Editor’s note: The current article was originally published on November 26, 2020, and updated on August 12, 2025.
If you’re an independent malware analyst or threat researcher, you need a solution that works as hard as you do; one that’s flexible, private, and built for deep, hands-on investigations.
Hunter puts that power in your hands. With 70% of ANY.RUN’s Interactive Sandbox capabilities, you can dive into advanced investigations, expose hidden threats, and keep every detail locked down.
Let’s look at why so many solo analysts make Hunter their plan of choice.
Keep Your Analyses Secure
The Hunter plan gives analysts the privacy they need to work with sensitive samples confidently.
You decide who can access your submissions, whether you want to keep them completely private, share with a trusted contact, or display them in a controlled presentation mode.
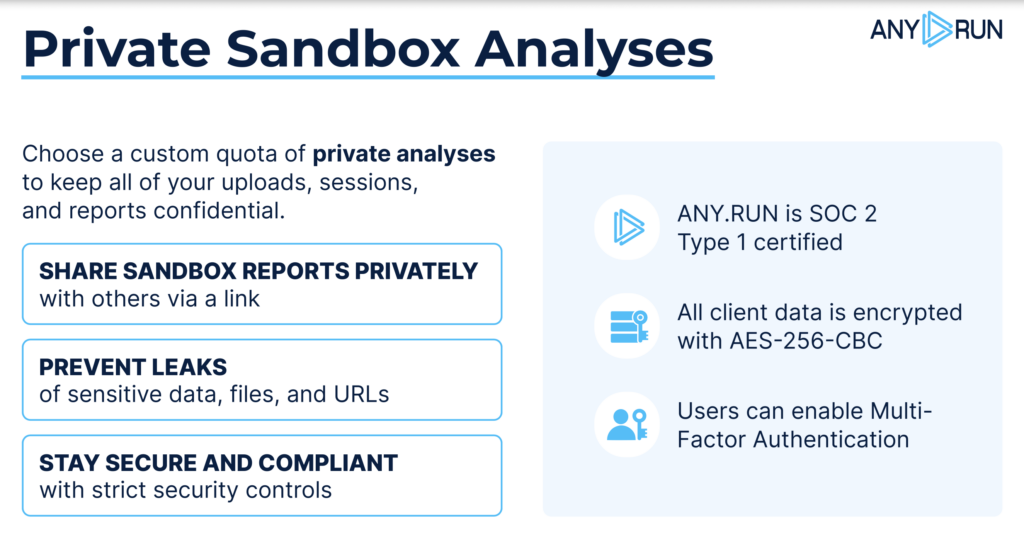
This control is backed by strong security measures that protect your data at every stage:
- Our SOC 2 Type 1 certification is backed by independent assessments, verifying that we have robust controls in place to protect user data, private malware analyses, and system integrity
- Data is encrypted at rest with AES-256, ensuring stored files remain secure against unauthorized access.
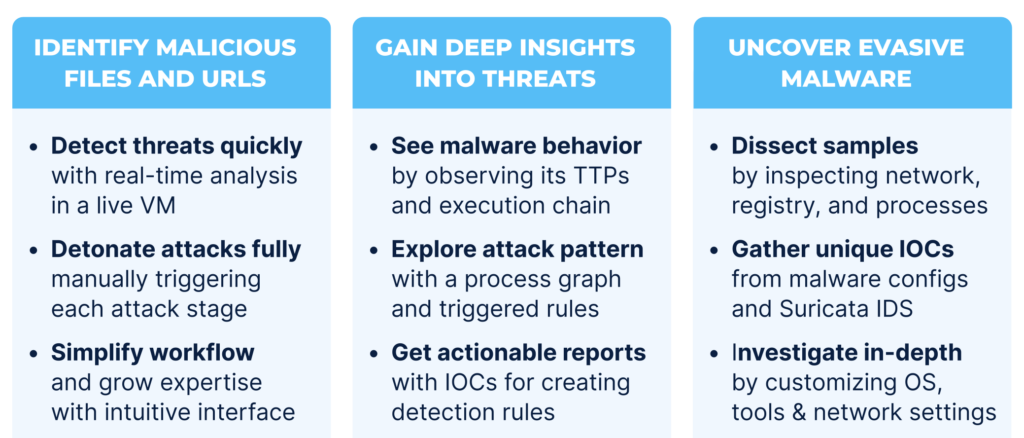
Identify Malicious Files and URLs Faster
Hunter enables rapid, controlled analysis of suspicious files and URLs across a range of environments, from Windows 7, 10, and 11 to Linux and Android. In most investigations, the sandbox delivers a reliable verdict in under 40 seconds, allowing analysts to act without delay.
