Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Prometei is a modular botnet malware family that silently infiltrates systems, hijacking their resources for illicit Monero (XMR) mining. Active since at least 2016, it combines stealth, persistence, and lateral movement capabilities. Notable for its global reach and opportunistic infection strategy, it is also used for credential theft.
|
Botnet
Type
:
|
Unknown
Origin
:
|
|
1 March, 2016
First seen
:
|
16 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 March, 2016
First seen
:
|
16 February, 2026
Last seen
:
|

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
The Prometei botnet represents one of the most persistent and evolving cryptocurrency mining threats in the cybersecurity landscape. There is evidence that it has been active since 2016, though it was described in 2020.
It is an advanced, multi-component malware system designed to mine cryptocurrency while staying under the radar. Written in multiple programming languages (including Delphi and PowerShell), it supports Windows and Linux platforms and is capable of self-propagation, data exfiltration, and command-and-control (C2) communications.
Its modular architecture allows attackers to dynamically deploy components like credential stealers, backdoors, and lateral movement tools based on the target environment. While its primary goal is cryptojacking, its deep penetration into systems makes it a gateway for broader cyber espionage or sabotage.
The botnet employs domain generation algorithms (DGA) for command and control communications, making it difficult to disrupt its operations through traditional domain blocking methods.
Recent analysis indicates that Prometei has experienced a significant resurgence since March 2025, with updated variants showing enhanced capabilities and more sophisticated anti-analysis features. The malware demonstrates continuous development, with threat actors regularly updating its modules and incorporating new exploitation techniques to maintain effectiveness against modern security measures.
Prometei’s victimology is opportunistic rather than highly targeted. It affects a wide range of industries, including finance, insurance, retail, manufacturing, utilities, travel, and construction.
It has been detected across the United States, the United Kingdom, Europe, South America, and East Asia. The botnet exploits unpatched systems, poorly configured servers, and devices with weak security, such as outdated Microsoft Exchange servers or IoT devices with default credentials.
Prometei has infected systems in over 90 countries, with particularly high concentrations observed in Brazil, Indonesia, and Turkey. Recent campaigns have shown over 10,000 systems compromised since November 2022.
Once installed on an endpoint device, Prometei can perform several malicious activities:
For businesses and organizations, Prometei presents multifaceted threats that extend far beyond cryptocurrency mining. The malware's ability to steal credentials and move laterally through networks means that a single infected system can potentially compromise an entire organizational infrastructure.
The cryptojacking component results in significant financial losses through increased electricity costs, reduced productivity due to system performance degradation, and potential hardware damage requiring replacement. More critically, the backdoor capabilities provide persistent access that can be leveraged for more damaging attacks, including data exfiltration, deployment of additional malware, or ransomware attacks.
The malware's credential harvesting capabilities can result in violations of data protection regulations.
Similar to other botnets like Mirai and Gafgyt Prometei infects systems through:
Once inside a system, it uses spreader modules to propagate across networks, scanning for additional vulnerable endpoints. Its worm-like capabilities enable rapid expansion within poorly secured environments.
Prometei operates through a modular framework, with each component handling specific tasks:
The botnet utilizes domain generation algorithms to maintain communication with command and control servers, generating new domains dynamically to evade detection and blocking efforts. This technique ensures that even if security teams identify and block known malicious domains, the botnet can continue operating through newly generated communication channels.
Prometei's self-updating capabilities allow it to download and install new modules or updates automatically, ensuring that infected systems remain current with the latest malware variants. This feature contributes to the botnet's longevity and helps it adapt to changing security landscapes and defensive measures.
ANY.RUN’s Interactive Sandbox has seen a variety of Prometei malware samples analyzed by its global community of 500,000 users. Let’s explore one to see how the botnet infiltrates the system.
 Prometei Botnet sample detonated in the Sandbox
Prometei Botnet sample detonated in the Sandbox
Prometei starts by making sure there is no older copy of itself on the machine. It searches the running processes for the names uplugplay and upnpsetup with the pgrep command. If it finds either name, it immediately stops those processes with killall5 and pidof. This step clears the way so only the newest version of the malware can run.
