Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Cerber is a Ransomware-as-a-Service (RaaS) that appeared in 2016, spread quickly and has been evolving since. It became well-known for its file encryption, offline capabilities, and sophisticated evasion techniques. It primarily targets enterprises, financial institutions, and government entities, encrypting their data and demanding ransom payments in Bitcoin. It also targets everyday users encrypting personal files (photos, documents) with the risk of their permanent loss.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
1 February, 2016
First seen
:
|
27 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 February, 2016
First seen
:
|
27 February, 2026
Last seen
:
|

 793
793
 0
0

 482
482
 0
0

 2730
2730
 0
0
Cerber is a Ransomware-as-a-service that does not require an attacker to be a skilled hacker to deploy it. Since its debut in 2016, it has been frequently updated to bypass signature-based detections.
It mostly arrives at the target network via phishing emails with malicious attachments (zipped .DOT files, Windows Script Files [WSF], or self-extracting archives). Some campaigns include password-protected attachments with the password provided in the email to bypass basic email filters.
Once inside a network, Cerber typically waits for an opportune moment (e.g., system reboot or user idle time) to execute, increasing its chances of going unnoticed initially. Then the malware scans local and network drives for specific file types (documents, databases, media). It encrypts the found files using AES-256 and RSA-2048 encryption.
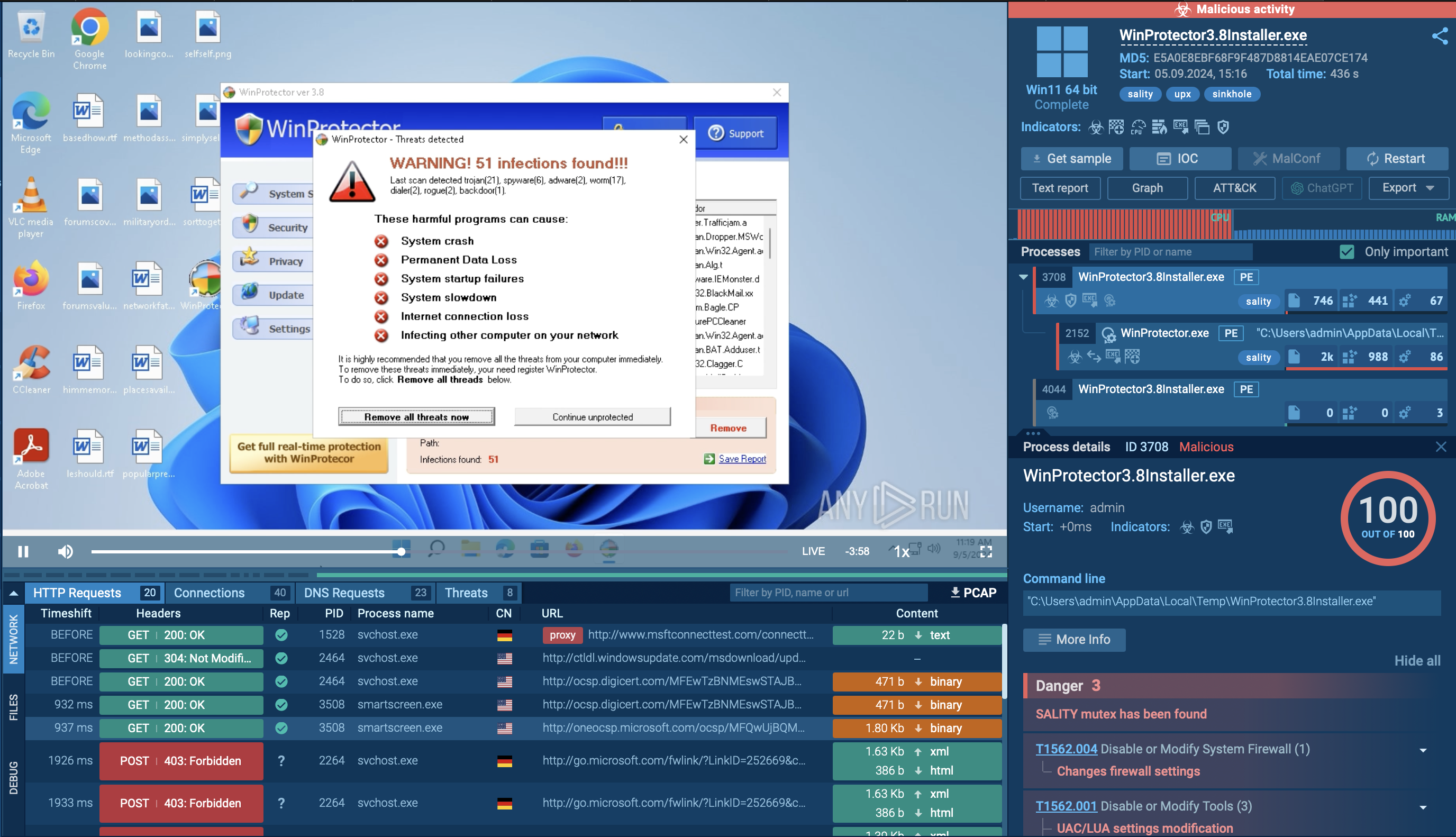
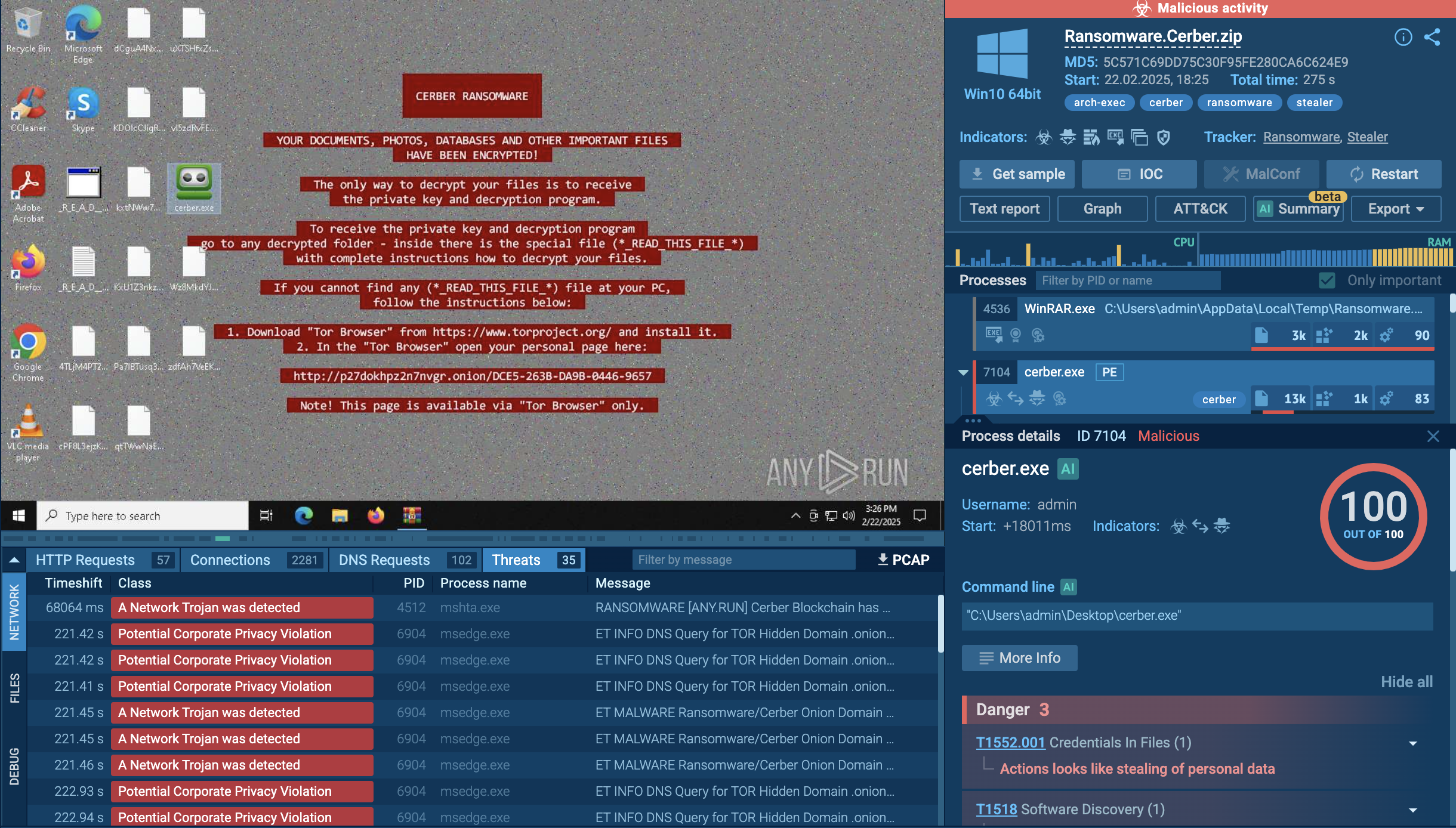 Analysis of Cerber Ransomware in the ANY.RUN sandbox
Analysis of Cerber Ransomware in the ANY.RUN sandbox
It deletes shadow copies of the decrypted files and disables recovery options; after the operations are finished, Cerber generates a ransom note and deletes its executable to minimize forensic evidence.
Cerber is equipped with advanced capabilities as it:
Let's use ANY.RUN's Interactive Sandbox to analyze a sample of the Cerber Ransomware to see how it operates.
