Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


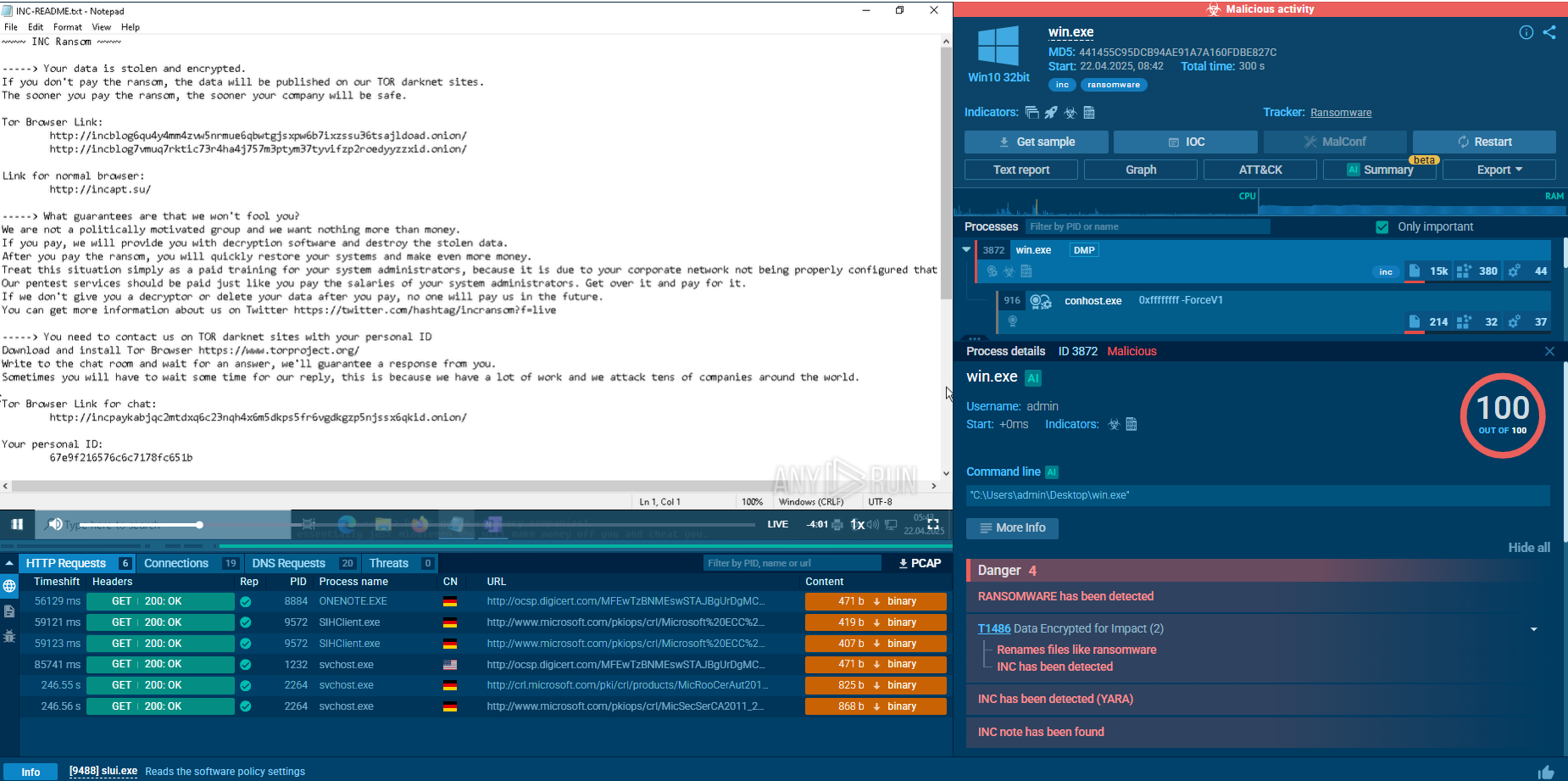
WannaCry is a famous Ransomware that utilizes the EternalBlue exploit. This malware is known for infecting at least 200,000 computers worldwide and it continues to be an active and dangerous threat.
|
Ransomware
Type
:
|
Likely North Korea
Origin
:
|
|
12 May, 2017
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
Likely North Korea
Origin
:
|
|
12 May, 2017
First seen
:
|
27 February, 2026
Last seen
:
|

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
WannaCry, sometimes also called WCry or WanaCryptor is ransomware malware, meaning that it encrypts files of its victims and demands a payment to restore the stolen information, usually in bitcoin with ransom amounts ranging from $300 to $600 equivalents.
