Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold.
|
Trojan
Type
:
|
Likely Turkey
Origin
:
|
|
1 January, 2014
First seen
:
|
7 February, 2026
Last seen
:
|
|
Type
:
|
Likely Turkey
Origin
:
|
|
1 January, 2014
First seen
:
|
7 February, 2026
Last seen
:
|

 435
435
 0
0

 2295
2295
 0
0

 4454
4454
 0
0
Agent Tesla is a password stealer spyware that has been around since 2014. The malware can be used by attackers to spy on victims, allowing them to see everything that has been typed in supported programs and web-browsers.
Being marketed and sold on its own website, which falsely claims that the program is a legitimate keylogger created for personal use, the Agent Tesla virus has become extremely popular in the hacker community. Not lastly due to its ease of use and tech support, available on the “official” website where this malware is being sold by the attackers, as well as on the dedicated Discord server. Despite claiming the legitimacy of the software, support staff gives advice on utilizing the virus illegally. It is thought that Agent Tesla spyware has originated in Turkey.
The spyware is created using .Net software framework. It is aimed at stealing personal data and transmitting it back to the C2 server. The malware is able to access information from web browsers, email clients, and FTP servers.
In addition, Agent Tesla malware can capture screenshots and videos. It can also record clipboard information and form values. The virus was being distributed on agenttesla-dot-com where attackers could purchase it for as little as $15. However, depending on the requested options the package price could easily reach roughly $70.
Uniquely, creators of the malware have set up a sort of an ecosystem around the program, providing 24/7 customer support as well as pre-matched purchase plans that include various options tailored for different budgets and goals. The virus is supplied with a dedicated builder that has a simple-to-use control panel. It allows even a non-technically savvy attacker to pack the payload into a malicious document. What’s more, after 2015 the control panel of Agent Tesla has been expanded with extensive automation functionality, allowing the attacker to automatically capture snapshots or remotely activate the webcam on a victim’s PC in set intervals.
