Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


BlackMoon also known as KrBanker is a trojan aimed at stealing payment credentials. It specializes in man-in-the-browser (MitB) attacks, web injection, and credential theft to compromise users' online banking accounts. It was first noticed in early 2014 attacking banks in South Korea and has impressively evolved since by adding a number of new infiltration techniques and information stealing methods.
|
Trojan
Type
:
|
Unknown
Origin
:
|
|
1 February, 2014
First seen
:
|
23 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 February, 2014
First seen
:
|
23 February, 2026
Last seen
:
|

 868
868
 0
0

 515
515
 0
0

 2802
2802
 0
0
BlackMoon (KRBanker) is one of the most sophisticated banking trojans, exploiting MitB attacks and web injections to steal financial data. Its stealthy evasion techniques, 2FA bypasses, and browser manipulation make it highly dangerous. Initially used in attacks targeting South Korea, it has since spread all over the world and threatens individuals and organizations in any region.
At the dawn of its “career" in 2015-2016, it employed a “pharming” technique to steal banking credentials. It redirected users to a fake website that imitated one of the banking sites and invited visitors to submit their payment data. The data is sent to C2 servers controlled by attackers, 2FA is bypassed by injecting fake OTP fields or session hijacking.
Beside luring information out of users, the malware generates fake alerts on banking websites prompting users to download a malicious security tool. BlackMoon employs a number of anti-detection and persistence mechanics. It injects itself into legitimate system processes, modifies Windows Registry, schedules tasks and startup entries. It also changes signatures to evade static detection, uses code obfuscation and targets specific banking URLs to minimize noise in network logs.
Blackmoon is detectable with threat intelligence tools by a number of indicators: associated domains, IPs, hashes, as well as known behavioral patterns. Network monitoring tools are triggered by outbound traffic to suspicious C2 servers, abnormal DNS queries, HTTP requests with suspicious headers related to web injections.
BlackMoon has some unique and some typical for malware of this type features that make it effective and hard to oppose.
