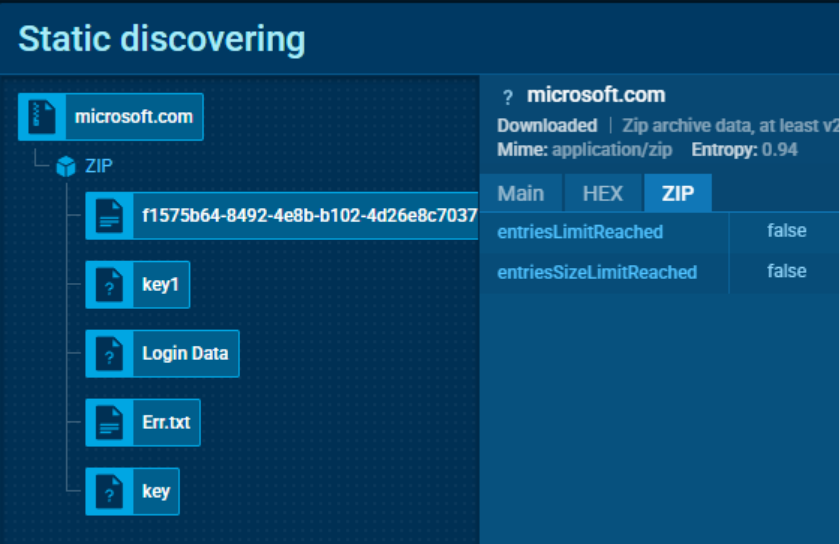 ACR Stealer ZIP archive with stolen data
ACR Stealer ZIP archive with stolen data
Data collected by ACR Stealer is sent to the attacker’s server as a ZIP archive. The configuration file usually contains a parameter responsible for downloading an additional executable file from an external resource. However, in the analyzed sample such a download was not performed.
It is reported that in new versions of ACR Stealer, the Dead Drop Resolver (DDR) method is used. The malware connects to a legitimate web platform, where a configuration string with the actual C2 server domain is placed on a specific page. The malware retrieves this string, parses it, and obtains the C2 address to proceed with its operations. This approach complicates detection and tracking of the malware.
Previously, ACRStealer used characteristic HTTP request signatures such as:
However, according to some sources, still newer versions of the malware have abandoned this format, making identification more difficult.
Best known campaigns include a 2025 operation using cracked software to distribute ACR alongside Lumma Stealer, resulting in widespread credential theft since January.
Another involved a fake Google Safety Centre phishing site spreading Latrodectus loader and ACR Stealer, compromising user security globally. In 2024, exploitation of CVE-2024-21412 facilitated delivery of ACR, Lumma, and Meduza stealers, evading Microsoft Defender and affecting numerous endpoints.
Additionally, web inject campaigns via ClearFake deployed Amatera variant, targeting cryptocurrency users with high success in data exfiltration.
Threat intelligence empowers defenders with real-time knowledge of ACR Stealer’s infrastructure, tactics, and IOCs. By enriching alerts with contextual data, security teams can distinguish real threats from noise, respond faster, and block communication with known C2 servers before data exfiltration succeeds.
Start using Threat Intelligence Lookup for free: collect IOCs, browse sandbox detonations.
Start with a malware name search request to ANY.RUN’s Threat Intelligence Lookup and dive deeper into contextual data on ACR Stealer. View public analyses of the malware’s fresh samples, extract the behavioral patterns, gather IOCs from each session.