Based on the analysis, the malware comes equipped with multiple persistence mechanisms that help it avoid antivirus detection. As such, it can resume operation automatically after a system reboot. It is also able to turn off Windows processes to stay hidden.
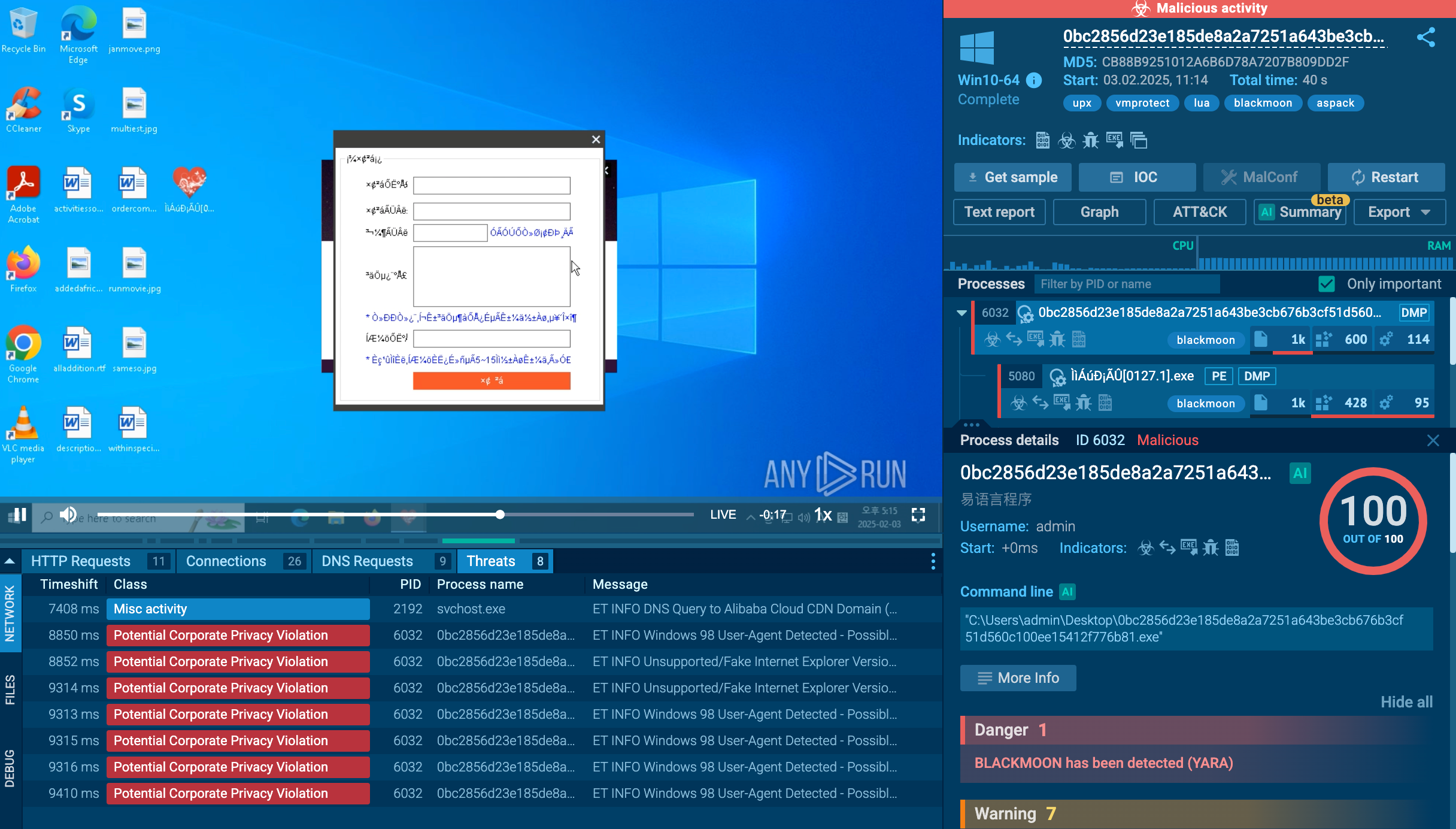
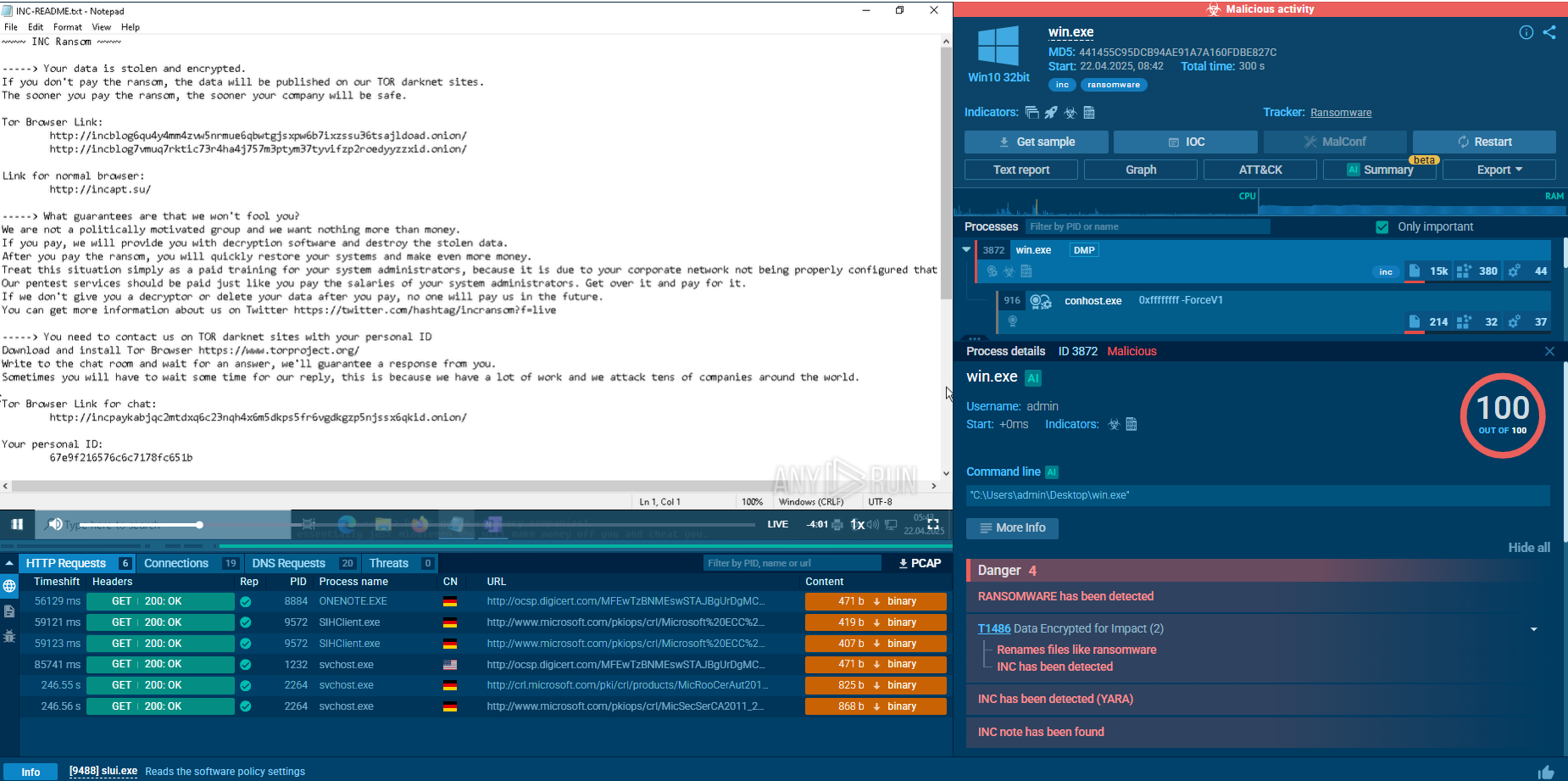
The interactivity of ANY.RUN service allows tracking activities in real-time and watching Agent Tesla in action in a controlled, safe environment with full real-time access to the sandbox simulation. A video recorded by the ANY.RUN gives us the ability to take a closer look at the lifecycle of this virus. You can also analyze fresh samples and IOCs in our threat intelligence feed in the public submissions.
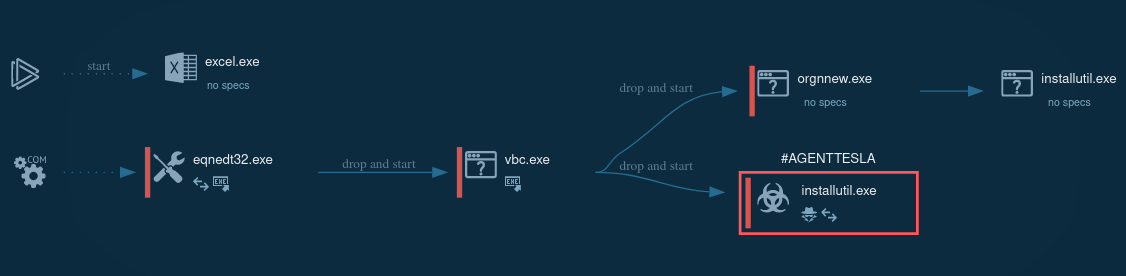 Figure 1: A lifecycle graph generated by ANY.RUN
Figure 1: A lifecycle graph generated by ANY.RUN
Agent Tesla malware is not an easy one to identify. The most robust way to stay safe is to exhibit caution when opening suspicious emails or visiting unknown links. Above all, one must be careful to download attachments in emails from unknown senders and try to identify scams.
