Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases

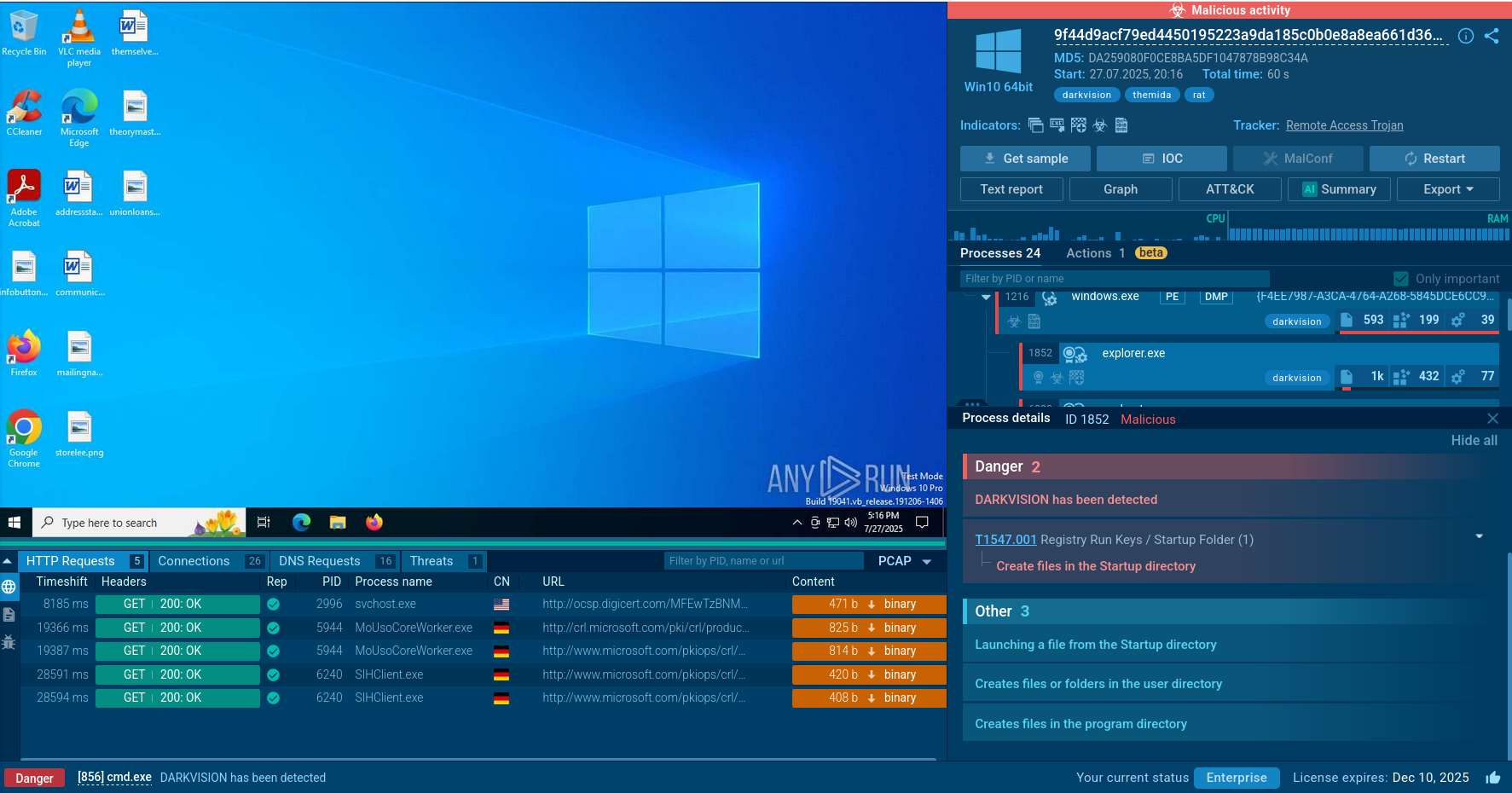
DragonForce is a ransomware strain operating under the Ransomware-as-a-Service (RaaS) model. First reported in December 2023, it encrypts files with ChaCha8, renames them with random strings, and appends “.dragonforce_encrypted.” By disabling backups, wiping recovery, and spreading across SMB shares, DragonForce maximizes damage and pressures victims into multimillion-dollar ransom negotiations. It has targeted manufacturing, construction, IT, healthcare, and retail sectors worldwide, making it a severe threat to modern enterprises.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
1 December, 2023
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 December, 2023
First seen
:
|
27 February, 2026
Last seen
:
|

 828
828
 0
0

 495
495
 0
0

 2760
2760
 0
0
DragonForce is a ransomware strain operating under the Ransomware-as-a-Service (RaaS) model. First observed in December 2023, it encrypts victim files and demands ransom for decryption keys. DragonForce quickly locks both local and network data while simultaneously disabling recovery options, maximizing pressure on the victim.
Its victims span industries such as manufacturing, construction, IT, healthcare, and retail; sectors where encryption of critical data can halt business operations entirely. Ransom demands vary from hundreds of thousands to millions of dollars, determined by the attackers after assessing the victim’s size and revenue. DragonForce operators also employ double extortion, stealing sensitive data before encryption and threatening to leak it if the ransom is not paid.
DragonForce does not strike randomly, it chooses victims where disruption brings maximum leverage.
There are numerous DragonForce ransomware samples detonated in ANY.RUN’s Interactive Sandbox and analyzed by SOC teams worldwide. Let’s walk through how a typical infection unfolds.
