Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases
A keylogger is a type of spyware that infects a system and has the ability to record every keystroke made on the device. This lets attackers collect personal information of victims, which may include their online banking credentials, as well as personal conversations. The most widespread vector of attack leading to a keylogger infection begins with a phishing email or link. Keylogging is also often present in remote access trojans as part of an extended set of malicious tools.

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
A keylogger, also known as a keystroke logger, is a type of malicious software which is intended for capturing information typed by users on their machines. They perform this activity by recording the keystrokes pressed by the person, saving this data and then transferring it to attackers.
Keylogging malware is typically used by operators who wish to gather sensitive information from compromised machines, including passwords, credit card numbers, cryptocurrency wallet credentials, and other similar details.
In many cases, keylogging is offered as an extra module of advanced remote access trojans (RATs). This means that attackers usually engage in several illegal activities simultaneously. Most often, such programs come equipped with additional features, enabling attackers to steal files and clipboard information from the system, drop additional payloads, and even monitor the user’s web camera.
Since many keyloggers come as extensions for RATs, the potential impact on the infected computer can be extremely serious. The type of information that keyloggers are capable of collecting is limited only by what the user types on their keyboard. Additionally, many of these programs also have access to the clipboard and subsequently can pull the information copied by the victim.
This stolen data can then be used for a variety of malicious purposes, including:
Many keyloggers or malware featuring keylogging modules are sold openly in the dark web, Telegram groups, and other platforms. This makes it possible for practically any person to gain access to this software and carry out attacks.
For instance, AgentTesla, a notable example of malware that is actually marketed as a legitimate keylogger for personal use. Criminals can purchase a subscription and use it freely to target different users.
As with most malware, keyloggers usually end up on users’ computers through multi-stage attacks. The first step is usually a deceptive email that is crafted to appear legitimate, containing a malicious attachment or a link to download one. Attachments can be in the form of office documents, PDFs, ZIP archives, or other files.
Attacks are often set up to require only a couple of clicks from the user to kickstart the infection chain. The result of this is the installation of keylogging software on the system and recording of keystrokes.
For instance, the Snake Keylogger operators are known to distribute phishing emails that exploit the theme of payments and invoices. Through this simple social engineering tactic, they manage to trick the user into downloading and opening a malicious file that causes their system to become compromised.
