Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


Dridex is a very evasive and technically complex banking trojan. Despite being based on a relatively old malware code, it was substantially updated over the years and became capable of using very effective infiltration techniques that make this malware especially dangerous.
|
Trojan
Type
:
|
ex-USSR territory
Origin
:
|
|
1 January, 2014
First seen
:
|
18 January, 2026
Last seen
:
|
|
Type
:
|
ex-USSR territory
Origin
:
|
|
1 January, 2014
First seen
:
|
18 January, 2026
Last seen
:
|

 861
861
 0
0

 511
511
 0
0

 2797
2797
 0
0
Dridex is one of the most technologically advanced banking trojans currently active. The primary target of this malware is stealing banking credentials from its victims. Dridex has been around since 2014 and has benefited from very consistent updates that helped the malware evolve and become more and more capable.
Thanks to constant evolution, Dridex currently supports very advanced functions like the Atom Bombing injection technique, web injects into Chrome, and Microsoft Word zero-day exploit which helped the Dridex malware to make its way into countless machines despite available removal tools.
Dridex is classified to be the evolution of the GameOver ZeuS, borrowing a C&C architecture from this virus and further improving upon it, making control servers very hard to pinpoint. The Dridex banking trojan also features similarities to other malware – CRIDEX and Bugat. However, while the latest relies mostly on vulnerabilities as an attack vector, Dridex also uses mail spam to infect the machines of its victims.
According to the new information, US and UK law enforcement organizations uncovered the identities of people behind Evil Corp — the cybergang that developed Dridex and several other malicious programs. Maxim Yakubets who is living in Moscow is suspected to be the group’s leader. He has been seen driving a Lamborghini Huracan with a number plate that reads “thief” in Russian. As a result of the investigation, the US Department of State has announced a $5 million reward for turning in Yakubets. This is the largest reward ever offered for a cybercriminal.
The spike in the popularity of the Dridex trojan was recorded in the period between its first spotting in the wild until the year 2015. The subsequent malicious campaigns were fewer in number and perhaps not as global as the ones observed before 2015. Usually, the malware targets victims in Europe with over half of recorded infections taking place in the UK, though, German, French, and US users are also in danger. Notably Dridex banking trojan never attacks victims in the Russian Federation, which could indicate that the group behind this threat comes from this country. Dridex is one of the most popular banking trojans in the world, placing at the seventh spot out of the top ten most widely spread viruses of this type by the number of infections in 2015, according to the data of flashpoint-intel.
The malware can perform a series of data-stealing actions including Form-grabbing, clickshot taking, and site injections. This allows Dredex to steal sensitive data such as logins and passwords when the victim logs into their banking account. This data can then be used by the attackers in future campaigns or sold to other criminals. In addition, the malware is capable of taking screenshots, allowing hackers to collect personal information about the victim. What’s more, the malware is able to change the content of web pages that the user is viewing using web-inject techniques, so when the user enters his login and password, instead of logging into a personal account this sensitive data is sent directly to the attackers.
Dridex trojan uses a Botnet as a Service operation model which entitles that infected PCs can become attack sources for future campaigns. This helps the malware to spread more efficiently and makes its attacks more global.
Some of the previous versions of this malware used to have a fairly unique persistence mechanism which researchers called “invisible”. It was dubbed so because the malware’ dynamic link library (DLL) was saved on a disk, and a registry value was generated to run the malicious DLL at system startup just only before the PC would be turned off.
The new version of Dridex’s maldocs contains hundreds of URLs from which to download the malware. This approach makes malware hard to take down by hosting providers, removal tools, and domain registers. It also increases the chances of downloading the payload. Security controls need to block a big number of URLs to prevent the malware from being downloaded.
Dridex was once again updated and stopped using the debug output message loop. Malware actors also switched their defense evasion technique from the usage of XSL Script Processing (ID T1220) to Signed Binary Proxy Execution using Rundll32 (ID T1218.011).
During 2020 the "team" behind Dridex heavily used Excel malicious documents with Macro 4.0 in its campaigns. Often these maldocs checked the language of the system in which they were opened and quit execution if it didn’t match.
A video simulation recorded on ANY.RUN allows us to examine the lifecycle of the Dridex malware. You can also investigate other cyber threats like FormBook and Lokibot.
