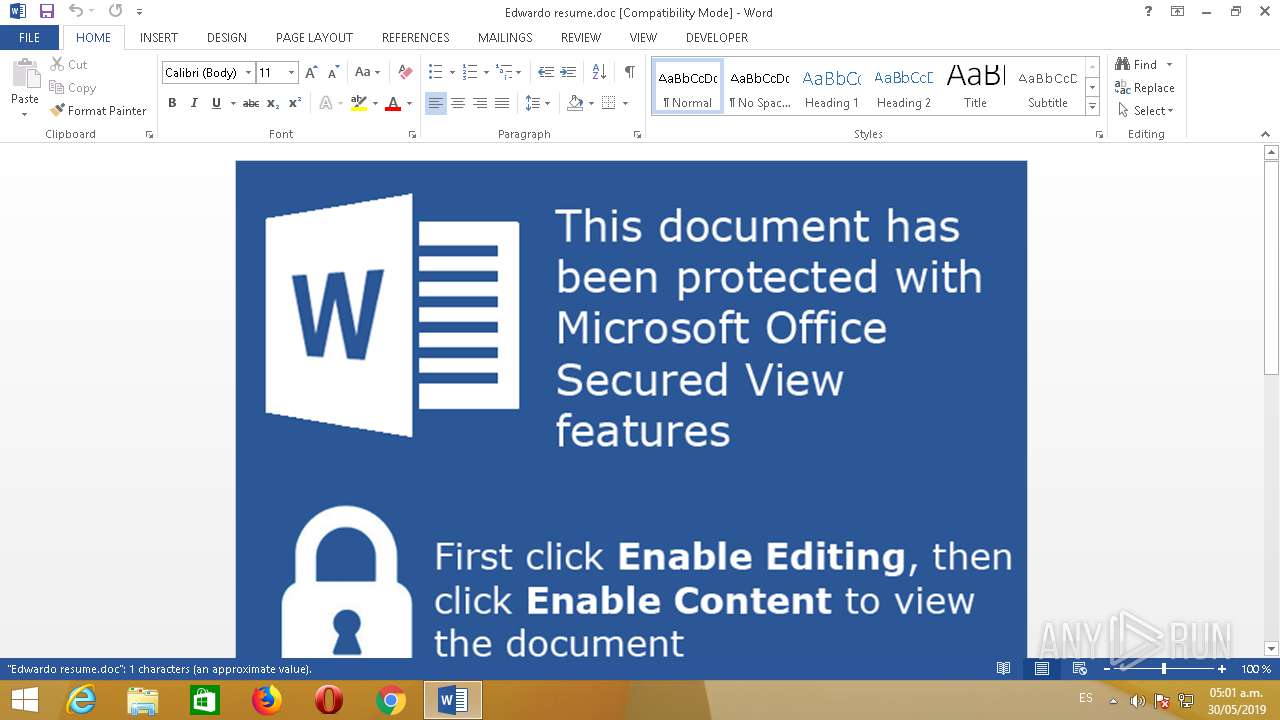
| File name: | Edwardo resume.doc |
| Full analysis: | https://app.any.run/tasks/1ccb505b-27b7-4f88-b095-0ae625f472ee |
| Verdict: | Malicious activity |
| Threats: | Dridex is a very evasive and technically complex banking trojan. Despite being based on a relatively old malware code, it was substantially updated over the years and became capable of using very effective infiltration techniques that make this malware especially dangerous. |
| Analysis date: | May 30, 2019, 08:00:51 |
| OS: | Windows 8.1 Professional (build: 9600, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 27D3E9403115EBC394906D266EDFC9AC |
| SHA1: | AF436ACE53070F9EEC1FF5049A07B950B2FCD9E5 |
| SHA256: | 60D5166AEBF70BDA86E0DD41B777BE550AD364CD310CBAD41780347B463B2689 |
| SSDEEP: | 1536:nALxk6rxmqXx6UoRSUNLmoy2+u1b5bWONWU73SgfqxKi:Af9mPDLmoyKjcUu4qxKi |
MALICIOUS
Application was dropped or rewritten from another process
- awMiOFl.exe (PID: 1244)
Downloads executable files from the Internet
- wmic.exe (PID: 2296)
Downloads executable files from IP
- wmic.exe (PID: 2296)
SUSPICIOUS
Creates files in the Windows directory
- WINWORD.EXE (PID: 932)
- wmic.exe (PID: 2296)
Executable content was dropped or overwritten
- wmic.exe (PID: 2296)
Removes files from Windows directory
- wmic.exe (PID: 2296)
Searches for installed software
- awMiOFl.exe (PID: 1244)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 932)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x746ff8d9 |
| ZipCompressedSize: | 445 |
| ZipUncompressedSize: | 1635 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | 6 minutes |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | home |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 12 |
| Keywords: | - |
| LastModifiedBy: | pablo.warner |
| RevisionNumber: | 10 |
| CreateDate: | 2019:05:22 12:44:00Z |
| ModifyDate: | 2019:05:30 05:22:00Z |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | admin |
| Description: | - |
Total processes
51
Monitored processes
5
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 588 | \??\C:\Windows\system32\conhost.exe 0xffffffff | C:\Windows\system32\conhost.exe | — | awMiOFl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 6.3.9600.16384 (winblue_rtm.130821-1623) Modules
| |||||||||||||||
| 932 | "C:\Program Files\Microsoft Office 15\Root\Office15\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Edwardo resume.doc.docm" /o "" | C:\Program Files\Microsoft Office 15\Root\Office15\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 15.0.4433.1506 Modules
| |||||||||||||||
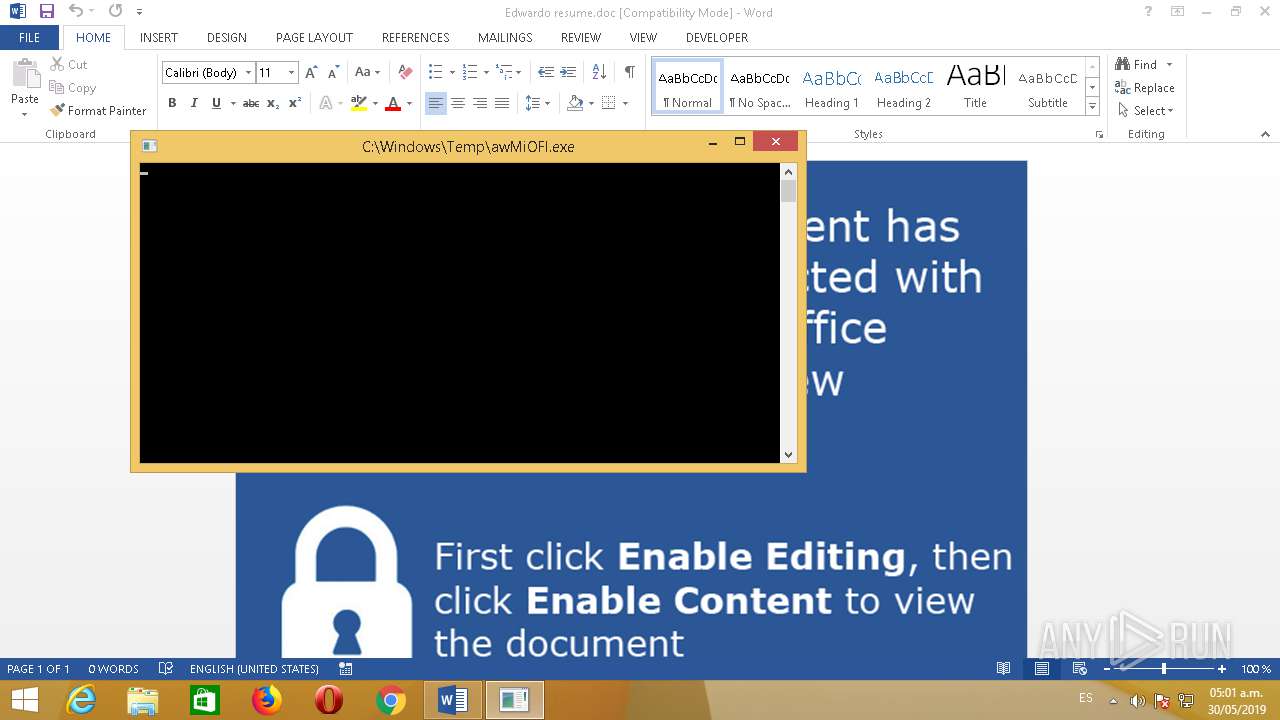