Some malware with keylogging capabilities can also move laterally, gradually infecting all computers belonging to the same network as the initial victim’s one. On top of that, many such malware exhibit worm activity and can spread through USB sticks. LimeRAT serves as a prime example of malware utilizing this method. Read a comprehensive technical analysis of LimeRAT in our blog.
After the installation stage begins, keyloggers attempt to gain persistence on the system, meaning that they try to ensure they will continue functioning without being detected even after a reboot or other disruptive activity. Some of the common ways for them to do this include injecting its malicious code into a legitimate process, modifying the registry, or adding itself to the Startup folder.
Analyze keylogger malware in the ANY.RUN sandbox – request a demo.
Once it establishes a strong presence on the device, the keylogger activates and discreetly attaches itself to the keyboard input process or hooks into the operating system's kernel. This allows it to continuously monitor all keystrokes and capture every key press.
After malware harvests enough information, it is configured to send it to attackers via a connection to its command-and-control server. The traffic between the malicious program and the operator is often obfuscated.
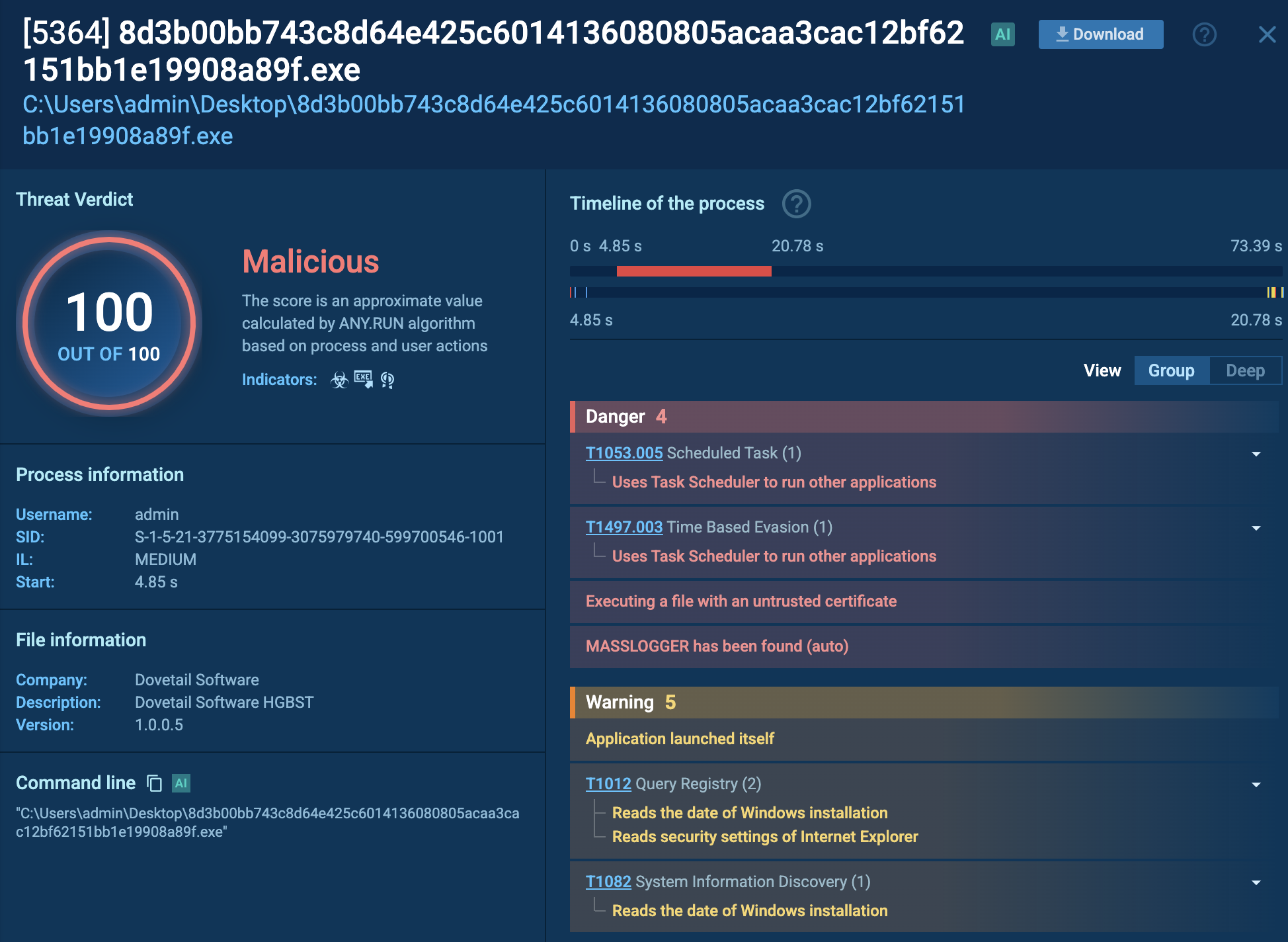
To properly assess the full scale of a typical keylogger operation, let’s examine a sample of Snake Keylogger, an infostealer with a focus on keystroke recording, in the ANY.RUN sandbox.
Snake malware uses a single process, arinzehfkd685371.exe, to steal data from compromised systems. It employs various tactics, including exploiting vulnerabilities, extracting credentials, querying the registry, and collecting emails. It also uses tool transfers and mail protocols for communication and data exfiltration. Analysis of Snake's configuration revealed the DES encryption key and SMTP credentials used for data exfiltration.
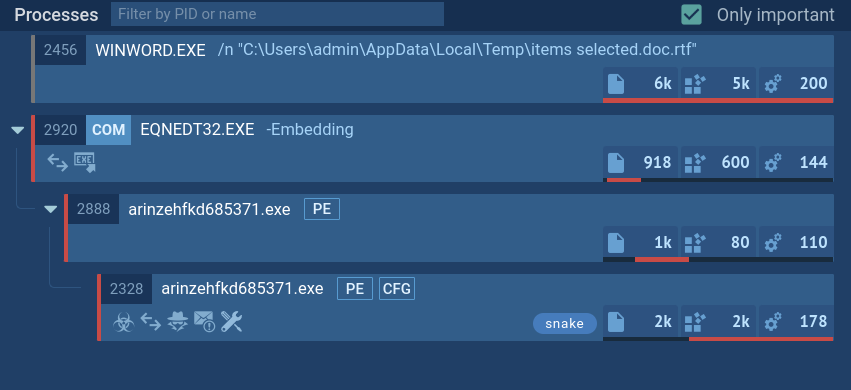 A process tree of a Snake Keylogger sample demonstrated by ANY.RUN
A process tree of a Snake Keylogger sample demonstrated by ANY.RUN
Proper protection against malware infections starts with a 360-degree visibility of the threat landscape. One of the best services for gaining an understanding of the current state of affairs in the malware realm is ANY.RUN’s Malware Trends Tracker.
Here are top three keyloggers, according to the service:
Safeguarding your organization from keyloggers and other malicious software demands a layered security approach. A critical element of this comprehensive strategy is utilizing malware analysis sandboxes.
ANY.RUN offers a convenient cloud environment for analyzing files and URLs. The service provides access to a variety of tools for investigating threats and automatically detects malicious activity.
ANY.RUN also makes it possible for users to interact with malware in an isolated virtual machine just like they would on their own computer to perform complex actions required for analyzing certain types of malware.
Try ANY.RUN for free – request a demo!