Blockchain mining is the process of solving complex mathematical equations to verify blockchain transactions. It functions much like bookkeeping, maintaining the blockchain in synchronization. Some cryptocurrencies — famously Bitcoin — compensate miners by “minting” new coins as a reward.
Mining, however, is computationally intensive. Prices for a specialized rig run into the tens of thousands of dollars, and even then, the system might generate electricity bills faster than it does cryptocurrency to cover expenses.
Hackers, who want all the profit but none of the challenge, resort to hyjacking systems of other users — specialized or not. This is where cryptomining malware comes in. Let’s break it down in this article.
How does mining work?
To understand the full impact of cryptocurrency mining malware, it’s important to start with the cryptomining definition. Cryptocurrencies, like Bitcoin and Monero use a consensus mechanism called Proof of Work (PoW). The essence of PoW is to solve a cryptographic puzzle to verify legitimacy of transactions. This puzzle is essentially finding a value that, when hashed with the SHA-256 algorithm (in Bitcoin’s case), results in a number that is less than or equal to a target value set by the network.
The process involves miners taking information from transactions waiting to be confirmed (from the mempool), a reference to the previous block’s hash, and a nonce. The nonce is a number that miners iterate over. They hash the block’s information along with the nonce, and if the result doesn’t meet the target, they change the nonce and try again.
Upon solving the puzzle, the miner broadcasts the new block to other network participants (nodes). These nodes verify the block’s validity, including the correctness of the solution and the legitimacy of the transactions contained within. Once verified, the block is added to the blockchain, and the successful miner receives a block reward — a new cryptocurrency unit.
What is cryptomining malware?
Going back to the crypto malware definition, we can answer the question of “what is cryptomalware” by stating that crypto miner malware is malicious software that secretly installs itself on a victim’s device and uses its processing power to perform calculations. Cryptominer malware hijacks other users’ systems to run the mining process described above. If successful, the hacker receives the reward, while the system’s owner gets nothing. This type of malware operates covertly, with the goal of staying undetected for as long as possible to maximize mining time.
Miners are unique because they typically don’t damage files or steal data but instead drain system resources. As a result, victims of Bitcoin malware may notice:
- Increased resource consumption: GPU, CPU or memory utilization gets abnormally high, as if the machine is endlessly running a benchmark.
- General unresponsiveness of infected systems: The server or computer might experience lag, overheating, and constantly operate with the fans at the highest setting.
Examples of cryptocurrency mining malware
There are many types of malicious software targeting cryptocurrency, including Bitcoin miner malware.
XMRig
Originally, XMRig is open-source CPU mining software. Unlike Bitcoin mining malware, XMRig is designed for mining Monero (XMR). Cybercriminals have repurposed it, embedding the software within malware. The malicious version of XMRig performs cryptojacking by intelligently adjusting the mining intensity based on the system’s CPU usage to minimize detection risk, making it difficult to identify through usual system symptoms.
DarkGate
DarkGate is a loader which executes crypto virus and other mining payloads, among others, including XMRig. DarkGate can elevate its privileges to system level on infected machines and employs rootkit-like features for persistence. Its methods include autostarting from an LNK file in the Startup folder, modifying registry keys to execute alongside the LNK file, or utilizing a DLL, depending on its configuration settings.
How to prevent crypto malware attacks?
- Configure Endpoint Detection and Response (EDR) systems: Configure EDR to alert about abnormal resource usage patterns, such as high CPU/GPU and memory usage by non-standard processes. Also monitor for unexpected process executions, especially those initiating network connections to known crypto mining pool addresses.
- Utilize Threat Intelligence Feeds. Integrate real-time threat intelligence to automatically update your TIP and SIEM systems with indicators of cryptomalware (IPs, domains, file hashes).
- Set up Email filters. Filter emails for attachments with executables, scripts, and documents with macros. Automatically send suspicious files for manual evaluation.
- Use Interactive Malware Sandboxes (such as ANY.RUN) to analyze samples. Automatically submit suspicious files detected by spam filters to ANY.RUN for detailed analysis — either by creating a ticket for manual analysis or sending samples directly via API. Then, analyze sandbox reports to collect IOCs and further configure security systems.
Analyzing crypto malware in ANY.RUN
Understanding what is a cryptominer and how to detect crypto mining malware is essential for protecting both personal and organizational computing resources.
Let’s picture an analyst at a company noticing an unusual download on one of their internal file servers. Curious to understand more, they decided to examine it by running it through the ANY.RUN interactive sandbox.
When investigating potential cryptocurrency mining malware, cybersecurity analysts should look for the specific IOC crypto malware might have left on the infected system.
In this task, ANY.RUN immediately detected a miner based on network activity, so we could skip the manual investigation and immediately start collecting IOCs.
