Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Akira Ransomware emerged in March 2023 and compromised over 250 organizations by January 2024 with approximately $42 million in ransom payments. It employs double extortion tactics exfiltrating data before encryption and threatening to publish it on a dedicated website.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
1 March, 2023
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 March, 2023
First seen
:
|
27 February, 2026
Last seen
:
|

 787
787
 0
0

 478
478
 0
0

 2728
2728
 0
0
Akira is a ransomware-as-a-service that became known in the spring of 2023 as a weapon in the hands of Howling Scorpius group. Its ability to adapt, exploit vulnerabilities, and employ double-extortion tactics makes it a significant cybersecurity concern. That perception has been well-supported by hundreds of victims with ransom payments surpassing $40 mln.
It targets a spectrum of industries, including finance, technology, healthcare, education, and manufacturing. Being a human-operated ransomware, it can be manually adapted to bypass network defenses.
This ransomware uses a variety of methods to gain initial access to networks, often exploiting weaknesses in external-facing systems or human error. The methods include phishing, stolen credentials, VPN vulnerabilities, exploit kits and RMM tools.
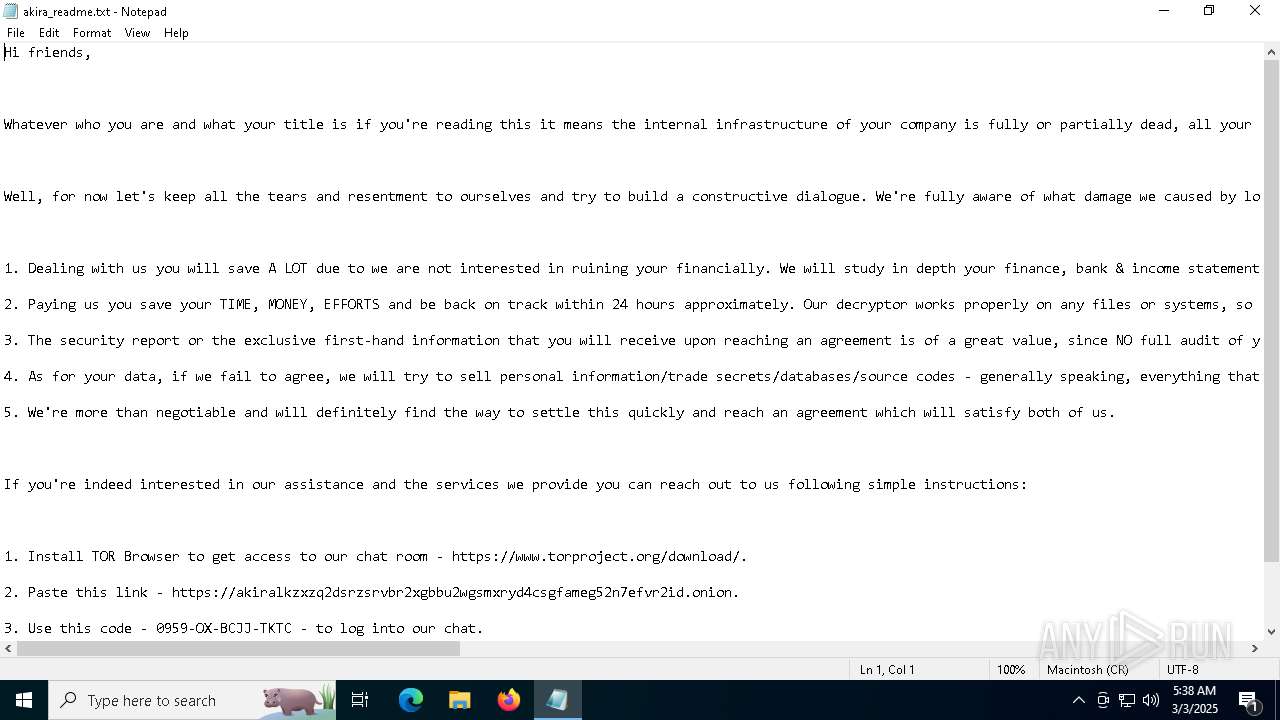 Akira Ransomware ransom note shown inside ANY.RUN's Interactive Sandbox
Akira Ransomware ransom note shown inside ANY.RUN's Interactive Sandbox
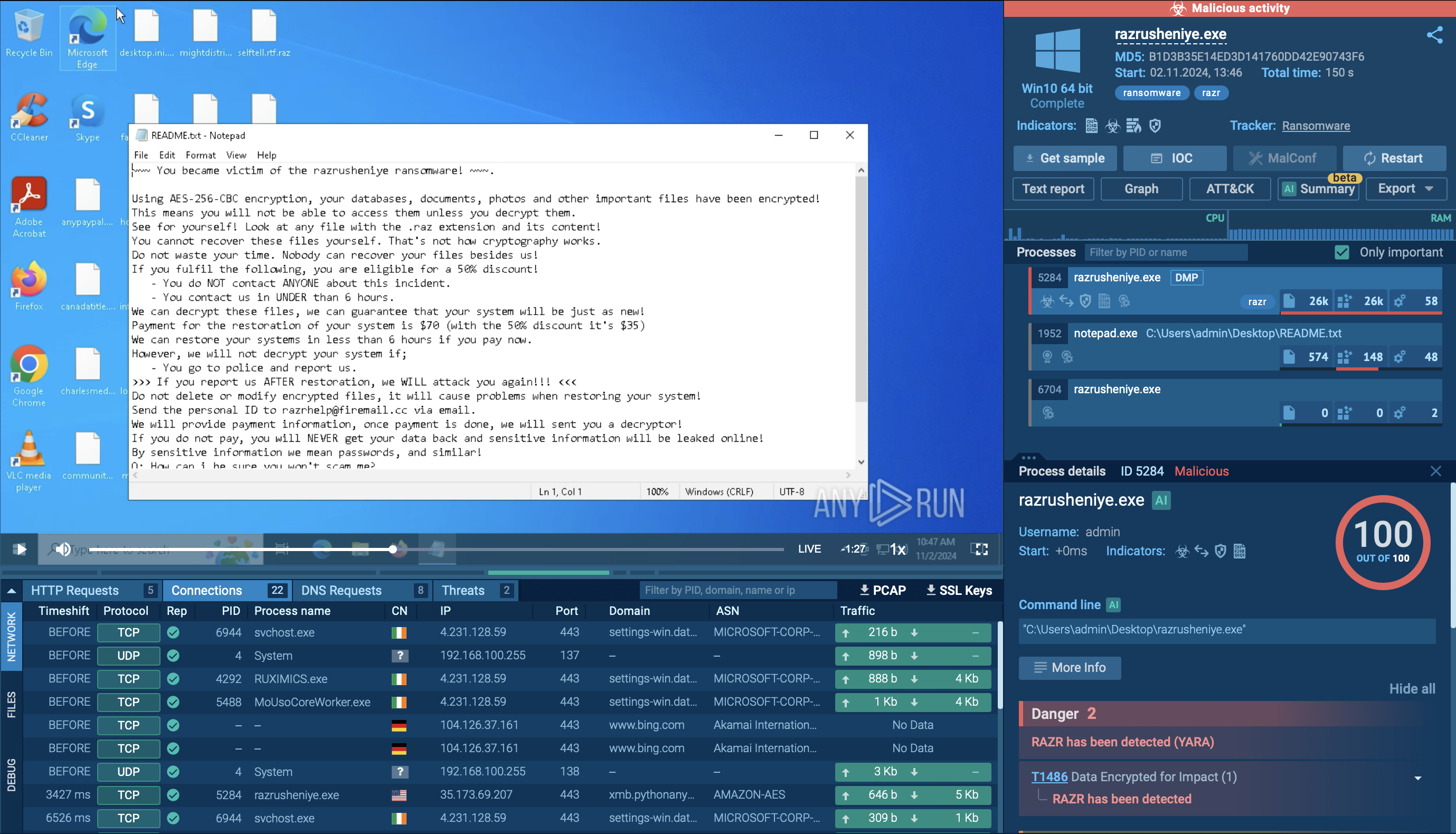
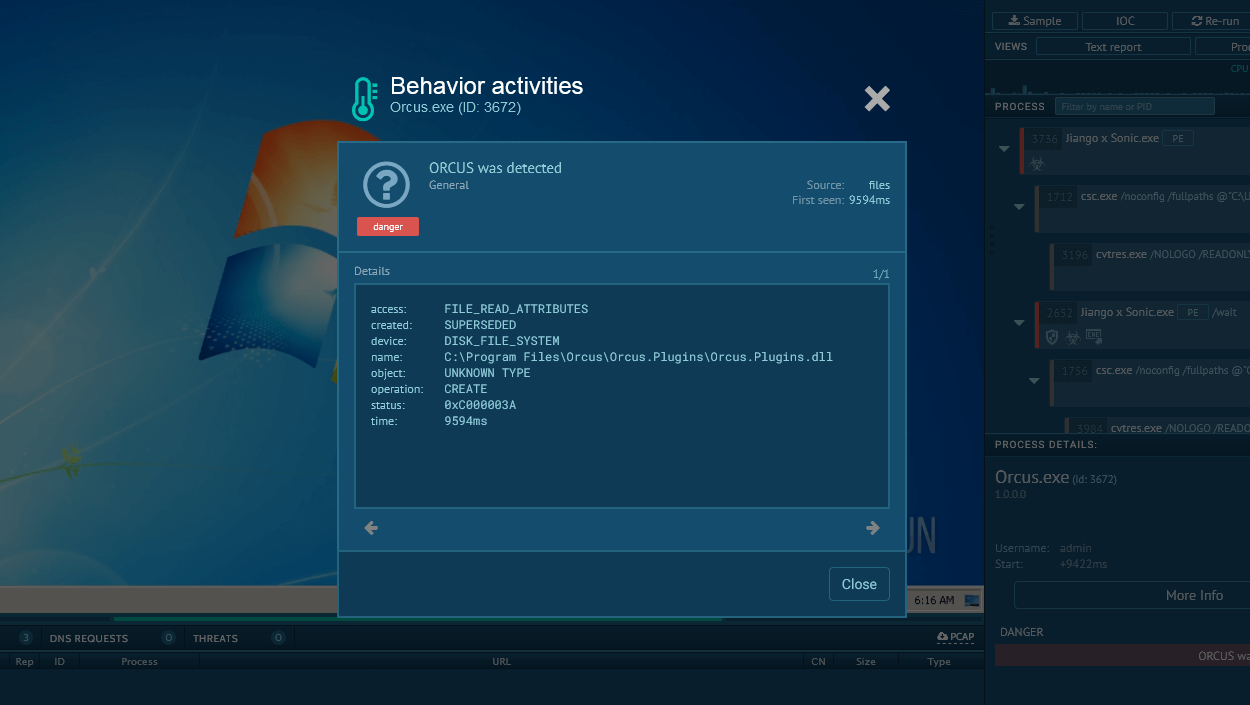
Once inside the network, Akira conducts a multi-stage attack: first it creates scheduled tasks and registry keys to maintain access, deploys backdoors to allow re-entry. It spreads in the network and scans it for valuable data. It exfiltrates the data and then encrypts it on the endpoint adding an .akira file extension which is a reference to the 1988 Japanese anime "Akira". A ransom note with payment instructions is generated.
Akira is good at evasion: it abuses native Windows tools to execute payloads, leverages process injection and living-off-the-land techniques (LOLBins). Some components execute filelessly, directly in memory, reducing the footprint on disk.
Considering the basic TTPs, Akira is similar to most ransomware families, but it has a number of outstanding features that render it notably dangerous:
ANY.RUN's Interactive Sandbox allows to detonate Akira on virtual machine with set-up parameters while bypassing its sandbox evasion capabilities.