When the system is clean, Prometei creates a small file called /etc/CommId. Inside this file it writes a random twelve-character code; in the sample run the code was CPGP332GT4P7AH6F.
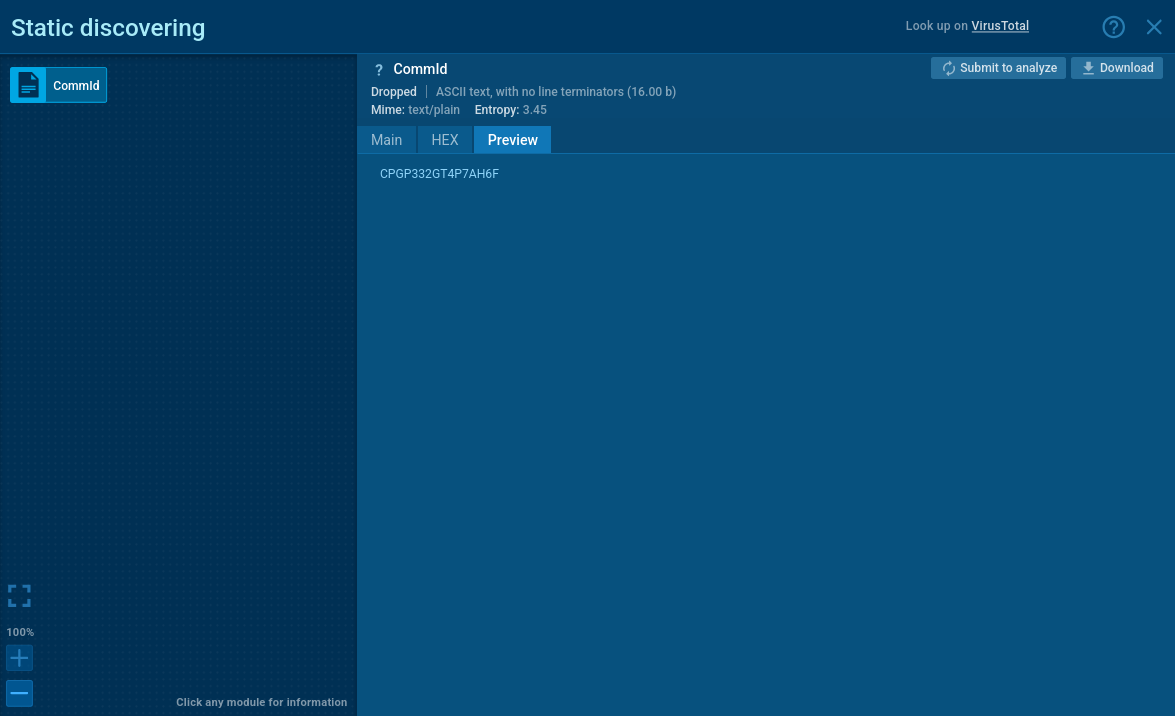 Prometei generates a code to identify the infected endpoint
Prometei generates a code to identify the infected endpoint
Right after that, the malware sends the code to its command-and-control server through an unencrypted HTTP request (http://152[.]36[.]128[.]18/cgi-bin/p.cgi?r=26&i=CPGP332GT4P7AH6F). The attackers use this code to recognize and track the infected computer.