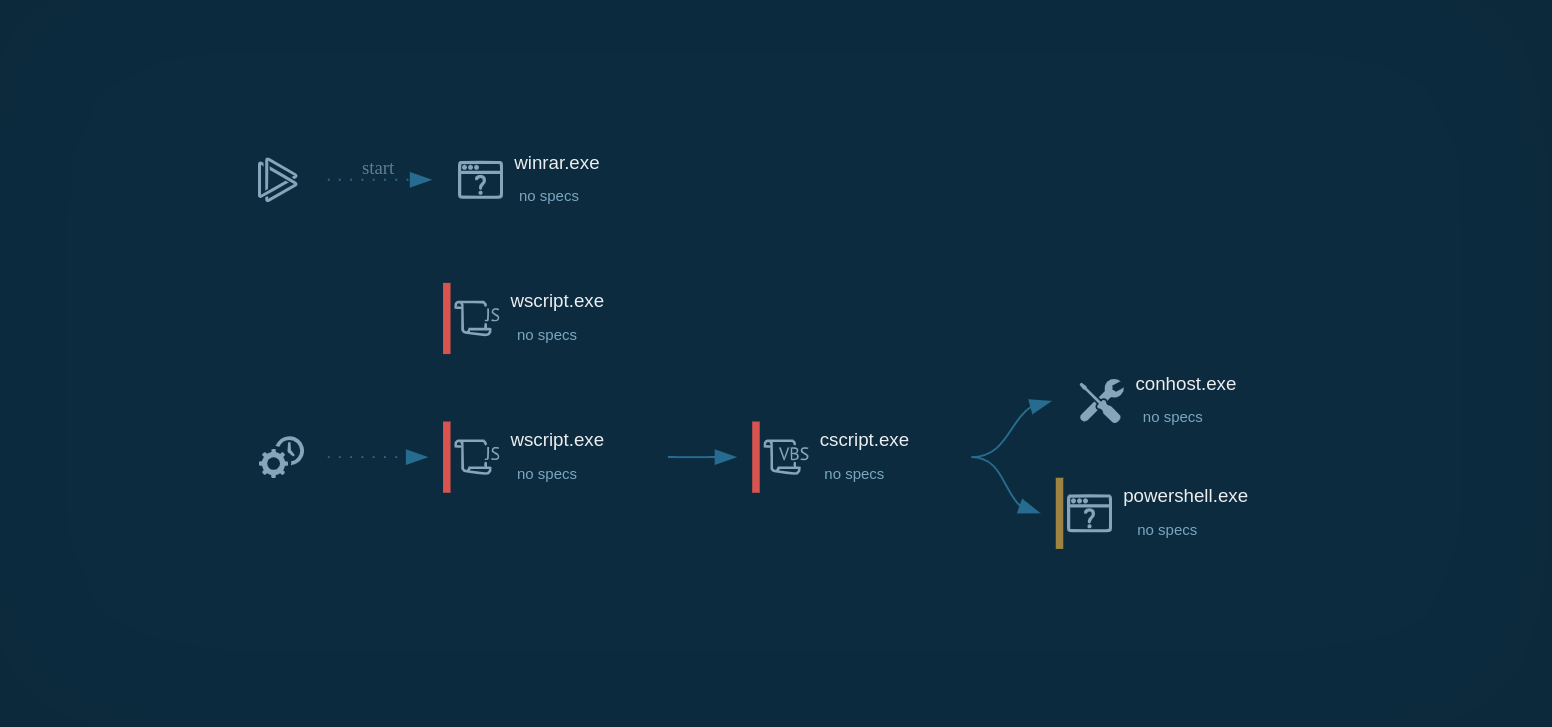
The malware is distributed at large via spam email campaigns like Vidar or IcedID. It is usually delivered to victims in malicious documents, or via malicious web links. Upon visiting such a link, a contaminated document will be automatically downloaded to a victim’s PC.
If opened, the document will trigger the download of the actual virus. The spyware saves itself in the “%temp%” folder and then automatically executes. Email campaigns usually target individuals working in different industries. Topics of malicious emails can be extremely diverse.
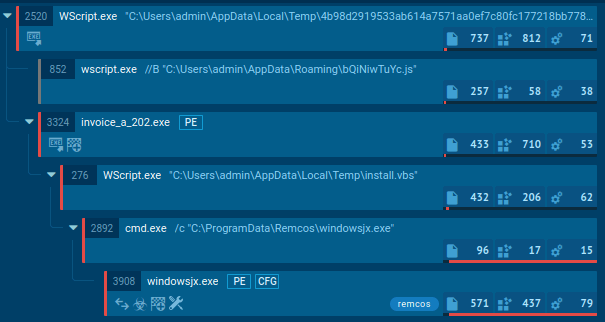
Agent Tesla keylogger is mostly spread via Microsoft Word documents that contain an embedded executed file or exploit. Once clicked, an executable file is downloaded and renamed. The downloaded file runs itself and creates a child process which in turn can create another child process.