View analysis session with DragonForce
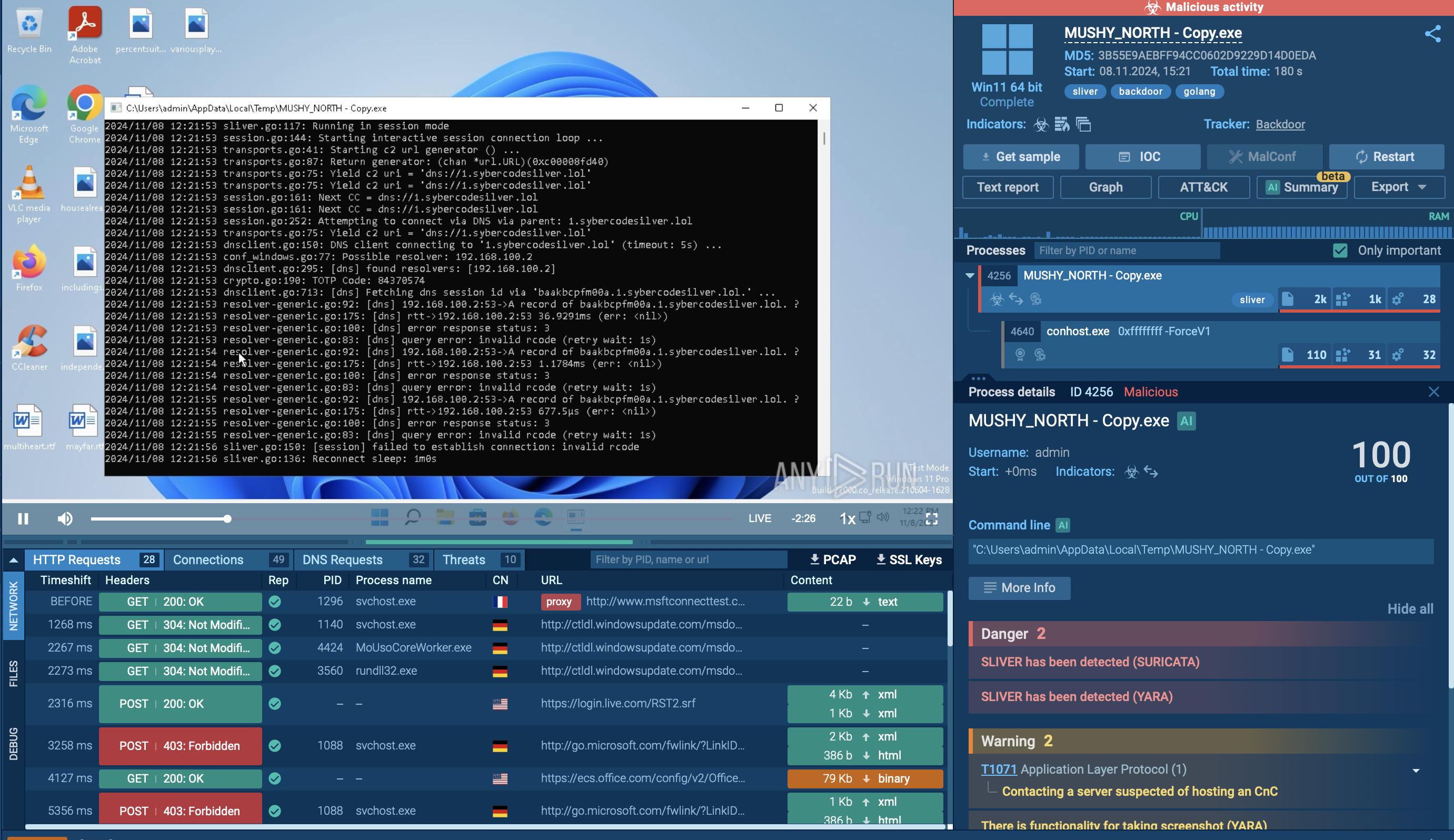
 DragonForce analyzed inside ANY.RUN sandbox
DragonForce analyzed inside ANY.RUN sandbox
Once launched, DragonForce first checks the environment for virtual machines and debuggers to avoid analysis. It then creates a unique mutex to prevent reinfection and copies itself into the system directory. Persistence is established by registering for autorun and creating scheduled tasks that ensure execution on reboot.