| 1244 | "C:\Windows\Temp\awMiOFl.exe" | C:\Windows\Temp\awMiOFl.exe | wmic.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: SPCtl DLL Exit code: 0 Version: 1, 0, 0, 9 Modules
| |||||||||||||||
| 2236 | \??\C:\Windows\system32\conhost.exe 0xffffffff | C:\Windows\system32\conhost.exe | — | wmic.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 6.3.9600.16384 (winblue_rtm.130821-1623) Modules
| |||||||||||||||
| 2296 | wmic os get /format:"C:\\Windows\\Temp\\aXwZvnt48.xsl" | C:\Windows\SysWOW64\Wbem\wmic.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 3221225547 Version: 6.3.9600.16384 (winblue_rtm.130821-1623) Modules
| |||||||||||||||
Total events
2 968
Read events
999
Write events
1 928
Delete events
41
Modification events
| (PID) Process: | (932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | fx9 |
Value: 66783900A40300000100000000000000D17F5ADFBD16D50100000000 | |||
| (PID) Process: | (932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 11274 |
Value: On | |||
| (PID) Process: | (932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Word |
| Operation: | write | Name: | MTTT |
Value: A40300006A3C62D9BD16D50100000000 | |||
| (PID) Process: | (932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | i}9 |
Value: 697D3900A40300000400000000000000B1B20FE0BD16D5018C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | i}9 |
Value: 697D3900A40300000400000000000000B1B20FE0BD16D5018C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Common\Roaming |
| Operation: | write | Name: | RoamingConfigurableSettings |
Value: B800000000000000803A0900E307050004001E00080001001800AB02000000000000000000000000201C0000201C00008051010080510100805101008051010080F4030080F4030080F403002C01000084030000805101000000000084030000805101000A0000001E0000001E000000000000000000000080510100010000000100000000000000000000000000000000000000008D2700008D2700008D2700010000000A00000080510100000030000000300000003000 | |||
| (PID) Process: | (932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Common\Roaming |
| Operation: | write | Name: | RoamingLastSyncTime |
Value: E307050004001E00080001001800AB02 | |||
| (PID) Process: | (932) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Common\Roaming |
| Operation: | write | Name: | RoamingLastWriteTime |
Value: E307050004001E00080001001800AB02 | |||
Executable files
2
Suspicious files
2
Text files
1
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 932 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRAC97.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 932 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\2ECCE926.png | — | |
