In today’s article, we’re going to look under the hood of a modular RAT — LimeRAT. Let’s get right into it!
What is LimeRat
LimeRAT is a Remote Access Trojan (RAT) that’s been around for a few years now. It’s a versatile piece of malware designed to give attackers control over an infected system. With its relatively small file size, it tries to fly under the radar of traditional antivirus solutions.

What makes LimeRAT particularly interesting is its ability to perform a wide range of malicious activities. Some of these include keylogging, stealing passwords, and capturing screenshots. Additionally, LimeRAT can execute arbitrary commands, download and upload files, and even use the infected machine for crypto-mining or DDoS attacks.
LimeRAT malware analysis
To start, let’s open a sample in Detect It Easy:
Upon inspection, we observe that the code has been obfuscated (MITRE T1027) and unreadable: the names of classes, methods, and variables are made out of random glyphs.
Since the sample is written in a .NET language, let’s open it in DnSpy.
Finding the configuration
After examining the malware’s classes, we find something resembling a class with its configuration:
We notice that this class contains a field that appears to be a string encoded using the Base64 algorithm (MITRE T1132.001):
We attempted to decode this string using CyberChef, but were unsuccessful. It is likely that the string is not only encoded but also encrypted.
Looks like the string is encoded and encrypted. Therefore, we will attempt to analyze this string and identify any functions or instructions that reference it. To do this, we right-click on the field and select “Analyse” from the context menu (alternatively, we can select the field and use the Ctrl + Shift + R shortcut).
In the resulting window, we are interested in where the value of this string is being read. We expand the “Read by” section and see that the string is being read in two methods:
We briefly inspect the first method but don’t see anything interesting here. It appears that this method is not specifically related to the virus configuration:
Let’s move on to the second method. We immediately notice some interesting code where our string is being used with the method WebClient.DownloadString, which is used to download a string from a remote resource.
Before our string is passed to WebClient.DownloadString is passed through another method that clearly transforms it into something that DownloadString can consume.
Let’s take a closer look at this method and see what it does to our string.
After a quick evaluation of the method, we see that it uses instances of the RijndaelManaged and MD5CryptoServiceProvider classes.
It appears that we have found the function where our string is decrypted:
LimeRAT decryption algorithm
Let’s break down how the decryption algorithm works in more detail:
- Instances of the RijndaelManaged and MD5CryptoServiceProvider classes are created. If we search for the RijndaelManaged class on MSDN, we see that it is essentially an obsolete implementation of the AES encryption algorithm (MITRE T1027). The MD5CryptoServiceProvider class, as the name implies, is used to compute an MD5 hash.
- An array of 32 bytes is created and initialized with zeros. This array will be used to store the AES key.
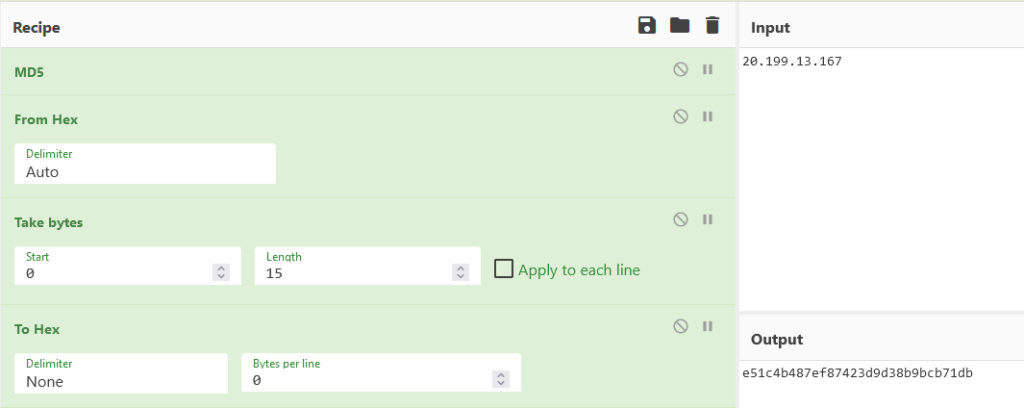
- To generate the key, the MD5 hash of another string from the configuration class is first computed (in our case, the string is “20[.]199.13.167”).
- Next, the first 15 bytes and then the first 16 bytes of the computed hash are copied to the previously created array. The last element of the array remains zero.
- The generated key is set to the key property of the RijndaelManaged instance. The Mode property is set to CipherMode.ECB.