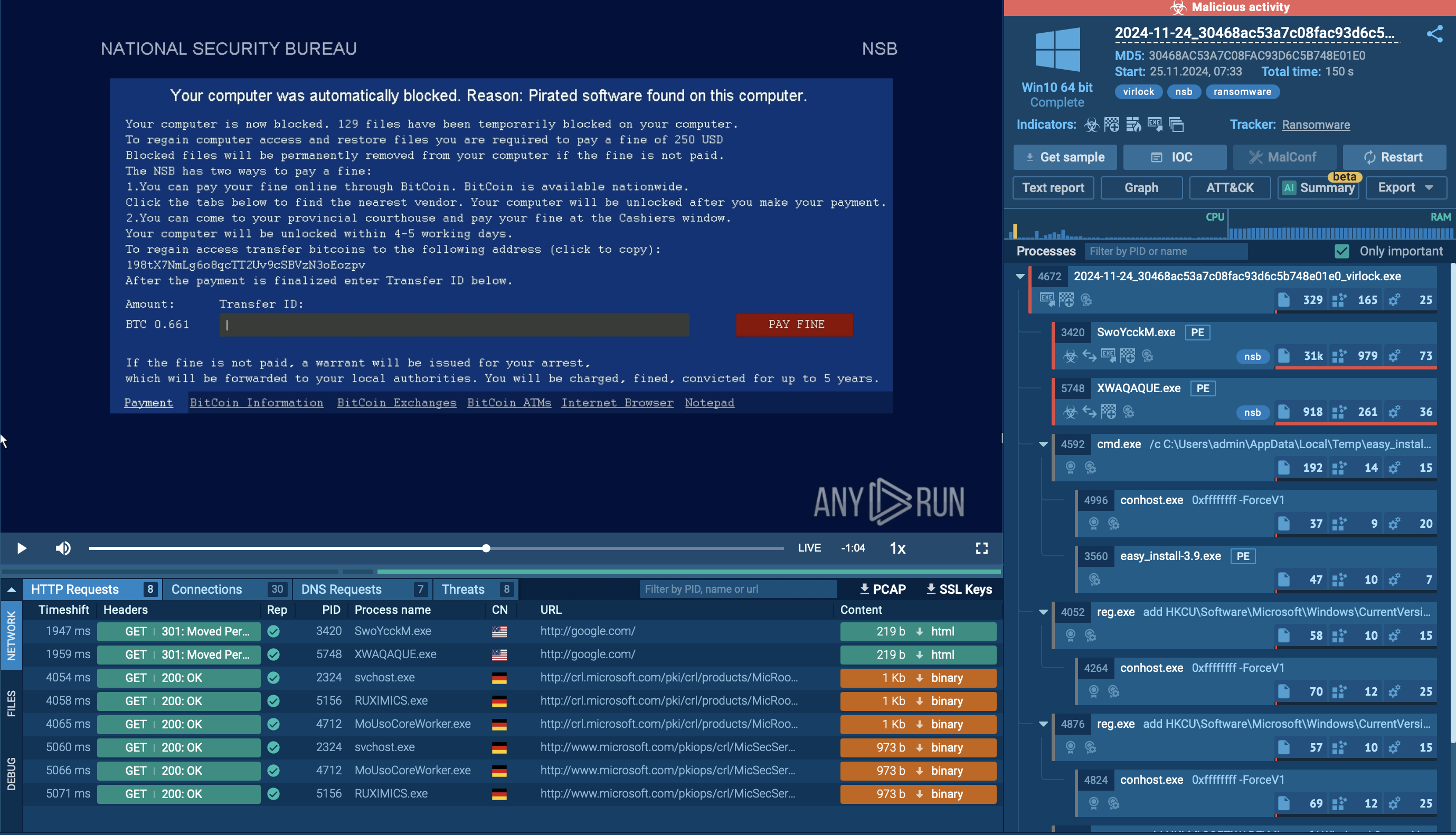
The execution chain of Akira ransomware involves several key steps, from initial access to data encryption. Initially, Akira operators may gain entry through multiple methods, including exploiting VPNs without multi-factor authentication (MFA) and other known vulnerabilities. Once inside, they focus on privilege escalation and lateral movement.
 Akira Ransomware analysis inside ANY.RUN's Interactive Sandbox
Akira Ransomware analysis inside ANY.RUN's Interactive Sandbox
Post-infiltration, Akira uses tools like Advanced IP Scanner, MASSCAN, PCHunter, SharpHound, AdFind, and net Windows commands to map networks, identify critical systems, and gather domain information.
It uses credential-dumping tools (e.g., Mimikatz, LaZagne) to extract credentials from memory (LSASS) or browsers. In some cases, Akira extracts the NTDS.dit file from domain controllers by manipulating virtual machine (VM) backups, granting access to domain admin privileges.