MD5:— | SHA256:— | |||
| 932 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$wardo resume.doc.docm | pgc | |
MD5:— | SHA256:— | |||
| 932 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2296 | wmic.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\IFB0YWPX\5[1].exe | executable | |
MD5:— | SHA256:— | |||
| 2296 | wmic.exe | C:\windows\temp\awMiOFl.exe | executable | |
MD5:— | SHA256:— | |||
| 1244 | awMiOFl.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 1244 | awMiOFl.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 932 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 932 | WINWORD.EXE | C:\Windows\Temp\aXwZvnt48.xsl | xml | |
MD5:B52D790F96FE1A504939D194C8DE4C65 | SHA256:5984FDFDF8F180CD06DB7ED978ADD90D805FEDCAB9BC1855F5B48A89895D487F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
2
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2296 | wmic.exe | GET | 200 | 209.141.46.175:80 | http://209.141.46.175/5.exe | US | executable | 260 Kb | malicious |
1244 | awMiOFl.exe | GET | 200 | 13.107.4.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?c518e8a7ab1cb476 | US | compressed | 56.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2296 | wmic.exe | 209.141.46.175:80 | — | FranTech Solutions | US | malicious |
1244 | awMiOFl.exe | 198.46.157.251:443 | — | ColoCrossing | US | malicious |
1244 | awMiOFl.exe | 13.107.4.50:80 | ctldl.windowsupdate.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2296 | wmic.exe | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
2296 | wmic.exe | A Network Trojan was detected | ET TROJAN Single char EXE direct download likely trojan (multiple families) |
2296 | wmic.exe | A Network Trojan was detected | ET CURRENT_EVENTS Possible Malicious Macro DL EXE Feb 2016 |
2296 | wmic.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2296 | wmic.exe | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
1244 | awMiOFl.exe | A Network Trojan was detected | ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex) |
1244 | awMiOFl.exe | A Network Trojan was detected | ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex) |
1244 | awMiOFl.exe | A Network Trojan was detected | MALWARE [PTsecurity] Dridex/Feodo SSL connection |
Process | Message |
|---|---|
WINWORD.EXE | SHIMVIEW: ShimInfo(Complete)
|
awMiOFl.exe | SHIMVIEW: ShimInfo(Complete)
|
awMiOFl.exe | Installing...
|
awMiOFl.exe | Installing...
|
awMiOFl.exe | Installing...
|
awMiOFl.exe | Installing...
|
awMiOFl.exe | Installing...
|
awMiOFl.exe | Installing...
|
awMiOFl.exe | Installing...
|
awMiOFl.exe | Installing...
|