Collecting forensics data is a great way to fend off future attacks by the same malware. Data that you acquire from analyzing samples can be classified as one of the two: artifacts and IoCs, or Indicators of Compromise.
Artifacts are left as the result of malware activity. When you perform the dynamic analysis you will collect lots of data such as IPs, modified files, and registry keys, created during malicious activity. All of that is evidence and it suggests that something nasty is lurking in your network.
The problem lies in the quantity of information. During analysis, researchers come across thousands of artifacts. Some of them are useful and reveal what is attacking you, others only give little hints or no actionable data at all.
This is where Indicators of Compromise come into play.
What are IoCs and Why They are Important?
IoCs are forensic evidence that points to a specific threat in your network. Often, they are made up of several artifacts, but in some cases, an artifact in itself can be an IoC. Their strength is in the usefulness of data.
Malware hunters can use IoCs to identify which malware has infiltrated the network, or analyze samples and collect forensics pieces that can be used in firewalls to protect the company from future attacks.
What types of IoCs are there?
The cybersecurity community widely identifies 15 types of Indicators of Compromise. Here is the full list:
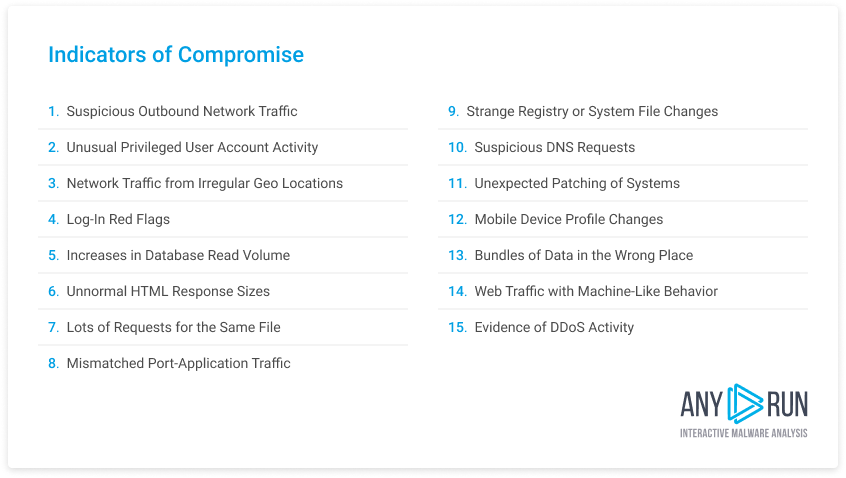
You can see all of these indicators for any malware sample in ANY.RUN by downloading a report in .json or MISP formats. However, not all of the indicators are equally useful. We prioritize the following SoCs: IP addresses from which the attack was launched, file hashes, and domains from which suspicious traffic originated. This last one is not always available, but it tells a lot about the nature of the threat.
You can use these 3 indicators in firewalls and fend off attacks of already known cyber threats, as well as reduce the number of false-positive alerts. More about those in the next section.
What’re the Weaknesses of IoCs?
IoCs are great cybersecurity tools, but they are not a cure-all. They have at least two major weaknesses — the potential for false-positive detection and lack of perspective. Let us elaborate.
- False-positives: sometimes analysts wrongly classify an artifact as an IoC. This brings a heap of problems, most notably false positive detections, when automated systems will alert the security team and take preventive measures against a harmless artifact, clogging the production network. Not a good thing to have. To avoid getting false positives, researchers often classify IoCs manually, which is a time-consuming process. Another way to minimize false positives is by referencing the 3 main IoCs that we outlined above.
- Lack of perspective: the information that researchers can get from IoCs is limited. IoCs are simply indicators — they show that an attack has taken place and what malware strain caused it. They don’t tell how the malware got into the network and what is the extent of the damage it has caused. Thus, analysts should not rely on IoCs exclusively in their response strategies.
How to Collect IoCs with ANY.RUN?