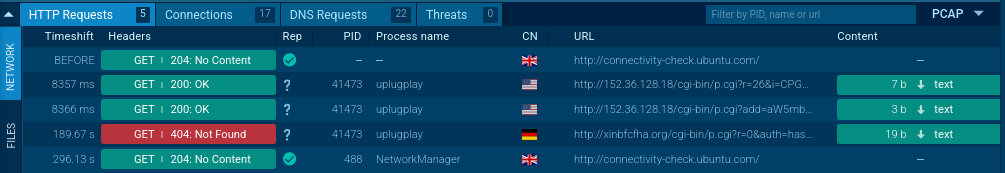 The code gets sent to C2C server
The code gets sent to C2C server
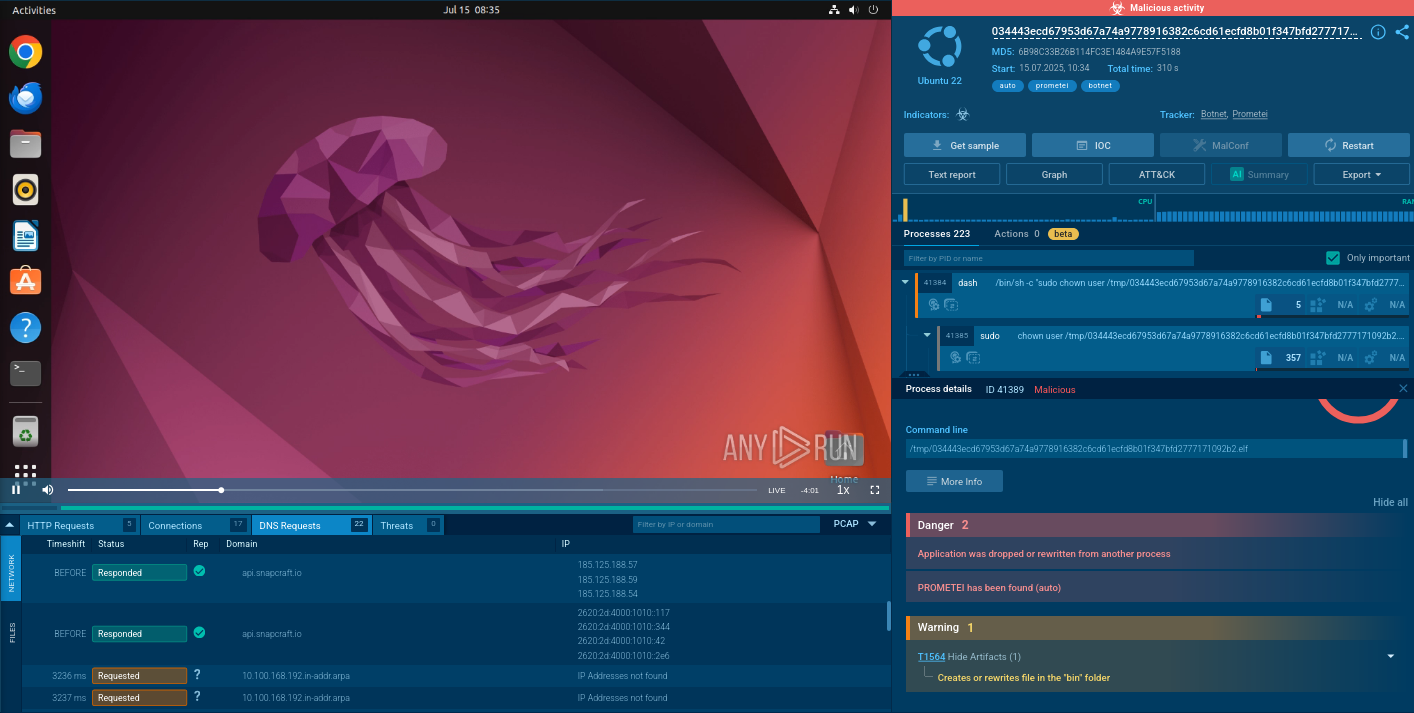
Next, the malware makes sure it will survive a reboot. It drops a new systemd service file called uplugplay.service in the folder /lib/systemd/system/. The service is listed under the friendly name UPlugPlay and is set to run the program /usr/sbin/uplugplay.