By fully detonating each attack and interacting with it at every stage, you can observe its complete execution chain, including those steps designed to evade automated tools. Detonation actions and environment fine-tuning work together to make threat identification both precise and efficient, even when dealing with multi-layered or highly evasive malware.
The intuitive interface makes it easy to navigate complex analyses, while helping analysts of all experience levels deepen their expertise with every investigation.
Real-World Example of Phishing Attack
One real-world case shows exactly why this capability matters.
Real Case Analysis: From Phishing Email to AsyncRAT
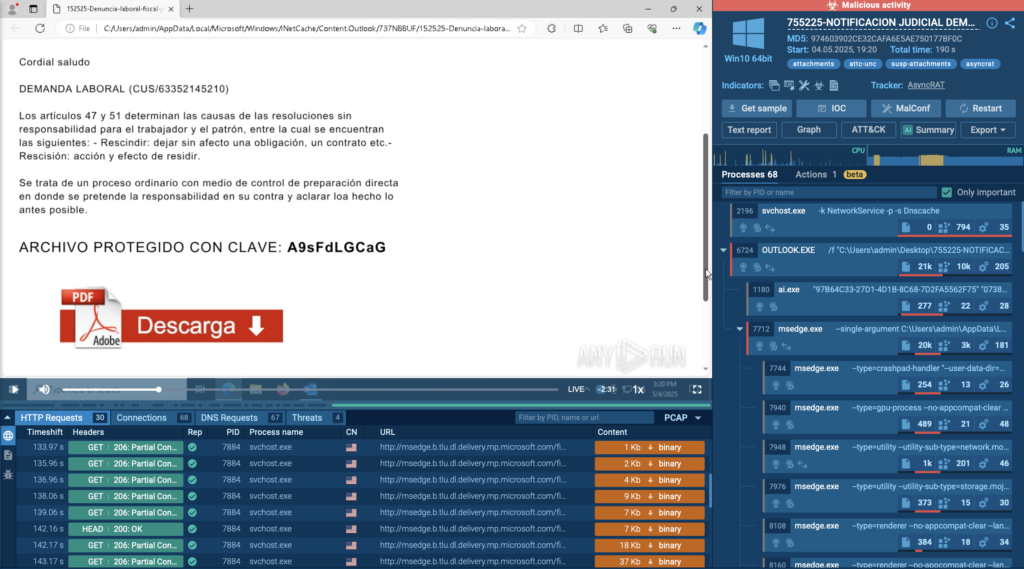
A phishing email arrived with an SVG attachment and a password hidden in the message body. Opening the SVG in the sandbox revealed a fake document containing a link to download a PDF. Clicking that link triggered the download of a ZIP archive; one that could only be extracted by manually entering the earlier password.
