Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Qbot is a banking Trojan — a malware designed to collect banking information from victims. Qbot targets organizations mostly in the US. It is equipped with various sophisticated evasion and info-stealing functions and worm-like functionality, and a strong persistence mechanism.
|
Botnet
Type
:
|
Unknown
Origin
:
|
|
1 January, 2009
First seen
:
|
28 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 January, 2009
First seen
:
|
28 February, 2026
Last seen
:
|

 868
868
 0
0

 515
515
 0
0

 2802
2802
 0
0
Qbot, also known as QakBot, Pinkslipbot, and Quakbot, is a banking trojan — malware designed to steal banking credentials, online banking session information, personal details of the victim, or any other banking data.
Although early versions of Qbot were spotted all the way back in 2009, its creators have maintained this trojan. Today, it continues to be active and features worm-like abilities to spread over networks, supports advanced web-injections techniques, and has a persistence mechanism that some researchers believe to be one of the best in its class. Additionally, the trojan has anti-VM, anti-debug and anti-sandbox functionally that makes research and analysis quite difficult.
Furthermore, Qbot is polymorphic, which means that it can change itself even after it is installed on an endpoint. The Trojan constantly modifies files, and the dropper that the newer version of Qbot continuously cycles through command and control servers.
The combination of these functions makes QakBot highly dangerous malware. Qbot has been used in several successful attacks on organizations and governmental structures and has infected tens of thousands of machines.
Qbot is dispatched in targeted attacks against businesses. With this trojan, the attackers go after bank accounts of organizations or private users who access their personal online banking cabinets from corporate networks by piggybacking into banking sessions of the victim.
The Trojan uses man-in-the-browser functionality to perform web injections, allowing it to alter what the victims see on the banking website when browsing from an infected machine. Interestingly, while most malware samples that use this technique contain the web injection code in their config file, Qbot can fetch the code from a controlled domain as it performs malicious activity.
Another trait that differentiates Qbot from other Trojans is its worm-like functionality. Qbot can copy itself using shared drives and spread over the network, spreading on its own or after receiving a command from the command and control server. Together with a highly developed persistence mechanism that uses registry runkeys and scheduled tasks, these traits make erasing Qbot from the infected network very difficult. The Trojan is designed to sustain itself despite system reboots and automatically launch itself when the system is turned on again.
This infamous persistence functionality has allegedly caused compromise of sensitive information in two government organizations in Massachusetts in 2011, while worm-like behavior helped the Qbot infiltrate thousands of machines and create a botnet with over 1,500 devices resulting from that attack.
Most of the targets that Qbot goes after are US-based organizations. Only about twenty percent of the new attack businesses are located outside of the United States. Although apart from the government offices, most of the attacks have been directed at banking, tech, and healthcare industries, there is no hard evidence to suggest that the attackers are aiming at specific fields. This means that businesses working in any industry can get hit by QakBot.
It is also important to note that an advanced cybergang operates the malware. Qbot attacks have been appearing on the radar of security researchers periodically, with phases of high activity and intervals when attacks would completely stop. This behavior is likely to avoid attracting too much attention from law enforcement and allows attackers to tweak and improve the malware during their time off.
The group behind Qbot is also notoriously known for pushing out new modified malware samples at astonishing rates. They repack and re-scramble the code daily, making malware identification by means of anti-virus software unreliable.
Unfortunately, people's identities behind Qbot are unknown, but it is widely believed that the cyber gang is based somewhere in Eastern Europe.
