Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Qilin ransomware (predecessor known as “Agenda”) is a rapidly evolving ransomware-as-a-service (RaaS) operation targeting organizations worldwide. Known for double extortion tactics (encrypting files while also threatening to leak stolen data) Qilin has quickly gained notoriety for its customization, flexibility, and impact on critical infrastructure.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
1 July, 2022
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 July, 2022
First seen
:
|
27 February, 2026
Last seen
:
|

 787
787
 0
0

 478
478
 0
0

 2728
2728
 0
0
Qilin operates as a Ransomware-as-a-Service (RaaS) platform, providing criminal affiliates with sophisticated tools and infrastructure to conduct ransomware attacks. Gained popularity by late 2023 and has since become increasingly sophisticated in its operations. Amassed over $50 million in ransom payments in 2024 alone. Ranked as the most prevalent ransomware in public threat intelligence reports by 2025.
Last year, cybersecurity company Halcyon discovered an improved version of the ransomware that it named Qilin.B. This newer variant demonstrates enhanced capabilities in terms of encryption speed, evasion techniques, and payload delivery mechanisms.
What sets Qilin apart from other ransomware families is its focus on operational efficiency and stealth. Once Qilin has gained initial access, it employs advanced obfuscation techniques to evade detection. The ransomware code is packed, disguising its true nature to avoid static analysis.
The group has also demonstrated remarkable adaptability, quickly capitalizing on disruptions to competing ransomware operations to expand their affiliate base and market presence.
