Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


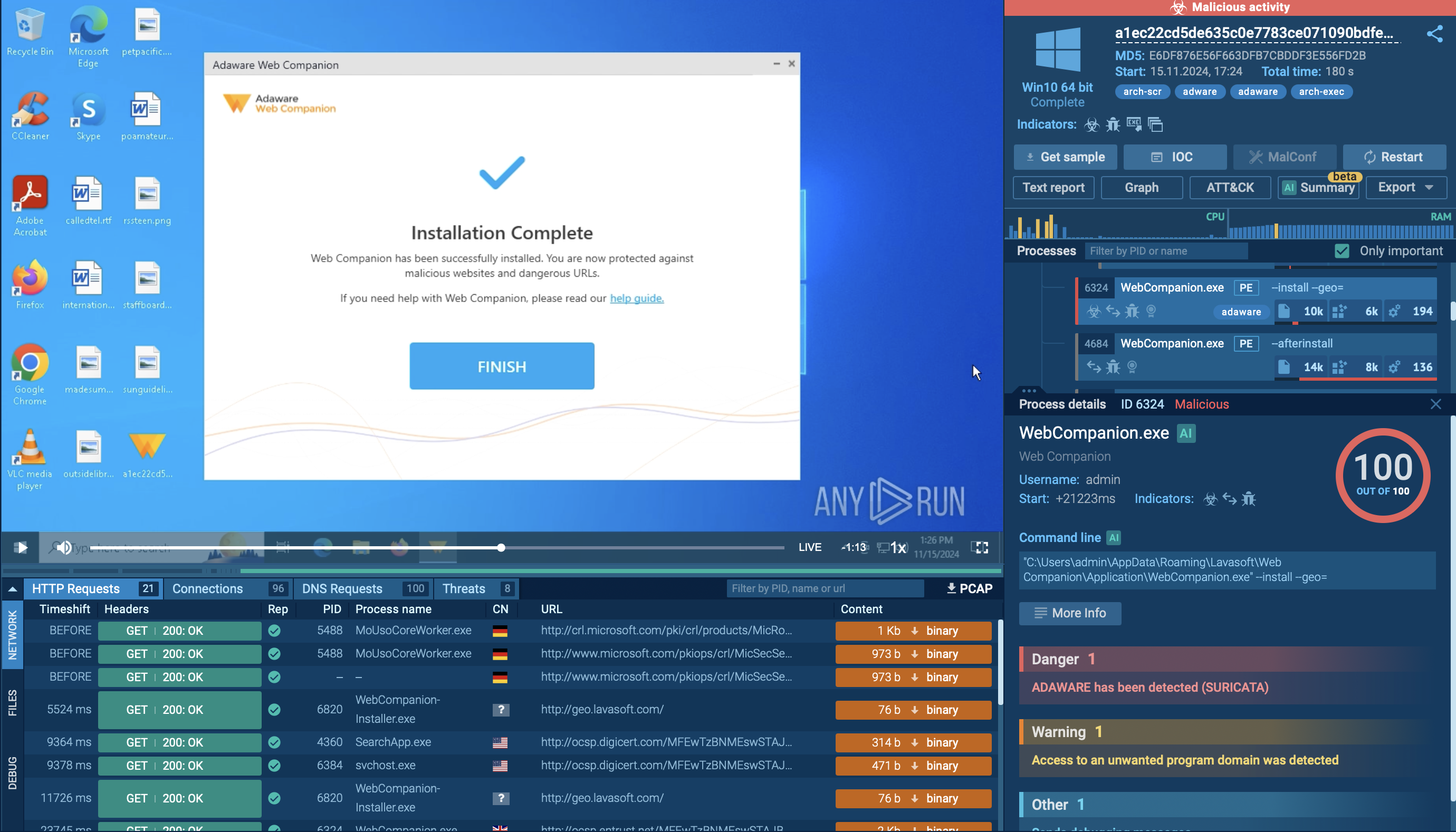
Play aka PlayCrypt ransomware group has been successfully targeting corporations, municipal entities, and infrastruction all over the world for about three years. It infiltrates networks via software vulnerabilities, phishing links and compromised websites. The ransomware abuses Windows system services to evade detection and maintain persistence. Play encrypts user files and steals sensitive data while demanding a ransom.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
1 March, 2022
First seen
:
|
12 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 March, 2022
First seen
:
|
12 February, 2026
Last seen
:
|

 813
813
 0
0

 490
490
 0
0

 2751
2751
 0
0
Play aka PlayCrypt is relatively new yet already notorious ransomware group active since mid-2022. It has impacted a wide range of businesses and critical infrastructure in North America, South America, and Europe.