Within ANY.RUN's Interactive Sandbox, we can observe the malware's entire execution chain in a safe virtual environment.
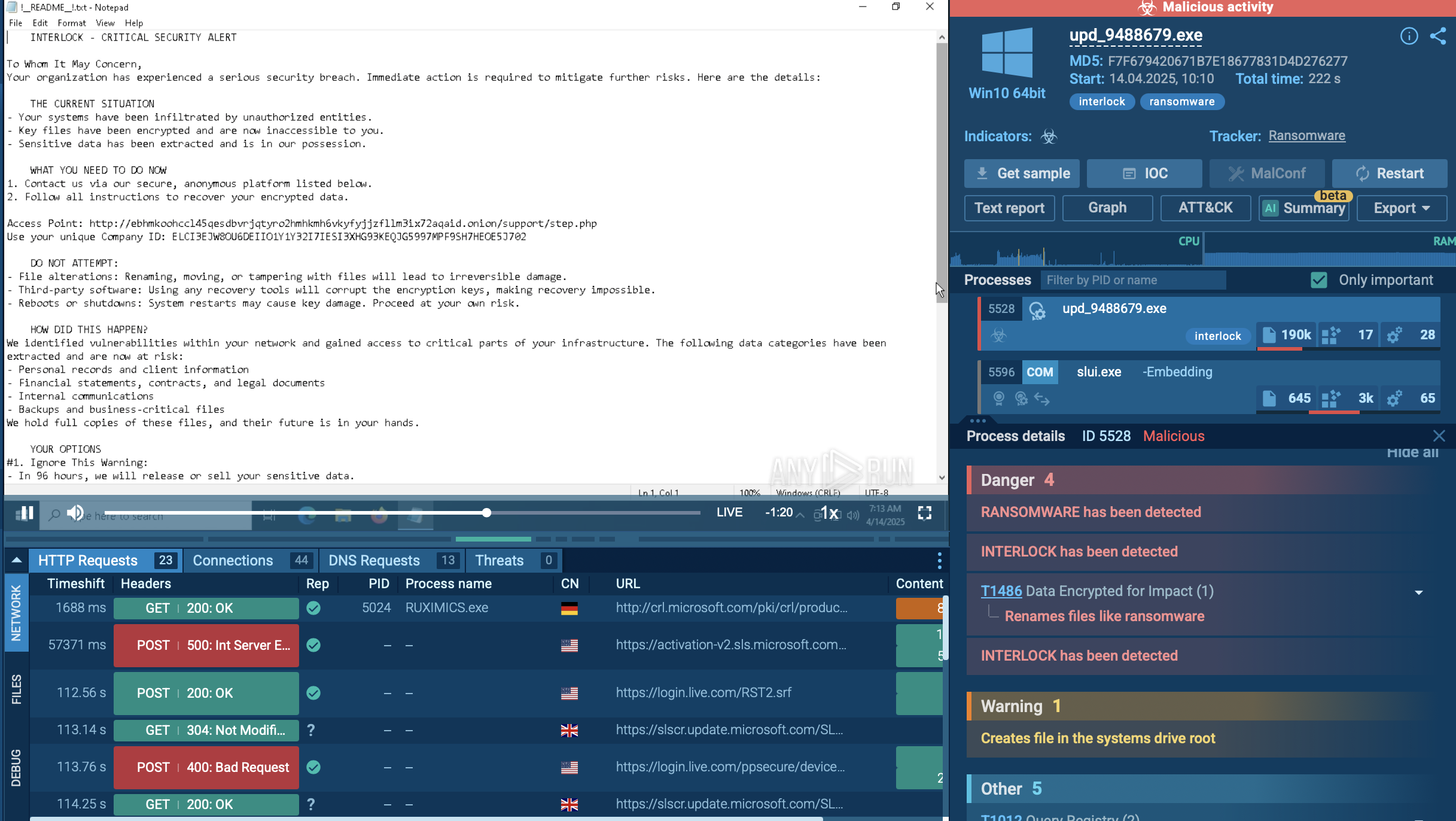
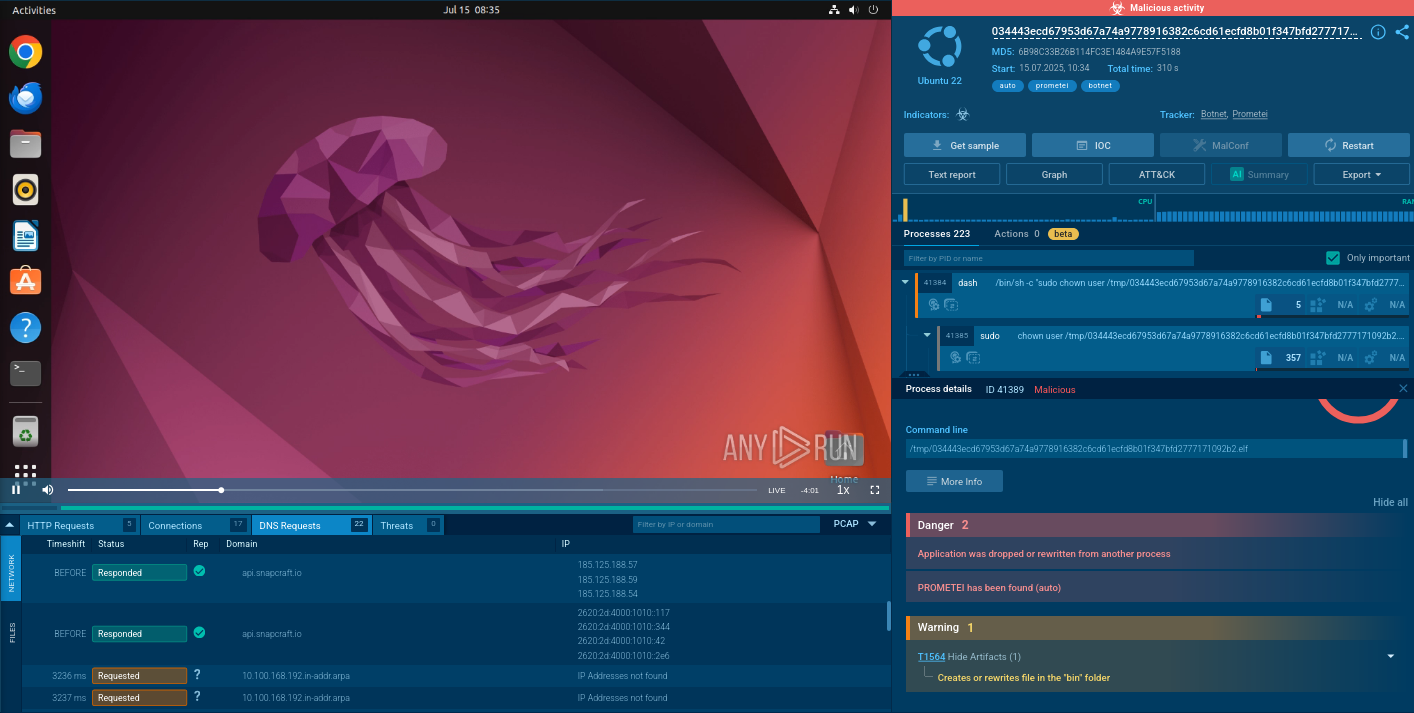
 KRBanker detonated in ANY.RUN’s Interactive Sandbox
KRBanker detonated in ANY.RUN’s Interactive Sandbox
BlackMoon malware employs a multi-stage execution chain specifically designed for financial theft, frequently targeting South Korean banking institutions. The infection process typically begins with a dropper file delivered through phishing campaigns or exploit kits that leverage browser vulnerabilities.
Once executed, this dropper retrieves additional components necessary for the BlackMoon Trojan’s full functionality. The malware’s operation is divided into three distinct stages. In the first stage, the Mini Downloader fetches a second component, which in turn initiates the next phase. The second stage uses the KRDownloader to complete the installation.
