Webinar
February 26
Better SOC with Interactive Sandbox
Practical Use Cases


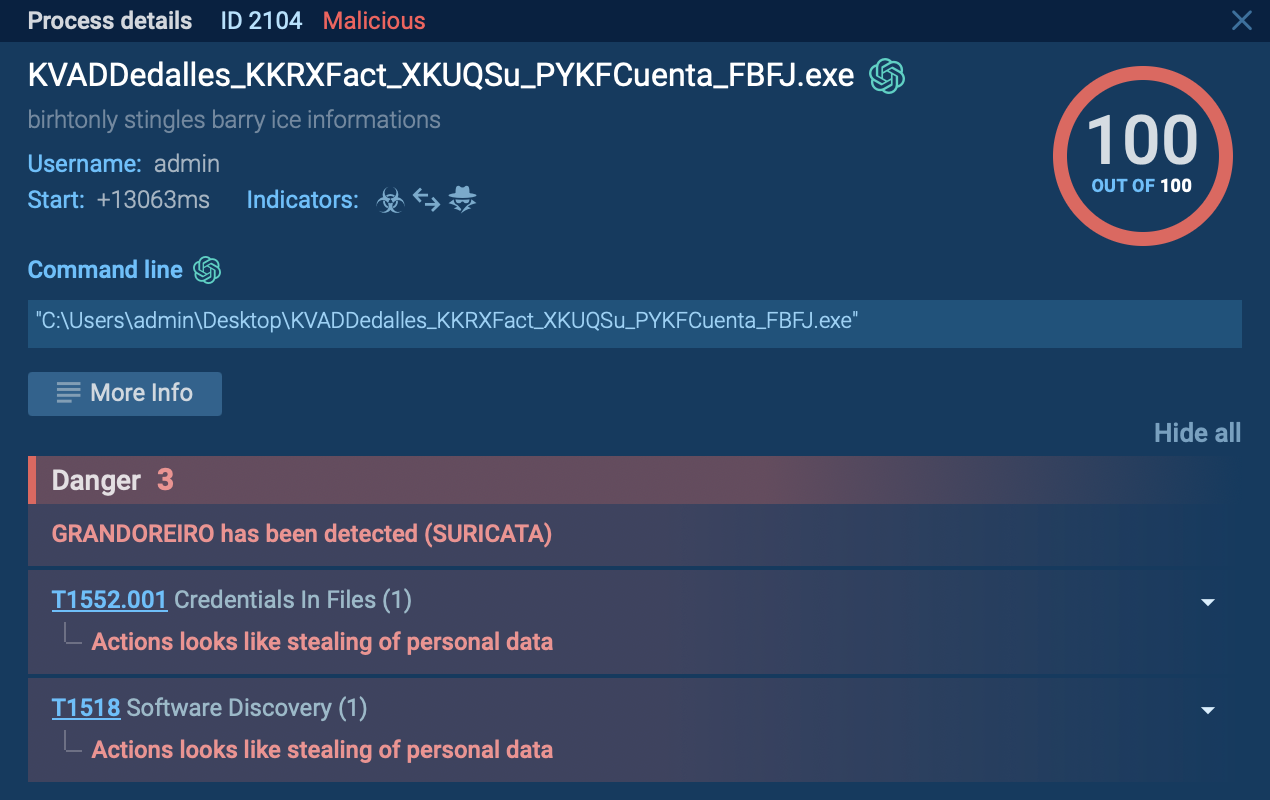
Virlock is a unique ransomware strain that combines encryption capabilities with file infection techniques. First observed in 2014, it stands out due to its polymorphic nature and ability to embed its code into compromised files, ensuring continued propagation. Once it infects a system, it encrypts files and locks the screen, demanding a ransom for file recovery and system access.
|
Ransomware
Type
:
|
Unknown
Origin
:
|
|
1 December, 2014
First seen
:
|
26 February, 2026
Last seen
:
|
|
Type
:
|
Unknown
Origin
:
|
|
1 December, 2014
First seen
:
|
26 February, 2026
Last seen
:
|

 833
833
 0
0

 497
497
 0
0

 2767
2767
 0
0
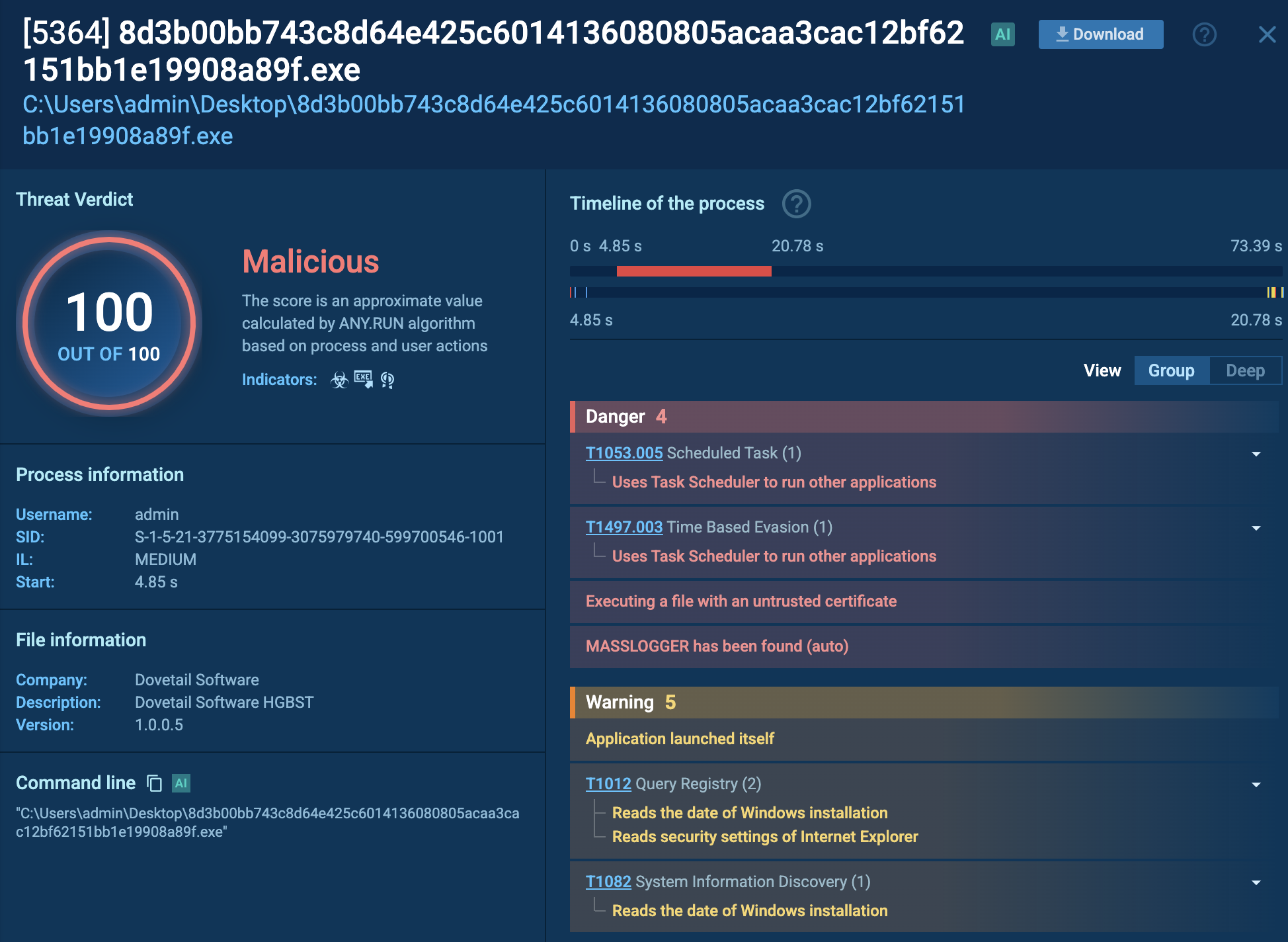
Virlock is a unique form of ransomware that combines traditional file encryption with virus-like propagation methods. First identified in 2014, it not only encrypts files but also embeds its malicious code