Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases
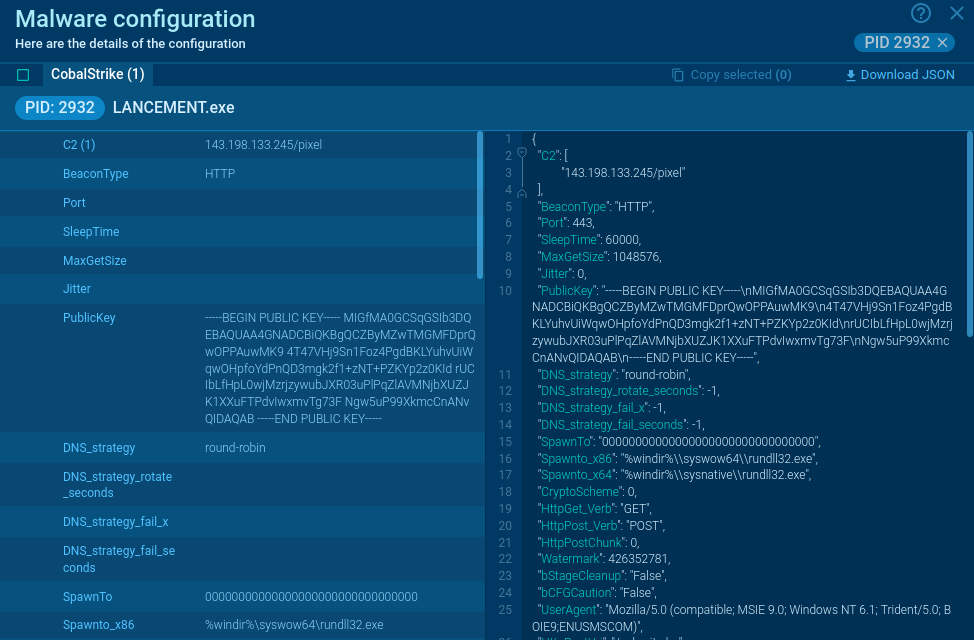
Sneaky 2FA is an Adversary-in-the-Middle (AiTM) phishing kit targeting Microsoft 365 accounts. Distributed as a Phishing-as-a-Service (PhaaS) through a Telegram bot, this malware bypasses two-factor authentication (2FA) to steal credentials and session cookies, posing a significant threat to individuals and organizations.
|
Phishingkit
Type
:
|
Unknown
Origin
:
|
|
1 October, 2024
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 October, 2024
First seen
:
|
27 February, 2026
Last seen
:
|

 787
787
 0
0

 478
478
 0
0

 2728
2728
 0
0
Sneaky 2FA phishing kit is a malware strain designed to bypass two-factor authentication (2FA), a critical security layer used by individuals and organizations worldwide. By hijacking authentication processes in real-time, this malware undermines what many consider a key safeguard in modern cybersecurity.
It often works as part of a larger attack chain, coordinating with infostealers, remote access trojans (RATs), and phishing kits. Its modular architecture, stealth capabilities, and real-time data interception make it a significant threat in today’s digital landscape.
First detected in October 2024, it is a full-featured phishing kit that compromises Microsoft 365 accounts. Sold via a Telegram-based PhaaS model, it provides cybercriminals with obfuscated source code for independent deployment.
Sneaky 2FA employs advanced anti-bot and anti-analysis measures, such as Cloudflare Turnstile challenges and IP filtering, to evade detection. Its fake Microsoft authentication pages, complete with auto-filled email fields and blurred legitimate interface screenshots, create a convincing illusion of authenticity. Nearly 100 domains hosting Sneaky 2FA phishing pages have been identified.