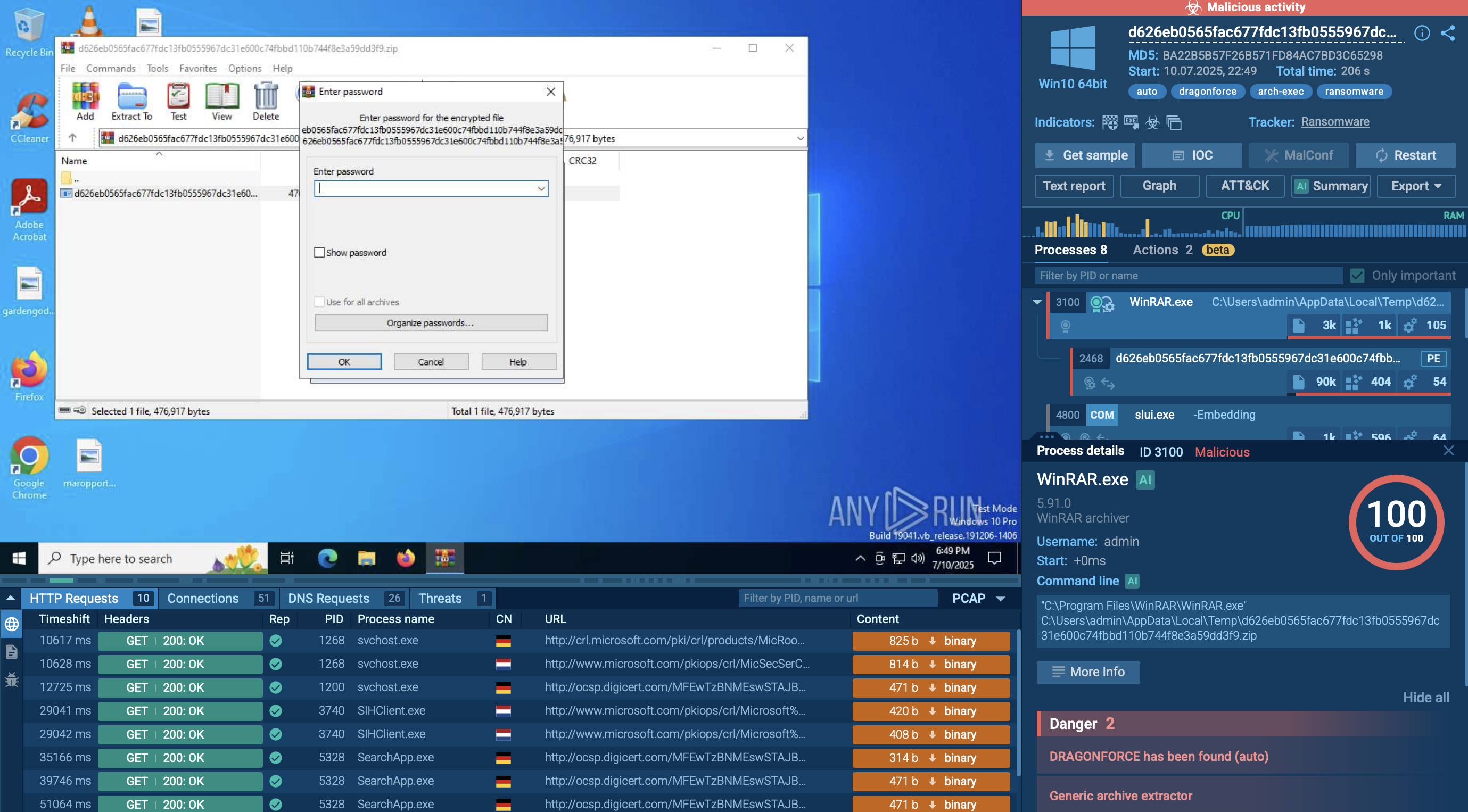
Next, the ransomware escalates privileges by bypassing UAC and modifying PowerShell settings (ExecutionPolicy Bypass) so its scripts can run without restriction. During the preparation phase, DragonForce deletes shadow copies (vssadmin), removes system backups (wbadmin), disables the Windows Recovery Environment (reagentc), and alters boot configuration (bcdedit) to prevent recovery.
In parallel, it uses taskkill.exe, sc.exe, and net.exe to terminate processes and services that could interfere with encryption, including antivirus tools, SQL databases, and mail servers.
 DragonForce renames files with the extension “.dragonforce_encrypted”
DragonForce renames files with the extension “.dragonforce_encrypted”
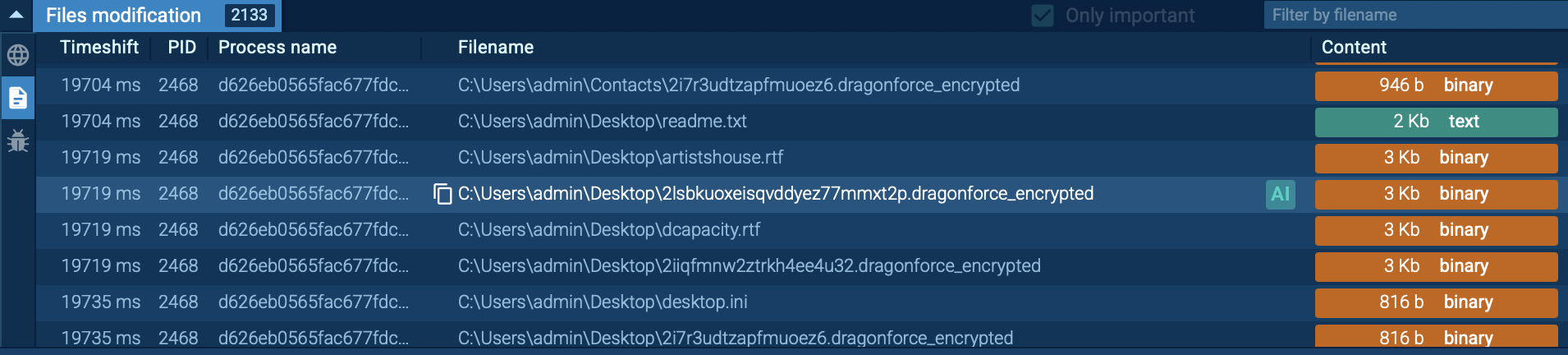
Finally, DragonForce scans local disks, network folders, and NAS devices for files to encrypt. All discovered data is locked with the “.dragonforce_encrypted” extension, and ransom notes (readme.txt) are left in every affected directory with payment instructions.