threatName:"acr" and threatLevel:"malicious"
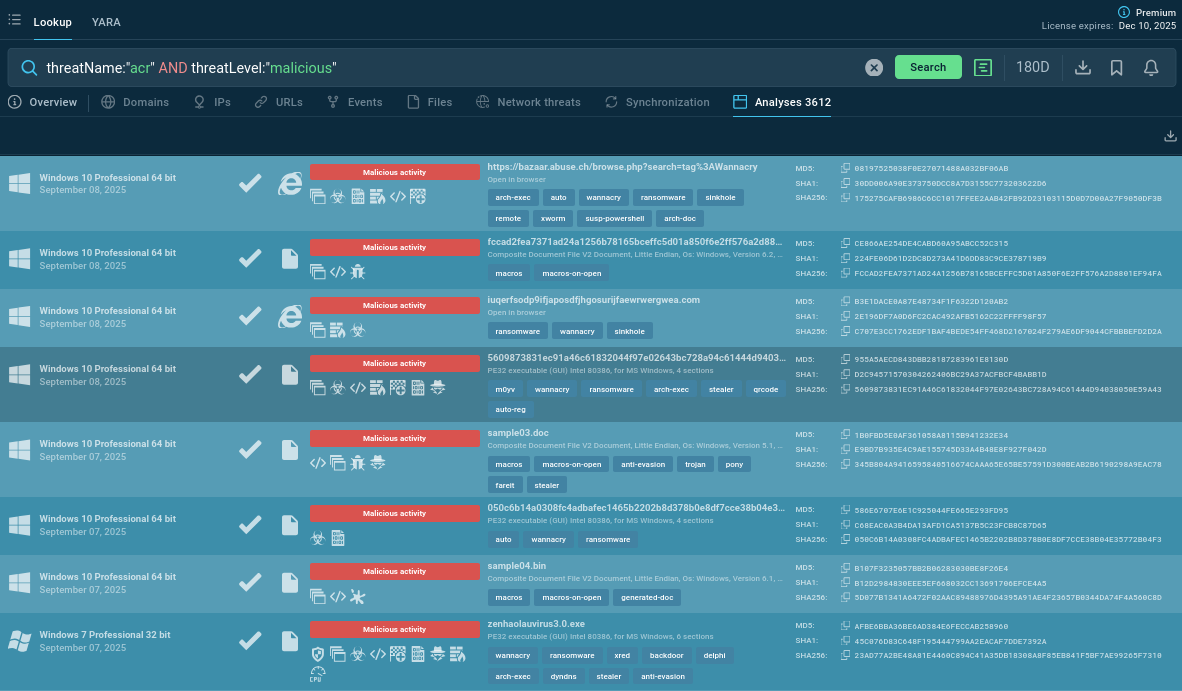 ACR Stealer malware analyses found via Threat Intelligence Lookup
ACR Stealer malware analyses found via Threat Intelligence Lookup
Gather indicators of compromise by clicking the IOCs button in Interactive Sandbox and look them up to find correlating IPs, domains, URLs, and more.
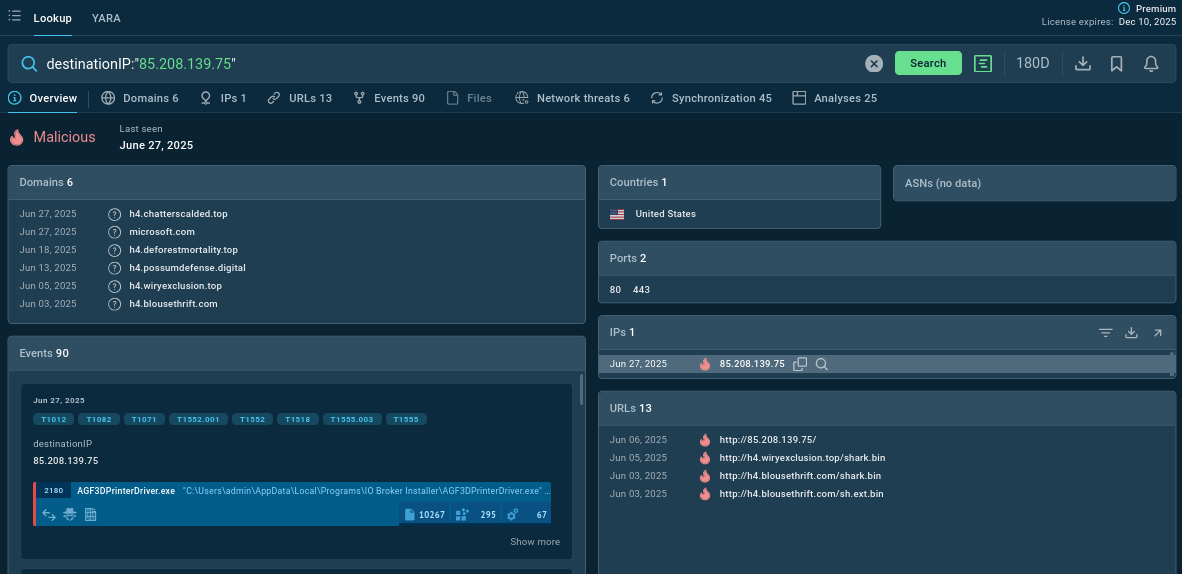 Lookup search for an IP found in ACR Stealer samples delivers more IOCs
Lookup search for an IP found in ACR Stealer samples delivers more IOCs
ACR Stealer represents a significant evolution in information-stealing malware, combining sophisticated evasion techniques with comprehensive data harvesting capabilities. Its ability to leverage legitimate platforms for command and control communication, employ advanced anti-analysis techniques, and continuously evolve demonstrates the dynamic nature of modern cyber threats. Organizations must adopt a proactive, multi-layered security approach that combines technical controls, user education, and threat intelligence to effectively defend against ACR Stealer and similar threats.
The rise in ACR Stealer incidents, particularly the dramatic increase observed in 2025, underscores the urgent need for enhanced security awareness and robust defensive measures across all sectors of the digital economy.
Sign up to use ANY.RUN’s TI Lookup for free: gather fresh actionable threat intelligence for quick detection and response.