into them, allowing it to spread across systems via shared drives and removable media. Once executed, Virlock locks the victim's screen and displays a ransom note, often masquerading as a legal warning, demanding payment for file recovery and system access.
You can see an example of a ransom note displayed inside ANY.RUN’s sandbox:
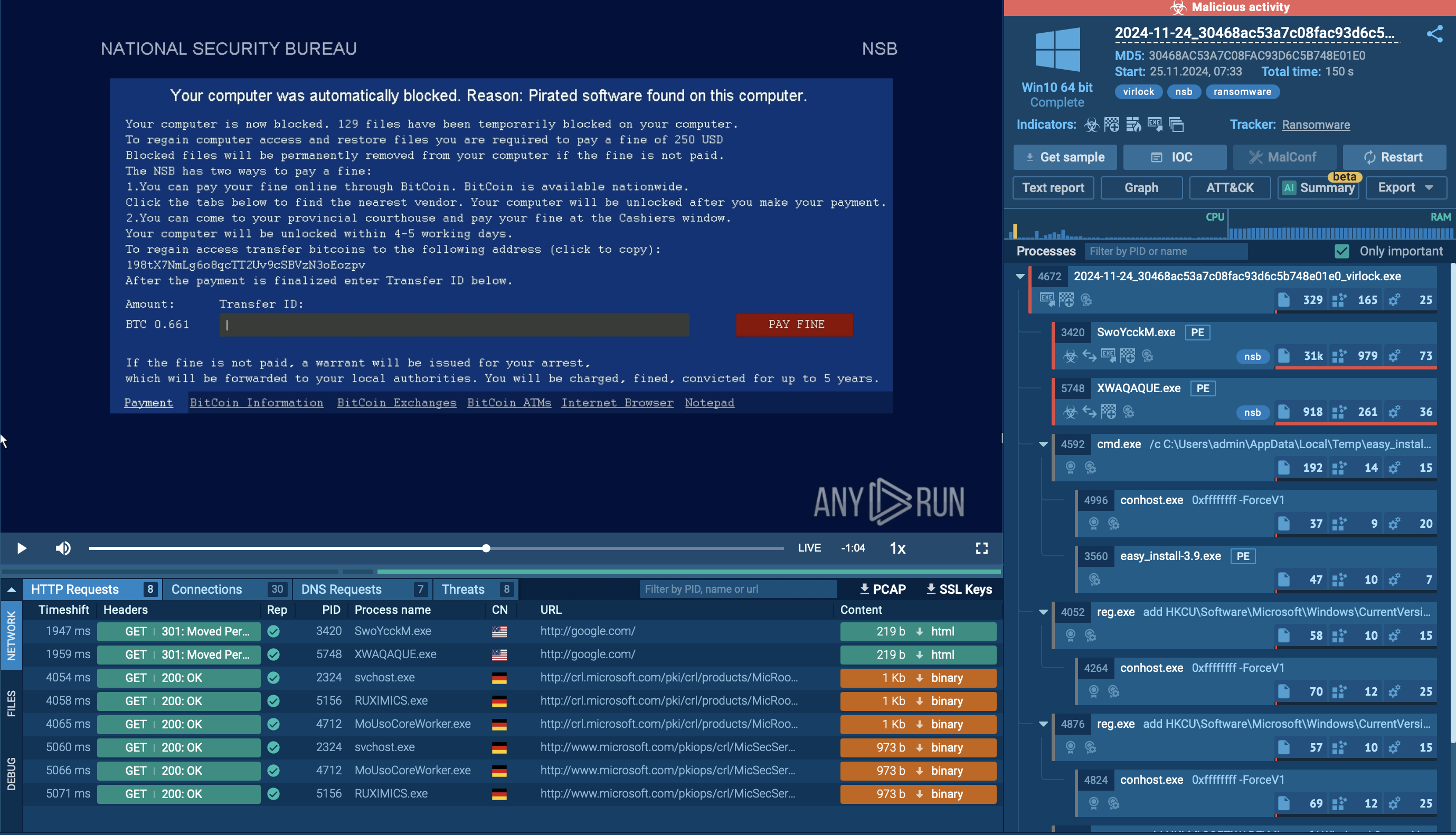 Ransom note displayed in ANY.RUN sandbox
Ransom note displayed in ANY.RUN sandbox
While specific large-scale attacks attributed solely to Virlock are not extensively documented, its unique propagation method poses significant risks, especially in environments that rely heavily on file sharing and collaboration tools. In 2016, security researchers highlighted Virlock's capability to spread through cloud storage and collaboration applications, emphasizing the potential for rapid, widespread infection within organizations.
Virlock's ability to both encrypt files and convert them into infectious agents makes it particularly dangerous. Even if a ransom is paid, residual infected files can lead to reinfection.