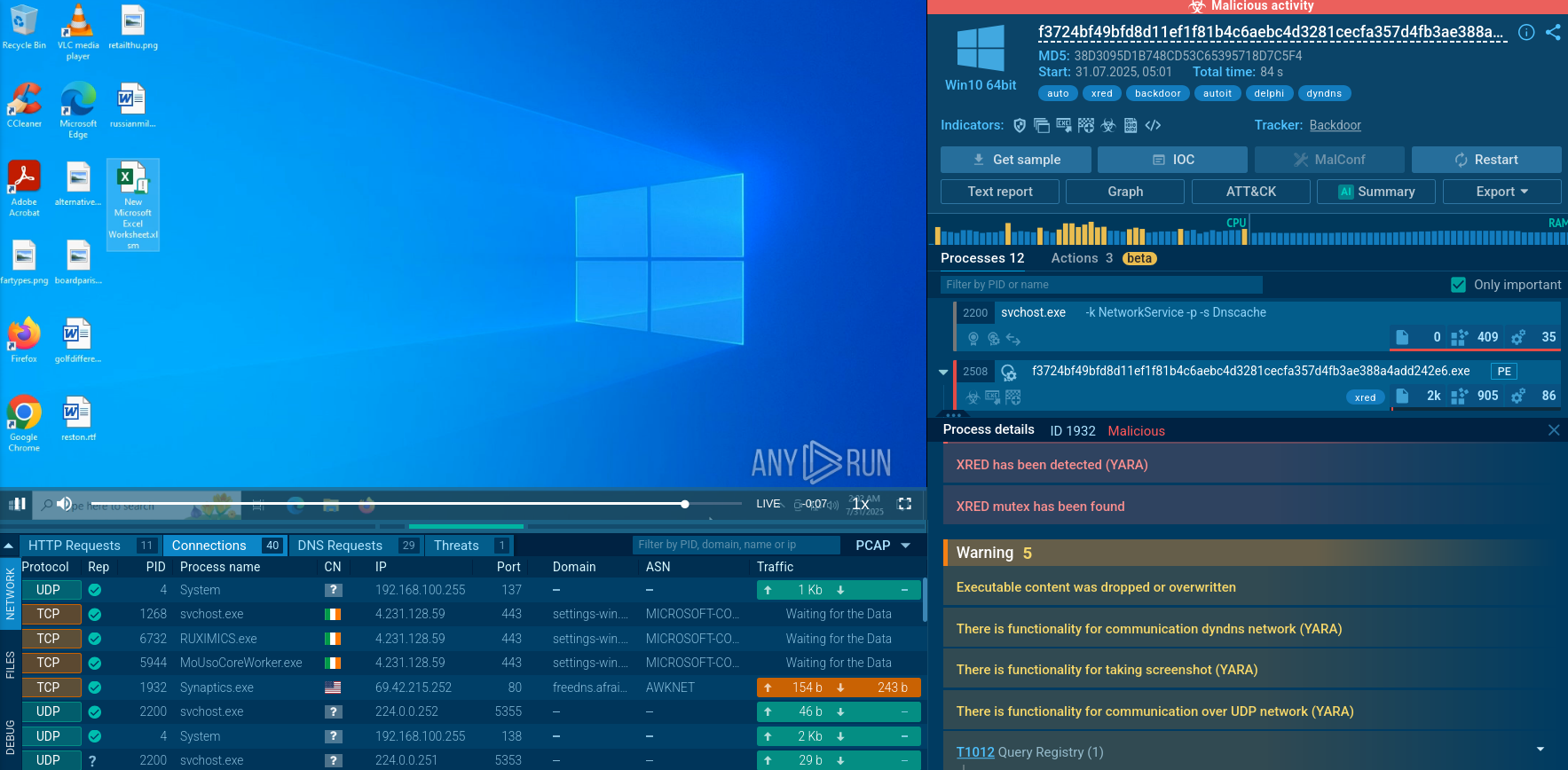
To evade detection, Akira actors employ various defense evasion strategies. They may use tools such as PowerTool, KillAV, and Terminator to disable antivirus solutions. Registry modifications are performed to disable or reconfigure Microsoft Defender and to hide accounts on the login screen, ensuring their malicious activities remain undetected for as long as possible.