It is based on double extortion technique and has intermittent encryption as its signature feature. Partial encryption is completed much faster, besides, it prevents detection by security solutions that monitor files for extensive modifications.
It infiltrates the targeted system by exploiting vulnerabilities in public-facing applications, such as Microsoft Exchange Server. It is also distributed via phishing emails containing malicious attachments or links. Malicious ads and compromised websites has also been detected as distribution vehicles.
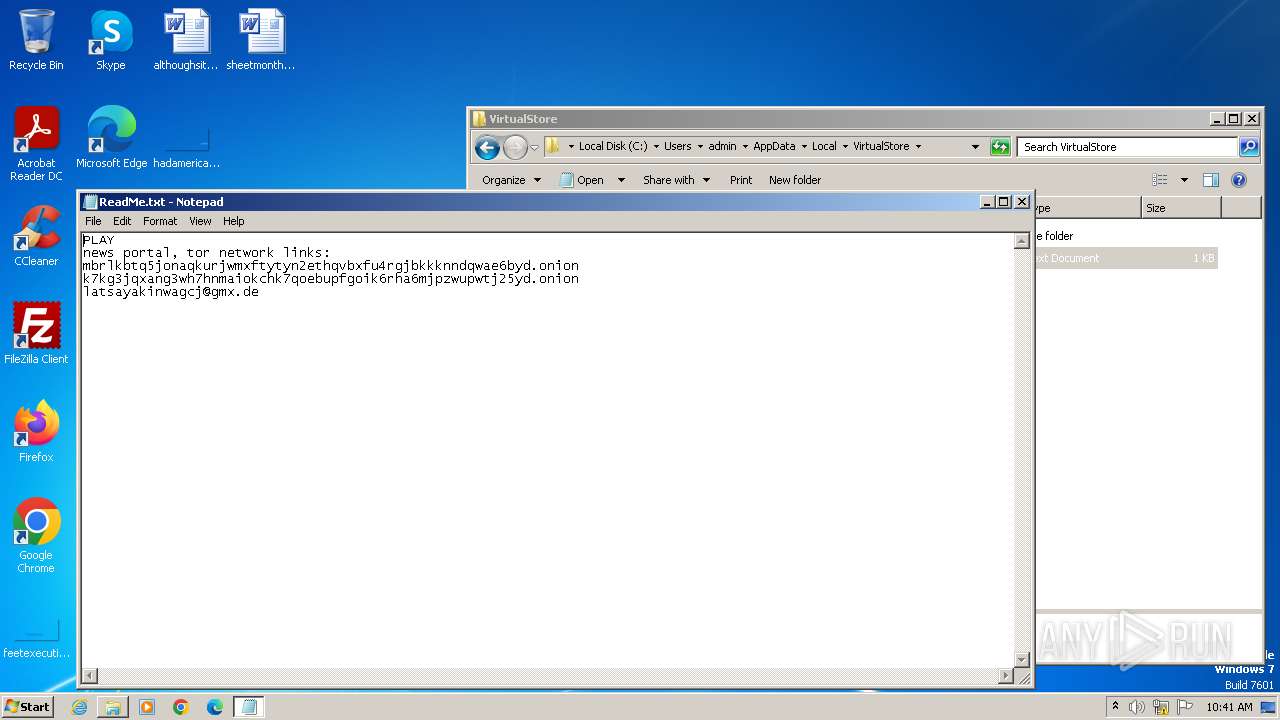 Play Ransomware ransom note shown in the ANY.RUN sandbox
Play Ransomware ransom note shown in the ANY.RUN sandbox
To move laterally within the network and deploy the ransomware payload, it abuses the legitimate tools and built-in system utilities (e.g., PowerShell, PsExec, Cobalt Strike).