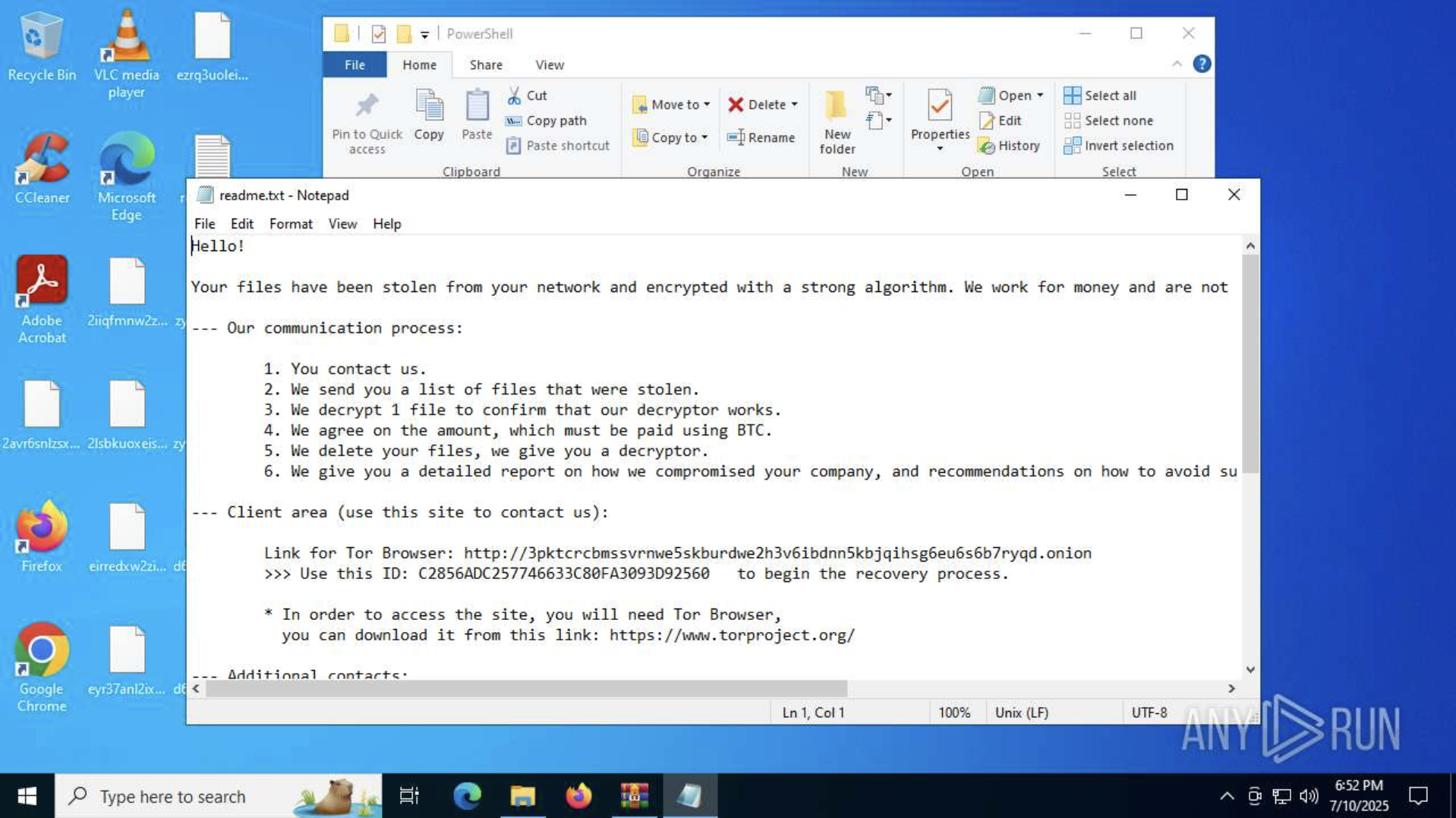 ANY.RUN sandbox reveals the ransom note left with payment instructions
ANY.RUN sandbox reveals the ransom note left with payment instructions
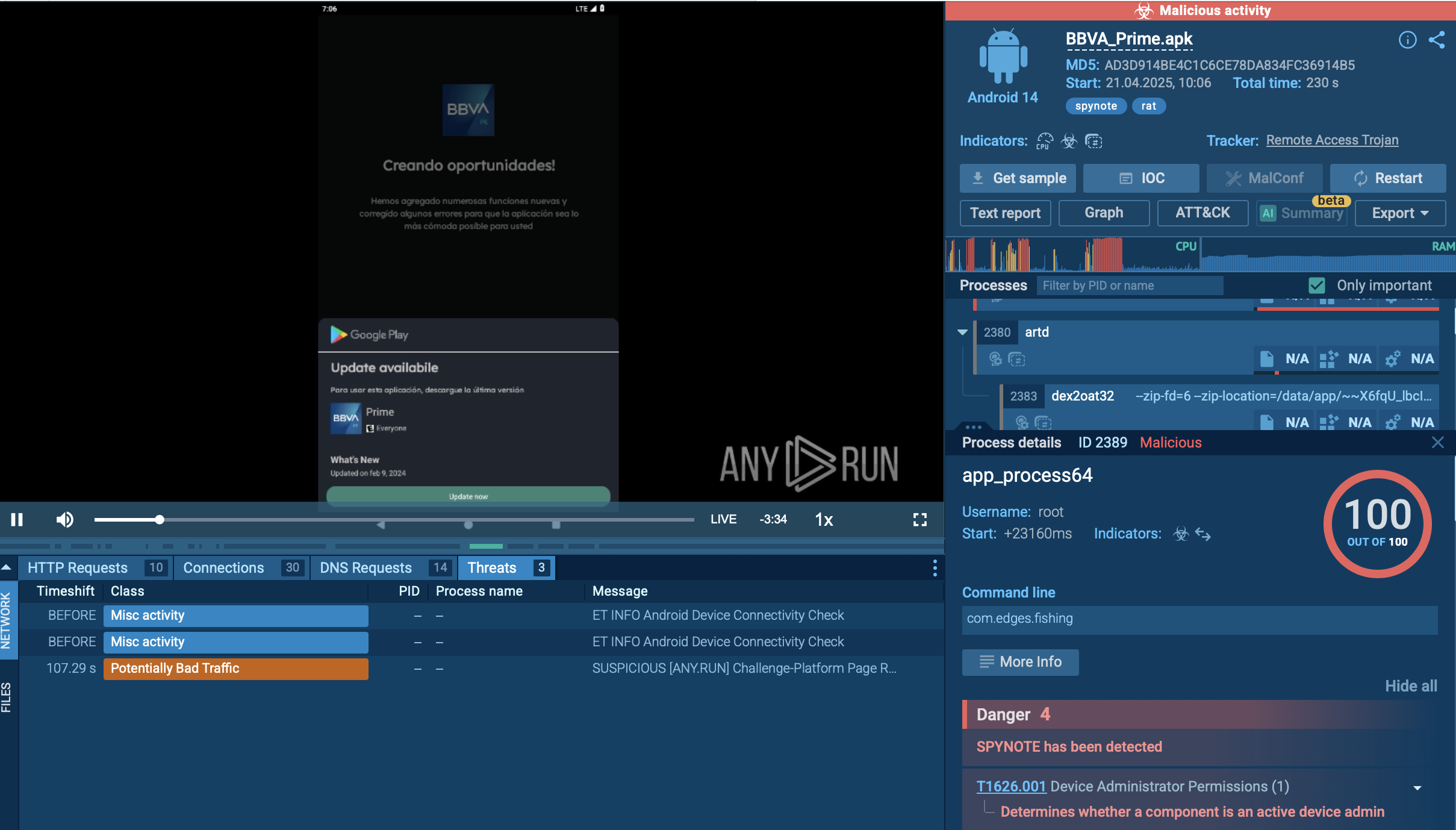
DragonForce primarily targets Windows environments (Windows 10/11 and server editions), with support for 64-bit systems and domain-based network resources. Variants have also been observed for Linux and VMware ESXi, signaling the group’s intent to disrupt entire enterprise infrastructures.
