Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases
Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security.

 799
799
 0
0

 484
484
 0
0

 2736
2736
 0
0
Adware, short for "advertising-supported software," is a type of malware designed to deliver intrusive advertisements to users, often without their consent. While some adware is legitimate and disclosed during software installation, malicious adware operates covertly, compromising user experience and system security.
Adware remains a persistent threat, with various campaigns targeting users globally. Some recent efforts have involved exploiting popular platforms, leveraging fake versions of legitimate software, and infiltrating users’ browsers through malicious extensions. These campaigns often disguise adware as utility applications or browser add-ons, making it difficult for users to detect their malicious intent.
Other tactics include using malvertising to redirect users to adware-laden websites or bundling adware with pirated content or freeware. These methods not only disrupt user experiences with intrusive ads but also create potential vulnerabilities for further exploitation. Keeping systems updated and practicing cautious browsing are essential to minimizing exposure to these evolving threats.
You can observe the behavior of adware and track all its executed processes in a safe and controlled environment using ANY.RUN’s secure sandbox.
For instance, here is a case where adware disguised itself as legitimate program to cause harm after its installation:
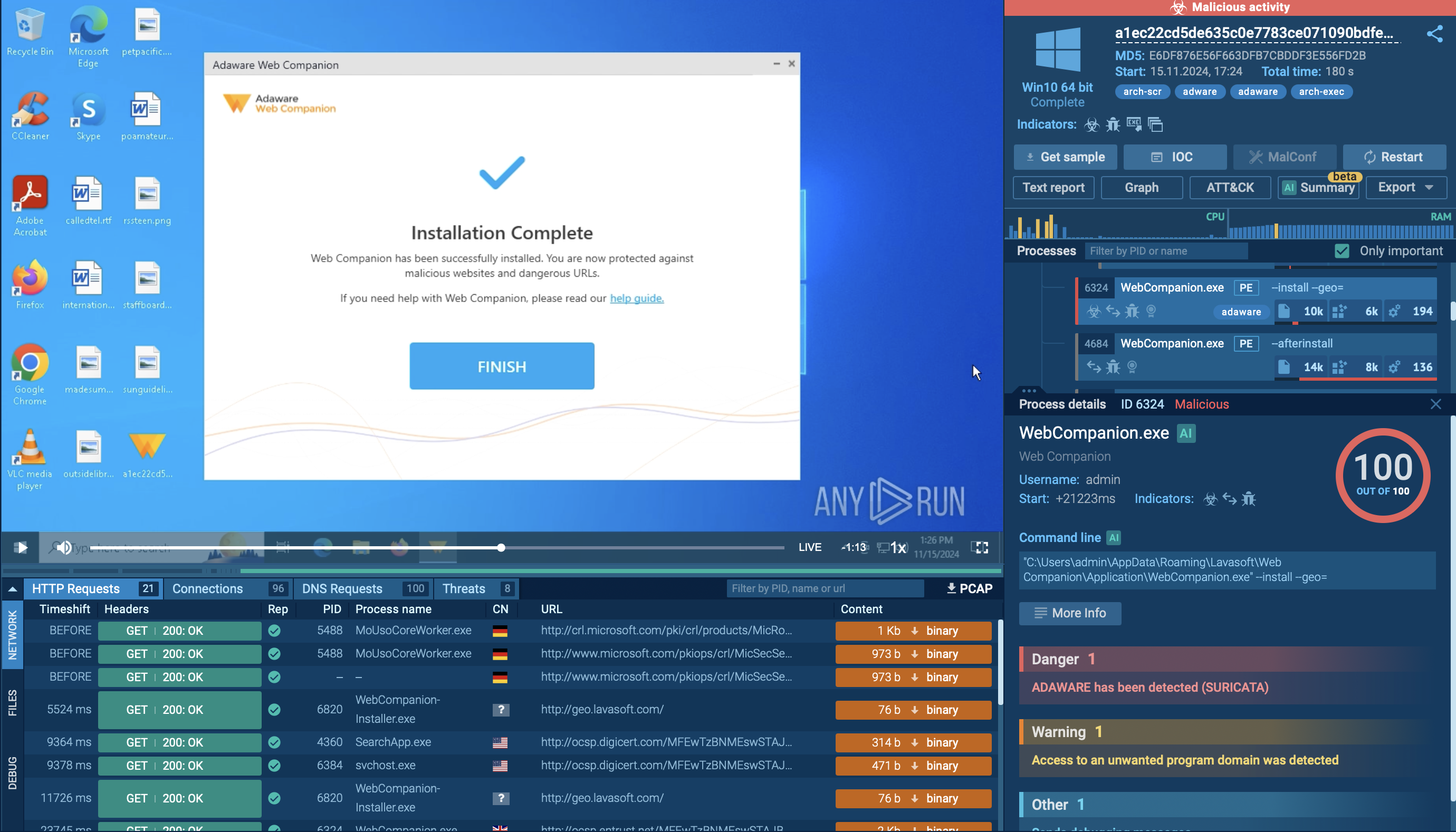 Adware detected inside ANY.RUN sandbox