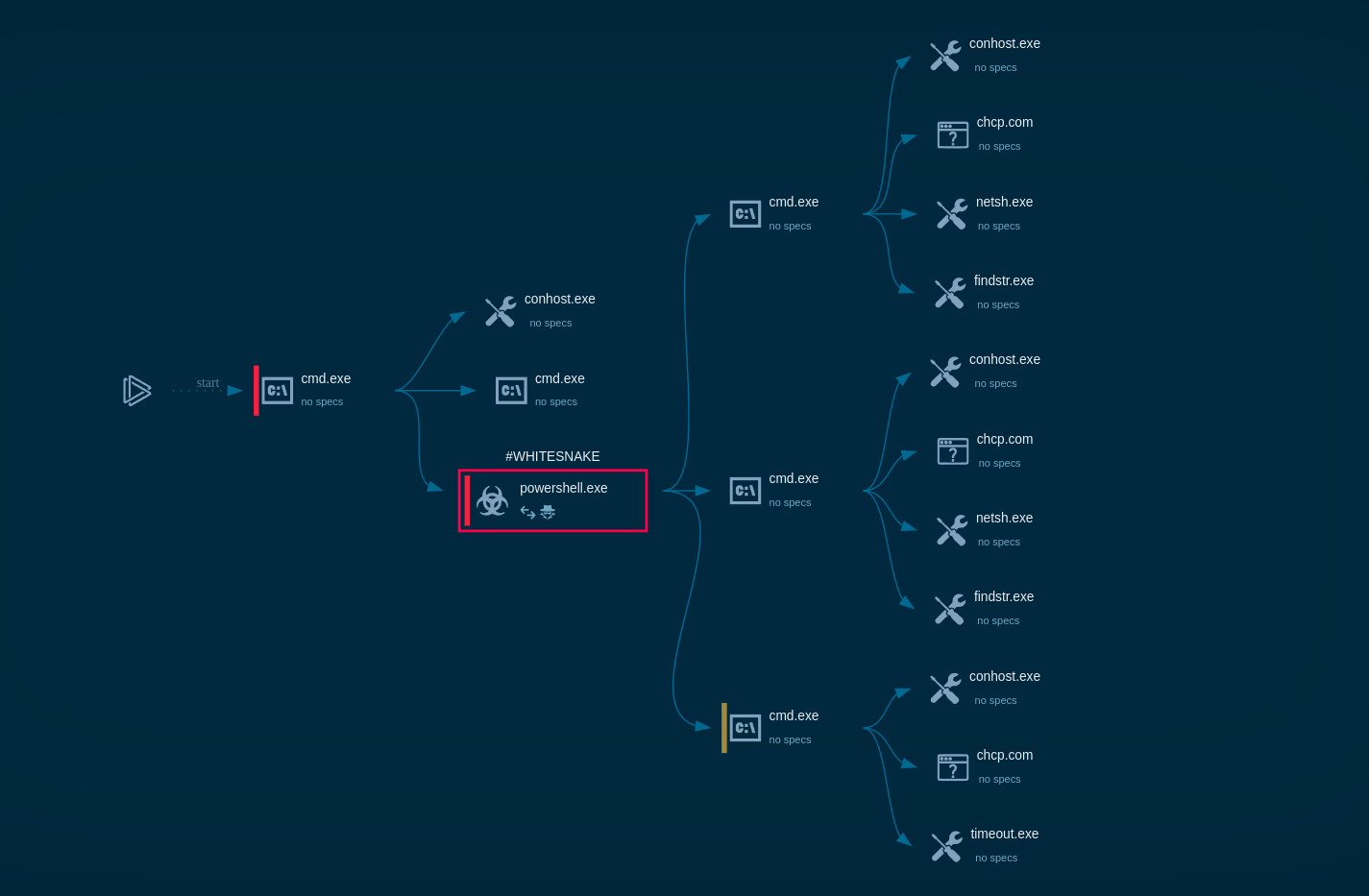
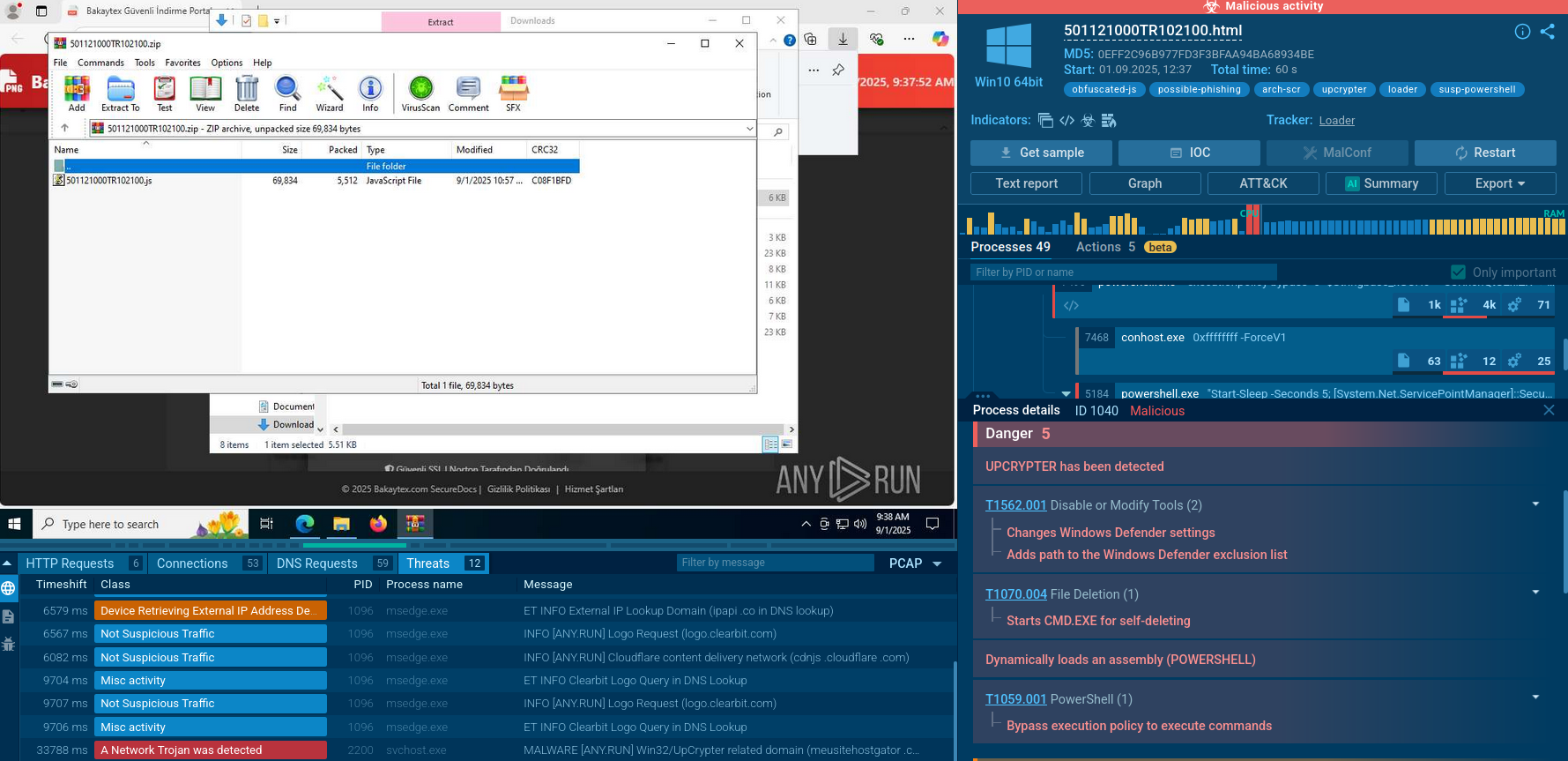
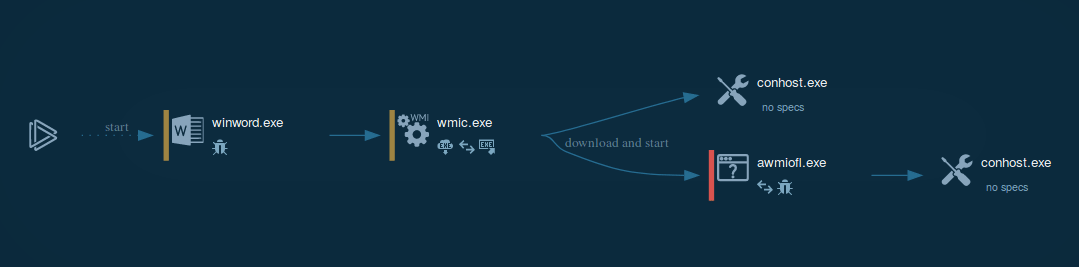 Figure 1: Process graph generated by ANY.RUN allows us to see the main processes of Dridex execution.