Virlock employs polymorphic techniques to evade detection. It changes its code structure with each infection, making it difficult for traditional signature-based antivirus solutions to recognize and block it.
The primary technical functionalities of Virlock ransomware include:
The Virlock ransomware employs several layers of encryption, including XOR and XOR-ROL (rotate left) algorithms, to obfuscate its code and hinder analysis.
After infecting files, Virlock appends an .exe extension and modifies system settings to hide file extensions, making it harder for users to identify infected files.
Besides, this ransomware drops multiple instances of itself in different locations and registers them as services or startup entries, ensuring it remains active even if some instances are removed.
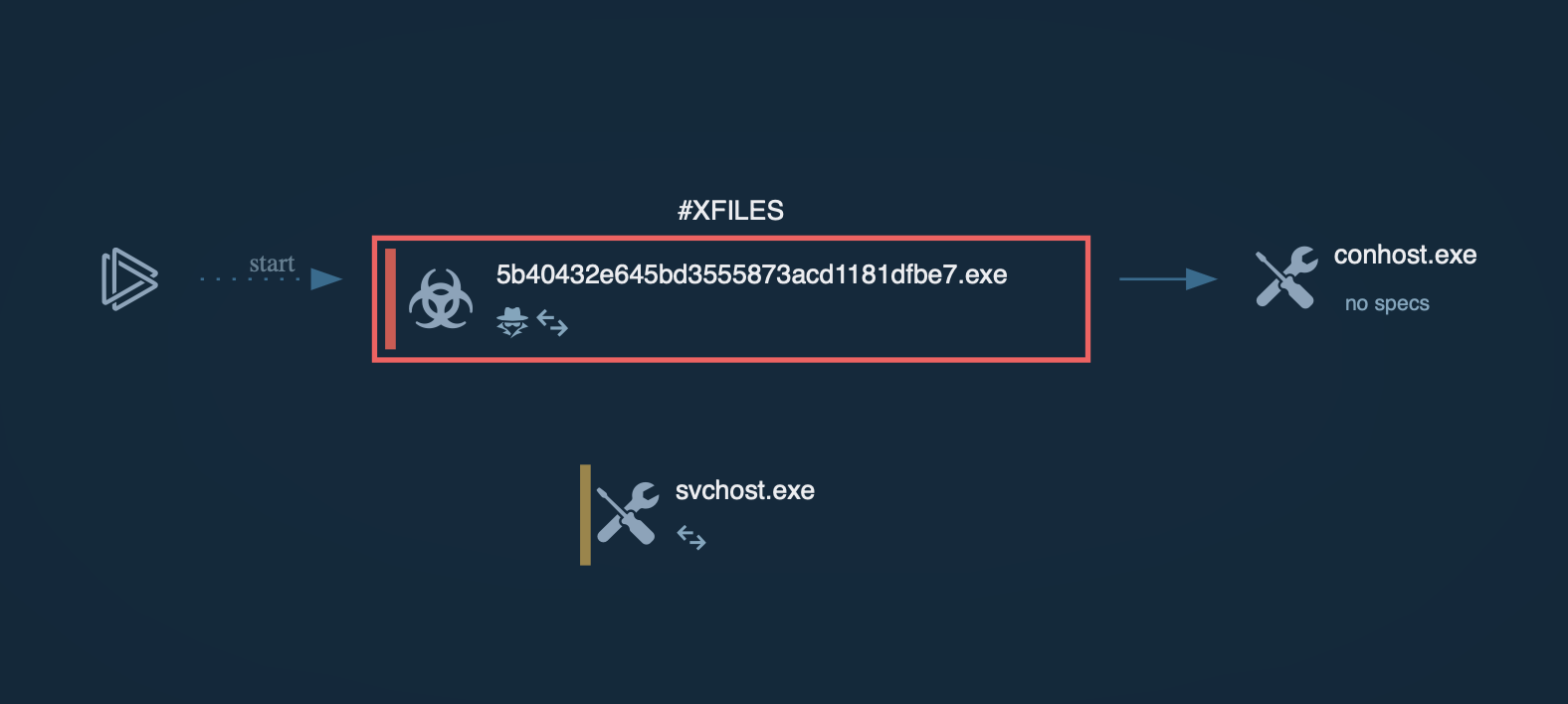
To see how Virlock operates, let’s upload its sample into ANY.RUN’s sandbox.