Sneaky 2FA propagates through multiple distribution channels, leveraging both technical and social engineering techniques:
Sneaky 2FA's impact extends beyond simple credential theft. Once attackers gain access to Microsoft 365 accounts, they can perform:
Session Hijacking: Steal active authentication sessions, allowing immediate access to user accounts without triggering additional security prompts
Persistent Access: Maintain long-term access to compromised accounts through stolen authentication tokens
Data Exfiltration: Access and download sensitive emails, documents, and organizational data stored in Microsoft 365 services
Account Takeover: Gain complete control over user accounts, including the ability to change passwords and security settings
Lateral Movement: Use compromised accounts as stepping-stones to access other systems and accounts within the organization
Sneaky 2FA poses severe risks to businesses, particularly those reliant on Microsoft 365 for operations:
Sneaky 2FA doesn't directly compromise individual computers but rather targets cloud-based accounts and services. The attack starts when users receive phishing emails containing links or QR codes that appear to be from Microsoft or other trusted sources.
After clicking malicious links, they are directed to convincing replicas of Microsoft 365 login pages hosted on attacker-controlled infrastructure. Sneaky 2FA as an adversary-in-the-middle intercepts information sent between a device with Microsoft 365 and a phishing server.
Even when users complete legitimate two-factor verification, the system captures and stores authentication tokens that can be replayed to gain account access. With valid session tokens, attackers can access Microsoft 365 accounts without triggering additional security prompts, effectively bypassing multi-factor authentication.
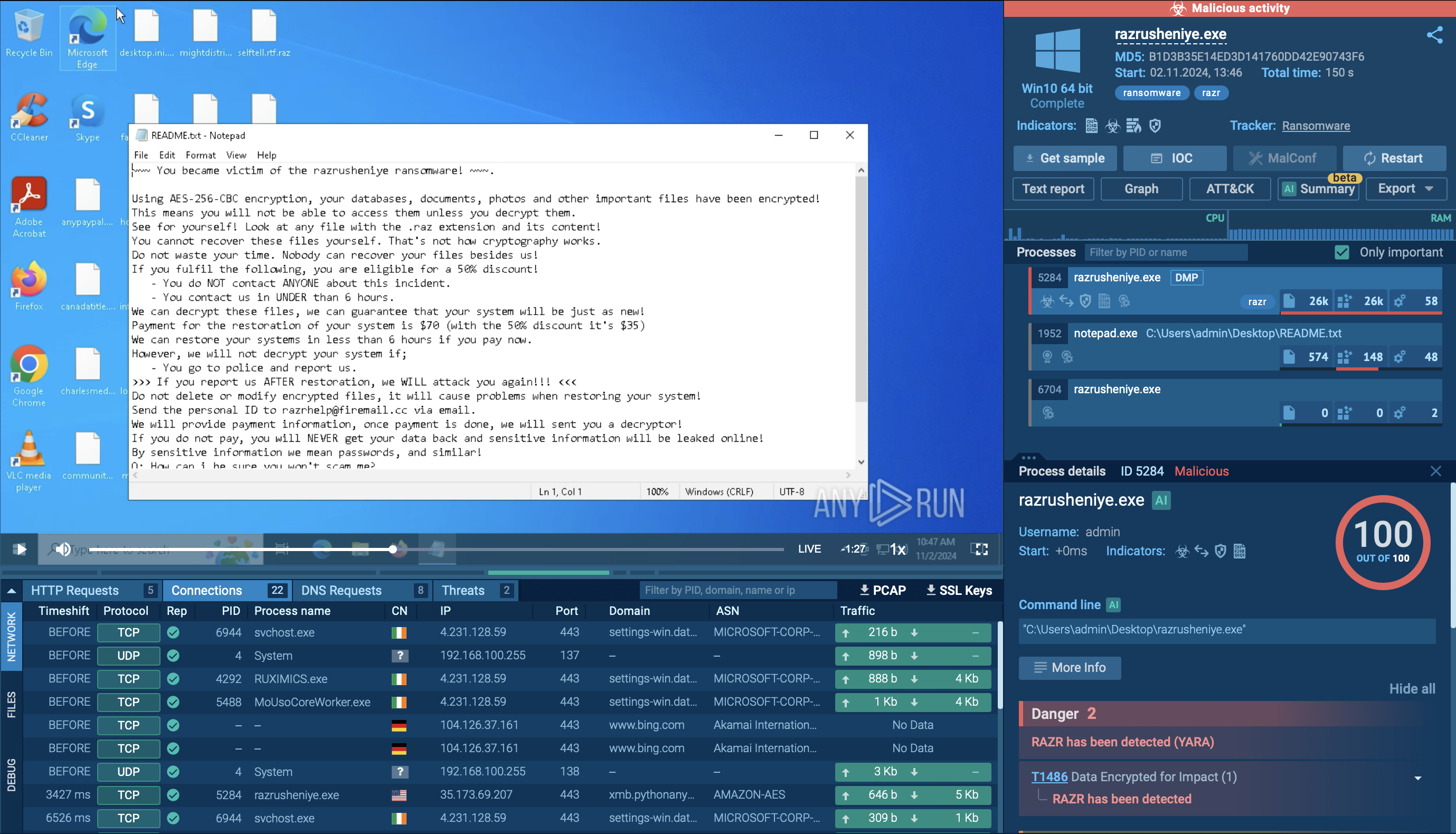
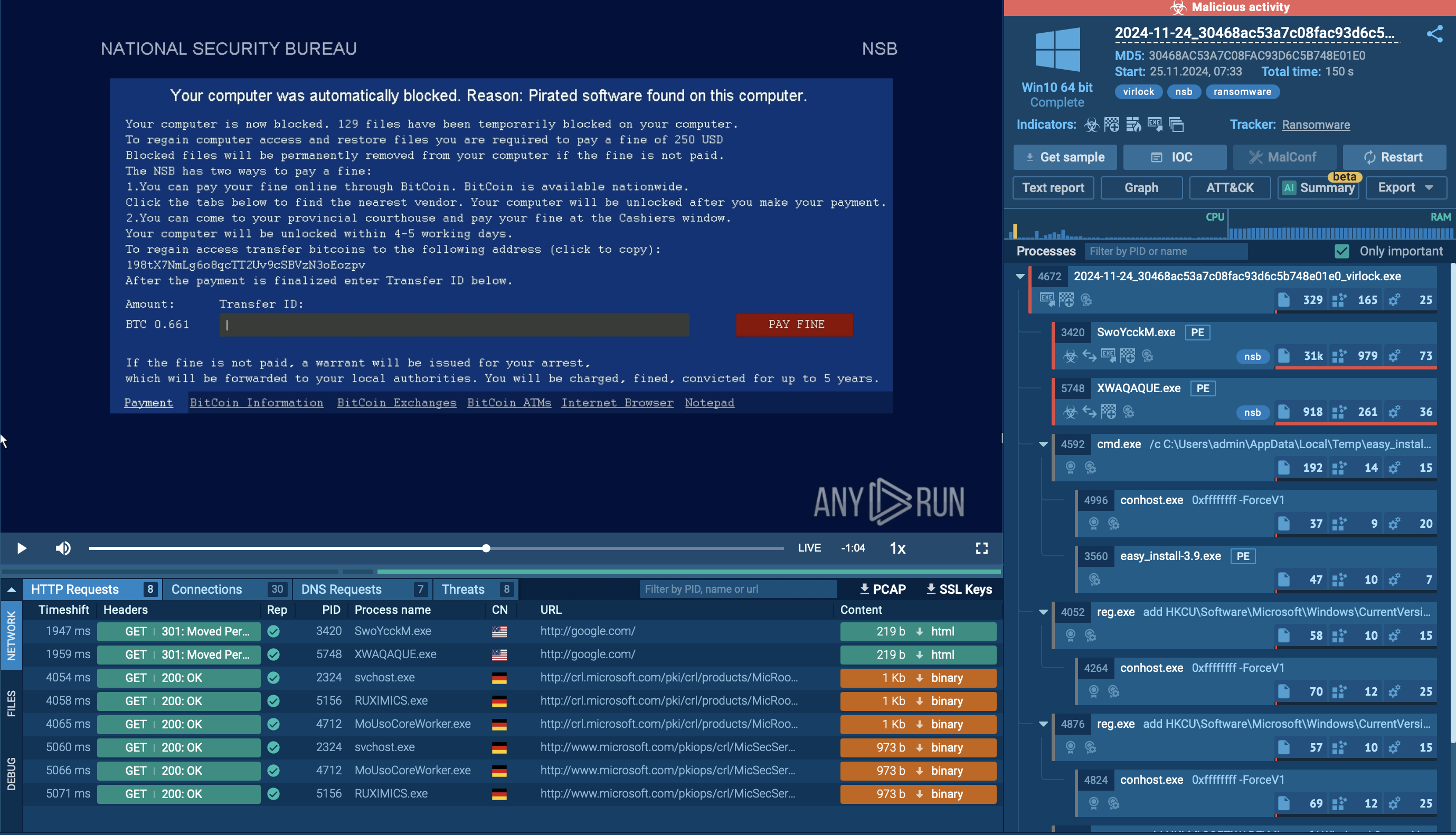
Samples of Sneaky2FA in action can be observed in ANY.RUN's Interactive Sandbox where the whole attack chain is dissected in a safe virtual machine environment.