The malware executes with the privileges of the current user but actively attempts to escalate to administrative rights. It bypasses User Account Control (UAC), disables protections, and ensures uninterrupted execution even in environments with weak or misconfigured defenses.
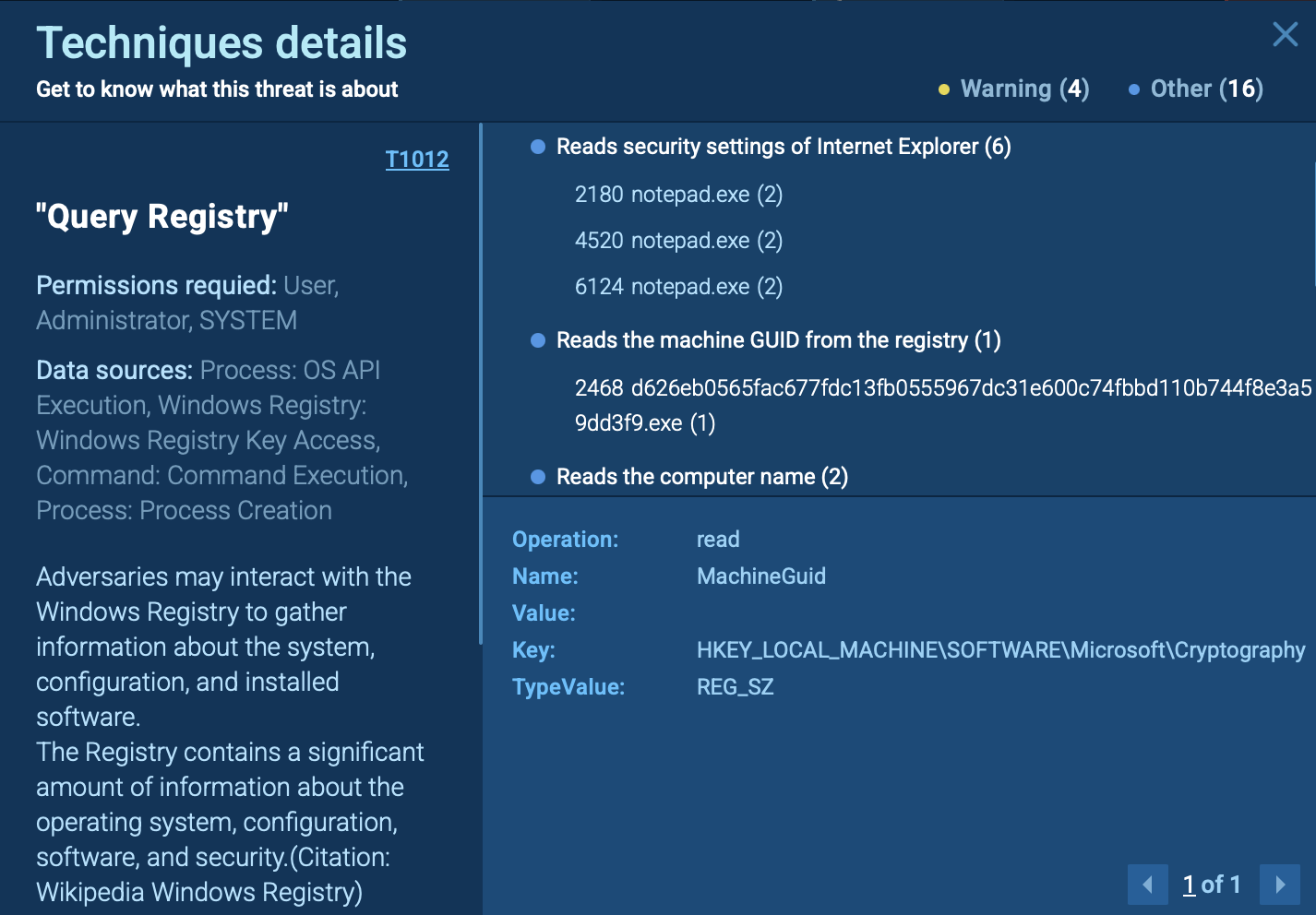 DragonForce gathers key system identifiers, such as computer name and Machine GUID
DragonForce gathers key system identifiers, such as computer name and Machine GUID
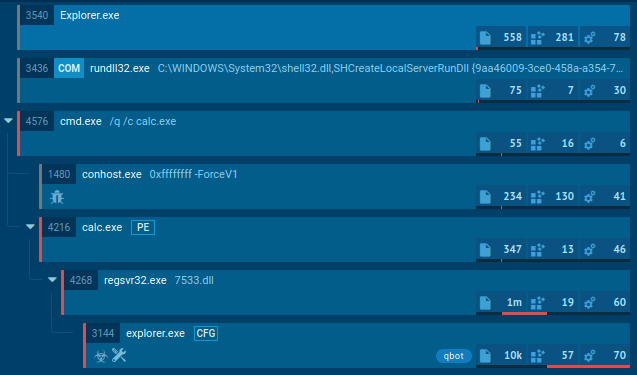
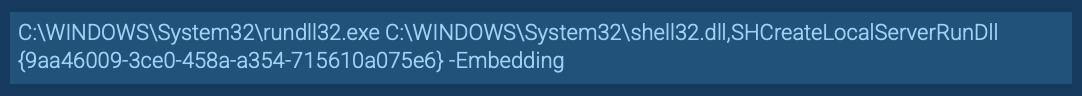 Rundll32.exe used to load a COM object and perform a UAC bypass
Rundll32.exe used to load a COM object and perform a UAC bypass
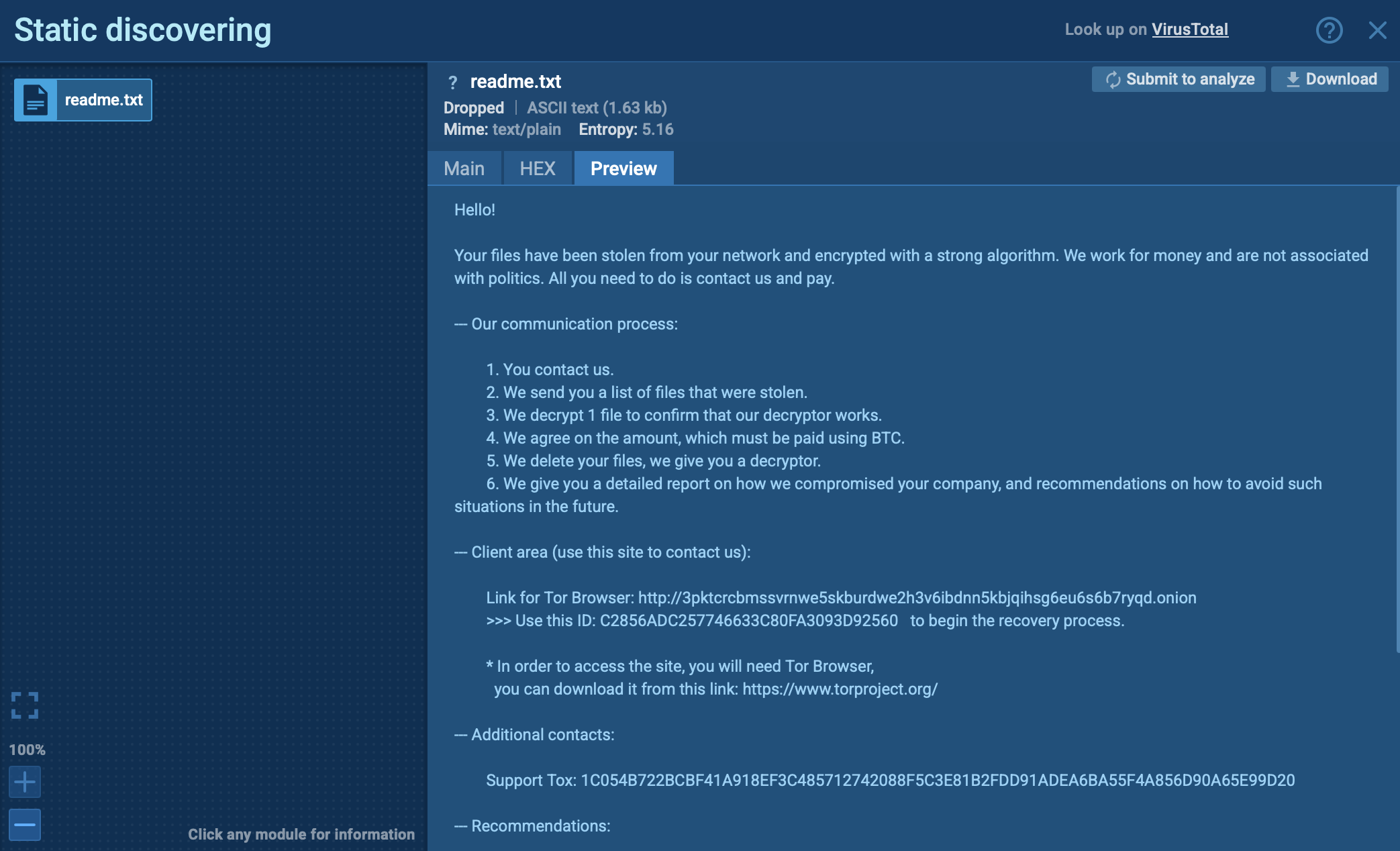 Ransom note with clear instructions exposed inside ANY.RUN sandbox