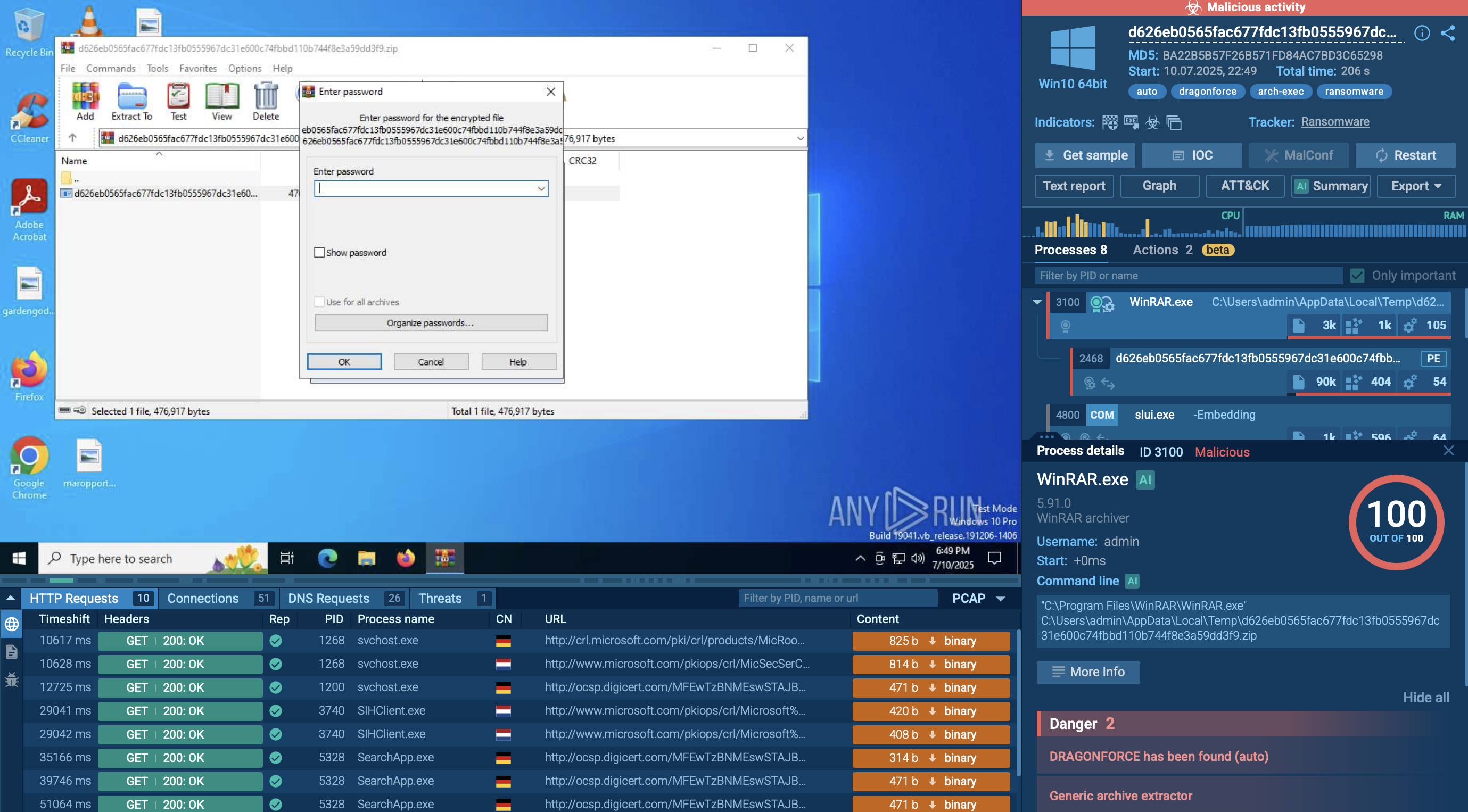
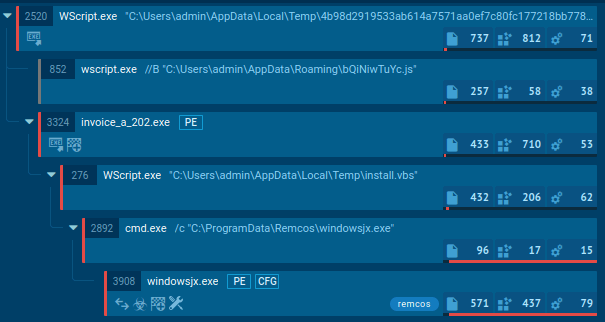
Cerber ransomware uses a multi-stage execution chain, often starting with distribution via phishing emails. These emails typically include malicious attachments—either zipped Windows Script Files (WSF) or Microsoft Office files (.DOC or .DOCX). The WSF file directly installs Cerber, while the Office documents prompt users to enable macros, which then download and install the malware. Cerber has also been observed exploiting known vulnerabilities to gain initial access.
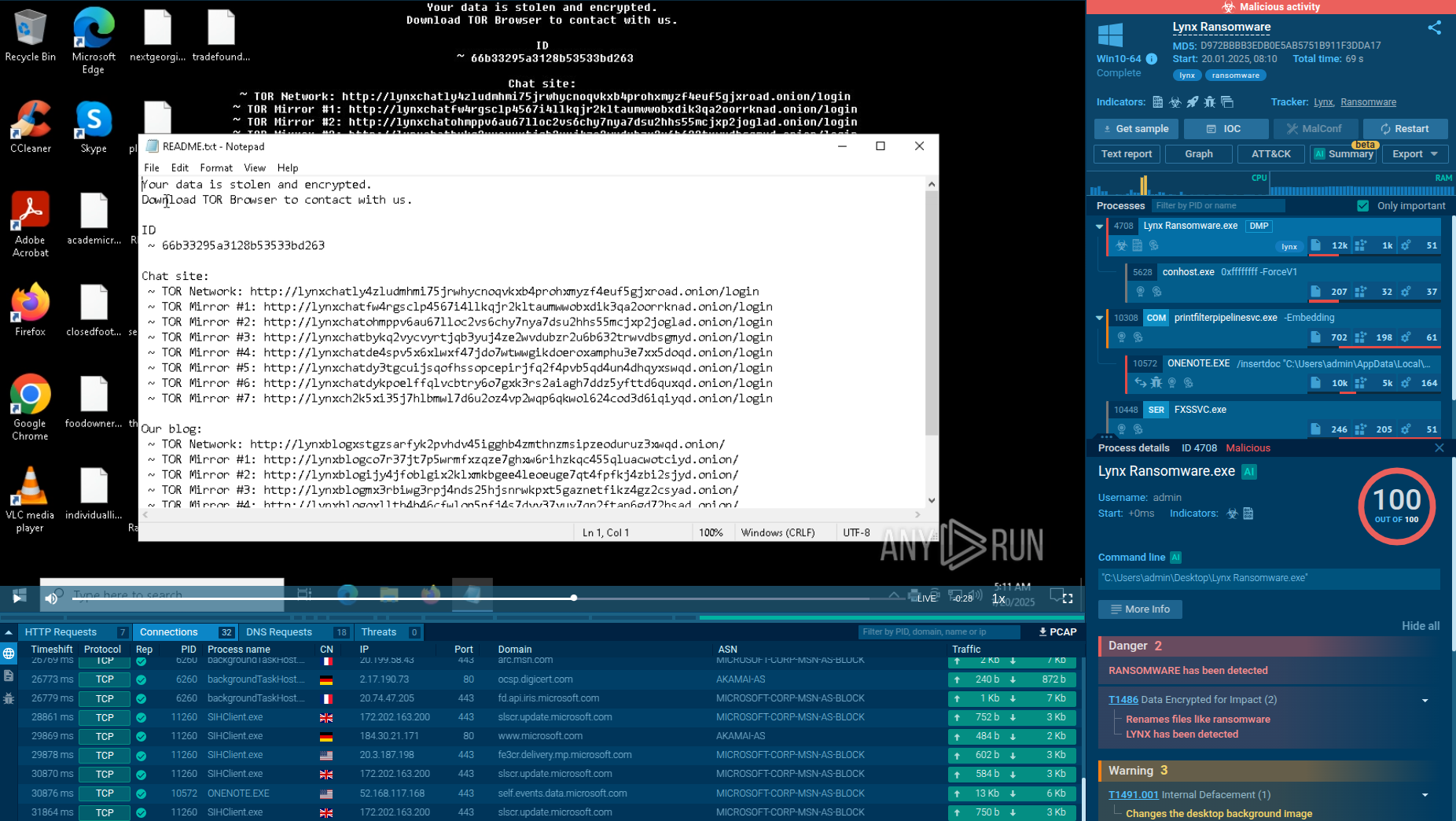
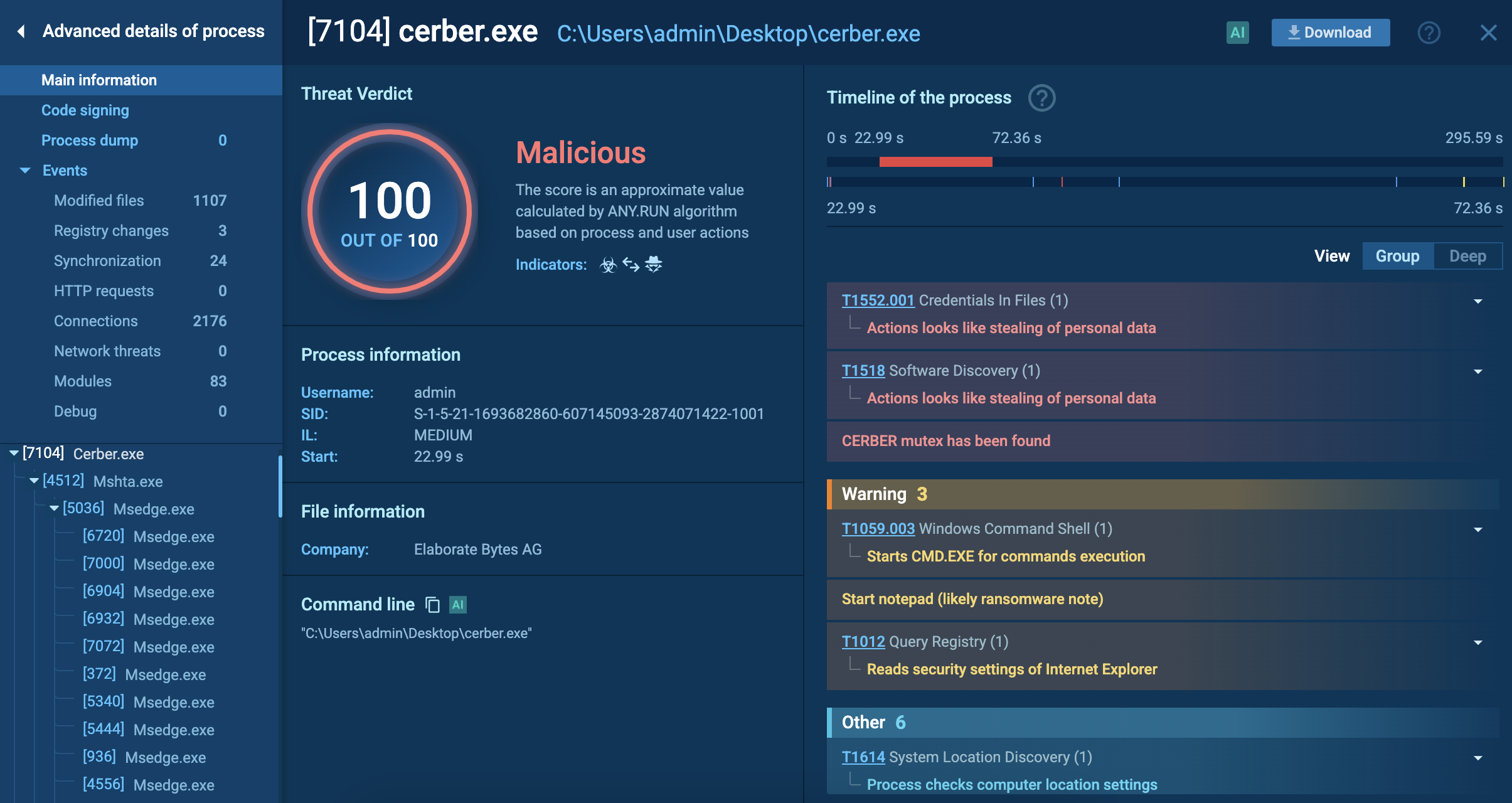 Process analysis of Cerber ransomware in ANY.RUN's Interactive Sandbox
Process analysis of Cerber ransomware in ANY.RUN's Interactive Sandbox
Once executed, Cerber may check for specific mutexes to avoid reinfecting the same machine. In this case, the mutex is SHELL.{9C578142-9AC8-5286-EEAE-C741EB3192B8}, and the ransomware also created several additional mutexes. It checks the system’s country location and terminates if it detects an ex-USSR region. To evade detection, Cerber can configure Windows Firewall rules to block outbound traffic from security tools. Some versions add a time delay to the attack chain to evade sandbox analysis.
Cerber often reboots the system into Safe Mode with Networking, then back to normal mode before initiating the encryption process. It uses AES-256 and RSA to encrypt files, appends a custom extension, and renames files with randomly generated strings. In this analysis, the extension used was “.ae90.” Cerber stores ransom instructions locally, can change the desktop wallpaper, and launches a ransom note in HTA format using mshta.exe. Finally, it deletes its own file from the infected system to conceal its presence.
Countering Cerber demands proactive threat hunting and protective measures. Leverage threat intelligence to track Cerber-related indicators of compromise like C2 domains & IPs, hashes of known Cerber variants, Tor-based payment portals used by attackers (e.g., port 6893 with specific packet structures like Machine GUID hashes).