Watch an analysis session of Sneaky 2FA fresh sample
 Sneaky 2FA analysis in ANY.RUN Interactive Sandbox
Sneaky 2FA analysis in ANY.RUN Interactive Sandbox
The attack unfolds through a carefully orchestrated series of steps designed to bypass two-factor authentication on Microsoft 365 accounts.
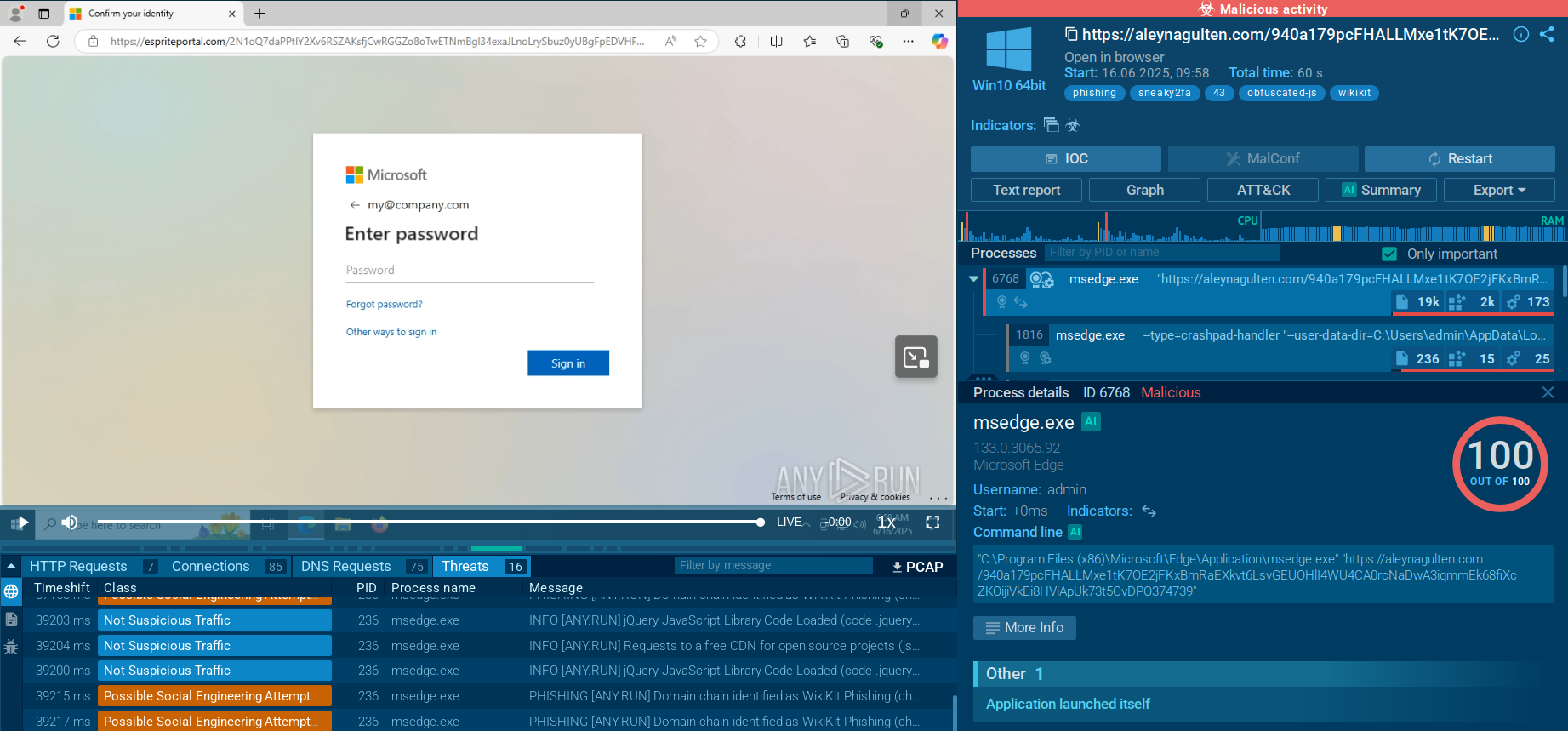
When a victim receives a phishing email, it typically appears as a legitimate security alert or notification from Microsoft 365, encouraging them to click a link. This link may contain an "autograb" feature that pre-fills the victim’s email address on the fake login page, increasing the illusion of authenticity.
Upon clicking the link, the victim encounters first a fake 'Access document' or other lure and then is redirected to a Cloudflare CAPTCHA designed to verify that they are human and to filter out automated bots, proxies, VPNs, or suspicious IP addresses and automated sandboxes without ML recognition. ANY.RUN has Automated interactivity (ML) which will click CAPTCHA. Visitors flagged as bots or researchers are redirected to harmless pages, such as a Wikipedia article, to avoid raising suspicion.
Once the victim passes the challenge, they are presented with a highly realistic fake Microsoft 365 login page, complete with blurred background images taken from actual Microsoft sites to enhance credibility. The victim enters their password, which is immediately captured by the phishing server. The kit then detects the victim’s configured 2FA method and prompts for the second authentication factor.
Acting as an adversary-in-the-middle, the phishing kit captures the 2FA code in real time as the victim submits it. With this information, the attackers hijack the session cookies, effectively bypassing the need for the 2FA code in subsequent accesses and gaining full control over the victim’s Microsoft 365 account.
If user submits URL or a file through API Throughout this process, the Sneaky 2FA kit employs multiple anti-detection techniques, including obfuscation of HTML and JavaScript code (tag obfuscated-js), embedding junk data and base64-encoded images, and using anti-debugging measures to thwart analysis via browser developer tools. The kit’s traffic filtering mechanisms ensure that only genuine targets are exposed to the phishing pages, minimizing the risk of detection by security researchers or automated defenses.
Threat intelligence plays a crucial role in defending against Sneaky 2FA and phishing kits in general by providing actionable data about attack patterns, indicators of compromise, and emerging threats. Indicators of Compromise enable proactive blocking of phishing infrastructure, and understanding Sneaky 2FA’s tactics, techniques, and procedures informs detection rules.