Ransom note with clear instructions exposed inside ANY.RUN sandbox
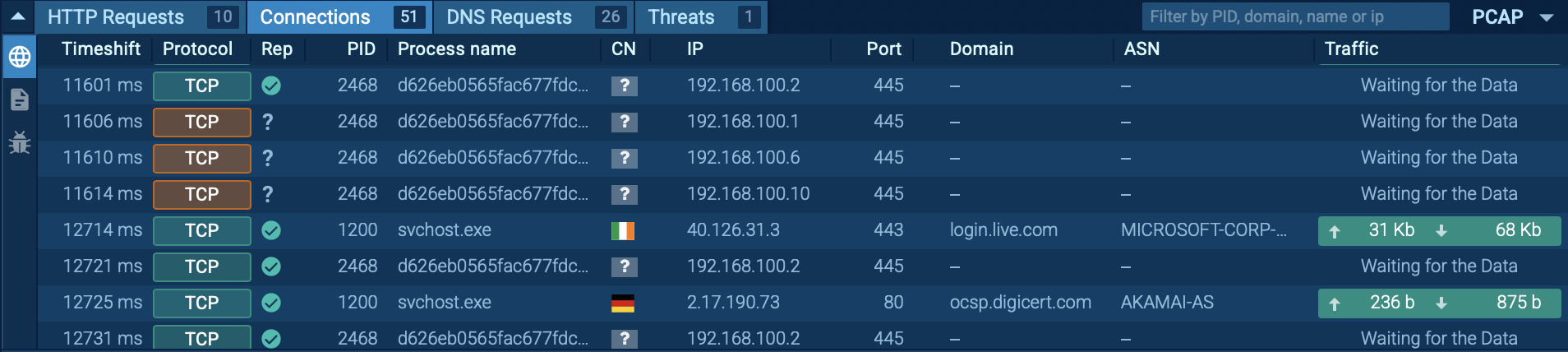 DragonForce scans SMB shares and network devices, attempting to spread laterally across the network
DragonForce scans SMB shares and network devices, attempting to spread laterally across the network
DragonForce is designed for speed, persistence, and maximum disruption. After gaining elevated privileges and disabling recovery options, it quickly encrypts both local and network data using the ChaCha8 algorithm. By renaming files, erasing backups, and spreading across SMB shares, it ensures that victims are left with no recovery path other than ransom negotiations.
DragonForce ransomware is engineered to cause rapid and large-scale disruption, leaving organizations with few options beyond ransom negotiations. Its threat profile extends beyond encrypted files to broader operational, financial, and reputational risks.
