Threat Intelligence in Cybersecurity
Cyber Threat Intelligence (CTI) — often referred to as “Threat Intelligence” or “Threat Intel” — is the practice of gathering and analyzing data to identify, understand, and counter existing and potential threats.
In cybersecurity, threat intelligence serves a similar function to reconnaissance in military operations. It provides insights into the specific threats facing your organization, the TTPs attackers are likely to employ, and the IOCs that can help in detection.
The intelligence can be either:
- Strategic, looking at long-term trends and emerging threats.
- Operational, concerned with TTPs and effective defense strategies.
- Or tactical, focusing on immediate IOCs like IP addresses or file hashes.
What makes threat intelligence a crucial aspect of your cybersecurity?
The malware threat landscape is highly dynamic, with some estimates indicating that a new malware variant is released every minute.
Beyond keeping up with these rapid changes, your organization may also face targeted threats from APT groups. These actors typically deploy custom attacks tailored specifically to exploit vulnerabilities in your organization.
Even if you have strong SOC, DFIR and CSIRT teams, a purely reactive approach isn’t enough. You need current, context-rich intelligence from external sources to drive effective responses. Threat intelligence provides:
- Proactive defense: Integrating IOCs such as hashes and IP addresses from threat feeds allows you to update SIEM, firewall, and EDR rules. This enables early detection and automated blocking of known threats before they penetrate the network.
- Faster incident response: During a breach, aligning indicators of intrusion with TTPs, and linking those TTPs to an attacker or threat profile, is crucial. This approach allows the CSIRT team to quickly understand the attacker’s tactics and pinpoint vulnerable systems, facilitating faster containment and remediation.