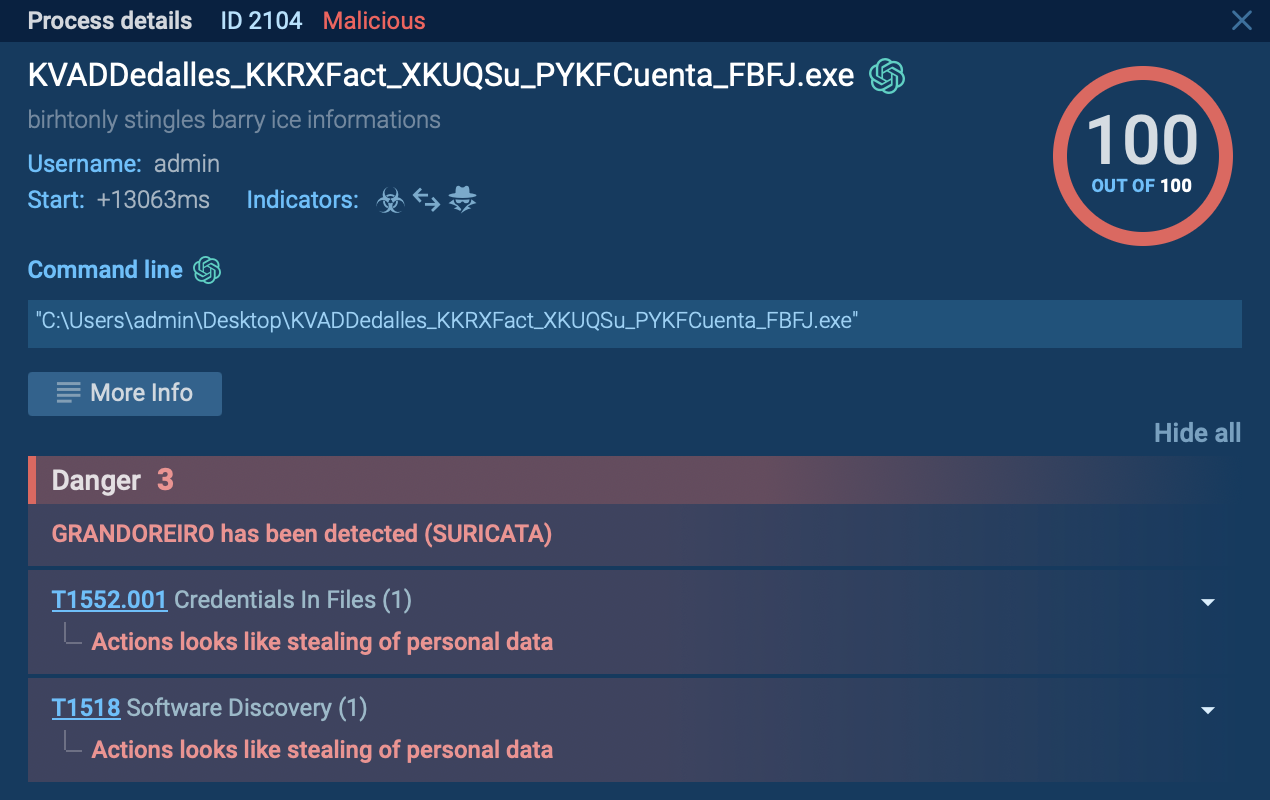
The malware is able to use Regsvcs and Regasm to proxy the code execution through a trusted Windows utility. The research and threat intelligence team can pay attention that in the given example RegSvcs.exe process is stealing personal data.
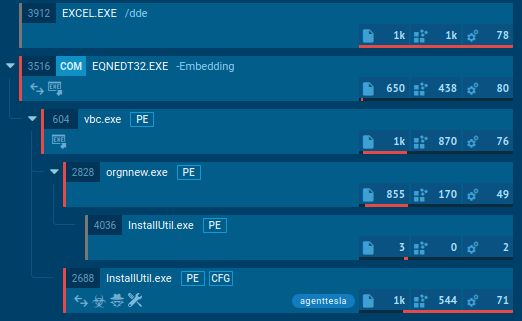 Figure 2: A process tree of the Agent Tesla execution
Figure 2: A process tree of the Agent Tesla execution
Since the main purpose of Agent Tesla RAT is stealing personal information you can identify it by behavioral activities. To do so, try the analysis of the indicators of a malicious process (most often it's an injected "RegAsm.exe"). If there is the indicator "Actions looks like stealing of personal data" in the "Process details" section you probably are dealing with the Agent Tesla trojan. Also, you can identify what information the malware has stolen by clicking on the indicator. You can navigate through by clicking right and left arrows in the appeared window.
Often Agenttesla packets encryption is unsuccessful and with ANY.RUN service's "Network Stream" analysts can take a look at what data this malware stole. To do it open the "Connections" tab in the lower part of the task's window and simply click on the connection which sent data. Not unusual that you can find inside this information even the attacker’s SMTP credential.
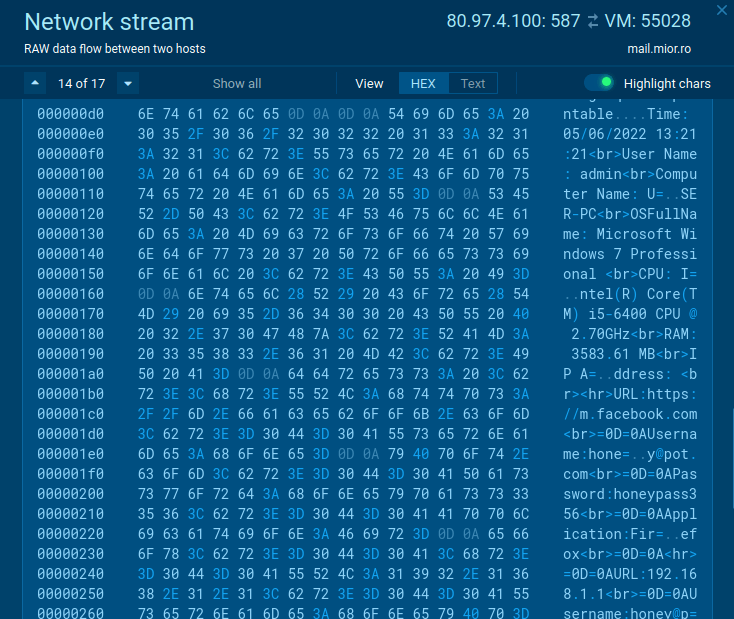 Figure 2: Agent Tesla’s Network stream without encryption
Figure 2: Agent Tesla’s Network stream without encryption
To collect up-to-date intelligence on Agent Tesla, use Threat Intelligence Lookup.
This service gives you access to a vast database filled with insights from millions of malware analysis sessions conducted in the ANY.RUN sandbox.
With over 40 customizable search parameters, including IPs, domains, file names, and process artifacts, you can efficiently gather relevant data on threats like Agent Tesla.