When Virlock is executed on a non-infected machine, it initiates by deploying three instances of itself, each with a specific function:
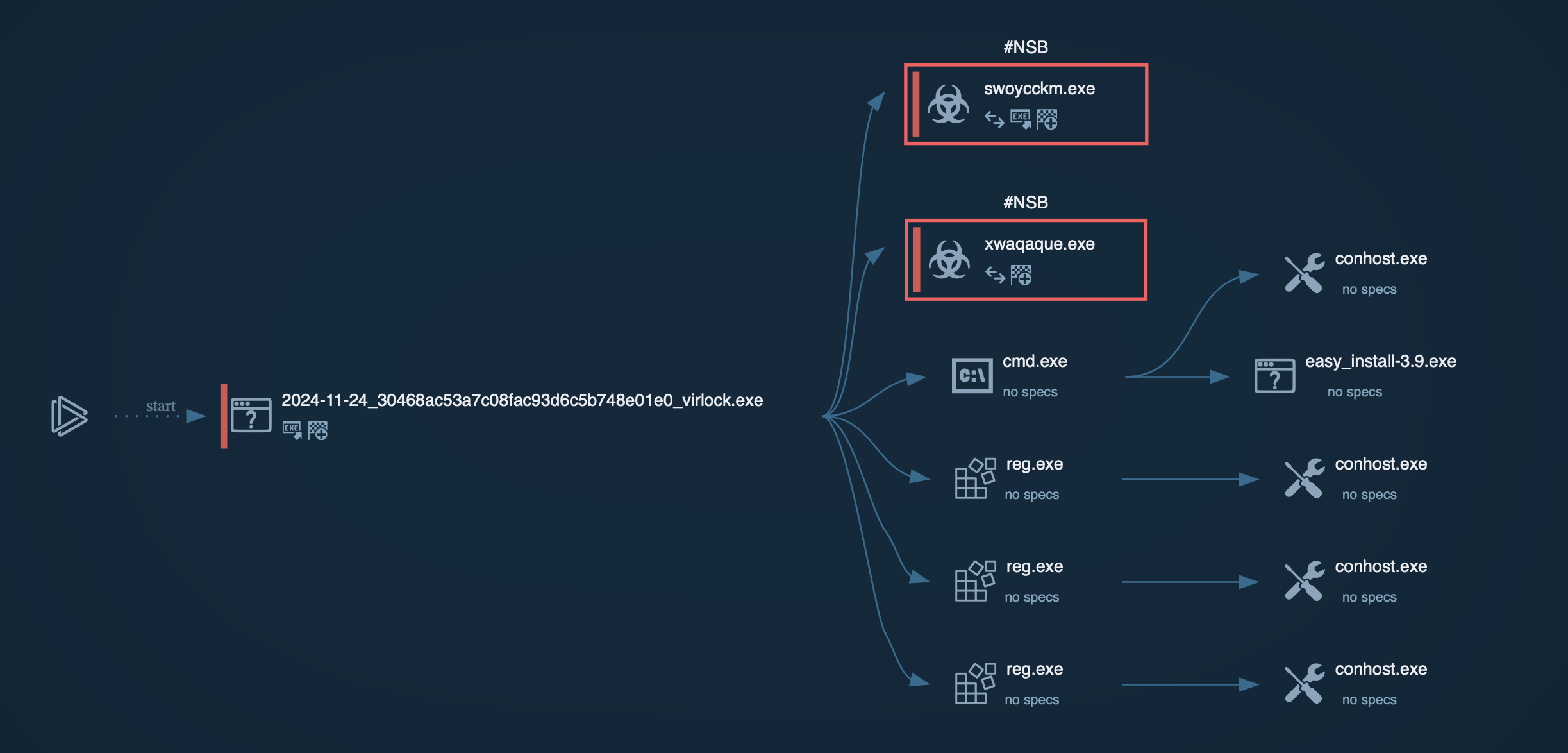 Process graph generated by ANY.RUN sandbox
Process graph generated by ANY.RUN sandbox
Virlock targets various file types, including documents and binary files. Upon locating these files, it encrypts their contents and appends its malicious code to the original file. This process transforms each infected file into a carrier capable of further spreading the ransomware. Any user who opens an infected file inadvertently activates the malware, enabling it to propagate within networks, particularly in cloud environments.