Adware detected inside ANY.RUN sandbox
Browser hijackers: Browser hijackers alter critical browser settings, such as the homepage, default search engine, or new tab page, to redirect users to specific websites. These sites often generate revenue for adware operators through increased traffic or clicks. The hijackers can also inject advertisements into search results or legitimate web pages, making the ads appear as though they originate from trusted sources.
Pop-up adware: Pop-up adware bombards users with intrusive advertisements that appear in new browser windows or overlay active applications. These ads disrupt user activity and often redirect users to dubious websites. The excessive resource consumption of pop-up adware can degrade system performance, while some variants push deceptive alerts urging users to download fake updates or software.
Bundled adware: Bundled adware is distributed alongside legitimate software or through pirated content, often installed without the user’s awareness. During installation, users may overlook pre-selected options that authorize the adware's installation. Once installed, it can persist on the system, displaying ads and tracking user behavior even after the primary software is uninstalled.
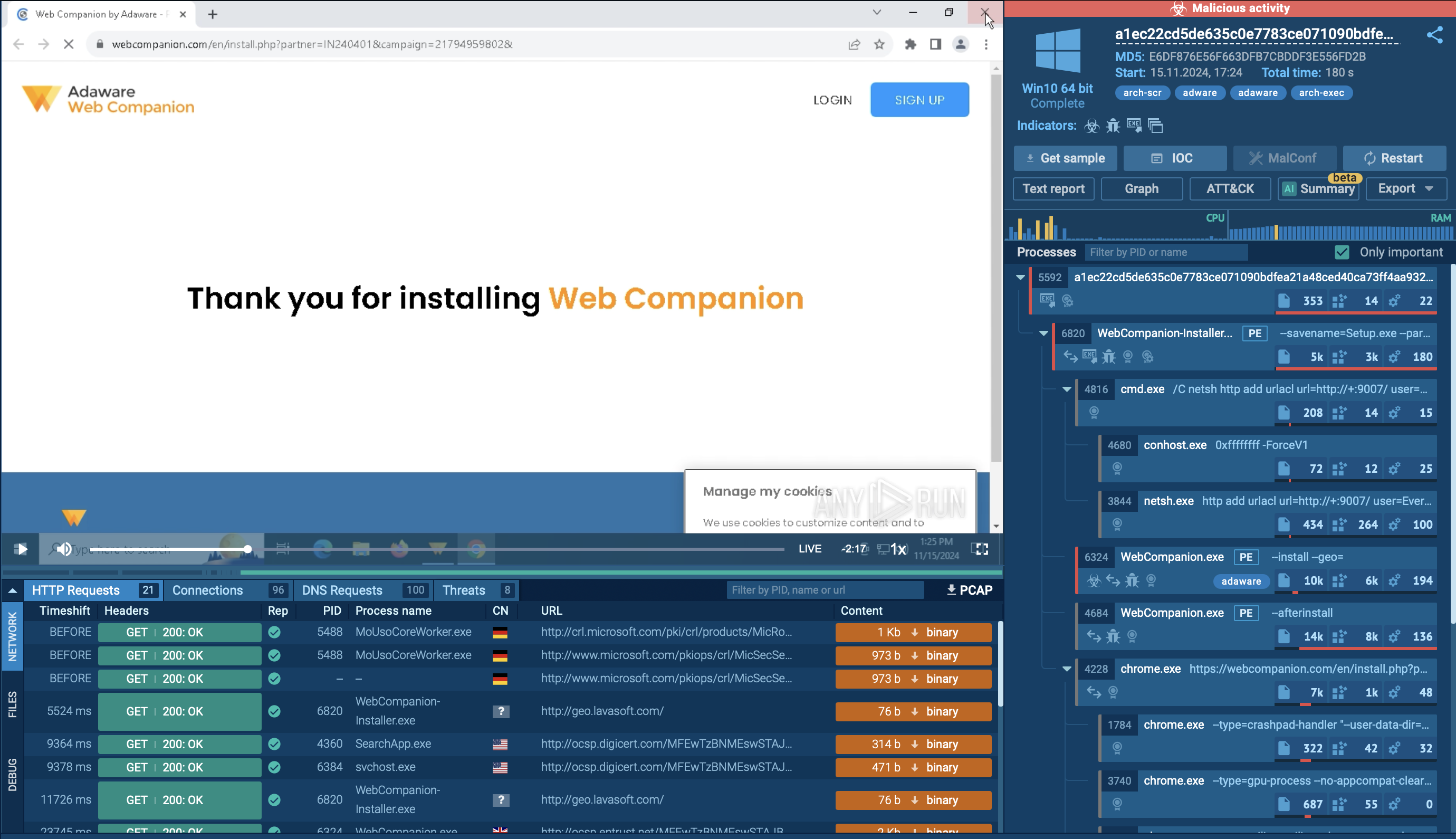 Bundled adware distributed via Adware Web Companion program
Bundled adware distributed via Adware Web Companion program
In-app adware: In-app adware is embedded within applications, especially free or pirated ones, and serves excessive ads in the app's interface. These ads may take the form of banners, video ads, or pop-ups that are difficult to close. In some cases, the adware manipulates app functionality to encourage users to click on malicious ads or links, potentially exposing them to further security risks.
Stealth adware: Stealth adware runs in the background, collecting user data such as browsing habits, search queries, and even sensitive information like login credentials. This type of adware is designed to remain hidden, making detection and removal challenging. It often delivers targeted ads based on the collected data and can also sell the information to third parties without user consent.
Malicious extensions: Malicious extensions masquerade as legitimate browser plugins but inject advertisements into web pages, replace links with affiliate content, or redirect users to specific sites. These extensions often gain elevated permissions, allowing them to access user data, manipulate browser behavior, and even track online activity without the user’s knowledge.
The primary functionalities and features of adware include:
To safely observe how adware operates, let's upload an adware sample to the ANY.RUN sandbox for analysis.
The execution chain of adware typically involves multiple stages that vary depending on the specific type and distribution methods. Adware is often bundled with legitimate software, particularly freeware or shareware.
Users may unknowingly install it by accepting the terms during installation without carefully reviewing them. Visiting compromised websites can also trigger automatic downloads of adware, exploiting web browser vulnerabilities and bypassing user consent.
Adware frequently disguises itself as legitimate applications to deceive users into installation.