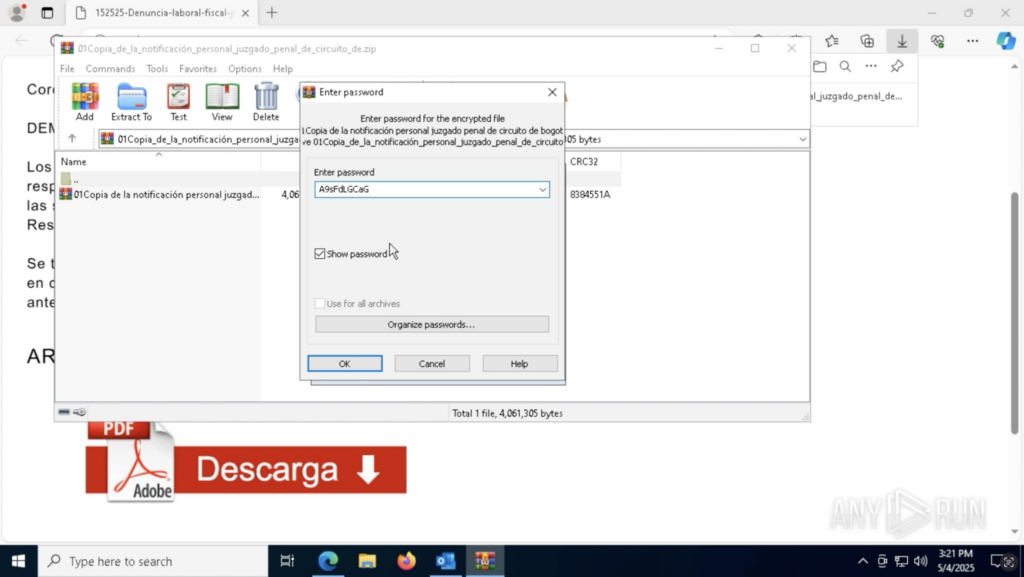
Inside was an executable file. When run, ANY.RUN immediately flagged it as AsyncRAT — a remote access trojan capable of spying on and controlling infected systems.
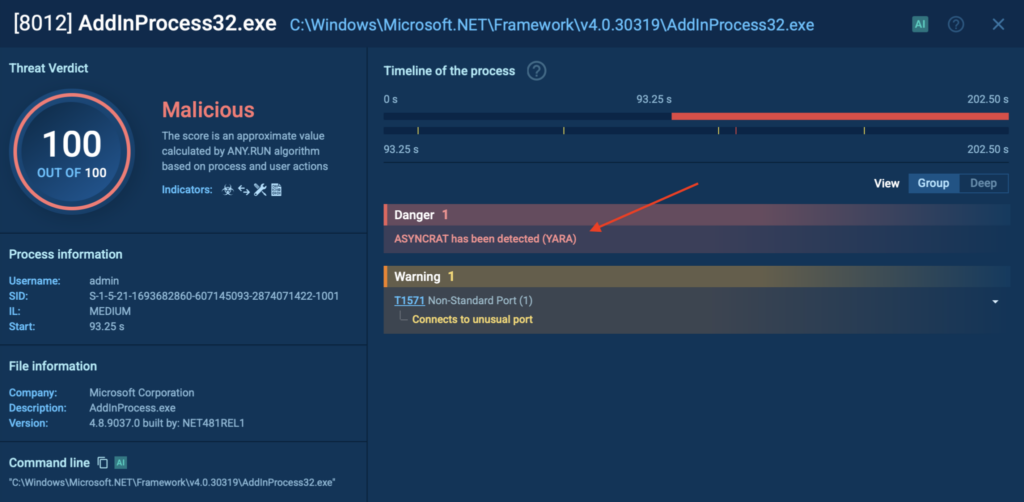
Without interactivity, this chain would have remained hidden. A fully automated tool wouldn’t have clicked the link, copied the password, or opened the archive, leaving the threat undetected.
Here, the AI Assistant also stepped in to summarize the full chain of actions, making it easier for a junior analyst to quickly understand the threat without manually piecing together every detail.