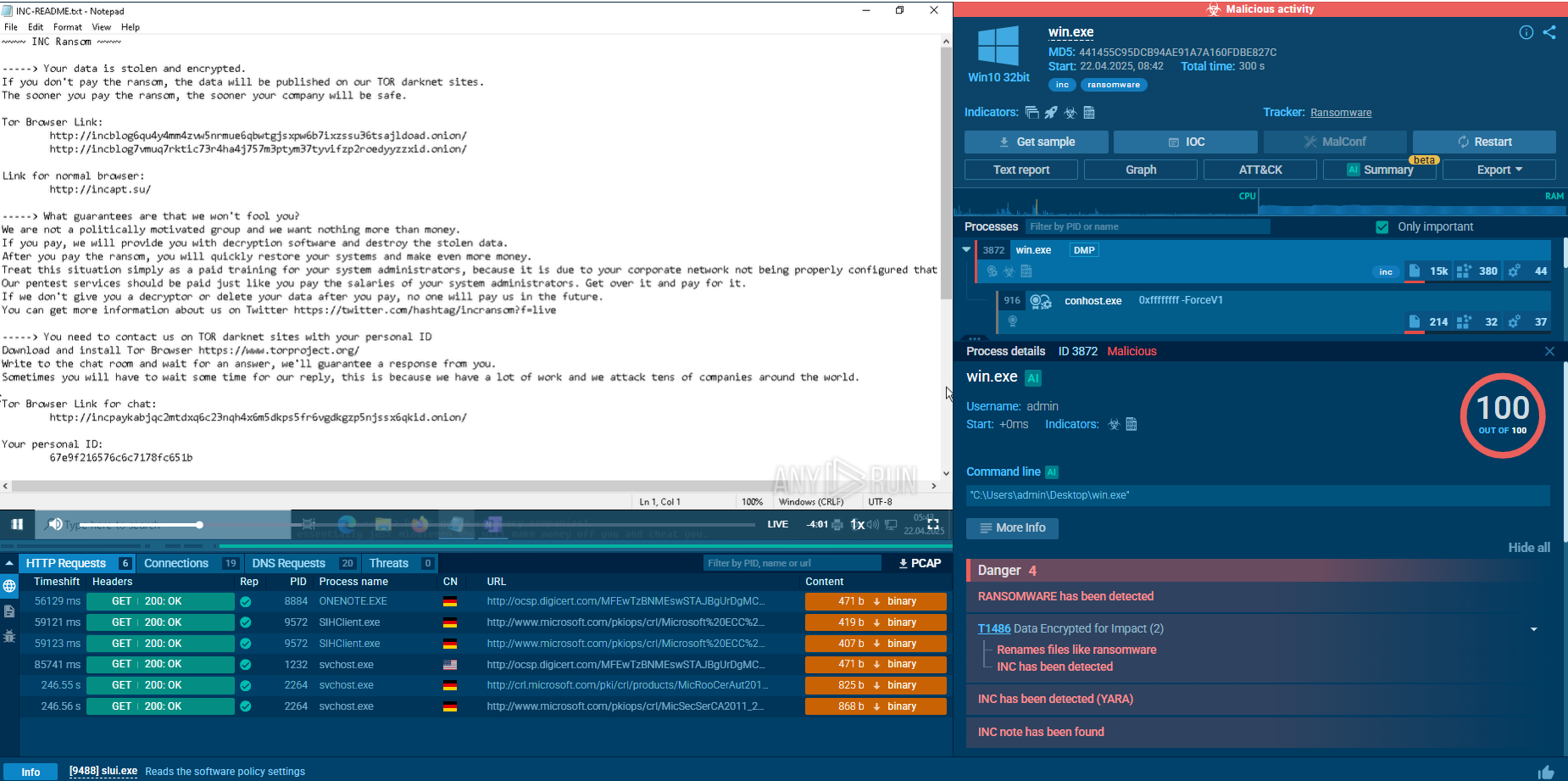
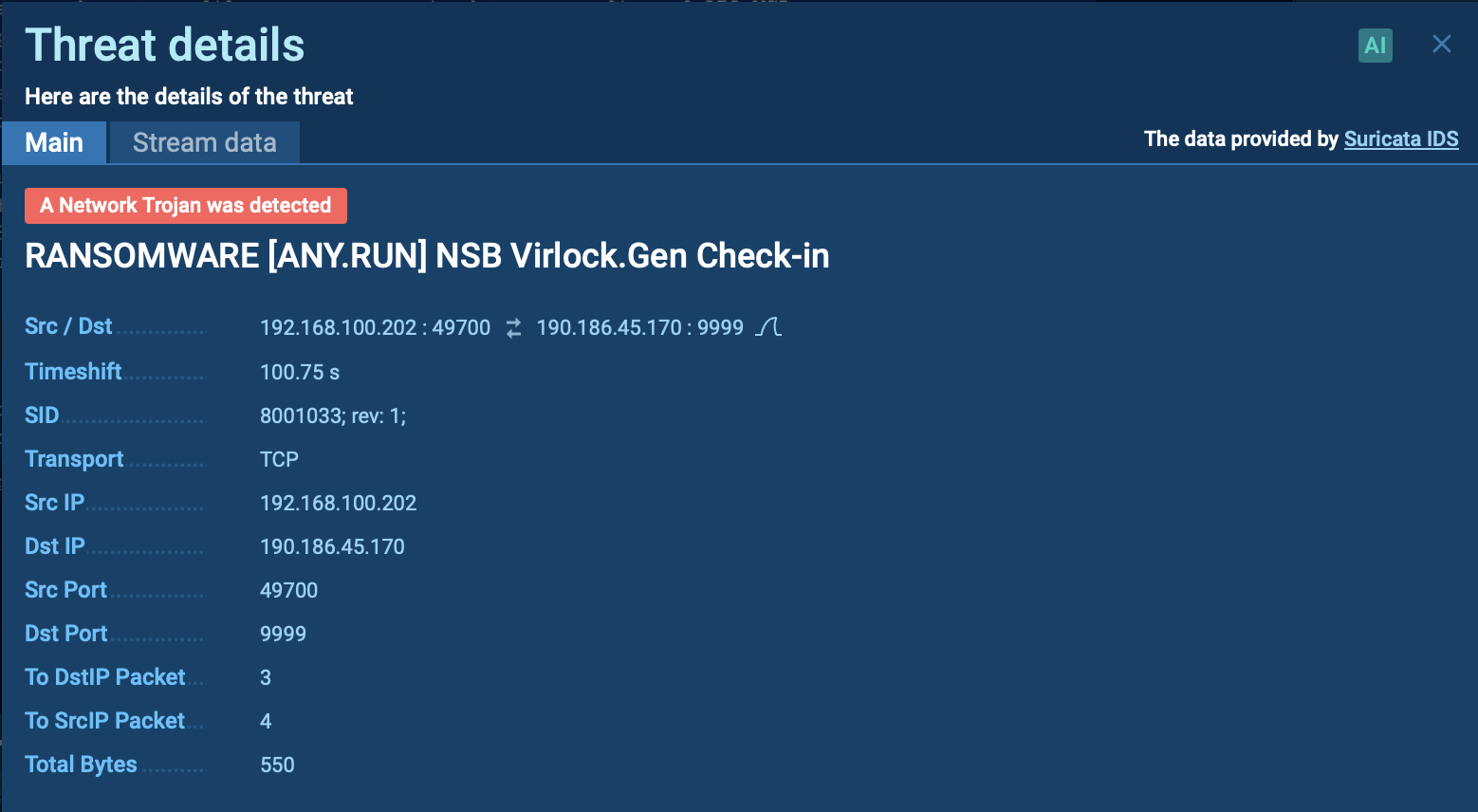 Suricata rule triggered by Virlock ransomware inside ANY.RUN’s sandbox
Suricata rule triggered by Virlock ransomware inside ANY.RUN’s sandbox
To ensure its continued operation even after system reboots, Virlock modifies the Windows registry:
During its operation, the second instance disables critical system processes