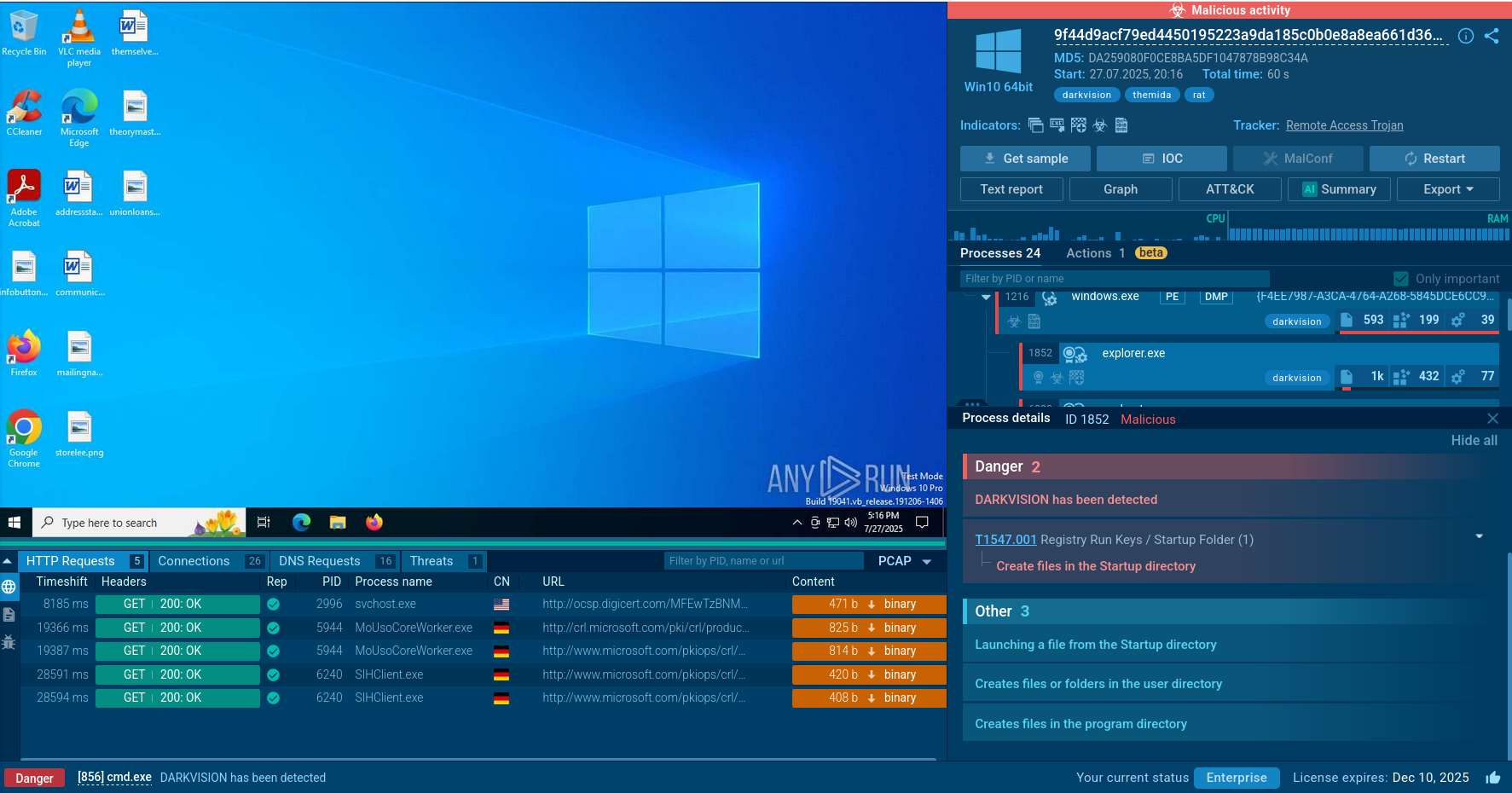
This video recorded in the ANY.RUN interactive malware hunting service shows the execution process of Qbot. You can also research other malware like Netwire and Predator the Thief.