ANY.RUN turns what is usually a labor-intensive process into a much simpler job. You can analyze any suspicious file or link in our interactive sandbox. Or head over to the Malware Trends Tracker for a list of malware strains that are most active right now.
Malware Trends Trackers is a dynamically updated database of the most active malware. It can help you prioritize which threats to analyze first and which you are less likely to encounter.
Let’s head over to the tracker to take a look.
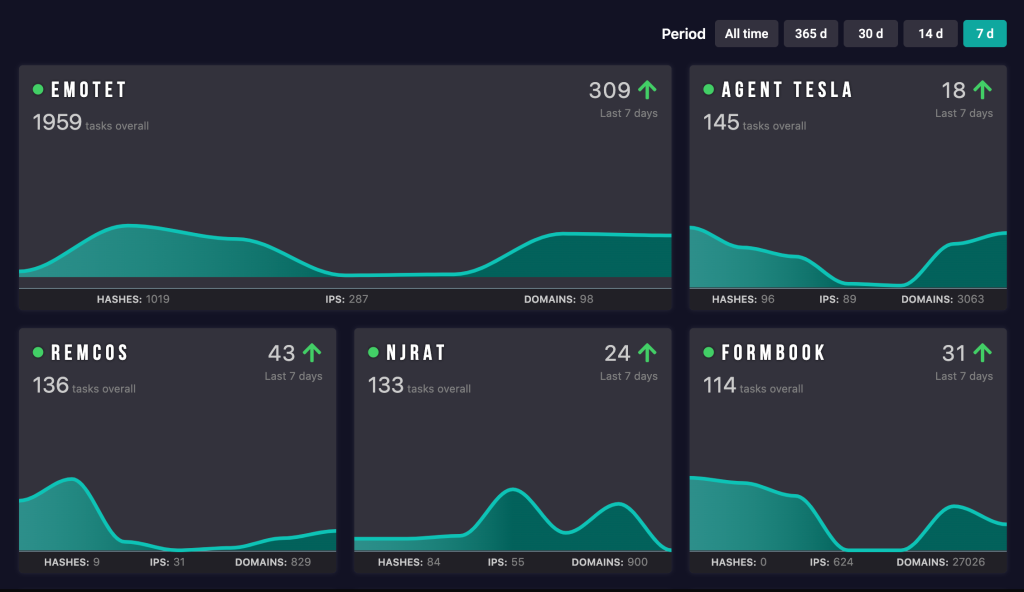
This is the homepage. The most active malware appears at the top. You can filter results by period or use a search bar to find a particular malware. Currently, the Tracker contains over 40 strains and we are always working on expanding it.
Let’s click on Agent Tesla.
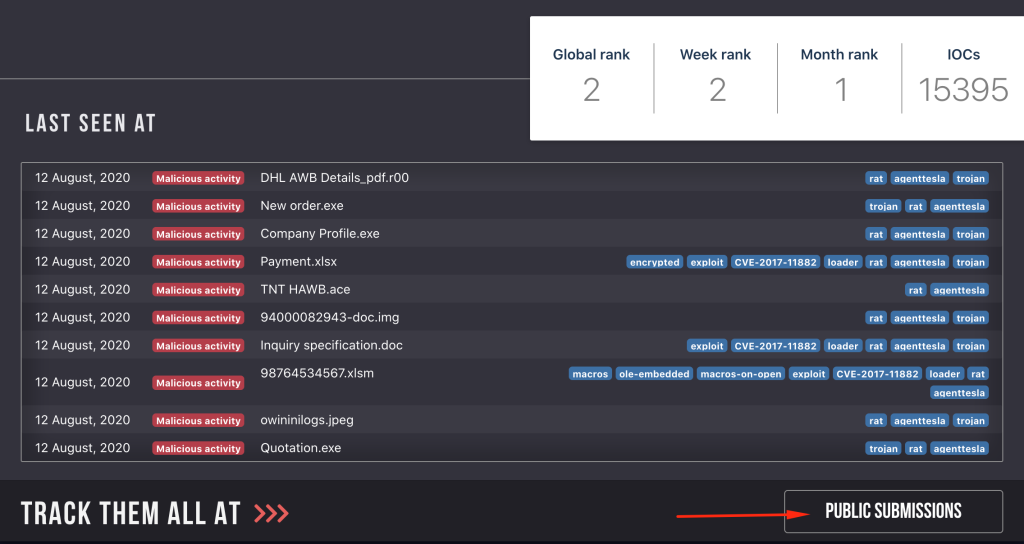
We will be taken to Agent Tesla’s homepage in the Trends Tracker. This page contains general information about the malware, but right now we are interested in IoCs. Let’s click the “Public Submissions” button to go to our open malware database.