such as explorer.exe and taskmgr.exe, effectively locking the victim’s screen.
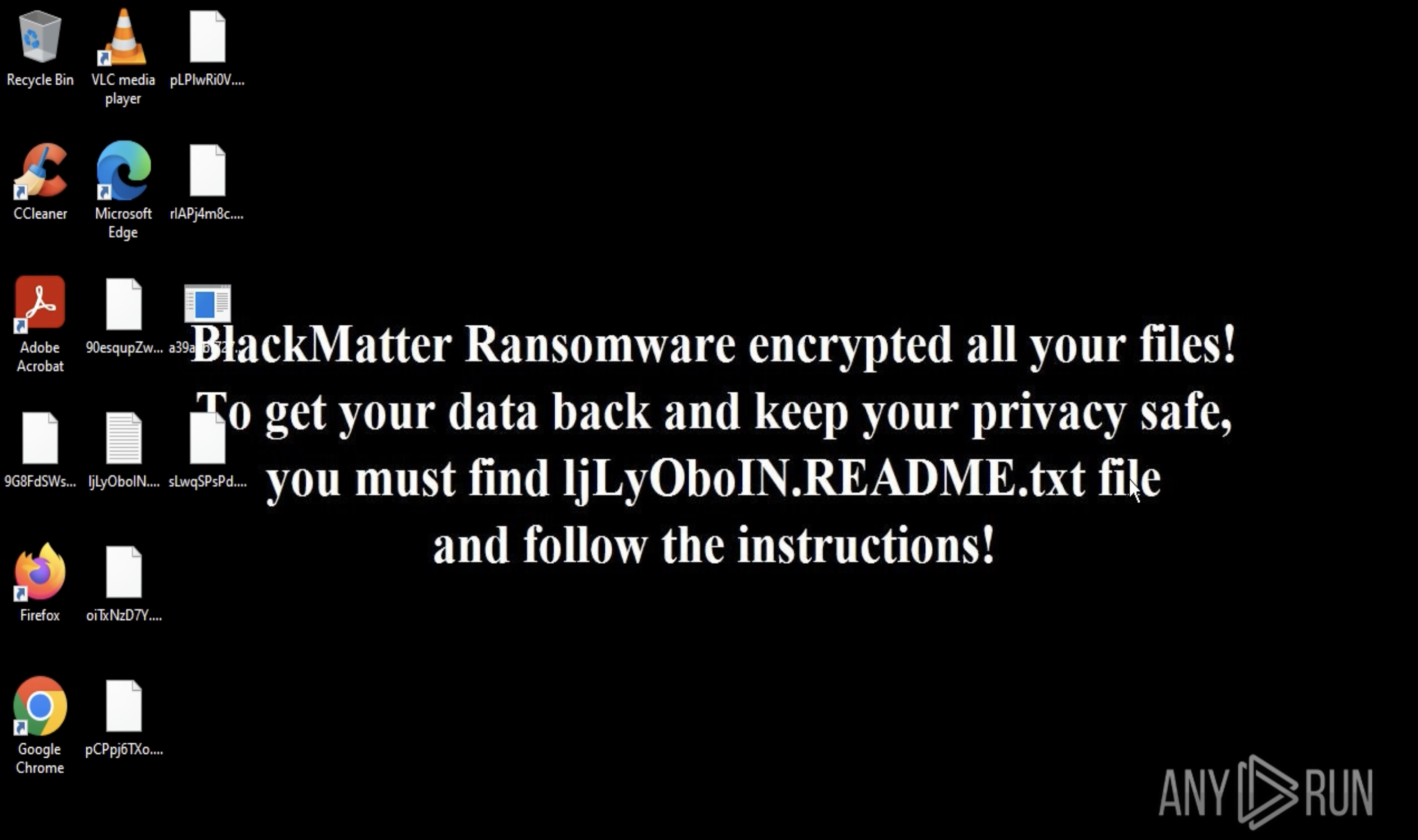
It also customizes the ransom message based on the victim's geolocation, demanding payment in Bitcoin to unlock the system. The ransom note often masquerades as an anti-piracy warning from law enforcement, threatening legal consequences to pressure victims into paying quickly.
