Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Black Basta is a ransomware-as-a-service operated by Storm-1811. It emerged in 2022 and uses double extortion tactics, encrypting data and stealing it for ransom. The malware often gains access through spear-phishing and uses tools like QakBot and Cobalt Strike. It's known for exploiting system vulnerabilities and using advanced obfuscation techniques.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
1 February, 2022
First seen
:
|
9 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 February, 2022
First seen
:
|
9 February, 2026
Last seen
:
|

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
Black Basta is a malware that falls under the category of ransomware-as-a-service (RaaS). This software is operated by the cybercrime group known as Storm-1811. First detected in 2022, Black Basta has gained attention for its tactics.
The strategy of Black Basta involves double extortion. Unlike traditional ransomware that only encrypts the victim's data, Black Basta also steals it. This dual threat strategy involves demanding a ransom for both the decryption of the data and the non-disclosure of the stolen information. The ransom demands can reach up to $2 million.
The operators of Black Basta set up a website where they publish information about their victims. This site also serves as a platform for leaking data of those who refuse to pay the ransom.
One of the first victims of Black Basta was the American Dental Association, an organization with over 100,000 members. The attack led to a partial shutdown of their infrastructure.
In their attacks, the operators of Black Basta have used QakBot as a means of initially breaching target systems. This tactic allows them to gain a foothold in the system, subsequently deploying the ransomware to encrypt and steal data. The use of QakBot underscores the complexity of the Black Basta attacks.
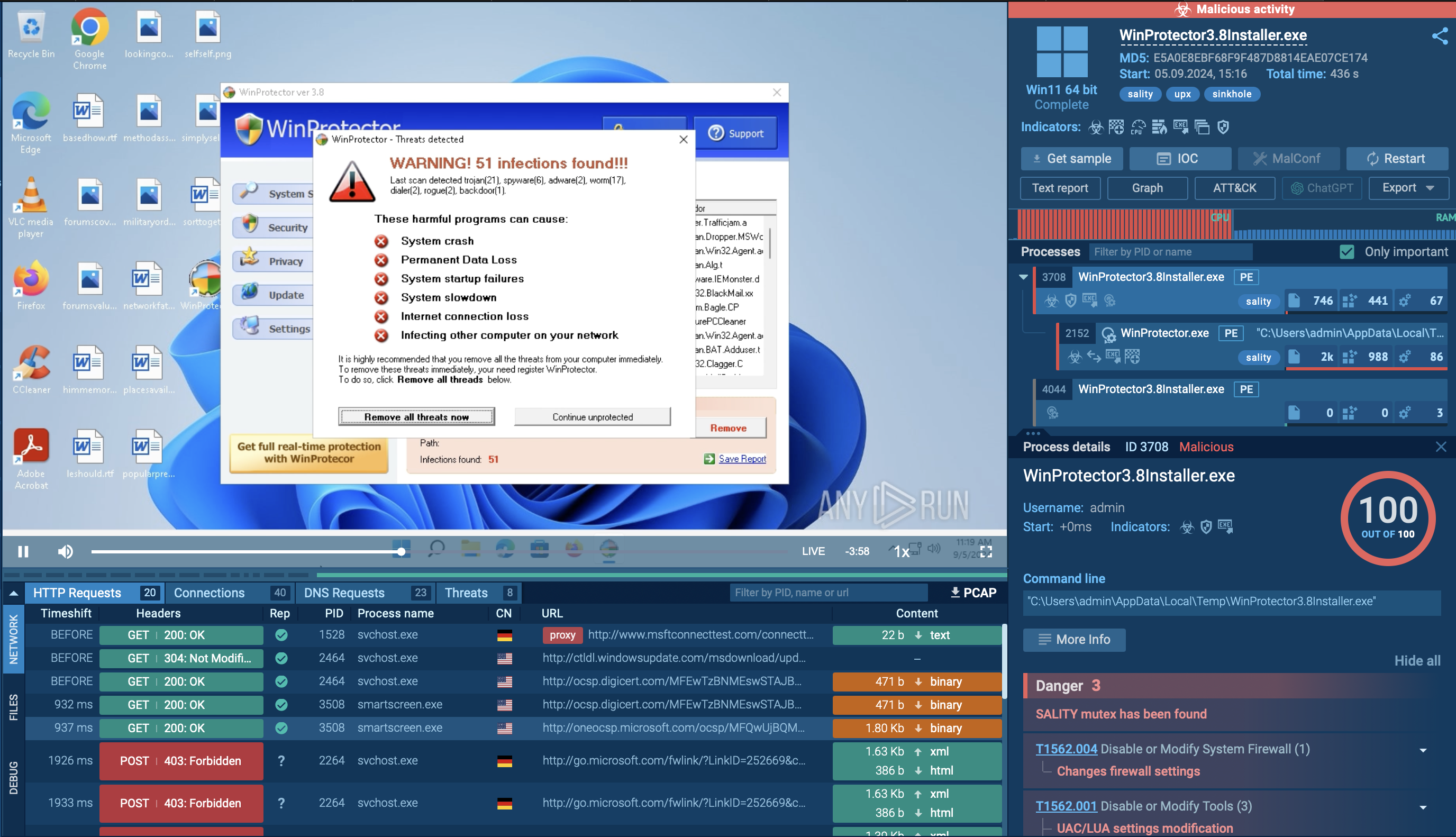
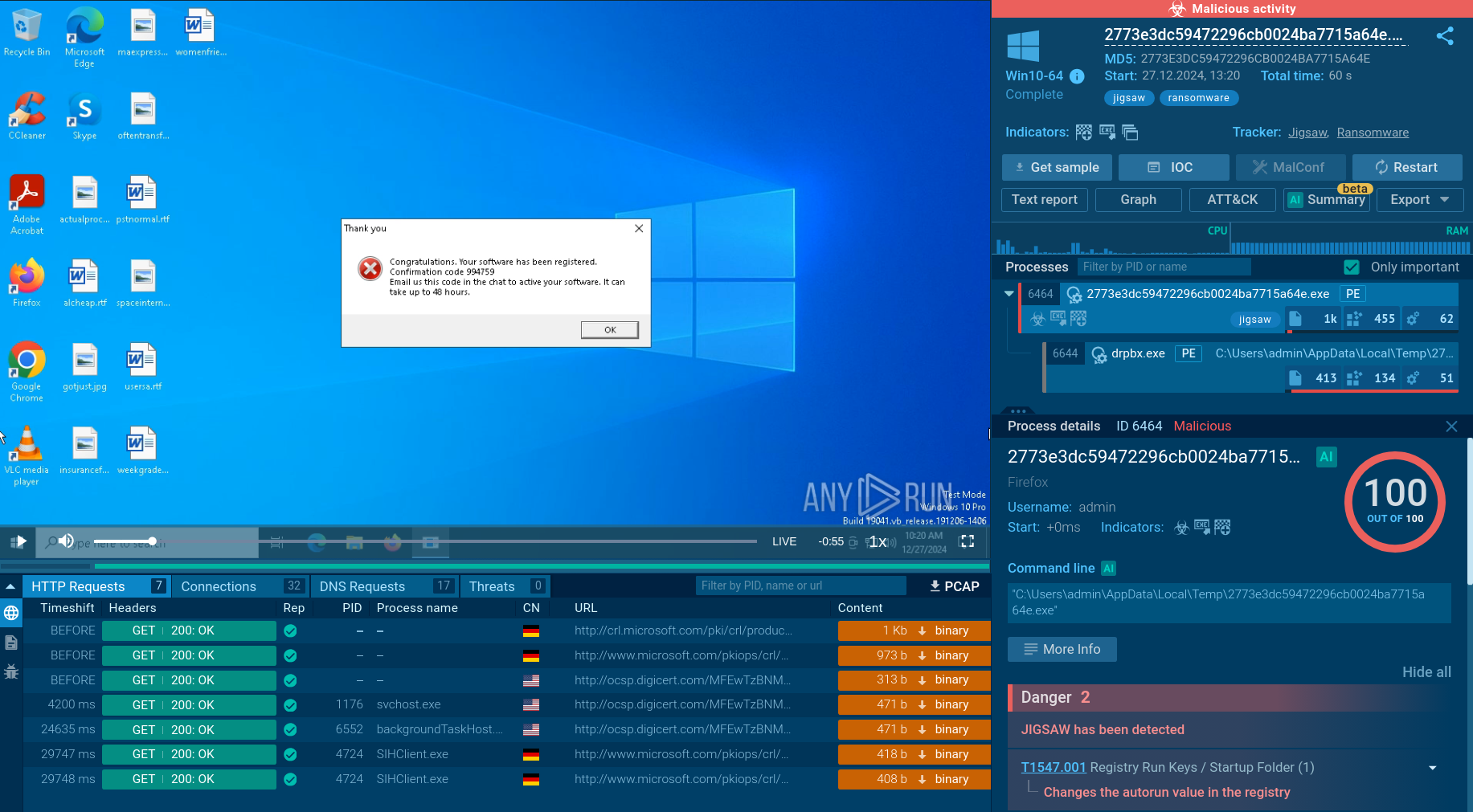