The virus can be described as ransomware like Dharma or Ryuk but with worm functionality, since it is capable of spreading itself within infected networks using the EternalBlue exploit. Additionally, the virus uses DoublePulsar exploit to upload and execute a copy of itself to a new machine.
Once WannaCry makes its way into a target computer, it begins its malicious activity by checking for a hardcoded kill switch domain - either fferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com or iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com. In the event, if one is found, the malware stops the execution. However, if a kill switch domain isn’t found, the ransomware encrypts files on the machine, following which an attempt to exploit the SMB vulnerability takes place. This is done in an effort to spread the virus over to other random PCs and all those connected to a local network. After encryption is completed, a ransom note is displayed to the user and the attackers demand $300 to be paid in a 3-day timespan. If the victim resists the ransom amount rises to $600 to be paid in 7 days. The payments are directed to multiple hardcoded bitcoin addresses. Typical for a cryptocurrency, anybody can check their balances and transaction history but the true owner of such a wallet can not be traced.
The first time WannaCry malware was seen in the wild was as a part of a devastating worldwide attack that took place in May 2017. The attack utilized an EternalBlue exploit, which was believed to have been developed by the American NSA and leaked by a cybergang known under the allies “The Shadow Brokers”.
The exploit leveraged a vulnerability in the Windows operating systems and while a patch fixing the issue was released quickly by the company, many individuals and organizations who didn’t promptly update their computers became victims of this attack.
By some broad estimations, over 200,000 computers worldwide were infected by WannaCry within those few days that the attack was ongoing. A fix of the EternalBlue exploit along with the discovery of the “kill switch” that allowed to stop the execution of the malware were the two main contributions that helped to slow down this malicious campaign. However, by the time the attack came to an end total damage amounted to billions of dollars, and victims from over 150 countries were affected.
A campaign of such scale raised international investigation of the highest level aimed to find out who was behind the outbreak. During WannaCry hack analysis experts investigated the ransom notes to find out that they were most likely written by hand and the writers seemed to be fluent in Chinese and English, as was suggested by the linguistics analysis. Further investigation suggested that the native language of the writer was Chinese since two versions of ransom note were composed in this language - one in Simplified and one in Traditional Chinese. Furthermore, some typos in the notes lead researchers to believe that a Chinese input system was used for typing during WannaCry cyber attack, as mistakes like those present could not have been easily made using any other form of input.
It should be noted, that in total the ransom note was written in 28 languages including both Chinese variations. However, for most of those languages, a machine translation was used.
The FBI then uncovered that Hangul fonts were installed on the machine that was used to compose the ransom notes. Hangul is an alphabet and a writing system used in the South as well as in North Korea. Further analysis of the language files metadata displayed that the computer was set to a Korean Timezone.
Upon further WannaCry ransomware attack analysis, security researchers from Google, Kaspersky Lab, and Symantec concluded that the code of WCry exhibited similarities to other malware used in the campaigns against Sony Pictures and a Bangladesh bank. Those attacks were carried out by a so-called Lazarus Group, members of which were linked to North Korea.
Of course, this evidence was not conclusive as other groups could have simply reused some of the code produced by the Lazarus Group. What’s more, the use of such code could have been intentional in order to mislead the investigators and put the blame on other cybercriminals.
However, a liked memo from NSA as well as findings made by UK's National Cyber Security Centre also pointed at North Korea as the country from which the attack originated. The United States Government subsequently proceeded to formally declare North Korea to be the attack origin.
In foresight, despite the fact that the WannaCry attack had a truly unprecedented scale, its impact is considered relatively low, compared to other ransomware. The aftermath could have been much worse if it was not for the discovery of the kill switch. Furthermore, the virus could have been targeted at high-level infrastructures like transport control systems and nuclear power plants. Had this been the case, some experts estimate possible losses in excess of hundreds of millions of dollars.