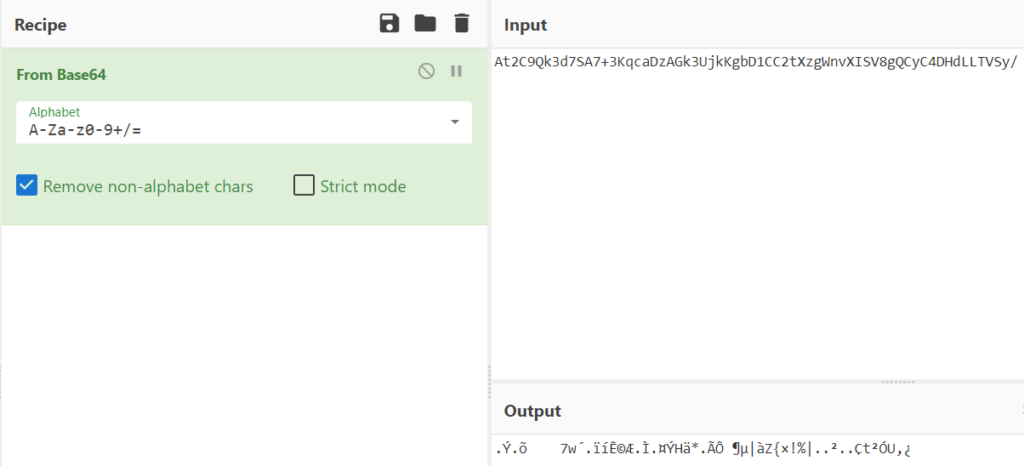
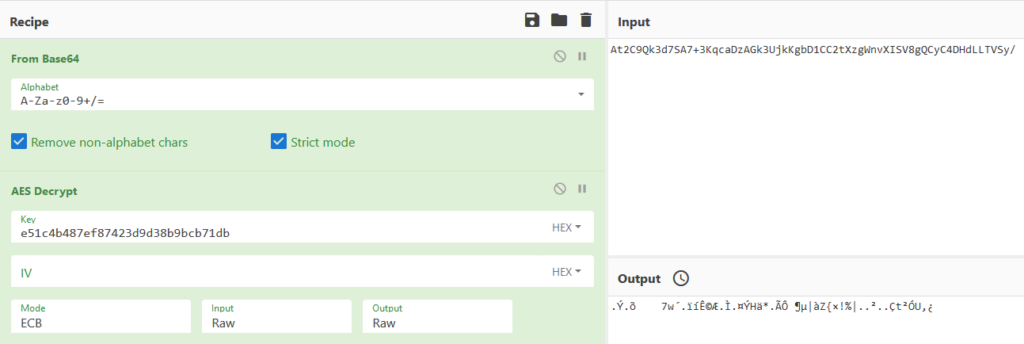
- Finally, the original string is decoded using the Base64 algorithm and decrypted using the AES256-ECB algorithm.
Let’s try to replicate this algorithm in CyberChef to confirm our findings. We will need 2 CyberChef tabs, one where we’ll use MD5 to generate the AES key, and another where we’ll attempt to decrypt the data.
First, we calculate the MD5 hash and take 15 bytes from it. Then copy them to the ‘Key’ field in the AES Decrypt section in another tab:
Then, we take the first 16 bytes of MD5 hash:
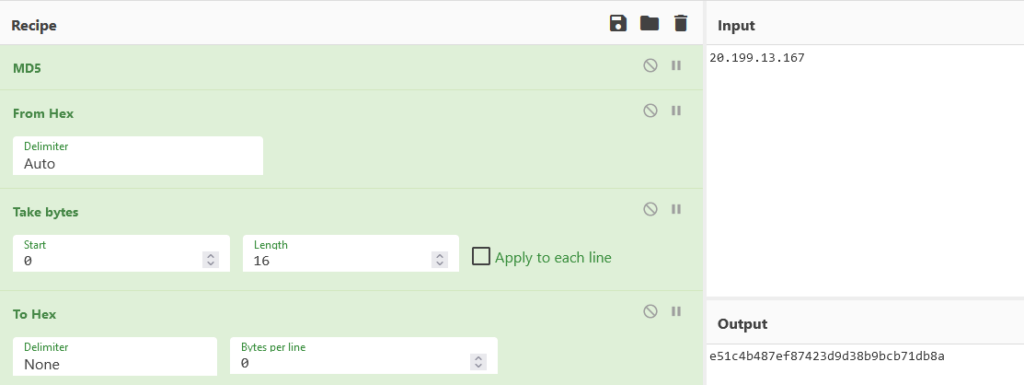
Our next step is to append them to previous 15 bytes and add a zero byte at the end as a padding byte (to 32 bytes):
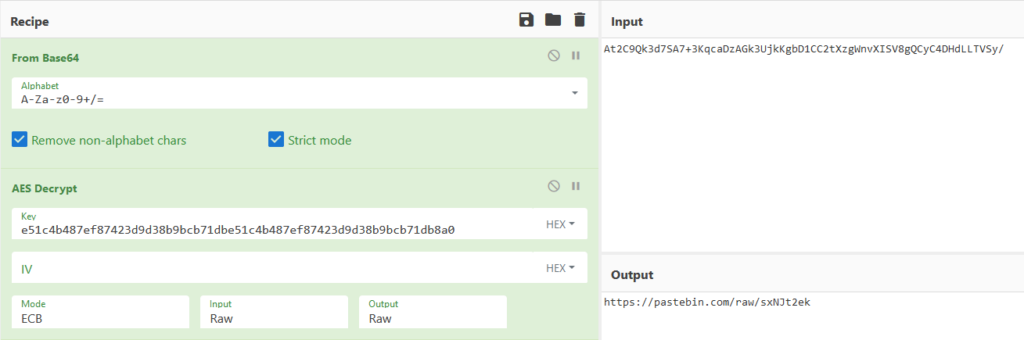
And now we can see the decrypted string in the output section.
You can try the same here as well.
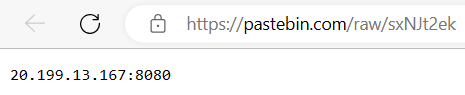
After decrypting the string, we get a link to a PasteBin note: https://pastebin[.]com/raw/sxNJt2ek. When we navigate to the link, we see the C2 address of the malware.
Wrapping Up
In this article, we successfully analyzed LimeRAT and uncovered its configuration. We identified the use of the .NET language and examined the malware classes, which revealed that obfuscation had been implemented. By meticulously inspecting these classes, we determined the decryption algorithm employed to decode the string containing the C2 address.
IOCs
Analyzed files:
| SHA1 | 14836dd608efb4a0c552a4f370e5aafb340e2a5d |
| SHA256 | 6d08ed6acac230f41d9d6fe2a26245eeaf08c84bc7a66fddc764d82d6786d334 |
| MD5 | d36f15bef276fd447e91af6ee9e38b28 |
| SSDEEP | 3072:DDiv2GSyn88sH888wQ2wmVgMk/211h36vEcIyNTY4WZd/w1UwIwEoTqPMinXHx+i:XOayy |
IPv4:
| IOC | Description |
| 20[.]199.13.167:8080 | LimeRAT’s C2 server |
Domains:
| IOC | Description |
| https://pastebin[.]com/raw/sxNJt2ek | PasteBin used by LimeRAT to hide its original C2 server |