To prevent Black Basta infection, it is important to proactively upload all suspicious files and links to the ANY.RUN sandbox. Here is an example of a malicious Black Basta sample, exposed by the service. Let’s break down the entire infection chain step by step:
Step 1: Black Basta can gain initial access through compromised credentials or be delivered to the system by other malware like Qbot.
Step 2: Black Basta then gathers information about the compromised system.
Step 3: The malware operators use tools like PsExec, Windows Management Instrumentation (WMI), and RDP to move across the network and infect other systems.
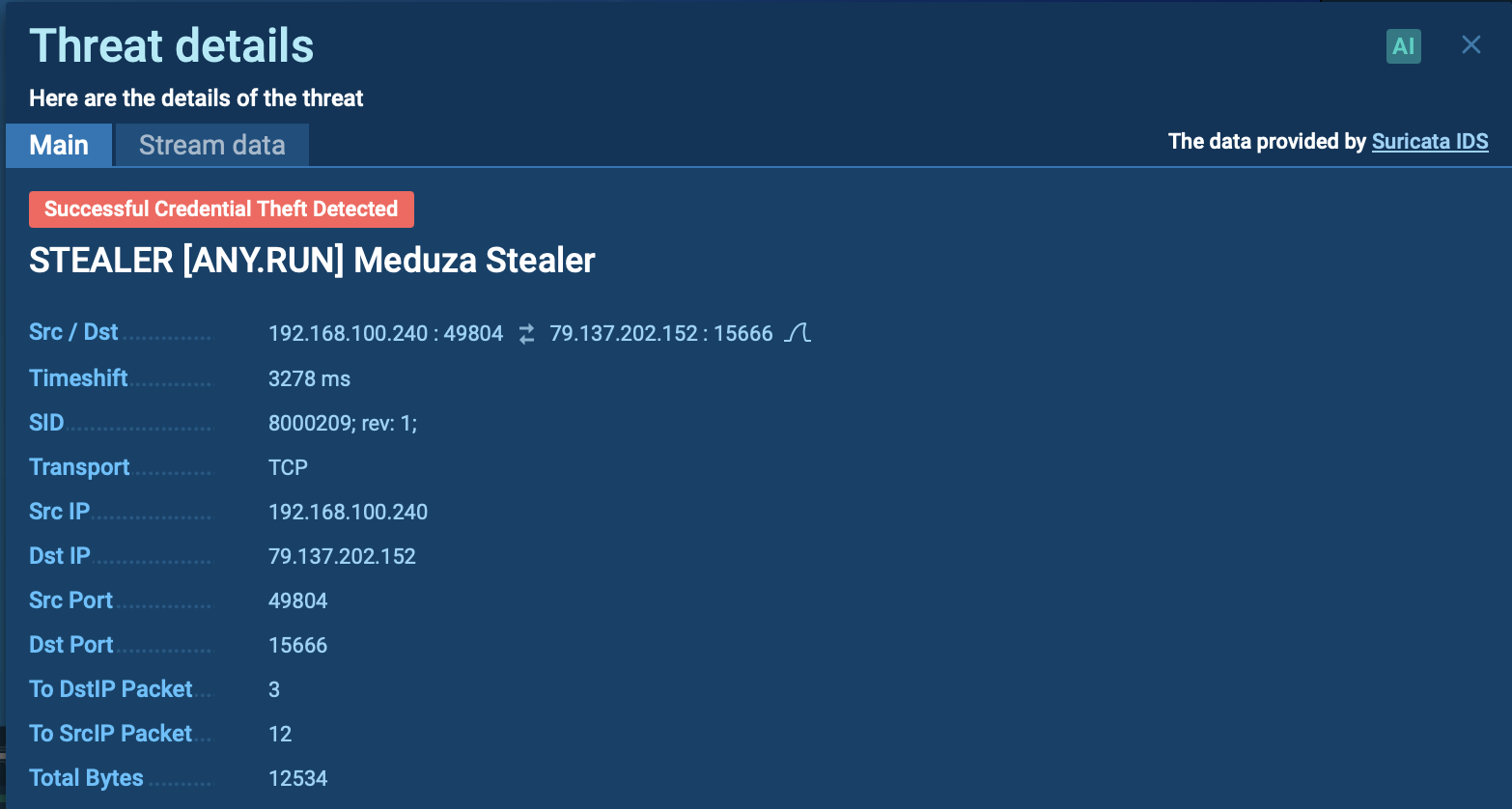
Step 4: Before deploying the ransomware, sensitive data is exfiltrated using tools like Cobeacon.
 BlackBasta wallpaper in ANY.RUN sandbox
BlackBasta wallpaper in ANY.RUN sandbox
Step 5: As mentioned, Black Basta samples can employ different versions of encryption. One of them is a hybrid encryption scheme combining ChaCha20 for file encryption with RSA-4096 for encrypting the encryption key.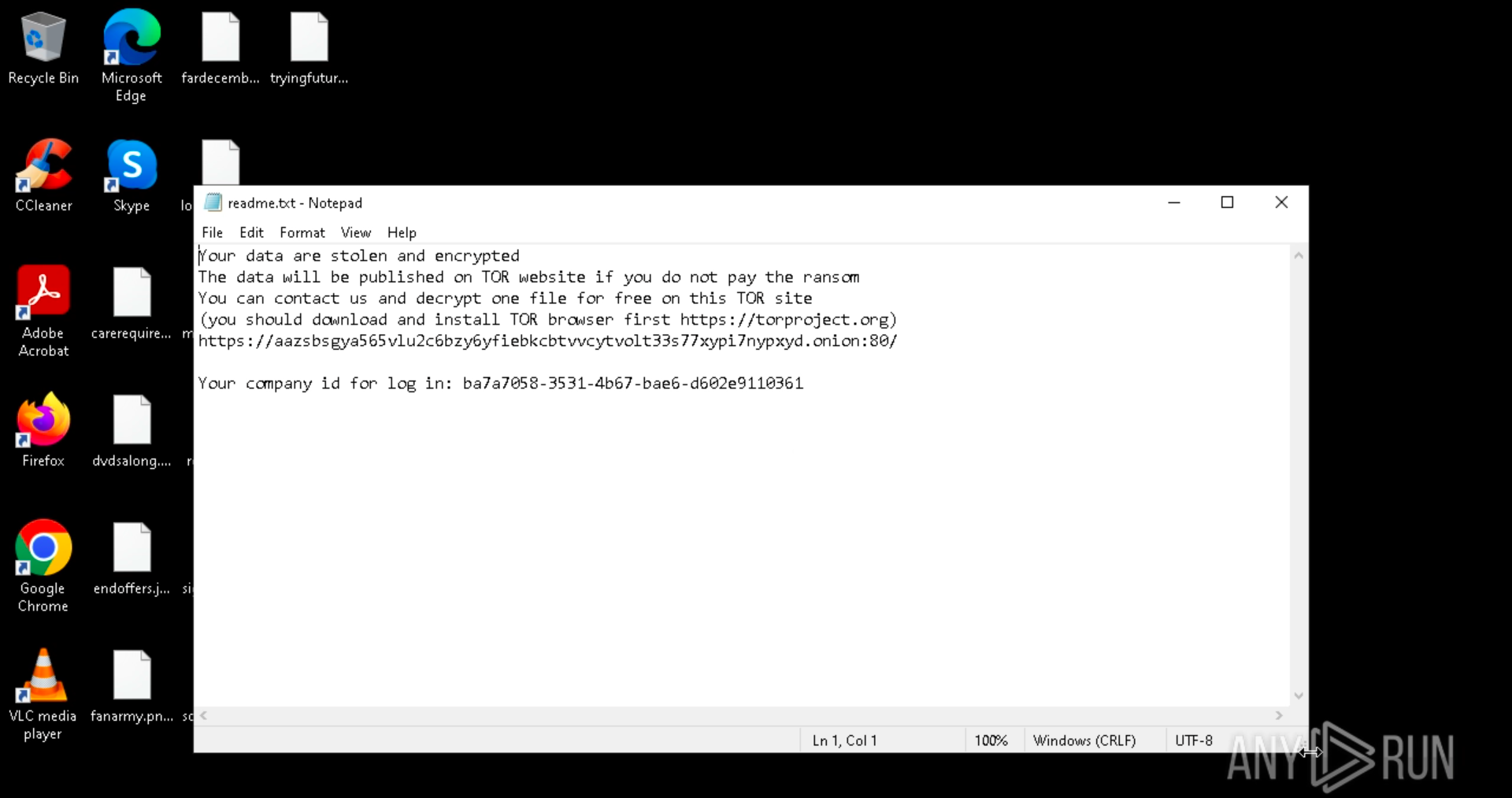 BlackBasta ransom note in ANY.RUN sandbox