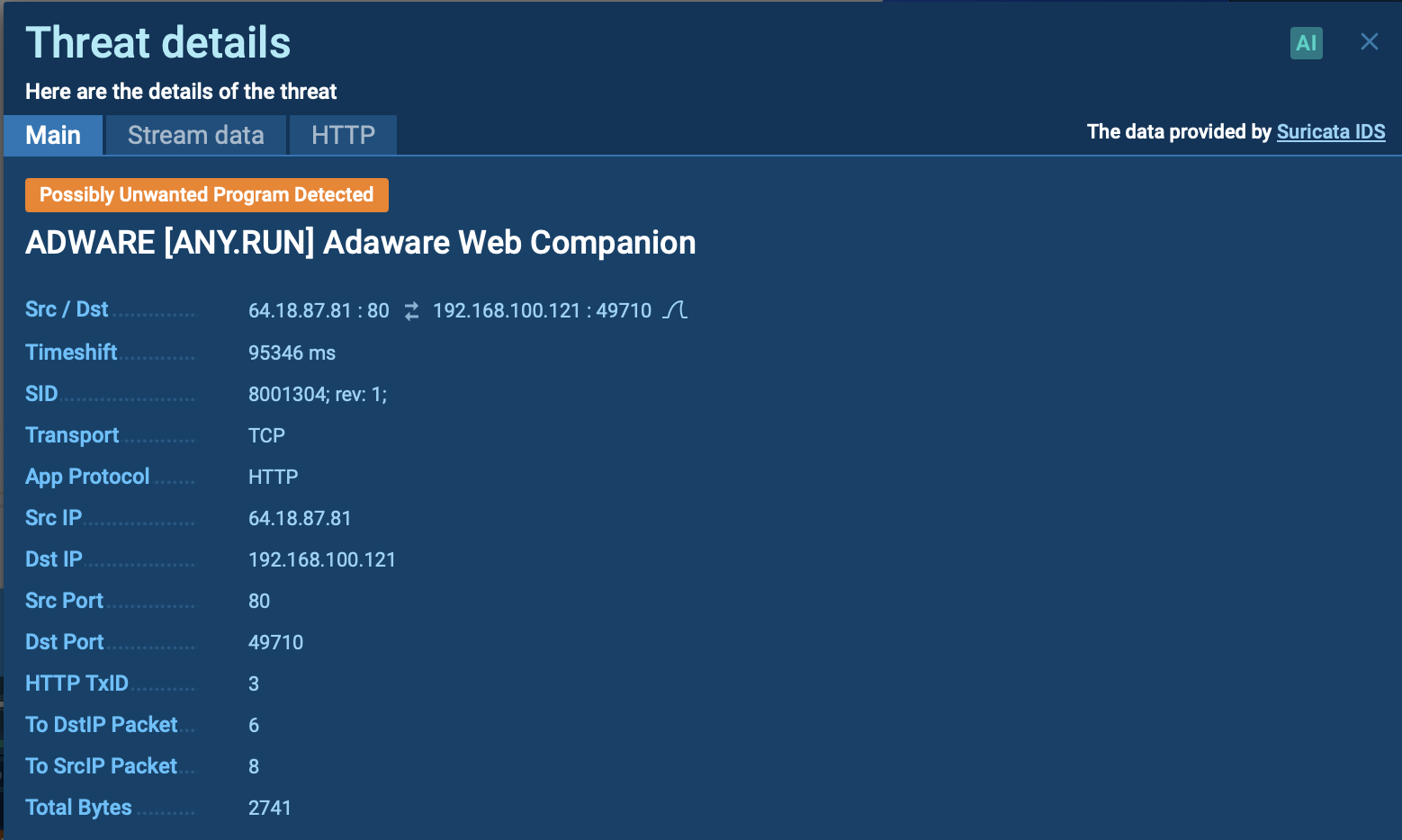 Suricata rule triggered by adware inside ANY.RUN sandbox
Suricata rule triggered by adware inside ANY.RUN sandbox
Once executed, it installs itself on the system and modifies settings to ensure it runs at startup, often by adding entries to the system registry or changing browser configurations. Once active, adware injects advertisements into web pages or generates pop-ups, redirecting users to unwanted sites and presenting misleading or dubious offers.