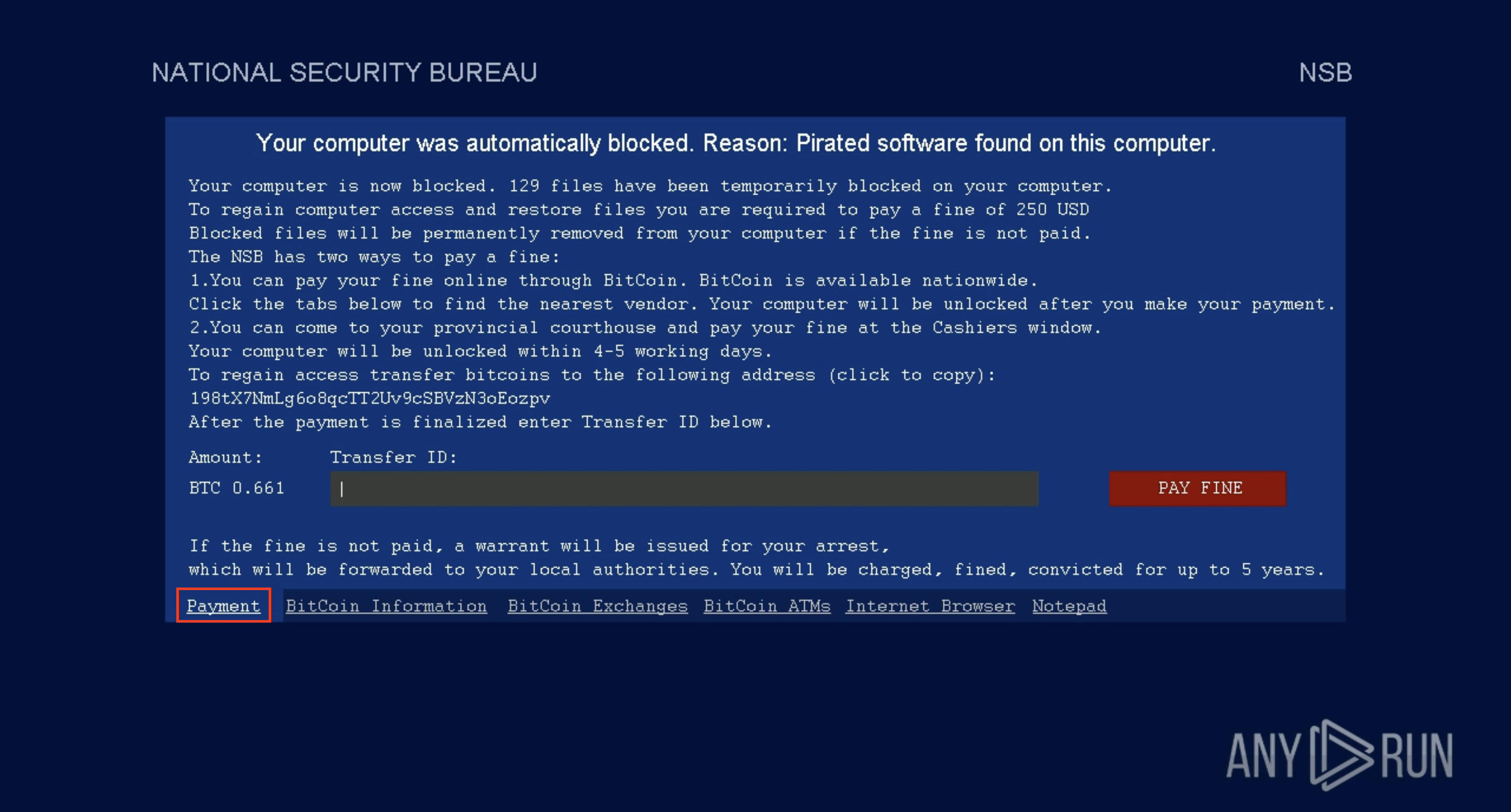 Virlock ransom note requiring payment in Bitcoin
Virlock ransom note requiring payment in Bitcoin
Virlock employs a variety of anti-debugging measures and heavily obfuscated code to hinder analysis and detection:
The ransom note leverages social engineering to manipulate victims, presenting itself as a warning from legal authorities. This tactic is designed to create urgency and confusion, leaving victims less likely to explore alternative options before complying with the ransom demands
To collect up-to-date intelligence on Virlock ransomware, use Threat Intelligence Lookup.