BlackBasta ransom note in ANY.RUN sandbox
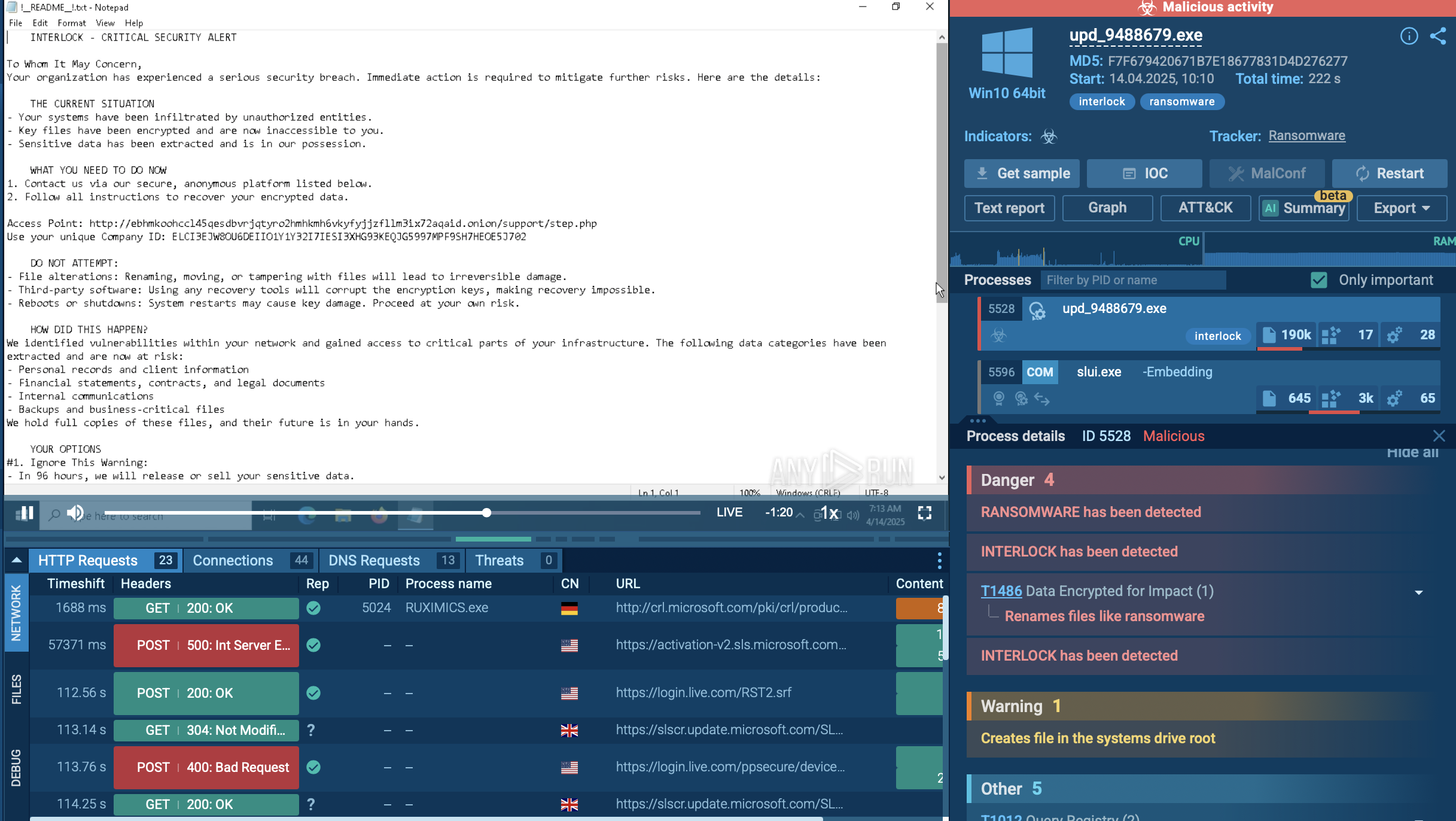
Step 6: A note is displayed on the victim's screen, and a text file with details on how to pay the ransom for decryption.
Step 7: To prevent recovery, Black Basta deletes shadow copies using commands like vssadmin.
Black Basta employs a range of technical tactics to infiltrate and manipulate target systems. One common method involves hijacking the legitimate system process 'Fax'. The malware deletes the process first, then creates a new registry path to gain elevated privileges within the system.
Once it has infiltrated the system, Black Basta deletes Windows shadow copies via 'vssadmin'. It then changes the wallpaper to announce that the user's computer has been infected by the Black Basta group. Following this, the system is restarted in safe mode.