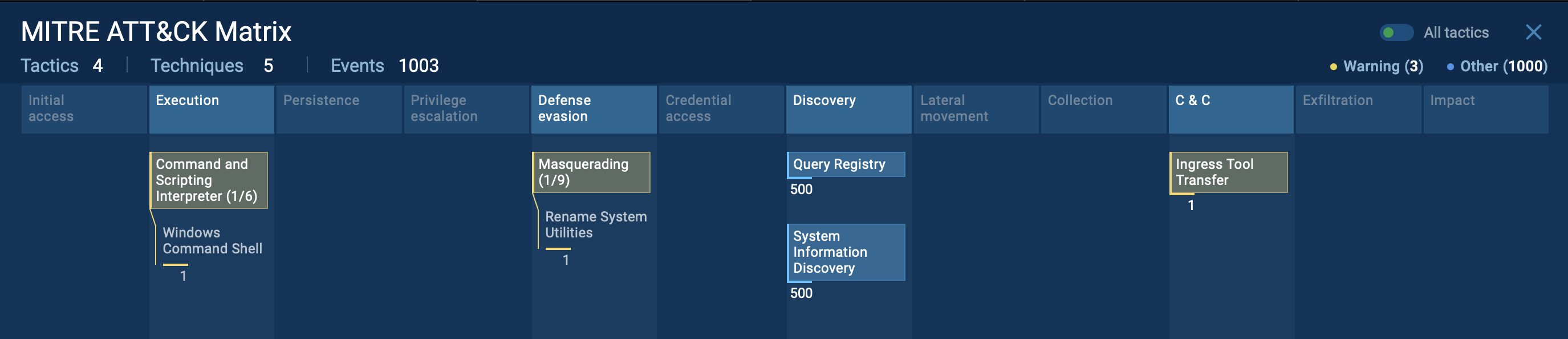 MITRE ATT&CK tactics and techniques revealed inside ANY.RUN sandbox
MITRE ATT&CK tactics and techniques revealed inside ANY.RUN sandbox
Adware commonly collects data on user browsing habits, such as visited sites and search queries, to tailor advertisements and potentially sell this information to third parties.
Advanced variants may establish connections with command-and-control (C2) servers to receive updates or instructions, enabling remote attackers to modify the adware's behavior or deploy additional payloads. In some cases, adware may capture sensitive information, including login credentials or financial data, and send it back to attackers. Adware can also act as a backdoor, allowing other, more harmful malware to be installed on the infected device.
Adware spreads through various deceptive methods, exploiting user trust and system vulnerabilities. These methods are designed to ensure widespread infection while remaining difficult to detect. Here are the primary ways adware is distributed:
To collect up-to-date intelligence on adware threats, use Threat Intelligence Lookup.
This powerful service provides access to an extensive database of insights gathered from millions of malware analysis sessions conducted in the ANY.RUN sandbox. With over 40 customizable search parameters, you can uncover valuable data on adware, including IPs, domains, file names, and process artifacts.