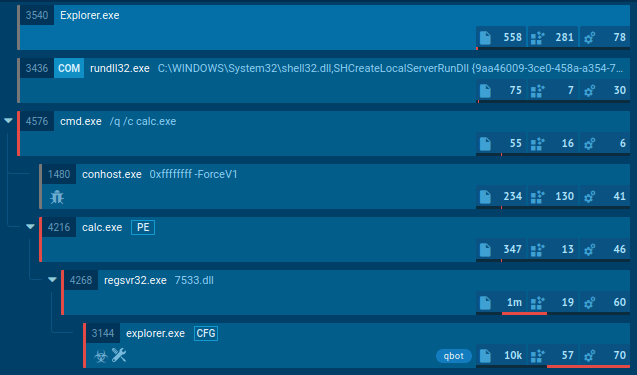
Figure 1: Displays the tree of processes created by the ANY.RUN interactive malware hunting service
Since Qbot is mostly targeted at the corporate sector, the main way of its penetration into infected systems is through a malicious document. In our example, maldoc starts several processes, including Powershell through by using a macro. Then, using cmd.exe, this trojan starts a chain of commands and executions, creating folders and temporary files. It utilizes Powershell to download the payload. Notably, the payload's name is as simple as six of the same digits or, less often, letters. Also, the payload often has a .png extension, although it is an executable file.
After that trojan starts its main execution, QakBot tries to evade detection by overwriting itself with the legitimate Windows executable calc.exe using the following commands: cmd.exe /c ping.exe -n 6 127.0.0.1 & type "C:\Windows\System32\calc.exe" > “Path to malware executable.” Qbot also injects explorer.exe and adds itself into autorun for persistence.
Qbot uses multiple attack vectors to infect victims. The malware uses email spam and phishing campaigns, as well as vulnerability exploits to infiltrate its targets. One of the more recent versions of the malware was observed being distributed by a dropper.
The dropper that installs Qbot is equipped with a delayed execution function. This means that after the dropper itself is downloaded onto a target machine, it waits around fifteen minutes before dropping the payload, likely in an effort to trick automatic sandboxes and avoid detection.
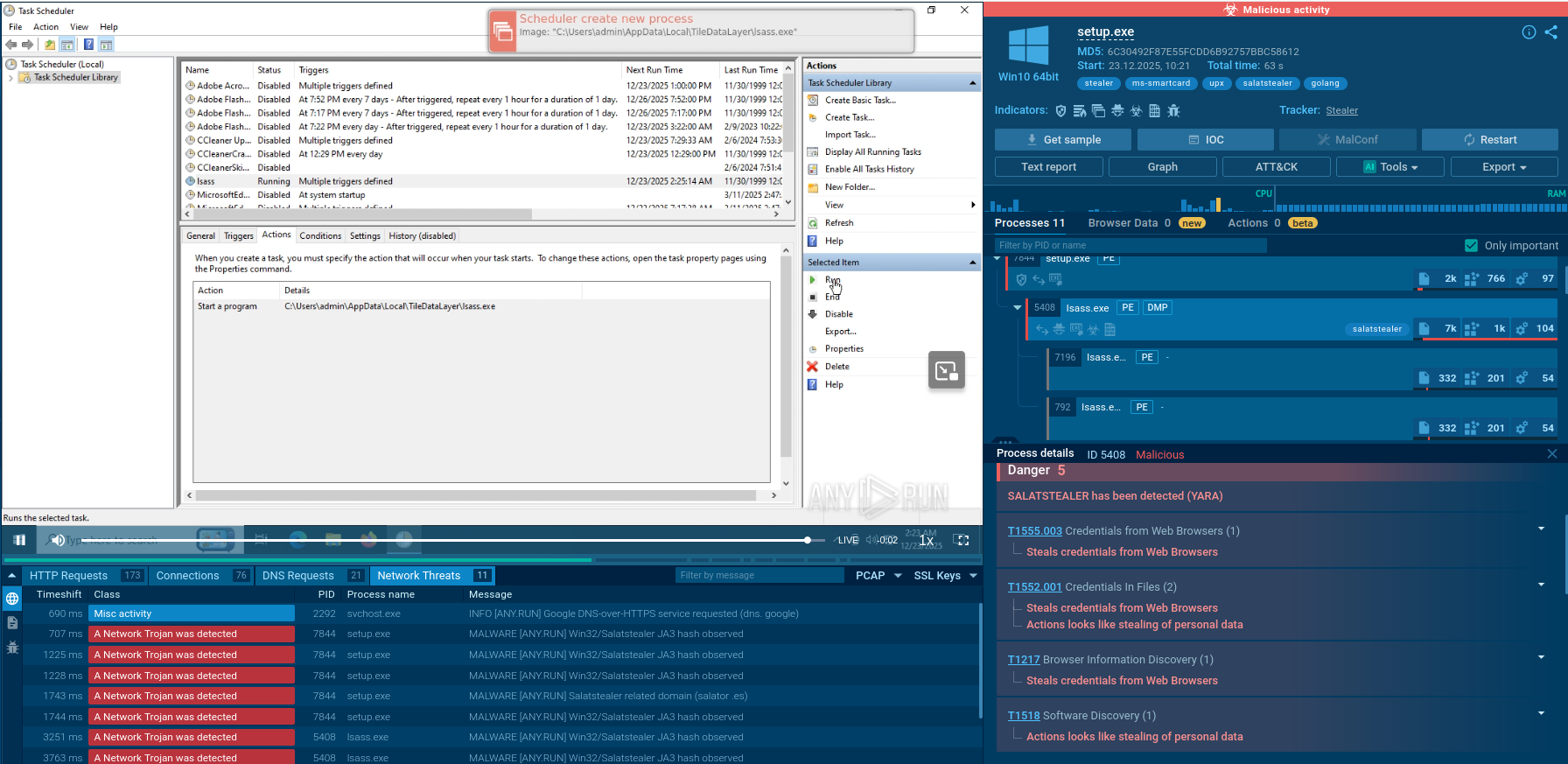