To bypass system defenses, the malware uses PowerShell to disable active antivirus software. Earlier versions of Black Basta used the ChaCha20 encryption algorithm, later switching to XChaCha20. The malware adds the '.basta' extension to the affected files, indicating their encryption.
Instructions for the victim's further actions are provided in text documents. These documents contain a Tor address and a unique ID for the victim to log in on the website.
As mentioned, many Black Basta attacks have been known to start with QakBot. This is done to establish an initial foothold on the system to then deliver the ransomware. Such attacks begin with the victim unsuspectingly downloading an Excel document with macros. The attack then leads to the malware download and installation process.
The operators of Black Basta also employ Cobalt Strike as a means of scanning the system. This tool allows them to gather information about the target system, identify vulnerabilities, and tailor their attacks accordingly.
The newer versions of the malware, emerging in 2023, utilize advanced obfuscation techniques to evade detection. The malware can also modify the registry to run automatically upon system startup.
Black Basta can also collect credentials stored on the system, further compromising system security.
The latest variants of Black Basta exploit the CVE-2024-1709 vulnerability. The malware is capable of performing lateral movement via tools like PsExec and Cobalt Strike, spreading the infection across the network.
In addition to these tactics, the attackers have started using Quick Assist, a legitimate program for remote connection, as part of their social engineering attacks. This tool allows them to gain remote access to the victim's system, further facilitating the malware's activities.
Black Basta operators often get into systems by using compromised login information. To do this, they work with Initial Access Brokers (IABs), selling access to already hacked networks. In return, they receive a share of the profits.