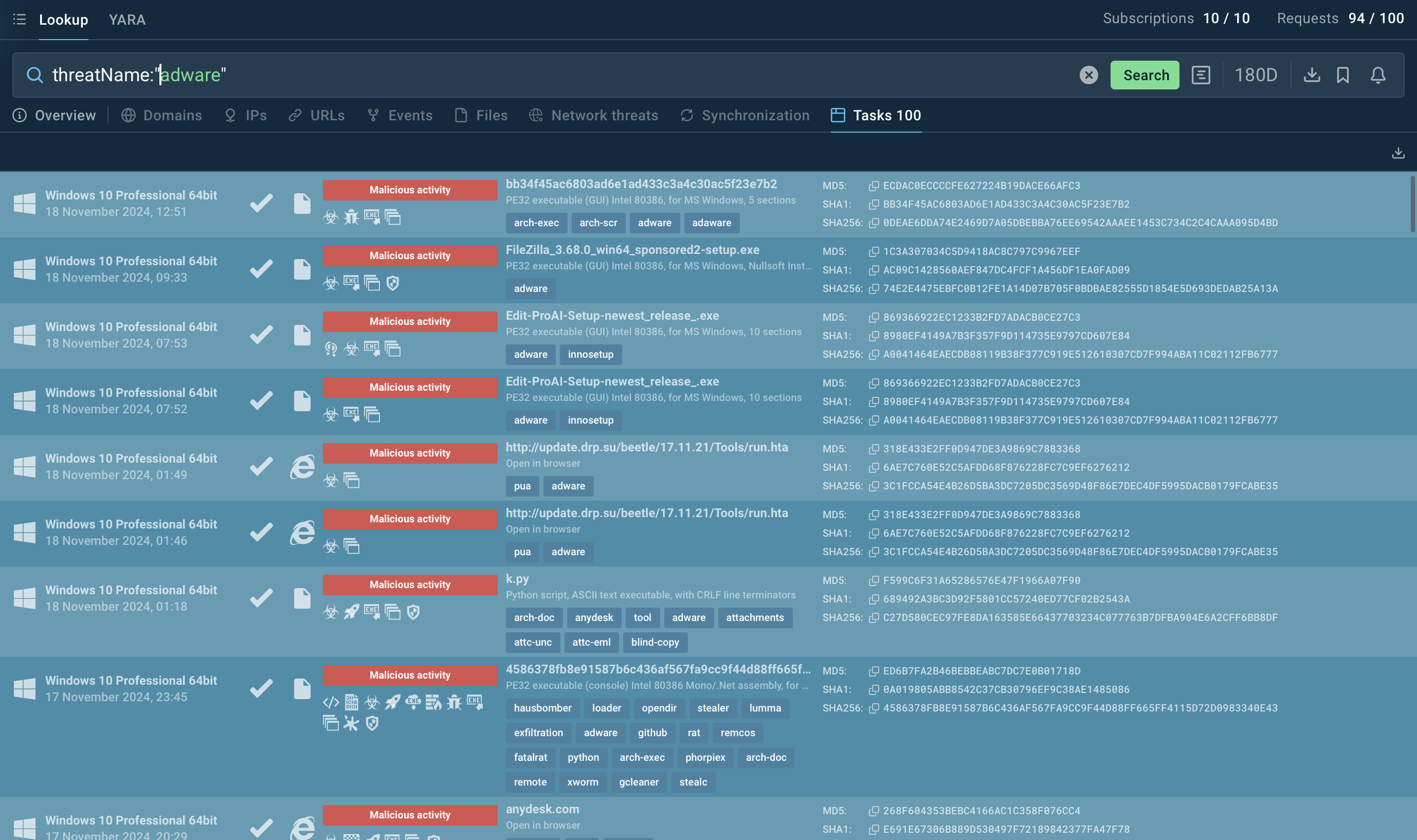 Search results for adware in Threat Intelligence Lookup
Search results for adware in Threat Intelligence Lookup
For instance, to analyze adware, you can search directly for its name or related artifacts. A query like threatName:"Adware" in Threat Intelligence Lookup will display all relevant samples and sandbox results, helping you better understand its behavior and impact.
Adware compromises privacy, weakens security, and disrupts device performance. To combat these risks, tools like ANY.RUN sandbox are essential for analyzing suspicious files and URLs in a safe and controlled environment.
ANY.RUN is a powerful malware analysis platform offering real-time insights, process visualization, and support for Windows and Linux systems. Its intuitive sandbox environment allows users to detect and understand threats with ease.
Sign up for a free ANY.RUN account today and take control of your malware analysis!