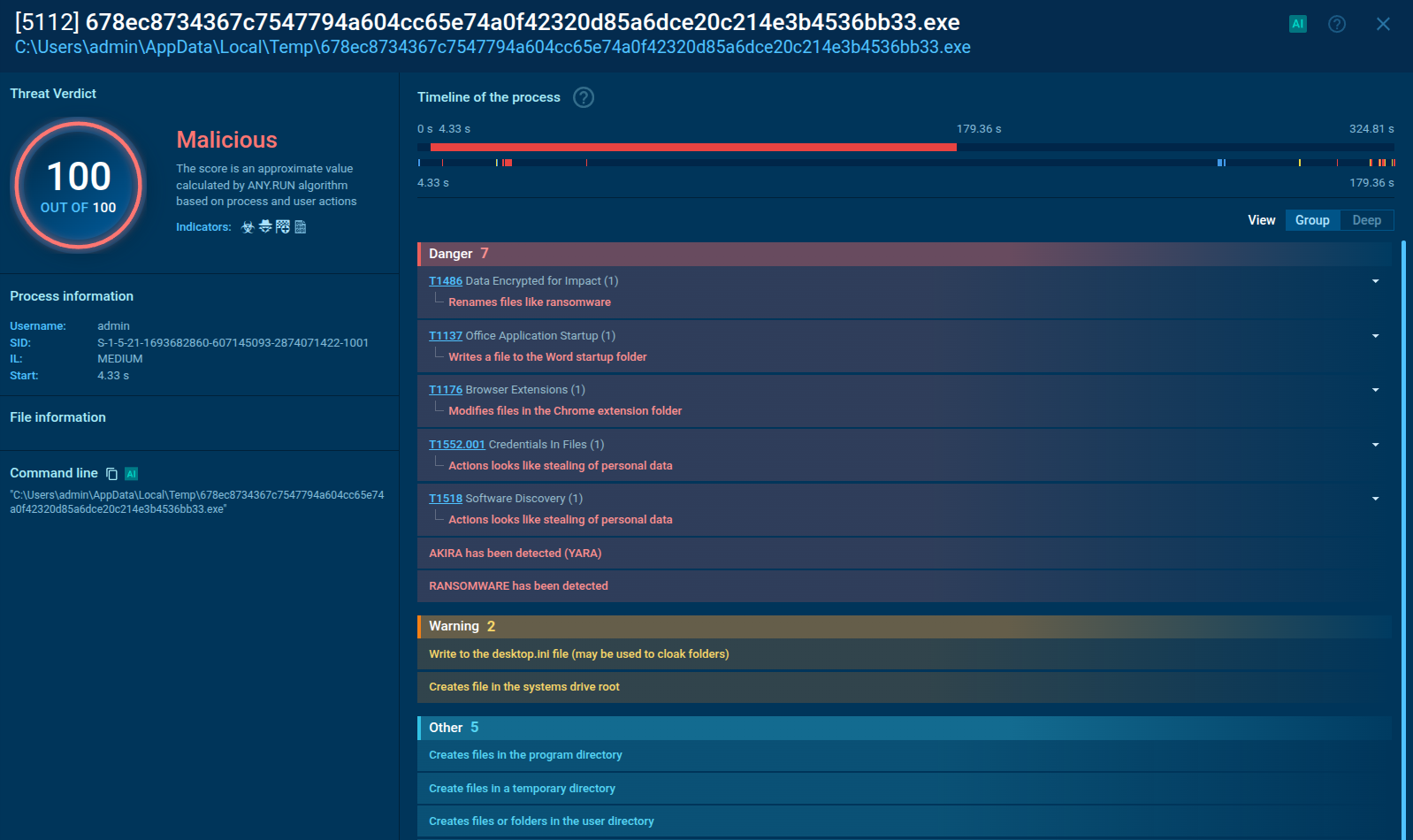 ANY.RUN highlights malicious activities performed by Akira Ransomware
ANY.RUN highlights malicious activities performed by Akira Ransomware
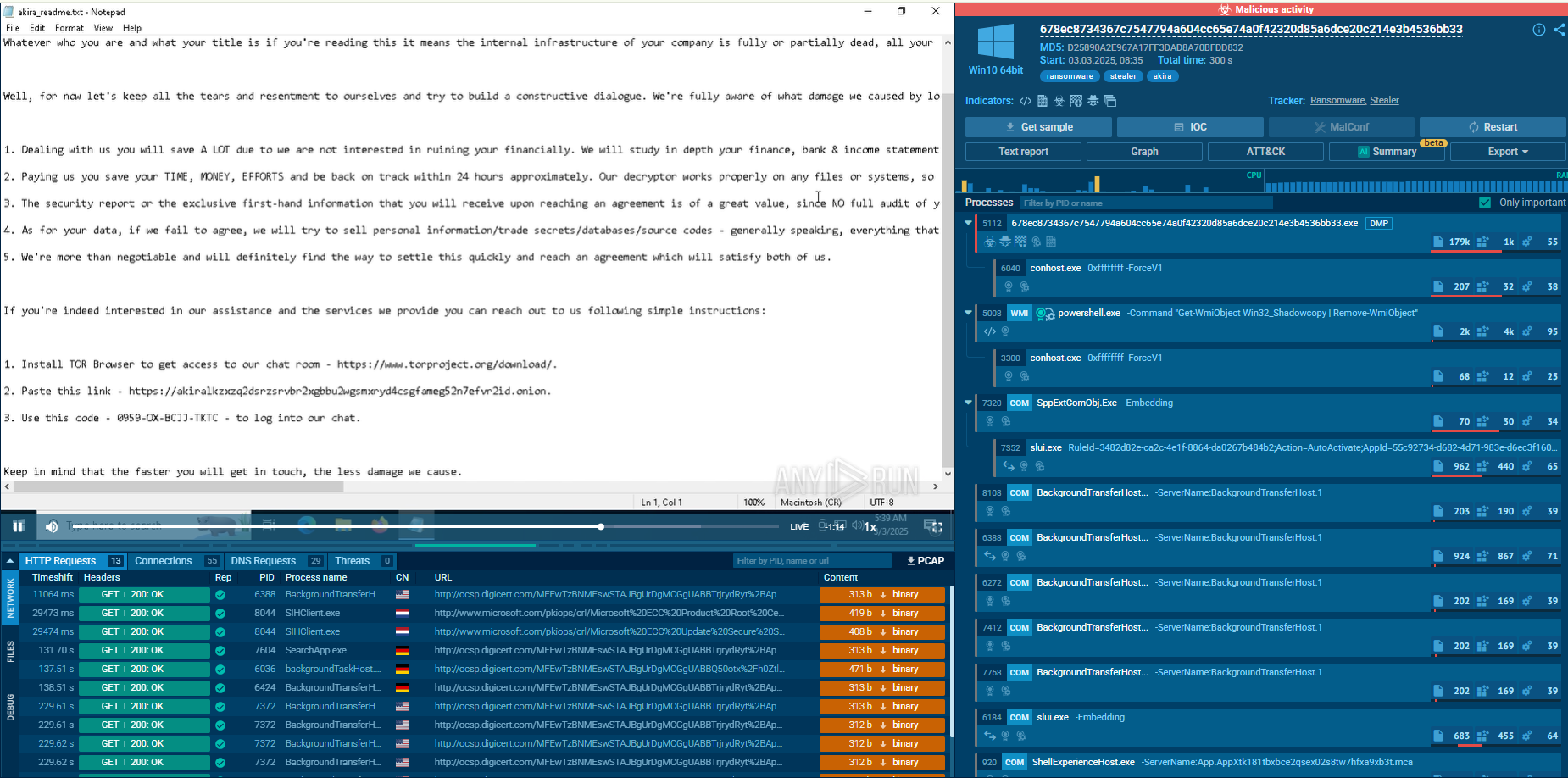
In the final stages, attackers exfiltrate and encrypt data. Akira uses a combination of ChaCha20 and RSA encryption algorithms for secure data encryption. Files are renamed with the .akira extension, and a ransom note is left behind. PowerShell commands are executed to delete Volume Shadow Copy Service (VSS) files—preventing easy file recovery.
In one observed instance, a PowerShell process (PID 5008) deleted these VSS files. Data is also compressed (using tools like WinRAR, FileZilla, WinSCP, Rclone) and exfiltrated, often camouflaged as legitimate traffic to avoid detection.
After encrypting and exfiltrating data, Akira places ransom notes, such as akira_readme.txt, in various directories. These notes provide instructions for victims to recover their encrypted files by paying a ransom. The ransom demand marks the culmination of the attack, as the attackers attempt to extort payment in exchange for the decryption key.
Akira continues to steadily spread and to result in more victims calling for special attention by SOC teams for timely prevention and response. Use Threat Intelligence Lookup to track IOCs like C2 domains, hashes, and known IPs related to Akira; apply YARA rules to identify malicious binaries and scripts.