Talking about the actual WannaCry analysis - it comes in the form of a dropper that holds various components as a ZIP archive which is protected by a password. This archive is being unpacked during the execution using a hardcoded password and dropped into a directory from which it was executed.
WCry ransomware uses two encryption methods during its execution: RSA and AES-128-CBC. To confuse the researchers the encryption scenario that is contained in a t.wnry file is actually encrypted in exactly the same way that the malware uses to encrypt data on an infected machine. A custom loader is used to load the module into memory, so the unencrypted version of the file never has to be recorded on the victim’s hard drive.
Upon the start of the execution process, the malware uses an RSA key to unpack the t.wnry file and decrypt it. Then a new RSA key will be generated and sent to a C&C server, while a duplicate of a public key is being saved on the infected machine.
This is where the malware starts to encrypt files – the virus searches the infected machine for files with supported extensions. Then, a 128 bit AES key is created per every single file that was selected for encryption and encrypted using the RSA key created earlier. RSA-encrypted AES key is placed in a header of an encrypted file. After this, the malware uses the AES key to encrypt data in the file.
The encryption is performed in such a way that it is virtually impossible to restore the lost data without access to the private key, that is stored in the control server. This means that for a victim the only way to regain access to their information is to fulfill the ransom demand, made by the attackers.
For persistence, WCry writes itself in the autorun keys in the registry and creates a couple of services.
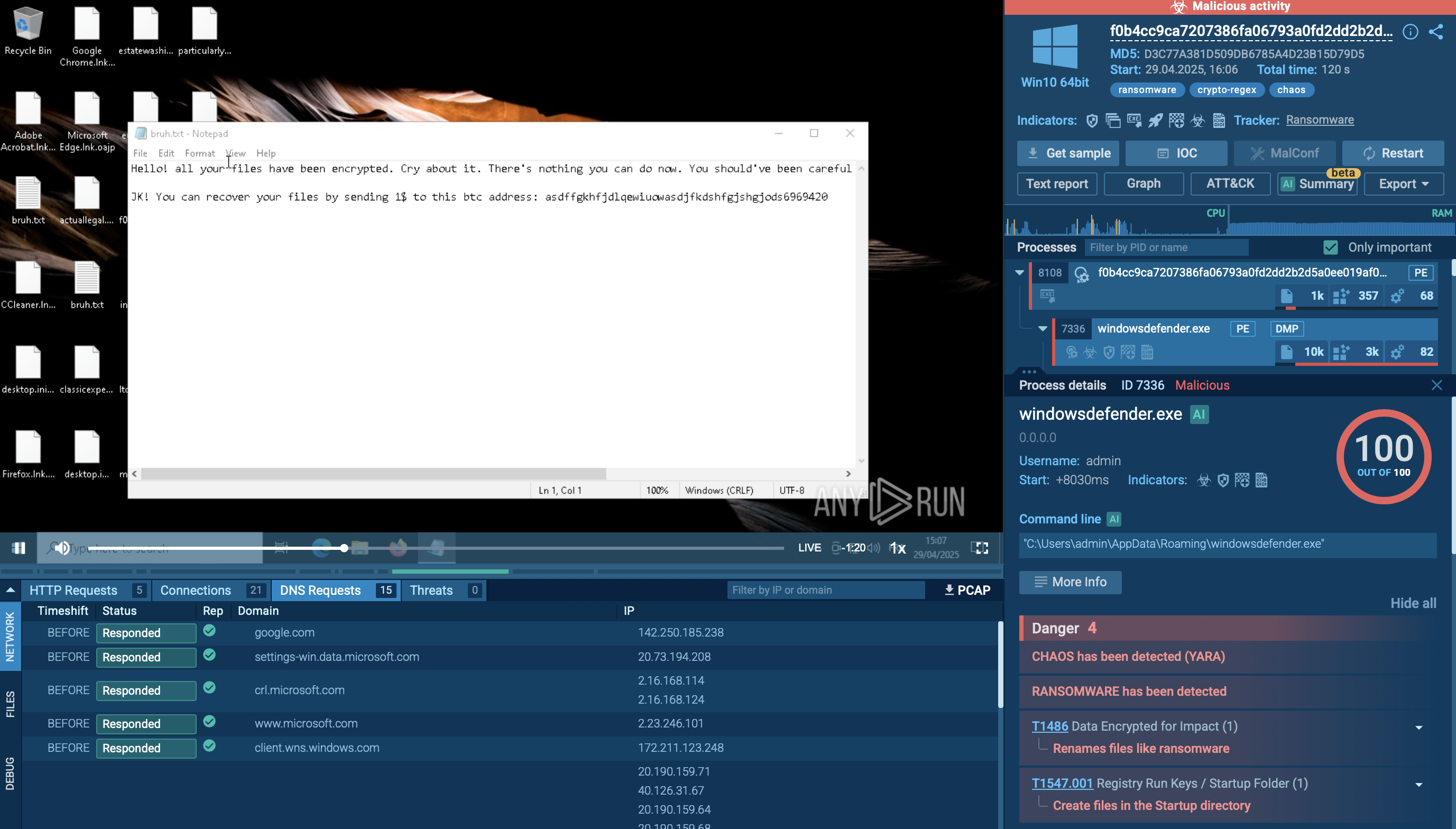
A video simulation recorded on ANY.RUN allows us to better understand what is WannaCry ransomware and examine the lifecycle of WannaCry.
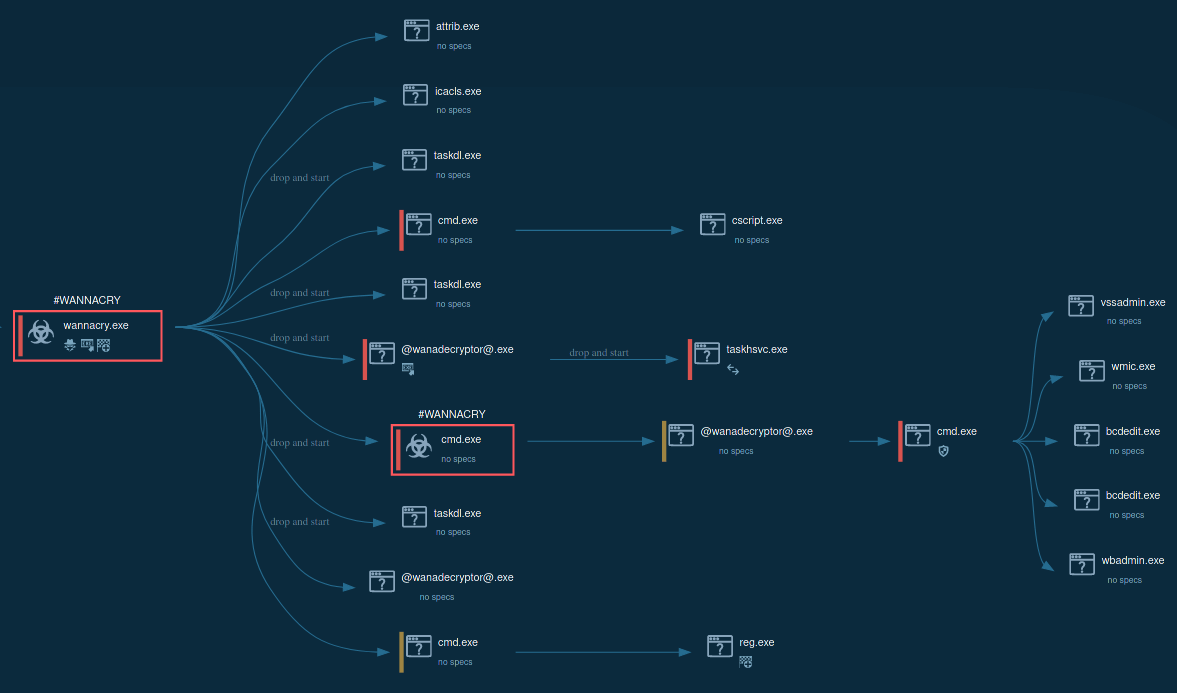
Figure 1: Process graph generated by ANY.RUN allows us to see the main processes of WannaCry execution.