Integrating threat intelligence into security operations is important for detecting and mitigating DragonForce attacks. Threat intelligence provides updated indicators of compromise (IOCs), such as malicious file hashes, domains, and network behaviors, which can be used to block activity and uncover infections before encryption begins.
It also supports proactive threat hunting, enabling SOC teams to detect DragonForce based on its known behaviors, including UAC bypass attempts, registry changes for persistence, recovery elimination with tools like vssadmin and wbadmin, and lateral movement through SMB scanning.
Start gathering IOCs and behavioral data with the malware name search request to Threat Intelligence Lookup:
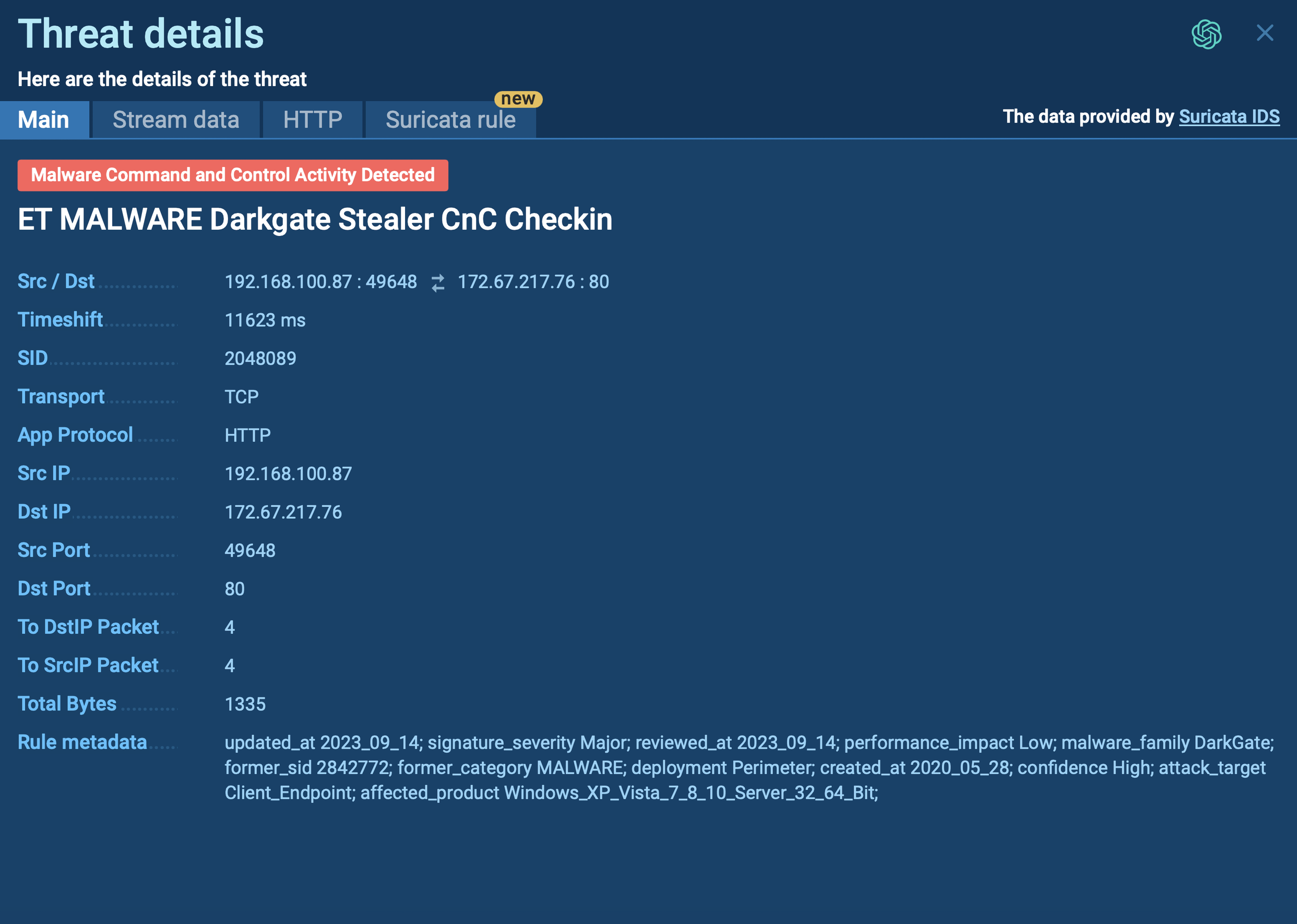