After successfully downloading its payload, KRDownloader executes it and then self-deletes to evade detection. The payload commonly includes credential theft features, often deploying man-in-the-browser techniques to intercept user credentials during interactions with banking websites. Once installed, BlackMoon persists on the system by modifying registry keys and, in some cases, altering the local Hosts file. These changes redirect users attempting to access legitimate banking sites to attacker-controlled phishing pages.
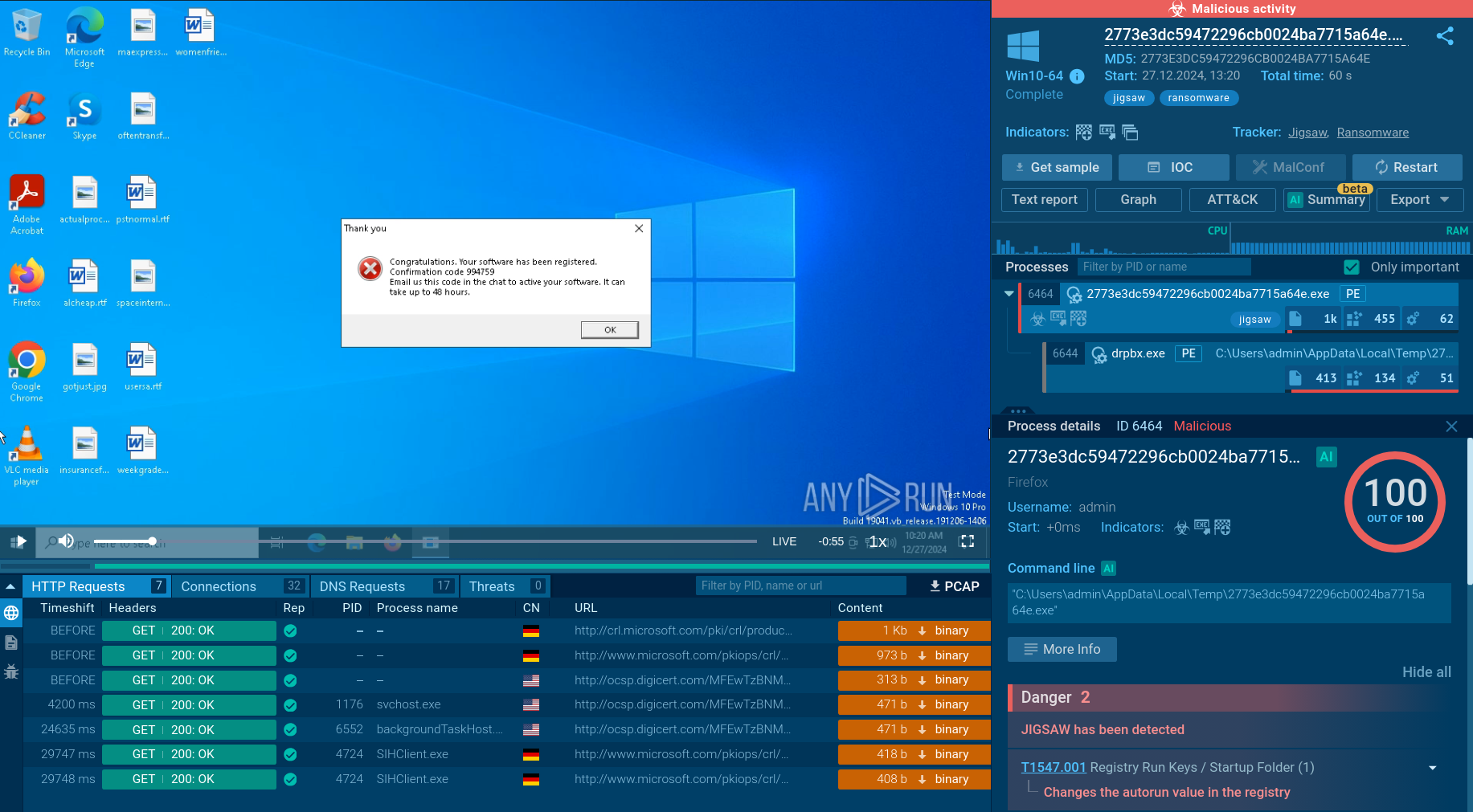
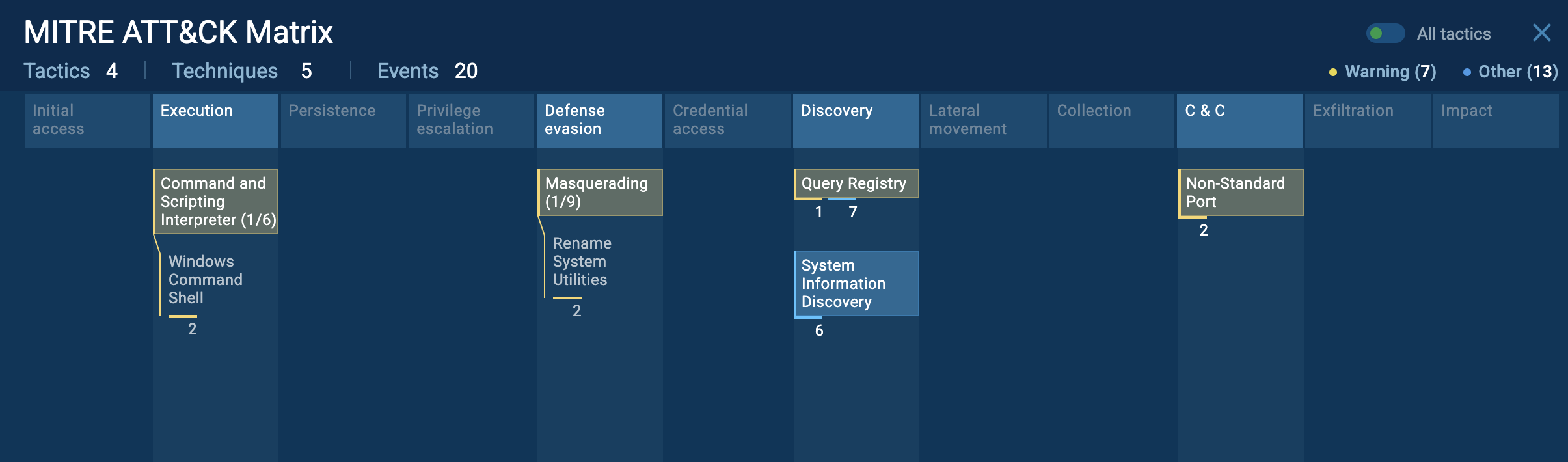 The tactics and techniques of Blackmoon mapped in the sandbox
The tactics and techniques of Blackmoon mapped in the sandbox
The use of a Proxy Auto-Config (PAC) file further enhances stealth, allowing BlackMoon to intercept and manipulate web traffic without immediately arousing suspicion. Beyond credential theft and phishing, BlackMoon maintains communication with its command-and-control (C&C) servers to receive updates and instructions. It retrieves encoded configuration blocks from hardcoded URLs, dictating operational parameters and target websites. This communication channel is critical for retaining control over infected devices and adjusting to new targets or evasion methods.