Qilin is written in Rust and Go, enabling cross-platform attacks against both Windows and Linux environments. Qilin’s modular design allows attackers to customize payloads, set encryption methods, and configure ransom notes. The ransomware has a professionalized infrastructure, including a data leak site where stolen information is published if victims refuse to pay.
Qilin targets a diverse range of organizations across multiple sectors, with a particular focus on high-value targets that are likely to pay substantial ransoms. In June 2025, the United States remained the primary target of ransomware attacks, recording 235 victims, far surpassing other nations. Canada (24), the United Kingdom (24), Germany (15), and Israel (13) also experienced notable activity.
The threat actors behind Qilin demonstrate a clear preference for:
The targeting strategy appears to prioritize organizations in developed economies where cyber insurance coverage is common and ransom payment capabilities are higher. The geographical distribution reflects this focus, with North America and Europe representing the majority of victims.
One of Qilin’s features is the requirement to input a unique password, passed as a command-line argument when launching the executable file, which enhances its protection against analysis.
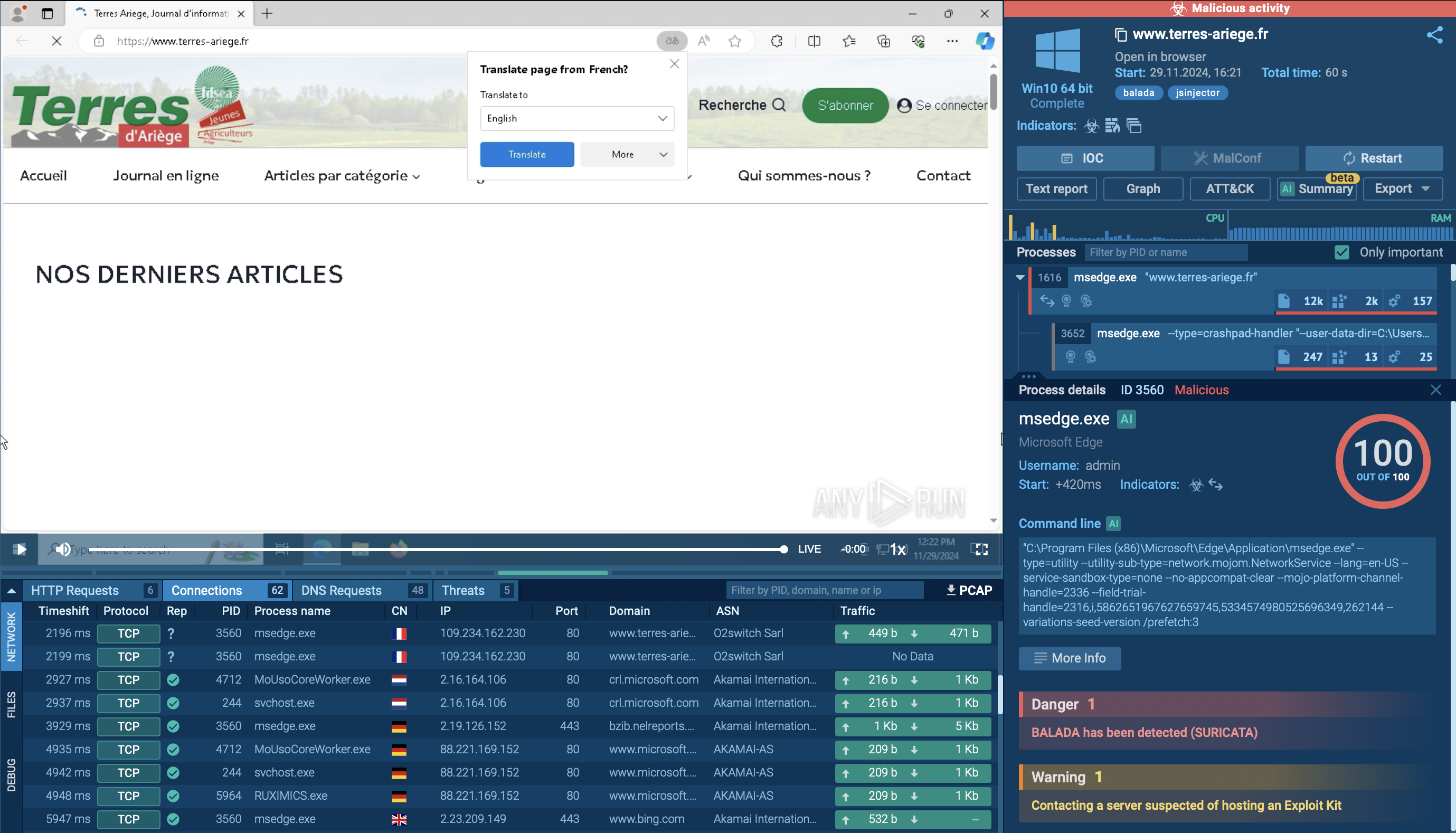
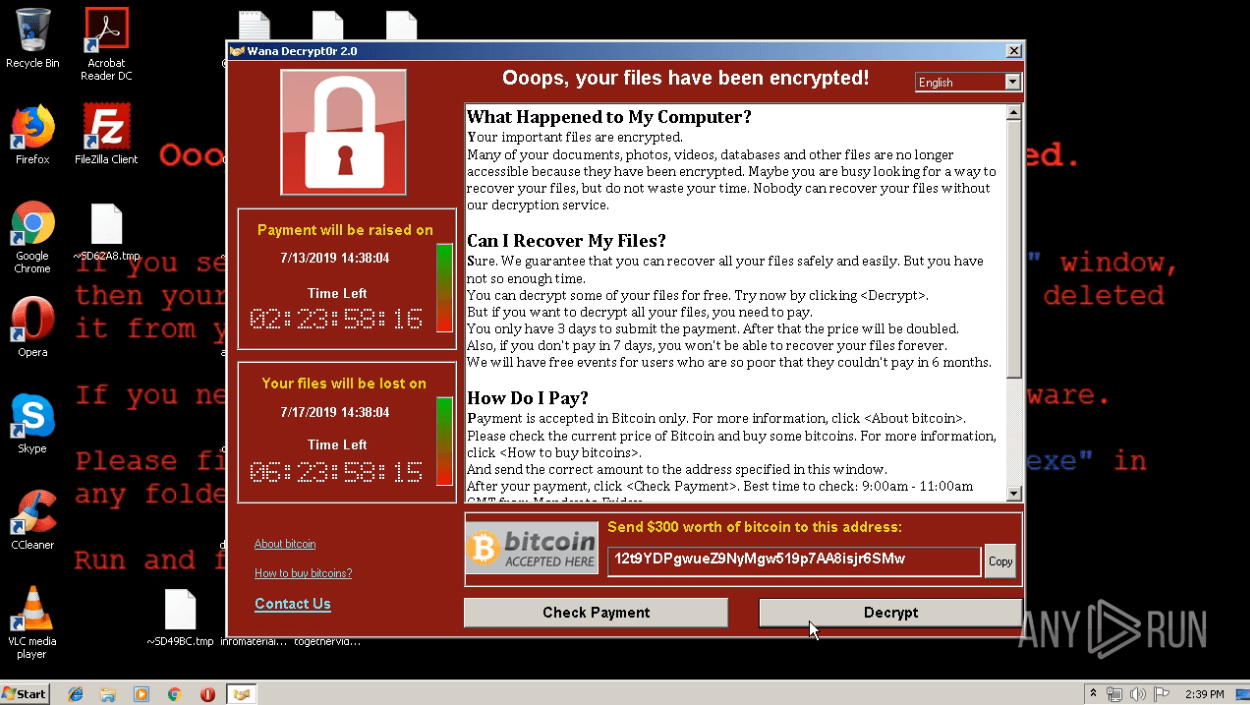
The community of about half a million users of ANY.RUN’s Interactive Sandbox has submitted and analyzed a number of Qilin’s samples featuring this password input. Let’s view an analysis with a correctly entered password.