After exfiltrating sensitive data, the ransomware encrypts files, adds the .play extension, and leaves a ransom note in each affected directory containing instructions on how to pay the ransom.
Play ransomware uses anti-analysis techniques to evade detection by security software, creates scheduled tasks and modifies registry entries to maintain persistence.
Play Ransomware is equipped with advanced capabilities focused on maximizing impact on the victims’ infrastructure:
Let’s upload the Play Ransomware to ANY.RUN’s Interactive Sandbox for analysis to see how it operates.
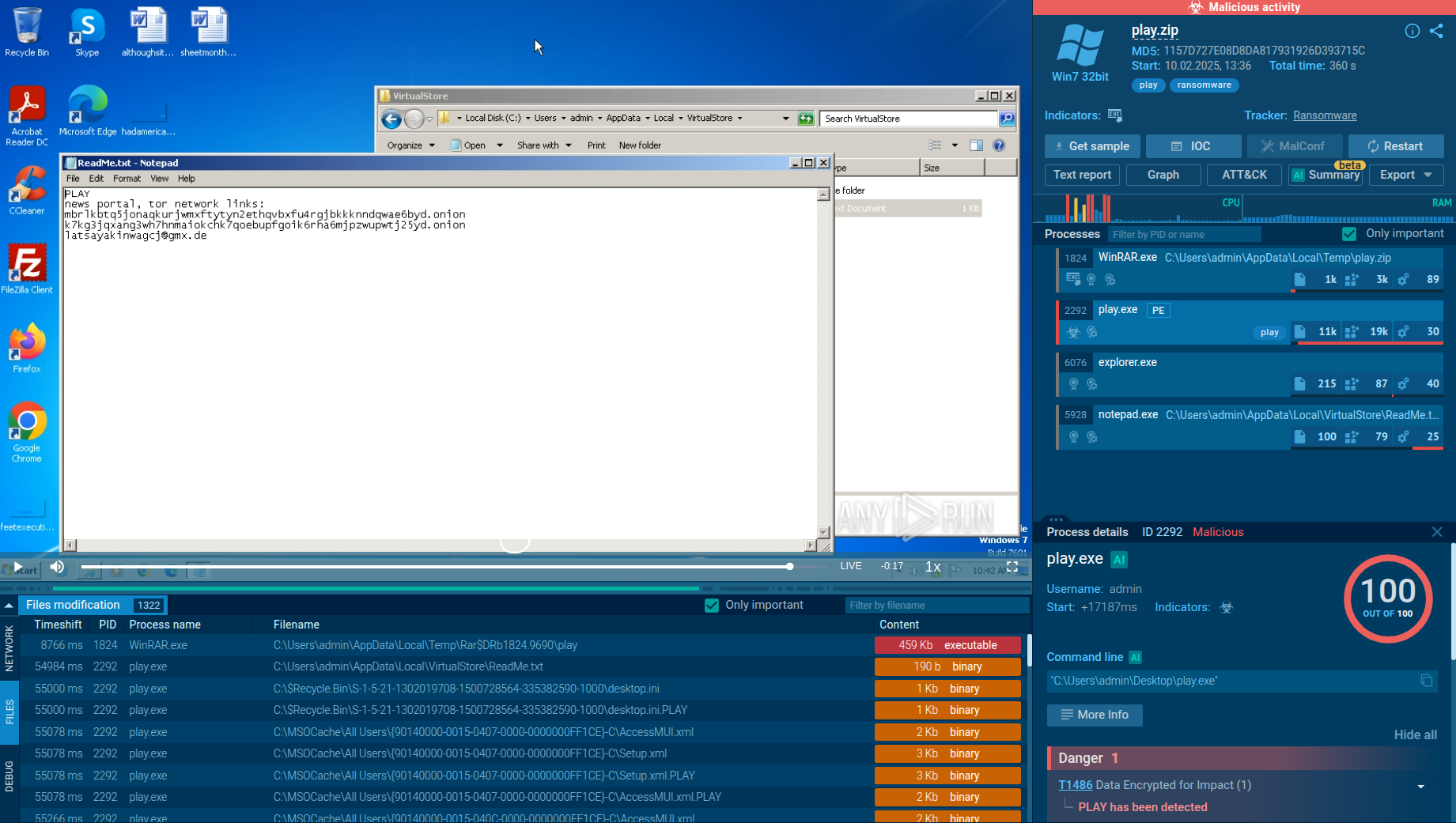 Play Ransomware analysis session in the ANY.RUN sandbox
Play Ransomware analysis session in the ANY.RUN sandbox