This powerful service provides access to a vast database populated with insights from millions of malware analysis sessions conducted in the ANY.RUN sandbox. With over 40 customizable search parameters, you can search for specific data related to Virlock, including IPs, domains, file hashes, file names, and process artifacts.
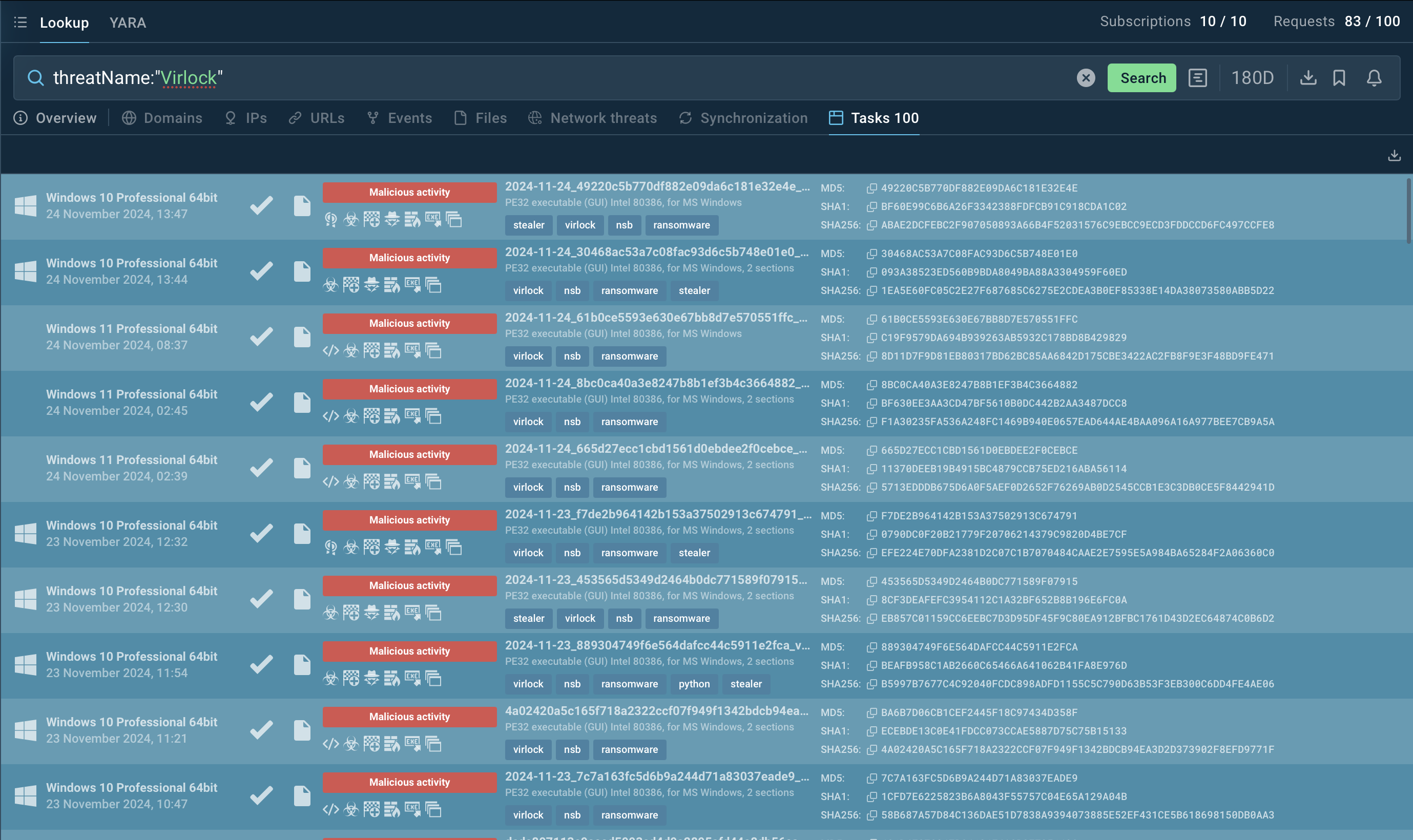 Virlock Lookup Search in ANY.RUN
Virlock Lookup Search in ANY.RUN
To gather intelligence on Virlock, you can search directly for its name or use related artifacts. For example, submitting a query like threatName:"Virlock" in Threat Intelligence Lookup will return a comprehensive list of associated samples and sandbox results, giving you actionable insights into the malware's behavior and indicators of compromise.
Virlock ransomware is a serious threat due to its ability to mutate, infect files, and evade detection, making it both difficult to detect and contain. Using tools like ANY.RUN is essential for proactively analyzing suspicious files and URLs to prevent potential attacks.
ANY.RUN offers real-time malware analysis with features like dynamic sandboxing, behavior tracking, and support for Windows and Linux. Its interactive platform simplifies threat detection and provides detailed insights to enhance cybersecurity defenses.
Sign up for a free ANY.RUN account today and start analyzing emerging threats with no limits!