View Qilin detonated in the Sandbox
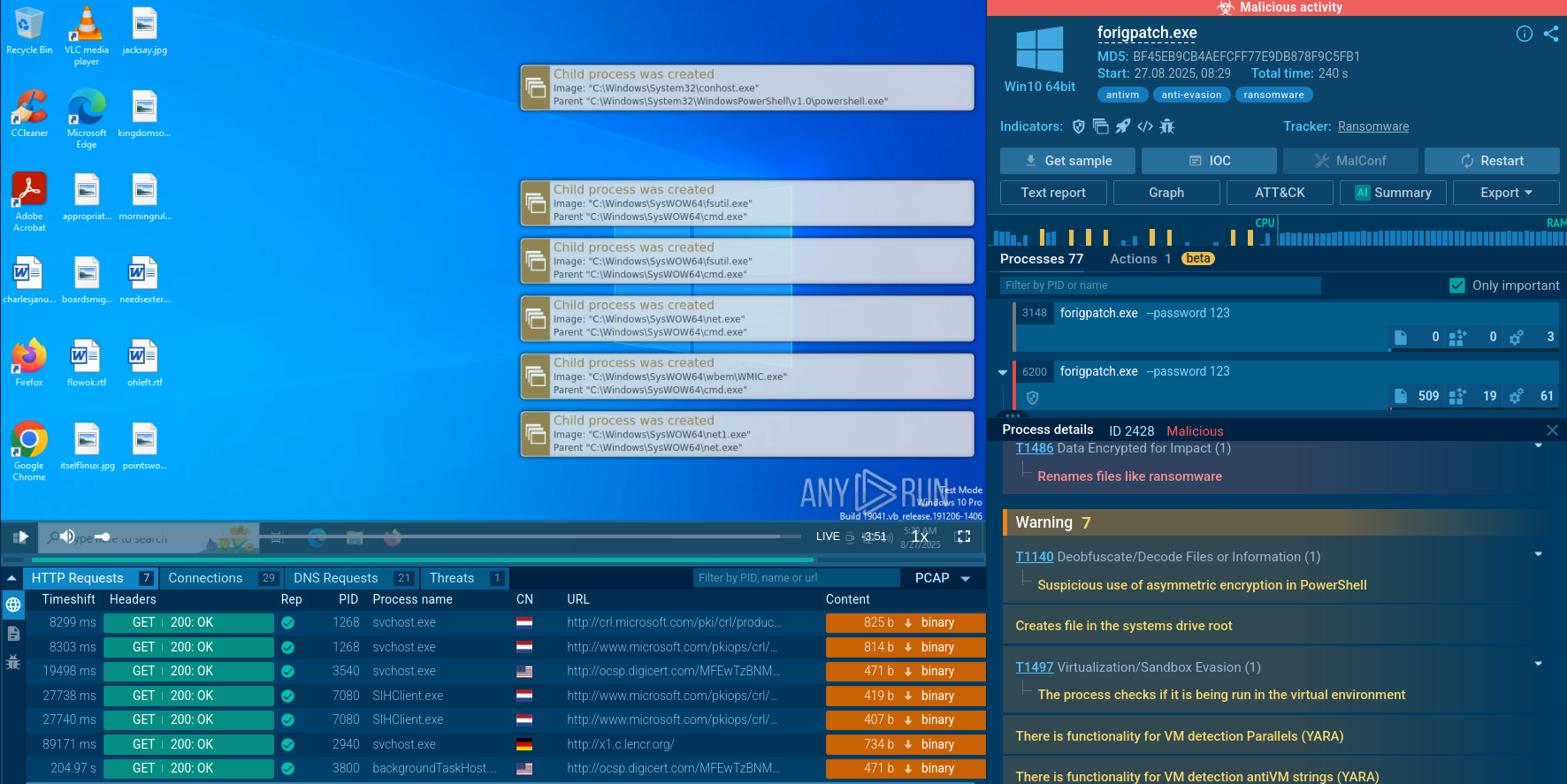 Qilin sample analysis in the Interactive Sandbox
Qilin sample analysis in the Interactive Sandbox
Qilin employs commands to manipulate symbolic links in Windows, altering the system's behavior regarding the handling of symbolic links. The commands used are:
fsutil behavior set SymlinkEvaluation R2R:1
fsutil behavior set SymlinkEvaluation R2L:1
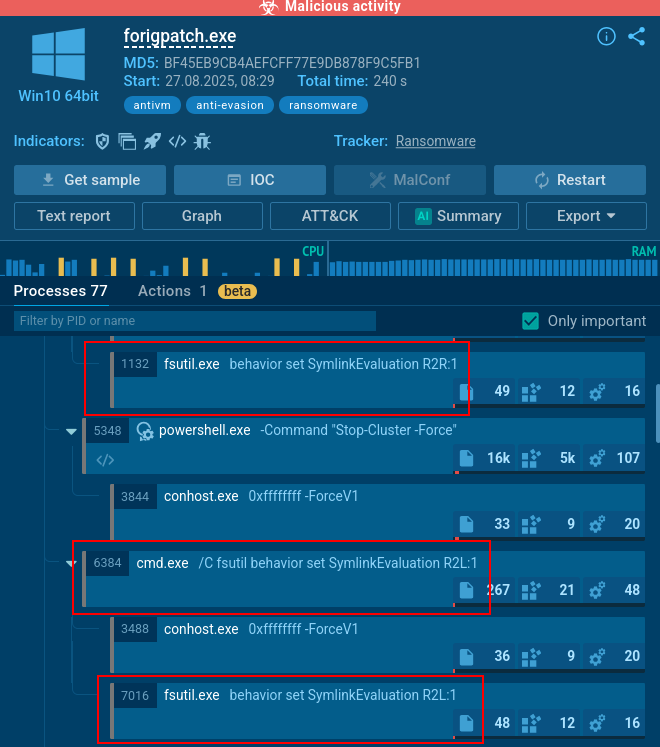 Qilin link commands in the process tree in the Interactive Sandbox
Qilin link commands in the process tree in the Interactive Sandbox
To conceal the traces of its activity, Qilin clears system logs, making it difficult to detect and analyze the attack, using a PowerShell script:
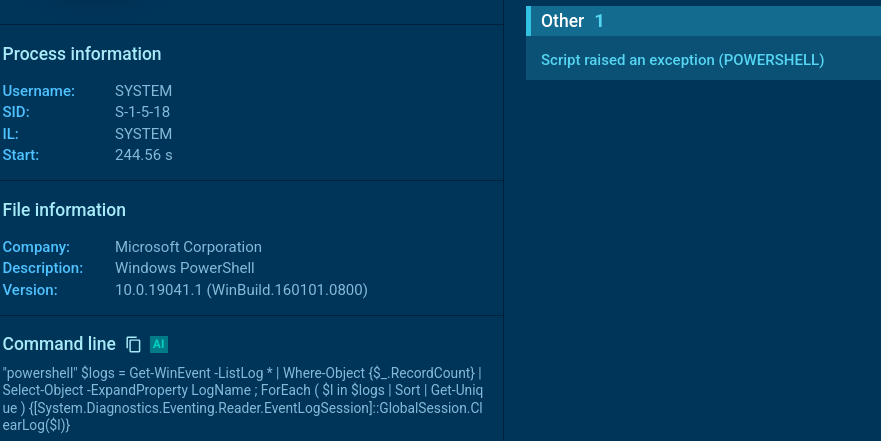 Qilin log wiping PowerShell script
Qilin log wiping PowerShell script
Subsequently, the malware destroys Volume Shadow Copies (VSS) to prevent data recovery without paying the ransom. To do this, the ransomware executes a sequence of commands that manipulate the Volume Shadow Copy Service and deletes all existing snapshots. The commands used are:
net start vss wmic service where name='vss' call ChangeStartMode Manual vssadmin.exe delete shadows /all /quiet net stop vss wmic service where name='vss' call ChangeStartMode Disabled
Qilin also uses commands to prevent failures in cluster services and to propagate through a domain environment via Active Directory (AD). These commands include:
Stop-Cluster -Force
Import-Module ActiveDirectory ; Get-ADComputer -Filter * | Select-Object -ExpandProperty DNSHostName
ServerManagerCmd.exe -i RSAT-AD-PowerShell ; Install-WindowsFeature RSAT-AD-PowerShell ; Add-WindowsCapability -Online -Name 'RSAT.ActiveDirectory.DS-LDS.Tools~0.0.1.0'
Qilin encrypts files, appending an extension composed of a unique set of random characters for each attack. This extension is also included in the name of the ransom note file left in the infected directories.
Qilin operates through a sophisticated technical architecture designed for maximum effectiveness and stealth. Adversaries operating the Qilin ransomware adopt a multi-pronged strategy to breach target networks, relying on both misconfigurations and software vulnerabilities.
Common Entry Points:
Lateral Movement Techniques:
Network Persistence:
Advanced Evasion Techniques:
Further, Qilin uses various code obfuscation methods, such as renaming functions, altering control flows, and encrypting strings, to complicate reverse engineering efforts. This also makes Qilin difficult to detect with IOCs located further along the killchain.
Anti-Analysis Mechanisms:
To further hinder analysis, Qilin integrates anti-analysis mechanisms designed to identify and disable debugging and sandbox environments. It actively scans for virtual machines and common sandbox artifacts to evade dynamic analysis, preventing security researchers from closely examining its behavior.
Encryption Implementation:
The ransomware implements robust encryption algorithms with the following characteristics:
Communication Infrastructure:
When Qilin successfully infiltrates a device, it implements a multi-stage attack process designed to maximize damage while evading detection:
Initial Compromise and Persistence:
System Manipulation:
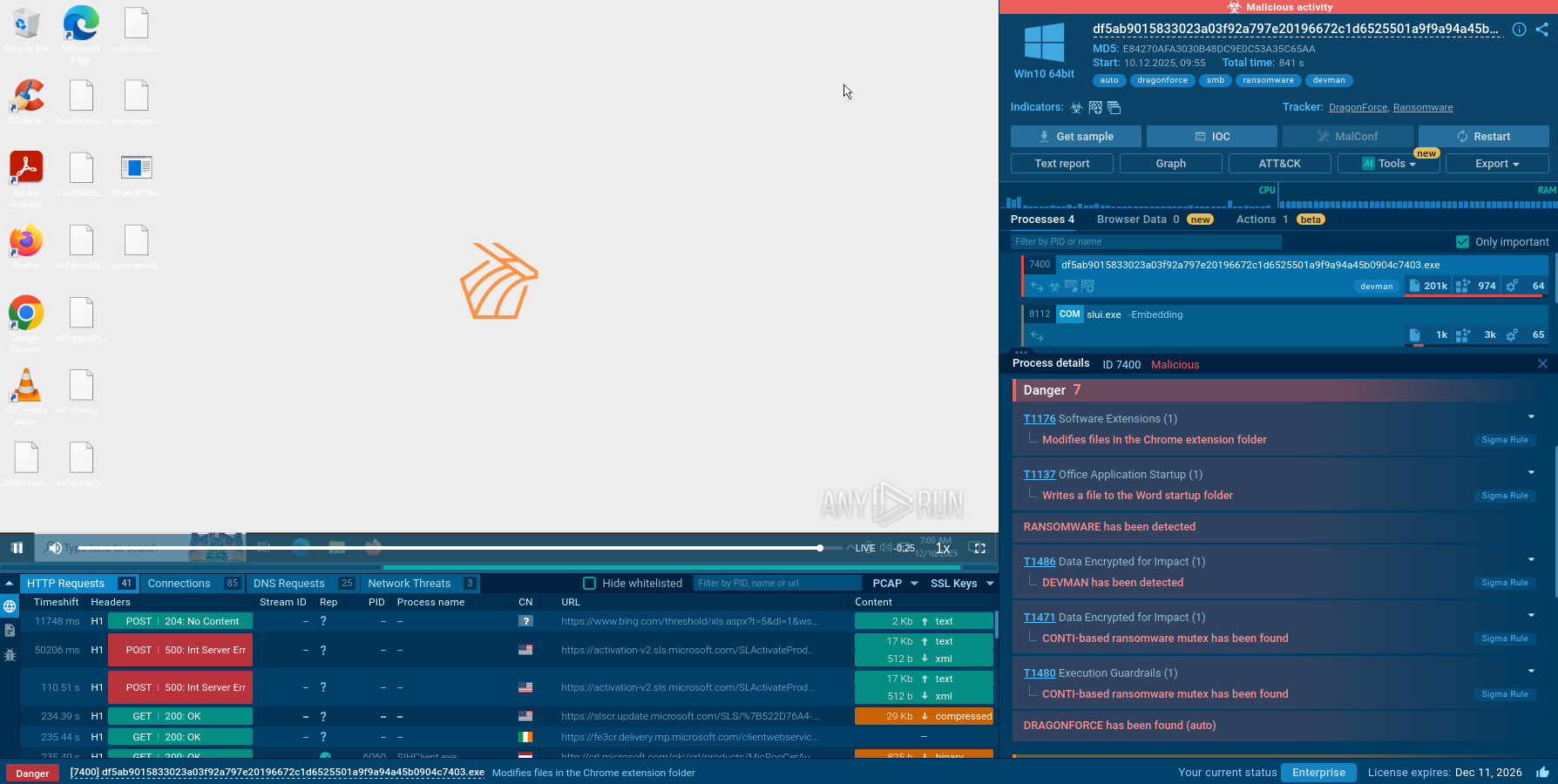
Using renamed binaries like upd.exe (a spoof of legitimate AV updaters), Qilin ransomware disables EDR, clears logs, and bypasses detection. The malware might even exploit outdated Carbon Black Cloud sensors to remain hidden.