Overall, BlackMoon’s carefully orchestrated, multi-stage downloader framework maximizes stealth and efficiency in delivering its malicious payload. This layered approach not only complicates analysis for security researchers but also enhances its effectiveness in compromising financial institutions and stealing sensitive user information.
Explore BlackMoon’s IOCs, IOBs and IOAs via ANY.RUN’s Threat Intelligence Lookup searches and collect data for setting up detection and response in your network.
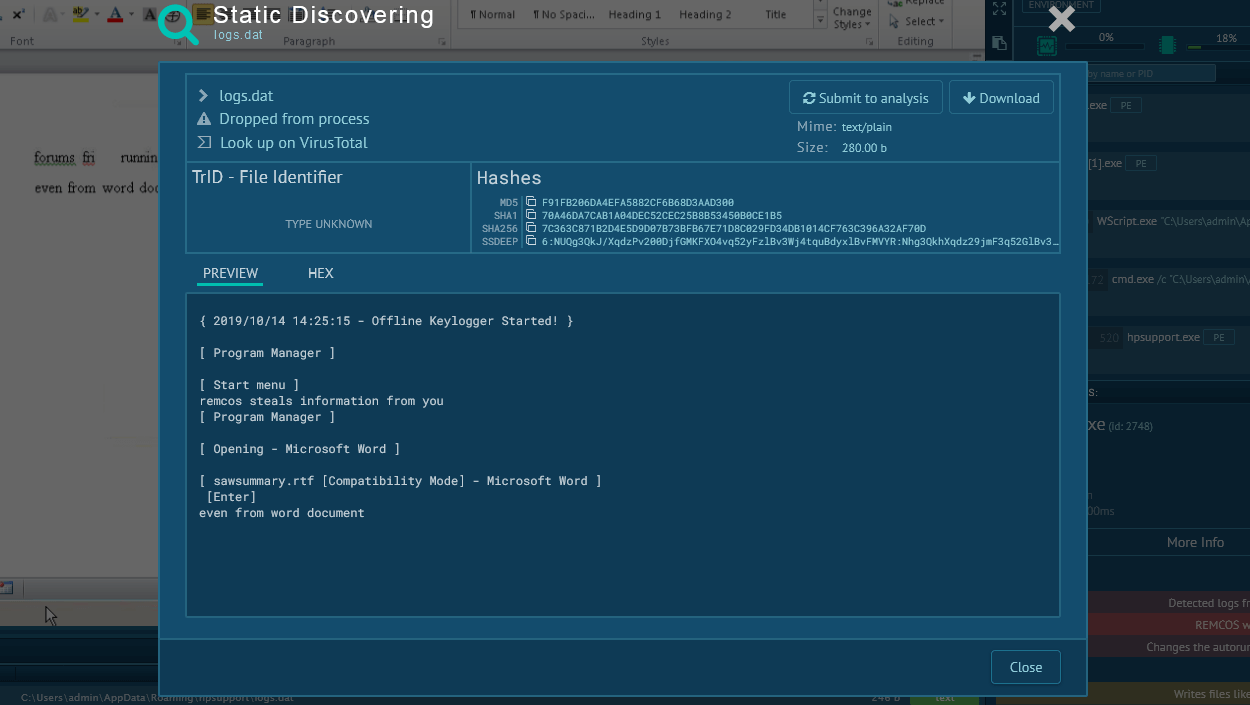