Sometimes Qbot trojan creates files that allow analysts to detect it with a high degree of certainty. To detect Qbot, open the "Files" tab in the lower part of the task's window and take a look at the created folders. If you see folders with names such as "Zulycjadyc" and "imtaykad" within C:\Users\admin\AppData\ Roaming\Microsoft\ directory and .exe or .dat file with a name "ytfovlym," as shown on the figure below, be sure that it is Qbot in front of you.
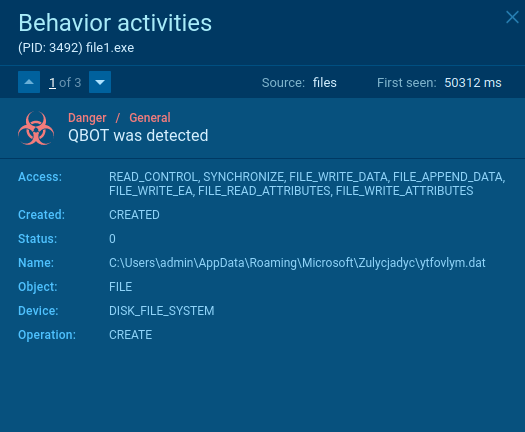
Figure 2: Detecting Qbot by local files
Security researchers successfully reversed a sample of QakBot in a 2020 investigation. Since the researchers managed to pinpoint a command and control server, they could identify the true scale of the attack. What they uncovered was an active Qbot botnet consisting of over 2,000 computers.
If there was any doubt that Qbot is a severe threat, hopefully, this should clear it. Advanced web injections, sophisticated anti-evasion techniques, worm-like functions, and an experienced cyber gang that constantly updates the malware is a dangerous cocktail.
As security researchers, it is essential to analyze malware like Qbot since code obfuscation makes research complicated. Every investigation has the potential to uncover important data that will help businesses avoid attacks or identify and eradicate this Trojan quicker. At the same time, Qbot avoids dynamic analysis with some automatic sandboxes with the delayed execution of its dropper and other tricks, interactive sandboxes like the one presented by the ANY.RUN malware hunting services are not so easily fooled.
ANY.RUN presents a good opportunity to perform dynamic analysis on this malware from a secure online environment and share your findings with fellow researchers in our public malware database.
.png)