- Better strategic planning: CTI gives CISOs and Intel analysts critical data on threats tailored to your organization, both emerging and persistent. This data helps shape a security strategy focused on the most likely threats you’ll encounter.
Cyber Threat Intelligence from ANY.RUN
ANY.RUN’s Threat Intelligence solutions empower Security Operations Centers (SOCs) with Threat Intelligence Lookup and Threat Intelligence Feeds. These solutions, coupled with Interactive Sandbox, are trusted by over 15,000 organizations, leverage data from millions of sandbox analyses to enhance threat detection and response.
Threat Intelligence Lookup: Targeted Threat Hunting and Enrichment
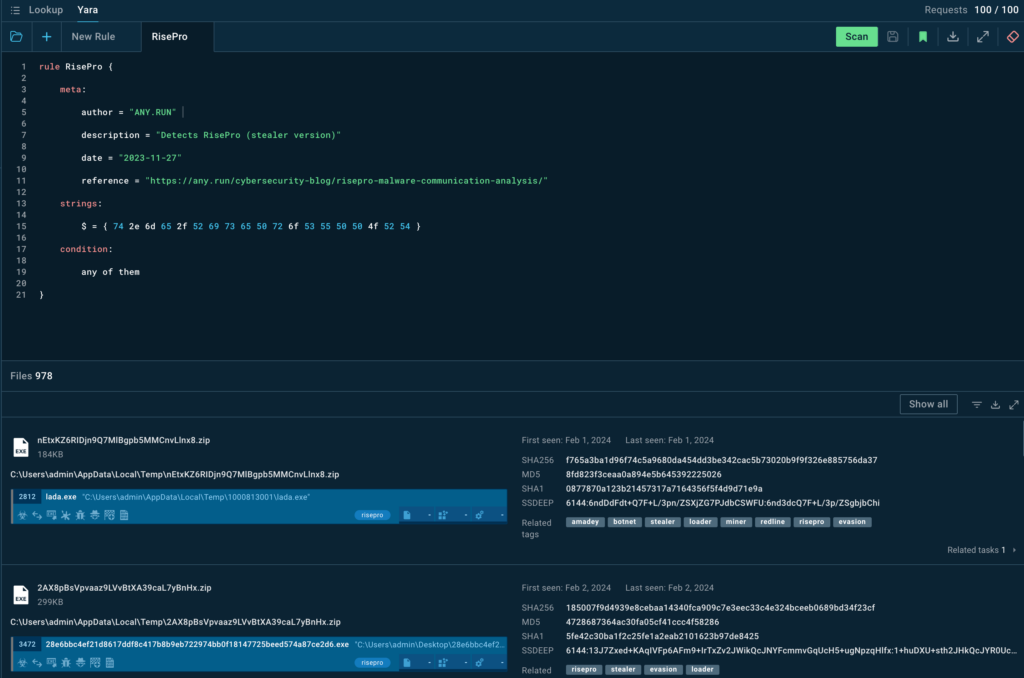
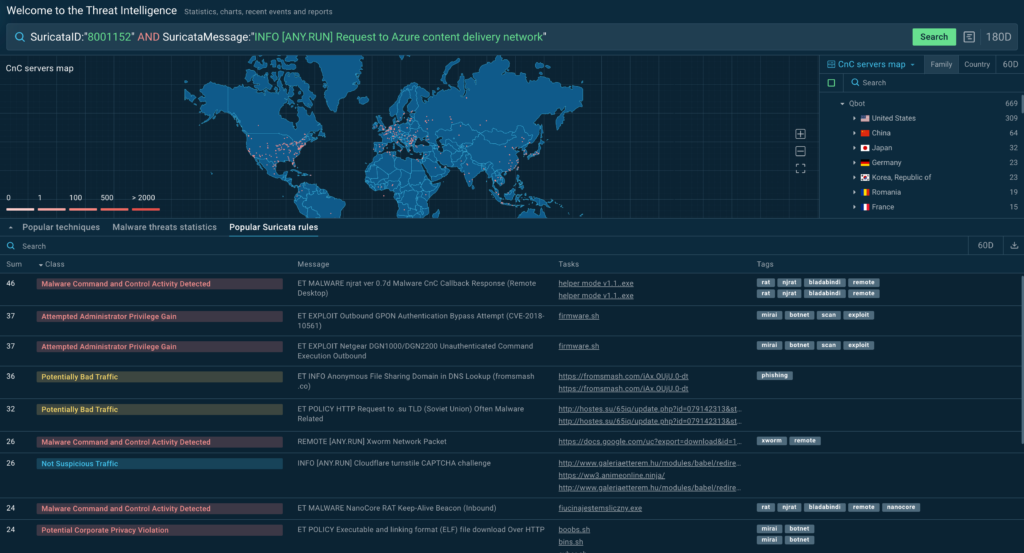
ANY.RUN’s TI Lookup is a searchable database of Indicators of Compromise (IOCs), Indicators of Attack (IOAs), Indicators of Behavior (IOBs), and Tactics, Techniques, and Procedures (TTPs). It allows analysts to query specific indicators like IPs, domains, or command lines and access real-time malware behavior insights from sandbox analyses, enabling rapid threat hunting and contextual enrichment.
- Faster Triage and Response: Query indicators in seconds to identify malicious activity and enrich with detailed attack context, speeding up incident resolution.
- Proactive Threat Hunting: Use 40+ query parameters and custom YARA rules to detect malware patterns and uncover hidden threats before exploitation.
- Enhanced Analyst Expertise: Access linked sandbox sessions to observe attack behaviors and TTPs, improving understanding of modern malware.
- Proactive Defense Development: Leverage insights to create new SIEM, IDS/IPS, or EDR rules, strengthening defenses against emerging threats.
- Reduced Breach Risk: Quick, accurate intelligence minimizes alert triage time, lowering the likelihood of successful attacks.