MITRE (ARMATTACK):
| Tactic | Technique | Description |
| TA0005: Defense Evasion | T1027: Obfuscated Files or Information | Malware is using obfuscator to strip its method names, class names, etc. |
| TA0005: Defense Evasion | T1027: Obfuscated Files or Information | Malware uses Base64 algorithm to encode and decode data |
| TA0005: Defense Evasion | T1027: Obfuscated Files or Information | Malware uses AES algorithm to encrypt and decrypt data |
Although effective, this manual process can be time-consuming. This is where interactive sandboxes, such as ANY.RUN, prove to be invaluable.
ANY.RUN offers a powerful and user-friendly platform for automating malware sample analysis. By enabling users to safely execute malware within a secure environment, ANY.RUN efficiently extracts configurations for malware like LimeRAT, ultimately saving security researchers precious time and resources.
Let us show you how our interactive sandbox can fit into your workflow — get a 14-day free trial with our friendly sales team.
Interested in more content like this?
- Read our analysis of Formbook/XLoader
- Learn how we used a sandbox to analyze CryptBot
- Or check out our deep dive into Orcus Rat
4 comments










Thanks for the detailed research. njRAT immediately comes to mind. From the configuration you identified, you can automatically generate a network rule and enable it to be downloaded in the any_run interface. FeatureRequest)
Thank you for the feeback! What rules format would you prefer to have? It seems like an interesting idea and we could consider to add this kind of feature to the service.
Under “Generating the key:” section, is the wrong screenshot included? I do not see the CyberChef example of creating the AES key.
Thank you for the note. We have changed the screenshot and added a more detailed walk-through of creating the AES key.
Please check it out and let us know if you have any more questions.