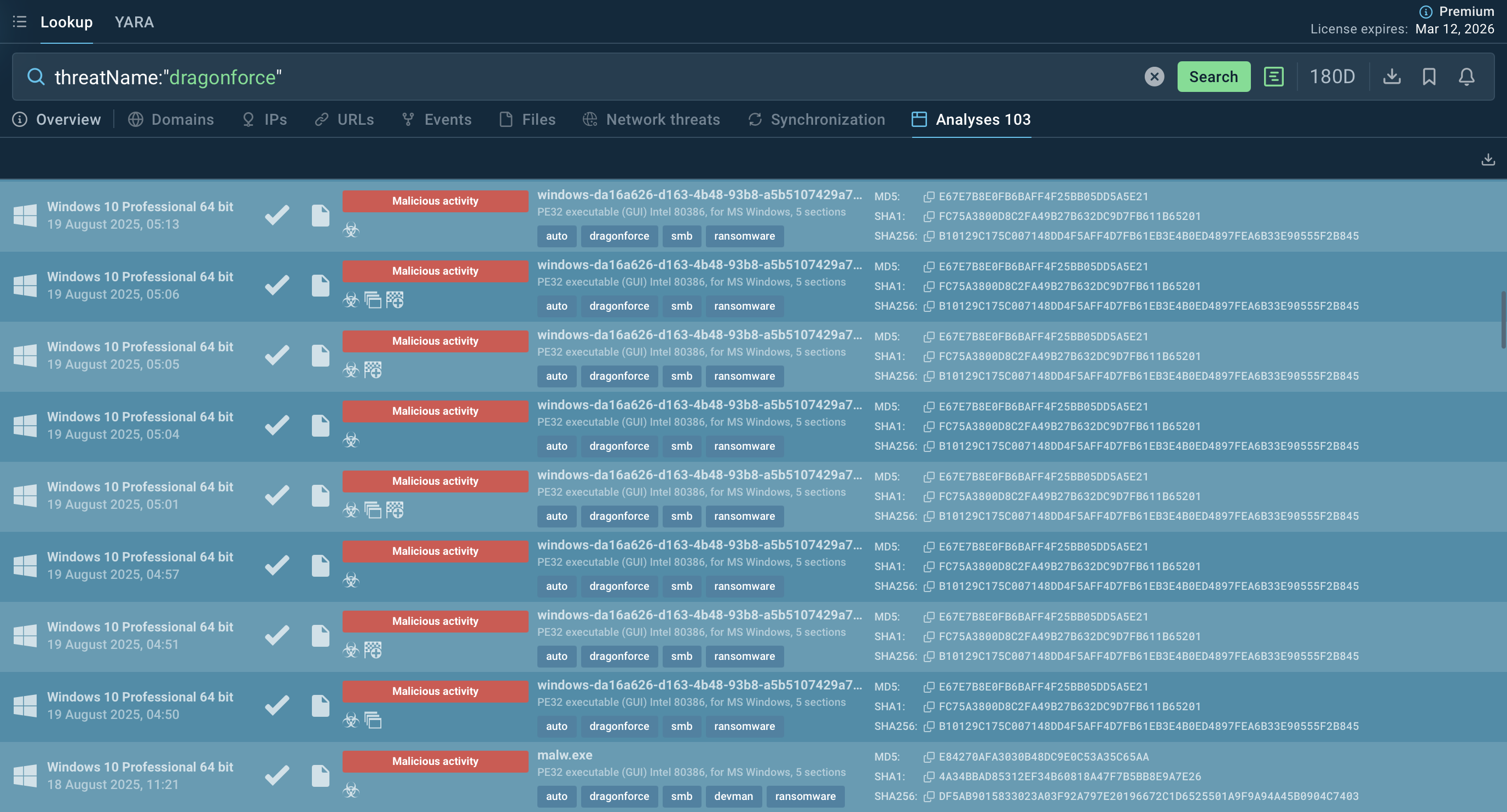 DragonForce ransomware samples found via TI Lookup
DragonForce ransomware samples found via TI Lookup
DragonForce is a destructive ransomware strain built to paralyze organizations. By wiping recovery options, escalating privileges, and encrypting both local and network data with ChaCha8, it leaves victims with no easy way out. The added pressure of double extortion makes it a severe risk for both operations and reputation.
To defend against it, security teams need early detection of behaviors like shadow copy deletion, UAC bypass, and SMB scanning, well before encryption begins. Actionable threat intelligence from ANY.RUN’s TI Lookup helps SOCs spot these patterns and respond faster.
Gather fresh intelligence via ANY.RUN’s TI Lookup: start with 50 trial requests.