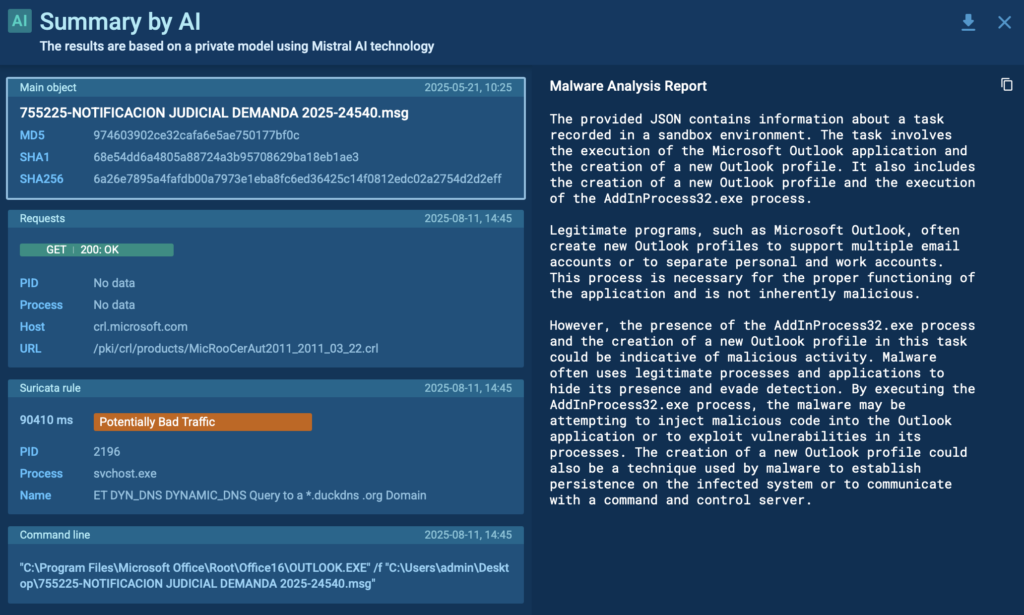
In this case, ANY.RUN sandbox provided:
- A full process breakdown, mapping the malware’s execution path
- Network activity visibility, enabling the team to block C2 communications before data exfiltration
Gain Better Visibility into Threat Behavior
Hunter helps you understand exactly how malware operates, so you can respond with precision.
Inside the analysis session, you can view MITRE ATT&CK®-mapped TTPs to see which tactics and techniques the threat uses. This makes it easier to assess the attack’s sophistication, connect it to known threat actors, and prioritize the right defensive actions.
You can also explore attack patterns through the process graph and triggered rules, visualizing every step of the execution chain. This helps analysts quickly grasp complex behaviors, uncover hidden stages, and spot anomalies that might otherwise be missed.
When the investigation is complete, you can generate detailed reports with IOCs, ready for sharing with colleagues, integrating into SIEM or EDR systems, or using to update detection rules. This ensures your findings don’t just stay in the lab but actively strengthen defenses.
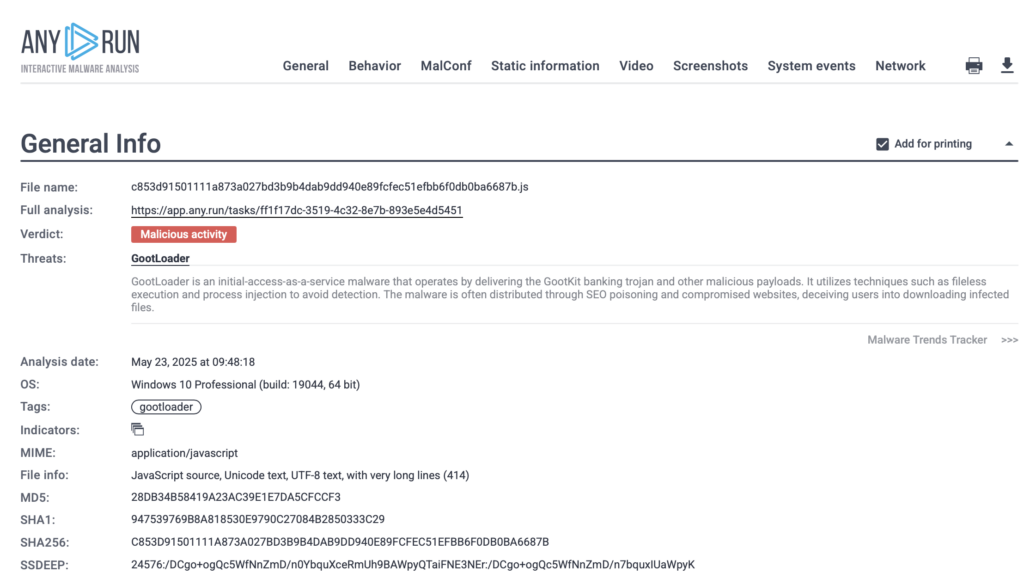
Real-World Example: Gootloader Infection Chain
A live Gootloader case in the Hunter sandbox begins with a user landing on a compromised website while searching for something business-related, such as a contract template. The site delivers a ZIP file containing a trojanized JavaScript file disguised as a common library like jQuery. Once opened, the script runs via wscript.exe, launching a heavily obfuscated payload.