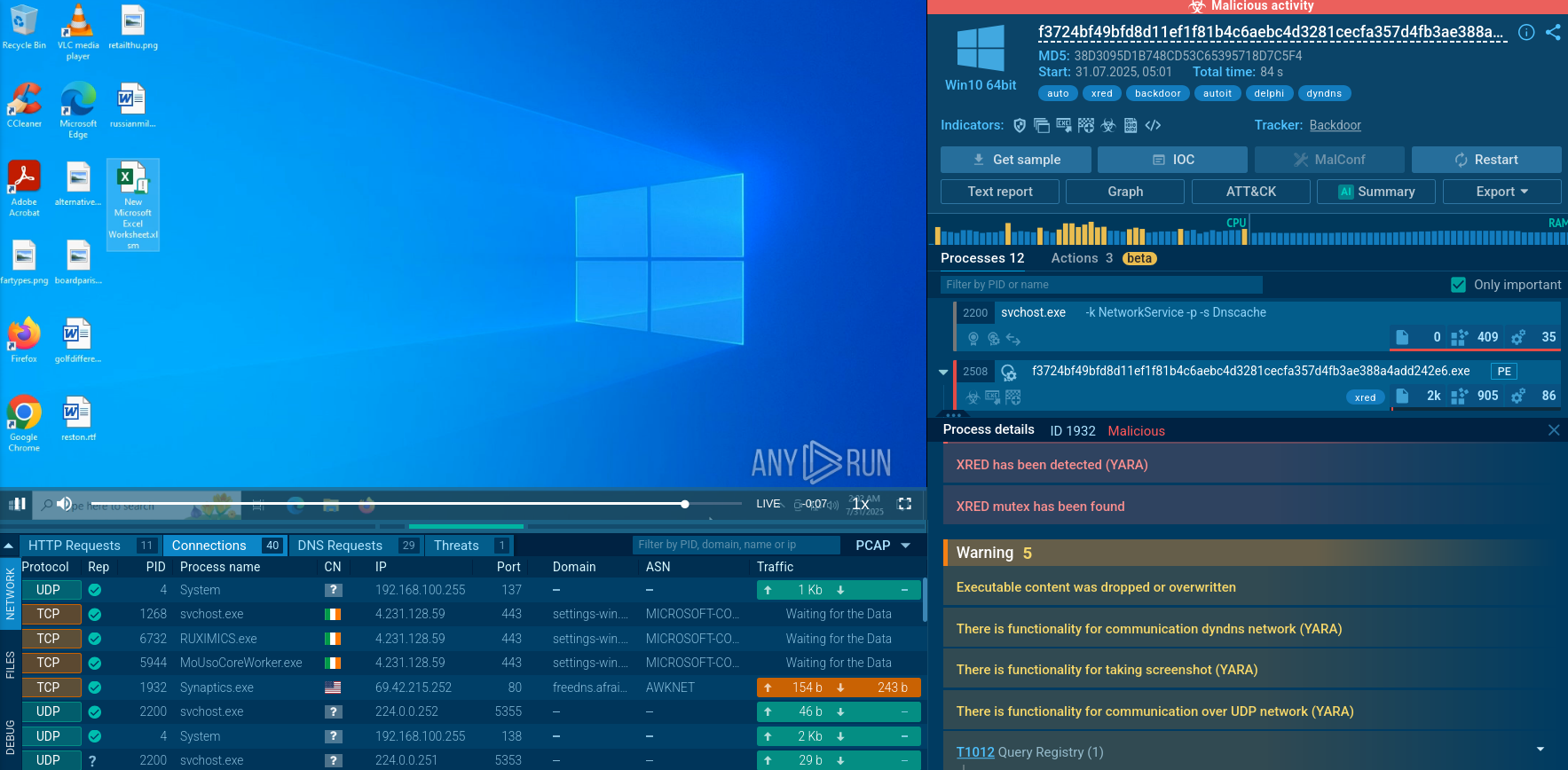
Start from searching Sneaky 2FA by the threat name in ANY.RUN Threat Intelligence Lookup:
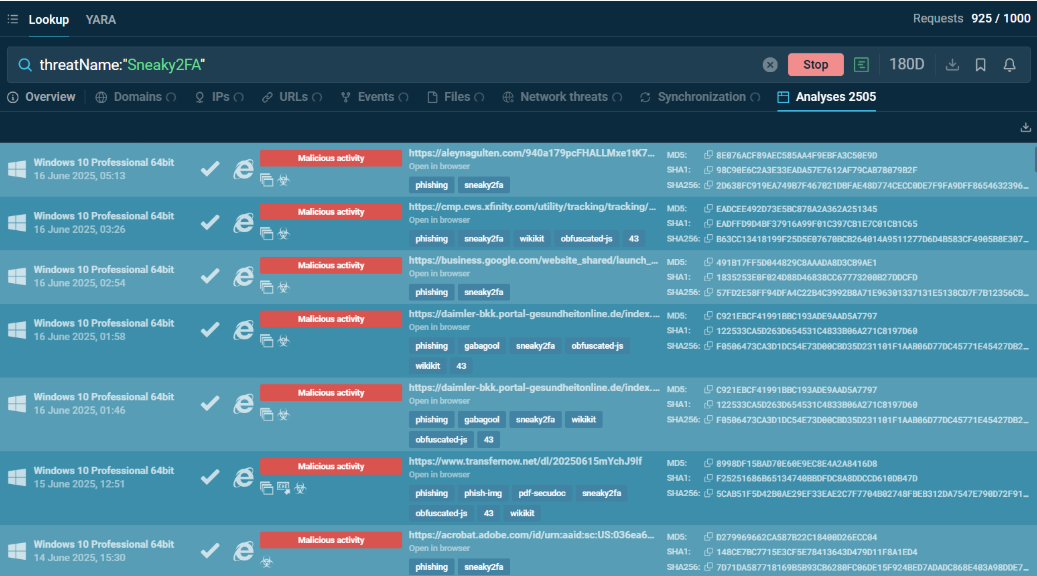 Sneaky 2FA sandbox analyses found via ANY.RUN TI Lookup