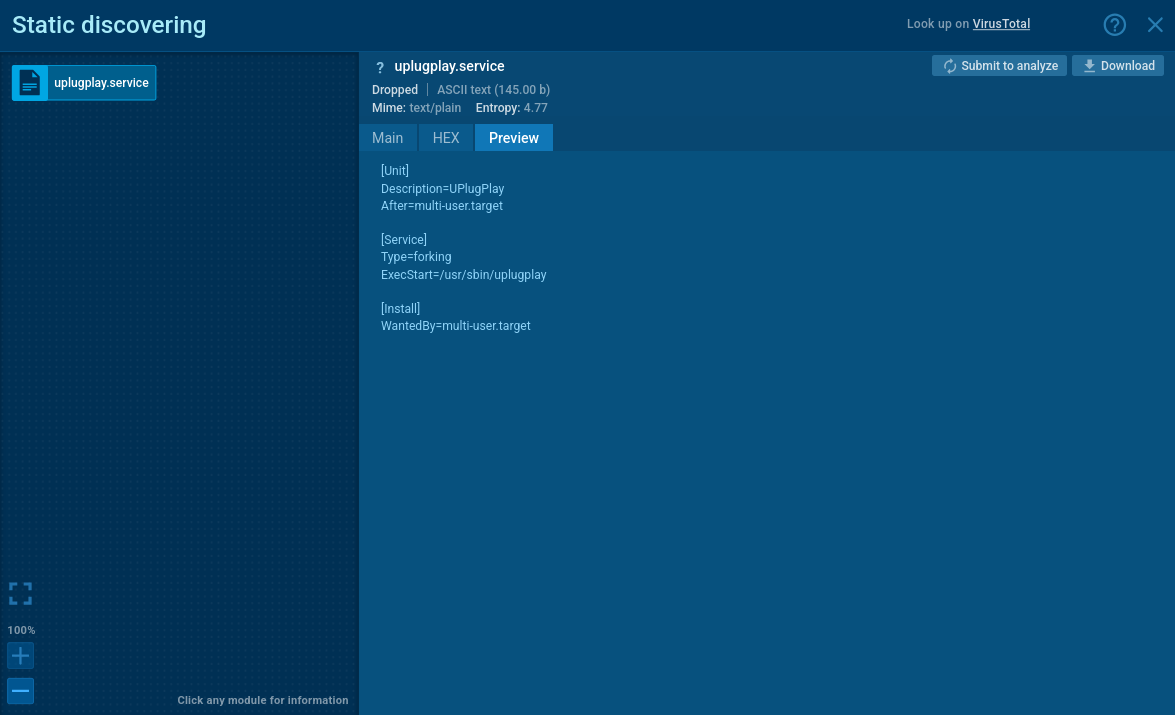 Part of Prometei persistence mechanism
Part of Prometei persistence mechanism
Prometei copies its own binary into that location, deletes the original dropper, and then runs two shell commands: systemctl enables uplugplay.service and systemctl starts uplugplay.service. These commands turn the service on right away and guarantee it will start automatically whenever the operating system boots.
After installation, the program becomes quiet. It checks whether it was launched with an extra parameter, so it can switch from the installer role to its normal botnet duties. The parameter it expects later is “Dcomsvc”, which would be used like this: /usr/sbin/uplugplay -Dcomsvc. Once everything is in place, Prometei waits in the background for more instructions from its command-and-control server, ready to carry out whatever tasks the attackers send next.
Threat intelligence plays a crucial role in defending against Prometei by providing actionable information about the malware's tactics, techniques, and procedures.
Behavioral intelligence describing Prometei's operational patterns helps security teams develop effective detection rules and monitoring strategies. Understanding the malware's lateral movement techniques and persistence mechanisms enables more comprehensive threat hunting activities.