Credential Harvesting:
Once elevated, Qilin dumps LSASS memory and extracts credentials to facilitate lateral movement across the network. This process allows the ransomware to escalate privileges and access additional systems.
Data Encryption Process:
System Degradation:
The scope of Qilin's operations has grown dramatically. investigated network artifacts related to Qilin and identified three probable cases of the ransomware across the Darktrace customer base between June 2022 and May 2024. However, by 2025, the frequency had increased exponentially, with the group claiming dozens of victims monthly.
A Qilin Ransomware Attack hit a U.S. financial advisory firm on July 1, 2025. The attackers allegedly exfiltrated approximately 340 GB of sensitive data, potentially including confidential financial records, client information, and internal communications. This incident underscores the persistent threat Qilin poses to financial services organizations.
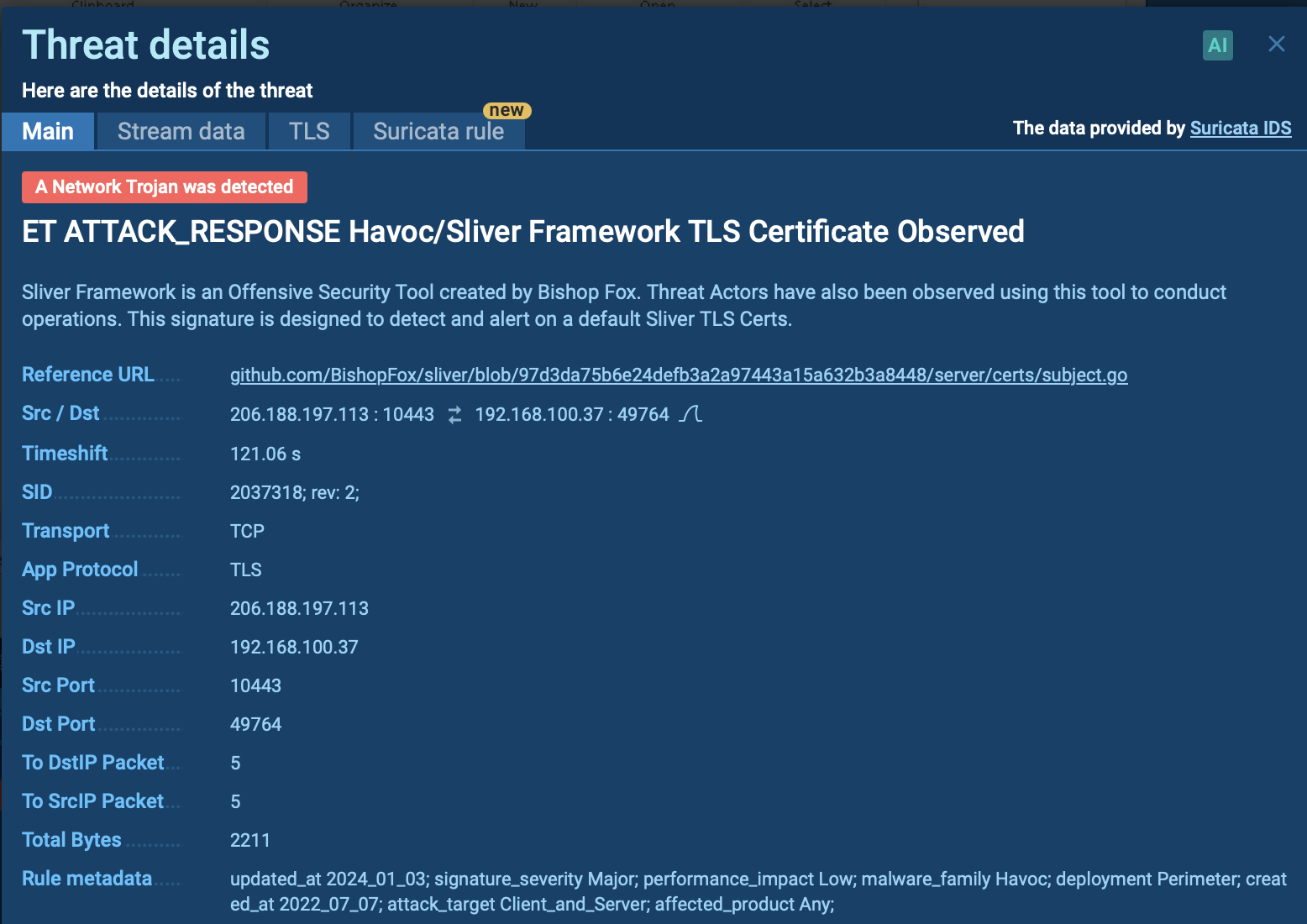
The Qilin ransomware group launched attacks exploiting Fortinet vulnerabilities CVE-2024-21762 and CVE-2024-55591 between May and June 2025. These attacks demonstrated Qilin's ability to target critical infrastructure through systematic exploitation of network security appliances.