Sneaky 2FA sandbox analyses found via ANY.RUN TI Lookup
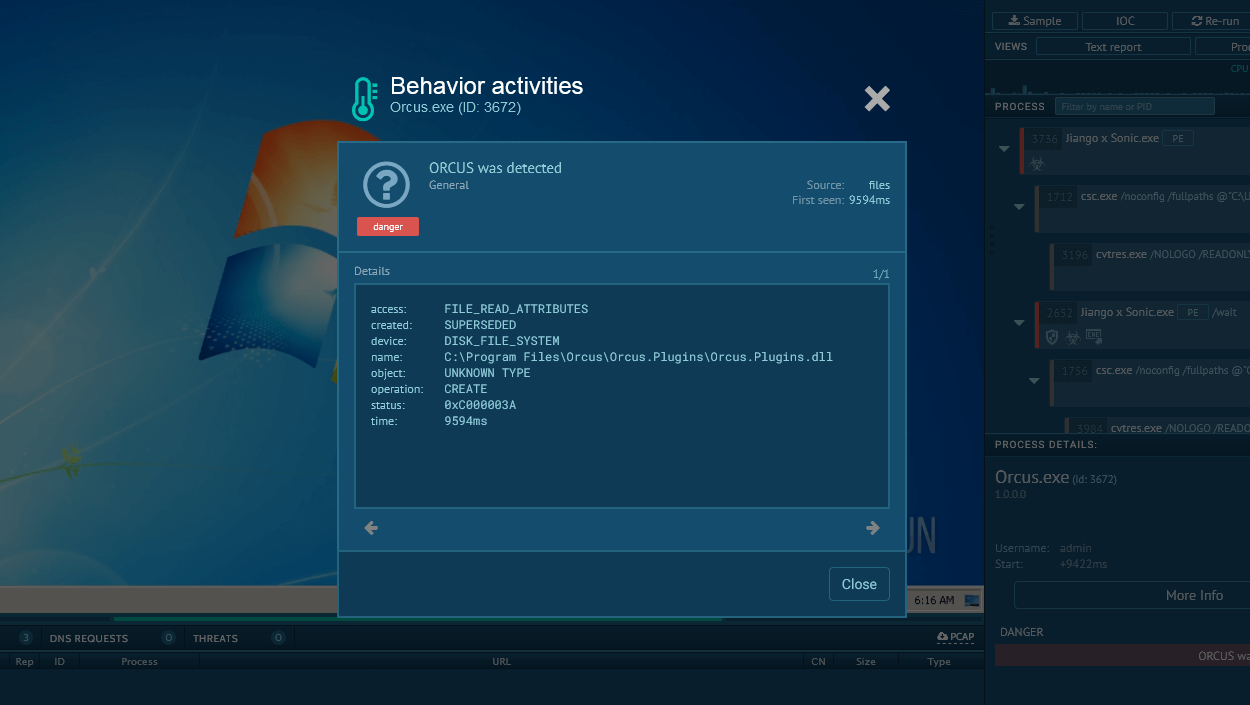
Extract IOCs from analysis sessions and come back to TI Lookup to research them, enrich them with context, and find associated indicators.