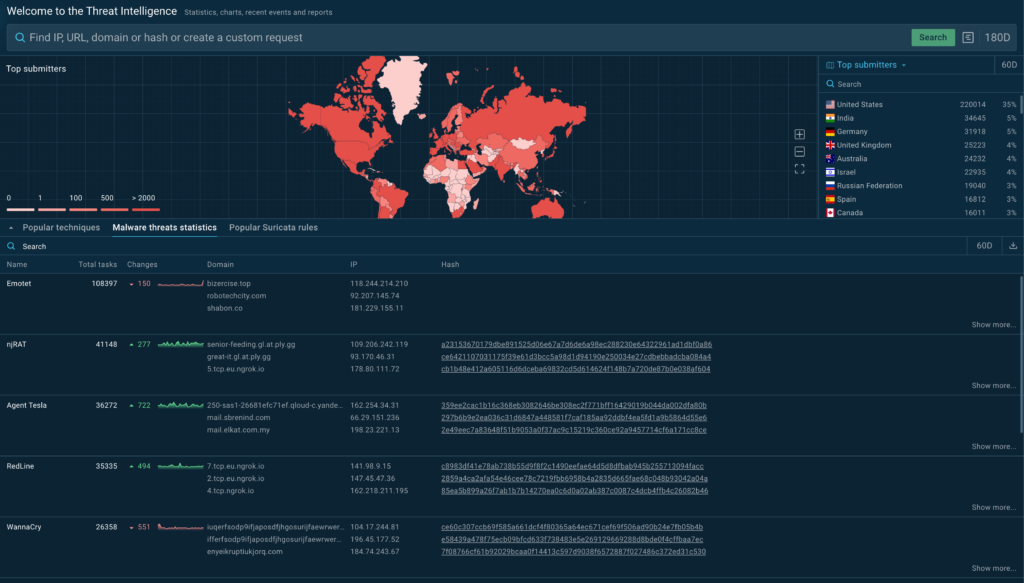
Threat Intelligence Feeds: Continuous, High-Fidelity Threat Data

ANY.RUN’s TI Feeds deliver a continuous stream of pre-filtered, high-quality IOCs such as malicious IPs, domains, URLs, and hashes, updated in real time. Compatible with STIX/TAXII and MISP formats, these feeds integrate seamlessly into SIEM, TIP, SOAR, and EDR systems, providing SOCs with fresh, actionable intelligence for automated threat monitoring.
- Expanded Threat Coverage: Includes exclusive IOCs from memory dumps, Suricata IDS, and in-browser data, enhancing detection of evasive threats.
- Reduced Workload: Pre-processed feeds remove false positives and duplicates, streamlining alert prioritization and analysis.
- Automated Threat Monitoring: Integrates with existing systems to enable continuous, real-time threat detection without manual intervention.
- Informed Incident Response: Provides rich metadata and sandbox-linked context for IOCs, enabling faster and more effective threat containment.
- Scalable Defense: Supports centralized protection across platforms like IBM QRadar and Microsoft Sentinel, optimizing SOC efficiency without alert overload.
Threat intelligence provides context for likely threats
Simply tracking most common malware types or families isn’t enough for effective threat intelligence, because this approach lacks the specific insights needed to understand the risks your organization actually faces.
Instead, effective threat intelligence strategies focus on gathering detailed, targeted data. They aim to answer key questions like:
- Who is likely to target my organization?
- What malware and TTPs will they probably use?
- What parts of our network are most at risk?
- What IOCs can help us detect an attack?
- How can we fortify our defenses against these particular threats?
Tools, people, and information comprising threat intelligence
Threat intelligence impacts every team, tool, and process in your organization’s cybersecurity framework. This data often comes from multiple sources, such as OSINT, commercial threat feeds, and internal logs and historical data. Here are some ways how different teams use it:
| Data source | Team | Benefit | Type |
|---|---|---|---|
| Threat feeds | SOC | Expand automated threat coverage and detection | Tactical |
| TI Lookup | SOC | Related events and IOCs | Technical, Tactical |
| Contextual IOC databases | CSIRT | More accurate and speedy threat identification | Tactical |
| Forensic Data | CSIRT | Faster and more accurate incident response | Operational |
| Detailed threat reports | Executive | Better risk assessment | Strategic |
Cyber Threat Intelligence Use Cases
Cyber threat intelligence transforms how organizations tackle cyber risks by delivering tailored, actionable insights across roles. Below are specific use cases demonstrating how CTI empowers Security Operations Centers (SOCs), Incident Response Teams (IRTs), analysts, and managers.
- SOC: CTI filters and prioritizes alerts by matching threats to known attack patterns, enabling SOC teams to focus on critical incidents and reduce false positives.
- Incident Response Team: CTI provides attacker tactics and context, speeding up incident investigations, containment, and mitigation to minimize damage.