Multiple healthcare organizations have fallen victim to Qilin attacks, resulting in cancelled surgeries, delayed medical procedures, and compromised patient care. These attacks highlight the life-threatening potential of ransomware when targeting critical infrastructure.
Several universities and school districts have been targeted, resulting in exposure of student records, research data, and administrative systems. These attacks often occur during critical periods such as registration or examination periods to maximize pressure for ransom payment.
Effectively countering such complex threats as Qilin is impossible without access to a large volume of detailed up-to-date threat Intelligence. It fuels:
Indicators of Compromise (IOCs) include:
Behavioral detection (via EDR/XDR) is critical: look for privilege escalation, mass file encryption, and registry tampering.
Start using Threat Intelligence Lookup for free: collect IOCs, browse sandbox detonations.
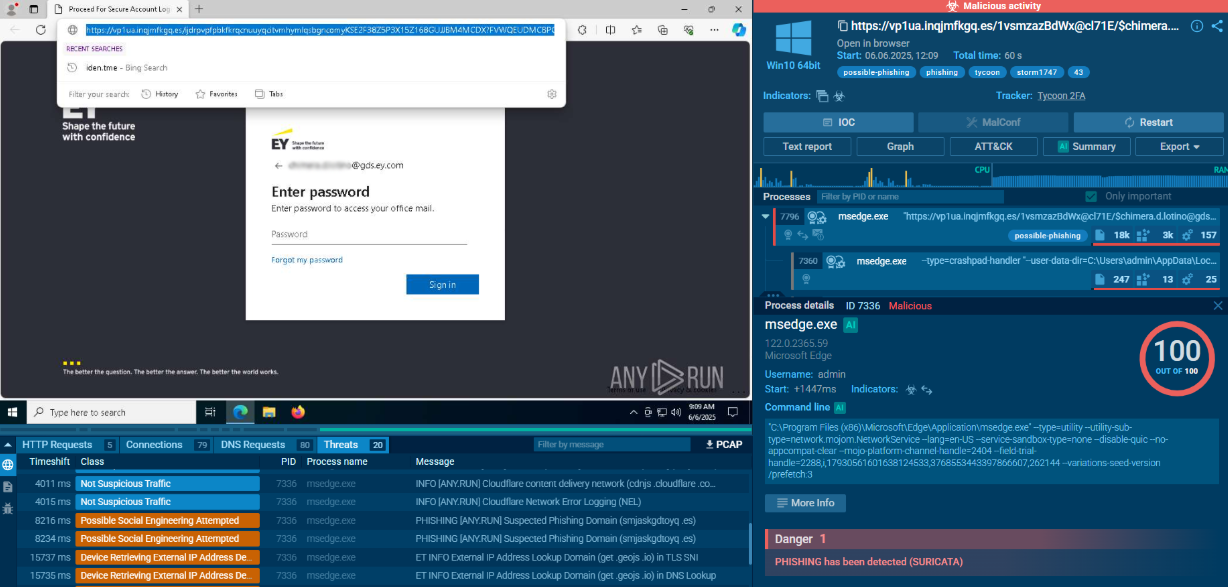
Start with a malware name search request to ANY.RUN’s Threat Intelligence Lookup and dive deeper into contextual data on Qilin. View public analyses of the malware’s fresh samples, extract the behavioral patterns, gather IOCs from each session.