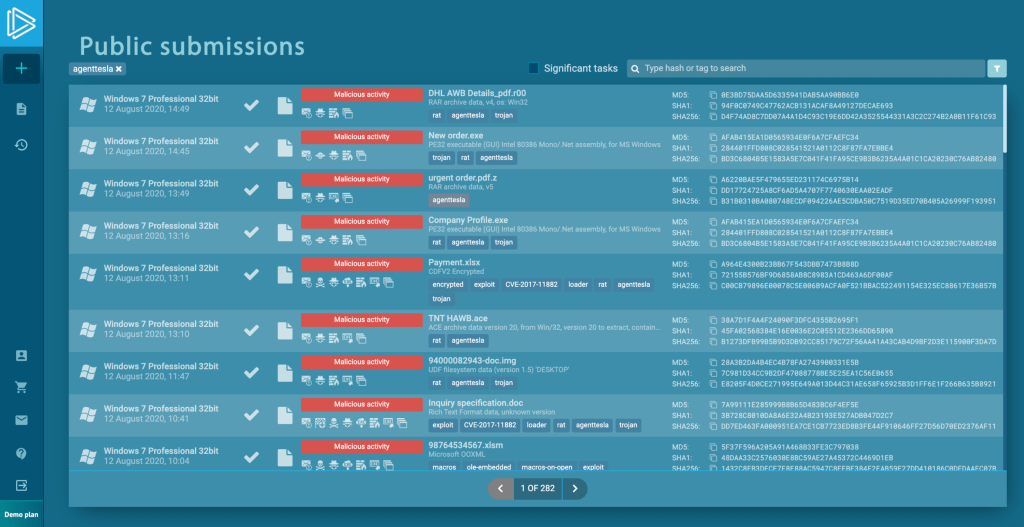
Here we are. ANY.RUN automatically filters for tasks where analysts confirmed Agent Tesla activity. Now all you need to do is is copy indicators from a dedicated column.
But, what if you are looking for malware that was not added to the tracker yet?
That is easy enough. Let’s say we are looking for Zeus. This time, we are going to start on the Public Submissions page.
We will use the search bar at the top right of the screen to filter tasks by tag. To find any particular malware all you need to do is enter the name. Let’s type in “Zeus” and hit “search.”
Not a bad catch. But we can make the result more precise by adding a verdict filter.
To do so, let’s click on the “filter” icon right next to the search area and choose “malicious.” Then, let’s click the “Search” button.
Now we are cooking. Collecting IoCs with ANY.RUN is that easy, and best of all you retain the manual element and don’t have to fully rely on automatic sandbox detection.
Conclusion
Indicators of Compromise are powerful cybersecurity tools that can protect against attacks or help identify an already ongoing threat. However, IoCs are not without their fault. Usually, collecting them requires a lot of time and effort, and when incorrectly used they are prone to false positives.
With ANY.RUN, researchers can find IoCs in minutes and by focusing on the 3 main types — IP addresses, domain names, and file hashes — reduce the number of false positives.
Stay safe online and get cracking with those IoCs!
2 comments








this is an excellent and helpful explanation, congratulations
After all, what a great site and informative posts, I will upload inbound link – bookmark this web site? Regards, Reader.