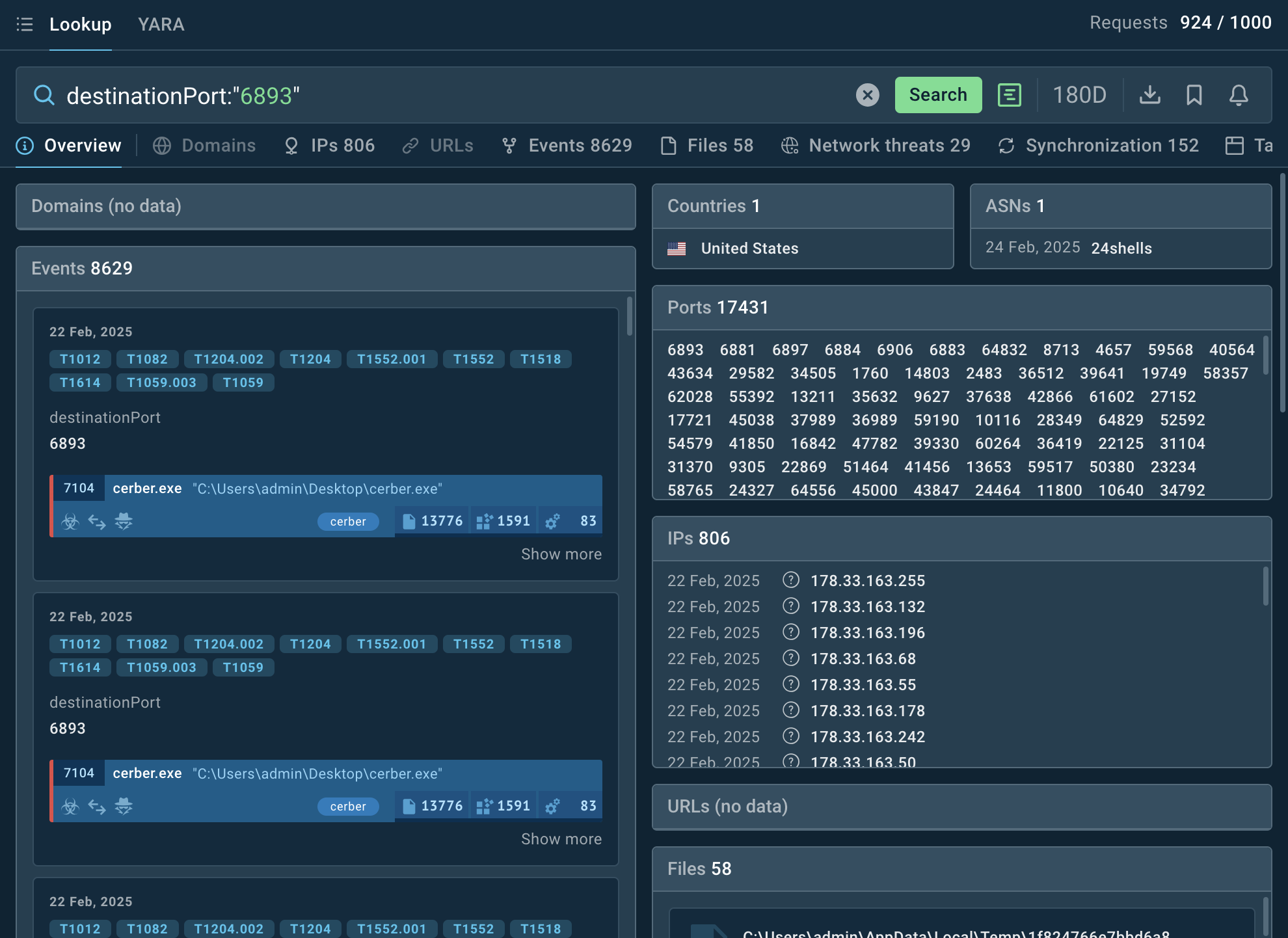 TI Lookup helps users collect fresh intel on Cerber Ransomware attacks
TI Lookup helps users collect fresh intel on Cerber Ransomware attacks
Threat Intelligence Lookup by ANY.RUN delivers fresh contextual data on IOCs and provides a selection of the malware’s samples in action detonated in the Interactive Sandbox. Learn more about TI Lookup.
TI Lookup search by a port typically engaged by Cerber gives a number of IOCs for further research: associated URLs, files, mutexes, etc.
Cerber stands out as a highly adaptive ransomware threat, blending traditional infection vectors with cutting-edge evasion techniques. Its danger lies in its ability to target both individuals and organizations, steal data, and disrupt operations while evading detection. By combining robust endpoint security, network monitoring, and real-time threat intelligence, defenders can detect and neutralize Cerber effectively.