A typical Play ransomware attack begins with gaining initial access to the victim’s network via exploiting public-facing applications or abusing valid accounts.
Once inside the targeted environment, the malware focuses on stealth by heavily relying on Living Off the Land Binaries (LOLBins). To facilitate lateral movement and execute files, Play may use command-and-control applications like Cobalt Strike or SystemBC.
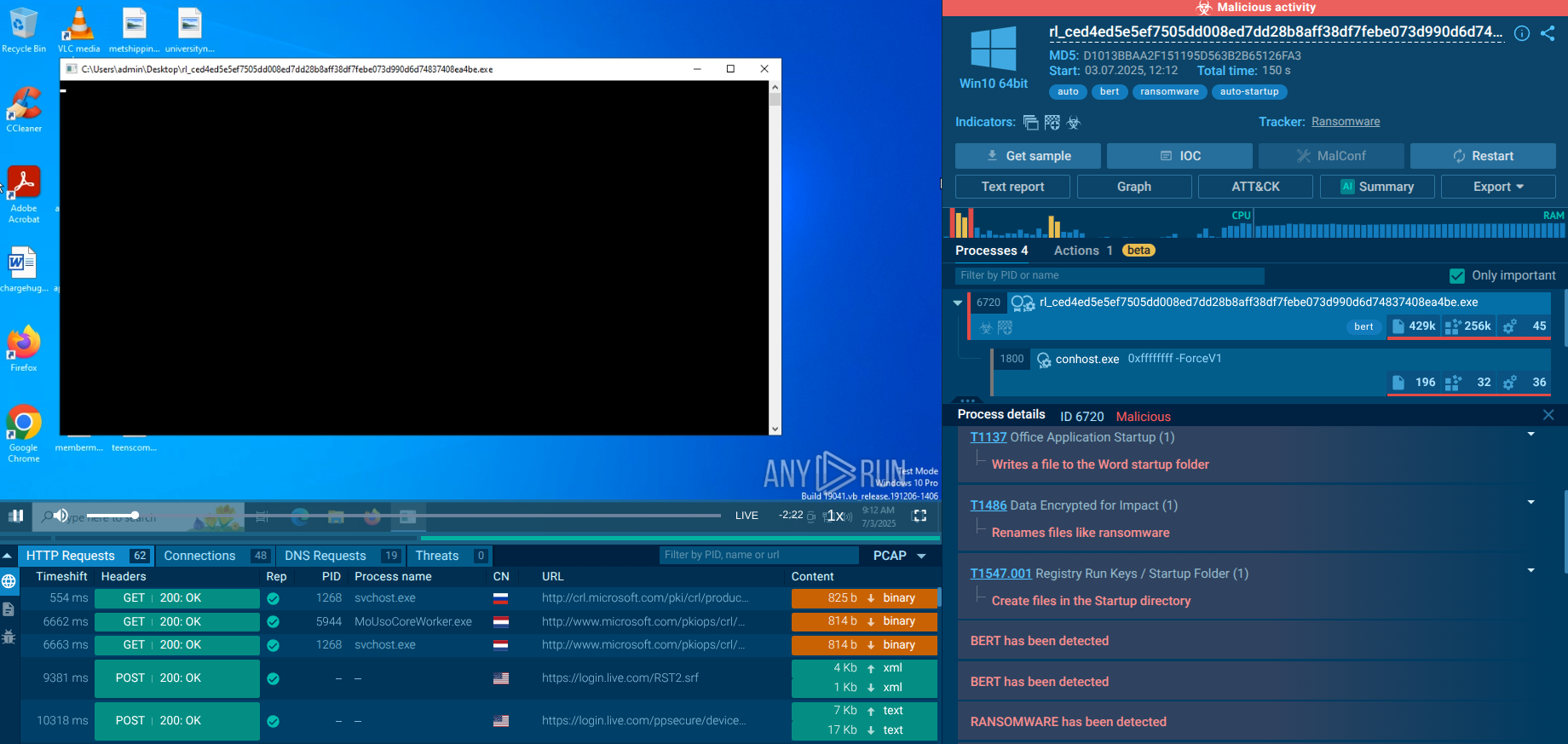
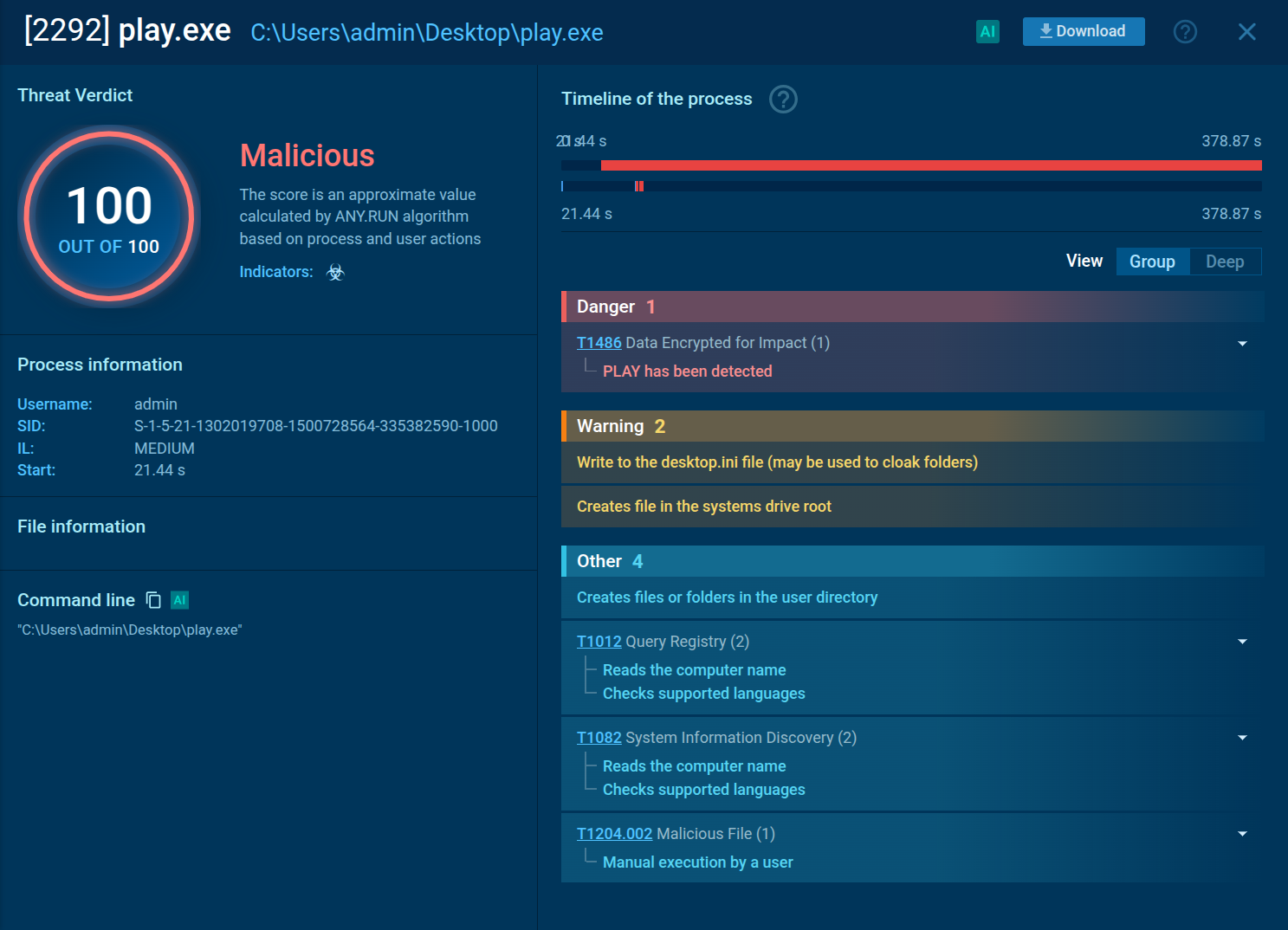 Play Ransomware process analysis in the ANY.RUN sandbox
Play Ransomware process analysis in the ANY.RUN sandbox
Before encrypting files, Play ransomware operators exfiltrate data. They do this by splitting compromised data into segments, compressing files, and transferring them to actor-controlled accounts.