- Analysts: CTI supports proactive threat hunting by analyzing indicators of compromise, helping analysts uncover vulnerabilities before they are exploited.
- Managers: CTI informs strategic decisions by mapping the threat landscape, aligning cybersecurity investments with business priorities, and enhancing risk communication with executives.
Tactical vs Strategic vs Operational threat intelligence
Threat intelligence data can be further categorized into three groups: tactical, strategic, and operational.
| Type of Cyber Threat Intelligence | Purpose | Audience | Timeframe | Example Use Case |
|---|---|---|---|---|
| Strategic | Provides high-level insights into threat trends and their business impact. | Executives, C-suite, risk managers | Long-term (months/years) | Guiding budget allocation by assessing emerging threats like ransomware campaigns. |
| Operational CTI | Focuses on threat actors’ motives, capabilities, and campaigns. | Security managers, IRT leaders | Medium-term (weeks/months) | Preparing defenses against a specific APT group targeting the industry. |
| Tactical CTI | Details attacker tactics, techniques, and procedures (TTPs) for response. | SOC teams, incident responders | Short-term (days/weeks) | Prioritizing alerts by correlating attack patterns with known TTPs of a phishing campaign. |
| Technical CTI | Supplies specific indicators of compromise (IOCs) for immediate action. | Analysts, threat hunters, SOC analysts | Immediate (hours/days) | Blocking malicious IPs or domains identified in a malware outbreak. |
Tactical threat intelligence focuses on immediate threats and technical indicators. It provides actionable data like IP addresses, hashes, and URLs that security teams can use for immediate defense measures. Mainly geared toward SOC analysts and incident responders, it helps in quick detection and mitigation of attacks.
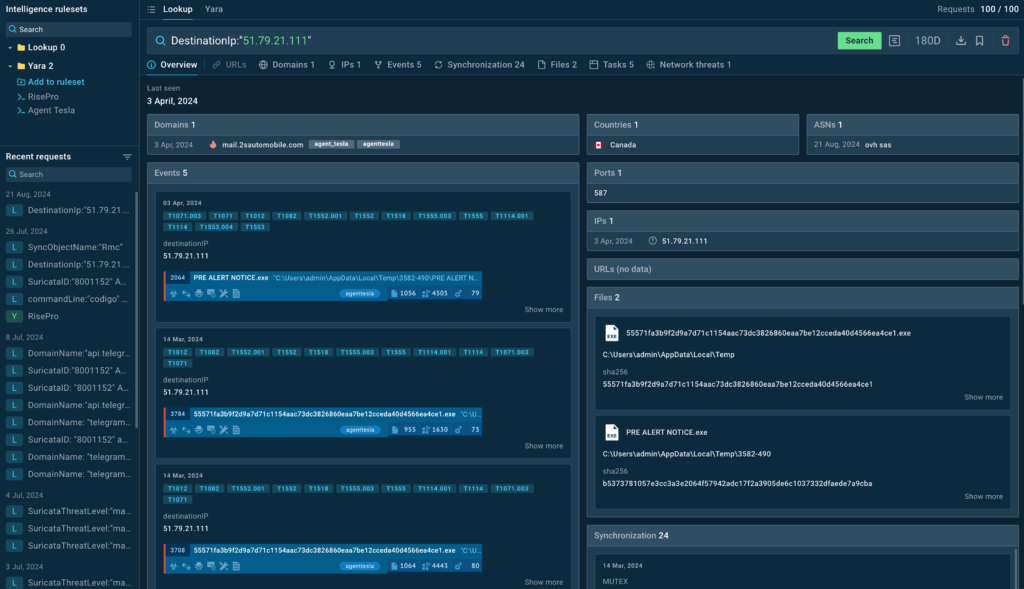
Operational threat intelligence sits between tactical and strategic, focusing on the “how” behind attacks. It offers context around TTPs used by attackers. Useful for threat hunters and mid-level security managers, it helps in understanding the motivation, capabilities, and methods of potential threats, allowing for more informed defense strategies.
Strategic threat intelligence is concerned with long-term security planning and risk assessment. It provides insights into broader threat landscapes, like emerging attack vectors or geopolitical factors that may influence threats. Strategic TI usually involves CISOs and high-level decision-makers and shapes the overall security strategy of a company.
Technical Threat Intelligence: what is it? There is a fourth type of threat intelligence – technical. It refers to machine-readable IT data, such as indicators of recent threats, that is delivered to the SIEM and TIP system through threat intelligence feeds.
6 steps of the threat intelligence lifecycle
Like incident response, threat intelligence is a complex process. To keep the initiative focused, it follows a cyclical approach that involves setting objectives, taking specific actions, and then reviewing and iterating.
The most common framework outlines 6 steps to create a continuous loop for improving your security posture:
- Requirements: In this phase, the threat intelligence team lays out a roadmap for a specific intelligence operation. They outline required actions and set measurable objectives, such as creating a report about the TTPs of a new adversary.
- Collection. Security analysts and engineers pool data from pre-determined sources like threat feeds, dark web forums, or internal logs. A successful criterion could be acquiring relevant IOCs within a set timeframe.
- Processing. Data scientists and engineers work to structure raw data. The aim is to transform it into machine-readable formats like STIX or human-readable formats like spreadsheets and diagrams. The focus is on filtering out false positives efficiently and compiling a dataset suitable for analysis.
- Analysis. Malware analysts examine the processed data, utilizing analytics platforms, sandboxing, and lookup services. They correlate events and map IOCs to TTPs. The goal is to add context. Potentially disjointed lists of indicators are transformed into cohesive description of attack patterns.
- Dissemination. Incident response and SOC teams receive the finalized intelligence. They use the information to update security systems like IDS, IPS, and firewalls.
- Feedback. Post-action reviews usually involve all teams. Feedback is used to adjust future intelligence requirements and operations.
How Threat Intelligence Contributes to Business Security
Cyber threat intelligence solutions deliver measurable impact on companies’ ability to identify cyberattacks and stop them before they cause damage.
- Informed Decision-Making: CTI offers insights into threats, aiding leaders in strategic investments and policies.
- Cost Reduction: Early threat detection prevents breaches, cutting financial losses and recovery expenses.
- Improved Operational Efficiency: CTI automates risk prioritization, freeing teams for core tasks.
- Enhanced Risk Management: Provides a full threat view to assess and minimize business disruptions.
- Faster Incident Response and Recovery: Enables quick detection and response, boosting resilience against attacks.
Cyber Threat Intelligence (CTI) FAQ
Here are answers to the most frequently asked questions about Cyber Threat Intelligence.
CTI is actionable information about cyber threats, including attacker tactics, motives, and indicators, used to enhance an organization’s security posture.
CTI enables proactive defense, reduces risks, lowers costs from breaches, and supports informed decision-making across organizational levels.
SOC teams, incident response teams (IRTs), analysts, and managers use CTI to monitor, respond to, and strategize against cyber threats.
CTI includes Strategic (high-level trends), Operational (threat actor campaigns), Tactical (TTPs), and Technical (IOCs like malicious IPs).
CTI provides context on attacker methods, enabling faster identification, containment, and mitigation of incidents.
Yes, analysts use CTI to proactively identify vulnerabilities and hidden threats by analyzing indicators of compromise (IOCs).
Strategic CTI informs executives about threat trends, helping align cybersecurity investments with business goals and risk management.
CTI is gathered from open-source intelligence, dark web monitoring, industry reports, threat-sharing communities, and internal security data.
By detecting threats early and prioritizing responses, CTI minimizes financial losses from breaches, downtime, and recovery efforts.
About ANY.RUN
ANY.RUN is trusted by more than 500,000 cybersecurity professionals and 15,000+ organizations across finance, healthcare, manufacturing, and other critical industries. Our platform helps security teams investigate threats faster and with more clarity.
Speed up incident response with our Interactive Sandbox: analyze suspicious files in real time, observe behavior as it unfolds, and make faster, more informed decisions.
Strengthen detection with Threat Intelligence Lookup and TI Feeds: give your team the context they need to stay ahead of today’s most advanced threats.
Want to see it in action? Start your 14-day trial of ANY.RUN today →










0 comments