Real Case Analysis: Contract Template Search Leads to Gootloader
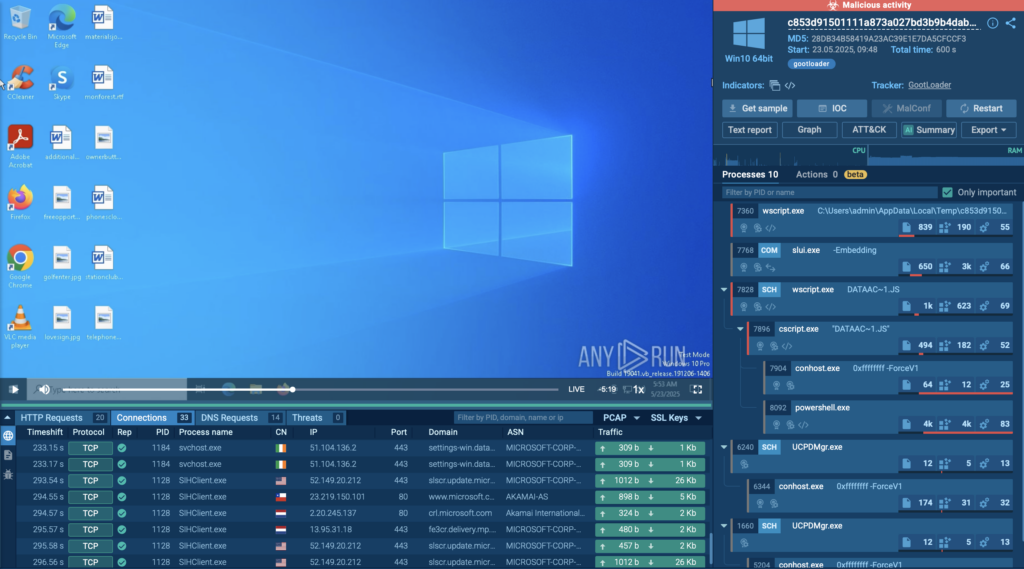
The process graph shows the full attack chain: the first-stage payload drops a second-stage JavaScript file, creates a scheduled task for persistence, and hands execution from wscript.exe to cscript.exe, which then spawns a PowerShell process.
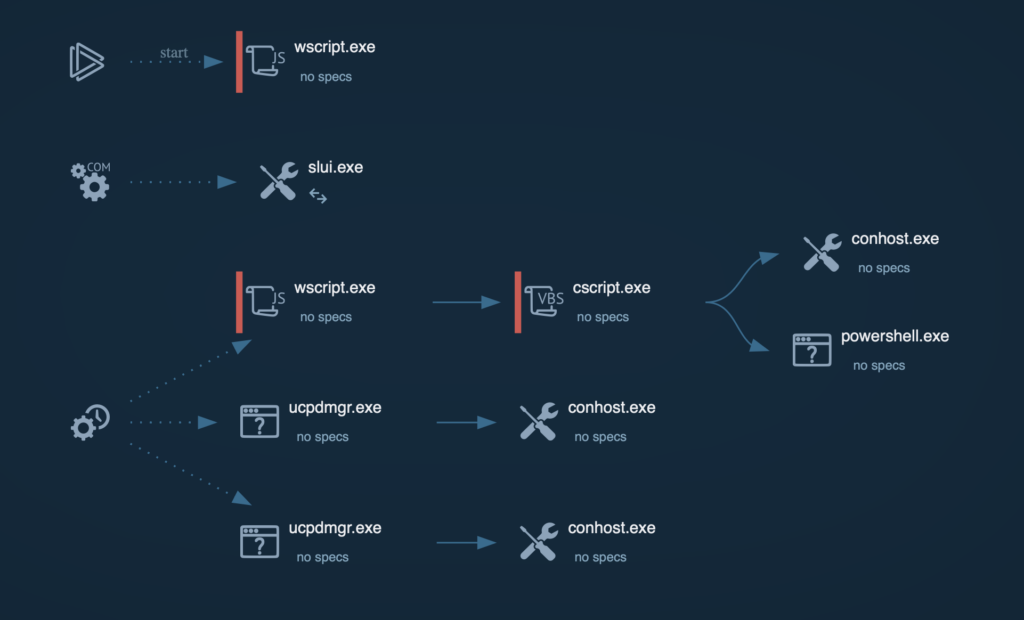
Mapped TTPs in the MITRE ATT&CK® section reveal multiple techniques, including system reconnaissance, persistence via scheduled tasks, and data exfiltration through HTTP headers.