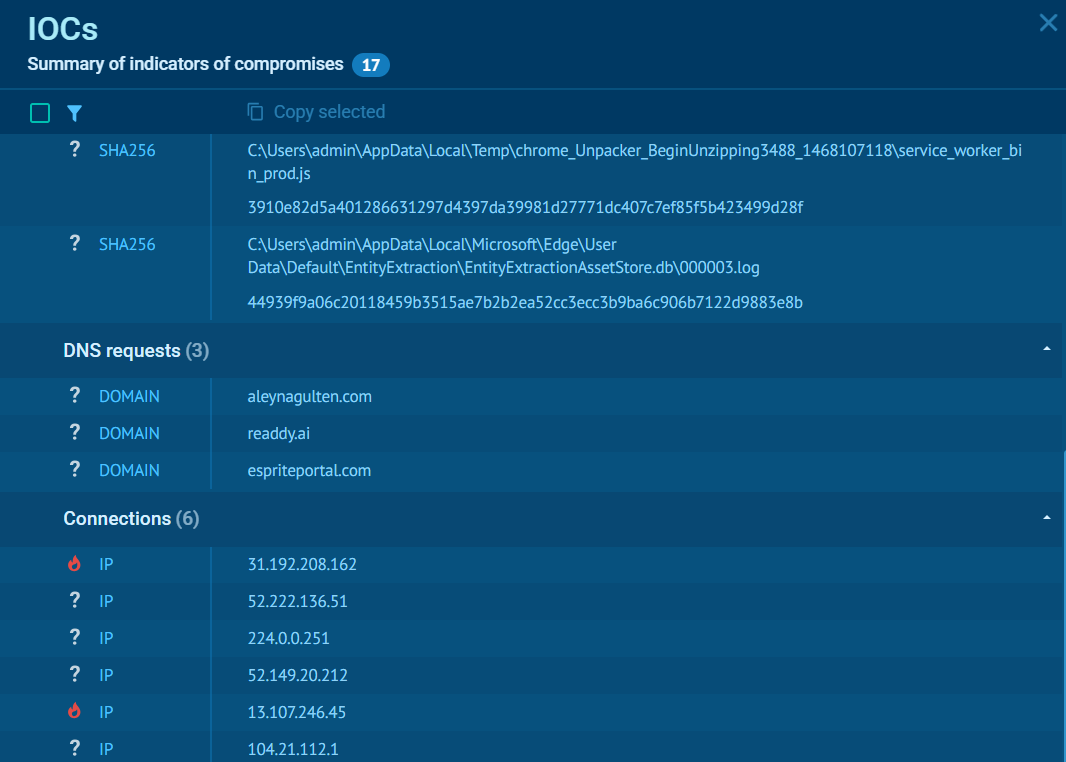 Sneaky 2FA IOCs from a sandbox analysis
Sneaky 2FA IOCs from a sandbox analysis
Sneaky 2FA illustrates the evolution of phishing attacks, demonstrating how cybercriminals continue to adapt their tactics to bypass increasingly sophisticated security measures. The threat's ability to circumvent two-factor authentication through adversary-in-the-middle techniques highlights the limitations of traditional security approaches and the need for more comprehensive protection strategies. The combination of technical controls, user education, and threat intelligence provides the best defense against this evolving threat landscape.
Gather actionable intelligence via ANY.RUN’s TI Lookup: start with 50 trial requests.