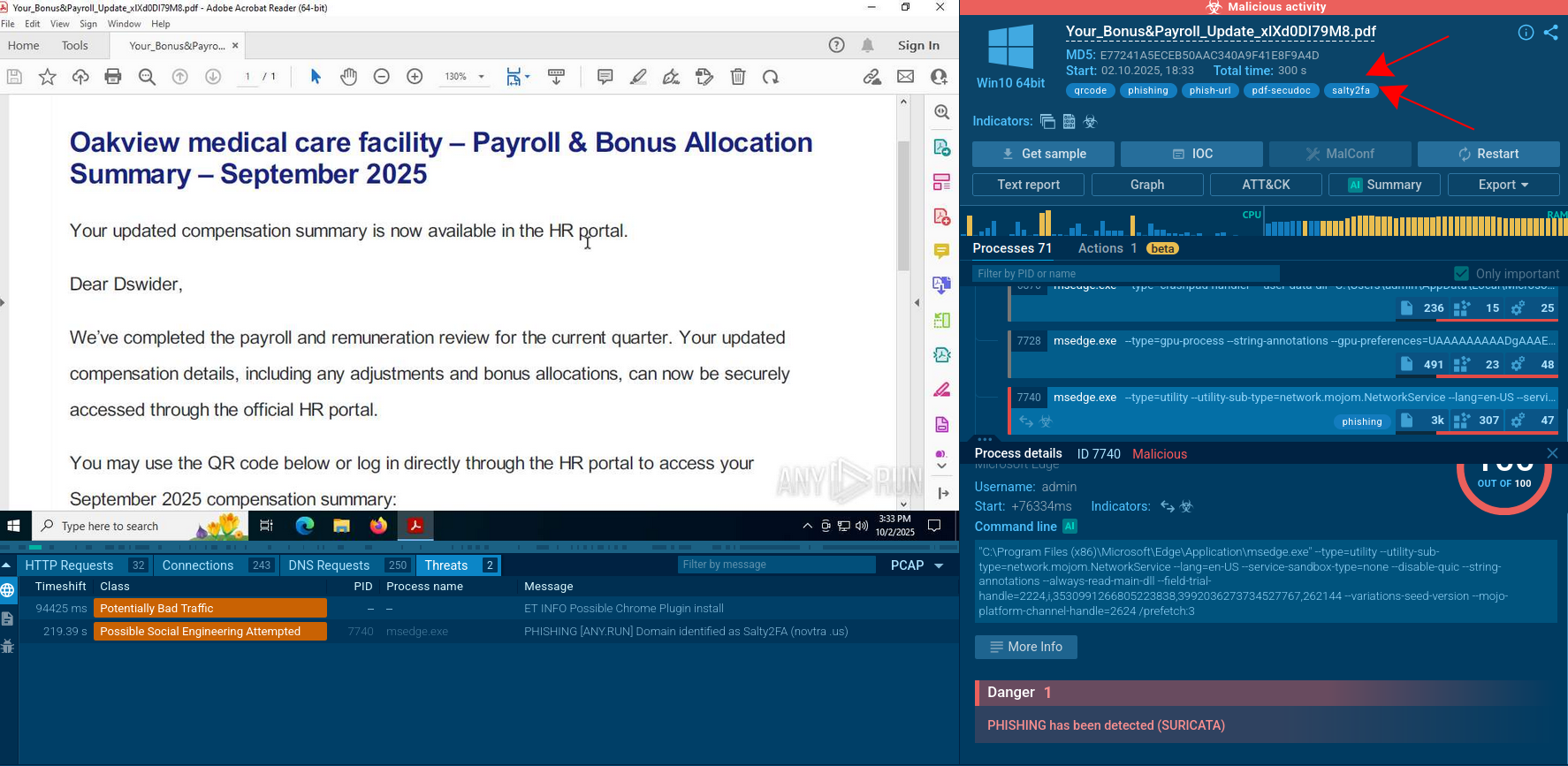
Many Black Basta attacks also begin with spear-phishing campaigns. These campaigns involve sending targeted emails to victims, often disguised as legitimate correspondence. The emails typically contain malicious attachments or links, which, when clicked or downloaded, initiate the malware infection process.
The latest attacks featuring Black Basta also include vishing, or voice phishing. This involves the impersonation of tech support or help desk personnel. The attackers use Quick Assist, a legitimate remote access tool, to trick users into entering a code provided by the attackers. This code allows the attackers to establish remote control over the victim's computer, subsequently downloading malicious files onto the host system.
Black Basta's double extortion, concealment, and abuse of system vulnerabilities make it a significant threat for organizations worldwide. To keep safe from ransomware, it's crucial to adopt suitable cybersecurity practices, including employing a sandbox for analyzing malware.
ANY.RUN's interactive sandbox offers various tools that make malware analysis simpler and faster. It can: