Today, we’re excited to announce a new service in ANY.RUN — YARA Search.
YARA Search offers a way to identify threats that differs from our TI Lookup. While TI Lookup allows you to search for related threat data using individual indicators like IP addresses or event fields, YARA Search analyzes the contents of files themselves.
This is a completely new way to search ANY.RUN‘s threat intelligence database, and a new addition to our range of threat intelligence tools — in true ANY.RUN fashion, giving you quick access to information from real-world data.
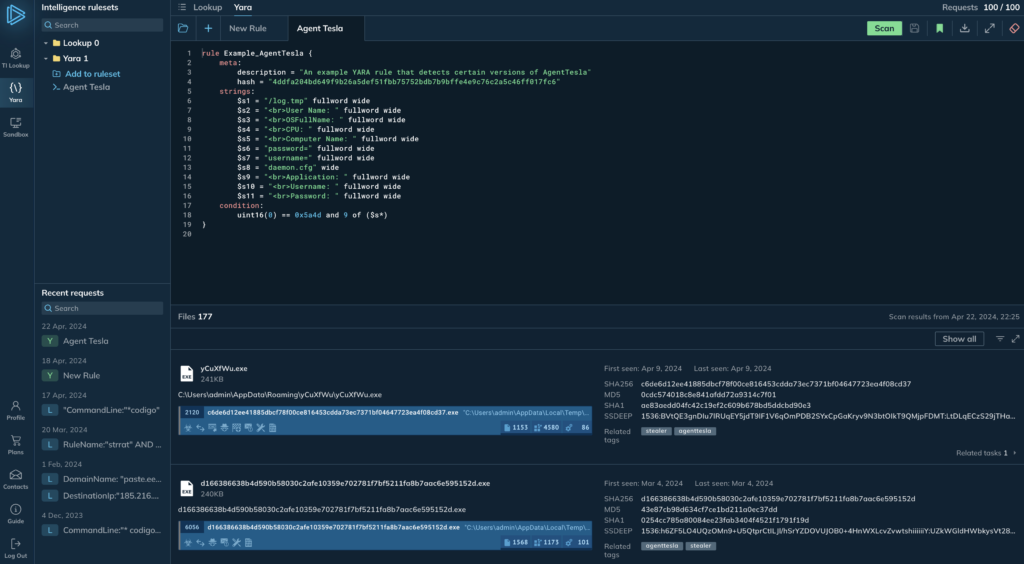
What is ANY.RUN’s YARA Search
In a nutshell, YARA is a tool that helps malware analysts find files by creating detailed descriptions based on regular expressions, textual patterns, or binary signatures. With YARA rules, you can, essentially, describe malware and then find files that match your descriptions.
YARA Search allows you to scan our threat intelligence database, holding extensive volumes of data collected by thousands of researchers who analyze real-world samples from around the globe, as well as our in-house team of malware analysts.
But that’s not all – YARA Search also allows you to write, edit, test, download, and manage your rules seamlessly within ANY.RUN, using your existing TI Lookup quota for searches.
- Find malicious files that match your YARA rules.
- See how these files operate within a system and explore examples of their real-world attack scenarios through associated recordings of sandbox analysis sessions.
- Download the identified files for further in-depth analysis.
How to access YARA Search
Getting started with YARA Search is easy — we offer 20 free trial requests to all ANY.RUN users with a paid plan (That’s Hunter, or Enterprise) so you can try this service.
And if you’re already a paid user of our TI Lookup service, you’ll be pleased to know that YARA Search shares the same request quota. So you can start using it right away as part of your existing subscription.
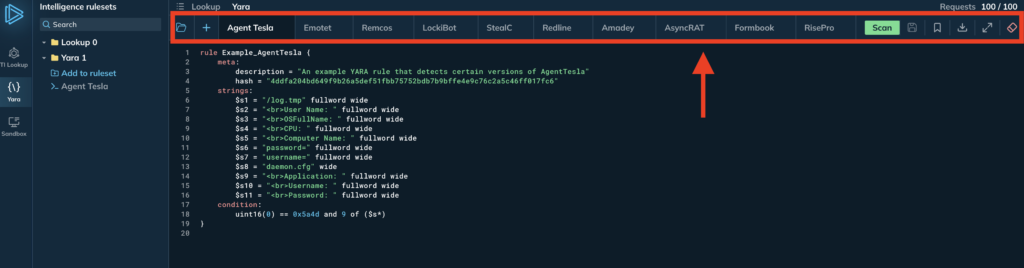
YARA Search capabilities
In ANY.RUN’s YARA Search, you’ll not only be able to search for files by running multiple searches in parallel, but also write and debug your YARA rules with ease in a robust online editor featuring syntax highlighting. Here’s what’s included with YARA Search:
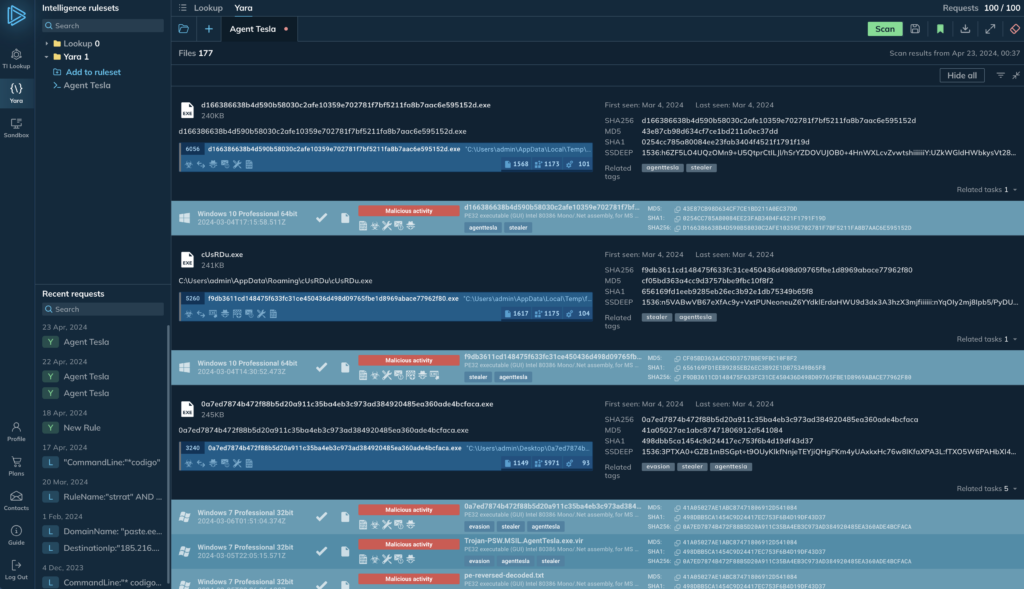
Search for processes and associated sandbox analysis sessions by file contents
Fast search and ability to run multiple searches at once
Receive initial search results from our threat data database in under 5 seconds. Moreover, you can run multiple searches simultaneously or utilize the TI Lookup while your YARA search is executing, simply by switching between tabs.
After running your YARA search, you’ll receive a clear breakdown of results, including:
- Matched files.
- Processes against which the rule was triggered
- Associated tags.
- File hashes
- A list of sandbox analysis sessions that match the YARA rule.
At any time, you can click on the process to browse the associated recording of the analysis session in the ANY.RUN sandbox or download a file for further local analysis.
A powerful online editor
Integrated editor makes it easy to create, save, and edit your YARA rules. It features syntax highlighting and a tabbed interface, allowing you to work on multiple rules simultaneously.
YARA has its own language with specific syntax, and like all programming languages, mistakes can happen when writing rules.
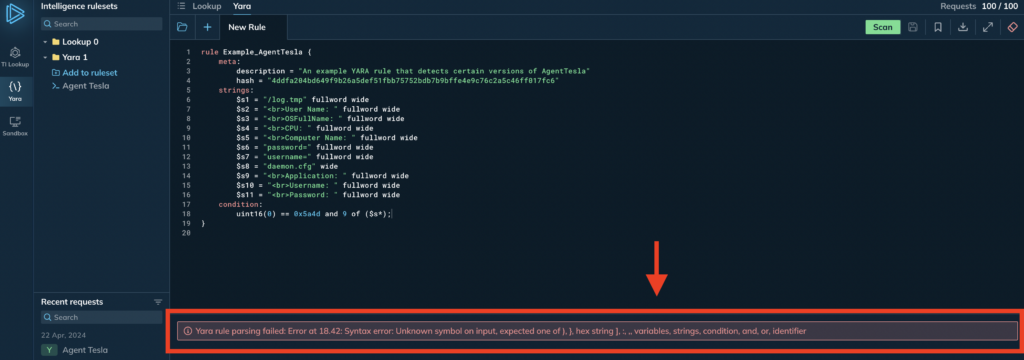
In ANY.RUN YARA Search, these errors are easy to spot and correct. If you make a mistake, the service will display a descriptive error message highlighting what went wrong, so you’ll never be left scratching your head wondering why your rule isn’t working.
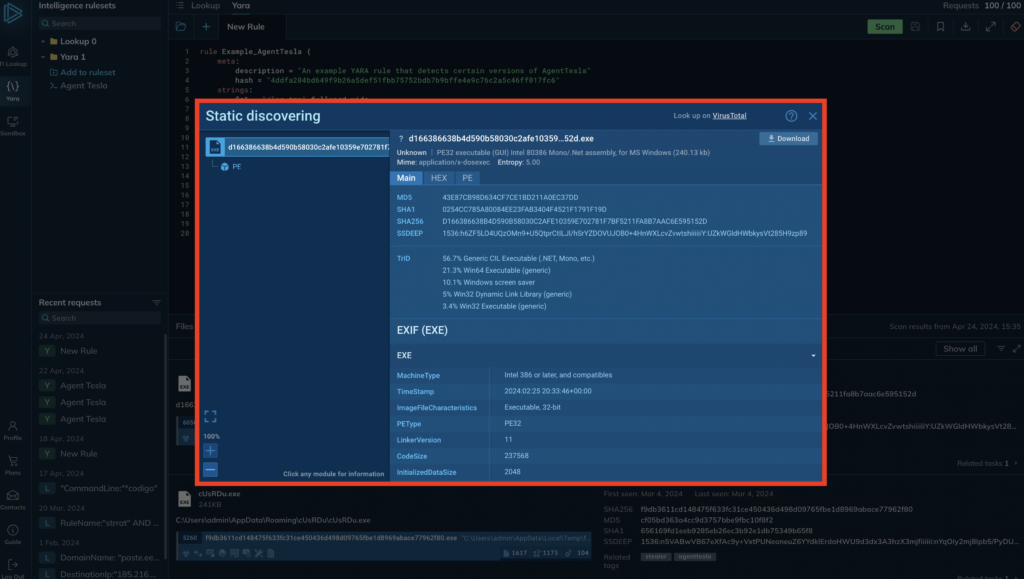
Analysis tools for every use case
ANY.RUN is known for giving researchers quick and easy access to threat information, and YARA Search is no exception. We have carefully designed the interface to give you analysis options.
- For each matched file, you can bring up the Static Discovering window — the same as in our sandbox — and view metadata such as TrID, EXIF data, file hex values, and it’s clear text and PE information — all without leaving the YARA Search page.
- You can also download matched files to analyze them in depth within your system, and reverse engineer them if necessary.
How YARA Search help you find real examples of malware usage
We share some of the YARA rules with the community through our public repository on GitHub. You can copy these rules directly and use them to detect threats.
For our example, we will choose a simple rule from our repository consisting of only one HEX string to detect the notorious malware family, RisePro:
rule RisePro { meta: author = "ANY.RUN" description = "Detects RisePro (stealer version)" date = "2023-11-27" reference = "https://any.run/cybersecurity-blog/risepro-malware-communication-analysis/" strings: $ = { 74 2e 6d 65 2f 52 69 73 65 50 72 6f 53 55 50 50 4f 52 54 } condition: any of them }
Let’s paste this Rule into YARA search and see what we can find:
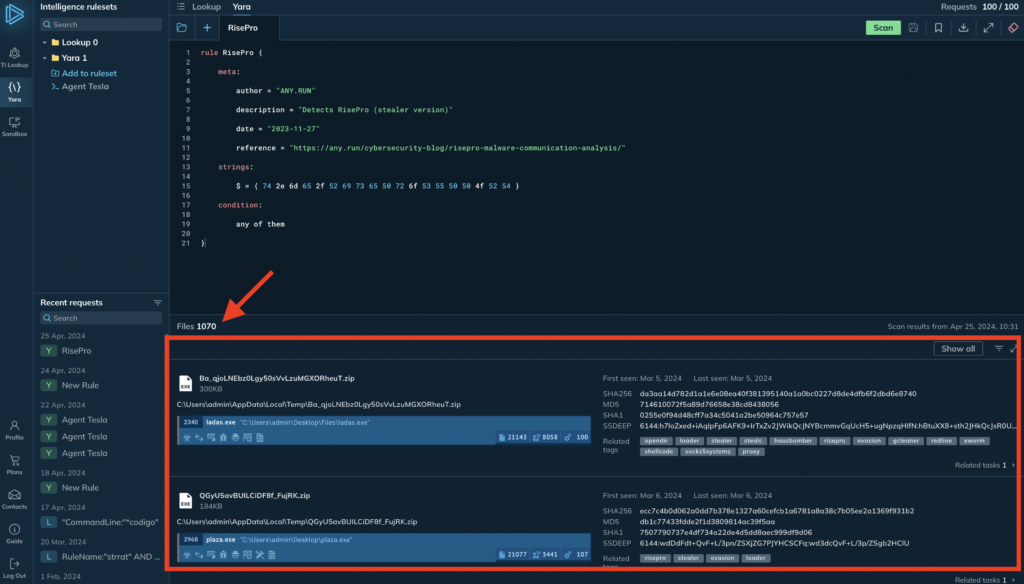
Within seconds we found over a thousand files infected with this malware. From here, we can download them to study the files locally, or open associated sandbox analysis sessions to learn more about what RisePro does after it infects a system.
Please note that if the search is too complex, it will not be processed. In order to continue the search, the user must simplify the search criteria.
Also note that sometimes the tasks found may not contain the tag of the searched malware, because this malware family was not detected when the sample was submitted to our service.
Get started with YARA Search today
Over 400,000 cybersecurity professionals trust ANY.RUN to analyze and detect malware. Our flagship product, an interactive malware analysis sandbox, simplifies threat research on both Windows and Linux. Our threat intelligence products, TI Lookup, TI Feeds — and now YARA Search — give you powerful tools to search for threat data.
Because all of these products are tightly integrated, our TI products can scan information from sandbox research sessions performed by the vast community of researchers. This gives you the ability to find unique, real-world examples of malware and see how hackers have used it in real-world attacks.
If you are interested in integrating YARA Search into your security team, contact us to get started.







0 comments