After exfiltration, the ransomware encrypts files using an AES-RSA hybrid approach with intermittent encryption while skipping system files.
Encrypted files are appended with the .play extension, and a ransom note named ReadMe.txt is placed in the file directory on the C:\ partition.
To get the most current information about Play Ransomware, use Threat Intelligence Lookup. It contains data extracted from millions of public malware analyses conducted in ANY.RUN’s Interactive Sandbox.
You can use over 40 different search parameters, including specific IPs, domains, file names, or even mutexes. Using these filters, you can quickly gather important details about threats like Play Ransomware.
For example, if you were investigating Play Ransomware, you could start by directly searching for its name within the Threat Intelligence Lookup. Or, if you had other clues like unique file codes (hashes) or website connections it uses, you could search with those instead.
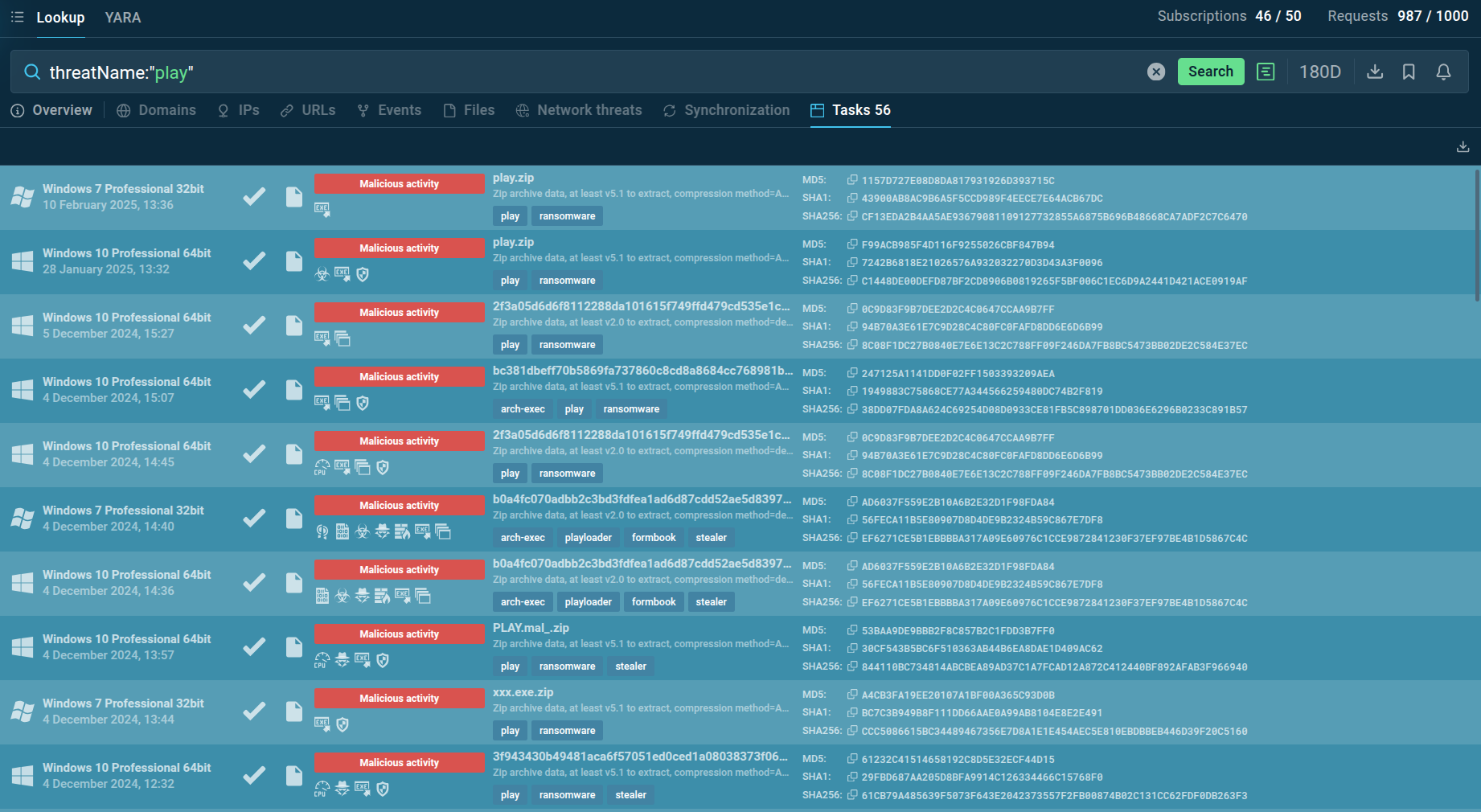 Search results for Play Ransomware in TI Lookup
Search results for Play Ransomware in TI Lookup
A simple and effective search would be to use the search term: threatName:"Play". This type of search will show you a list of sandbox reports associated with Play Ransomware. You can then explore these reports to get a deep understanding of exactly how this ransomware works and what it does.
Play Ransomware commonly gains initial access through several attack vectors. Compromised Remote Desktop Protocol (RDP) servers are a frequent entry point, often due to weak security configurations. Attackers exploit known vulnerabilities like CVE-2020-12812 in RDP services to bypass authentication and gain unauthorized system access.
Another prevalent method involves exploiting CVE-2022-41040, the ProxyNotShell vulnerability in Microsoft Exchange, allowing for remote code execution directly on vulnerable servers.
Play Ransomware poses a serious risk to organizations. Its blend of advanced techniques, such as partial encryption and lateral movement, coupled with readily exploitable entry points like RDP and VPN vulnerabilities, requires comprehensive security attention.
To prevent Play Ransomware infections, organizations can analyze suspicious files and URLs in ANY.RUN's Interactive Sandbox. The service provides fast insights into the malicious behavior and allows users to manually engage with threats in a safe environment just like on a standard computer.
.png)