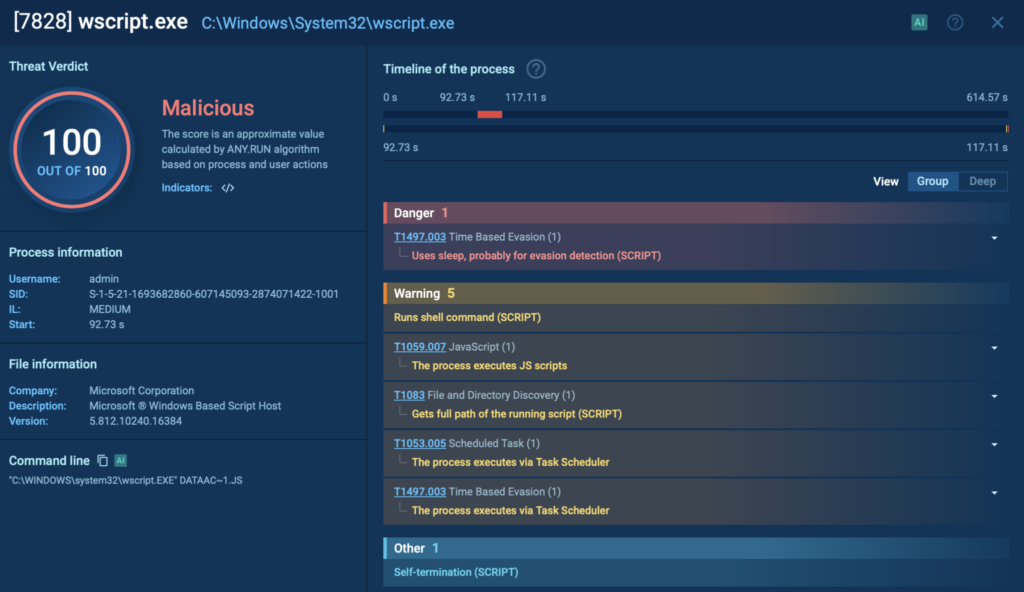
At the end of the investigation, a detailed report with IOCs is generated, containing domains, file hashes, and registry keys. These can be shared instantly with your team or imported into security tools to block future attacks.
Uncover Evasive Malware Designed to Evade Detection
Some threats are designed to stay hidden, activating only under specific system conditions, locales, or network environments. Hunter equips you with the tools to expose them.
You can dissect samples in depth by inspecting network traffic, registry modifications, and running processes, giving you a complete picture of the malware’s activity and persistence mechanisms. This visibility is critical for detecting hidden payloads and spotting malicious behavior that traditional scanners might miss.
Hunter also lets you gather unique IOCs directly from malware configurations and Suricata IDS detections. These high-confidence indicators can be used to update detection rules, block malicious infrastructure, and improve threat-hunting accuracy across your environment.
Finally, you can investigate in-depth by customizing the OS, installed tools, and network settings. Switch locales, adjust keyboard languages, or route traffic through specific regions using a residential proxy to bypass geofencing. This flexibility enables you to trigger and observe behaviors that would otherwise remain dormant, ensuring no evasion technique goes unnoticed.
Revealing Geofenced Malware with Locale and Network Routing
Some malware is geofenced, checking the geolocation of the infected host before delivering a payload. If the system isn’t in a target country, the attack simply won’t proceed.