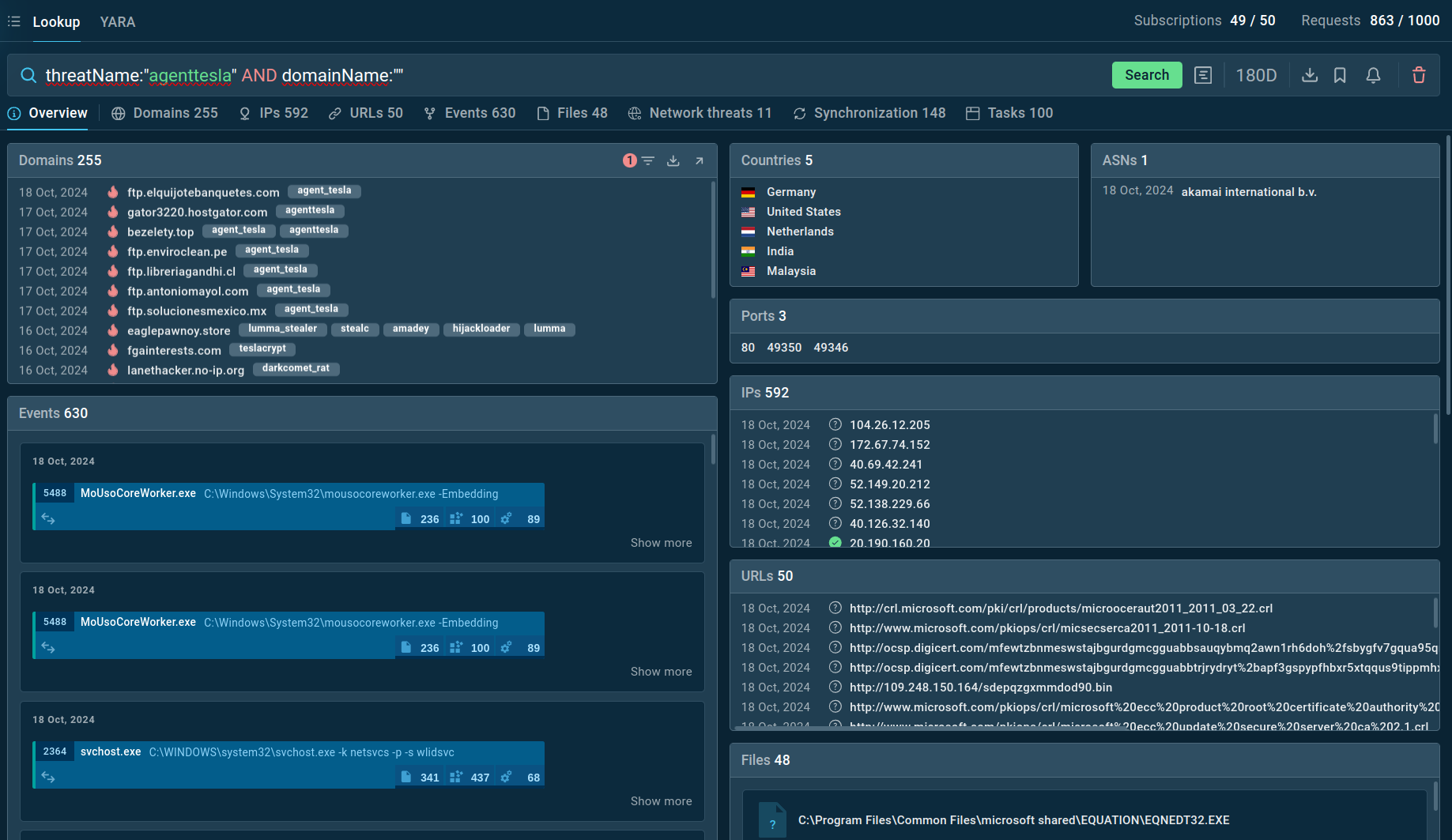 Search results for Agent Tesla in Threat Intelligence Lookup
Search results for Agent Tesla in Threat Intelligence Lookup
For example, you can search directly for the threat name or use related indicators like hash values or network connections. Submitting a query such as threatName:"agenttesla" AND domainName:"" will generate a list of files, events, domain names, and other data extracted from Agent Tesla samples along with sandbox sessions that you can explore in detail to gain comprehensive insights into this malware’s behavior.
According to threat intelligence reports, since its creation, Agent Tesla trojan has been used by over 6,300 customers. Unfortunately, the popularity of the virus is only continuing to rise. The upward trend is of, course, supported by the ease of use which allows even novice attackers to set up attacks.
A company-like service provided by the virus creators also plays a significant role. The danger of Agent Tesla for incident response and threat intelligence teams lies not only in the fact that it can be used by almost anybody but also in its ability to open doors to more destructive viruses. Thankfully, interactive analysis services such as ANY.RUN allows professionals to examine the malware behavior in detail and set up appropriate security responses.
Create your free ANY.RUN account to analyze malware and phishing without limits!