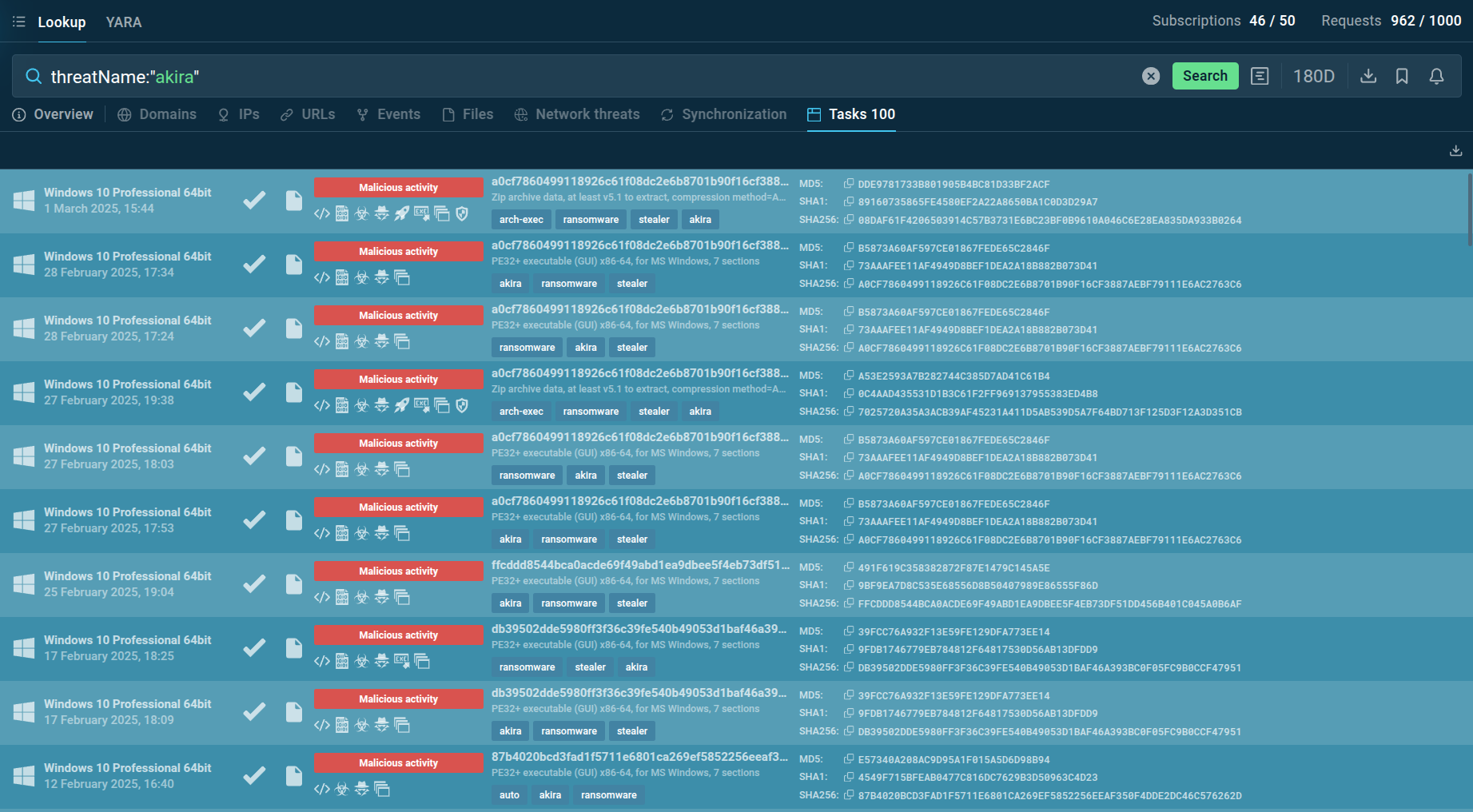 TI Lookup helps users collect fresh intel on Akira Ransomware attacks
TI Lookup helps users collect fresh intel on Akira Ransomware attacks
With the use of the query threatName:"akira", we can identify the latest samples of this ransomware and collect fresh intel.
TI Lookup provides a list of recent sandbox sessions featuring analysis of Akira Ransomware. You can explore each of these in more detail and export the findings in JSON.
Akira RaaS has emerged as a significant threat in the landscape because it enables even low-skilled actors to deploy highly sophisticated ransomware attacks and operates encryptors for Windows and Linux operating systems. Organizations should secure their perimeter and ensure proactive defense against this threat by employing threat intelligence tools like TI Lookup to gather the latest IOCs.