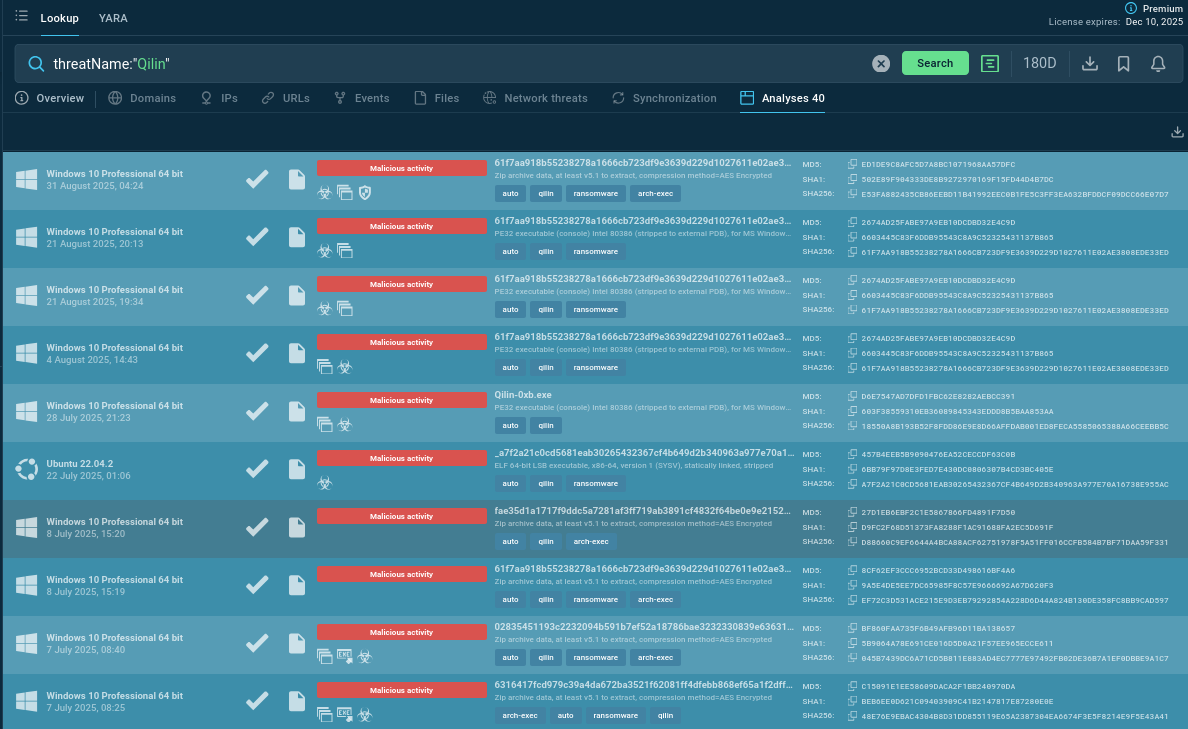 Qilin sample analyses found via Threat Intelligence Lookup
Qilin sample analyses found via Threat Intelligence Lookup
To find Qilin samples with the above-mentioned password submitting, use an additional search parameter:
threatName:"Qilin" and commandLine:"password"
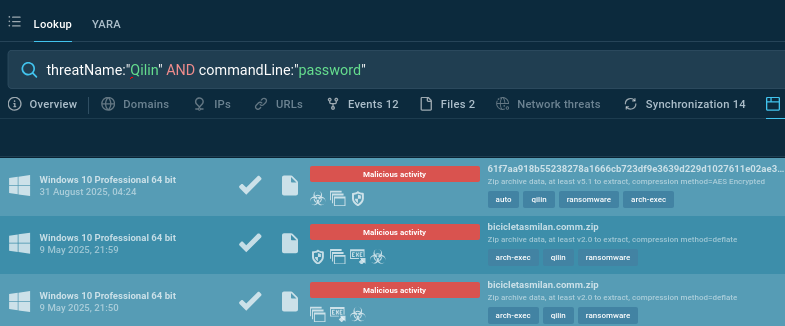 Qilin samples with password analyzed in the Sandbox
Qilin samples with password analyzed in the Sandbox
Qilin is now one of the most prominent ransomware threats globally. Its rapid rise, adoption by advanced threat actors, and the growing number of victims in late 2024 and early 2025 point to sustained activity well into the years ahead. The threat is likely to persist and potentially intensify, making preparation and prevention more critical than ever.
The ransomware family represents a significant evolution in cybercriminal sophistication, combining advanced technical capabilities with effective business operations to create a formidable threat.
Although Qilin follows a typical ransomware attack chain, its success lies in the effectiveness of its evasion strategies, allowing it to execute attacks with minimal detection until the final encryption phase.
The fight against Qilin ransomware is not just a technical challenge but also a strategic business imperative. Organizations that invest in comprehensive cybersecurity programs, maintain current threat intelligence, and prepare for incident response will be better positioned to resist this sophisticated threat and protect their critical assets and operations.
Sign up to use ANY.RUN’s TI Lookup for free: gather fresh actionable threat intelligence for quick detection and response.