With Hunter, you can bypass these restrictions by changing the system locale and routing traffic through another region, either via TOR or a residential proxy.
In this case, a malicious document with an Italian-language template was analyzed in a default en-US environment. The Regsvr32.exe process launched but didn’t receive any payload, terminating shortly after. Restarting the analysis with the locale set to it-IT and routing traffic through Italy via TOR revealed the hidden threat: Ursnif (Gozi) was successfully downloaded as a payload.
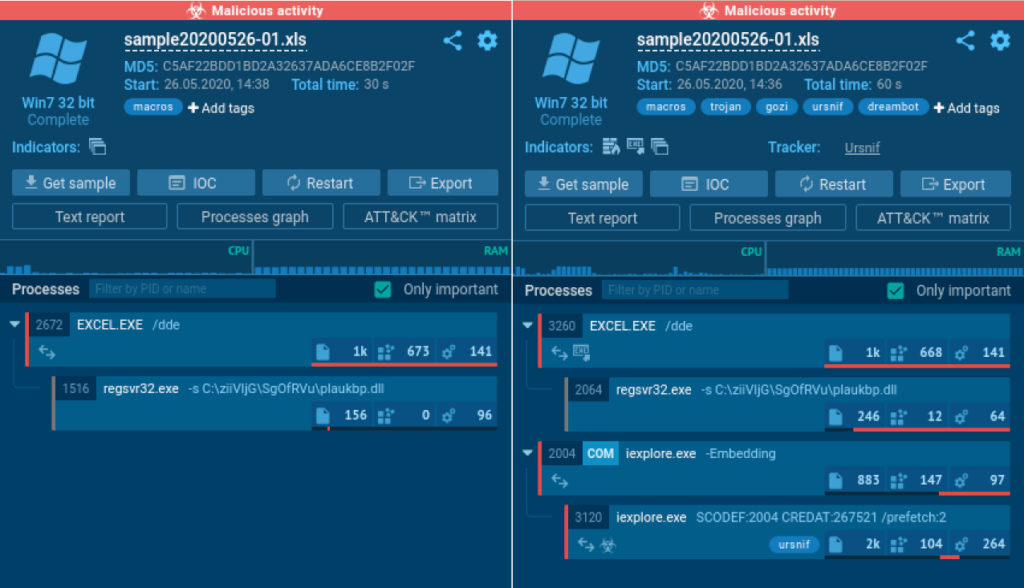
This combination of environment customization and network rerouting allows analysts to uncover full attack chains, capture critical IOCs, and study malware that would otherwise remain invisible in automated or default setups.
Scale Early Threat Detection, Reduce Business Risks with Enterprise Plan
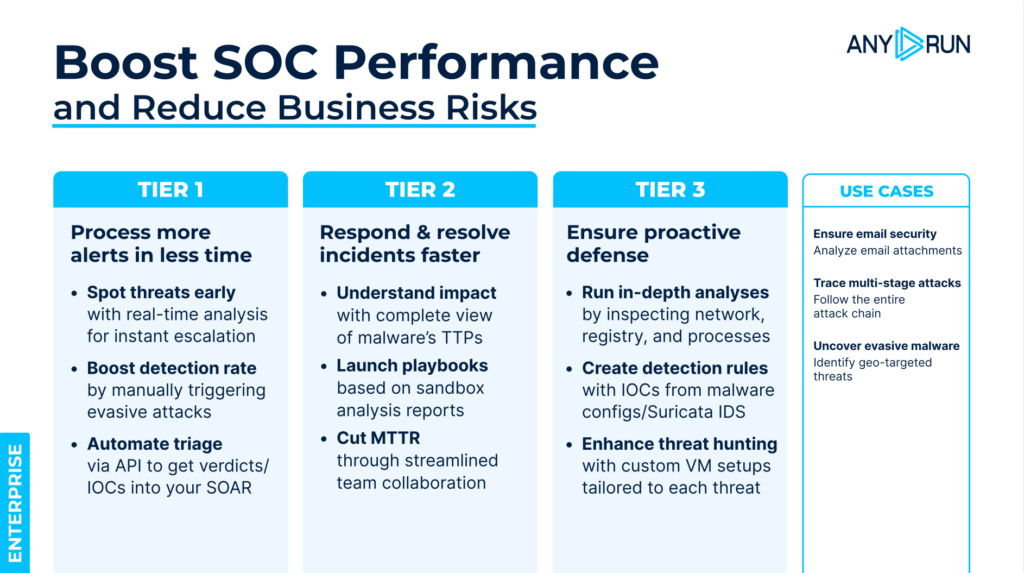
Built for SMBs, large enterprises, MSSPs, and government agencies, the Enterprise plan gives SOC teams the full power of ANY.RUN’s Interactive Sandbox, with advanced capabilities for security, automation, and collaboration.