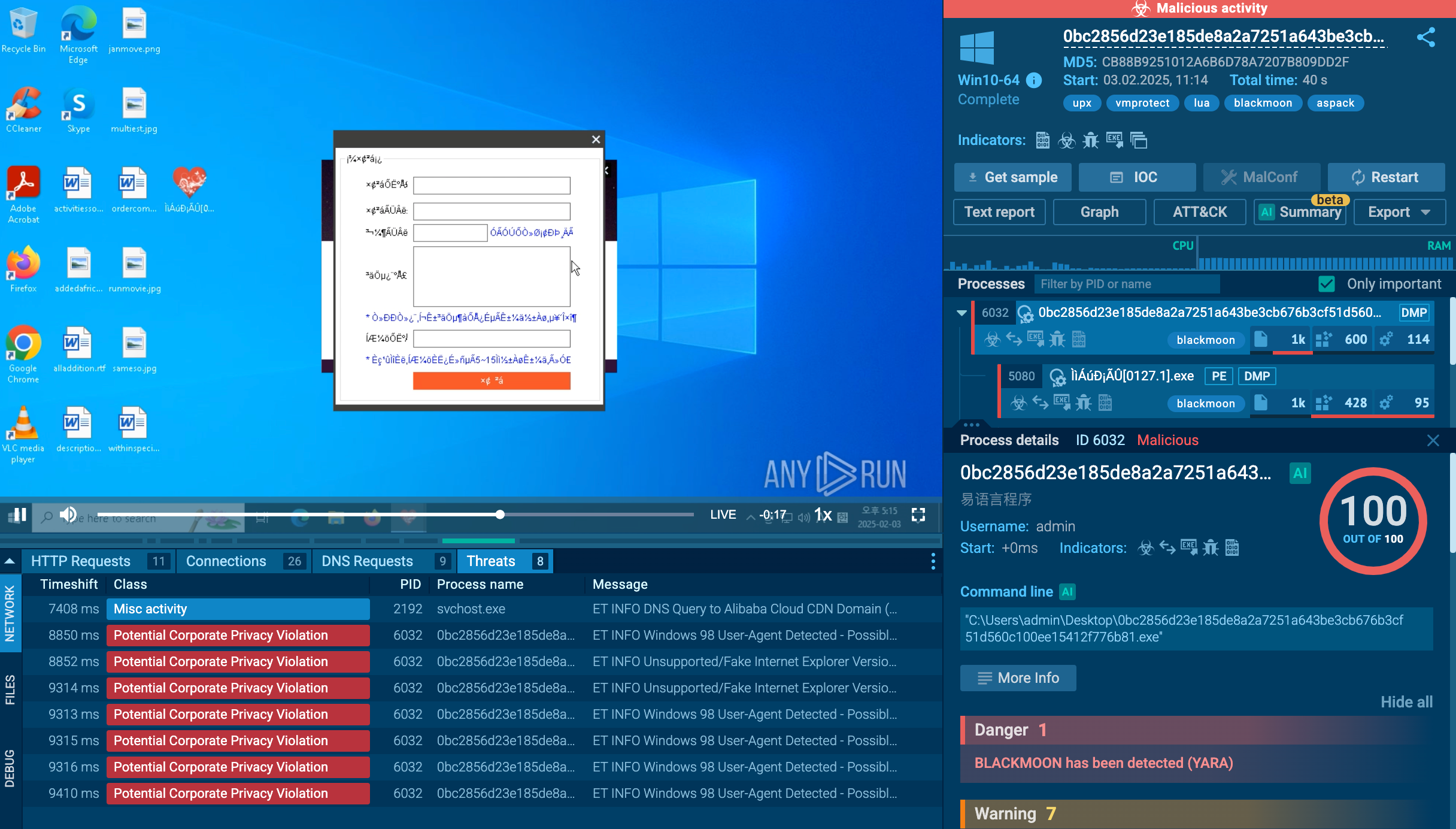
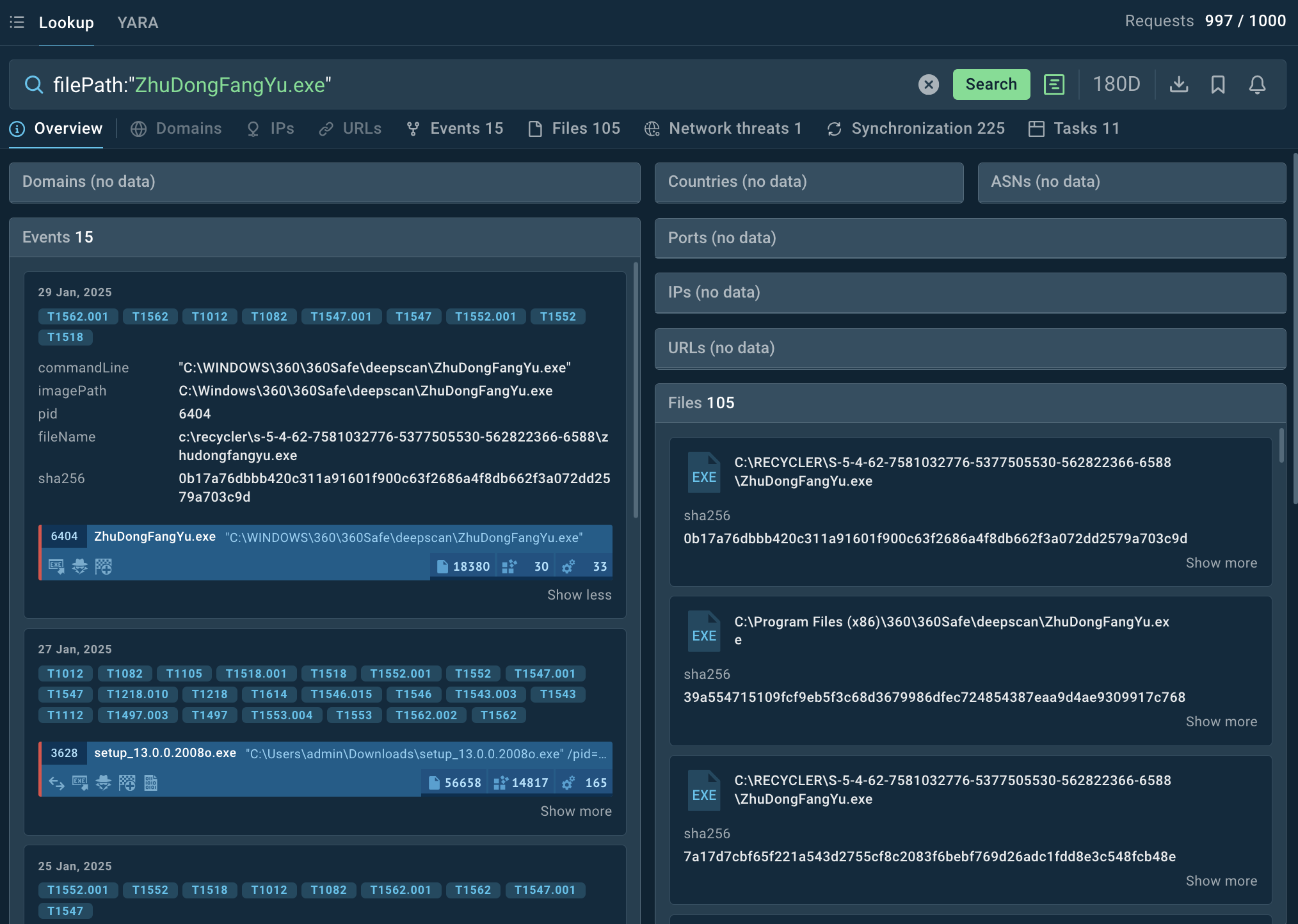 TI Lookup overview of a malicious file associated with Blackmoon attacks
TI Lookup overview of a malicious file associated with Blackmoon attacks
Leverage TI feeds to track C2 infrastructure, malware hashes, keep a watch over evolving tactics of KRBanker via MITRE ATT&CK mappings. For example, we can use the following query filePath:"ZhuDongFangYu.exe" to find sandbox reports featuring the file named ZhuDongFangYu commonly used in BlackMoon attacks.
KRBanker typically spreads through:
BlackMoon remains highly dangerous because it leads directly to financial losses through critical data theft. Its stealthy evasion techniques, 2FA bypasses, and browser manipulation also put it in the high-risk group. Using threat intelligence-driven detection and response, security teams can monitor IOCs, implement behavioral analytics, and harden authentication mechanisms to combat this evolving banking malware threat.
Sign up for ANY.RUN to analyze malware and phishing threats for free.