Even if that weren’t the case, the malware gave itself away by the amount of system resources it consumes — note the maxed-out CPU immediately after startup and a substantial increase in RAM utilization:
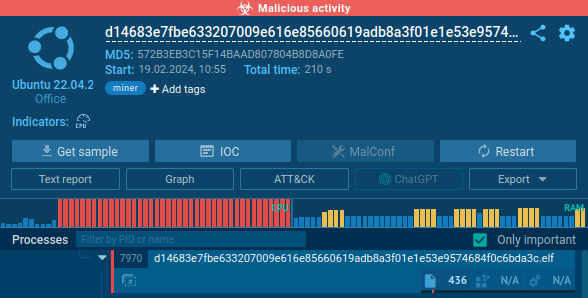
Also, network activity is off the charts. In less than 4 minutes, the miner sent almost 300,000 DNS requests to generated domain names:
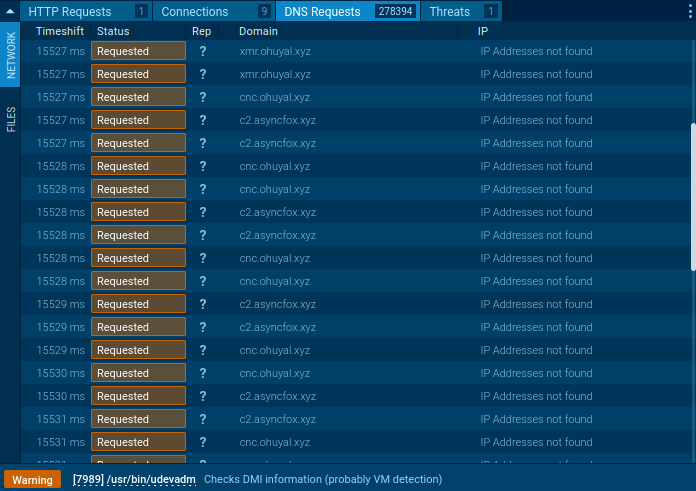
No legitimate software behaves in this manner, so the findings above are sufficient to prove that we’re dealing with a malicious entity, specifically a miner. From this point, we can access the IOC report and gather indicators to configure SIEM and WAF systems against this particular crypto-malware threat:
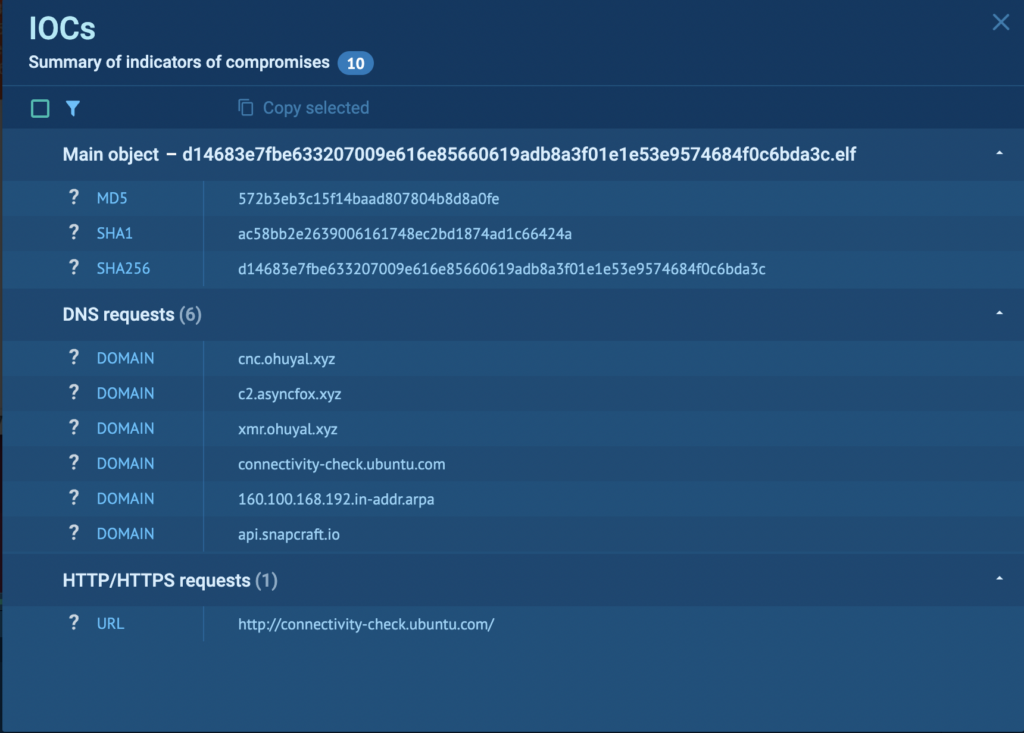
About ANY.RUN
ANY.RUN is a developer of cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams, as well as Threat Intelligence Feeds and Threat Intelligence Lookup. Every day, 400,000 professionals use our platform to investigate incidents and streamline threat analysis.
Get started in ANY.RUN for free today →
2 comments










Hello! I was told to drop a line here for individual research access to the software. Can you help?
Hello! If you want to register with a non-business email for your individual research, please do it here: https://discord.gg/anyrun
You’ll need to fill out the form. Let us know if you need any assistance!