Figure 1: Process graph generated by ANY.RUN allows us to see the main processes of Dridex execution.
 Figure 2: Displays the customizable text report generated by ANY.RUN.
Figure 2: Displays the customizable text report generated by ANY.RUN.
The execution process of Dridex is pretty short and straightforward. Similar to a lot of malware nowadays, the banking trojan makes its way into the victim's system as a malicious attachment, usually a Microsoft Office file, which is delivered in spam emails. After the user downloads and opens such a file and enables macros, the infection process begins. Dridex trojan is capable of utilizing different techniques to deliver the main payload. The payload can be downloaded directly by Microsoft Office or by injected system applications, for example, explorer.exe, or leveraged by the vulnerabilities exploit such as Microsoft Equation Editor. After the downloaded payload starts execution, it begins the main malicious activity such as writing itself into autorun in the registry, searching for installed software, executing scripts, connecting to the C2 server, and more.
Users can avoid getting infected by banking trojans such as Dridex by staying clear of suspiciously-looking emails. To stay completely safe one should never launch files downloaded from emails that were delivered from unknown senders. A clear indication of the malicious nature of downloaded files can be that when opened, Microsoft Office files will prompt the user to enable macros – something users should never do to avoid infection. Additionally, it is advised to keep an updated version of a trusted antivirus product and removal tools on a machine at all times.
Dridex mainly spreads using spam email campaigns and makes its way into targeted machines in the form of malicious email attachments. The emails are designed to resemble financial-related messages, such as invoice delivery from real businesses, and usually contain a malicious Microsoft Office document as an attachment.
Social engineering is used to trick potential victims into downloading and opening attached files, which when run execute a malicious macro that installs the Dridex banking trojan on the machine.
If Dridex detection trojan wasn't successful or you want to double-check you can use additional ANY.RUN functionality to get more from your analysis. During execution, Dridex unpacks itself in memory and enters the long-drawn-out loop. On each loop iteration malware output debug string "Installing...", so if you run into this first, think that Dridex detection is complete.
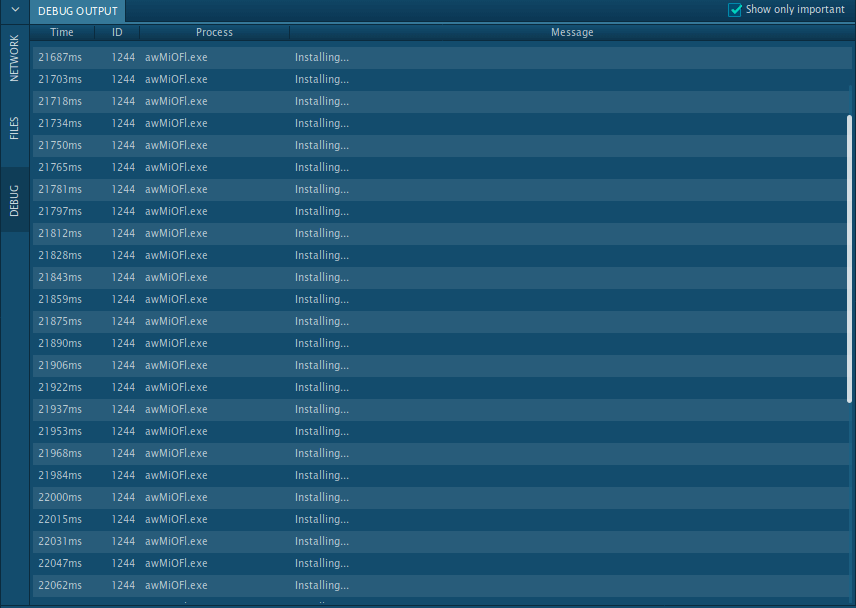 Figure 3: Dridex debug output
Figure 3: Dridex debug output
Even though Dridex popularity has declined somewhat since its initial release, it is still an extremely popular and capable malware that is used in several attacks targeting companies in Europe and North America. Thanks to advanced persistence mechanisms and almost untraceable C&C servers, Dridex attacks are very hard to battle, making this virus extremely effective.
Thankfully, malware hunting services like ANY.RUN allow researchers to perform detection and analysis of threats similar to Dridex to set up effective countermeasures.