Figure 2: Displays the customizable text report generated by ANY.RUN.
Besides being distributed by malicious spam campaigns, ransomware uses a more interesting way to infect devices - it utilizes an operating system vulnerability as the initial attack vector. Once the malware successfully leverages an exploit and makes its way into a machine, it will scan the IP addresses in an attempt to infect connected devices through the SMB vulnerability on port 445/TCP. This vulnerability has CVE ID 2017-0144 and is also known as MS17-010 EternalBlue.
All devices in a local network exhibiting potential vulnerability will also be infected.
First of all, after running, WCry sends an HTTP GET request to hardcoded domains and stops execution if the request is successful. Although the WannaCry execution process is pretty straightforward, it does not just encrypt files on the infected machine, but it's also trying to infect as many nearby machines as it can. To do so, the ransomware scans all machines with port 445 being open and if the connection is made, tries to exploit the SMBv1 vulnerability (EternalBlue). On the local system, WannaCry executable file extracts and installs binary and configuration files from its resource section.
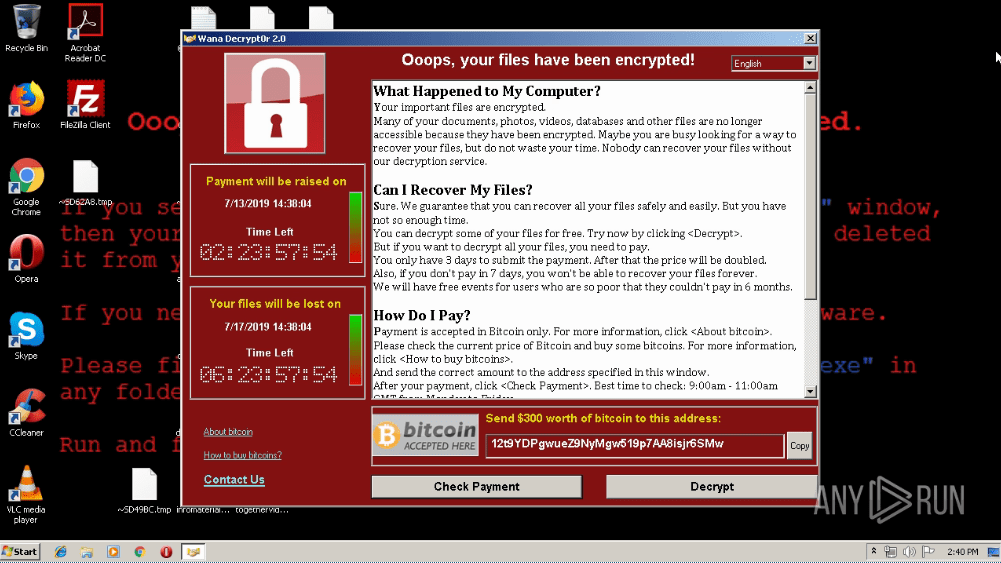
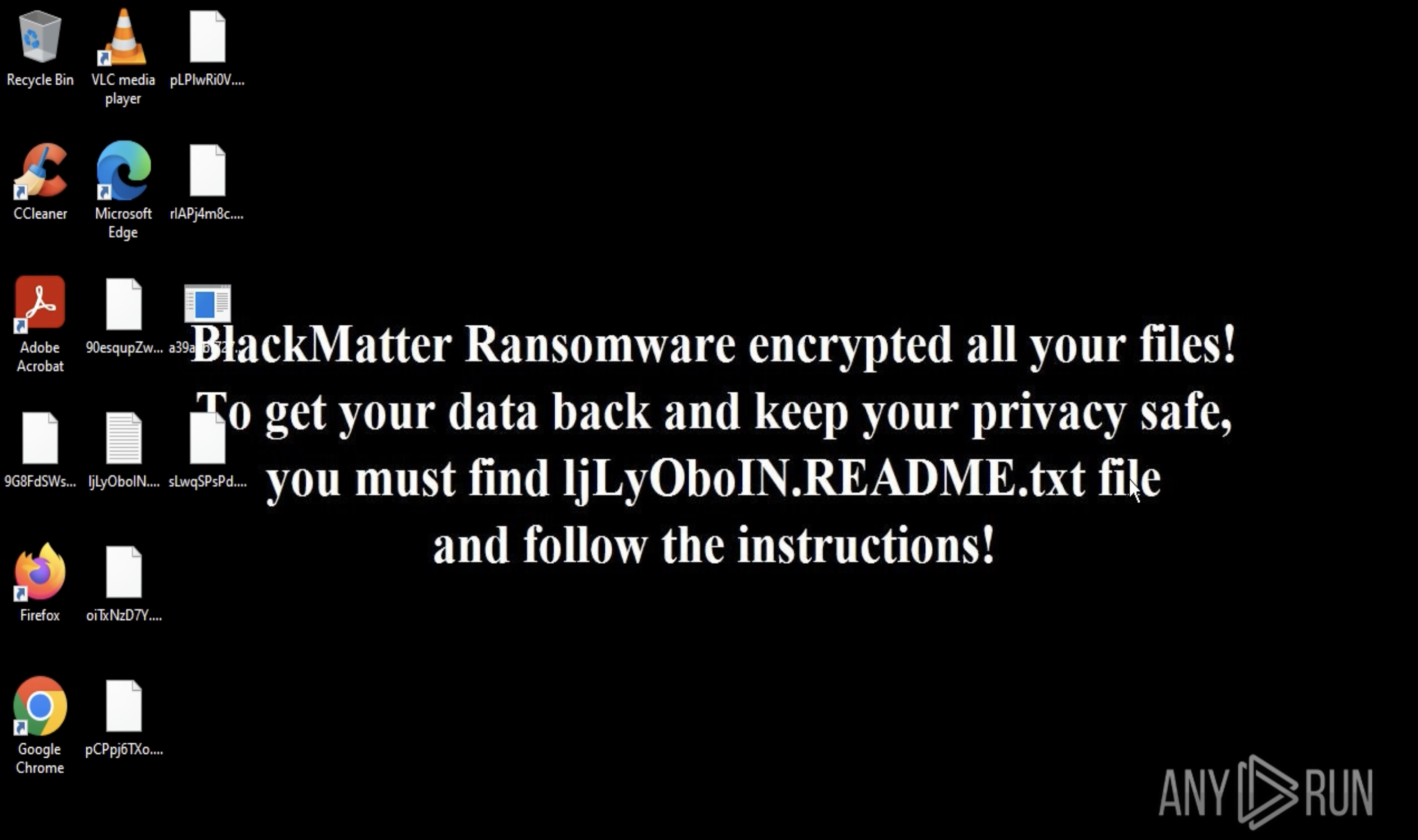
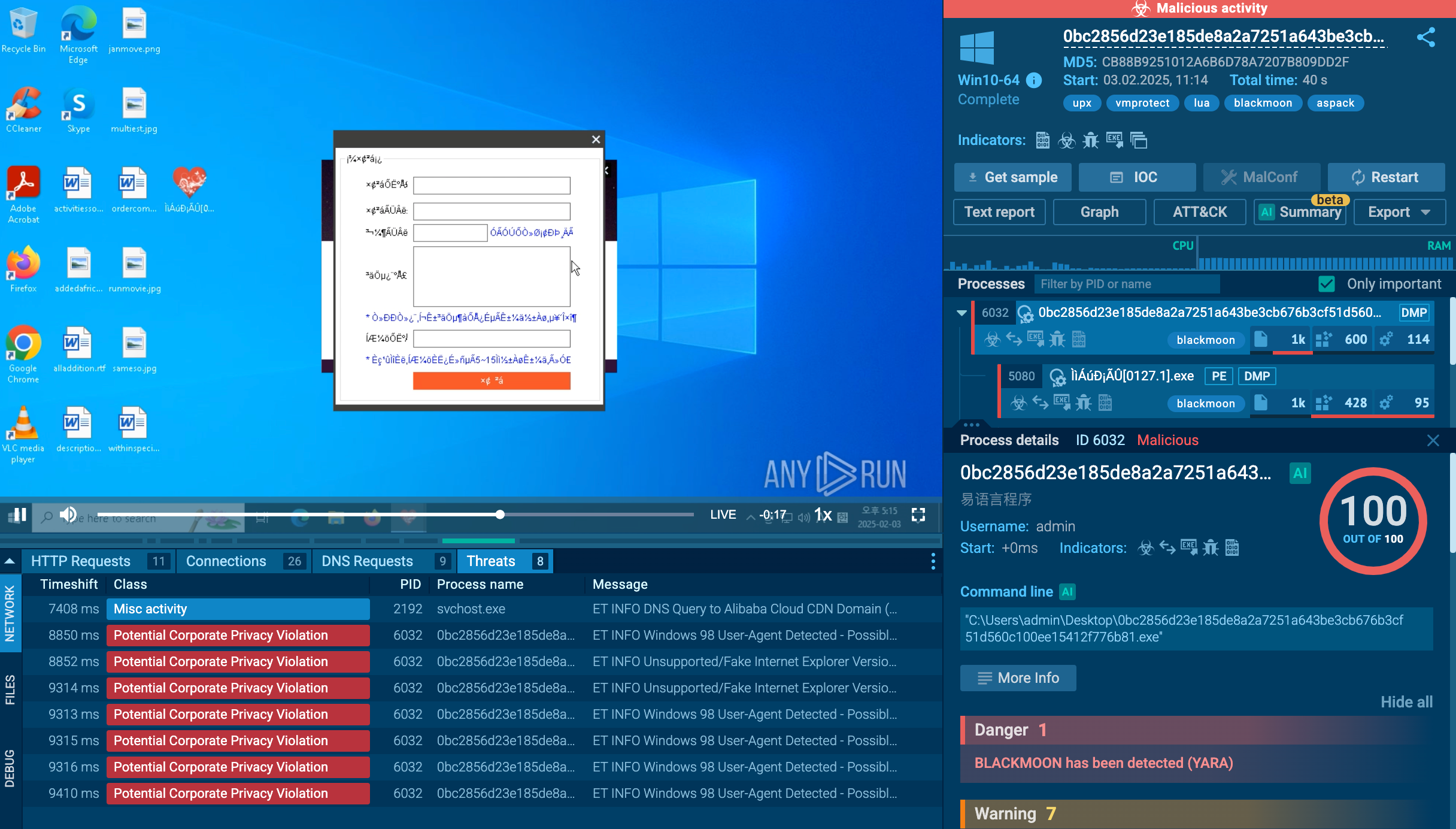
Figure 3: A Desktop of a system infected by WannaCry
It also hides the extracted directory, modifies security descriptors, creates an encryption key, deletes shadow copies, and so on. After all these steps, WannaCry encrypts the files of the user and sets the wallpaper to a ransom note. In addition, a @WanaDecryptor@.exe executable file is being started to provide information about the countdown and payment method to a victim.
In order to prevent potential WannaCry attacks, users should install security patches created by Microsoft in response to the original incident. Today, early versions of WCry won't work because their killswitch is still active.
The patch code for this security update is MS-17-010 and the update is available even for Windows XP; it was the first update to this operating system issued by Microsoft in 3 years.
Since crooks behind WCry offer decryption of three images for free you can use the interactivity of ANY.RUN to take additional steps in your analysis. Open the website specified in a ransom note in the browser and follow all steps to decrypt images to get a bigger picture of a ransomware infection process.
 Figure 4: Wannacry ransom note
Figure 4: Wannacry ransom note
WannaCry ransomware is undoubtedly one of the most destructive malware ever used by cyberattacks. The first malicious campaign utilizing this dangerous virus had a truly unprecedented scale.
Thankfully, due to outstanding work done by cybersecurity professionals, the attack was contained in just a few days by finding an effective kill switch and patching the vulnerability in the Microsoft operating systems that the ransomware was targeting. However, even despite such quick reaction times made by cybersecurity professionals all around the world, billions of dollars were lost by victims all across the world.
To prevent devastating cyber attacks such as the one performed using the WannaCry virus, researchers should learn as much as possible about the existing malware samples and analyze their code. This task is greatly simplified with the use of interactive sandboxes like ANY.RUN, which allows users to influence the simulation in real-time in order to get the best results.
Create your free ANY.RUN account to analyze malware and phishing without limits!