- +36% average detection rate improvement in SOC environments
- 20% workload reduction for Tier 1 analysts through automated triage
- 21 minutes faster MTTR per case boosting overall SOC efficiency
- Up to 3x overall SOC performance gains when scaling across large teams
- 30% fewer escalations from Tier 1 to Tier 2, thanks to skill-building through interactive analysis
- Trusted by 15,000+ organizations across finance, telecom, retail, government, and healthcare
Enterprise is designed for teams that need to investigate faster, work together seamlessly, and stay ahead of evolving threats.
With Enterprise, you can:
- Slash business risk with early threat detection to prevent costly damage to your infrastructure and reputation.
- Cut MTTR through quick triage and clear threat insights that speed up decisive threat response.
- Increase detection rate by analyzing all types of Windows, Linux (including ARM), and Android files to identify more threats faster.
- Enhance productivity by automating routine tasks to help teams focus on critical incidents with less fatigue.
- Develop analyst expertise through hands-on, guided analysis that doubles as real-world training and saves on resources on onboarding.
- Protect sensitive data with private analyses, compliance with strict security frameworks, and isolated working environments.
- Collaborate seamlessly with shared investigations, role-based permissions, and productivity tracking for the whole SOC.
Enterprise provides API/SDK access that lets SOC teams utilize ANY.RUN’s connectors for popular security solutions like SIEM, XDR, TIP systems to streamline workflows and increse response speed even further.

Sandbox for Businesses
Boost performance of your SOC with the Enterprise plan designed for SMBs, MSSPs, enterprise companies, and government organizations.
Case Study: Expertware Cuts Investigation Time by 50%
Challenge:
Expertware, a leading European MSSP, needed to accelerate malware investigations, cut down on manual processes, and deliver faster, higher-quality results to its clients.
Result:
By adopting ANY.RUN Enterprise, Expertware reduced investigation turnaround time by 50%, boosted SOC efficiency with real-time collaborative analysis and shared reports, and gained complete visibility into multi-stage and fileless attacks, from initial macro execution to C2 communications. These improvements allowed them to deliver clearer, more actionable reports, enabling clients to respond before threats escalated.
“ANY.RUN’s interactive approach was critical in dissecting a complex multi-stage XLoader campaign and swiftly mitigating its impact across our network.”
— Expertware, Leading European MSSP
Ready to Get Started?
Whether you need the agility of Hunter or the full-scale power of Enterprise, ANY.RUN gives you the solutions to detect, investigate, and stop threats faster.
Contact us for a trial or a personalized quote today.
About ANY.RUN
Designed to accelerate threat detection and improve response times, ANY.RUN equips teams with interactive malware analysis capabilities and real-time threat intelligence.
ANY.RUN’s cloud-based sandbox supports investigations across Windows, Linux, and Android environments. Combined with Threat Intelligence Lookup and Feeds, our solutions give security teams full behavioral visibility, context-rich IOCs, and automation-ready outputs, all with zero infrastructure overhead.
Ready to see how ANY.RUN’s services can power your SOC?
3 comments








I don’t even understand how I finished up here, however I thought this submit was good. Cheers!
Someone essentially help to make critically posts I might state.
This is the very first time I frequented your web page and so
far? I surprised with the research you made to create this
actual publish amazing. Magnificent task!
fantastic issues altogether, you just received a new reader.