Start gathering IOCs and behavioral data with the malware name search request to Threat Intelligence Lookup:
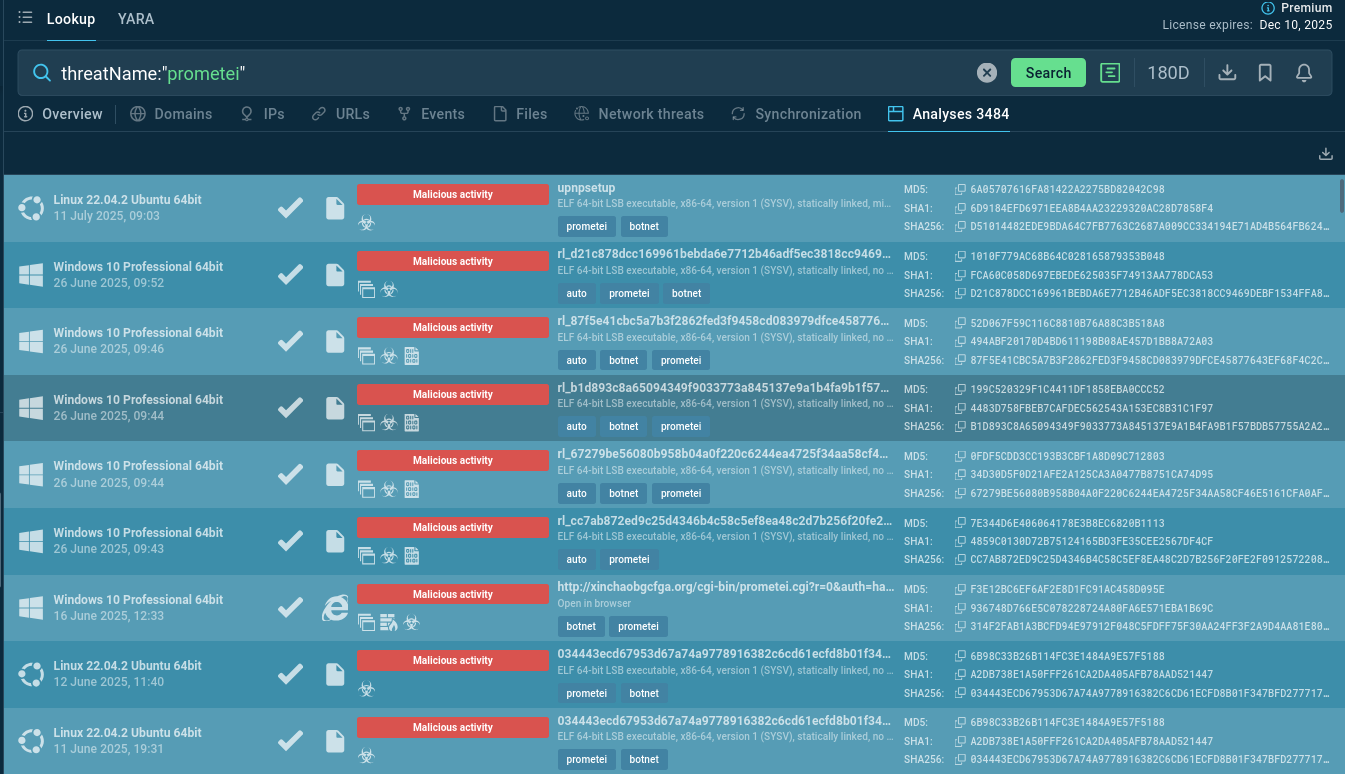 Prometei Botnet samples recently analyzed in ANY.RUN's Sandbox
Prometei Botnet samples recently analyzed in ANY.RUN's Sandbox
Prometei Botnet is more than just another cryptominer — it’s a modular, persistent, and evasive malware that undermines enterprise security while silently monetizing your infrastructure. With its stealth tactics, lateral movement, and built-in credential theft, it opens doors to deeper compromise. Preventing Prometei requires rigorous patching, strong authentication, and proactive threat intelligence. By understanding its tactics and staying informed with real-time threat data, organizations can turn the tide against this parasitic threat.
Gather fresh actionable threat intelligence via ANY.RUN’s TI Lookup: start with 50 trial requests.